AZ-304 : Microsoft Azure Architect Design : Part 01
AZ-304 : Microsoft Azure Architect Design : Part 01
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview. General Overview
Litware, Inc. is a medium-sized finance company.
Overview. Physical Locations
Litware has a main office in Boston.
Existing Environment. Identity Environment
The network contains an Active Directory forest named Litware.com that is linked to an Azure Active Directory (Azure AD) tenant named Litware.com. All users have Azure Active Directory Premium P2 licenses.
Litware has a second Azure AD tenant named dev.Litware.com that is used as a development environment.
The Litware.com tenant has a conditional access policy named capolicy1. Capolicy1 requires that when users manage the Azure subscription for a production environment by using the Azure portal, they must connect from a hybrid Azure AD-joined device.
Existing Environment. Azure Environment
Litware has 10 Azure subscriptions that are linked to the Litware.com tenant and five Azure subscriptions that are linked to the dev.Litware.com tenant. All the subscriptions are in an Enterprise Agreement (EA).
The Litware.com tenant contains a custom Azure role-based access control (Azure RBAC) role named Role1 that grants the DataActions read permission to the blobs and files in Azure Storage.
Existing Environment. On-premises Environment
The on-premises network of Litware contains the resources shown in the following table.
AZ-304 Microsoft Azure Architect Design Part 01 Q01 001 Existing Environment. Network Environment
Litware has ExpressRoute connectivity to Azure.
Planned Changes and Requirements. Planned Changes
Litware plans to implement the following changes:
– Migrate DB1 and DB2 to Azure.
– Migrate App1 to Azure virtual machines.
– Deploy the Azure virtual machines that will host App1 to Azure dedicated hosts.Planned Changes and Requirements. Authentication and Authorization Requirements
Litware identifies the following authentication and authorization requirements:
– Users that manage the production environment by using the Azure portal must connect from a hybrid Azure AD-joined device and authenticate by using Azure Multi-Factor Authentication (MFA).
– The Network Contributor built-in RBAC role must be used to grant permission to all the virtual networks in all the Azure subscriptions.
– To access the resources in Azure, App1 must use the managed identity of the virtual machines that will host the app.
– Role1 must be used to assign permissions to the storage accounts of all the Azure subscriptions.
– RBAC roles must be applied at the highest level possible.Planned Changes and Requirements. Resiliency Requirements
Litware identifies the following resiliency requirements:
Once migrated to Azure, DB1 and DB2 must meet the following requirements:
– Maintain availability if two availability zones in the local Azure region fail.
– Fail over automatically.
– Minimize I/O latency.App1 must meet the following requirements:
– Be hosted in an Azure region that supports availability zones.
– Be hosted on Azure virtual machines that support automatic scaling.
– Maintain availability if two availability zones in the local Azure region fail.Planned Changes and Requirements. Security and Compliance Requirements
Litware identifies the following security and compliance requirements:
– Once App1 is migrated to Azure, you must ensure that new data can be written to the app, and the modification of new and existing data is prevented for a period of three years.
– On-premises users and services must be able to access the Azure – Storage account that will host the data in App1.
– Access to the public endpoint of the Azure Storage account that will host the App1 data must be prevented.
– All Azure SQL databases in the production environment must have Transparent Data Encryption (TDE) enabled.
– App1 must not share physical hardware with other workloads.Planned Changes and Requirements. Business Requirements
Litware identifies the following business requirements:
– Minimize administrative effort.
– Minimize costs.-
HOTSPOT
You plan to migrate App1 to Azure.
You need to estimate the compute costs for App1 in Azure. The solution must meet the security and compliance requirements.
What should you use to estimate the costs, and what should you implement to minimize the costs? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-304 Microsoft Azure Architect Design Part 01 Q01 002 Question 
AZ-304 Microsoft Azure Architect Design Part 01 Q01 002 Answer Explanation:Box 1: The Azure Total Cost of Ownership (TCO) Calculator
The Total Cost of Ownership (TCO) Calculator estimates the cost savings you can realize by migrating your workloads to Azure.Note: The TCO Calculator recommends a set of equivalent services in Azure that will support your applications. Our analysis will show each cost area with an estimate of your on-premises spend versus your spend in Azure. There are several cost categories that either decrease or go away completely when you move workloads to the cloud.
Box 2: Azure Hybrid Benefit
Azure Hybrid Benefit is a licensing benefit that helps you to significantly reduce the costs of running your workloads in the cloud. It works by letting you use your on-premises Software Assurance-enabled Windows Server and SQL Server licenses on Azure. And now, this benefit applies to RedHat and SUSE Linux subscriptions, too.Scenario:
Litware identifies the following security and compliance requirements:– Once App1 is migrated to Azure, you must ensure that new data can be written to the app, and the modification of new and existing data is prevented for a period of three years.
– On-premises users and services must be able to access the Azure Storage account that will host the data in App1.
– Access to the public endpoint of the Azure Storage account that will host the App1 data must be prevented.
– All Azure SQL databases in the production environment must have Transparent Data Encryption (TDE) enabled.
– App1 must not share physical hardware with other workloads.
-
-
You need to recommend a solution to generate a monthly report of all the new Azure Resource Manager resource deployments in your subscription.
What should you include in the recommendation?
- the Change Tracking management solution
- Application Insights
- Azure Monitor action groups
- Azure Activity Log
Explanation:Activity logs are kept for 90 days. You can query for any range of dates, as long as the starting date isn’t more than 90 days in the past.
