AZ-204 : Developing Solutions for Microsoft Azure : Part 06
AZ-204 : Developing Solutions for Microsoft Azure : Part 06
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Background
Wide World Importers is moving all their datacenters to Azure. The company has developed several applications and services to support supply chain operations and would like to leverage serverless computing where possible.
Current environment
Windows Server 2016 virtual machine
This virtual machine (VM) runs BizTalk Server 2016. The VM runs the following workflows:
-Ocean Transport – This workflow gathers and validates container information including container contents and arrival notices at various shipping ports.
-Inland Transport – This workflow gathers and validates trucking information including fuel usage, number of stops, and routes.The VM supports the following REST API calls:
-Container API – This API provides container information including weight, contents, and other attributes.
-Location API – This API provides location information regarding shipping ports of call and trucking stops.
-Shipping REST API – This API provides shipping information for use and display on the shipping website.Shipping Data
The application uses MongoDB JSON document storage database for all container and transport information.
Shipping Web Site
The site displays shipping container tracking information and container contents. The site is located at http://shipping.wideworldimporters.com/
Proposed solution
The on-premises shipping application must be moved to Azure. The VM has been migrated to a new Standard_D16s_v3 Azure VM by using Azure Site Recovery and must remain running in Azure to complete the BizTalk component migrations. You create a Standard_D16s_v3 Azure VM to host BizTalk Server. The Azure architecture diagram for the proposed solution is shown below:
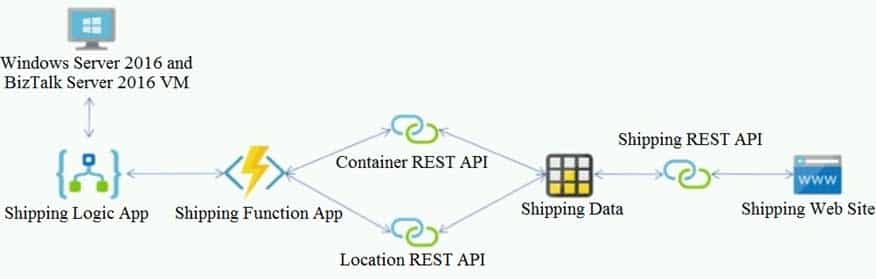
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q01 154 Requirements
Shipping Logic app
The Shipping Logic app must meet the following requirements:
-Support the ocean transport and inland transport workflows by using a Logic App.
-Support industry-standard protocol X12 message format for various messages including vessel content details and arrival notices.
-Secure resources to the corporate VNet and use dedicated storage resources with a fixed costing model.
-Maintain on-premises connectivity to support legacy applications and final BizTalk migrations.Shipping Function app
Implement secure function endpoints by using app-level security and include Azure Active Directory (Azure AD).
REST APIs
The REST API’s that support the solution must meet the following requirements:
-Secure resources to the corporate VNet.
-Allow deployment to a testing location within Azure while not incurring additional costs.
-Automatically scale to double capacity during peak shipping times while not causing application downtime.
-Minimize costs when selecting an Azure payment model.Shipping data
Data migration from on-premises to Azure must minimize costs and downtime.
Shipping website
Use Azure Content Delivery Network (CDN) and ensure maximum performance for dynamic content while minimizing latency and costs.
Issues
Windows Server 2016 VM
The VM shows high network latency, jitter, and high CPU utilization. The VM is critical and has not been backed up in the past. The VM must enable a quick restore from a 7-day snapshot to include in-place restore of disks in case of failure.
Shipping website and REST APIs
The following error message displays while you are testing the website:
Failed to load http://test-shippingapi.wideworldimporters.com/: No ‘Access-Control-Allow-Origin’ header is present on the requested resource. Origin ‘http://test.wideworldimporters.com/’ is therefore not allowed access.
-
HOTSPOT
You need to secure the Shipping Function app.
How should you configure the app? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-204 Developing Solutions for Microsoft Azure Part 06 Q01 155 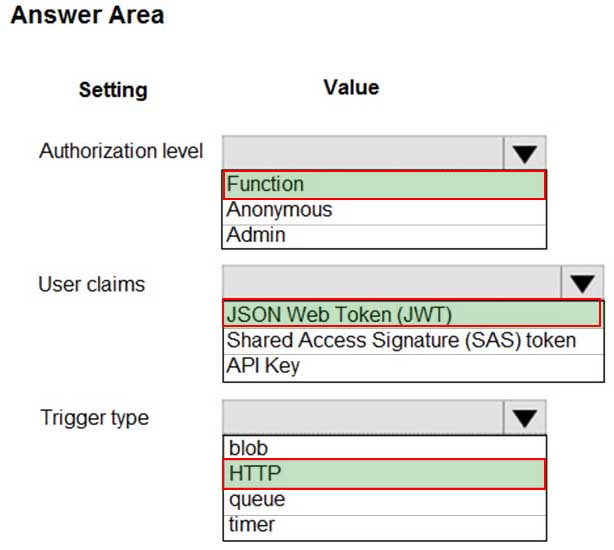
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q01 156 Explanation:Scenario: Shipping Function app: Implement secure function endpoints by using app-level security and include Azure Active Directory (Azure AD).
Box 1: Function
Box 2: JSON based Token (JWT)
Azure AD uses JSON based tokens (JWTs) that contain claimsBox 3: HTTP
How a web app delegates sign-in to Azure AD and obtains a token
User authentication happens via the browser. The OpenID protocol uses standard HTTP protocol messages. -
You need to secure the Shipping Logic App.
What should you use?
- Azure App Service Environment (ASE)
- Integration Service Environment (ISE)
- VNet service endpoint
- Azure AD B2B integration
Explanation:Scenario: The Shipping Logic App requires secure resources to the corporate VNet and use dedicated storage resources with a fixed costing model.
You can access to Azure Virtual Network resources from Azure Logic Apps by using integration service environments (ISEs).
Sometimes, your logic apps and integration accounts need access to secured resources, such as virtual machines (VMs) and other systems or services, that are inside an Azure virtual network. To set up this access, you can create an integration service environment (ISE) where you can run your logic apps and create your integration accounts.
-
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Background
City Power & Light company provides electrical infrastructure monitoring solutions for homes and businesses. The company is migrating solutions to Azure.
Current environment
Architecture overview
The company has a public website located at http://www.cpandl.com/. The site is a single-page web application that runs in Azure App Service on Linux. The website uses files stored in Azure Storage and cached in Azure Content Delivery Network (CDN) to serve static content.
API Management and Azure Function App functions are used to process and store data in Azure Database for PostgreSQL. API Management is used to broker communications to the Azure Function app functions for Logic app integration. Logic apps are used to orchestrate the data processing while Service Bus and Event Grid handle messaging and events.
