AZ-304 : Microsoft Azure Architect Design : Part 02
AZ-304 : Microsoft Azure Architect Design : Part 02
-
DRAG DROP
Your company has users who work remotely from laptops.
You plan to move some of the applications accessed by the remote users to Azure virtual machines. The users will access the applications in Azure by using a point-to-site VPN connection. You will use certificates generated from an on-premises-based Certification authority (CA).
You need to recommend which certificates are required for the deployment.
What should you include in the recommendation? To answer, drag the appropriate certificates to the correct targets. Each certificate may be used once, more than once, of not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
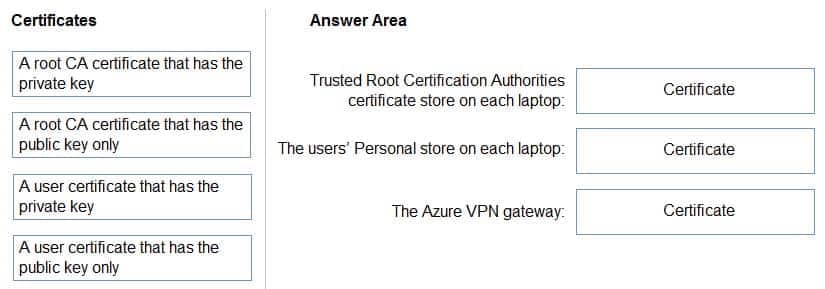
AZ-304 Microsoft Azure Architect Design Part 02 Q01 019 Question 
AZ-304 Microsoft Azure Architect Design Part 02 Q01 019 Answer -
HOTSPOT
You are building an application that will run in a virtual machine (VM). The application will use Azure Managed Identity.
The application uses Azure Key Vault, Azure SQL Database, and Azure Cosmos DB.
You need to ensure the application can use secure credentials to access these services.
Which authorization method should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
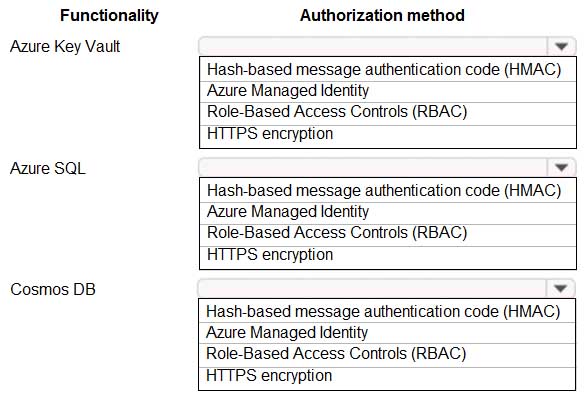
AZ-304 Microsoft Azure Architect Design Part 02 Q02 020 Question 
AZ-304 Microsoft Azure Architect Design Part 02 Q02 020 Answer Explanation:Note: Managed identities for Azure resources is the new name for the service formerly known as Managed Service Identity (MSI).
-
You have an Azure subscription that contains a custom application named Application1. Application1 was developed by an external company named Fabrikam, Ltd. Developers at Fabrikam were assigned role-based access control (RBAC) permissions to the Application1 components. All users are licensed for the Microsoft 365 E5 plan.
You need to recommend a solution to verify whether the Fabrikam developers still require permissions to Application1. The solution must meet the following requirements:
– To the manager of the developers, send a monthly email message that lists the access permissions to Application1.
– If the manager does not verify an access permission, automatically revoke that permission.
– Minimize development effort.What should you recommend?
- Create an Azure Automation runbook that runs the Get-AzureADUserAppRoleAssignment cmdlet.
- Create an Azure Automation runbook that runs the Get-AzRoleAssignment cmdlet.
- In Azure Active Directory (Azure AD), create an access review of Application1.
- In Azure Active Directory (AD) Privileged Identity Management, create a custom role assignment for the Application1 resources.
-
DRAG DROP
A company named Contoso, Ltd. has an Azure Active Directory (Azure AD) tenant that uses the Basic license.
You plan to deploy two applications to Azure. The applications have the requirements shown in the following table.
