AZ-104 : Microsoft Azure Administrator : Part 10
AZ-104 : Microsoft Azure Administrator : Part 10
-
You have five Azure virtual machines that run Windows Server 2016. The virtual machines are configured as web servers.
You have an Azure load balancer named LB1 that provides load balancing services for the virtual machines.
You need to ensure that visitors are serviced by the same web server for each request.
What should you configure?
- Floating IP (direct server return) to Disabled
- Session persistence to None
- Floating IP (direct server return) to Enabled
- Session persistence to Client IP
Explanation:
With Sticky Sessions when a client starts a session on one of your web servers, session stays on that specific server. To configure An Azure Load-Balancer For Sticky Sessions set Session persistence to Client IP or to Client IP and protocol.On the following image you can see sticky session configuration:
Note:
– Client IP and protocol specifies that successive requests from the same client IP address and protocol combination will be handled by the same virtual machine.
– Client IP specifies that successive requests from the same client IP address will be handled by the same virtual machine. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains the following resources:
– A virtual network that has a subnet named Subnet1
– Two network security groups (NSGs) named NSG-VM1 and NSG-Subnet1
– A virtual machine named VM1 that has the required Windows Server configurations to allow Remote Desktop connectionsNSG-Subnet1 has the default inbound security rules only.
NSG-VM1 has the default inbound security rules and the following custom inbound security rule:
– Priority: 100
– Source: Any
– Source port range: *
– Destination: *
– Destination port range: 3389
– Protocol: UDP
– Action: AllowVM1 has a public IP address and is connected to Subnet1. NSG-VM1 is associated to the network interface of VM1. NSG-Subnet1 is associated to Subnet1.
You need to be able to establish Remote Desktop connections from the internet to VM1.
Solution: You add an inbound security rule to NSG-Subnet1 that allows connections from the Any source to the *destination for port range 3389 and uses the TCP protocol. You remove NSG-VM1 from the network interface of VM1.
Does this meet the goal?
- Yes
- No
Explanation:
The default port for RDP is TCP port 3389. A rule to permit RDP traffic must be created automatically when you create your VM.Note on NSG-Subnet1: Azure routes network traffic between all subnets in a virtual network, by default.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains the following resources:
– A virtual network that has a subnet named Subnet1
– Two network security groups (NSGs) named NSG-VM1 and NSG-Subnet1
– A virtual machine named VM1 that has the required Windows Server configurations to allow Remote Desktop connectionsNSG-Subnet1 has the default inbound security rules only.
NSG-VM1 has the default inbound security rules and the following custom inbound security rule:
– Priority: 100
– Source: Any
– Source port range: *
– Destination: *
– Destination port range: 3389
– Protocol: UDP
– Action: AllowVM1 has a public IP address and is connected to Subnet1. NSG-VM1 is associated to the network interface of VM1. NSG-Subnet1 is associated to Subnet1.
You need to be able to establish Remote Desktop connections from the internet to VM1.
Solution: You add an inbound security rule to NSG-Subnet1 that allows connections from the internet source to the Virtual Network destination for port range 3389 and uses the UDP protocol.
Does this meet the goal?
- Yes
- No
Explanation:
The default port for RDP is TCP port 3389. A rule to permit RDP traffic must be created automatically when you create your VM.Note on NSG-Subnet1: Azure routes network traffic between all subnets in a virtual network, by default.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains the following resources:
– A virtual network that has a subnet named Subnet1
– Two network security groups (NSGs) named NSG-VM1 and NSG-Subnet1
– A virtual machine named VM1 that has the required Windows Server configurations to allow Remote Desktop connectionsNSG-Subnet1 has the default inbound security rules only.
NSG-VM1 has the default inbound security rules and the following custom inbound security rule:
– Priority: 100
– Source: Any
– Source port range: *
– Destination: *
– Destination port range: 3389
– Protocol: UDP
– Action: AllowVM1 has a public IP address and is connected to Subnet1. NSG-VM1 is associated to the network interface of VM1. NSG-Subnet1 is associated to Subnet1.
You need to be able to establish Remote Desktop connections from the internet to VM1.
Solution: You add an inbound security rule to NSG-Subnet1 and NSG-VM1 that allows connections from the internet source to the Virtual Network destination for port range 3389 and uses the TCP protocol.
