AZ-303 : Microsoft Azure Architect Technologies : Part 06
AZ-303 : Microsoft Azure Architect Technologies : Part 06
-
A company hosts virtual machines (VMs) in an on-premises datacenter and in Azure. The on-premises and Azure-based VMs communicate using ExpressRoute.
The company wants to be able to continue regular operations if the ExpressRoute connection fails. Failover connections must use the Internet and must not require Multiprotocol Label Switching (MPLS) support.
You need to recommend a solution that provides continued operations.
What should you recommend?
- Increase the bandwidth of the existing ExpressRoute connection.
- Increase the bandwidth for the on-premises internet connection.
- Set up a VPN connection.
- Set up a second ExpressRoute connection.
-
You have an Azure subscription that contains the resources shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q02 121 Subnet1 is on VNET1. VM1 connects to Subnet1.
You plan to create a virtual network gateway on VNET1.
You need to prepare the environment for the planned virtual network gateway.
What should you do?
- Create a local network gateway.
- Modify the address space used by Subnet1.
- Create a subnet named GatewaySubnet on VNET1.
- Modify the address space used by VNET1.
- Delete Subnet1.
-
Your network contains an on-premises Active Directory and an Azure Active Directory (Azure AD) tenant.
You deploy Azure AD Connect and configure pass-through authentication.
Your Azure subscription contains several web apps that are accessed from the Internet.
You plan to use Azure Multi-Factor Authentication (MFA) with the Azure Active Directory tenant.
You need to recommend a solution to prevent users from being prompted for Azure MFA when they access the web apps from the on-premises network.
What should you include in the recommendation?
- an Azure policy
- trusted IPs
- a site-to-site VPN between the on-premises network and Azure
- an Azure ExpressRoute circuit
Explanation:
The Trusted IPs feature of Azure Multi-Factor Authentication is used by administrators of a managed or federated tenant. The feature bypasses two-step verification for users who sign in from the company intranet. The feature is available with the full version of Azure Multi-Factor Authentication, and not the free version for administrators. -
HOTSPOT
Your network contains an on-premises Active Directory domain named contoso.com that contains a user named User1. The domain syncs to Azure Active Directory (Azure AD).
You have the Windows 10 devices shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q04 122 The User Sign-In settings are configured as shown in the following exhibit.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q04 123 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q04 124 Question 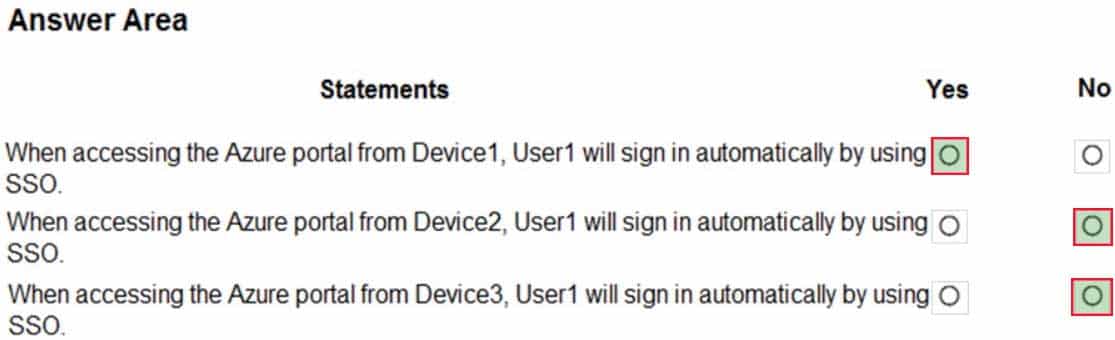
AZ-303 Microsoft Azure Architect Technologies Part 06 Q04 124 Answer Explanation:Box 1: Yes
Seamless SSO needs the user’s device to be domain-joined only, but it is not used on Azure AD Joined or Hybrid Azure AD joined devices. SSO on Azure AD joined, Hybrid Azure AD joined, and Azure AD registered devices works based on the primary refresh token.
