AZ-104 : Microsoft Azure Administrator : Part 11
AZ-104 : Microsoft Azure Administrator : Part 11
-
You have an Azure subscription named Subscription1. Subscription1 contains a virtual machine named VM1.
You have a computer named Computer1 that runs Windows 10. Computer1 is connected to the Internet.
You add a network interface named vm1173 to VM1 as shown in the exhibit. (Click the Exhibit tab.)
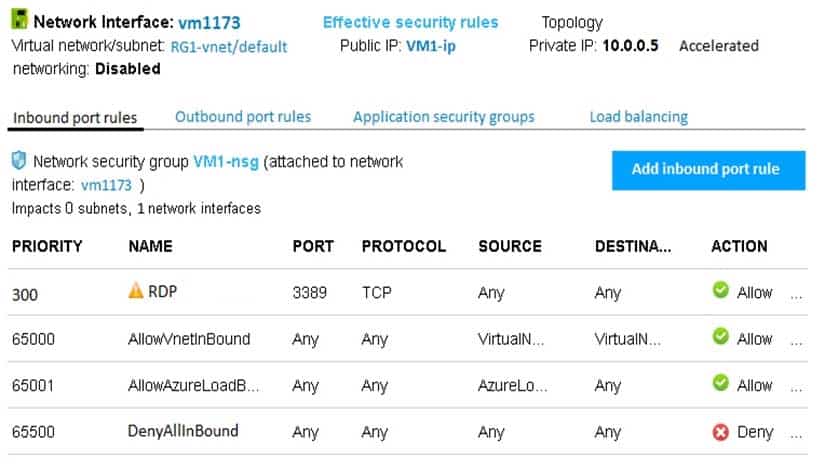
AZ-104 Part 11 Q01 209 From Computer1, you attempt to connect to VM1 by using Remote Desktop, but the connection fails.
You need to establish a Remote Desktop connection to VM1.
What should you do first?
- Change the priority of the RDP rule
- Attach a network interface
- Delete the DenyAllInBound rule
- Start VM1
Explanation:Incorrect Answers:
A: Rules are processed in priority order, with lower numbers processed before higher numbers, because lower numbers have higher priority. Once traffic matches a rule, processing stops. RDP already has the lowest number and thus the highest priority.
B: The network interface has already been added to VM.
C: The Outbound rules are fine. -
You have the Azure virtual machines shown in the following table.
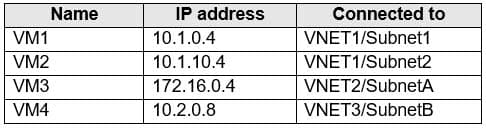
AZ-104 Part 11 Q02 210 A DNS service is installed on VM1.
You configure the DNS servers settings for each virtual network as shown in the following exhibit.
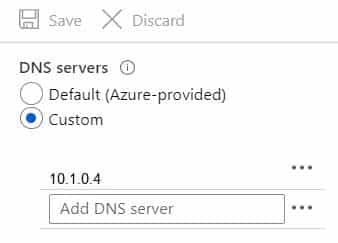
AZ-104 Part 11 Q02 211 You need to ensure that all the virtual machines can resolve DNS names by using the DNS service on VM1.
What should you do?
- Configure a conditional forwarder on VM1
- Add service endpoints on VNET1
- Add service endpoints on VNET2 and VNET3
- Configure peering between VNET1, VNET2, and VNET3
Explanation:
Virtual network peering enables you to seamlessly connect networks in Azure Virtual Network. The virtual networks appear as one for connectivity purposes. The traffic between virtual machines uses the Microsoft backbone infrastructure.Incorrect Answers:
B, C: Virtual Network (VNet) service endpoint provides secure and direct connectivity to Azure services over an optimized route over the Azure backbone network. Endpoints allow you to secure your critical Azure service resources to only your virtual networks. Service Endpoints enables private IP addresses in the VNet to reach the endpoint of an Azure service without needing a public IP address on the VNet. -
HOTSPOT
You have an Azure subscription that contains the Azure virtual machines shown in the following table.
AZ-104 Part 11 Q03 212 You add inbound security rules to a network security group (NSG) named NSG1 as shown in the following table.
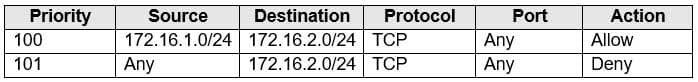
AZ-104 Part 11 Q03 213 You run Azure Network Watcher as shown in the following exhibit.