The solution uses Application Insights, Azure Monitor, and Azure Key Vault.
Architecture diagram
The company has several applications and services that support their business. The company plans to implement serverless computing where possible. The overall architecture is shown below.
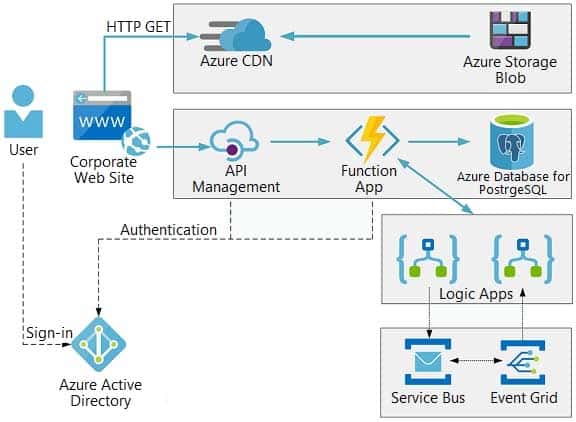
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 157 User authentication
The following steps detail the user authentication process:
1.The user selects Sign in in the website.
2.The browser redirects the user to the Azure Active Directory (Azure AD) sign in page.
3.The user signs in.
4.Azure AD redirects the user’s session back to the web application. The URL includes an access token.
5.The web application calls an API and includes the access token in the authentication header. The application ID is sent as the audience (‘aud’) claim in the access token.
6.The back-end API validates the access token.Requirements
Corporate website
-Communications and content must be secured by using SSL.
-Communications must use HTTPS.
-Data must be replicated to a secondary region and three availability zones.
-Data storage costs must be minimized.Azure Database for PostgreSQL
The database connection string is stored in Azure Key Vault with the following attributes:
-Azure Key Vault name: cpandlkeyvault
-Secret name: PostgreSQLConn
-Id: 80df3e46ffcd4f1cb187f79905e9a1e8The connection information is updated frequently. The application must always use the latest information to connect to the database.
Azure Service Bus and Azure Event Grid
-Azure Event Grid must use Azure Service Bus for queue-based load leveling.
-Events in Azure Event Grid must be routed directly to Service Bus queues for use in buffering.
-Events from Azure Service Bus and other Azure services must continue to be routed to Azure Event Grid for processing.Security
-All SSL certificates and credentials must be stored in Azure Key Vault.
-File access must restrict access by IP, protocol, and Azure AD rights.
-All user accounts and processes must receive only those privileges which are essential to perform their intended function.Compliance
Auditing of the file updates and transfers must be enabled to comply with General Data Protection Regulation (GDPR). The file updates must be read-only, stored in the order in which they occurred, include only create, update, delete, and copy operations, and be retained for compliance reasons.
Issues
Corporate website
While testing the site, the following error message displays:
CryptographicException: The system cannot find the file specified.Function app
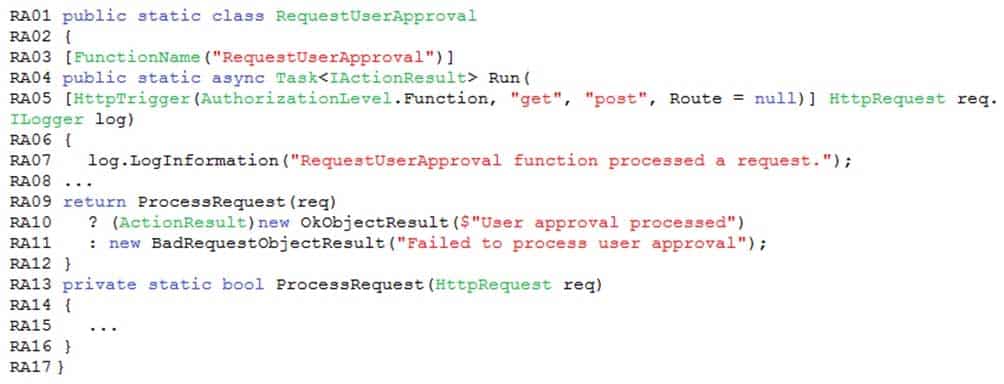
You perform local testing for the RequestUserApproval function. The following error message displays:
‘Timeout value of 00:10:00 exceeded by function: RequestUserApproval’The same error message displays when you test the function in an Azure development environment when you run the following Kusto query:
FunctionAppLogs
| where FunctionName = = “RequestUserApproval”Logic app
You test the Logic app in a development environment. The following error message displays:
‘400 Bad Request’
Troubleshooting of the error shows an HttpTrigger action to call the RequestUserApproval function.Code
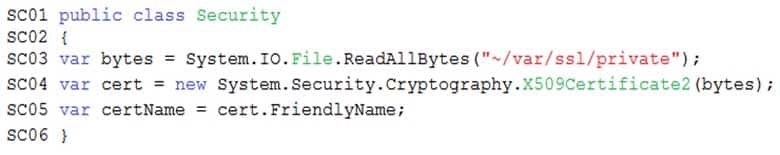
Corporate website
Security.cs:
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 158 Function app
RequestUserApproval.cs:
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 159 -
HOTSPOT
You need to retrieve the database connection string.
Which values should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 160 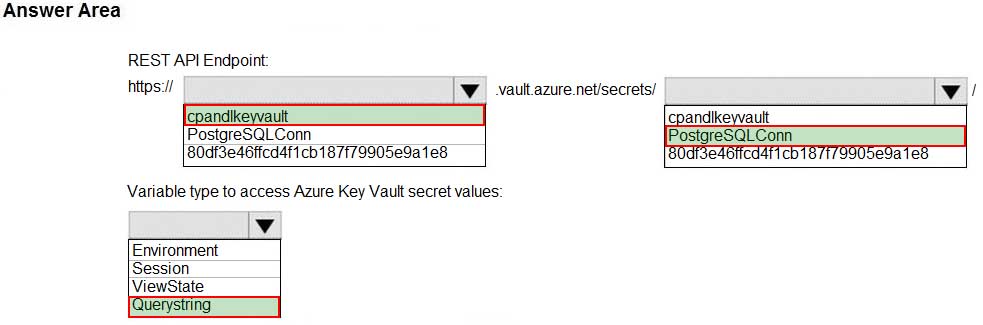
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 161 Explanation:Azure database connection string retrieve REST API vault.azure.net/secrets/
Box 1: cpandlkeyvault
We specify the key vault, cpandlkeyvault.Scenario: The database connection string is stored in Azure Key Vault with the following attributes:
Azure Key Vault name: cpandlkeyvault
Secret name: PostgreSQLConn
Id: 80df3e46ffcd4f1cb187f79905e9a1e8Box 2: PostgreSQLConn
We specify the secret, PostgreSQLConnExample, sample request:
https://myvault.vault.azure.net//secrets/mysecretname/4387e9f3d6e14c459867679a90fd0f79?api-version=7.1Box 3: Querystring
-
DRAG DROP
You need to correct the corporate website error.
