AZ-104 : Microsoft Azure Administrator : Part 12
AZ-104 : Microsoft Azure Administrator : Part 12
-
HOTSPOT
You manage two Azure subscriptions named Subscription1 and Subscription2.
Subscription1 has following virtual networks:
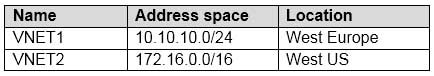
AZ-104 Part 12 Q01 240 The virtual networks contain the following subnets:
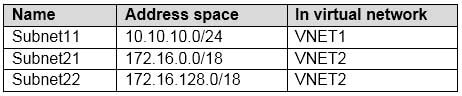
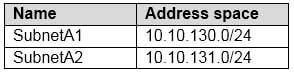
AZ-104 Part 12 Q01 241 Subscription2 contains the following virtual network:
– Name: VNETA
– Address space: 10.10.128.0/17
– Location: Canada CentralVNETA contains the following subnets:
AZ-104 Part 12 Q01 242 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
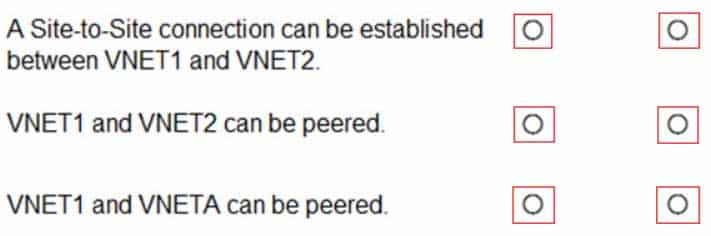
AZ-104 Part 12 Q01 243 Question 
AZ-104 Part 12 Q01 243 Answer Explanation:
Box 1: Yes
With VNet-to-VNet you can connect Virtual Networks in Azure across different regions.Box 2: Yes
Azure supports the following types of peering:
– Virtual network peering: Connect virtual networks within the same Azure region.
– Global virtual network peering: Connecting virtual networks across Azure regions.Box 3: No
The virtual networks you peer must have non-overlapping IP address spaces. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an app named App1 that is installed on two Azure virtual machines named VM1 and VM2. Connections to App1 are managed by using an Azure Load Balancer.
The effective network security configurations for VM2 are shown in the following exhibit.
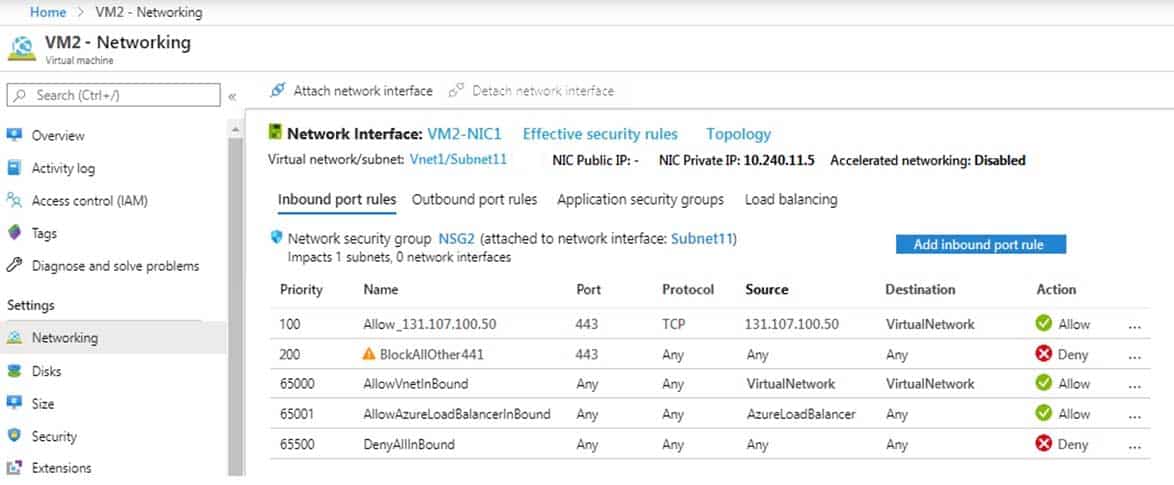
AZ-104 Part 12 Q02 244 You discover that connections to App1 from 131.107.100.50 over TCP port 443 fail.
You verify that the Load Balancer rules are configured correctly.
You need to ensure that connections to App1 can be established successfully from 131.107.100.50 over TCP port 443.