Does this meet the goal?
- Yes
- No
Explanation:
The default port for RDP is TCP port 3389. A rule to permit RDP traffic must be created automatically when you create your VM.Note on NSG-Subnet1: Azure routes network traffic between all subnets in a virtual network, by default.
-
HOTSPOT
You have a virtual network named VNet1 that has the configuration shown in the following exhibit.
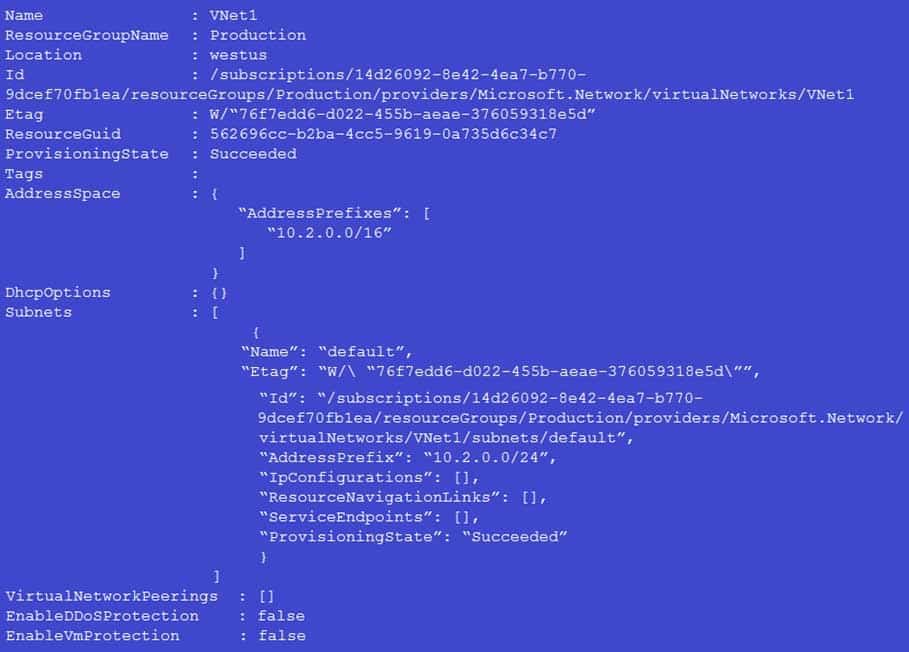
AZ-104 Part 10 Q05 188 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
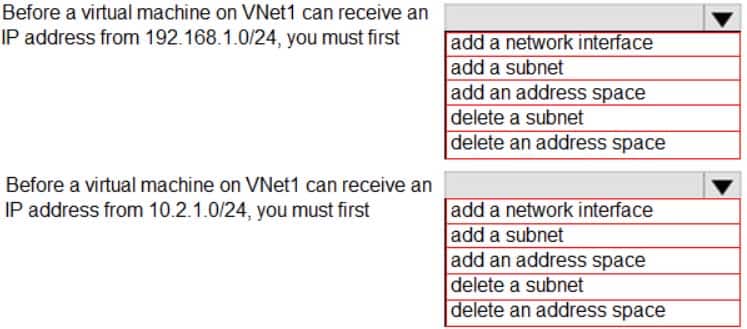
AZ-104 Part 10 Q05 189 Question 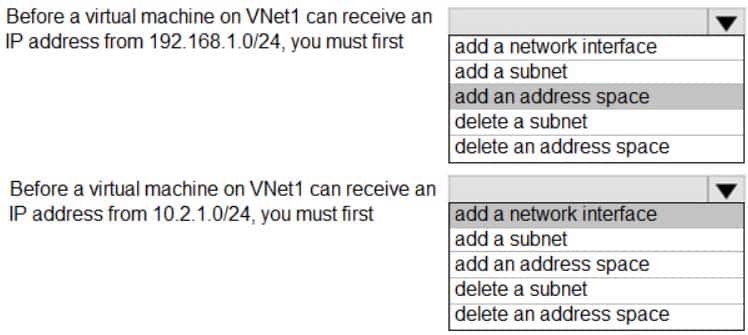
AZ-104 Part 10 Q05 189 Answer Explanation:
Box 1: add an address space
Your IaaS virtual machines (VMs) and PaaS role instances in a virtual network automatically receive a private IP address from a range that you specify, based on the address space of the subnet they are connected to. We need to add the 192.168.1.0/24 address space.Box 2: add a network interface
The 10.2.1.0/24 network exists. We need to add a network interface. -
You have an Azure subscription that contains a virtual network named VNET1. VNET1 contains the subnets shown in the following table.