Which four actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 162 
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 163 Explanation:Scenario: Corporate website
While testing the site, the following error message displays:
CryptographicException: The system cannot find the file specified.Step 1: Generate a certificate
Step 2: Upload the certificate to Azure Key Vault
Scenario: All SSL certificates and credentials must be stored in Azure Key Vault.Step 3: Import the certificate to Azure App Service
Step 4: Update line SCO5 of Security.cs to include error handling and then redeploy the code
-
HOTSPOT
You need to configure API Management for authentication.
Which policy values should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 164 
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 165 Explanation:Box 1: Validate JWT
The validate-jwt policy enforces existence and validity of a JWT extracted from either a specified HTTP Header or a specified query parameter.Scenario: User authentication (see step 5 below)
The following steps detail the user authentication process:
The user selects Sign in in the website.
The browser redirects the user to the Azure Active Directory (Azure AD) sign in page.
The user signs in.
Azure AD redirects the user’s session back to the web application. The URL includes an access token.
The web application calls an API and includes the access token in the authentication header. The application ID is sent as the audience (‘aud’) claim in the access token.
The back-end API validates the access token.Incorrect Answers:
Limit call rate by key – Prevents API usage spikes by limiting call rate, on a per key basis.
Restrict caller IPs – Filters (allows/denies) calls from specific IP addresses and/or address ranges.
Check HTTP header – Enforces existence and/or value of a HTTP Header.Box 2: Outbound
-
You need to authenticate the user to the corporate website as indicated by the architectural diagram.
Which two values should you use? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- ID token signature
- ID token claims
- HTTP response code
- Azure AD endpoint URI
- Azure AD tenant ID
Explanation:A: Claims in access tokens
JWTs (JSON Web Tokens) are split into three pieces:
-Header – Provides information about how to validate the token including information about the type of token and how it was signed.
-Payload – Contains all of the important data about the user or app that is attempting to call your service.
-Signature – Is the raw material used to validate the token.E: Your client can get an access token from either the v1.0 endpoint or the v2.0 endpoint using a variety of protocols.
Scenario: User authentication (see step 5 below)
The following steps detail the user authentication process:
1.The user selects Sign in in the website.
2.The browser redirects the user to the Azure Active Directory (Azure AD) sign in page.
3.The user signs in.
4.Azure AD redirects the user’s session back to the web application. The URL includes an access token.
5.The web application calls an API and includes the access token in the authentication header. The application ID is sent as the audience (‘aud’) claim in the access token.
6.The back-end API validates the access token. -
HOTSPOT
You need to correct the Azure Logic app error message.
Which configuration values should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 166 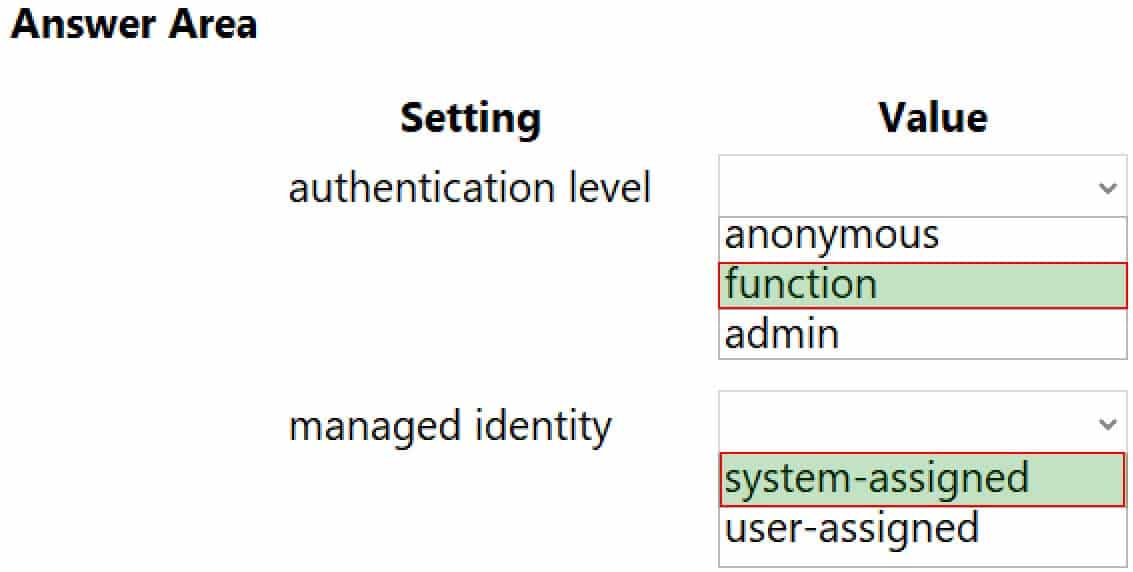
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 167 Explanation:Scenario: You test the Logic app in a development environment. The following error message displays:
‘400 Bad Request’
Troubleshooting of the error shows an HttpTrigger action to call the RequestUserApproval function.Note: If the inbound call’s request body doesn’t match your schema, the trigger returns an HTTP 400 Bad Request error.
Box 1: function
If you have an Azure function where you want to use the system-assigned identity, first enable authentication for Azure functions.Box 2: system-assigned
Your logic app or individual connections can use either the system-assigned identity or a single user-assigned identity, which you can share across a group of logic apps, but not both. -
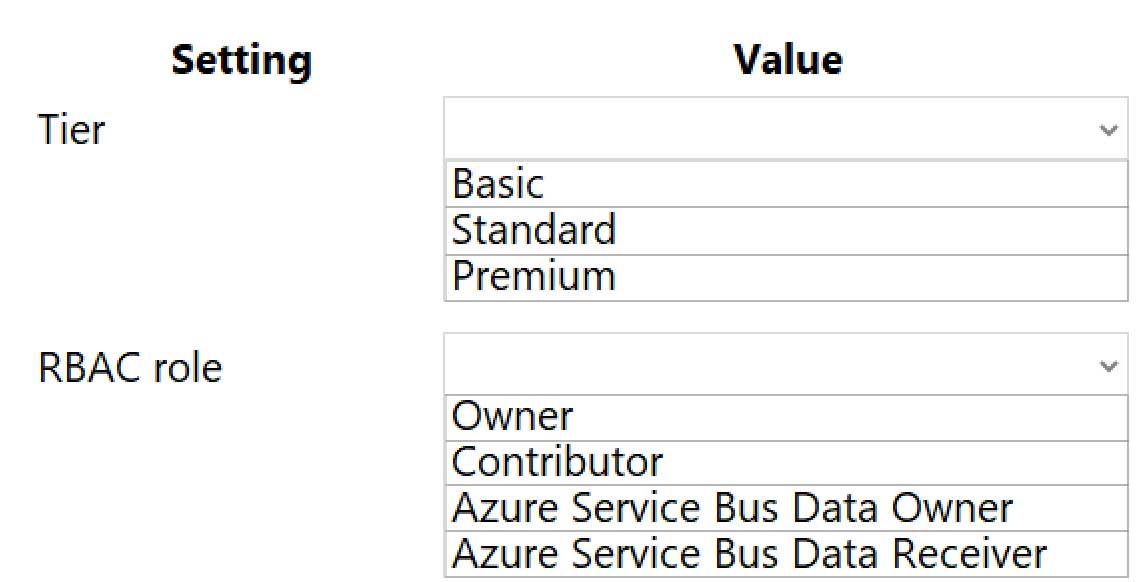
HOTSPOT
You need to configure Azure Service Bus to Event Grid integration.