Through activity logs, you can determine:
– what operations were taken on the resources in your subscription
– who started the operation
– when the operation occurred
– the status of the operation
– the values of other properties that might help you research the operation -
You have an Azure subscription that contains an Azure SQL database named DB1.
Several queries that query the data in DB1 take a long time to execute.
You need to recommend a solution to identify the queries that take the longest to execute.
What should you include in the recommendation?
- SQL Database Advisor
- Azure Monitor
- Performance Recommendations
- Query Performance Insight
Explanation:
Query Performance Insight provides intelligent query analysis for single and pooled databases. It helps identify the top resource consuming and long-running queries in your workload. This helps you find the queries to optimize to improve overall workload performance and efficiently use the resource that you are paying for. -
HOTSPOT
You have an Azure App Service Web App that includes Azure Blob storage and an Azure SQL Database instance. The application is instrumented by using the Application Insights SDK.
You need to design a monitoring solution for the web app.
Which Azure monitoring services should you use? To answer, select the appropriate Azure monitoring services in the answer area.
NOTE: Each correct selection is worth one point.

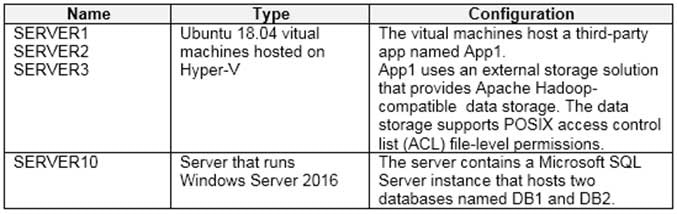
AZ-304 Microsoft Azure Architect Design Part 01 Q04 003 Question 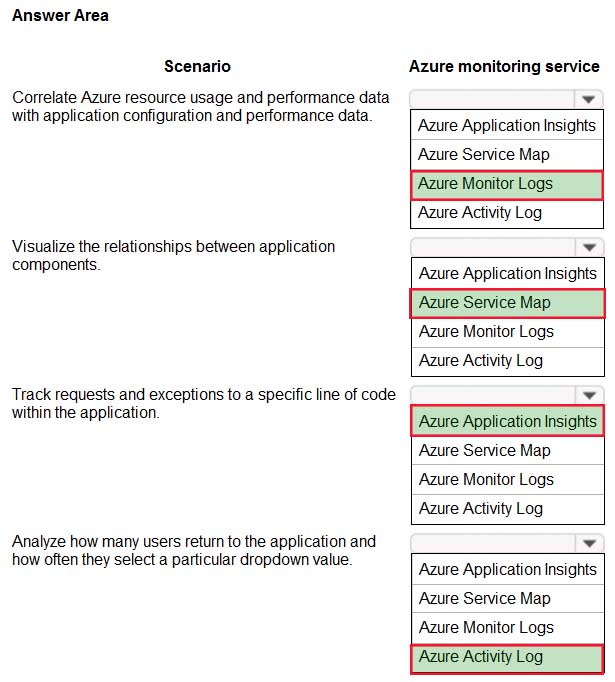
AZ-304 Microsoft Azure Architect Design Part 01 Q04 003 Answer Explanation:Note: You can select Logs from either the Azure Monitor menu or the Log Analytics workspaces menu.
-
You have an on-premises Hyper-V cluster. The cluster contains Hyper-V hosts that run Windows Server 2016 Datacenter. The hosts are licensed under a Microsoft Enterprise Agreement that has Software Assurance.
The Hyper-V cluster contains 30 virtual machines that run Windows Server 2012 R2. Each virtual machine runs a different workload. The workloads have predictable consumption patterns.
You plan to replace the virtual machines with Azure virtual machines that run Windows Server 2016. The virtual machines will be sized according to the consumption pattern of each workload.
You need to recommend a solution to minimize the compute costs of the Azure virtual machines.
Which two recommendations should you include in the solution? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Configure a spending limit in the Azure account center.
- Create a virtual machine scale set that uses autoscaling.
- Activate Azure Hybrid Benefit for the Azure virtual machines.
- Purchase Azure Reserved Virtual Machine Instances for the Azure virtual machines.
- Create a lab in Azure DevTest Labs and place the Azure virtual machines in the lab.
Explanation:C: For customers with Software Assurance, Azure Hybrid Benefit for Windows Server allows you to use your on-premises Windows Server licenses and run Windows virtual machines on Azure at a reduced cost. You can use Azure Hybrid Benefit for Windows Server to deploy new virtual machines with Windows OS.
D: With Azure Reserved VM Instances (RIs) you reserve virtual machines in advance and save up to 80 percent.
-
HOTSPOT
You have an Azure subscription that contains the SQL servers on Azure shown in the following table.

AZ-304 Microsoft Azure Architect Design Part 01 Q06 004 The subscription contains the storage accounts shown in the following table.

AZ-304 Microsoft Azure Architect Design Part 01 Q06 005 You create the Azure SQL databases shown in the following table.
AZ-304 Microsoft Azure Architect Design Part 01 Q06 006 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-304 Microsoft Azure Architect Design Part 01 Q06 007 Question 
AZ-304 Microsoft Azure Architect Design Part 01 Q06 007 Answer Explanation:Box 1: Yes
Be sure that the destination is in the same region as your database and server.Box 2: No
Box 3: No
-
A company has a hybrid ASP.NET Web API application that is based on a software as a service (SaaS) offering.
Users report general issues with the data. You advise the company to implement live monitoring and use ad hoc queries on stored JSON data. You also advise the company to set up smart alerting to detect anomalies in the data.