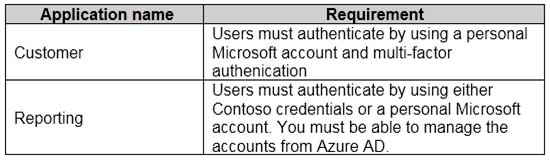
AZ-304 Microsoft Azure Architect Design Part 02 Q04 021 Which authentication strategy should you recommend for each application? To answer, drag the appropriate authentication strategies to the correct applications. Each authentication strategy may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
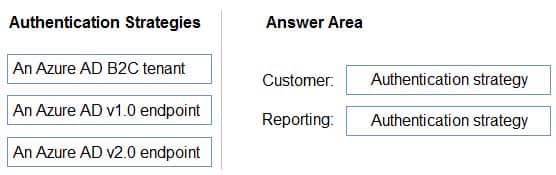
AZ-304 Microsoft Azure Architect Design Part 02 Q04 022 Question 
AZ-304 Microsoft Azure Architect Design Part 02 Q04 022 Answer Explanation:Box 1: Azure AD V2.0 endpoint
Microsoft identity platform is an evolution of the Azure Active Directory (Azure AD) developer platform. It allows developers to build applications that sign in all Microsoft identities and get tokens to call Microsoft APIs, such as Microsoft Graph, or APIs that developers have built. The Microsoft identity platform consists of:OAuth 2.0 and OpenID Connect standard-compliant authentication service that enables developers to authenticate any Microsoft identity, including:
Work or school accounts (provisioned through Azure AD)
Personal Microsoft accounts (such as Skype, Xbox, and Outlook.com)
Social or local accounts (via Azure AD B2C)Box 2: Azure AD B2C tenant
Azure Active Directory B2C provides business-to-customer identity as a service. Your customers use their preferred social, enterprise, or local account identities to get single sign-on access to your applications and APIs.
Azure Active Directory B2C (Azure AD B2C) integrates directly with Azure Multi-Factor Authentication so that you can add a second layer of security to sign-up and sign-in experiences in your applications. -
HOTSPOT
You manage a network that includes an on-premises Active Directory domain and an Azure Active Directory (Azure AD).
Employees are required to use different accounts when using on-premises or cloud resources. You must recommend a solution that lets employees sign in to all company resources by using a single account. The solution must implement an identity provider.
You need to provide guidance on the different identity providers.
How should you describe each identity provider? To answer, select the appropriate description from each list in the answer area.
NOTE: Each correct selection is worth one point.
AZ-304 Microsoft Azure Architect Design Part 02 Q05 023 Question 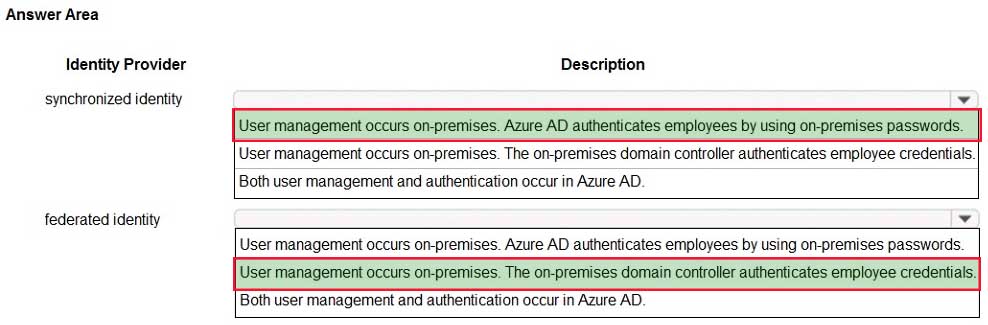
AZ-304 Microsoft Azure Architect Design Part 02 Q05 023 Answer Explanation:Box1: User management occurs on-premises. Azure AD authenticates employees by using on-premises passwords.
Azure AD Domain Services for hybrid organizations
Organizations with a hybrid IT infrastructure consume a mix of cloud resources and on-premises resources. Such organizations synchronize identity information from their on-premises directory to their Azure AD tenant. As hybrid organizations look to migrate more of their on-premises applications to the cloud, especially legacy directory-aware applications, Azure AD Domain Services can be useful to them.Example: Litware Corporation has deployed Azure AD Connect, to synchronize identity information from their on-premises directory to their Azure AD tenant. The identity information that is synchronized includes user accounts, their credential hashes for authentication (password hash sync) and group memberships.