Solution: You create an inbound security rule that denies all traffic from the 131.107.100.50 source and has a cost of 64999.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an app named App1 that is installed on two Azure virtual machines named VM1 and VM2. Connections to App1 are managed by using an Azure Load Balancer.
The effective network security configurations for VM2 are shown in the following exhibit.
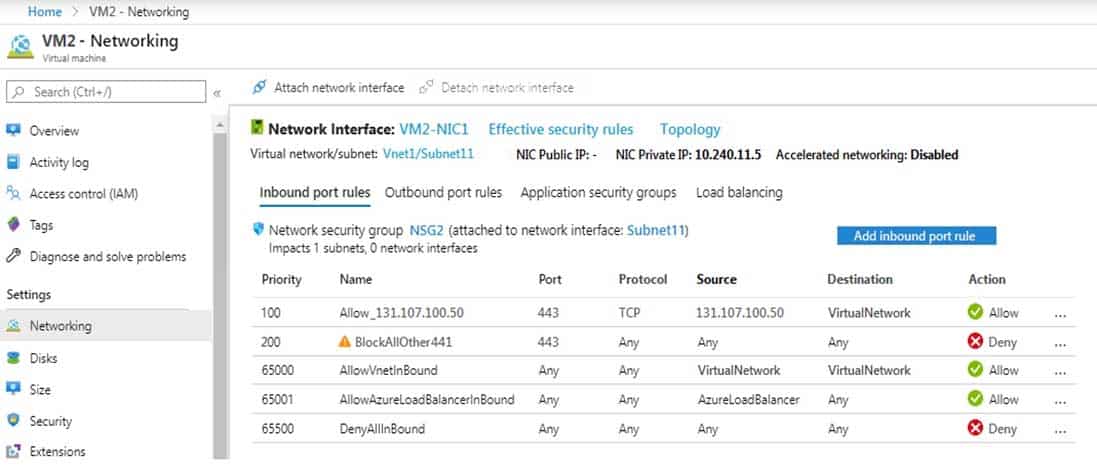
AZ-104 Part 12 Q03 245 You discover that connections to App1 from 131.107.100.50 over TCP port 443 fail.
You verify that the Load Balancer rules are configured correctly.
You need to ensure that connections to App1 can be established successfully from 131.107.100.50 over TCP port 443.
Solution: You delete the BlockAllOther443 inbound security rule.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an app named App1 that is installed on two Azure virtual machines named VM1 and VM2. Connections to App1 are managed by using an Azure Load Balancer.
The effective network security configurations for VM2 are shown in the following exhibit.
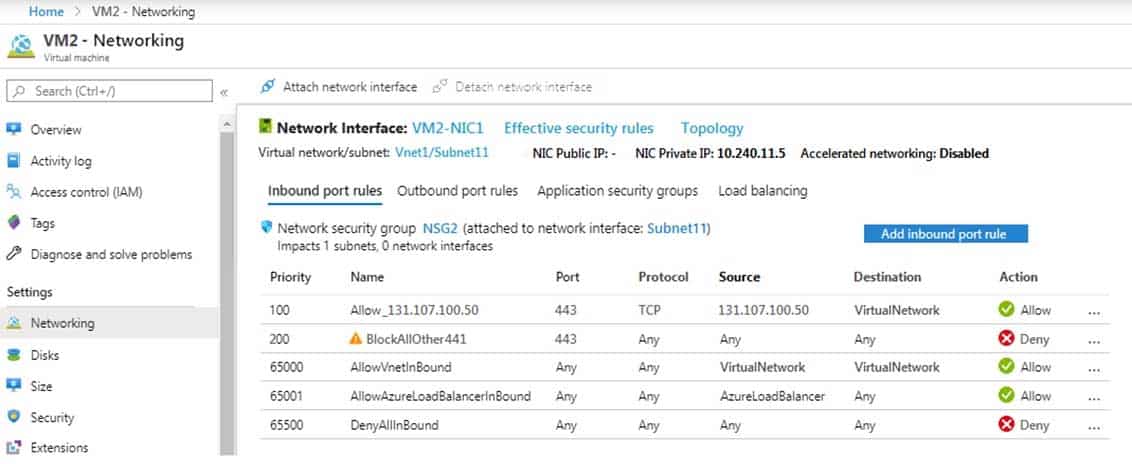
AZ-104 Part 12 Q04 246 You discover that connections to App1 from 131.107.100.50 over TCP port 443 fail.
You verify that the Load Balancer rules are configured correctly.