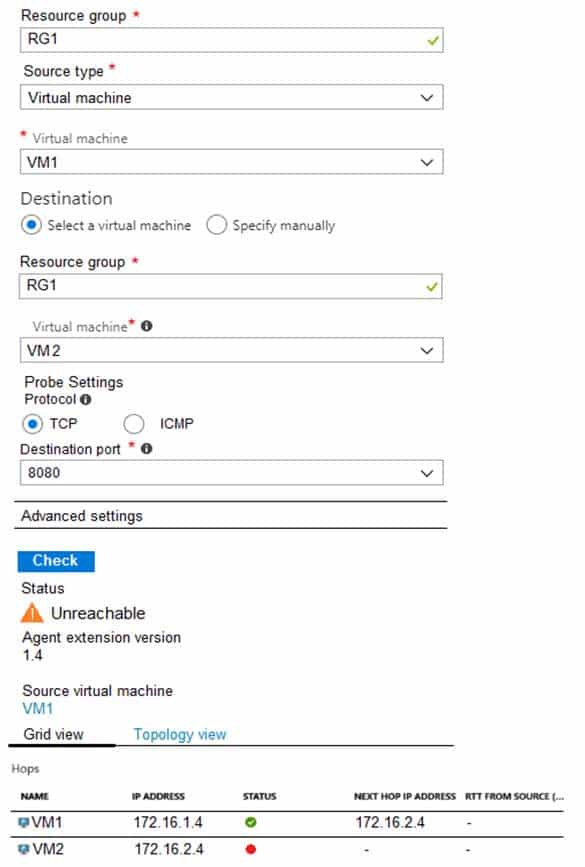
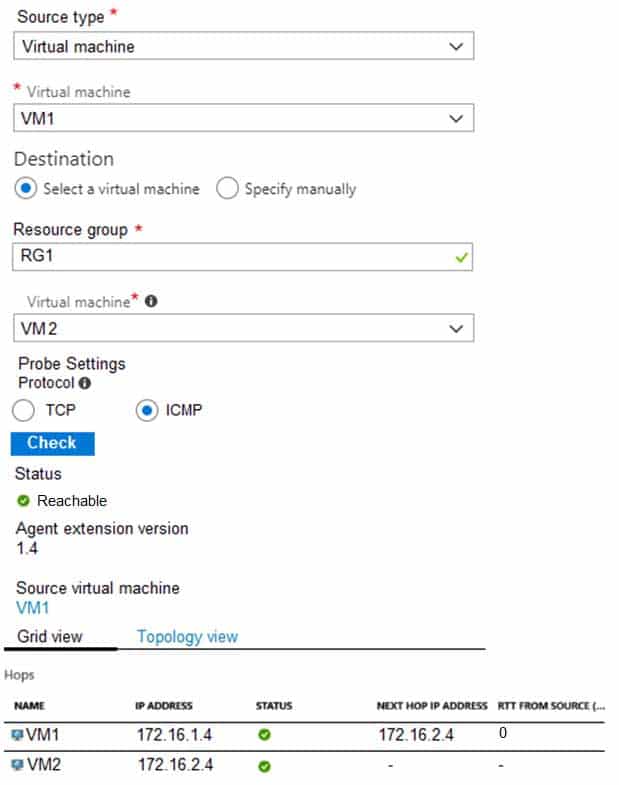
AZ-104 Part 11 Q03 214 You run Network Watcher again as shown in the following exhibit.
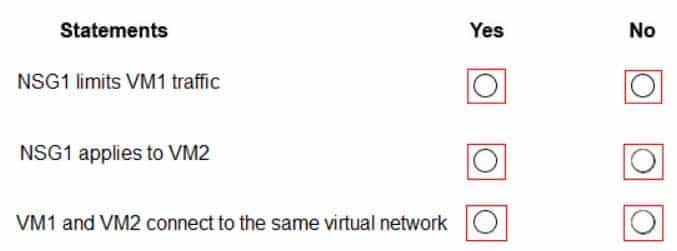
AZ-104 Part 11 Q03 215 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
AZ-104 Part 11 Q03 216 Question 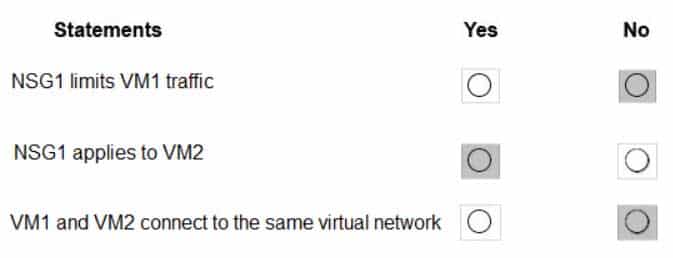
AZ-104 Part 11 Q03 216 Answer Explanation:
Box 1: No
It limits traffic to VM2, but not VM1 traffic.Box 2: Yes
Yes, the destination is VM2.Box 3: No
-
You have the Azure virtual network named VNet1 that contains a subnet named Subnet1. Subnet1 contains three Azure virtual machines. Each virtual machine has a public IP address.
The virtual machines host several applications that are accessible over port 443 to users on the Internet.
Your on-premises network has a site-to-site VPN connection to VNet1.
You discover that the virtual machines can be accessed by using the Remote Desktop Protocol (RDP) from the Internet and from the on-premises network.
You need to prevent RDP access to the virtual machines from the Internet, unless the RDP connection is established from the on-premises network. The solution must ensure that all the applications can still be accessed by the Internet users.
What should you do?
- Modify the address space of the local network gateway
- Create a deny rule in a network security group (NSG) that is linked to Subnet1
- Remove the public IP addresses from the virtual machines
- Modify the address space of Subnet1
Explanation:You can use a site-to-site VPN to connect your on-premises network to an Azure virtual network. Users on your on-premises network connect by using the RDP or SSH protocol over the site-to-site VPN connection. You don’t have to allow direct RDP or SSH access over the internet.