Box 2: No
Box 3: No
-
You create a new Azure subscription. You create a resource group named RG1. In RG1, you create the resources shown in the following table.
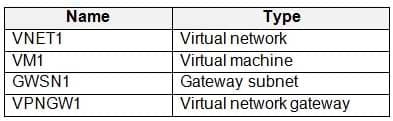
AZ-303 Microsoft Azure Architect Technologies Part 06 Q05 125 You need to configure an encrypted tunnel between your on-premises network and VNET1.
Which two additional resources should you create in Azure? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- a VPN gateway
- a site-to-site connection
- a point-to-site configuration
- a VNet-to-VNet connection
- a local network gateway
Explanation:A Site-to-Site VPN gateway connection is used to connect your on-premises network to an Azure virtual network over an IPsec/IKE (IKEv1 or IKEv2) VPN tunnel. This type of connection requires a VPN device, a local network gateway, located on-premises that has an externally facing public IP address assigned to it.
Finally, create a Site-to-Site VPN connection between your virtual network gateway and your on-premises VPN device.
-
You plan to create an Azure Storage account named storage1 that will store blobs and be accessed by Azure Databricks.
You need to ensure that you can set permissions for individual blobs by using Azure Active Directory (Azure AD) authentication.
Which Advanced setting should you enable for storage1?
- Large file shares
- Hierarchical namespace
- NFS v3
- Blob soft delete
Explanation:Question: Do I have to enable support for ACLs?
No. Access control via ACLs is enabled for a storage account as long as the Hierarchical Namespace (HNS) feature is turned ON.Note 1: We [Microsoft] are pleased to share the general availability of Azure Active Directory (AD) based access control for Azure Storage Blobs and Queues. Enterprises can now grant specific data access permissions to users and service identities from their Azure AD tenant using Azure’s Role-based access control (RBAC).
Note 2: Azure Data Lake Storage Gen2 implements an access control model that supports both Azure role-based access control (Azure RBAC) and POSIX-like access control lists (ACLs).
You can associate a security principal with an access level for files and directories. These associations are captured in an access control list (ACL). Each file and directory in your storage account has an access control list. When a security principal attempts an operation on a file or directory, An ACL check determines whether that security principal (user, group, service principal, or managed identity) has the correct permission level to perform the operation.
Incorrect Answers:
D: Blob soft delete protects your data from being accidentally or erroneously modified or deleted. When blob soft delete is enabled for a storage account, blobs, blob versions, and snapshots in that storage account may be recovered after they are deleted, within a retention period that you specify. -
HOTSPOT
You have an Azure subscription that includes an Azure key vault named Vault1.
You create the Azure virtual machines shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q07 126 You enable Azure Disk Encryption for all the virtual machines and use the –VolumeType All parameter.
You add data disks to the virtual machines as shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q07 127 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q07 128 Question 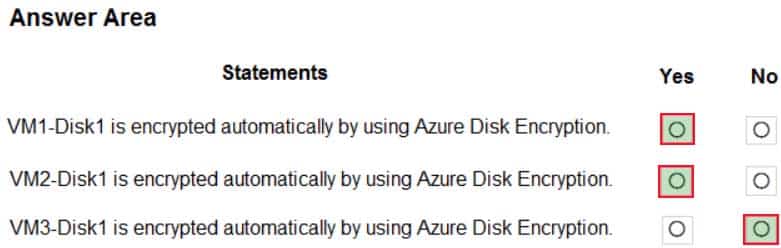
AZ-303 Microsoft Azure Architect Technologies Part 06 Q07 128 Answer Explanation:Premium and standard, but not basic, account types support disk encryption.
Disk encryption requires managed disks. -
You have the following Azure Active Directory (Azure AD) tenants:
Contoso.onmicrosoft.com: Linked to a Microsoft 365 tenant and syncs to an Active Directory forest named contoso.com by using password hash synchronization
– Contosoazure.onmicrosoft.com: Linked to an Azure subscription named Subscription1– You need to ensure that you can assign the users in contoso.com access to the resources in Subscription1.
What should you do?