You need to ensure that connections to App1 can be established successfully from 131.107.100.50 over TCP port 443.
Solution: You modify the priority of the Allow_131.107.100.50 inbound security rule.
Does this meet the goal?
- Yes
- No
Explanation:The rule currently has the highest priority.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains 10 virtual networks. The virtual networks are hosted in separate resource groups.
Another administrator plans to create several network security groups (NSGs) in the subscription.
You need to ensure that when an NSG is created, it automatically blocks TCP port 8080 between the virtual networks.
Solution: You assign a built-in policy definition to the subscription.
Does this meet the goal?
- Yes
- No
Explanation:Resource policy definition used by Azure Policy enables you to establish conventions for resources in your organization by describing when the policy is enforced and what effect to take. By defining conventions, you can control costs and more easily manage your resources.
-
You have an Azure subscription.
You plan to deploy an Azure Kubernetes Service (AKS) cluster to support an app named App1. On-premises clients connect to App1 by using the IP address of the pod.
For the AKS cluster, you need to choose a network type that will support App1.
What should you choose?
- kubenet
- Azure Container Networking Interface (CNI)
- Hybrid Connection endpoints
- Azure Private Link
Explanation:
With Azure CNI, every pod gets an IP address from the subnet and can be accessed directly. These IP addresses must be unique across your network space.Incorrect Answers:
A: The kubenet networking option is the default configuration for AKS cluster creation. With kubenet, nodes get an IP address from the Azure virtual network subnet. Pods receive an IP address from a logically different address space to the Azure virtual network subnet of the nodes. Network address translation (NAT) is then configured so that the pods can reach resources on the Azure virtual network.C, D: AKS only supports Kubenet networking and Azure Container Networking Interface (CNI) networking
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains the virtual machines shown in the following table.

AZ-104 Part 12 Q07 247 You deploy a load balancer that has the following configurations:
– Name: LB1
– Type: Internal
– SKU: Standard
– Virtual network: VNET1You need to ensure that you can add VM1 and VM2 to the backend pool of LB1.
Solution: You disassociate the public IP address from the network interface of VM2.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains 10 virtual networks. The virtual networks are hosted in separate resource groups.
Another administrator plans to create several network security groups (NSGs) in the subscription.
You need to ensure that when an NSG is created, it automatically blocks TCP port 8080 between the virtual networks.
Solution: You configure a custom policy definition, and then you assign the policy to the subscription.
Does this meet the goal?
- Yes
- No
Explanation:Resource policy definition used by Azure Policy enables you to establish conventions for resources in your organization by describing when the policy is enforced and what effect to take. By defining conventions, you can control costs and more easily manage your resources.
-
You have two Azure virtual networks named VNet1 and VNet2. VNet1 contains an Azure virtual machine named VM1. VNet2 contains an Azure virtual machine named VM2.
VM1 hosts a frontend application that connects to VM2 to retrieve data.
Users report that the frontend application is slower than usual.
You need to view the average round-trip time (RTT) of the packets from VM1 to VM2.
Which Azure Network Watcher feature should you use?
- IP flow verify
- Connection troubleshoot
- Connection monitor
- NSG flow logs
Explanation:
The connection monitor capability monitors communication at a regular interval and informs you of reachability, latency, and network topology changes between the VM and the endpointIncorrect Answers:
A: The IP flow verify capability enables you to specify a source and destination IPv4 address, port, protocol (TCP or UDP), and traffic direction (inbound or outbound). IP flow verify then tests the communication and informs you if the connection succeeds or fails. If the connection fails, IP flow verify tells you which security rule allowed or denied the communication, so that you can resolve the problem.B: The connection troubleshoot capability enables you to test a connection between a VM and another VM, an FQDN, a URI, or an IPv4 address. The test returns similar information returned when using the connection monitor capability, but tests the connection at a point in time, rather than monitoring it over time, as connection monitor does.
D: The NSG flow log capability allows you to log the source and destination IP address, port, protocol, and whether traffic was allowed or denied by an NSG.
-
HOTSPOT
You have an Azure subscription that contains the public load balancers shown in the following table.
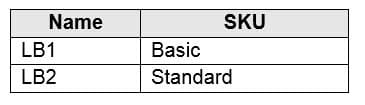
AZ-104 Part 12 Q10 248 You plan to create six virtual machines and to load balance requests to the virtual machines. Each load balancer will load balance three virtual machines.
You need to create the virtual machines for the planned solution.