-
You have an Azure subscription that contains the resources in the following table.
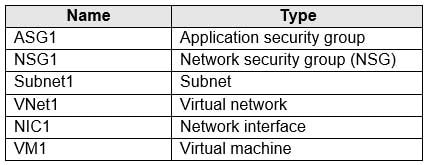
AZ-104 Part 11 Q05 217 Subnet1 is associated to VNet1. NIC1 attaches VM1 to Subnet1.
You need to apply ASG1 to VM1.
What should you do?
- Associate NIC1 to ASG1
- Modify the properties of ASG1
- Modify the properties of NSG1
Explanation:Application Security Group can be associated with NICs.
-
You have an Azure subscription named Subscription1 that contains an Azure virtual network named VNet1. VNet1 connects to your on-premises network by using Azure ExpressRoute.
You plan to prepare the environment for automatic failover in case of ExpressRoute failure.
You need to connect VNet1 to the on-premises network by using a site-to-site VPN. The solution must minimize cost.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Create a connection
- Create a local site VPN gateway
- Create a VPN gateway that uses the VpnGw1 SKU
- Create a gateway subnet
- Create a VPN gateway that uses the Basic SKU
-
HOTSPOT
You have peering configured as shown in the following exhibit.
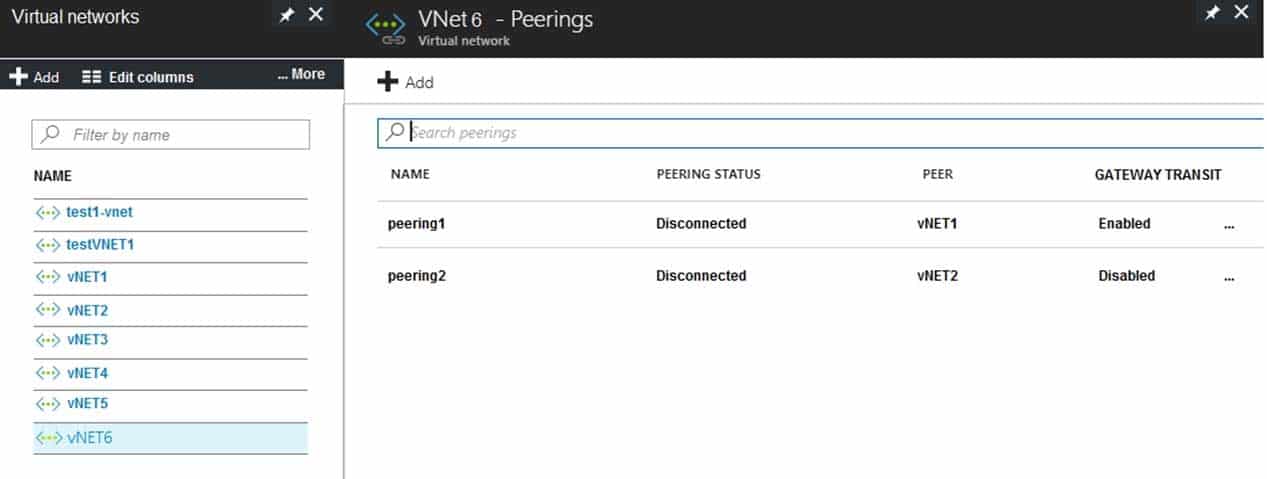
AZ-104 Part 11 Q07 218 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
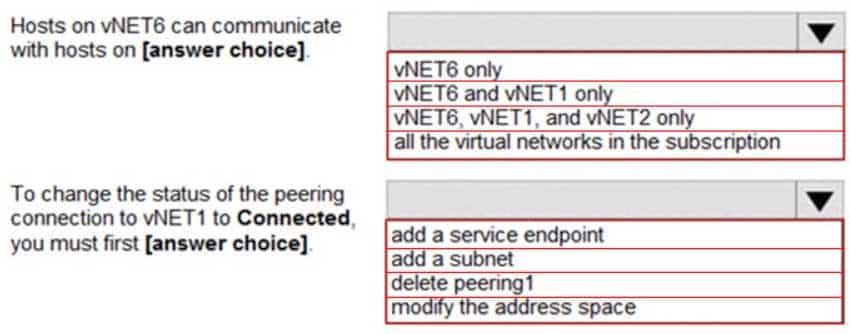
AZ-104 Part 11 Q07 219 Question 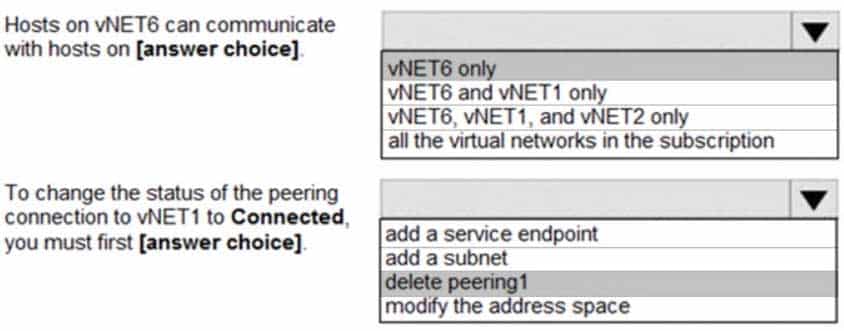
AZ-104 Part 11 Q07 219 Answer Explanation:
Box 1: vNET6 only
Peering status to both VNet1 and Vnet2 are disconnected.Box 2: delete peering1
Peering to Vnet1 is Enabled but disconnected. We need to update or re-create the remote peering to get it back to Initiated state. -
HOTSPOT
You have an Azure subscription that contains the resources in the following table.