You need to recommend a solution to set up smart alerting.
What should you recommend?
- Azure Site Recovery and Azure Monitor Logs
- Azure Data Lake Analytics and Azure Monitor Logs
- Azure Application Insights and Azure Monitor Logs
- Azure Security Center and Azure Data Lake Store
Explanation:
Application Insights, a feature of Azure Monitor, is an extensible Application Performance Management (APM) service for developers and DevOps professionals. Use it to monitor your live applications. It will automatically detect performance anomalies, and includes powerful analytics tools to help you diagnose issues and to understand what users actually do with your app. -
You have an Azure subscription that is linked to an Azure Active Directory (Azure AD) tenant. The subscription contains 10 resource groups, one for each department at your company.
Each department has a specific spending limit for its Azure resources.
You need to ensure that when a department reaches its spending limit, the compute resources of the department shut down automatically.
Which two features should you include in the solution? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Azure Logic Apps
- Azure Monitor alerts
- the spending limit of an Azure account
- Cost Management budgets
- Azure Log Analytics alerts
Explanation:C: The spending limit in Azure prevents spending over your credit amount. All new customers who sign up for an Azure free account or subscription types that include credits over multiple months have the spending limit turned on by default. The spending limit is equal to the amount of credit and it can’t be changed.
D: Turn on the spending limit after removing
This feature is available only when the spending limit has been removed indefinitely for subscription types that include credits over multiple months. You can use this feature to turn on your spending limit automatically at the start of the next billing period.1. Sign in to the Azure portal as the Account Administrator.
2. Search for Cost Management + Billing.
3. Etc. -
HOTSPOT
You have an Azure subscription that contains the resources shown in the following table.

AZ-304 Microsoft Azure Architect Design Part 01 Q09 008 You create an Azure SQL database named DB1 that is hosted in the East US region.
To DB1, you add a diagnostic setting named Settings1. Settings1 archives SQLInsights to storage1 and sends SQLInsights to Workspace1.
For each of the following statements, select Yes if the statement is true, Otherwise, select No.
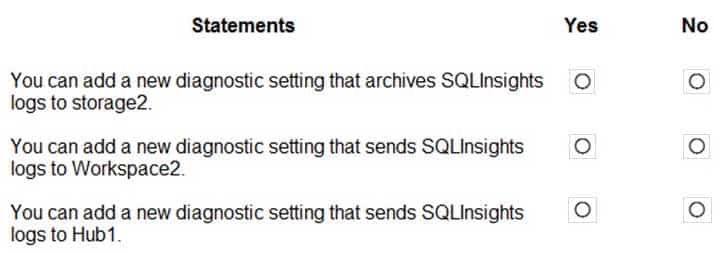
AZ-304 Microsoft Azure Architect Design Part 01 Q09 009 Question 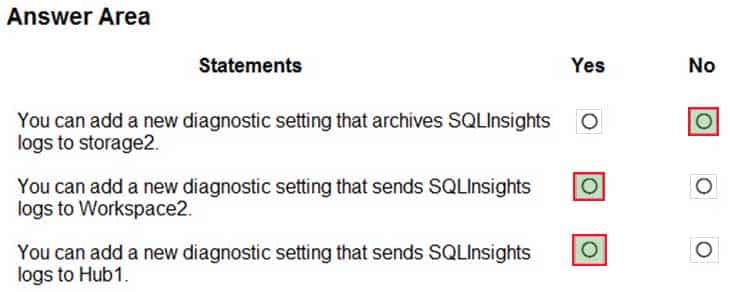
AZ-304 Microsoft Azure Architect Design Part 01 Q09 009 Answer Explanation:Box 1: No
You archive logs only to Azure Storage accounts.Box 2: Yes
Box 3: Yes
Sending logs to Event Hubs allows you to stream data to external systems such as third-party SIEMs and other log analytics solutions.Note: A single diagnostic setting can define no more than one of each of the destinations. If you want to send data to more than one of a particular destination type (for example, two different Log Analytics workspaces), then create multiple settings. Each resource can have up to 5 diagnostic settings.
-
HOTSPOT
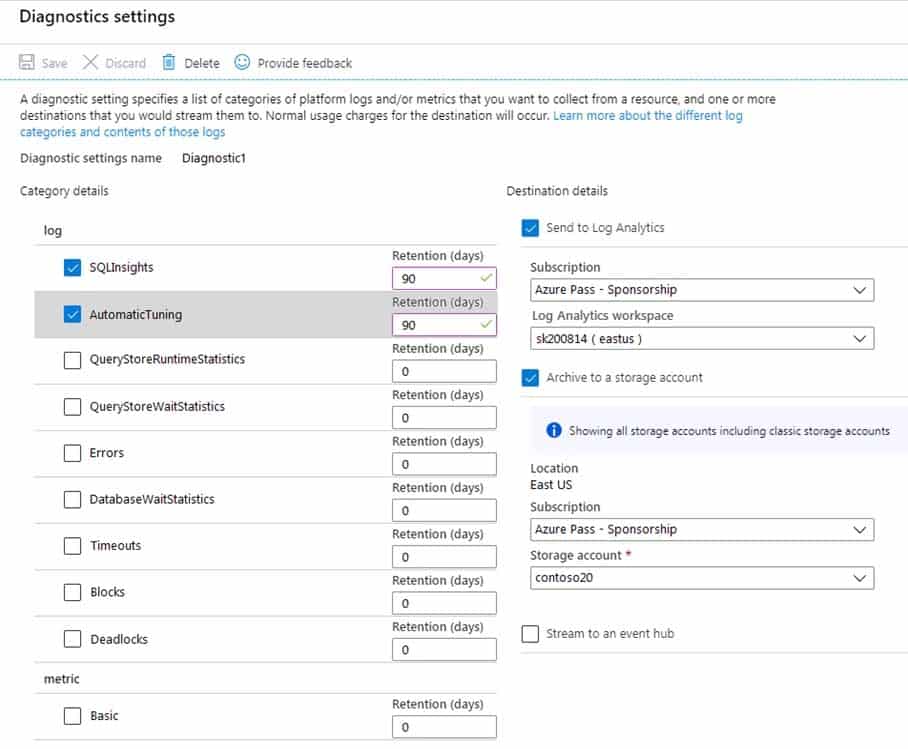
You deploy several Azure SQL Database instances.