AZ-104 Part 10 Q06 190 Each virtual machine uses a static IP address.
You need to create network security groups (NSGs) to meet following requirements:
– Allow web requests from the internet to VM3, VM4, VM5, and VM6.
– Allow all connections between VM1 and VM2.
– Allow Remote Desktop connections to VM1.
– Prevent all other network traffic to VNET1.What is the minimum number of NSGs you should create?
- 1
- 3
- 4
- 12
Explanation:
Each network security group also contains default security rules.Note: A network security group (NSG) contains a list of security rules that allow or deny network traffic to resources connected to Azure Virtual Networks (VNet). NSGs can be associated to subnets, individual VMs (classic), or individual network interfaces (NIC) attached to VMs (Resource Manager).
-
You have an Azure subscription that contains the resources shown in the following table.
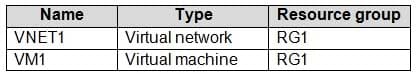
AZ-104 Part 10 Q07 191 The Not allowed resource types Azure policy is assigned to RG1 and uses the following parameters:
Microsoft.Network/virtualNetworks Microsoft.Compute/virtualMachines
In RG1, you need to create a new virtual machine named VM2, and then connect VM2 to VNET1.
What should you do first?
- Remove Microsoft.Compute/virtualMachines from the policy.
- Create an Azure Resource Manager template
- Add a subnet to VNET1.
- Remove Microsoft.Network/virtualNetworks from the policy.
Explanation:
The Not allowed resource types Azure policy prohibits the deployment of specified resource types. You specify an array of the resource types to block.Virtual Networks and Virtual Machines are prohibited.
-
Your company has an Azure subscription named Subscription1.
The company also has two on-premises servers named Server1 and Server2 that run Windows Server 2016. Server1 is configured as a DNS server that has a primary DNS zone named adatum.com. Adatum.com contains 1,000 DNS records.
You manage Server1 and Subscription1 from Server2. Server2 has the following tools installed:
– The DNS Manager console
– Azure PowerShell
– Azure CLI 2.0You need to move the adatum.com zone to an Azure DNS zone in Subscription1. The solution must minimize administrative effort.
What should you use?
- Azure CLI
- Azure PowerShell
- the Azure portal
- the DNS Manager console
Explanation:
Step 1: Installing the DNS migration script
Open an elevated PowerShell window (Administrative mode) and run following commandinstall-script Private Dns Migration Script
Step 2: Running the script
Execute following command to run the scriptPrivateDnsMigrationScript.ps1
-
You have a public load balancer that balances ports 80 and 443 across three virtual machines named VM1, VM2, and VM3.
You need to direct all the Remote Desktop Protocol (RDP) connections to VM3 only.
What should you configure?
- an inbound NAT rule
- a new public load balancer for VM3
- a frontend IP configuration
- a load balancing rule
-
HOTSPOT
You have an Azure subscription named Subscription1 that contains the virtual networks in the following table.
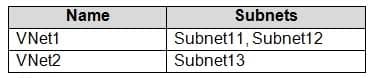
AZ-104 Part 10 Q10 192 Subscription1 contains the virtual machines in the following table.
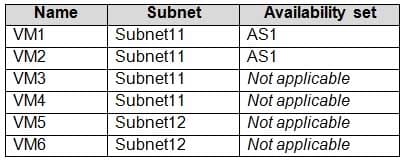
AZ-104 Part 10 Q10 193 In Subscription1, you create a load balancer that has the following configurations:
– Name: LB1
– SKU: Basic
– Type: Internal
– Subnet: Subnet12
– Virtual network: VNET1For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-104 Part 10 Q10 194 Question 
AZ-104 Part 10 Q10 194 Answer -
HOTSPOT
You have an Azure virtual machine that runs Windows Server 2019 and has the following configurations:
– Name: VM1
– Location: West US
– Connected to: VNET1
– Private IP address: 10.1.0.4
– Public IP addresses: 52.186.85.63
– DNS suffix in Windows Server: Adatum.comYou create the Azure DNS zones shown in the following table.
