AZ-220 : Microsoft Azure IoT Developer : Part 04
AZ-220 : Microsoft Azure IoT Developer : Part 04
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
ADatum Corporation is an international manufacturing company that has 3,000 employees.ADatum has a main office in New York and more than 100 branch offices worldwide.
Requirements. Planned Changes
ADatum is developing an Azure IoT solution to monitor environmental conditions. The IoT solution consists of hardware devices and cloud services. All the devices will communicate directly to Azure IoT Hub.The hardware devices will be deployed to the branch offices and will collect data about various environmental conditions such as temperature, humidity, air quality, and noise level. The devices will be wired by using Power over Ethernet (PoE) connections.
ADatum is developing the solution in the following three phases: proof of value (POV), pilot, and production.
Requirements. POV Requirements
The POV phase will demonstrate that a technical solution is viable. During this phase, 100 devices will be deployed to the main office and Azure Stream Analytics will be connected to an IoT hub to generate real-time alerts. Stream Analytics will perform the following processing:– Calculate the median rate of the telemetry across the entire device fleet and issue alerts for devices that exceed the median rate by a factor of 4.
– Compare the current telemetry to the specified thresholds and issue alerts when telemetry values are out of range.
– Ensure that all message content during this phase is human readable to simplify debugging.Requirements. Pilot Requirements
During the pilot phase, devices will be deployed to 10 offices. Each office will have up to 1,000 devices.During this phase, you will add Azure Time Series Insights in parallel to Stream Analytics to support real-time graphs and queries in a dashboard web app.
The pilot deployment must minimize operating costs.
Requirements. Production Requirements
The production phase will include all the offices.The production deployment will have one IoT hub in each Azure region. Devices must connect to the IoT hub in their region.
The production phase must meet the following requirements:
– Ensure that the IoT solution can support performance and scale targets.
– Ensure that the IoT solution supports up to 1,000 devices per office.
– Minimize operating costs of the IoT solution.Requirements. Technical Requirements
Datum identifies the following requirements for the planned IoT solution:– The solution must generate real-time alerts when a fire condition is detected in an office. All the devices in that office must trigger an audible alarm siren within 10 seconds of the alert.
– A dashboard UI must display alerts and the system status in real time and must allow device operators to make adjustments to the system.
– Each device will send hourly updates to IoT Hub. Condition alerts will be sent immediately.
– Multiple types of devices will collect telemetry that has different schemas.
– IoT Hub must perform message routing based on the message body.
– Direct methods must be used for cloud-to-device communication.
– Reports must be provided monthly, quarterly, and annually.
– Stored data queries must be as efficient as possible.
– The device message size will be under 4 KB.
– Development effort must be minimized.Requirements. Throttle and Quotas
The relevant throttles and quotas for various IoT Hub tiers are shown in the following table.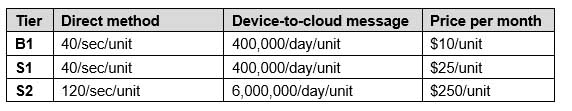
AZ-220 Microsoft Azure IoT Developer Part 04 Q01 042 Requirements. IoT Hub Routing
You plan to implement IoT Hub routing during the POV phase as shown in the following exhibit.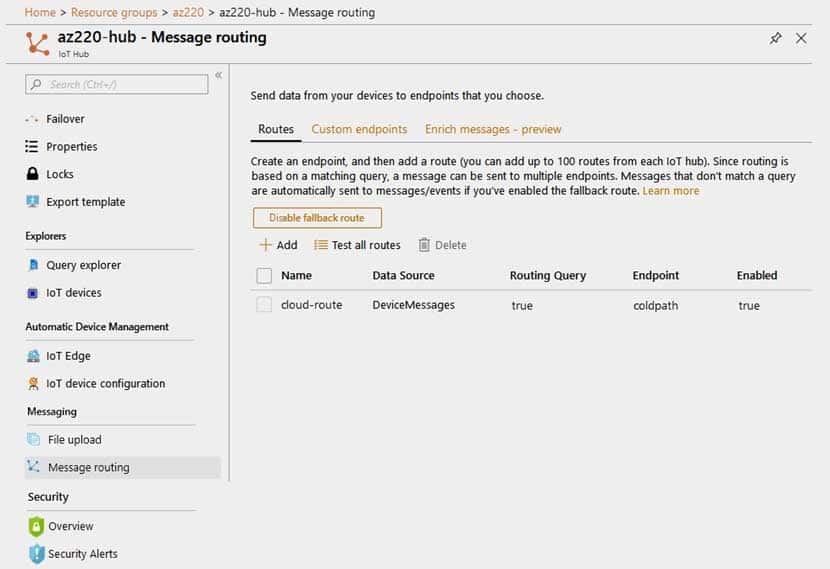
AZ-220 Microsoft Azure IoT Developer Part 04 Q01 043 -
During the POV phase, you connect a device to IoT Hub and start sending telemetry messages.
You need to verify the content of the messages received by IoT Hub during the POV phase.