You plan to configure the Diagnostics settings on the databases as shown in the following exhibit.
AZ-304 Microsoft Azure Architect Design Part 01 Q10 010 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
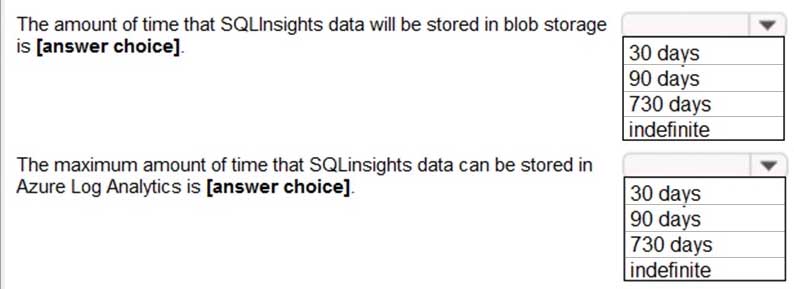
AZ-304 Microsoft Azure Architect Design Part 01 Q10 011 Question 
AZ-304 Microsoft Azure Architect Design Part 01 Q10 011 Answer Explanation:In the exhibit, the SQLInsights data is configured to be stored in Azure Log Analytics for 90 days. However, the question is asking for the “maximum” amount of time that the data can be stored which is 730 days.
-
Your company uses Microsoft System Center Service Manager on its on-premises network.
You plan to deploy several services to Azure.
You need to recommend a solution to push Azure service health alerts to Service Manager.
What should you include in the recommendation?
- IT Service Management Connector (ITSM)
- Azure Event Hubs
- Azure Notification Hubs
- Application Insights Connector
-
HOTSPOT
You have an Azure subscription that contains 300 Azure virtual machines that run Windows Server 2019.
You need to centrally monitor all warning events in the System logs of the virtual machines.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-304 Microsoft Azure Architect Design Part 01 Q12 012 Question 
AZ-304 Microsoft Azure Architect Design Part 01 Q12 012 Answer -
You have an Azure SQL database named DB1 that contains multiple tables.
You need to improve the performance of DB1. The solution must minimize administrative effort.
What should you use?
- automatic tuning
- Azure Advisor
- Azure Monitor
- Query Performance Insight
Explanation:Azure SQL Database and Azure SQL Managed Instance automatic tuning provides peak performance and stable workloads through continuous performance tuning based on AI and machine learning.
Automatic tuning is a fully managed intelligent performance service that uses built-in intelligence to continuously monitor queries executed on a database, and it automatically improves their performance.
-
You need to recommend a solution to generate a monthly report of all the new Azure Resource Manager resource deployments in your subscription.
What should you include in the recommendation?
- Azure Advisor
- Azure Analysis Services
- Azure Monitor action groups
- Azure Log Analytics
Explanation:
Log Analytics is a tool in the Azure portal used to edit and run log queries with data in Azure Monitor Logs. You may write a simple query that returns a set of records and then use features of Log Analytics to sort, filter, and analyze them. Or you may write a more advanced query to perform statistical analysis and visualize the results in a chart to identify a particular trend. -
Your company provides customer support for multiple Azure subscriptions and third-party hosting providers.
You are designing a centralized monitoring solution. The solution must provide the following services:
– Collect log and diagnostic data from all the third-party hosting providers into a centralized repository.
– Collect log and diagnostic data from all the subscriptions into a centralized repository.
– Automatically analyze log data and detect threats.
– Provide automatic responses to known events.Which Azure service should you include in the solution?
- Azure Sentinel
- Azure Log Analytics
- Azure Monitor
- Azure Application Insights
Explanation:The following diagram gives a high-level view of Azure Monitor. At the center of the diagram are the data stores for metrics and logs, which are the two fundamental types of data used by Azure Monitor. On the left are the sources of monitoring data that populate these data stores. On the right are the different functions that Azure Monitor performs with this collected data. This includes such actions as analysis, alerting, and streaming to external systems.

AZ-304 Microsoft Azure Architect Design Part 01 Q15 014 -
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview. General Overview
Litware, Inc. is a medium-sized finance company.
Overview. Physical Locations
Litware has a main office in Boston.
Existing Environment. Identity Environment
The network contains an Active Directory forest named Litware.com that is linked to an Azure Active Directory (Azure AD) tenant named Litware.com. All users have Azure Active Directory Premium P2 licenses.
Litware has a second Azure AD tenant named dev.Litware.com that is used as a development environment.
The Litware.com tenant has a conditional acсess policy named capolicy1. Capolicy1 requires that when users manage the Azure subscription for a production environment by using the Azure portal, they must connect from a hybrid Azure AD-joined device.