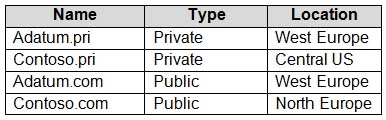
AZ-104 Part 10 Q11 195 You need to identify which DNS zones you can link to VNET1 and the DNS zones to which VM1 can automatically register.
Which zones should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
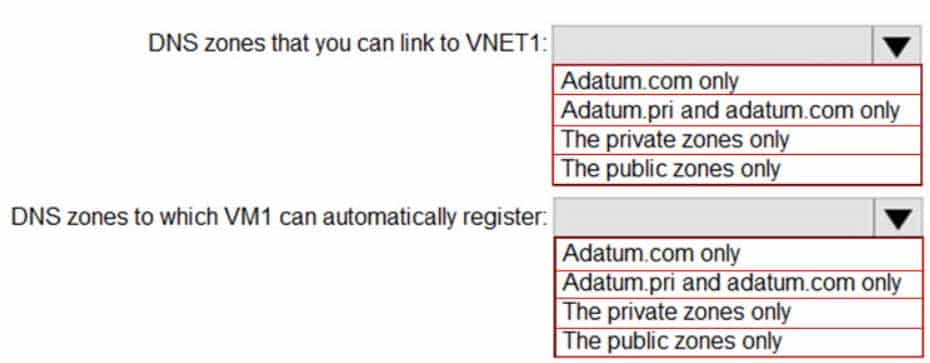
AZ-104 Part 10 Q11 196 Question 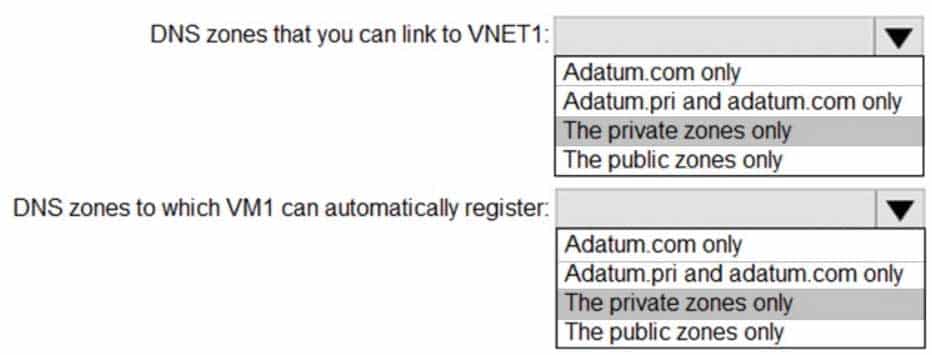
AZ-104 Part 10 Q11 196 Answer -
DRAG DROP
You have an on-premises network that you plan to connect to Azure by using a site-so-site VPN.
In Azure, you have an Azure virtual network named VNet1 that uses an address space of 10.0.0.0/16 VNet1 contains a subnet named Subnet1 that uses an address space of 10.0.0.0/24.
You need to create a site-to-site VPN to Azure.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
NOTE: More than one order of answer choice is correct. You will receive credit for any of the correct orders you select.