What should you use?
- the Monitoring settings of IoT Hub or a Postman call to the IoT Hub REST API
- Azure Monitor or Azure Log Analytics
- Microsoft Visual Studio Code that uses the IoT Hub Toolkit or Azure CLI that uses the IoT Hub extension
- Splunk or Grafana
-
-
You have 10 IoT devices that connect to an Azure IoT hub named Hub1.
From Azure Cloud Shell, you run az iot hub monitor-events –hub-name Hub1 and receive the following error message: “az iot hub: ‘monitor-events’ is not in the ‘az iot hub’ command group. See ‘az iot hub –help’.”
You need to ensure that you can run the command successfully.
What should you run first?
-
az iot hub monitor-feedback --hub-name Hub1
-
az iot hub generate-sas-token --hub-name Hub1
-
az iot hub configuration list --hub-name Hub1
-
az extension add -name azure-cli-iot-ext
Explanation:Execute az extension add –name azure-cli-iot-ext once and try again.
In order to read the telemetry from your hub by CLI, you have to enable IoT Extension with the following commands:
Add: az extension add –name azure-cli-iot-ext -
-
You have an Azure Stream Analytics job that connects to an Azure IoT hub named Hub1445 as a streaming data source. Hub1445 is configured as shown in the exhibit.
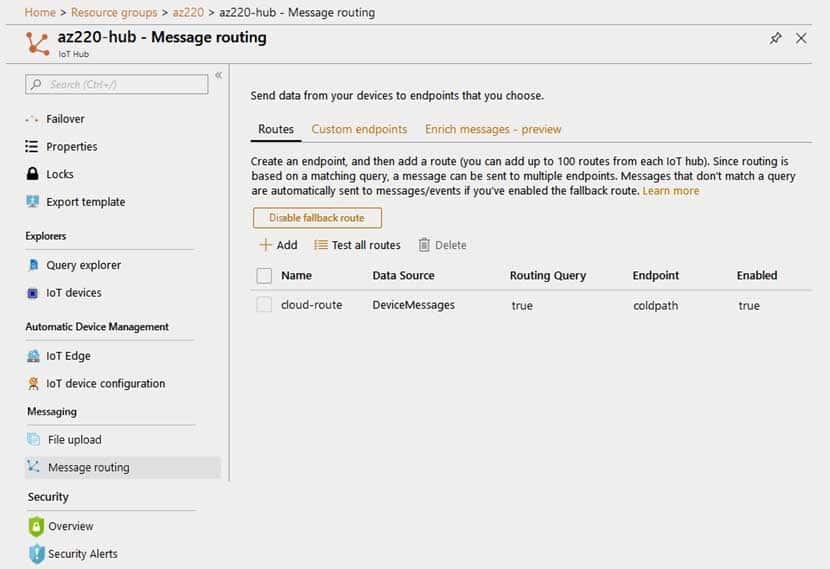
AZ-220 Microsoft Azure IoT Developer Part 04 Q03 043 The Stream Analytics job fails to receive any messages from the IoT hub.
What should you do to resolve the issue?
- Change the Route1 route query to true.
- Enable the Route3 route.
- Disable the Route2 route.
- Enable the fallback route.
Explanation:Events are not getting through as Route3, with an events Endpoint, is not enabled.
Note: Azure IoT Hub is a highly scalable publish-subscribe event ingestor optimized for IoT scenarios.
The default timestamp of events coming from an IoT Hub in Stream Analytics is the timestamp that the event arrived in the IoT Hub, which is EventEnqueuedUtcTime.
-
You are troubleshooting an Azure IoT hub.
You discover that some telemetry messages are dropped before they reach downstream processing.
You suspect that IoT Hub throttling is the root cause.
Which log in the Diagnostics settings of the IoT hub should you use to capture the throttling error events?
- Routes
- DeviceTelemetry
- Connections
- C2DCommands
Explanation:The device telemetry category tracks errors that occur at the IoT hub and are related to the telemetry pipeline. This category includes errors that occur when sending telemetry events (such as throttling) and receiving telemetry events (such as unauthorized reader). This category cannot catch errors caused by code running on the device itself.
Note: The metric d2c.telemetry.ingress.sendThrottle is the number of throttling errors due to device throughput throttles.
-
You have 20 devices that connect to an Azure IoT hub.
You open Azure Monitor as shown in the exhibit.