Which Azure Service Bus settings should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 168 
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q02 169 Explanation:Explanation:
Box 1: Premium
Service Bus can now emit events to Event Grid when there are messages in a queue or a subscription when no receivers are present. You can create Event Grid subscriptions to your Service Bus namespaces, listen to these events, and then react to the events by starting a receiver. With this feature, you can use Service Bus in reactive programming models.To enable the feature, you need the following items:
A Service Bus Premium namespace with at least one Service Bus queue or a Service Bus topic with at least one subscription.
Contributor access to the Service Bus namespace.Box 2: Contributor
-
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Background
You are a developer for Litware Inc., a SaaS company that provides a solution for managing employee expenses. The solution consists of an ASP.NET Core Web API project that is deployed as an Azure Web App.
Overall architecture
Employees upload receipts for the system to process. When processing is complete, the employee receives a summary report email that details the processing results. Employees then use a web application to manage their receipts and perform any additional tasks needed for reimbursement.
Receipt processing
Employees may upload receipts in two ways:-Uploading using an Azure Files mounted folder
-Uploading using the web applicationData Storage
Receipt and employee information is stored in an Azure SQL database.Documentation
Employees are provided with a getting started document when they first use the solution. The documentation includes details on supported operating systems for Azure File upload, and instructions on how to configure the mounted folder.
Solution details
Users table
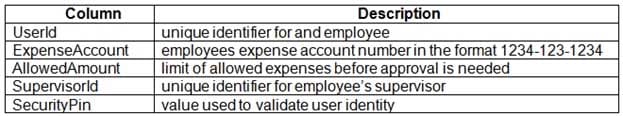
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q03 170 Web Application
You enable MSI for the Web App and configure the Web App to use the security principal name WebAppIdentity.
Processing
Processing is performed by an Azure Function that uses version 2 of the Azure Function runtime. Once processing is completed, results are stored in Azure Blob Storage and an Azure SQL database. Then, an email summary is sent to the user with a link to the processing report. The link to the report must remain valid if the email is forwarded to another user.
Logging
Azure Application Insights is used for telemetry and logging in both the processor and the web application. The processor also has TraceWriter logging enabled. Application Insights must always contain all log messages.
Requirements
Receipt processing
Concurrent processing of a receipt must be prevented.
Disaster recovery
Regional outage must not impact application availability. All DR operations must not be dependent on application running and must ensure that data in the DR region is up to date.
Security
-User’s SecurityPin must be stored in such a way that access to the database does not allow the viewing of SecurityPins. The web application is the only system that should have access to SecurityPins.
-All certificates and secrets used to secure data must be stored in Azure Key Vault.
-You must adhere to the principle of least privilege and provide privileges which are essential to perform the intended function.
-All access to Azure Storage and Azure SQL database must use the application’s Managed Service Identity (MSI).
-Receipt data must always be encrypted at rest.
-All data must be protected in transit.
-User’s expense account number must be visible only to logged in users. All other views of the expense account number should include only the last segment, with the remaining parts obscured.
-In the case of a security breach, access to all summary reports must be revoked without impacting other parts of the system.Issues
Upload format issue
Employees occasionally report an issue with uploading a receipt using the web application. They report that when they upload a receipt using the Azure File Share, the receipt does not appear in their profile. When this occurs, they delete the file in the file share and use the web application, which returns a 500 Internal Server error page.
Capacity issue
During busy periods, employees report long delays between the time they upload the receipt and when it appears in the web application.
Log capacity issue
Developers report that the number of log messages in the trace output for the processor is too high, resulting in lost log messages.
Application code
Processing.cs
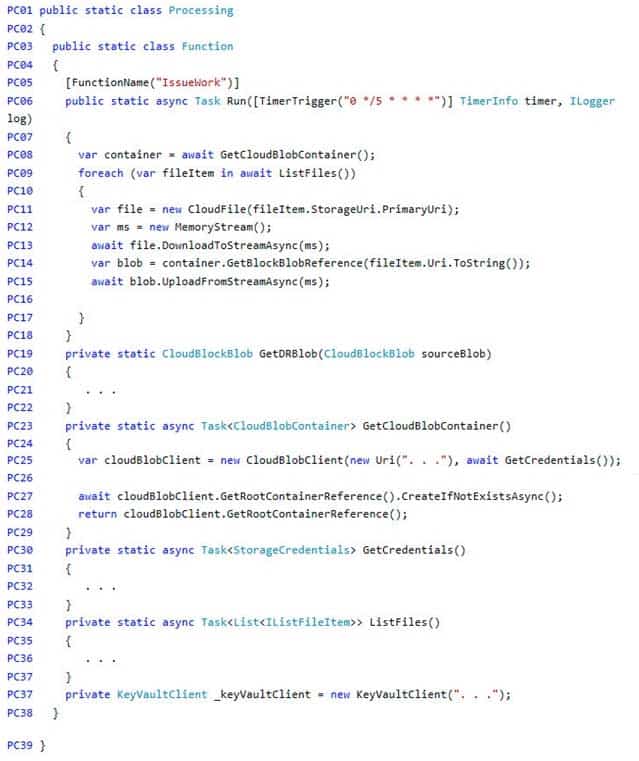
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q03 171 Database.cs

AZ-204 Developing Solutions for Microsoft Azure Part 06 Q03 172 ReceiptUploader.cs
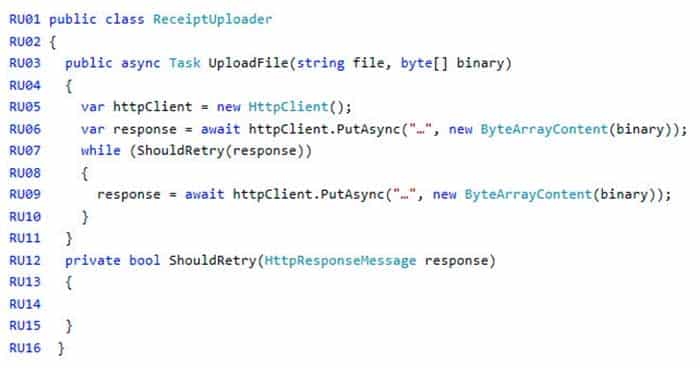
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q03 173 ConfigureSSE.ps1
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q03 174 -
HOTSPOT
You need to add code at line PC26 of Processing.cs to ensure that security policies are met.