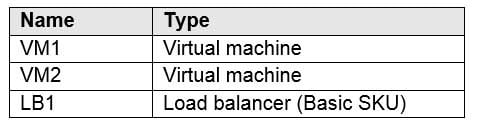
AZ-104 Part 11 Q09 220 You install the Web Server server role (IIS) on VM1 and VM2, and then add VM1 and VM2 to LB1.
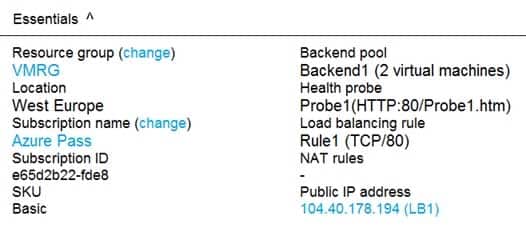
LB1 is configured as shown in the LB1 exhibit. (Click the LB1 tab.)
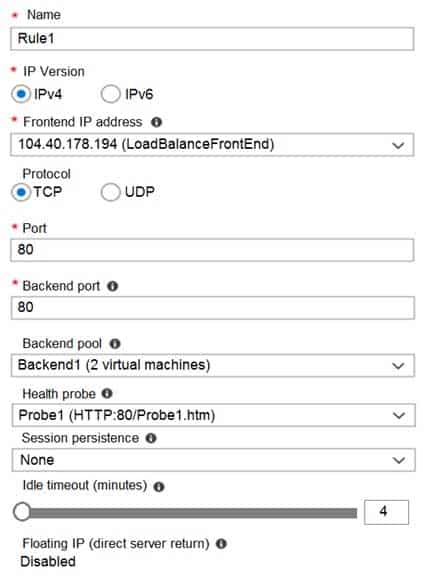
AZ-104 Part 11 Q09 221 Rule1 is configured as shown in the Rule1 exhibit. (Click the Rule1 tab.)
AZ-104 Part 11 Q09 222 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
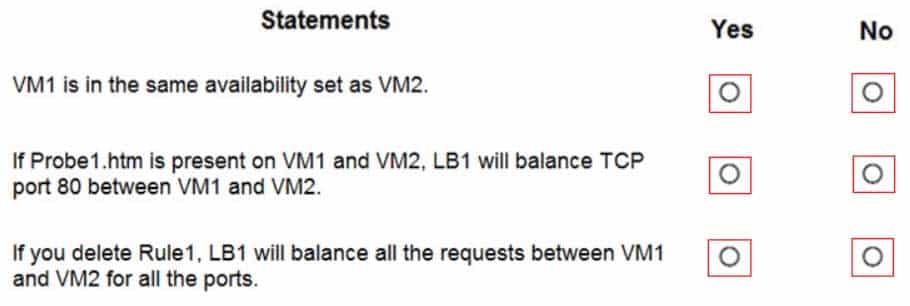
AZ-104 Part 11 Q09 223 Question 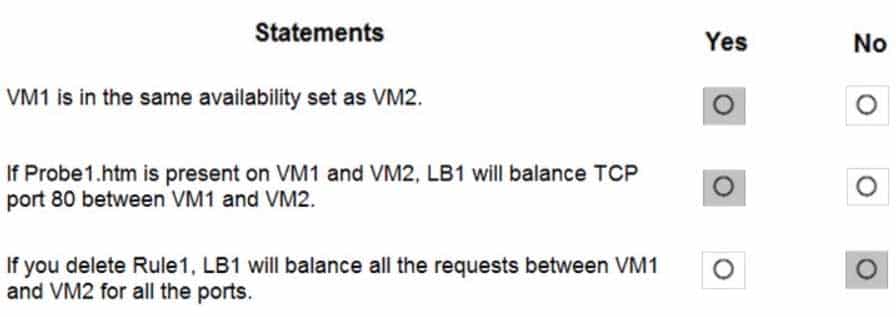
AZ-104 Part 11 Q09 223 Answer Explanation:
Box 1: Yes
A Basic Load Balancer supports virtual machines in a single availability set or virtual machine scale set.Box 2: Yes
When using load-balancing rules with Azure Load Balancer, you need to specify health probes to allow Load Balancer to detect the backend endpoint status. The configuration of the health probe and probe responses determine which backend pool instances will receive new flows. You can use health probes to detect the failure of an application on a backend endpoint. You can also generate a custom response to a health probe and use the health probe for flow control to manage load or planned downtime. When a health probe fails, Load Balancer will stop sending new flows to the respective unhealthy instance. Outbound connectivity is not impacted, only inbound connectivity is impacted.Box 3: No
-
HOTSPOT
You have an Azure virtual machine named VM1 that connects to a virtual network named VNet1. VM1 has the following configurations:
– Subnet: 10.0.0.0/24
– Availability set: AVSet
– Network security group (NSG): None
– Private IP address: 10.0.0.4 (dynamic)
– Public IP address: 40.90.219.6 (dynamic)You deploy a standard, Internet-facing load balancer named slb1.