Existing Environment. Azure Environment
Litware has 10 Azure subscriptions that are linked to the Litware.com tenant and five Azure subscriptions that are linked to the dev.Litware.com tenant. All the subscriptions are in an Enterprise Agreement (EA).
The Litware.com tenant contains a custom Azure role-based access control (Azure RBAC) role named Role1 that grants the DataActions read permission to the blobs and files in Azure Storage.
Existing Environment. On-premises Environment
The on-premises network of Litware contains the resources shown in the following table.
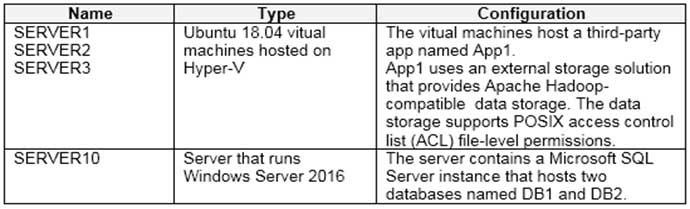
AZ-304 Microsoft Azure Architect Design Part 01 Q16 015 Existing Environment. Network Environment
Litware has ExpressRoute connectivity to Azure.
Planned Changes and Requirements. Planned Changes
Litware plans to implement the following changes:
– Migrate DB1 and DB2 to Azure.
– Migrate App1 to Azure virtual machines.
Deploy the Azure virtual machines that will host App1 to Azure dedicated hosts.Planned Changes and Requirements. Authentication and Authorization Requirements
Litware identifies the following authentication and authorization requirements:
Users that manage the production environment by using the Azure portal must connect from a hybrid Azure AD-joined device and authenticate by using Azure Multi-Factor Authentication (MFA).
The Network Contributor built-in RBAC role must be used to grant permission to all the virtual networks in all the Azure subscriptions.
To access the resources in Azure, App1 must use the managed identity of the virtual machines that will host the app.
Role1 must be used to assign permissions to the storage accounts of all the Azure subscriptions.
RBAC roles must be applied at the highest level possible.Planned Changes and Requirements. Resiliency Requirements
Litware identifies the following resiliency requirements:
Once migrated to Azure, DB1 and DB2 must meet the following requirements:
– Maintain availability if two availability zones in the local Azure region fail.
– Fail over automatically.
– Minimize I/O latency.App1 must meet the following requirements:
– Be hosted in an Azure region that supports availability zones.
– Be hosted on Azure virtual machines that support automatic scaling.
– Maintain availability if two availability zones in the local Azure region fail.Planned Changes and Requirements. Security and Compliance Requirements
Litware identifies the following security and compliance requirements:
– Once App1 is migrated to Azure, you must ensure that new data can be written to the app, and the modification of new and existing data is prevented for a period of three years.
– On-premises users and services must be able to access the Azure Storage account that will host the data in App1.
Access to the public endpoint of the Azure Storage account that will host the App1 data must be prevented.
All Azure SQL databases in the production environment must have Transparent Data Encryption (TDE) enabled.
App1 must not share physical hardware with other workloads.Planned Changes and Requirements. Business Requirements
Litware identifies the following business requirements:
– Minimize administrative effort.
– Minimize costs.-
HOTSPOT
You plan to migrate App1 to Azure.
You need to recommend a storage solution for App1 that meets the security and compliance requirements.
Which type of storage should you recommend, and how should you recommend configuring the storage? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
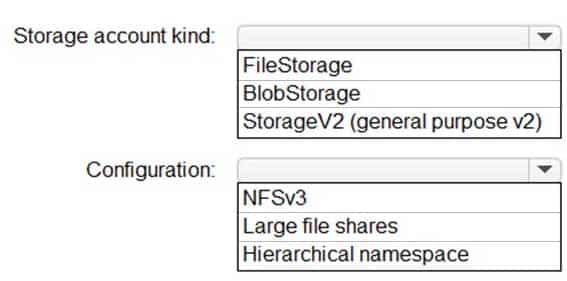
AZ-304 Microsoft Azure Architect Design Part 01 Q16 016 Question 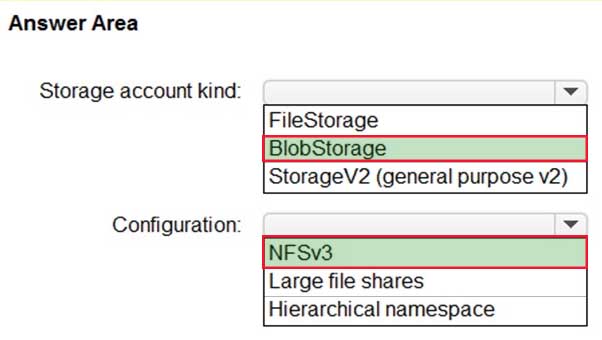
AZ-304 Microsoft Azure Architect Design Part 01 Q16 016 Answer Explanation:Box 1: BlobStorage
BlobStorage supports NFSv3, see below.Box 2: NFSv3
Blob storage now supports the Network File System (NFS) 3.0 protocol. This support provides Linux file system compatibility at object storage scale and prices and enables Linux clients to mount a container in Blob storage from an Azure Virtual Machine (VM) or a computer on-premises.Scenario: Litware identifies the following security and compliance requirements:
On-premises users and services must be able to access the Azure Storage account that will host the data in App1.
-
You migrate App1 to Azure.
You need to ensure that the data storage for App1 meets the security and compliance requirements.
What should you do?
- Create Azure RBAC assignments.