How should you complete the code that you will add at line PC26? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-204 Developing Solutions for Microsoft Azure Part 06 Q03 175 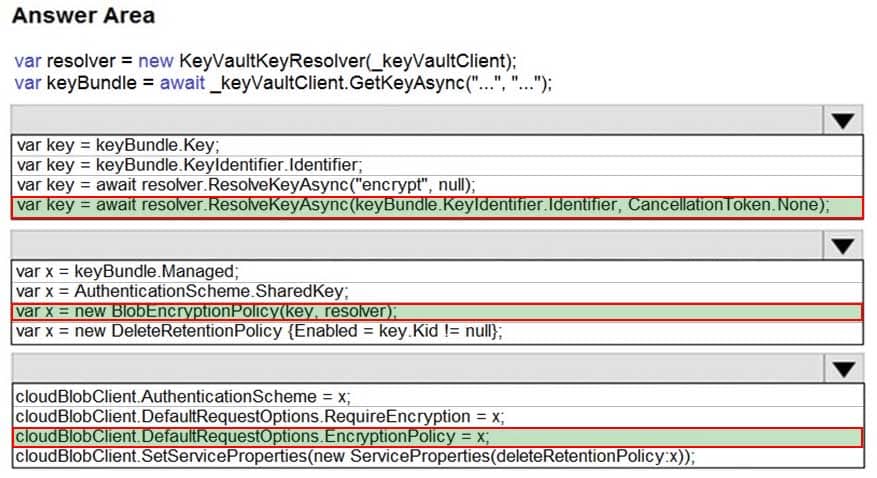
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q03 176 Explanation:Box 1: var key = await Resolver.ResolveKeyAsyn(keyBundle,KeyIdentifier.CancellationToken.None);
Box 2: var x = new BlobEncryptionPolicy(key,resolver);
Example:
// We begin with cloudKey1, and a resolver capable of resolving and caching Key Vault secrets.
BlobEncryptionPolicy encryptionPolicy = new BlobEncryptionPolicy(cloudKey1, cachingResolver);
client.DefaultRequestOptions.EncryptionPolicy = encryptionPolicy;Box 3: cloudblobClient. DefaultRequestOptions.EncryptionPolicy = x;
-
You need to ensure the security policies are met.
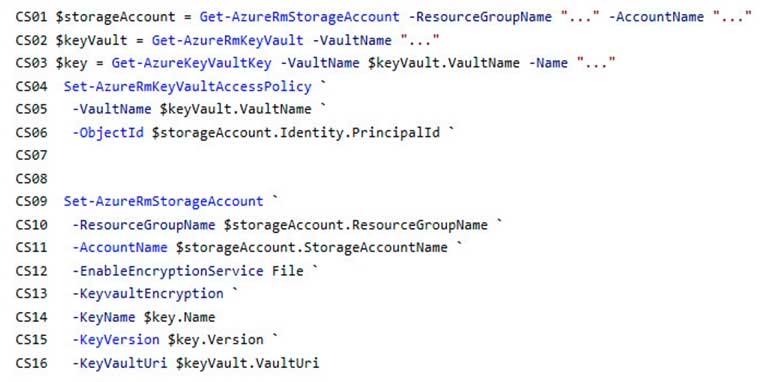
What code do you add at line CS07 of ConfigureSSE.ps1?
- –PermissionsToKeys create, encrypt, decrypt
- –PermissionsToCertificates create, encrypt, decrypt
- –PermissionsToCertificates wrapkey, unwrapkey, get
- –PermissionsToKeys wrapkey, unwrapkey, get
Explanation:Scenario: All certificates and secrets used to secure data must be stored in Azure Key Vault.
You must adhere to the principle of least privilege and provide privileges which are essential to perform the intended function.The Set-AzureRmKeyValutAccessPolicy parameter -PermissionsToKeys specifies an array of key operation permissions to grant to a user or service principal. The acceptable values for this parameter: decrypt, encrypt, unwrapKey, wrapKey, verify, sign, get, list, update, create, import, delete, backup, restore, recover, purge
Incorrect Answers:
A, C: The Set-AzureRmKeyValutAccessPolicy parameter -PermissionsToCertificates specifies an array of certificate permissions to grant to a user or service principal. The acceptable values for this parameter: get, list, delete, create, import, update, managecontacts, getissuers, listissuers, setissuers, deleteissuers, manageissuers, recover, purge, backup, restore
-
-
DRAG DROP
You develop a web application.
You need to register the application with an active Azure Active Directory (Azure AD) tenant.
Which three actions should you perform in sequence? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.

AZ-204 Developing Solutions for Microsoft Azure Part 06 Q04 177 
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q04 178 Explanation:Register a new application using the Azure portal
Sign in to the Azure portal using either a work or school account or a personal Microsoft account.
If your account gives you access to more than one tenant, select your account in the upper right corner. Set your portal session to the Azure AD tenant that you want.
Search for and select Azure Active Directory. Under Manage, select App registrations.
Select New registration. (Step 1)
In Register an application, enter a meaningful application name to display to users.
Specify who can use the application. Select the Azure AD instance. (Step 2)
Under Redirect URI (optional), select the type of app you’re building: Web or Public client (mobile & desktop). Then enter the redirect URI, or reply URL, for your application. (Step 3)
When finished, select Register. -
You have a new Azure subscription. You are developing an internal website for employees to view sensitive data. The website uses Azure Active Directory (Azure AD) for authentication.
You need to implement multifactor authentication for the website.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Configure the website to use Azure AD B2C.
- In Azure AD, create a new conditional access policy.
- Upgrade to Azure AD Premium.
- In Azure AD, enable application proxy.
- In Azure AD conditional access, enable the baseline policy.