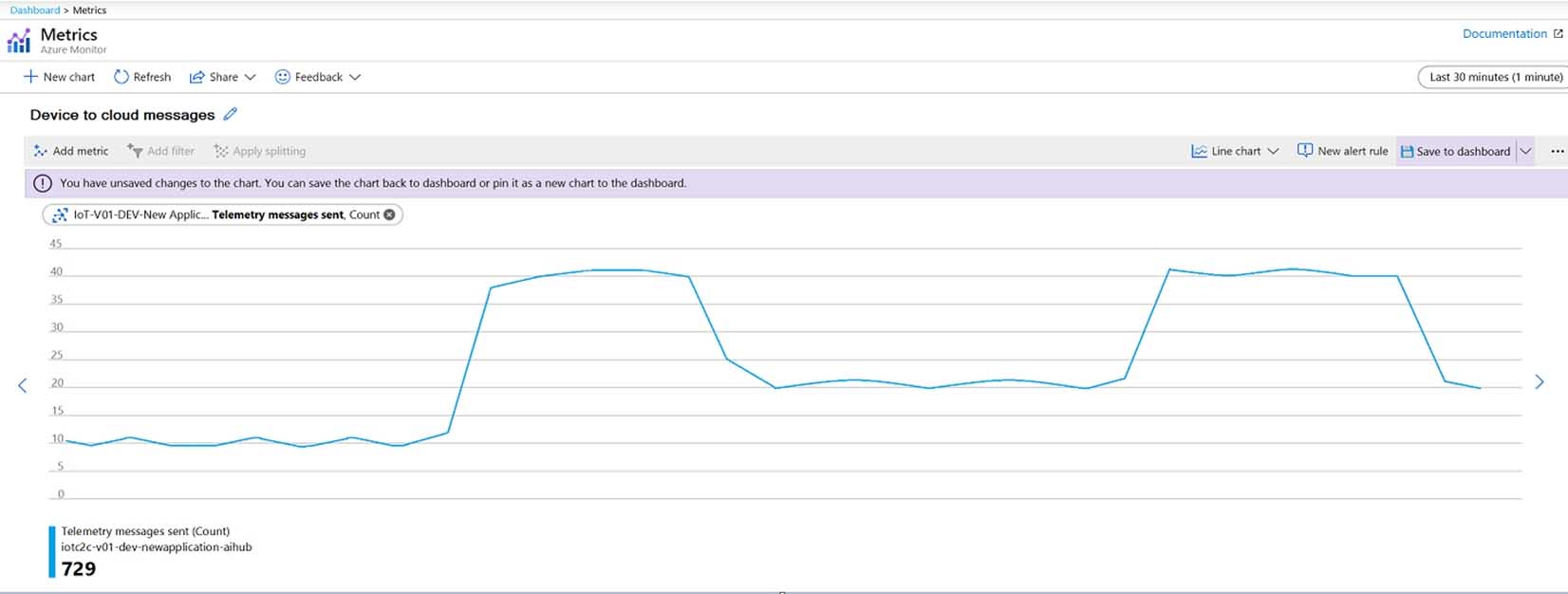
AZ-220 Microsoft Azure IoT Developer Part 04 Q05 044 You discover that telemetry is not being received from five IoT devices.
You need to identify the names of the devices that are not generating telemetry and visualize the data.
What should you do first?
- Add the Number of throttling errors metric and archive the logs to an Azure storage account.
- Configure diagnostics for Routes and stream the logs to Azure Event Hubs.
- Add the Telemetry messages sent metric and archive the logs to an Azure Storage account.
- Configure diagnostics for Connections and send the logs to Azure Log Analytics.
Explanation:To log device connection events and errors, turn on diagnostics for IoT Hub. We recommend turning on these logs as early as possible, because if diagnostic logs aren’t enabled, when device disconnects occur, you won’t have any information to troubleshoot the problem with.
1. Sign in to the Azure portal.
2. Browse to your IoT hub.
3. Select Diagnostics settings.
4. Select Turn on diagnostics.
5. Enable Connections logs to be collected.
For easier analysis, turn on Send to Log Analytics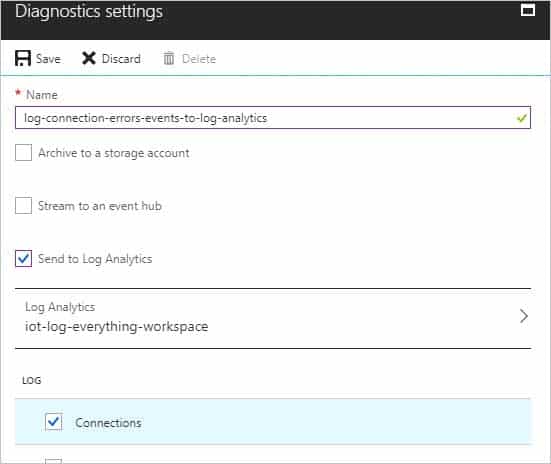
AZ-220 Microsoft Azure IoT Developer Part 04 Q05 045 
AZ-220 Microsoft Azure IoT Developer Part 04 Q05 046 -
You have an Azure IoT solution that includes a standard tier Azure IoT hub and an IoT device.
The device sends one 100-KB device-to-cloud message every hour.
You need to calculate the total daily message consumption of the device.
What is the total daily message consumption of the device?
- 24
- 600
- 2,400
- 4.800
Explanation:100 KB * 24 is around 2,400 bytes.
The 100 KB message is divided into 4 KB blocks, and it is billed for 25 messages. 25 times 24 is 600Note: The maximum message size for messages sent from a device to the cloud is 256 KB. These messages are metered in 4 KB blocks for the paid tiers so for instance if the device sends a 16 KB message via the paid tiers it will be billed as 4 messages.