AZ-304 Microsoft Azure Architect Design Part 02 Q05 024 User accounts, group memberships, and credentials from Litware’s on-premises directory are synchronized to Azure AD via Azure AD Connect. These user accounts, group memberships, and credentials are automatically available within the managed domain.
Box 2: User management occurs on-premises. The on-promises domain controller authenticates employee credentials.
You can federate your on-premises environment with Azure AD and use this federation for authentication and authorization. This sign-in method ensures that all user authentication occurs on-premises.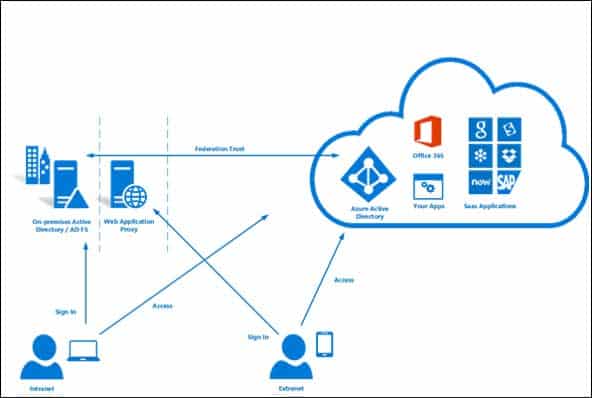
AZ-304 Microsoft Azure Architect Design Part 02 Q05 025 -
HOTSPOT
You configure the Diagnostics settings for an Azure SQL database as shown in the following exhibit.

AZ-304 Microsoft Azure Architect Design Part 02 Q06 026 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
AZ-304 Microsoft Azure Architect Design Part 02 Q06 027 Question 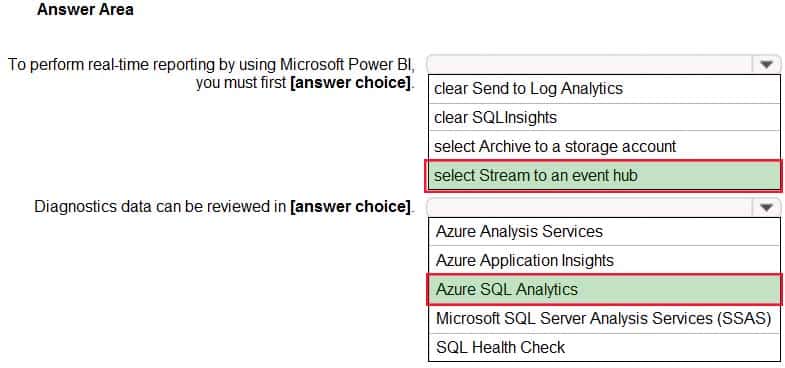
AZ-304 Microsoft Azure Architect Design Part 02 Q06 027 Answer -
You plan to deploy an application named App1 that will run on five Azure virtual machines. Additional virtual machines will be deployed later to run App1.
You need to recommend a solution to meet the following requirements for the virtual machines that will run App1:
– Ensure that the virtual machines can authenticate to Azure Active Directory (Azure AD) to gain access to an Azure key vault, Azure Logic Apps instances, and an Azure SQL database.
– Avoid assigning new roles and permissions for Azure services when you deploy additional virtual machines.
– Avoid storing secrets and certificates on the virtual machines.
– Minimize administrative effort for managing identities.Which type of identity should you include in the recommendation?
- a service principal that is configured to use a certificate
- a system-assigned managed identity
- a service principal that is configured to use a client secret
- a user-assigned managed identity
Explanation:Managed identities for Azure resources is a feature of Azure Active Directory.
User-assigned managed identity can be shared. The same user-assigned managed identity can be associated with more than one Azure resource.Incorrect Answers:
B: System-assigned managed identity cannot be shared. It can only be associated with a single Azure resource. -
You are designing a large Azure environment that will contain many subscriptions.
You plan to use Azure Policy as part of a governance solution.