- Create an access policy for the blob service.
- Modify the access level of the blob service.
- Implement Azure resource locks.
Explanation:Azure Active Directory (Azure AD) authorizes access rights to secured resources through Azure role-based access control (Azure RBAC). Azure Storage defines a set of Azure built-in roles that encompass common sets of permissions used to access blob data.
When an Azure role is assigned to an Azure AD security principal, Azure grants access to those resources for that security principal. An Azure AD security principal may be a user, a group, an application service principal, or a managed identity for Azure resources.
Scenario:
To access the resources in Azure, App1 must use the managed identity of the virtual machines that will host the app.The Litware.com tenant contains a custom Azure role-based access control (Azure RBAC) role named Role1 that grants the Data Actions read permission to the blobs and files in Azure Storage.
Litware identifies the following security and compliance requirements:
– On-premises users and services must be able to access the Azure Storage account that will host the data in App1.
-
HOTSPOT
You need to ensure that users managing the production environment are registered for Azure MFA and must authenticate by using Azure MFA when they sign in to the Azure portal. The solution must meet the authentication and authorization requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-304 Microsoft Azure Architect Design Part 01 Q16 017 Question 
AZ-304 Microsoft Azure Architect Design Part 01 Q16 017 Answer Explanation:Box 1: Azure AD Identity Protection
Azure AD Identity Protection helps you manage the roll-out of Azure AD Multi-Factor Authentication (MFA) registration by configuring a Conditional Access policy to require MFA registration no matter what modern authentication app you are signing in to.Scenario: Users that manage the production environment by using the Azure portal must connect from a hybrid Azure AD-joined device and authenticate by using Azure Multi-Factor Authentication (MFA).
Box 2: Sign-in risk policy…
Scenario: The Litware.com tenant has a conditional access policy named capolicy1. Capolicy1 requires that when users manage the Azure subscription for a production environment by using the Azure portal, they must connect from a hybrid Azure AD-joined device.Identity Protection policies we have two risk policies that we can enable in our directory.
Sign-in risk policy
User risk policy -
You plan to migrate App1 to Azure.
You need to recommend a network connectivity solution for the Azure Storage account that will host the App1 data. The solution must meet the security and compliance requirements.
What should you include in the recommendation?
- a private endpoint
- a service endpoint that has a service endpoint policy
- Azure public peering for an ExpressRoute circuit
- Microsoft peering for an ExpressRoute circuit
Explanation:By default, Azure service resources secured to virtual networks aren’t reachable from on-premises networks. If you want to allow traffic from on-premises, you must also allow public (typically, NAT) IP addresses from your on-premises or ExpressRoute. You can add these IP addresses through the IP firewall configuration for Azure service resources.
You can use ExpressRoute for public peering and Microsoft peering.
Scenario:
– On-premises users and services must be able to access the Azure Storage account that will host the data in App1.
– Access to the public endpoint of the Azure Storage account that will host the App1 data must be prevented.Incorrect Answers:
C: Public Peering is deprecated for new circuits. -
You plan to migrate App1 to Azure. The solution must meet the authentication and authorization requirements.
Which type of endpoint should App1 use to obtain an access token?
- Azure Instance Metadata Service (IMDS)
- Azure AD
- Azure Service Management
- Microsoft identity platform
Explanation:Scenario: To access the resources in Azure, App1 must use the managed identity of the virtual machines that will host the app.
Managed identities provide an identity for applications to use when connecting to resources that support Azure Active Directory (Azure AD) authentication. Applications may use the managed identity to obtain Azure AD tokens.
-
DRAG DROP
You need to configure an Azure policy to ensure that the Azure SQL databases have TDE enabled. The solution must meet the security and compliance requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

AZ-304 Microsoft Azure Architect Design Part 01 Q16 018 Question 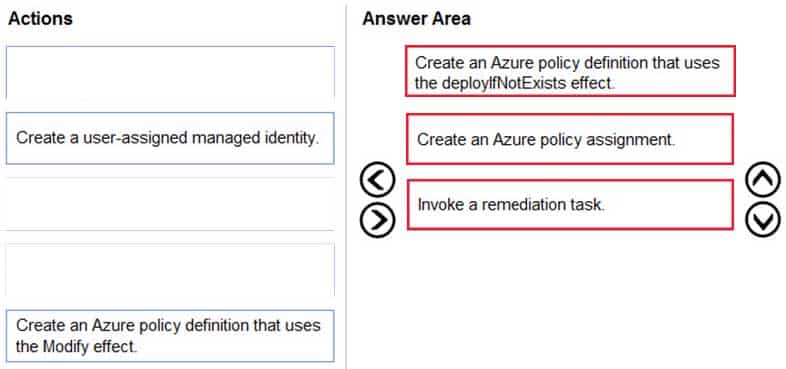
AZ-304 Microsoft Azure Architect Design Part 01 Q16 018 Answer Explanation:Scenario: All Azure SQL databases in the production environment must have Transparent Data Encryption (TDE) enabled.
Step 1: Create an Azure policy definition that uses the deployIfNotExists identity.
The first step is to define the roles that deployIfNotExists and modify needs in the policy definition to successfully deploy the content of your included template.Step 2: Create an Azure policy assignment
When creating an assignment using the portal, Azure Policy both generates the managed identity and grants it the roles defined in roleDefinitionIds.Step 3: Invoke a remediation task
Resources that are non-compliant to a deployIfNotExists or modify policy can be put into a compliant state through Remediation. Remediation is accomplished by instructing Azure Policy to run the deployIfNotExists effect or the modify operations of the assigned policy on your existing resources and subscriptions, whether that assignment is to a management group, a subscription, a resource group, or an individual resource.During evaluation, the policy assignment with deployIfNotExists or modify effects determines if there are non-compliant resources or subscriptions. When non-compliant resources or subscriptions are found, the details are provided on the Remediation page.