Explanation:B: MFA Enabled by conditional access policy. It is the most flexible means to enable two-step verification for your users. Enabling using conditional access policy only works for Azure MFA in the cloud and is a premium feature of Azure AD.
C: Multi-Factor Authentication comes as part of the following offerings:
-Azure Active Directory Premium licenses – Full featured use of Azure Multi-Factor Authentication Service (Cloud) or Azure Multi-Factor Authentication Server (On-premises).
-Multi-Factor Authentication for Office 365
-Azure Active Directory Global Administrators -
You are developing a Java application that uses Cassandra to store key and value data. You plan to use a new Azure Cosmos DB resource and the Cassandra API in the application. You create an Azure Active Directory (Azure AD) group named Cosmos DB Creators to enable provisioning of Azure Cosmos accounts, databases, and containers.
The Azure AD group must not be able to access the keys that are required to access the data.
You need to restrict access to the Azure AD group.
Which role-based access control should you use?
- DocumentDB Accounts Contributor
- Cosmos Backup Operator
- Cosmos DB Operator
- Cosmos DB Account Reader
Explanation:Azure Cosmos DB now provides a new RBAC role, Cosmos DB Operator. This new role lets you provision Azure Cosmos accounts, databases, and containers, but can’t access the keys that are required to access the data. This role is intended for use in scenarios where the ability to grant access to Azure Active Directory service principals to manage deployment operations for Cosmos DB is needed, including the account, database, and containers.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are developing a website that will run as an Azure Web App. Users will authenticate by using their Azure Active Directory (Azure AD) credentials.
You plan to assign users one of the following permission levels for the website: admin, normal, and reader. A user’s Azure AD group membership must be used to determine the permission level.
You need to configure authorization.
Solution: Configure the Azure Web App for the website to allow only authenticated requests and require Azure AD log on.
Does the solution meet the goal?
- Yes
- No
Explanation:Instead in the Azure AD application’s manifest, set value of the groupMembershipClaims option to All.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are developing a website that will run as an Azure Web App. Users will authenticate by using their Azure Active Directory (Azure AD) credentials.
You plan to assign users one of the following permission levels for the website: admin, normal, and reader. A user’s Azure AD group membership must be used to determine the permission level.
You need to configure authorization.
Solution:
Create a new Azure AD application. In the application’s manifest, set value of the groupMembershipClaims option to All.
In the website, use the value of the groups claim from the JWT for the user to determine permissions.Does the solution meet the goal?
- Yes
- No
Explanation:To configure Manifest to include Group Claims in Auth Token
Go to Azure Active Directory to configure the Manifest. Click on Azure Active Directory, and go to App registrations to find your application:
Click on your application (or search for it if you have a lot of apps) and edit the Manifest by clicking on it.
Locate the “groupMembershipClaims” setting. Set its value to either “SecurityGroup” or “All”. To help you decide which:
“SecurityGroup” – groups claim will contain the identifiers of all security groups of which the user is a member.
“All” – groups claim will contain the identifiers of all security groups and all distribution lists of which the user is a memberNow your application will include group claims in your manifest and you can use this fact in your code.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are developing a website that will run as an Azure Web App. Users will authenticate by using their Azure Active Directory (Azure AD) credentials.
You plan to assign users one of the following permission levels for the website: admin, normal, and reader. A user’s Azure AD group membership must be used to determine the permission level.
You need to configure authorization.
Solution:
Create a new Azure AD application. In the application’s manifest, define application roles that match the required permission levels for the application.
Assign the appropriate Azure AD group to each role. In the website, use the value of the roles claim from the JWT for the user to determine permissions.Does the solution meet the goal?
- Yes
- No
Explanation:To configure Manifest to include Group Claims in Auth Token
1.Go to Azure Active Directory to configure the Manifest. Click on Azure Active Directory, and go to App registrations to find your application:
2.Click on your application (or search for it if you have a lot of apps) and edit the Manifest by clicking on it.
3.Locate the “groupMembershipClaims” setting. Set its value to either “SecurityGroup” or “All”. To help you decide which:
-“SecurityGroup” – groups claim will contain the identifiers of all security groups of which the user is a member.
-“All” – groups claim will contain the identifiers of all security groups and all distribution lists of which the user is a memberNow your application will include group claims in your manifest and you can use this fact in your code.
-
DRAG DROP
You are developing an application to securely transfer data between on-premises file systems and Azure Blob storage. The application stores keys, secrets, and certificates in Azure Key Vault. The application uses the Azure Key Vault APIs.
The application must allow recovery of an accidental deletion of the key vault or key vault objects. Key vault objects must be retained for 90 days after deletion.
You need to protect the key vault and key vault objects.
Which Azure Key Vault feature should you use? To answer, drag the appropriate features to the correct actions. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

AZ-204 Developing Solutions for Microsoft Azure Part 06 Q10 179 
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q10 180 Explanation:Box 1: Soft delete
When soft-delete is enabled, resources marked as deleted resources are retained for a specified period (90 days by default). The service further provides a mechanism for recovering the deleted object, essentially undoing the deletion.Box 2: Purge protection
Purge protection is an optional Key Vault behavior and is not enabled by default. Purge protection can only be enabled once soft-delete is enabled.When purge protection is on, a vault or an object in the deleted state cannot be purged until the retention period has passed. Soft-deleted vaults and objects can still be recovered, ensuring that the retention policy will be followed.
-
You provide an Azure API Management managed web service to clients. The back-end web service implements HTTP Strict Transport Security (HSTS).
Every request to the backend service must include a valid HTTP authorization header.
You need to configure the Azure API Management instance with an authentication policy.
Which two policies can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Basic Authentication
- Digest Authentication
- Certificate Authentication
- OAuth Client Credential Grant
-
DRAG DROP
You are developing an ASP.NET Core website that can be used to manage photographs which are stored in Azure Blob Storage containers.
Users of the website authenticate by using their Azure Active Directory (Azure AD) credentials.
You implement role-based access control (RBAC) role permissions on the containers that store photographs. You assign users to RBAC roles.
You need to configure the website’s Azure AD Application so that user’s permissions can be used with the Azure Blob containers.