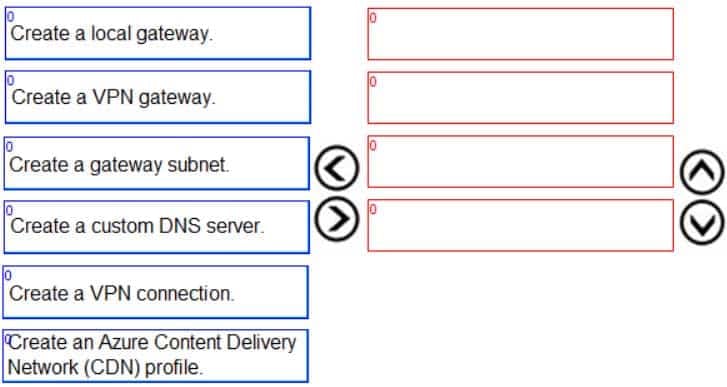
AZ-104 Part 10 Q12 197 Question 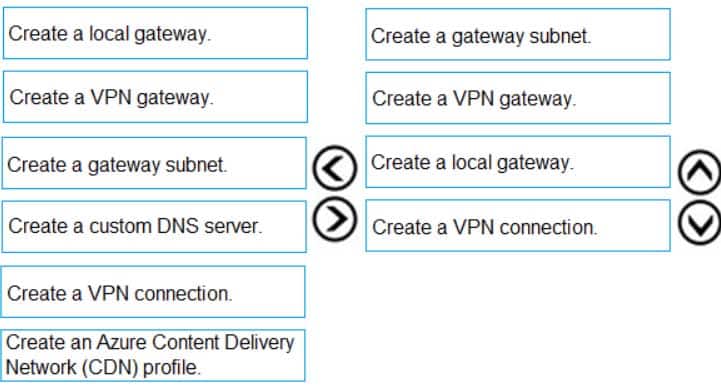
AZ-104 Part 10 Q12 197 Answer -
You have an Azure subscription that contains the resources in the following table.
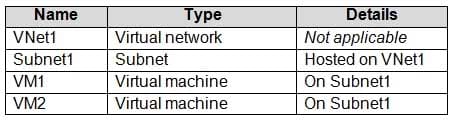
AZ-104 Part 10 Q13 198 VM1 and VM2 are deployed from the same template and host line-of-business applications.
You configure the network security group (NSG) shown in the exhibit. (Click the Exhibit tab.)
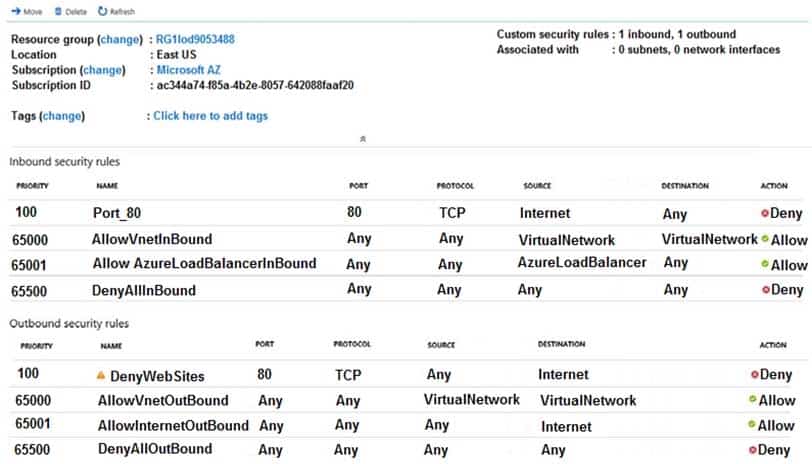
AZ-104 Part 10 Q13 199 You need to prevent users of VM1 and VM2 from accessing websites on the Internet over TCP port 80.
What should you do?
- Disassociate the NSG from a network interface
- Change the Port_80 inbound security rule.
- Associate the NSG to Subnet1.
- Change the DenyWebSites outbound security rule.
Explanation:
You can associate or dissociate a network security group from a network interface or subnet.
The NSG has the appropriate rule to block users from accessing the Internet. We just need to associate it with Subnet1. -
You have two subscriptions named Subscription1 and Subscription2. Each subscription is associated to a different Azure AD tenant.
Subscription1 contains a virtual network named VNet1. VNet1 contains an Azure virtual machine named VM1 and has an IP address space of 10.0.0.0/16.
Subscription2 contains a virtual network named VNet2. VNet2 contains an Azure virtual machine named VM2 and has an IP address space of 10.10.0.0/24.
You need to connect VNet1 to VNet2.
What should you do first?
- Move VM1 to Subscription2.
- Move VNet1 to Subscription2.
- Modify the IP address space of VNet2.
- Provision virtual network gateways.