You need to configure slb1 to allow connectivity to VM1.
Which changes should you apply to VM1 as you configure slb1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
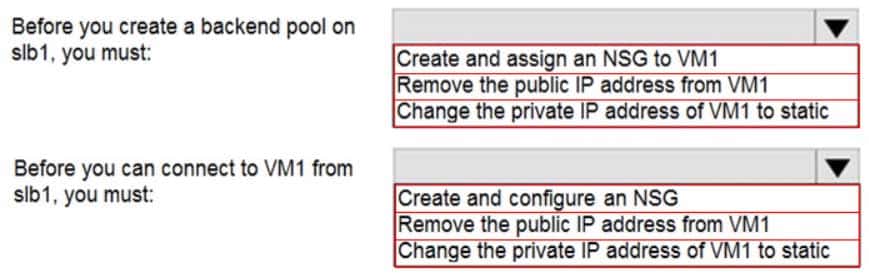
AZ-104 Part 11 Q09 224 Question 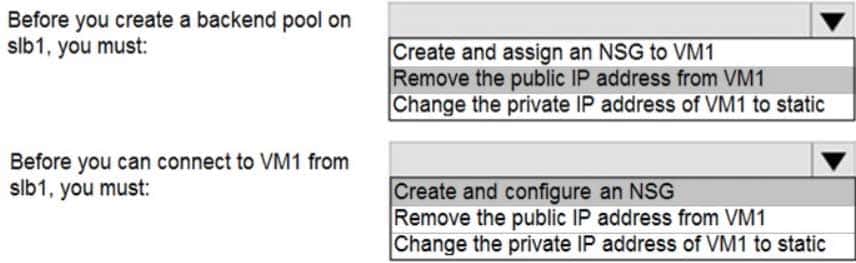
AZ-104 Part 11 Q09 224 Answer Explanation:
Change the private IP address of VM1 to static
Box 1: Remove the public IP address from VM1
Note: A public load balancer can provide outbound connections for virtual machines (VMs) inside your virtual network. These connections are accomplished by translating their private IP addresses to public IP addresses. Public Load Balancers are used to load balance internet traffic to your VMs.
Box 2: Create and configure an NSG
NSGs are used to explicitly permit allowed traffic. If you do not have an NSG on a subnet or NIC of your virtual machine resource, traffic is not allowed to reach this resource. -
You have an Azure subscription that contains the resources shown in the following table.
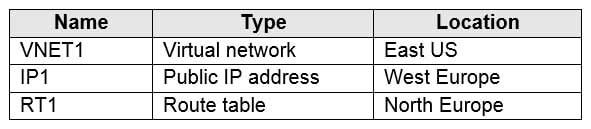
AZ-104 Part 11 Q10 225 You need to create a network interface named NIC1.
In which location can you create NIC1?
- East US and North Europe only
- East US only
- East US, West Europe, and North Europe
- East US and West Europe only
Explanation:Before creating a network interface, you must have an existing virtual network in the same location and subscription you create a network interface in.
-
You have Azure virtual machines that run Windows Server 2019 and are configured as shown in the following table.
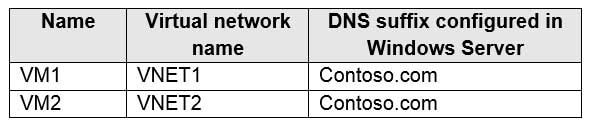
AZ-104 Part 11 Q11 226 You create a public Azure DNS zone named adatum.com and a private Azure DNS zone named contoso.com.
For controso.com, you create a virtual network link named link1 as shown in the exhibit. (Click the Exhibit tab.)
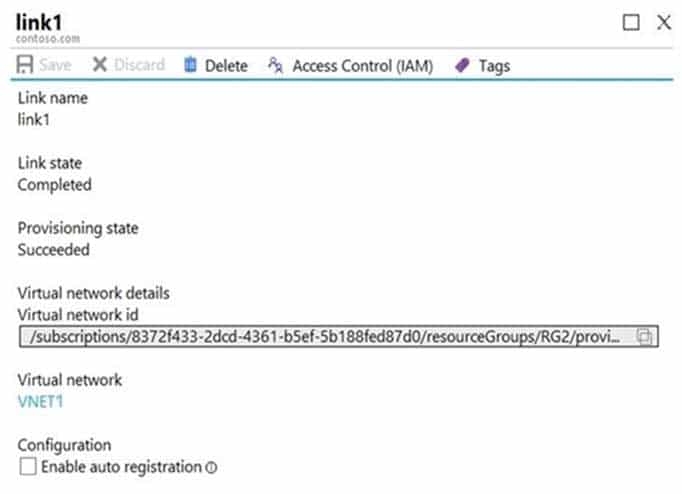
AZ-104 Part 11 Q11 227 You discover that VM1 can resolve names in contoso.com but cannot resolve names in adatum.com. VM1 can resolve other hosts on the Internet.