-
You have 1,000 devices that connect to an Azure IoT hub.
You are performing a scheduled check of deployed IoT devices.
You plan to run the following command from the Azure CLI prompt.
az iot hub query --hub-name hub1 --query-command "SELECT * FROM devices WHERE connectionState = 'Disconnected'"
What does the command return?
- the Device Disconnected events
- the device twins
- the Connections logs
- the device credentials
Explanation:
Device twin queries: IoT Hub exposes the device twins as a document collection called devices. For example, the following query retrieves the whole set of device twins:
SELECT * FROM devices -
You have an Azure IoT solution that includes several Azure IoT hubs.
A new alerting feature was recently added to the IoT devices. The feature uses a new device twin reported property named alertCondition.
You need to send alerts to an Azure Service Bus queue named MessageAlerts. The alerts must include alertCondition and the name of the IoT hub.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Configure File upload for each IoT hub. Configure the device to send a file to an Azure Storage container that contains the device name and status message.
- Add the following message enrichments:
Name = iotHubName Value = $twin.tag.location Endpoint = MessageAlerts
- Create an IoT Hub routing rule that has a data source of Device Twin Change Events and select the endpoint for MessageAlerts.
- Add the following message enrichments:
Name = iotHubName
Value = $iothubname
Endpoint = MessageAlerts - Create an IoT Hub routing rule that has a data source of Device Telemetry Messages and select the endpoint for MessageAlerts.
Explanation:C: Device twins change notifications allow back end applications to be notified in real-time of twin changes and react as business logic requires. For instance, when building an application that notifies an operator directly that a device has a firmware update pending and is “ready to update”. This is accomplished by creating a routing rule from the “Twin Change Events” source and filtering all events that involve the software update status.
D: Applying enrichments
The messages can come from any data source supported by IoT Hub message routing, including the following examples:
– –>device twin change notifications — changes in the device twin
– device telemetry, such as temperature or pressure
– device life-cycle events, such as when the device is created or deleted -
DRAG DROP
You have 100 devices that connect to an Azure IoT hub.
You need to be notified about failed local logins to a subset of the devices.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

AZ-220 Microsoft Azure IoT Developer Part 04 Q09 047 Question 
AZ-220 Microsoft Azure IoT Developer Part 04 Q09 047 Answer Explanation:Step 1: Enable Azure Security Center for IoT
Security alerts, such as failed local IoT hub logins, are stored in AzureSecurityOfThings.SecurityAlert table in the Log Analytics workspace configured for the Azure Security Center for IoT solution.Step 2: Select a device security group
Update a device security group..Step 3: Create a custom alert rule
..by creating a custom alert rule -
You have an Azure IoT solution that includes a basic tier Azure IoT hub named Hub1 and a Raspberry Pi device named Device1. Device1 connects to Hub1.
You back up Device1 and restore the backup to a new Raspberry Pi device.
When you start the new Raspberry Pi device, you receive the following error message in the diagnostic logs of Hub1: “409002 LinkCreationConflict.”
You need to ensure that Device1 and the new Raspberry Pi device can run simultaneously without error.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- On the new Raspberry Pi device, modify the connection string.
- From Hub1, modify the device shared access policy.
- Upgrade Hub1 to the standard tier.
- From Hub1, create a new consumer group.
- From Hub1, create a new IoT device.
Explanation:Note: Symptoms
You see the error 409002 LinkCreationConflict in logs along with device disconnection or cloud-to-device message failure.Cause
Generally, this error happens when IoT Hub detects a client has more than one connection. In fact, when a new connection request arrives for a device with an existing connection, IoT Hub closes the existing connection with this error. -
You have 1,000 devices that connect to an Azure IoT hub.
You discover that some of the devices fail to send data to the IoT hub.
You need to ensure that you can use Azure Monitor to troubleshoot the device connectivity issues.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- From the Diagnostics settings of the IoT hub, select Archive to a storage account.
- Collect the DeviceTelemetry, Connections, and Routes logs.
- Collect all metrics.
- From the Diagnostics settings of the IoT hub, select Send to Log Analytic.
- Collect the JobsOperations, DeviceStreams, and FileUploadOperations logs.
Explanation:The IoT Hub resource logs connections category emits operations and errors having to do with device connections. The following screenshot shows a diagnostic setting to route these logs to a Log Analytics workspace:

AZ-220 Microsoft Azure IoT Developer Part 04 Q11 048 Note: Azure Monitor: Route connection events to logs:
IoT hub continuously emits resource logs for several categories of operations. To collect this log data, though, you need to create a diagnostic setting to route it to a destination where it can be analyzed or archived. One such destination is Azure Monitor Logs via a Log Analytics workspace, where you can analyze the data using Kusto queries. -
You have an Azure IoT solution that includes an Azure IoT hub.
You plan to deploy 10,000 IoT devices.
You need to validate the performance of the IoT solution while 10,000 concurrently connected devices stream telemetry. The solution must minimize effort.