-
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
Fabrikam, Inc. is an engineering company that has offices throughout Europe. The company has a main office in London and three branch offices in Amsterdam, Berlin, and Rome.
Existing Environment. Active Directory Environment
The network contains two Active Directory forests named corp.fabrikam.com and rd.fabrikam.com. There are no trust relationships between the forests.
Corp.fabrikam.com is a production forest that contains identities used for internal user and computer authentication.
Rd.fabrikam.com is used by the research and development (R&D) department only.
Existing Environment. Network Infrastructure
Each office contains at least one domain controller from the corp.fabrikam.com domain. The main office contains all the domain controllers for the rd.fabrikam.com forest.
All the offices have a high-speed connection to the Internet.
An existing application named WebApp1 is hosted in the data center of the London office. WebApp1 is used by customers to place and track orders. WebApp1 has a web tier that uses Microsoft Internet Information Services (IIS) and a database tier that runs Microsoft SQL Server 2016. The web tier and the database tier are deployed to virtual machines that run on Hyper-V.
The IT department currently uses a separate Hyper-V environment to test updates to WebApp1.
Fabrikam purchases all Microsoft licenses through a Microsoft Enterprise Agreement that includes Software Assurance.
Existing Environment. Problem Statements
The use of WebApp1 is unpredictable. At peak times, users often report delays. At other times, many resources for WebApp1 are underutilized.
Requirements. Planned Changes
Fabrikam plans to move most of its production workloads to Azure during the next few years.
As one of its first projects, the company plans to establish a hybrid identity model, facilitating an upcoming Microsoft 365 deployment.
All R&D operations will remain on-premises.
Fabrikam plans to migrate the production and test instances of WebApp1 to Azure.
Requirements. Technical Requirements
Fabrikam identifies the following technical requirements:
– Web site content must be easily updated from a single point.
– User input must be minimized when provisioning new web app instances.
– Whenever possible, existing on-premises licenses must be used to reduce cost.
– Users must always authenticate by using their corp.fabrikam.com UPN identity.
– Any new deployments to Azure must be redundant in case an Azure region fails.
– Whenever possible, solutions must be deployed to Azure by using the Standard pricing tier of Azure App Service.
– An email distribution group named IT Support must be notified of any issues relating to the directory synchronization services.
– Directory synchronization between Azure Active Directory (Azure AD) and corp.fabrikam.com must not be affected by a link failure between Azure and the on-premises network.Requirements. Database Requirements
Fabrikam identifies the following database requirements:
– Database metrics for the production instance of WebApp1 must be available for analysis so that database administrators can optimize the performance settings.
– To avoid disrupting customer access, database downtime must be minimized when databases are migrated.
– Database backups must be retained for a minimum of seven years to meet compliance requirements.Requirements. Security Requirements
Fabrikam identifies the following security requirements:
– Company information including policies, templates, and data must be inaccessible to anyone outside the company.
– Users on the on-premises network must be able to authenticate to corp.fabrikam.com if an Internet link fails.
– Administrators must be able authenticate to the Azure portal by using their corp.fabrikam.com credentials.
– All administrative access to the Azure portal must be secured by using multi-factor authentication.
– The testing of WebApp1 updates must not be visible to anyone outside the company.-
What should you include in the identity management strategy to support the planned changes?
- Move all the domain controllers from corp.fabrikam.com to virtual networks in Azure.
- Deploy domain controllers for the rd.fabrikam.com forest to virtual networks in Azure.
- Deploy domain controllers for corp.fabrikam.com to virtual networks in Azure.
- Deploy a new Azure AD tenant for the authentication of new R&D projects.