You need to ensure that VM1 can resolve host names in adatum.com.
What should you do?
- Update the DNS suffix on VM1 to be adatum.com
- Configure the name servers for adatum.com at the domain registrar
- Create an SRV record in the contoso.com zone
- Modify the Access control (IAM) settings for link1
Explanation:If you use Azure Provided DNS then appropriate DNS suffix will be automatically applied to your virtual machines. For all other options you must either use Fully Qualified Domain Names (FQDN) or manually apply appropriate DNS suffix to your virtual machines.
-
HOTSPOT
You plan to use Azure Network Watcher to perform the following tasks:
– Task1: Identify a security rule that prevents a network packet from reaching an Azure virtual machine.
– Task2: Validate outbound connectivity from an Azure virtual machine to an external host.Which feature should you use for each task? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
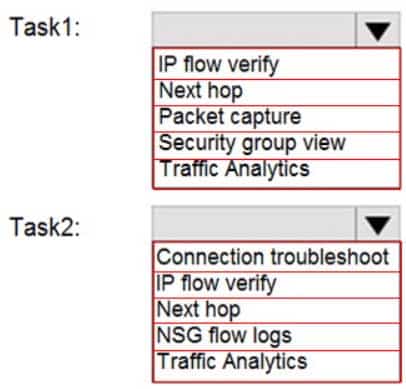
AZ-104 Part 11 Q12 228 Question 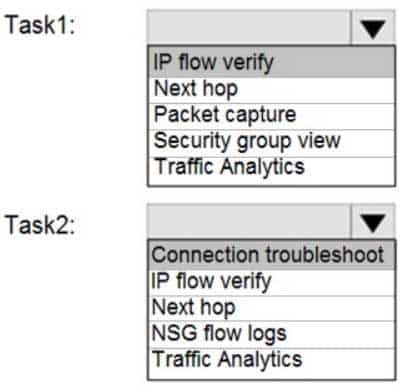
AZ-104 Part 11 Q12 228 Answer Explanation:
Box 1: IP flow verify
At some point, a VM may become unable to communicate with other resources, because of a security rule. The IP flow verify capability enables you to specify a source and destination IPv4 address, port, protocol (TCP or UDP), and traffic direction (inbound or outbound). IP flow verify then tests the communication and informs you if the connection succeeds or fails. If the connection fails, IP flow verify tells you which.Box 2: Connection troubleshoot
Diagnose outbound connections from a VM: The connection troubleshoot capability enables you to test a connection between a VM and another VM, an FQDN, a URI, or an IPv4 address. The test returns similar information returned when using the connection monitor capability, but tests the connection at a point in time, rather than monitoring it over time, as connection monitor does. Learn more about how to troubleshoot connections using connection-troubleshoot. -
HOTSPOT
You have an Azure subscription that contains the Azure virtual machines shown in the following table.
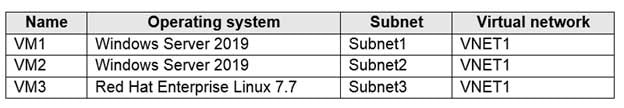
AZ-104 Part 11 Q13 229 You configure the network interfaces of the virtual machines to use the settings shown in the following table.
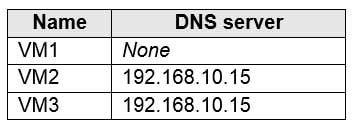
AZ-104 Part 11 Q13 230 From the settings of VNET1 you configure the DNS servers shown in the following exhibit.
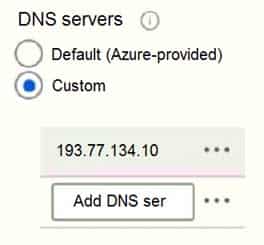
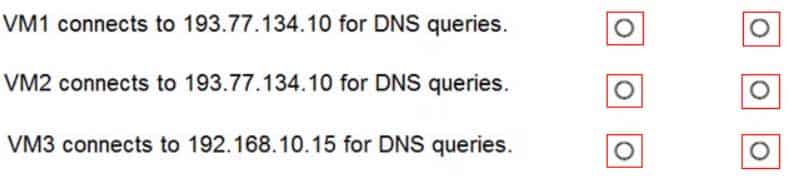
AZ-104 Part 11 Q13 231 The virtual machines can successfully connect to the DNS server that has an IP address of 192.168.10.15 and the DNS server that has an IP address of 193.77.134.10.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
AZ-104 Part 11 Q13 232 Question 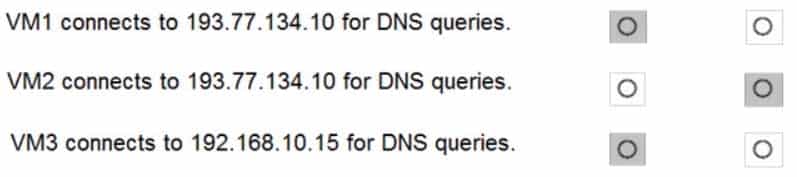
AZ-104 Part 11 Q13 232 Answer Explanation:
Box 1: Yes
You can specify DNS server IP addresses in the VNet settings. The setting is applied as the default DNS server(s) for all VMs in the VNet.Box 2: No
You can set DNS servers per VM or cloud service to override the default network settings.Box 3: Yes
You can set DNS servers per VM or cloud service to override the default network settings. -
HOTSPOT
You have an Azure subscription that contains the resource groups shown in the following table.