What should you deploy?
- an Azure IoT Device Simulation from Azure IoT Solution Accelerator
- an Azure function, an IoT Hub device SDK, and a timer trigger
- Azure IoT Central application and a template for the retail industry
- an Azure IoT Edge gateway configured as a protocol translation gateway
Explanation:
The IoT solution accelerators are complete, ready-to-deploy IoT solutions that implement common IoT scenarios. The scenarios include connected factory and device simulation.Use the Device Simulation solution accelerator to run simulated devices that generate realistic telemetry. You can use this solution accelerator to test the behavior of the other solution accelerators or to test your own custom IoT solutions.
-
You have an Azure IoT Central application that monitors 100 IoT devices.
You need to generate alerts when the temperature of a device exceeds 100 degrees. The solution must meet the following requirements:
– Minimize costs
– Minimize deployment timeWhat should you do?
- Perform a data export to Azure Service Bus.
- Create an email property in the device templates.
- Perform a data export to Azure Blob storage and create an Azure function.
- Create a rule that uses an email action.
Explanation:
You can create rules in IoT Central that trigger actions, such as sending an email, in response to telemetry-based conditions, such as device temperature exceeding a threshold. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have 20 IoT devices deployed across two floors of a building. The devices on the first floor must be set to 60 degrees. The devices on the second floor must be set to 80 degrees.
The device twins are configured to use a tag that identifies the floor on which the twins are located.
You create the following automatic configuration for the devices on the first floor.

AZ-220 Microsoft Azure IoT Developer Part 04 Q14 049 You create the following automatic configuration for the devices on the second floor.
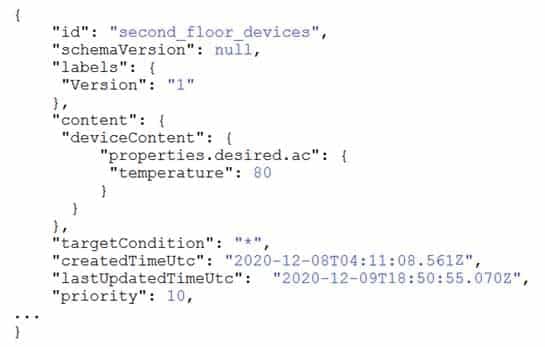
AZ-220 Microsoft Azure IoT Developer Part 04 Q14 050 The IoT devices on the first floor report that the temperature is set to 80 degrees.
You need to ensure that the first-floor devices are set to the correct temperature.
Solution: In the automatic configuration for the second-floor devices, you set targetCondition to “tags.floor=’second'”.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have 20 IoT devices deployed across two floors of a building. The devices on the first floor must be set to 60 degrees. The devices on the second floor must be set to 80 degrees.
The device twins are configured to use a tag that identifies the floor on which the twins are located.
You create the following automatic configuration for the devices on the first floor.

AZ-220 Microsoft Azure IoT Developer Part 04 Q15 051 You create the following automatic configuration for the devices on the second floor.

AZ-220 Microsoft Azure IoT Developer Part 04 Q15 052 The IoT devices on the first floor report that the temperature is set to 80 degrees.
You need to ensure that the first-floor devices are set to the correct temperature.
Solution: In the automatic configuration for the second-floor devices, you set Version to 2.
Does this meet the goal?
- Yes
- No
-
You use Azure Security Center in an Azure IoT solution.
You need to exclude some security events. The solution must minimize development effort.
What should you do?
- Create an Azure function to filter security messages.
- Add a configuration to the code of the physical IoT device.
- Add configuration details to the device twin object.
- Create an azureiotsecurity module twin and add configuration details to the module twin object.
Explanation:Properties related to every Azure Security Center for IoT security agent are located in the agent configuration object, within the desired properties section, of the azureiotsecurity module.
To modify the configuration, create and modify this object inside the azureiotsecurity module twin identity.
Note: Azure Security Center for IoT’s security agent twin configuration object is a JSON format object. The configuration object is a set of controllable properties that you can define to control the behavior of the agent.
These configurations help you customize the agent for each scenario required. For example, automatically excluding some events, or keeping power consumption to a minimal level are possible by configuring these properties.
-
You have an Azure IoT hub that uses a Device Provisioning Service instance.
You have 1,000 legacy IoT devices that only support MAC address or serial number identities. The devices do NOT have a security feature that can be used to securely identify the device or a hardware security module (HSM).
You plan to deploy the devices to a secure environment.
You need to configure the Device Provisioning Service instance to ensure that all the devices are identified securely before they receive updates.
Which attestation mechanism should you choose?
- Trusted Platform Module (TPM) 1.2 attestation
- symmetric key attestation
- X.509 certificates
Explanation:
A common problem with many legacy devices is that they often have an identity that is composed of a single piece of information. This identity information is usually a MAC address or a serial number. Legacy devices may not have a certificate, TPM, or any other security feature that can be used to securely identify the device. The Device Provisioning Service for IoT hub includes symmetric key attestation. Symmetric key attestation can be used to identify a device based off information like the MAC address or a serial number. -
From the Device Provisioning Service, you create an enrollment as shown in the exhibit.