- Associate Subscription1 to contoso.onmicrosoft.com. Reassign all the roles in Subscription1.
- Configure the existing Azure AD Connect server to sync contoso.com to contosoazure.onmicrosoft.com.
- Configure contoso.onmicrosoft.com to use pass-through authentication.
- Configure contosoazure.onmicrosoft.com to use pass-through authentication.
-
You have several Azure web apps that use access keys to access databases.
You plan to migrate the access keys to Azure Key Vault. Each app must authenticate by using Azure Active Directory (Azure AD) to gain access to the access keys.
What should you create in Azure to ensure that the apps can access the access keys?
- managed identities
- managed applications
- Azure policies
- an App Service plan
Explanation:
Azure Key Vault provides a way to securely store credentials and other secrets, but your code needs to authenticate to Key Vault to retrieve them. Managed identities for Azure resources overview helps to solve this problem by giving Azure services an automatically managed identity in Azure AD. You can use this identity to authenticate to any service that supports Azure AD authentication, including Key Vault, without having to display credentials in your code. -
You have an Azure key vault named KV1.
You need to implement a process that will digitally sign the blobs stored in Azure Storage.
What is required in KV1 to sign the blobs?
- a key
- a secret
- a certificate
Explanation:
Use an Azure key vault secret to key of your blob storage account container. -
You set the multi-factor authentication status for a user named admin1@contoso.com to Enabled.
Admin1 accesses the Azure portal by using a web browser.
Which additional security verifications can Admin1 use when accessing the Azure portal?
- a phone call, an email message that contains a verification code, and a text message that contains an app password.
- an app password, a text message that contains a verification code, and a verification code sent from the Microsoft Authenticator app.
- an app password, a text message that contains a verification code, and a notification sent from the Microsoft Authenticator app.
- a phone call, a text message that contains a verification code, and a notification or a verification code sent from the Microsoft Authenticator app.
Explanation:
The Microsoft Authenticator app can help prevent unauthorized access to accounts and stop fraudulent transactions by pushing a notification to your smartphone or tablet. Users view the notification, and if it’s legitimate, select Verify. Otherwise, they can select Deny. -
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant that contains the user groups shown in the following table.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q12 129 You enable self-service password reset (SSPR) for Group1.
You configure the Notifications settings as shown in the following exhibit.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q12 130 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q12 131 Question 
AZ-303 Microsoft Azure Architect Technologies Part 06 Q12 131 Answer Explanation:Box 1: Yes
Notify all admins when other admins reset their passwords: Yes.Box 2: No
Notify users on password resets: No.Box 3: No
– Notify users on password resets
If this option is set to Yes, then users resetting their password receive an email notifying them that their password has been changed. The email is sent via the SSPR portal to their primary and alternate email addresses that are on file in Azure AD. No one else is notified of the reset event.– Notify all admins when other admins reset their passwords
If this option is set to Yes, then all administrators receive an email to their primary email address on file in Azure AD. The email notifies them that another administrator has changed their password by using SSPR.Example: There are four administrators in an environment. Administrator A resets their password by using SSPR. Administrators B, C, and D receive an email alerting them of the password reset.
-
Your company has an Azure subscription.
You enable multi-factor authentication (MFA) for all users.
The company’s help desk reports an increase in calls from users who receive MFA requests while they work from the company’s main office.
You need to prevent the users from receiving MFA requests when they sign in from the main office.
What should you do?
- From Conditional access in Azure Active Directory (Azure AD), create a named location.
- From the MFA service settings, create a trusted IP range.
- From Conditional access in Azure Active Directory (Azure AD), create a custom control.
- From Azure Active Directory (Azure AD), configure organizational relationships.
Explanation:The first thing you may want to do, before enabling Multi-Factor Authentication for any users, is to consider configuring some of the available settings. One of the most important features is a trusted IPs list. This will allow you to whitelist a range of IPs for your network. This way, when users are in the office, they will not get prompted with MFA, and when they take their devices elsewhere, they will. Here’s how to do it:
Log in to your Azure Portal.