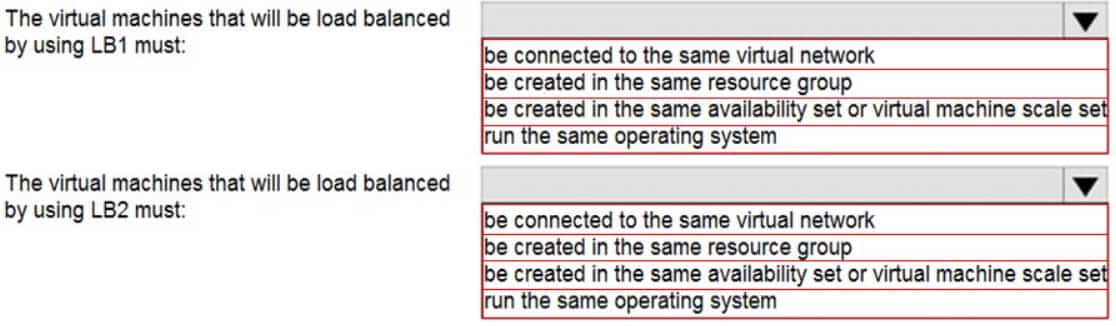
AZ-104 Part 12 Q10 249 Question 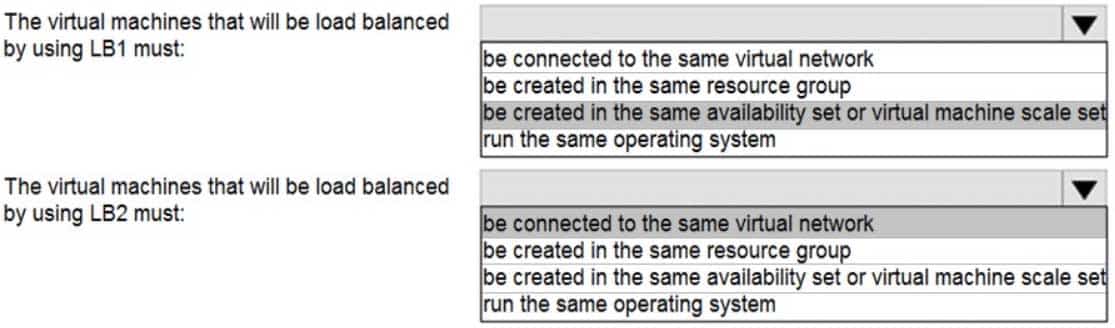
AZ-104 Part 12 Q10 249 Answer Explanation:
Box 1: be created in the same availability set or virtual machine scale set.
The Basic tier is quite restrictive. A load balancer is restricted to a single availability set, virtual machine scale set, or a single machine.Box 2: be connected to the same virtual network
The Standard tier can span any virtual machine in a single virtual network, including blends of scale sets, availability sets, and machines. -
HOTSPOT
You have an on-premises data center and an Azure subscription. The data center contains two VPN devices. The subscription contains an Azure virtual network named VNet1. VNet1 contains a gateway subnet.
You need to create a site-to-site VPN. The solution must ensure that if a single instance of an Azure VPN gateway fails, or a single on-premises VPN device fails, the failure will not cause an interruption that is longer than two minutes.
What is the minimum number of public IP addresses, virtual network gateways, and local network gateways required in Azure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
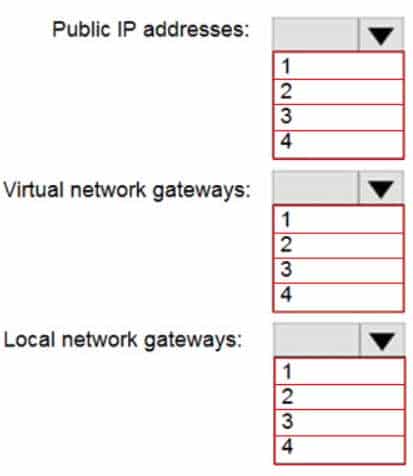
AZ-104 Part 12 Q11 250 Question 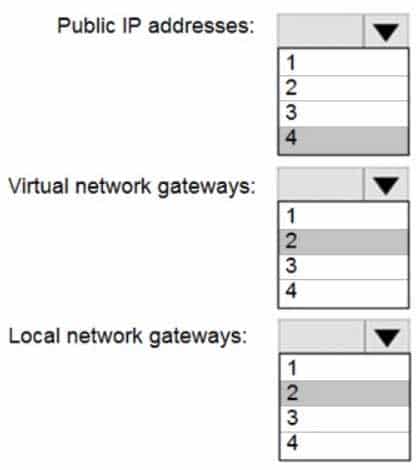
AZ-104 Part 12 Q11 250 Answer Explanation:
Box 1: 4
Two public IP addresses in the on-premises data center, and two public IP addresses in the VNET.