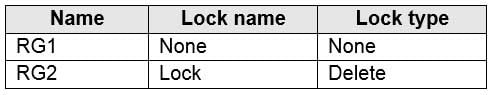
AZ-104 Part 11 Q14 233 RG1 contains the resources shown in the following table.
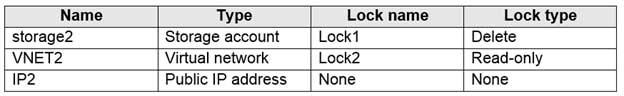
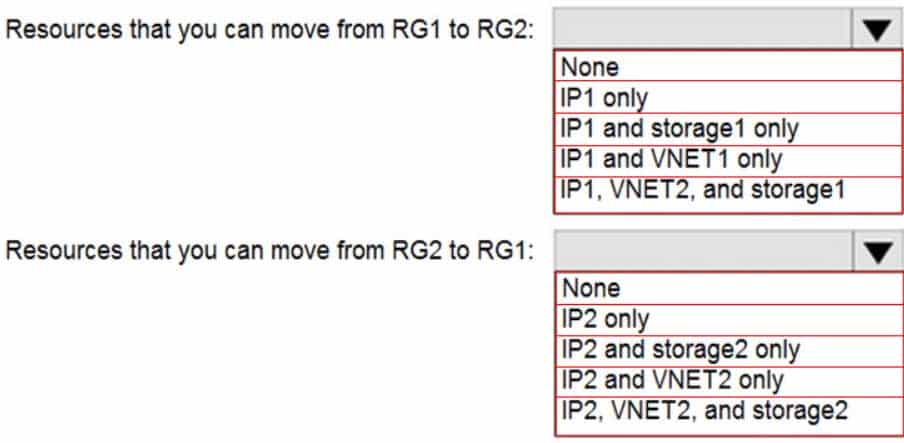
AZ-104 Part 11 Q14 234 You need to identify which resources you can move from RG1 to RG2, and which resources you can move from RG2 to RG1.
Which resources should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-104 Part 11 Q14 235 Question 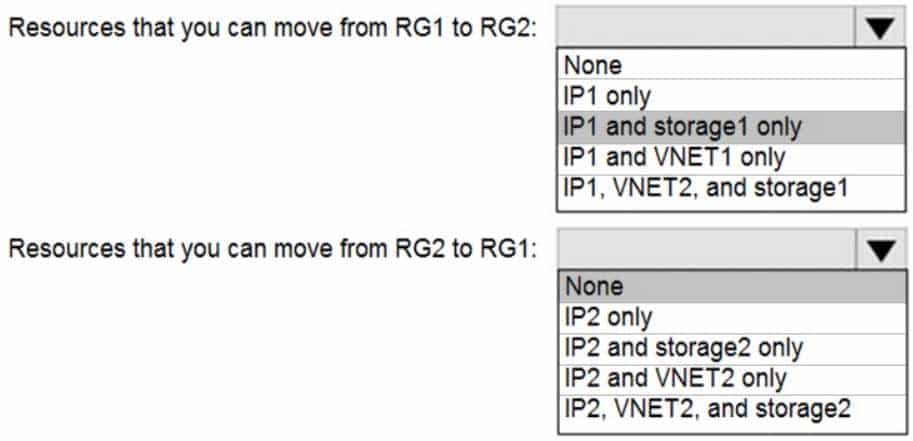
AZ-104 Part 11 Q14 235 Answer Explanation:
Box 1: IP1, Storage1
IP addresses and storage accounts can be moved.
Virtual networks cannot be moved.There is no lock on RG1.
Box 2: None
There is a delete lock on RG2.Note: When you apply a lock at a parent scope, all resources within that scope inherit the same lock. Even resources you add later inherit the lock from the parent. The most restrictive lock in the inheritance takes precedence.
CanNotDelete means authorized users can still read and modify a resource, but they can’t delete the resource.
ReadOnly means authorized users can read a resource, but they can’t delete or update the resource. Applying this lock is similar to restricting all authorized users to the permissions granted by the Reader role. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains the virtual machines shown in the following table.

AZ-104 Part 11 Q15 236 You deploy a load balancer that has the following configurations:
– Name: LB1
– Type: Internal
– SKU: Standard
– Virtual network: VNET1You need to ensure that you can add VM1 and VM2 to the backend pool of LB1.
Solution: You create a Basic SKU public IP address, associate the address to the network interface of VM1, and then start VM1.