How should you configure the application? To answer, drag the appropriate setting to the correct location. Each setting can be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q12 181 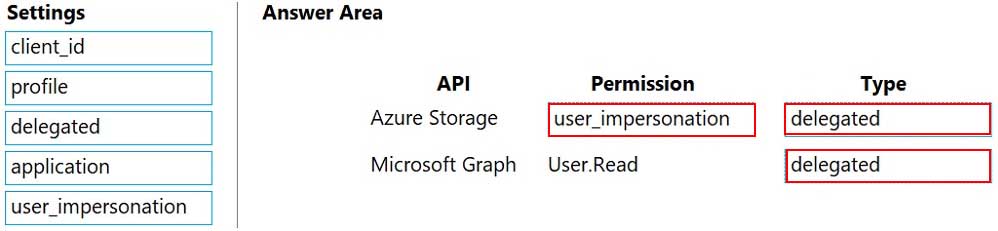
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q12 182 Explanation:Box 1: user_impersonation
Box 2: delegated
Example:
1. Select the API permissions section
2. Click the Add a permission button and then:
Ensure that the My APIs tab is selected
3. In the list of APIs, select the API TodoListService-aspnetcore.
4. In the Delegated permissions section, ensure that the right permissions are checked: user_impersonation.
5. Select the Add permissions button.Box 3: delegated
Example
1. Select the API permissions section
2. Click the Add a permission button and then,
Ensure that the Microsoft APIs tab is selected
3. In the Commonly used Microsoft APIs section, click on Microsoft Graph
4. In the Delegated permissions section, ensure that the right permissions are checked: User.Read. Use the search box if necessary.
5. Select the Add permissions button -
HOTSPOT
You are developing an ASP.NET Core app that includes feature flags which are managed by Azure App Configuration. You create an Azure App Configuration store named AppFeatureFlagStore that contains a feature flag named Export.
You need to update the app to meet the following requirements:
Use the Export feature in the app without requiring a restart of the app.
Validate users before users are allowed access to secure resources.
Permit users to access secure resources.How should you complete the code segment? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-204 Developing Solutions for Microsoft Azure Part 06 Q13 183 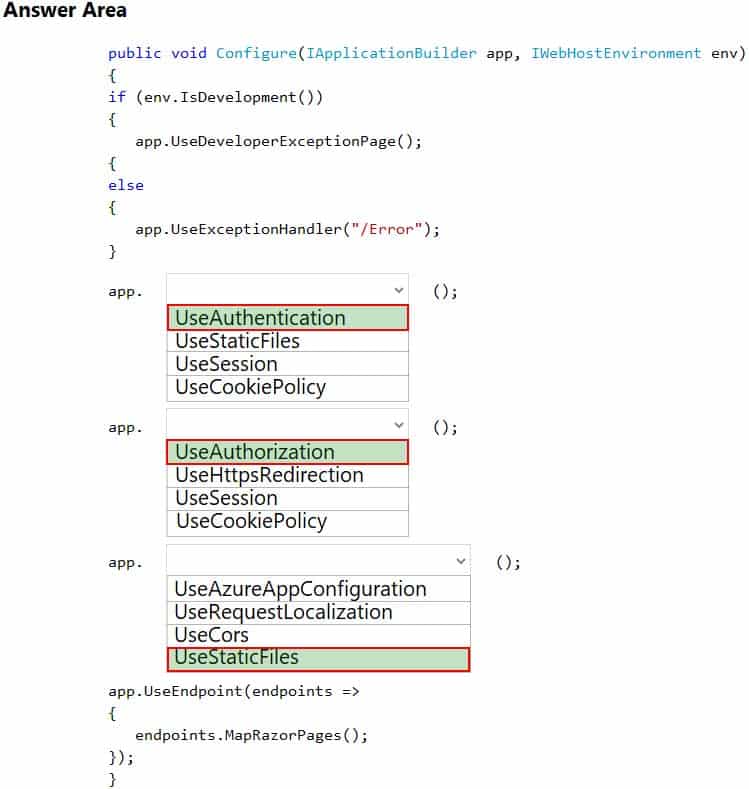
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q13 184 Explanation:Box 1: UseAuthentication
Need to validate users before users are allowed access to secure resources.UseAuthentication adds the AuthenticationMiddleware to the specified IApplicationBuilder, which enables authentication capabilities.
Box 2: UseAuthorization
Need to permit users to access secure resources.
UseAuthorization adds the AuthorizationMiddleware to the specified IApplicationBuilder, which enables authorization capabilities.Box 3: UseStaticFiles
Need to use the Export feature in the app without requiring a restart of the app.UseStaticFiles enables static file serving for the current request path
-
You have an application that includes an Azure Web app and several Azure Function apps. Application secrets including connection strings and certificates are stored in Azure Key Vault.
Secrets must not be stored in the application or application runtime environment. Changes to Azure Active Directory (Azure AD) must be minimized.
You need to design the approach to loading application secrets.
What should you do?
- Create a single user-assigned Managed Identity with permission to access Key Vault and configure each App Service to use that Managed Identity.
- Create a single Azure AD Service Principal with permission to access Key Vault and use a client secret from within the App Services to access Key Vault.
- Create a system assigned Managed Identity in each App Service with permission to access Key Vault.
- Create an Azure AD Service Principal with Permissions to access Key Vault for each App Service and use a certificate from within the App Services to access Key Vault.
Explanation:Use Key Vault references for App Service and Azure Functions.
Key Vault references currently only support system-assigned managed identities. User-assigned identities cannot be used. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are developing a medical records document management website. The website is used to store scanned copies of patient intake forms.
If the stored intake forms are downloaded from storage by a third party, the contents of the forms must not be compromised.
You need to store the intake forms according to the requirements.
Solution:
1.Create an Azure Key Vault key named skey.
2.Encrypt the intake forms using the public key portion of skey.
3.Store the encrypted data in Azure Blob storage.Does the solution meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are developing a medical records document management website. The website is used to store scanned copies of patient intake forms.
If the stored intake forms are downloaded from storage by a third party, the contents of the forms must not be compromised.
You need to store the intake forms according to the requirements.
Solution:
1.Create an Azure Cosmos DB database with Storage Service Encryption enabled.
2.Store the intake forms in the Azure Cosmos DB database.Does the solution meet the goal?
- Yes
- No
Explanation:
Instead use an Azure Key vault and public key encryption. Store the encrypted from in Azure Storage Blob storage. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are developing a medical records document management website. The website is used to store scanned copies of patient intake forms.
If the stored intake forms are downloaded from storage by a third party, the contents of the forms must not be compromised.
You need to store the intake forms according to the requirements.
Solution: Store the intake forms as Azure Key Vault secrets.
Does the solution meet the goal?
- Yes
- No
Explanation:
Instead use an Azure Key vault and public key encryption. Store the encrypted from in Azure Storage Blob storage. -
HOTSPOT
You plan to deploy a new application to a Linux virtual machine (VM) that is hosted in Azure.
The entire VM must be secured at rest by using industry-standard encryption technology to address organizational security and compliance requirements.
You need to configure Azure Disk Encryption for the VM.