The most reliable option is to combine the active-active gateways on both your network and Azure, as shown in the diagram below.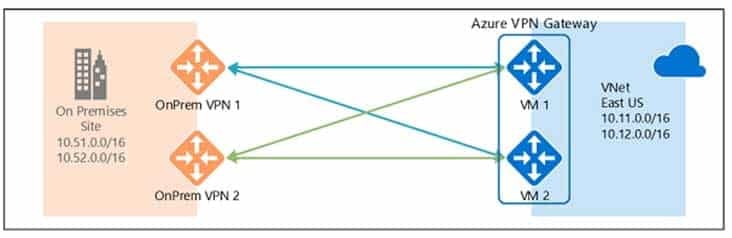
AZ-104 Part 12 Q11 251 Box 2: 2
Every Azure VPN gateway consists of two instances in an active-standby configuration. For any planned maintenance or unplanned disruption that happens to the active instance, the standby instance would take over (failover) automatically, and resume the S2S VPN or VNet-to-VNet connections.Box 3: 2
Dual-redundancy: active-active VPN gateways for both Azure and on-premises networks -
You have an Azure subscription that contains two virtual machines as shown in the following table.
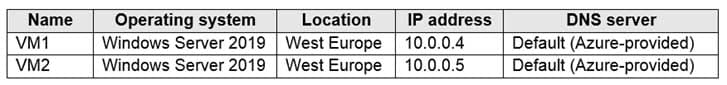
AZ-104 Part 12 Q12 252 You perform a reverse DNS lookup for 10.0.0.4 from VM2.
Which FQDN will be returned?
- vm1.core.windows.net
- vm1.azure.com
- vm1.westeurope.cloudapp.azure.com
- vm1.internal.cloudapp.net
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an app named App1 that is installed on two Azure virtual machines named VM1 and VM2. Connections to App1 are managed by using an Azure Load Balancer.
The effective network security configurations for VM2 are shown in the following exhibit.
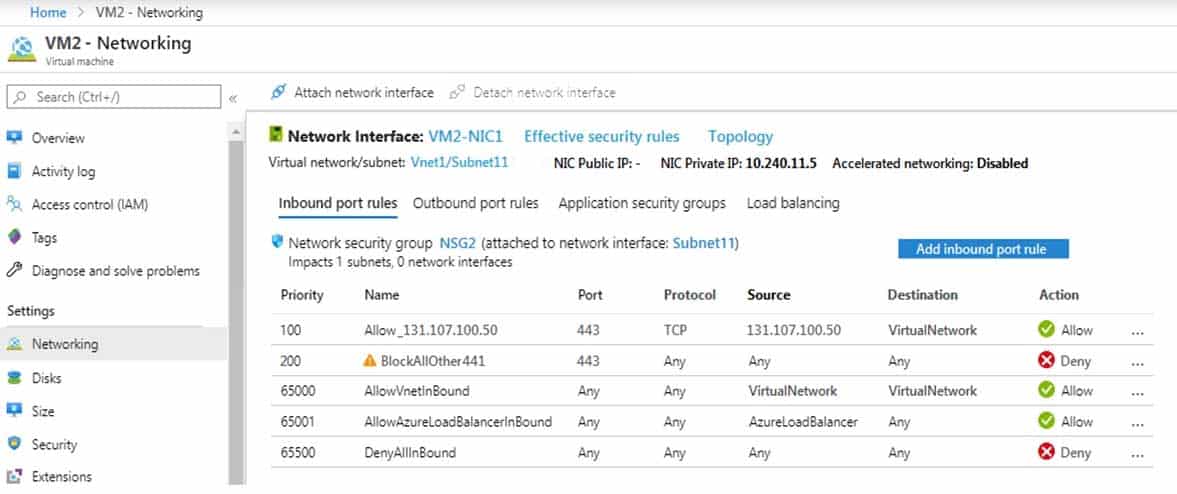
AZ-104 Part 12 Q13 253 You discover that connections to App1 from 131.107.100.50 over TCP port 443 fail.
You verify that the Load Balancer rules are configured correctly.
You need to ensure that connections to App1 can be established successfully from 131.107.100.50 over TCP port 443.