Explanation:
The virtual networks can be in the same or different regions, and from the same or different subscriptions. When connecting VNets from different subscriptions, the subscriptions do not need to be associated with the same Active Directory tenant.Configuring a VNet-to-VNet connection is a good way to easily connect VNets. Connecting a virtual network to another virtual network using the VNet-to-VNet connection type (VNet2VNet) is similar to creating a Site-to-Site IPsec connection to an on-premises location. Both connectivity types use a VPN gateway to provide a secure tunnel using IPsec/IKE, and both function the same way when communicating.
The local network gateway for each VNet treats the other VNet as a local site. This lets you specify additional address space for the local network gateway in order to route traffic.
-
You plan to create an Azure virtual machine named VM1 that will be configured as shown in the following exhibit.
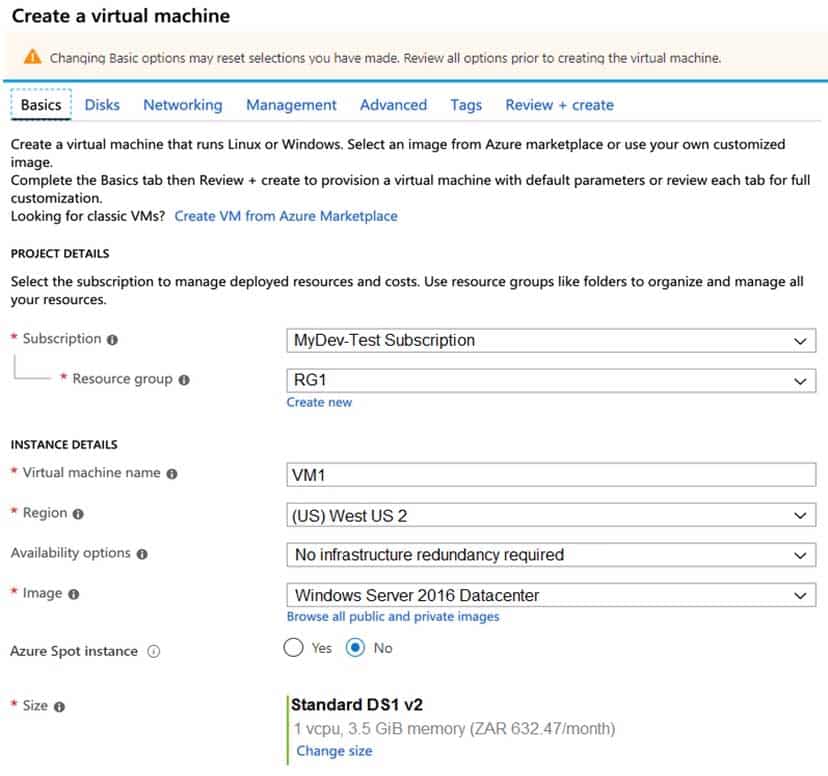
AZ-104 Part 10 Q15 200 The planned disk configurations for VM1 are shown in the following exhibit.
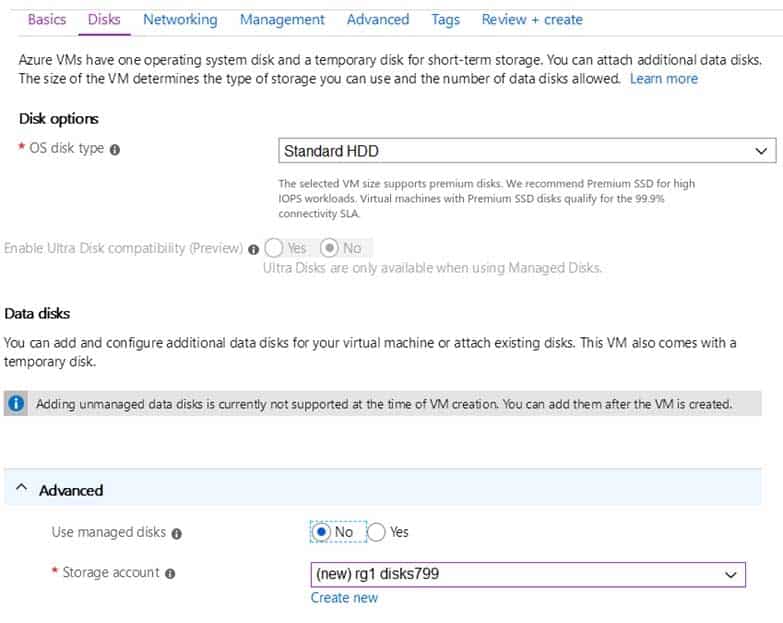
AZ-104 Part 10 Q15 201 You need to ensure that VM1 can be created in an Availability Zone.