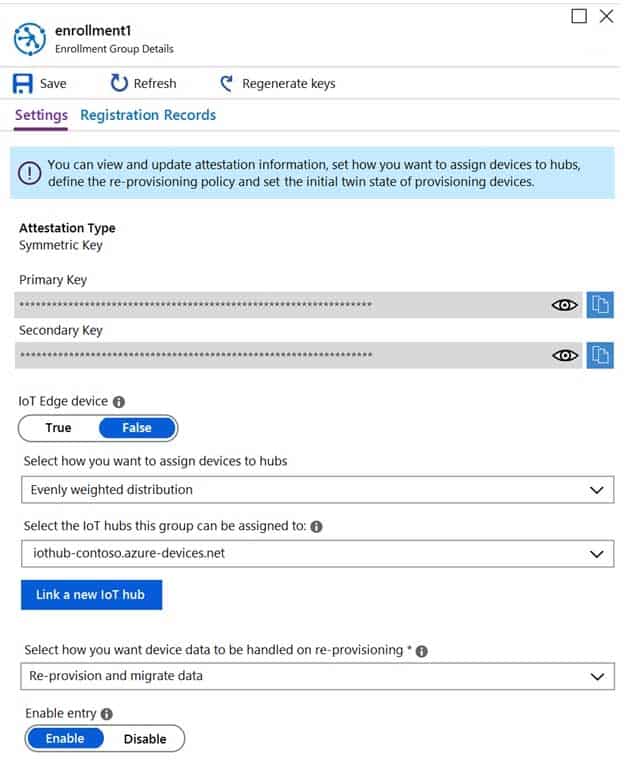
AZ-220 Microsoft Azure IoT Developer Part 04 Q18 053 You need to deploy a new IoT device.
What should you use as the device identity during attestation?
- a self-signed X.509 certificate
- the random string of alphanumeric characters
- the HMAC-SHA256 hash of the device’s registration ID
- the endorsement key of the device’s Trusted Platform Module (TPM)
Explanation:
Each device uses its derived device key with your unique registration ID to perform symmetric key attestation with the enrollment during provisioning. To generate the device key, use the key you copied from your DPS enrollment to compute an HMAC-SHA256 of the unique registration ID for the device and convert the result into Base64 format. -
DRAG DROP
You have an Azure IoT Edge solution.
You plan to deploy an Azure Security Center for IoT security agent. You need to configure the security agent to meet the following requirements:
– Connection events must be reported as high priority.
– High priority events must be collected every seven minutes.How should you configure the azureiotsecurity module twin? To answer, drag the appropriate values to the correct locations. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
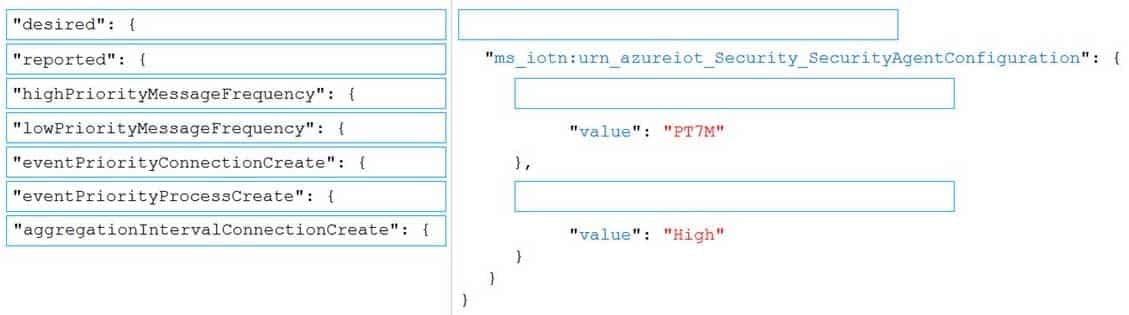
AZ-220 Microsoft Azure IoT Developer Part 04 Q19 054 Question 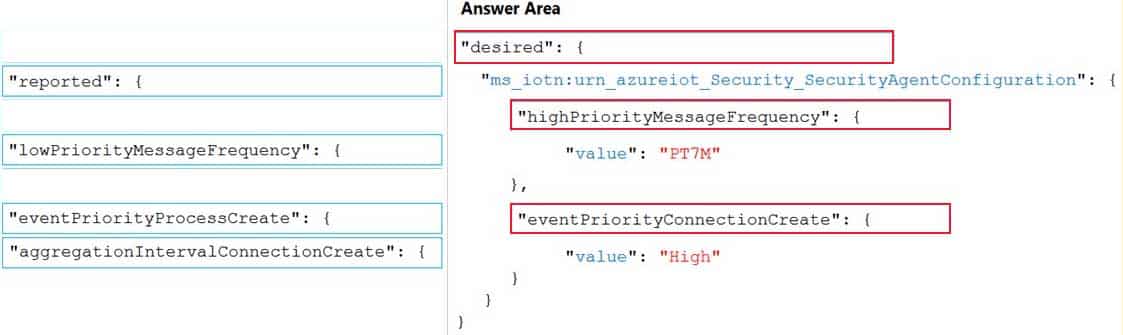
AZ-220 Microsoft Azure IoT Developer Part 04 Q19 054 Answer Explanation:Box 1: “desired”: {
To configure connection events as high priority and collect high priority events every 7 minutes, use the following configuration.