Solution: You create an inbound security rule that allows any traffic from the AzureLoadBalancer source and has a cost of 150.
Does this meet the goal?
- Yes
- No
-
You have an Azure subscription that contains a policy-based virtual network gateway named GW1 and a virtual network named VNet1.
You need to ensure that you can configure a point-to-site connection from an on-premises computer to VNet1.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Add a service endpoint to VNet1
- Reset GW1
- Create a route-based virtual network gateway
- Add a connection to GW1
- Delete GW1
- Add a public IP address space to VNet1
Explanation:
C: A VPN gateway is used when creating a VPN connection to your on-premises network.
Route-based VPN devices use any-to-any (wildcard) traffic selectors, and let routing/forwarding tables direct traffic to different IPsec tunnels. It is typically built on router platforms where each IPsec tunnel is modeled as a network interface or VTI (virtual tunnel interface).E: Policy-based VPN devices use the combinations of prefixes from both networks to define how traffic is encrypted/decrypted through IPsec tunnels. It is typically built on firewall devices that perform packet filtering. IPsec tunnel encryption and decryption are added to the packet filtering and processing engine.
Incorrect Answers:
F: Point-to-Site connections do not require a VPN device or a public-facing IP address. -
HOTSPOT
You have an Azure subscription that contains the resources in the following table:
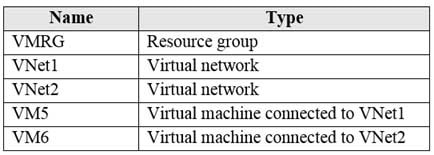
AZ-104 Part 12 Q15 254 In Azure, you create a private DNS zone named adatum.com. You set the registration virtual network to VNet2. The adatum.com zone is configured as shown in the following exhibit:
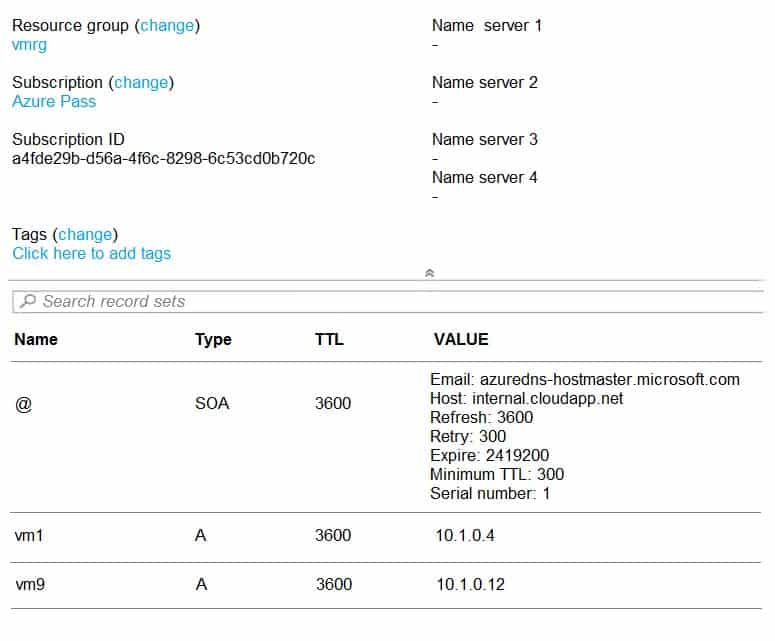
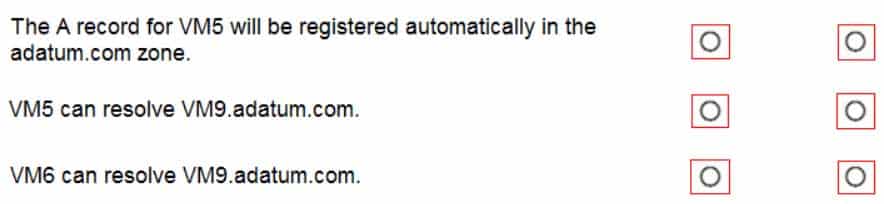
AZ-104 Part 12 Q15 255 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
AZ-104 Part 12 Q15 256 Question 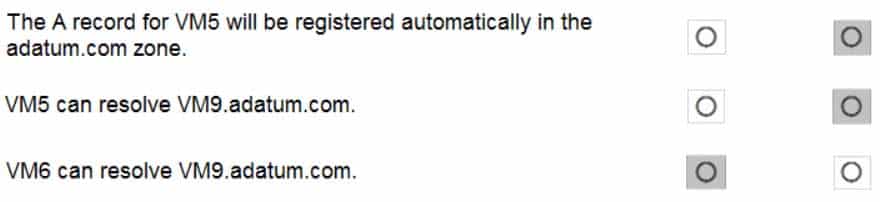
AZ-104 Part 12 Q15 256 Answer Explanation:
Box 1: No
Azure DNS provides automatic registration of virtual machines from a single virtual network that’s linked to a private zone as a registration virtual network. VM5 does not belong to the registration virtual network though.Box 2: No
Forward DNS resolution is supported across virtual networks that are linked to the private zone as resolution virtual networks. VM5 does belong to a resolution virtual network.Box 3: Yes
VM6 belongs to registration virtual network, and an A (Host) record exists for VM9 in the DNS zone.