Which two settings should you modify? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Use managed disks
- OS disk type
- Availability options
- Size
- Image
Explanation:
A: Your VMs should use managed disks if you want to move them to an Availability Zone by using Site Recovery.C: When you create a VM for an Availability Zone, Under Settings > High availability, select one of the numbered zones from the Availability zone dropdown.
-
HOTSPOT
You have an Azure subscription that contains the resources shown in the following table.
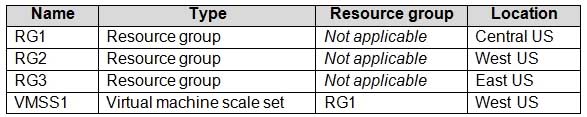
AZ-104 Part 10 Q16 203 VMSS1 is set to VM (virtual machines) orchestration mode.
You need to deploy a new Azure virtual machine named VM1, and then add VM1 to VMSS1.
Which resource group and location should you use to deploy VM1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-104 Part 10 Q16 204 Question 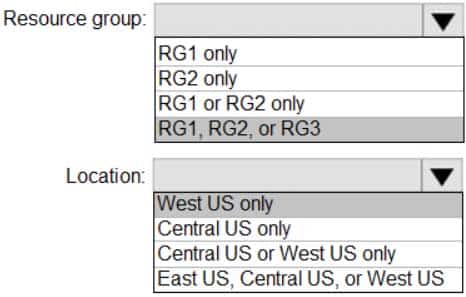
AZ-104 Part 10 Q16 204 Answer Explanation:
Box 1: RG1, RG2, or RG3
The resource group stores metadata about the resources. When you specify a location for the resource group, you’re specifying where that metadata is stored.
Box 2: West US only
Note: Virtual machine scale sets will support 2 distinct orchestration modes:
ScaleSetVM – Virtual machine instances added to the scale set are based on the scale set configuration model. The virtual machine instance lifecycle – creation, update, deletion – is managed by the scale set.
VM (virtual machines) – Virtual machines created outside of the scale set can be explicitly added to the scaleset. -
HOTSPOT
You have an Azure subscription that contains three virtual networks named VNET1, VNET2, and VNET3.
Peering for VNET1 is configured as shown in the following exhibit.
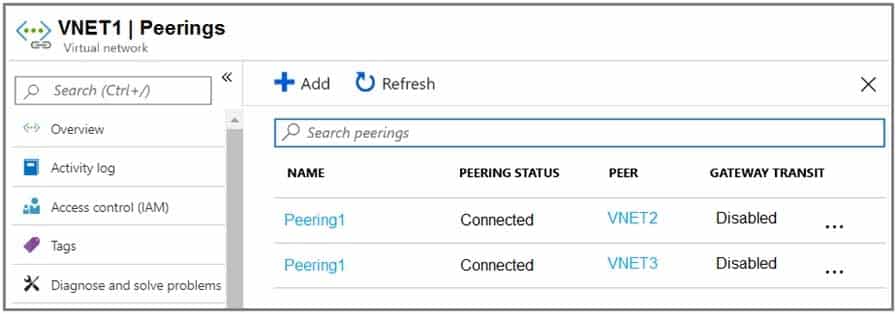
AZ-104 Part 10 Q17 205 Peering for VNET2 is configured as shown in the following exhibit.