Does this meet the goal?
- Yes
- No
Explanation:A Backend Pool configured by IP address has the following limitations:
Standard load balancer only -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains the virtual machines shown in the following table.

AZ-104 Part 11 Q16 237 You deploy a load balancer that has the following configurations:
– Name: LB1
– Type: Internal
– SKU: Standard
– Virtual network: VNET1You need to ensure that you can add VM1 and VM2 to the backend pool of LB1.
Solution: You create a Standard SKU public IP address, associate the address to the network interface of VM1, and then stop VM2.
Does this meet the goal?
- Yes
- No
Explanation:A Backend Pool configured by IP address has the following limitations:
– Standard load balancer only -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains the virtual machines shown in the following table.

AZ-104 Part 11 Q17 238 You deploy a load balancer that has the following configurations:
– Name: LB1
– Type: Internal
– SKU: Standard
– Virtual network: VNET1You need to ensure that you can add VM1 and VM2 to the backend pool of LB1.
Solution: You create two Standard public IP addresses and associate a Standard SKU public IP address to the network interface of each virtual machine.
Does this meet the goal?
- Yes
- No
Explanation:A Backend Pool configured by IP address has the following limitations:
– Standard load balancer only -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that has a point-to-site VPN connection to an Azure virtual network named VNet1. The point-to-site connection uses a self-signed certificate.
From Azure, you download and install the VPN client configuration package on a computer named Computer2.
You need to ensure that you can establish a point-to-site VPN connection to VNet1 from Computer2.
Solution: You export the client certificate from Computer1 and install the certificate on Computer2.
Does this meet the goal?
- Yes
- No
Explanation:Each client computer that connects to a VNet using Point-to-Site must have a client certificate installed. You generate a client certificate from the self-signed root certificate, and then export and install the client certificate. If the client certificate is not installed, authentication fails.
-
You have an Azure virtual machine named VM1.
The network interface for VM1 is configured as shown in the exhibit. (Click the Exhibit tab.)
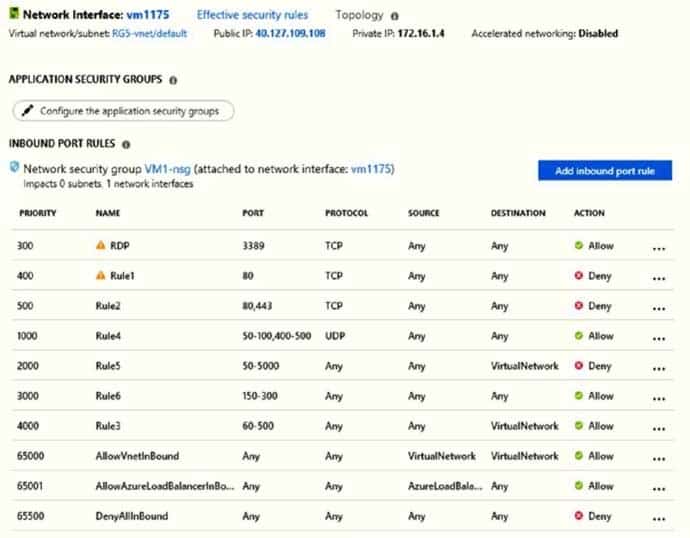
AZ-104 Part 11 Q19 239 You deploy a web server on VM1, and then create a secure website that is accessible by using the HTTPS protocol. VM1 is used as a web server only.
You need to ensure that users can connect to the website from the Internet.
What should you do?
- Modify the protocol of Rule4
- Delete Rule1
- For Rule5, change the Action to Allow and change the priority to 401
- Create a new inbound rule that allows TCP protocol 443 and configure the rule to have a priority of 501.
Explanation:
HTTPS uses port 443.
Rule2, with priority 500, denies HTTPS traffic.
Rule5, with priority changed from 2000 to 401, would allow HTTPS traffic.Note: Priority is a number between 100 and 4096. Rules are processed in priority order, with lower numbers processed before higher numbers, because lower numbers have higher priority. Once traffic matches a rule, processing stops. As a result, any rules that exist with lower priorities (higher numbers) that have the same attributes as rules with higher priorities are not processed.
Note:
There are several versions of this question in the exam. The question has two possible correct answers:
Change the priority of Rule3 to 450.
For Rule5, change the Action to Allow and change the priority to 401.Other incorrect answer options you may see on the exam include the following:
Modify the action of Rule1.
Change the priority of Rule6 to 100.
For Rule4, change the protocol from UDP to Any. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains 10 virtual networks. The virtual networks are hosted in separate resource groups.
Another administrator plans to create several network security groups (NSGs) in the subscription.
You need to ensure that when an NSG is created, it automatically blocks TCP port 8080 between the virtual networks.
Solution: From the Resource providers blade, you unregister the Microsoft.ClassicNetwork provider.
Does this meet the goal?
- Yes
- No
Explanation:
You should use a policy definition.Resource policy definition used by Azure Policy enables you to establish conventions for resources in your organization by describing when the policy is enforced and what effect to take. By defining conventions, you can control costs and more easily manage your resources.