Navigate to Azure AD > Conditional Access > Named locations.
From the top toolbar select Configure MFA trusted IPs. -
HOTSPOT
You have an Azure logic app named App1 and an Azure Service Bus queue named Queue1.
You need to ensure that App1 can read messages from Queue1. App1 must authenticate by using Azure Active Directory (Azure AD).
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q14 132 Question 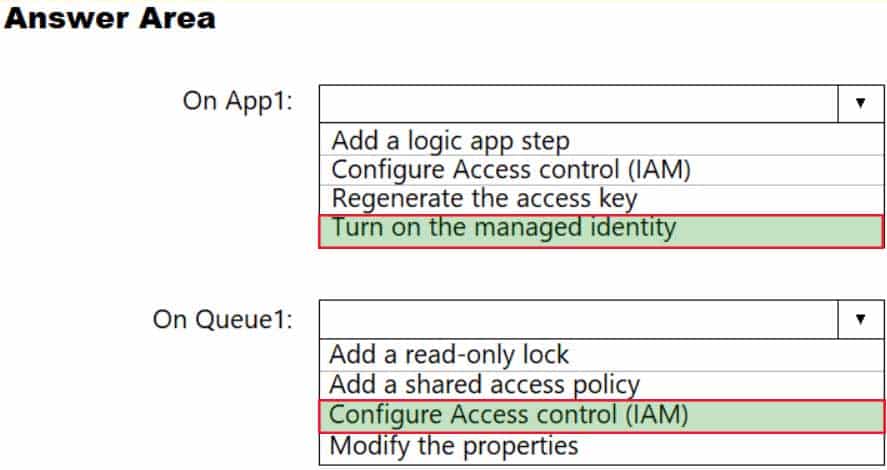
AZ-303 Microsoft Azure Architect Technologies Part 06 Q14 132 Answer Explanation:On App1: Turn on the managed identity
To use Service Bus with managed identities, you need to assign the identity the role and the appropriate scope. The procedure in this section uses a simple application that runs under a managed identity and accesses Service Bus resources.Once the application is created, follow these steps:
1. Go to Settings and select Identity.
2. Select the Status to be On.
3. Select Save to save the setting.On Queue1: Configure Access Control (IAM)
Azure Active Directory (Azure AD) authorizes access rights to secured resources through role-based access control (RBAC). Azure Service Bus defines a set of built-in RBAC roles that encompass common sets of permissions used to access Service Bus entities and you can also define custom roles for accessing the data.Assign RBAC roles using the Azure portal
In the Azure portal, navigate to your Service Bus namespace. Select Access Control (IAM) on the left menu to display access control settings for the namespace. If you need to create a Service Bus namespace.
Select the Role assignments tab to see the list of role assignments. Select the Add button on the toolbar and then select Add role assignment. -
You have the following Azure Active Directory (Azure AD) tenants:
– Contoso.onmicrosoft.com: Linked to a Microsoft 365 tenant and syncs to an Active Directory forest named contoso.com by using password hash synchronization
– Contosoazure.onmicrosoft.com: Linked to an Azure subscription named Subscription1You need to ensure that you can assign the users in contoso.com access to the resources in Subscription1.
What should you do?
- Create an Azure management group that contains Subscription1.
- Configure the existing Azure AD Connect server to sync contoso.com to contosoazure.onmicrosoft.com.
- Deploy a second Azure AD Connect server and sync contoso.com to contosoazure.onmicrosoft.com.
- Create guest accounts for all the contoso.com users in contosoazure.onmicrosoft.com.
Explanation:Azure AD Connect allows you to quickly onboard to Azure AD and Office 365.
In this topology, one Azure AD Connect sync server is connected to each Azure AD tenant. The Azure AD Connect sync servers must be configured for filtering so that each has a mutually exclusive set of objects to operate on. You can, for example, scope each server to a particular domain or organizational unit.
-
You have an application named App1 that does not support Azure Active Directory (Azure AD) authentication.
You need to ensure that App1 can send messages to an Azure Service Bus queue. The solution must prevent App1 from listening to the queue.