Explanation:
Directory synchronization between Azure Active Directory (Azure AD) and corp.fabrikam.com must not be affected by a link failure between Azure and the on-premises network. (This requires domain controllers in Azure)
Users on the on-premises network must be able to authenticate to corp.fabrikam.com if an Internet link fails. (This requires domain controllers on-premises) -
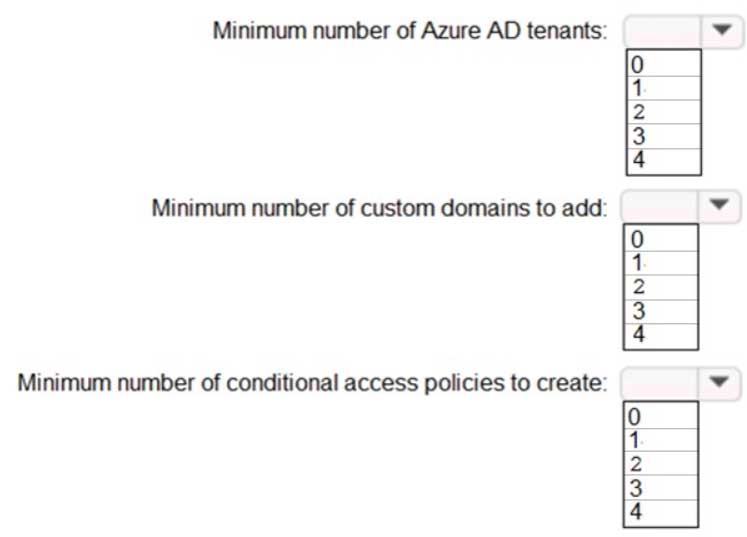
HOTSPOT
To meet the authentication requirements of Fabrikam, what should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
AZ-304 Microsoft Azure Architect Design Part 01 Q17 018-A Question 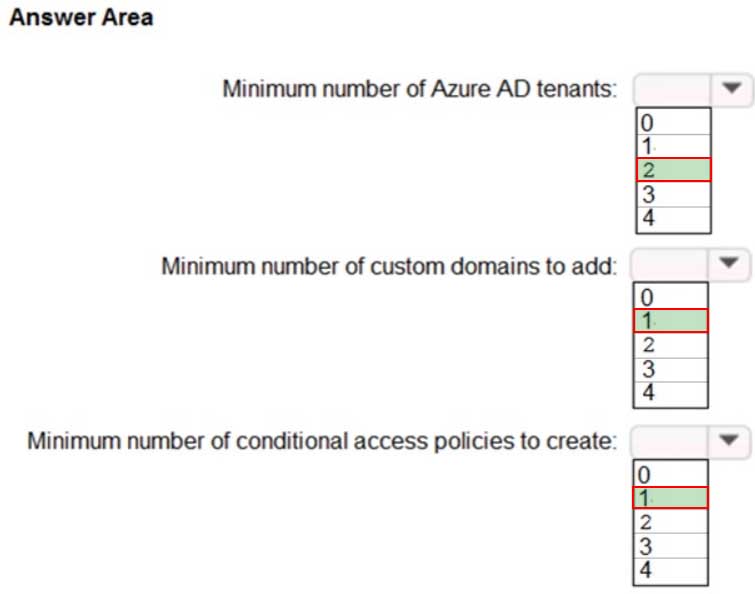
AZ-304 Microsoft Azure Architect Design Part 01 Q17 018-B Answer Explanation:Box 1: 2
The network contains two Active Directory forests named corp.fabrikam.com and rd.fabrikam.com. There are no trust relationships between the forests.Box 2: 1
Box 3: 1
Scenario:
– Users on the on-premises network must be able to authenticate to corp.fabrikam.com if an Internet link fails.
– Administrators must be able authenticate to the Azure portal by using their corp.fabrikam.com credentials.
– All administrative access to the Azure portal must be secured by using multi-factor authentication.Note:
Users must always authenticate by using their corp.fabrikam.com UPN identity.
The network contains two Active Directory forests named corp.fabrikam.com and rd.fabrikam.com. There are no trust relationships between the forests.Corp.fabrikam.com is a production forest that contains identities used for internal user and computer authentication.
Rd.fabrikam.com is used by the research and development (R&D) department only.
-
-
You are designing an Azure resource deployment that will use Azure Resource Manager templates. The deployment will use Azure Key Vault to store secrets.
You need to recommend a solution to meet the following requirements:
– Prevent the IT staff that will perform the deployment from retrieving the secrets directly from Key Vault.
– Use the principle of least privilege.Which two actions should you recommend? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Create a Key Vault access policy that allows all get key permissions, get secret permissions, and get certificate permissions.
- From Access policies in Key Vault, enable access to the Azure Resource Manager for template deployment.
- Create a Key Vault access policy that allows all list key permissions, list secret permissions, and list certificate permissions.
- Assign the IT staff a custom role that includes the Microsoft.KeyVault/Vaults/Deploy/Action permission.
- Assign the Key Vault Contributor role to the IT staff.
Explanation:B: To access a key vault during template deployment, set enabledForTemplateDeployment on the key vault to true.
D: The user who deploys the template must have the Microsoft.KeyVault/vaults/deploy/action permission for the scope of the resource group and key vault.
Incorrect Answers:
E: To grant access to a user to manage key vaults, you assign a predefined key vault Contributor role to the user at a specific scope.
If a user has Contributor permissions to a key vault management plane, the user can grant themselves access to the data plane by setting a Key Vault access policy. You should tightly control who has Contributor role access to your key vaults. Ensure that only authorized persons can access and manage your key vaults, keys, secrets, and certificates. -
You have an Azure subscription that contains web apps in three Azure regions.
You need to implement Azure Key Vault to meet the following requirements:
– In the event of a regional outage, all keys must be readable.
– All the web apps in the subscription must be able to access Key Vault.
– The number of Key Vault resources to be deployed and managed must be minimized.How many instances of Key Vault should you implement?
- 1
- 2
- 3
- 6
Explanation:The contents of your key vault are replicated within the region and to a secondary region at least 150 miles away but within the same geography. This maintains high durability of your keys and secrets. See the Azure paired regions document for details on specific region pairs.
Example: Secrets that must be shared by your application in both Europe West and Europe North. Minimize these as much as you can. Put these in a key vault in either of the two regions. Use the same URI from both regions. Microsoft will fail over the Key Vault service internally.
-
You have an Azure Active Directory (Azure AD) tenant.
You plan to provide users with access to shared files by using Azure Storage. The users will be provided with different levels of access to various Azure file shares based on their user account or their group membership.
You need to recommend which additional Azure services must be used to support the planned deployment.
What should you include in the recommendation?
- an Azure AD enterprise application
- Azure Information Protection
- an Azure AD Domain Services (Azure AD DS) instance
- an Azure Front Door instance
Explanation:
Azure Files supports identity-based authentication over Server Message Block (SMB) through two types of Domain Services: on-premises Active Directory Domain Services (AD DS) and Azure Active Directory Domain Services (Azure AD DS).