To which three scopes can you assign Azure Policy definitions? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- management groups
- subscriptions
- Azure Active Directory (Azure AD) tenants
- resource groups
- Azure Active Directory (Azure AD) administrative units
- compute resources
Explanation:
Azure Policy evaluates resources in Azure by comparing the properties of those resources to business rules. Once your business rules have been formed, the policy definition or initiative is assigned to any scope of resources that Azure supports, such as management groups, subscriptions, resource groups, or individual resources. -
You are designing a microservices architecture that will be hosted in an Azure Kubernetes Service (AKS) cluster. Apps that will consume the microservices will be hosted on Azure virtual machines. The virtual machines and the AKS cluster will reside on the same virtual network.
You need to design a solution to expose the microservices to the consumer apps. The solution must meet the following requirements:
– Ingress access to the microservices must be restricted to a single private IP address and protected by using mutual TLS authentication.
– The number of incoming microservice calls must be rate-limited.
– Costs must be minimized.What should you include in the solution?
- Azure App Gateway with Azure Web Application Firewall (WAF)
- Azure API Management Premium tier with virtual network connection
- Azure API Management Standard tier with a service endpoint
- Azure Front Door with Azure Web Application Firewall (WAF)
Explanation:
One option is to deploy APIM (API Management) inside the cluster VNet.
The AKS cluster and the applications that consume the microservices might reside within the same VNet, hence there is no reason to expose the cluster publicly as all API traffic will remain within the VNet. For these scenarios, you can deploy API Management into the cluster VNet. API Management Premium tier supports VNet deployment. -
HOTSPOT
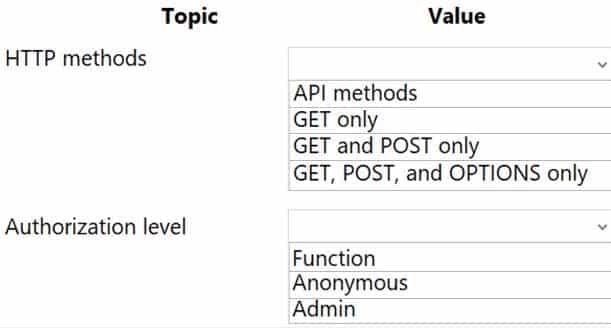
A company plans to implement an HTTP-based API to support a web app. The web app allows customers to check the status of their orders.
The API must meet the following requirements:
– Implement Azure Functions.
– Provide public read-only operations.
– Do not allow write operations.You need to recommend configuration options.
What should you recommend? To answer, configure the appropriate options in the dialog box in the answer area.
NOTE: Each correct selection is worth one point.
AZ-304 Microsoft Azure Architect Design Part 02 Q10 028 Question 
AZ-304 Microsoft Azure Architect Design Part 02 Q10 028 Answer Explanation:
HTTP methods: GET only
Authorization level: Anonymous
The option is Allow Anonymous requests. This option turns on authentication and authorization in App Service, but defers authorization decisions to your application code. For authenticated requests, App Service also passes along authentication information in the HTTP headers.
This option provides more flexibility in handling anonymous requests. -
A company named Contoso Ltd., has a single-domain Active Directory forest named contoso.com.
Contoso is preparing to migrate all workloads to Azure. Contoso wants users to use single sign-on (SSO) when they access cloud-based services that integrate with Azure Active Directory (Azure AD).
You need to identify any objects in Active Directory that will fail to synchronize to Azure AD due to formatting issues. The solution must minimize costs.
What should you include in the solution?
- Azure AD Connect Health
- Microsoft Office 365 IdFix
- Azure Advisor
- Password Export Server version 3.1 (PES v3.1) in Active Directory Migration Tool (ADMT)
-
DRAG DROP
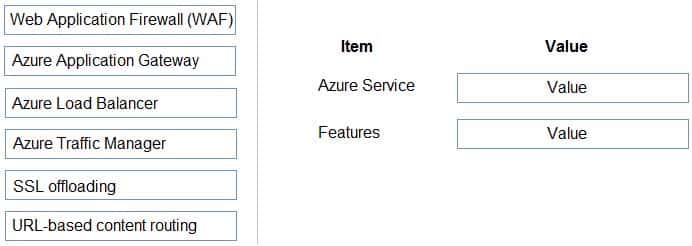
A company has an existing web application that runs on virtual machines (VMs) in Azure.