"desired": { "ms_iotn:urn_azureiot_Security_SecurityAgentConfiguration": { "highPriorityMessageFrequency": { "value": "PT7M" }, "eventPriorityConnectionCreate": { "value": "High" }Box 2: “highPriorityMessageFrequency “: {
Box 3: “eventPriorityConnectionCreate”: {
-
You have an Azure IoT hub that has a hostname of contoso-hub.azure-devices.net and an MCU-based IoT device named Device1. Device1 does NOT support Azure IoT SDKs.
You plan to connect Device1 to the IoT hub by using the Message Queuing Telemetry Transport (MQTT) protocol and to authenticate by using X.509 certificates.
You need to ensure that Device1 can authenticate to the IoT hub.
What should you do?
- Create an Azure key vault and enable the encryption of data at rest for the IoT hub by using a customer-managed key.
- Enable a hardware security module (HSM) on Device1.
- From the Azure portal, create an IoT Hub Device Provisioning Service (DPS) instance and add a certificate enrollment for Device1.
- Add the DigiCert Baltimore Root Certificate to Device1.
Explanation:
The connection to Azure IoT Hub with MQTT is secured using TLS.
The Azure IoT Hub library requires the provisioning of the following certificates and a private key for a successful TLS connection:
1. Baltimore CyberTrust Root certificate – Server certificate, used to verify the server’s certificate while connecting.
2. Device certificate – generated by the procedures described in Creating Azure IoT Hub certificates , used by Azure IoT Hub to authenticate the device.
3. Private key of the device. -
HOTSPOT
You are planning a proof of concept (POC) that will use an Azure IoT hub.
You have two self-signed client authentication certificates named Cert1 and Cert2. Cert1 has a basic constraint that contains Subject Type=CA. Cert2 has a basic constraint that contains Subject Type=End Entity.
You need to identify which certificates to use.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
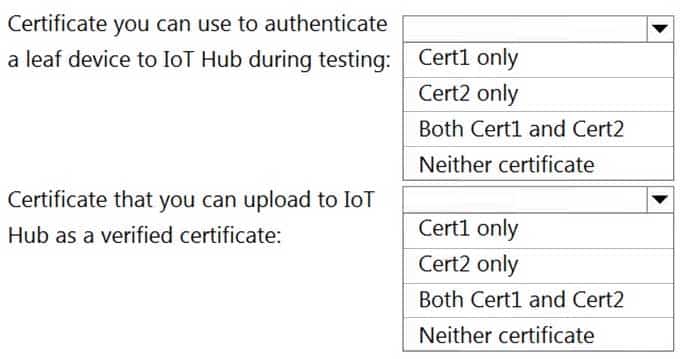
AZ-220 Microsoft Azure IoT Developer Part 04 Q21 055 Question 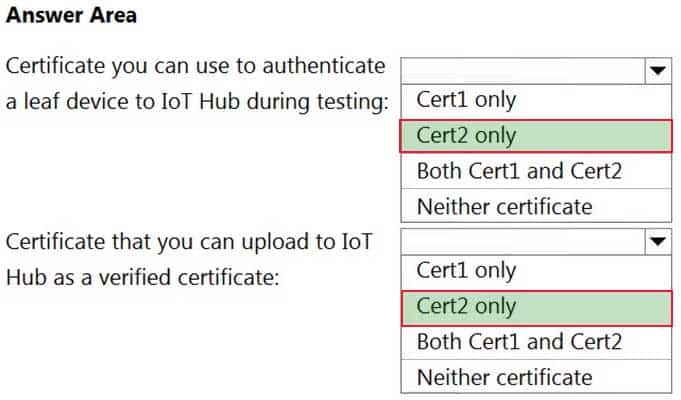
AZ-220 Microsoft Azure IoT Developer Part 04 Q21 055 Answer Explanation:Box 1: Cert2 only
Cert2: The leaf certificate, or end-entity certificate, identifies the certificate holder. It has the root certificate in its certificate chain as well as zero or more intermediate certificates. The leaf certificate is not used to sign any other certificates. It uniquely identifies the device to the provisioning service and is sometimes referred to as the device certificate.Box 2: Cert1 only
Cert1: A root certificate is a self-signed X.509 certificate representing a certificate authority (CA). It is the terminus, or trust anchor, of the certificate chain. Root certificates can be self-issued by an organization or purchased from a root certificate authority. -
You have an Azure IoT Edge device.
You need to modify the credentials used to access the container registry.
What should you modify?