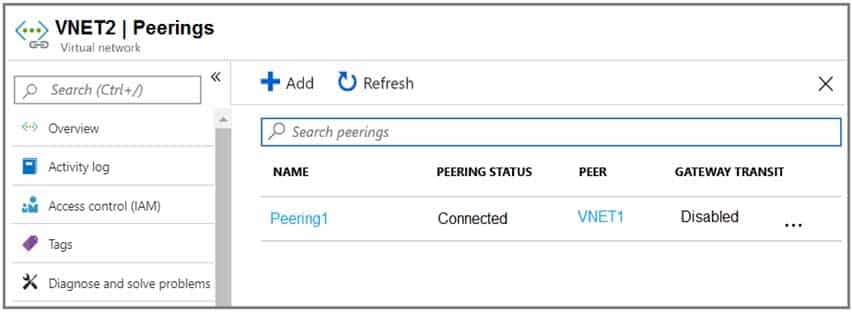
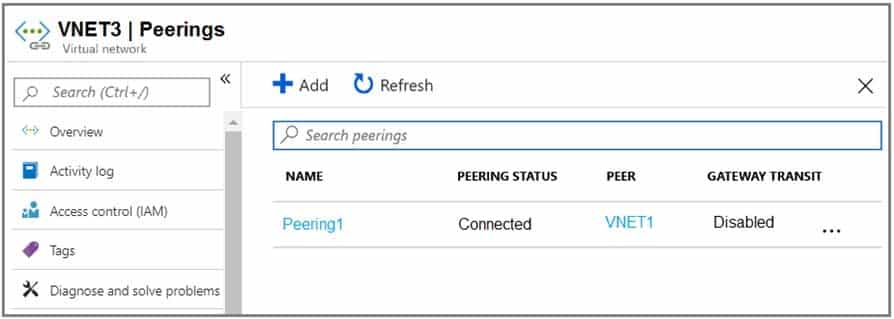
AZ-104 Part 10 Q17 206 Peering for VNET3 is configured as shown in the following exhibit.
AZ-104 Part 10 Q17 207 How can packets be routed between the virtual networks? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
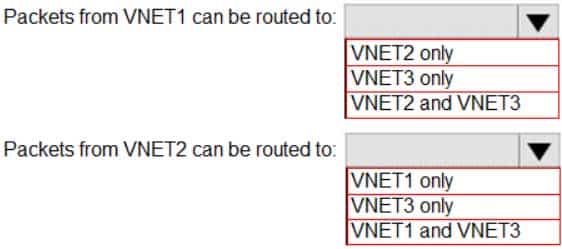
AZ-104 Part 10 Q17 208 Question 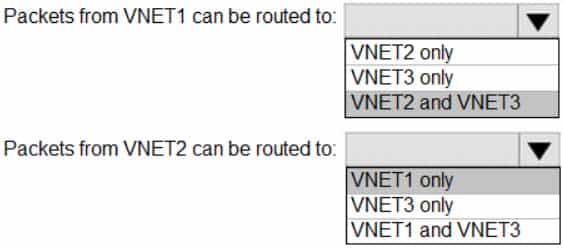
AZ-104 Part 10 Q17 208 Answer Explanation:
Box 1. VNET2 and VNET3
Box 2: VNET1
Gateway transit is disabled. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that has a point-to-site VPN connection to an Azure virtual network named VNet1. The point-to-site connection uses a self-signed certificate.
From Azure, you download and install the VPN client configuration package on a computer named Computer2.
You need to ensure that you can establish a point-to-site VPN connection to VNet1 from Computer2.
Solution: You modify the Azure Active Directory (Azure AD) authentication policies.
Does this meet the goal?
- Yes
- No
Explanation:
Instead export the client certificate from Computer1 and install the certificate on Computer2.Note:
Each client computer that connects to a VNet using Point-to-Site must have a client certificate installed. You generate a client certificate from the self-signed root certificate, and then export and install the client certificate. If the client certificate is not installed, authentication fails. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that has a point-to-site VPN connection to an Azure virtual network named VNet1. The point-to-site connection uses a self-signed certificate.
From Azure, you download and install the VPN client configuration package on a computer named Computer2.
You need to ensure that you can establish a point-to-site VPN connection to VNet1 from Computer2.
Solution: You join Computer2 to Azure Active Directory (Azure AD)
Does this meet the goal?
- Yes
- No
Explanation:A client computer that connects to a VNet using Point-to-Site must have a client certificate installed
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains 10 virtual networks. The virtual networks are hosted in separate resource groups.
Another administrator plans to create several network security groups (NSGs) in the subscription.
You need to ensure that when an NSG is created, it automatically blocks TCP port 8080 between the virtual networks.
Solution: You create a resource lock, and then you assign the lock to the subscription.
Does this meet the goal?
- Yes
- No