You need to ensure that the application is protected from SQL injection attempts and uses a layer-7 load balancer. The solution must minimize disruption to the code for the existing web application.
What should you recommend? To answer, drag the appropriate values to the correct items. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
AZ-304 Microsoft Azure Architect Design Part 02 Q12 029 Question 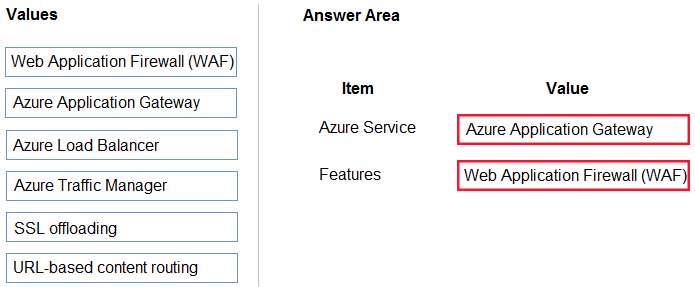
AZ-304 Microsoft Azure Architect Design Part 02 Q12 029 Answer Explanation:Box 1: Azure Application Gateway
Azure Application Gateway provides an application delivery controller (ADC) as a service. It offers various layer 7 load-balancing capabilities for your applications.Box 2: Web Application Firewall (WAF)
Application Gateway web application firewall (WAF) protects web applications from common vulnerabilities and exploits.
This is done through rules that are defined based on the OWASP core rule sets 3.0 or 2.2.9.
There are rules that detects SQL injection attacks. -
You have an Azure subscription. The subscription has a blob container that contains multiple blobs.
Ten users in the finance department of your company plan to access the blobs during the month of April.
You need to recommend a solution to enable access to the blobs during the month of April only.
Which security solution should you include in the recommendation?
- access keys
- conditional access policies
- certificates
- shared access signatures (SAS)
-
HOTSPOT
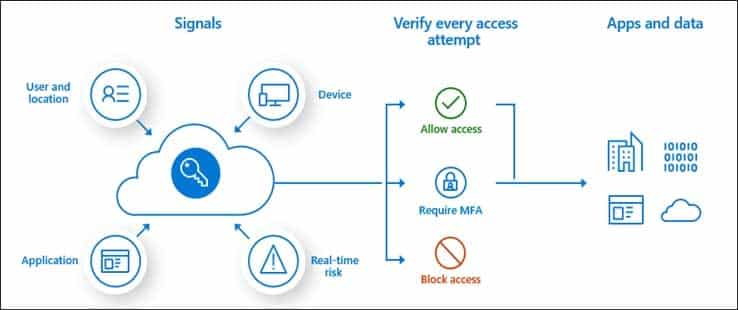
You plan to deploy an Azure web app named App1 that will use Azure Active Directory (Azure AD) authentication.
App1 will be accessed from the internet by the users at your company. All the users have computers that run Windows 10 and are joined to Azure AD.
You need to recommend a solution to ensure that the users can connect to App1 without being prompted for authentication and can access App1 only from company-owned computers.
What should you recommend for each requirement? To answer, select the appropriate options in the answer area.

AZ-304 Microsoft Azure Architect Design Part 02 Q14 030 Question 
AZ-304 Microsoft Azure Architect Design Part 02 Q14 030 Answer Explanation:Box 1: An Azure AD app registration
Azure active directory (AD) provides cloud based directory and identity management services. You can use azure AD to manage users of your application and authenticate access to your applications using azure active directory.
You register your application with Azure active directory tenant.Box 2: A conditional access policy
Conditional Access policies at their simplest are if-then statements, if a user wants to access a resource, then they must complete an action.By using Conditional Access policies, you can apply the right access controls when needed to keep your organization secure and stay out of your user’s way when not needed.
AZ-304 Microsoft Azure Architect Design Part 02 Q14 031 -
HOTSPOT
You plan to create an Azure environment that will contain a root management group and 10 child management groups. Each child management group will contain five Azure subscriptions. You plan to have between 10 and 30 resource groups in each subscription.