By default, registration virtual networks also act as resolution virtual networks, in the sense that DNS resolution against the zone works from any of the virtual machines within the registration virtual network. -
HOTSPOT
You have an Azure subscription that contains the virtual networks shown in the following table.
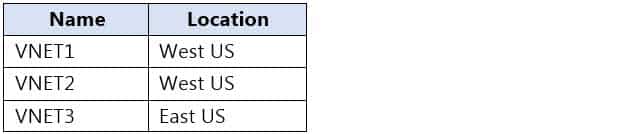
AZ-104 Part 12 Q16 257 The subscription contains the private DNS zones shown in the following table.
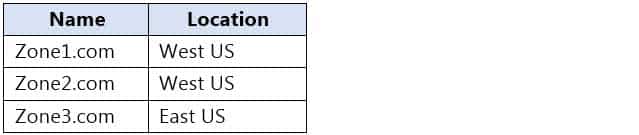
AZ-104 Part 12 Q16 258 You add virtual network links to the private DNS zones as shown in the following table.
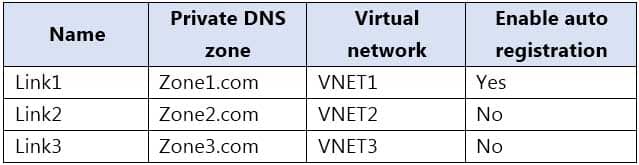
AZ-104 Part 12 Q16 259 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
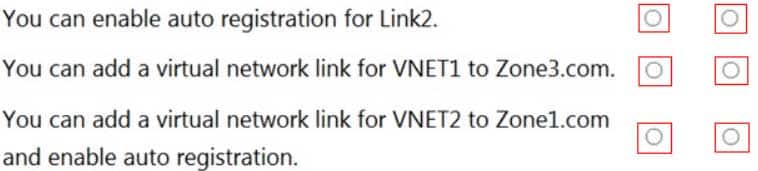
AZ-104 Part 12 Q16 260 Question 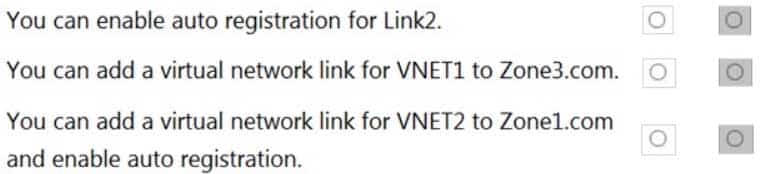
AZ-104 Part 12 Q16 260 Answer -
HOTSPOT
You have an Azure subscription.
You plan to use an Azure Resource Manager template to deploy a virtual network named VNET1 that will use Azure Bastion.