How should you complete the Azure CLI commands? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
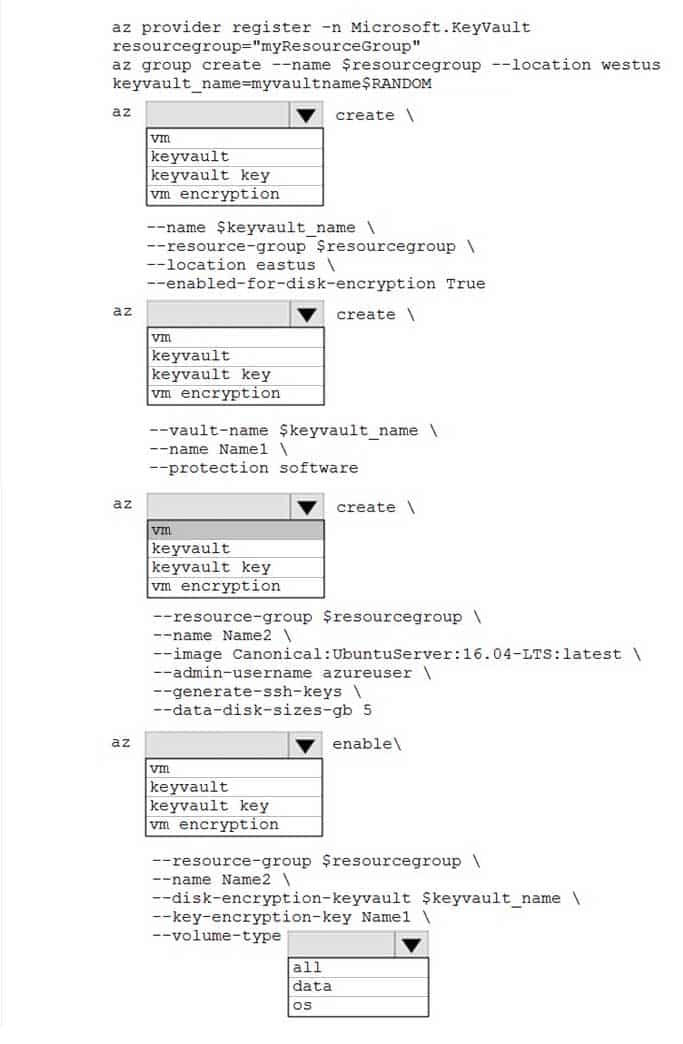
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q18 185 
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q18 186 -
Your company is developing an Azure API hosted in Azure.
You need to implement authentication for the Azure API to access other Azure resources. You have the following requirements:
All API calls must be authenticated.
Callers to the API must not send credentials to the API.Which authentication mechanism should you use?
- Basic
- Anonymous
- Managed identity
- Client certificate
Explanation:Azure Active Directory Managed Service Identity (MSI) gives your code an automatically managed identity for authenticating to Azure services, so that you can keep credentials out of your code.
Note: Use the authentication-managed-identity policy to authenticate with a backend service using the managed identity. This policy essentially uses the managed identity to obtain an access token from Azure Active Directory for accessing the specified resource. After successfully obtaining the token, the policy will set the value of the token in the Authorization header using the Bearer scheme.
Incorrect Answers:
A: Use the authentication-basic policy to authenticate with a backend service using Basic authentication. This policy effectively sets the HTTP Authorization header to the value corresponding to the credentials provided in the policy.
B: Anonymous is no authentication at all.
D: Your code needs credentials to authenticate to cloud services, but you want to limit the visibility of those credentials as much as possible. Ideally, they never appear on a developer’s workstation or get checked-in to source control. Azure Key Vault can store credentials securely so they aren’t in your code, but to retrieve them you need to authenticate to Azure Key Vault. To authenticate to Key Vault, you need a credential! A classic bootstrap problem. -
DRAG DROP
You are developing an application. You have an Azure user account that has access to two subscriptions.
You need to retrieve a storage account key secret from Azure Key Vault.
In which order should you arrange the PowerShell commands to develop the solution? To answer, move all commands from the list of commands to the answer area and arrange them in the correct order.

AZ-204 Developing Solutions for Microsoft Azure Part 06 Q20 187 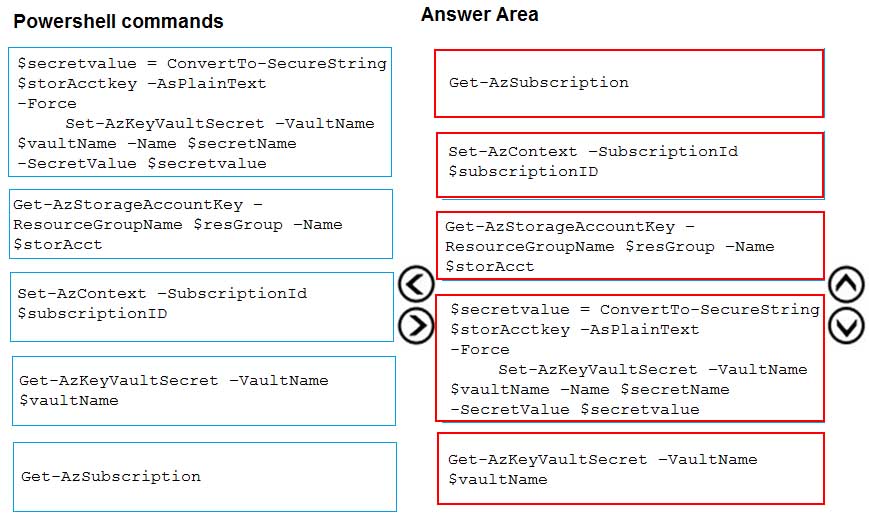
AZ-204 Developing Solutions for Microsoft Azure Part 06 Q20 188 Explanation:Step 1: Get-AzSubscription
If you have multiple subscriptions, you might have to specify the one that was used to create your key vault. Enter the following to see the subscriptions for your account:
Get-AzSubscriptionStep 2: Set-AzContext -SubscriptionId
To specify the subscription that’s associated with the key vault you’ll be logging, enter:
Set-AzContext -SubscriptionId <subscriptionID>Step 3: Get-AzStorageAccountKey
You must get that storage account key.Step 4: $secretvalue = ConvertTo-SecureString <storageAccountKey> -AsPlainText -Force
Set-AzKeyVaultSecret -VaultName <vaultName> -Name <secretName> -SecretValue $secretvalueAfter retrieving your secret (in this case, your storage account key), you must convert that key to a secure string, and then create a secret with that value in your key vault.
Step 5: Get-AzKeyVaultSecret
Next, get the URI for the secret you created. You’ll need this URI in a later step to call the key vault and retrieve your secret. Run the following PowerShell command and make note of the ID value, which is the secret’s URI:
Get-AzKeyVaultSecret –VaultName <vaultName>