What should you do?
- Configure Access control (IAM) for the Service Bus.
- Add a shared access policy to the queue.
- Modify the locks of the queue.
- Configure Access control (IAM) for the queue.
Explanation:
There are two ways to authenticate and authorize access to Azure Service Bus resources: Azure Activity Directory (Azure AD) and Shared Access Signatures (SAS).
Each Service Bus namespace and each Service Bus entity has a Shared Access Authorization policy made up of rules. -
An administrator plans to create a function app in Azure that will have the following settings:
– Runtime stack: .NET Core
– Operating System: Linux
– Plan type: Consumption
– Enable Application Insights: YesYou need to ensure that you can back up the function app.
Which settings should you recommend changing before creating the function app?
- Runtime stack
- Disable Application Insights
- Operating System
- Plan type
Explanation:
The Backup and Restore feature requires the App Service plan to be in the Standard, Premium or Isolated tier. -
HOTSPOT
You have an Azure subscription.
You plan to deploy an app that has a web front end and an application tier.
You need to recommend a load balancing solution that meets the following requirements:
– Internet to web tier:
– Provides URL-based routing
– Supports connection draining
– Prevents SQL injection attacks– Web tier to application tier:
– Provides port forwarding
– Supports HTTPS health probes
– Supports an availability set as a backend poolYour solution must minimize costs.
Which load balancing solution should you recommend for each tier? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-303 Microsoft Azure Architect Technologies Part 06 Q18 133 Question 
AZ-303 Microsoft Azure Architect Technologies Part 06 Q18 133 Answer Explanation:Box 1: An Azure Application Gateway that has a web application firewall (WAF)
Azure Application Gateway offers a web application firewall (WAF) that provides centralized protection of your web applications from common exploits and vulnerabilities. Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities. SQL injection and cross-site scripting are among the most common attacks.Application Gateway operates as an application delivery controller (ADC). It offers Secure Sockets Layer (SSL) termination, cookie-based session affinity, round-robin load distribution, content-based routing, ability to host multiple websites, and security enhancements.
Box 2: An internal Azure Standard Load Balancer
The internet to web tier is the public interface, while the web tier to application tier should be internal.Note: When using load-balancing rules with Azure Load Balancer, you need to specify a health probes to allow Load Balancer to detect the backend endpoint status.
Health probes support the TCP, HTTP, HTTPS protocols. -
You have 10 Azure virtual machines on a subnet named Subnet1. Subnet1 is on a virtual network named VNet1.
You plan to deploy a public Azure Standard Load Balancer named LB1 to the same Azure region as the 10 virtual machines.
You need to ensure that traffic from all the virtual machines to the internet flows through LB1. The solution must prevent the virtual machines from being accessible on the internet.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Add health probes to LB1.
- Add the network interfaces of the virtual machines to the backend pool of LB1.
- Add an inbound rule to LB1.
- Add an outbound rule to LB1.
- Associate a network security group (NSG) to Subnet1.
- Associate a user-defined route to Subnet1.
Explanation:A: To allow the Load Balancer to monitor the status of your app, you use a health probe. The health probe dynamically adds or removes VMs from the Load Balancer rotation based on their response to health checks.
B: To distribute traffic to the VMs, a backend address pool contains the IP addresses of the virtual (NICs) connected to the Load Balancer.
D: A Load Balancer rule is used to define how traffic is distributed to the VMs. Only outbound traffic is allowed.
-
You have SQL Server on an Azure virtual machine named SQL1.
You need to automate the backup of the databases on SQL1 by using Automated Backup v2 for the virtual machines. The backups must meet the following requirements:
– Meet a recovery point objective (RPO) of 15 minutes.
– Retain the backups for 30 days.
– Encrypt the backups at rest.What should you provision as part of the backup solution?
- Elastic Database jobs
- Azure Key Vault
- an Azure Storage account
- a Recovery Services vault
Explanation:
An Azure storage account is used for storing Automated Backup files in blob storage. A container is created at this location to store all backup files. The backup file naming convention includes the date, time, and database GUID.