How should you complete the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
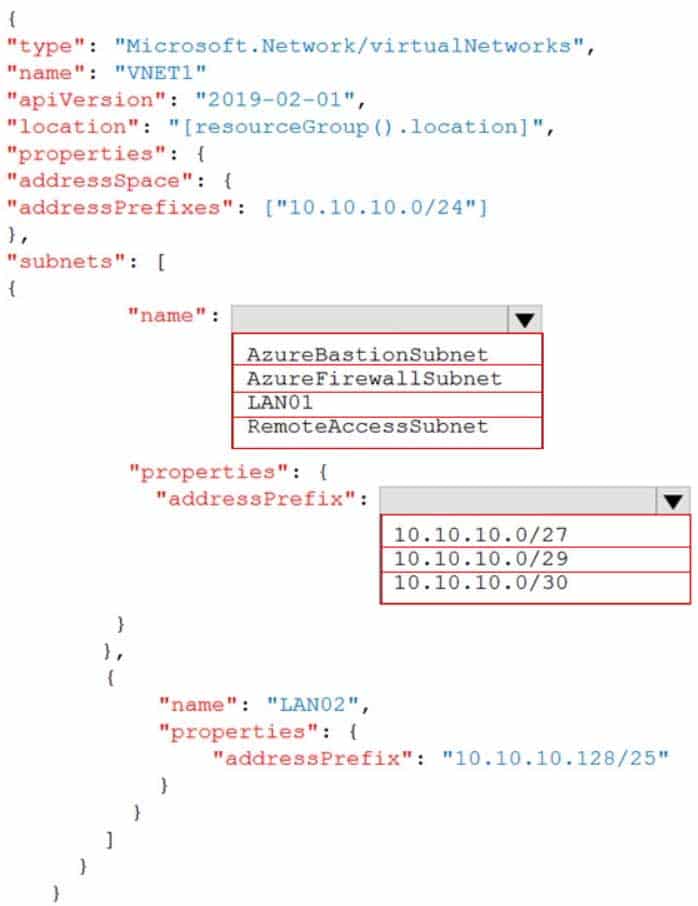
AZ-104 Part 12 Q17 261 Question 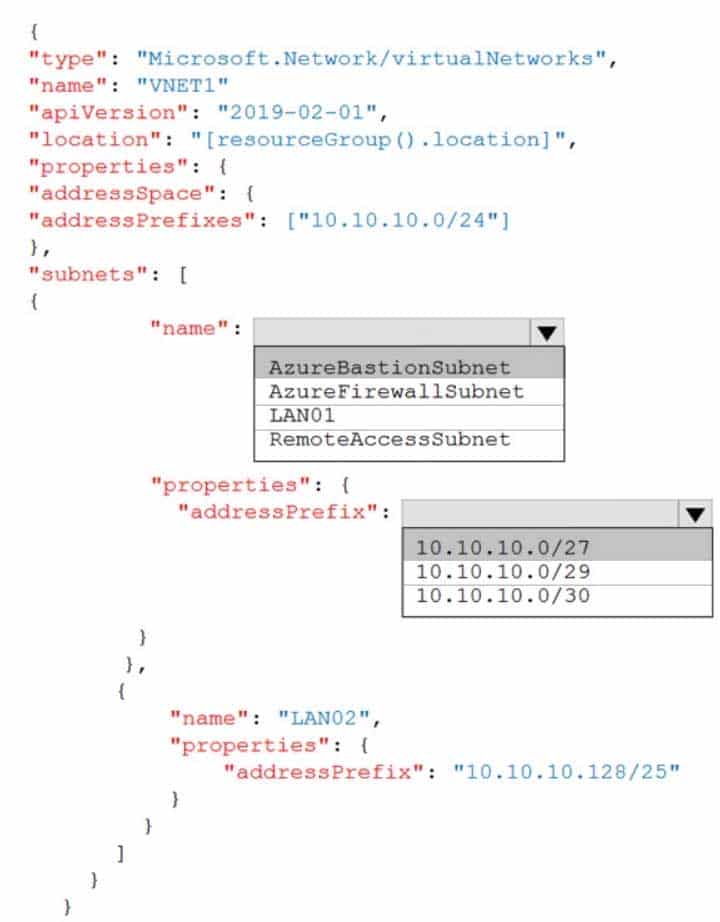
AZ-104 Part 12 Q17 261 Answer -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You manage a virtual network named VNet1 that is hosted in the West US Azure region.
VNet1 hosts two virtual machines named VM1 and VM2 that run Windows Server.
You need to inspect all the network traffic from VM1 to VM2 for a period of three hours.
Solution: From Azure Network Watcher, you create a packet capture.
Does this meet the goal?
- Yes
- No
Explanation:Use the Connection Monitor feature of Azure Network Watcher.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You manage a virtual network named VNet1 that is hosted in the West US Azure region.
VNet1 hosts two virtual machines named VM1 and VM2 that run Windows Server.
You need to inspect all the network traffic from VM1 to VM2 for a period of three hours.
Solution: From Azure Network Watcher, you create a connection monitor.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You manage a virtual network named VNet1 that is hosted in the West US Azure region.
VNet1 hosts two virtual machines named VM1 and VM2 that run Windows Server.
You need to inspect all the network traffic from VM1 to VM2 for a period of three hours.
Solution: From Performance Monitor, you create a Data Collector Set (DCS).
Does this meet the goal?
- Yes
- No