- the $edgeHub module twin
- the IoT Edge module
- the $edgeAgent module twin
- the Azure IoT Hub device twin
Explanation:The module twin for the IoT Edge agent is called $edgeAgent and coordinates the communications between the IoT Edge agent running on a device and IoT Hub. The desired properties are set when applying a deployment manifest on a specific device as part of a single-device or at-scale deployment.
These properties include:
– runtime.settings.registryCredentials.{registryId}.username
– runtime.settings.registryCredentials.registryId}.password -
You enable Azure Security Center for IoT.
You need to onboard a device to Azure Security Center.
What should you do?
- Add the azureiotsecurity module identity to the Azure IoT Hub device identity.
- Open incoming TCP port 8883 on the device.
- Modify the connection string of the device.
- Install an X.509 certificate on the hardware security module (HSM) of the device.
Explanation:Use the following workflow to deploy and test your Azure Security Center for IoT security agents:
1. Enable Azure Security Center for IoT service to your IoT Hub
2. If your IoT Hub has no registered devices, Register a new device.
3. Create an azureiotsecurity security module for your devices.Azure Security Center for IoT makes use of the module twin mechanism and maintains a security module twin named azureiotsecurity for each of your devices.
Note: To manually create a new azureiotsecurity module twin for a device use the following instructions:
1. In your IoT Hub, locate and select the device you wish to create a security module twin for.
2. Click on your device, and then on Add module identity.
3. In the Module Identity Name field, enter azureiotsecurity.
4. Click Save. -
You have an Azure IoT solution that includes an Azure IoT hub, 100 Azure IoT Edge devices, and 500 leaf devices.
You need to perform a key rotation across the devices.
Which three types of entities should you update? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- the $edgeHub module identity
- the $edgeAgent module identity
- the leaf module identities
- the IoT Edge device identities
- the iothubowner policy credentials
- the leaf device identities
Explanation:To get authorization to connect to IoT Hub, devices and services must send security tokens signed with either a shared access or symmetric key. These keys are stored with a device identity in the identity registry.
An IoT Hub identity registry can be accessed like a dictionary, by using the deviceId or moduleId as the key.
-
You have an Azure IoT hub that is being taken from prototype to production.
You plan to connect IoT devices to the IoT hub. The devices have hardware security modules (HSMs).
You need to use the most secure authentication method between the devices and the IoT hub. Company policy prohibits the use of internally generated certificates.
Which authentication method should you use?
- an X.509 self-signed certificate
- a certificate thumbprint
- a symmetric key
- An X.509 certificate signed by a root certification authority (CA).
Explanation:Purchase X.509 certificates from a root certificate authority (CA). This method is recommended for production environments.
The hardware security module, or HSM, is used for secure, hardware-based storage of device secrets, and is the most secure form of secret storage. Both X.509 certificates and SAS tokens can be stored in the HSM
-
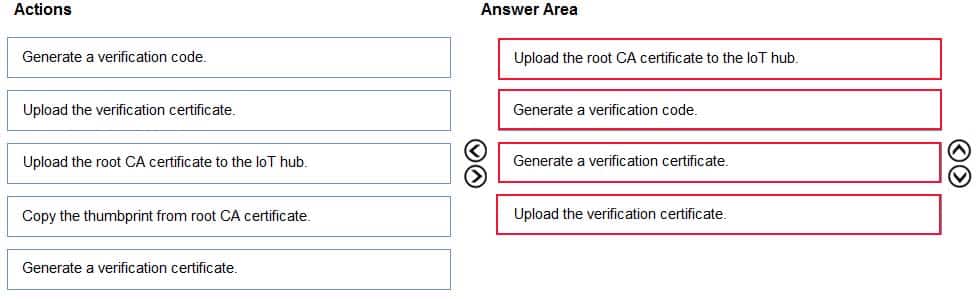
DRAG DROP
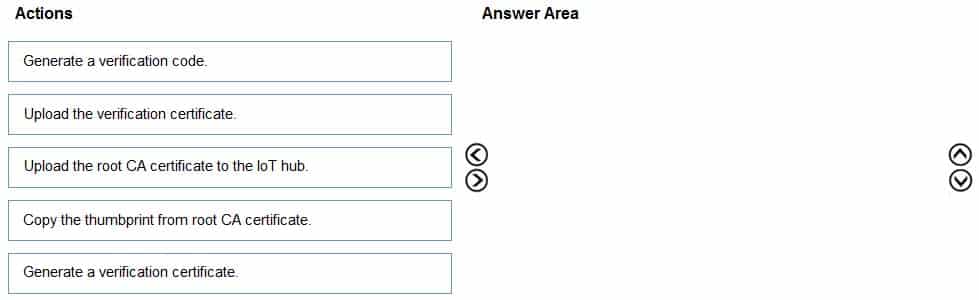
You have an Azure IoT solution that includes an Azure IoT hub.
You receive a root certification authority (CA) certificate from the security department at your company.
You need to configure the IoT hub to use the root CA certificate.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
AZ-220 Microsoft Azure IoT Developer Part 04 Q26 056 Question