You need to design an Azure governance solution. The solution must meet the following requirements:
– Use Azure Blueprints to control governance across all the subscriptions and resource groups.
– Ensure that Blueprints-based configurations are consistent across all the subscriptions and resource groups.
– Minimize the number of blueprint definitions and assignments.What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-304 Microsoft Azure Architect Design Part 02 Q15 032 Question 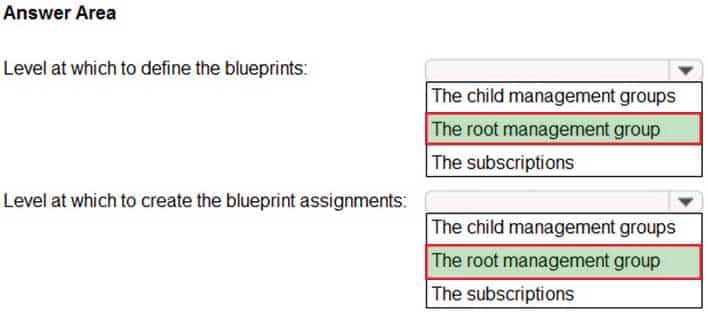
AZ-304 Microsoft Azure Architect Design Part 02 Q15 032 Answer Explanation:Box 1: The root management group
When creating a blueprint definition, you’ll define where the blueprint is saved. Blueprints can be saved to a management group or subscription that you have Contributor access to. If the location is a management group, the blueprint is available to assign to any child subscription of that management group.Box 2: The root management group
Each directory is given a single top-level management group called the “Root” management group. This root management group is built into the hierarchy to have all management groups and subscriptions fold up to it. This root management group allows for global policies and Azure role assignments to be applied at the directory level.Each Published Version of a blueprint can be assigned to an existing management group or subscription.
-
You have an Azure subscription.
You need to recommend a solution to provide developers with the ability to provision Azure virtual machines. The solution must meet the following requirements:
– Only allow the creation of the virtual machines in specific regions.
– Only allow the creation of specific sizes of virtual machines.What should you include in the recommendation?
- Azure Resource Manager templates
- Azure Policy
- conditional access policies
- role-based access control (RBAC)
-
Your company has the offices shown in the following table.
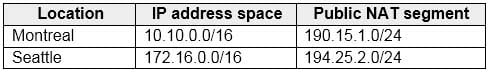
AZ-304 Microsoft Azure Architect Design Part 02 Q17 033 The network contains an Active Directory domain named contoso.com that is synced to Azure Active Directory (Azure AD).
All users connect to an Exchange Online.
You need to recommend a solution to ensure that all the users use Azure Multi-Factor Authentication (MFA) to connect to Exchange Online from one of the offices.
What should you include in the recommendation?
- a virtual network and two Microsoft Cloud App Security policies
- a named location and two Microsoft Cloud App Security policies
- a conditional access policy and two virtual networks
- a conditional access policy and two named locations
Explanation:
Conditional Access policies are at their most basic an if-then statement combining signals, to make decisions, and enforce organization policies. One of those signals that can be incorporated into the decision-making process is network location. -
HOTSPOT
Your organization has developed and deployed several Azure App Service Web and API applications. The applications use Azure Key Vault to store several authentication, storage account, and data encryption keys. Several departments have the following requests to support the applications:
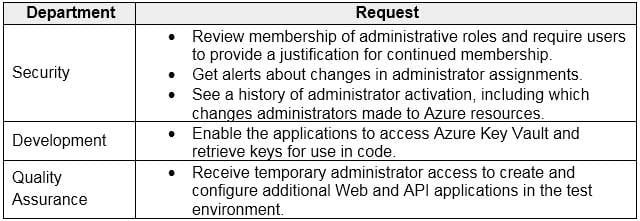
AZ-304 Microsoft Azure Architect Design Part 02 Q18 034 You need to recommend the appropriate Azure service for each department request.
What should you recommend? To answer, configure the appropriate options in the dialog box in the answer area.
NOTE: Each correct selection is worth one point.
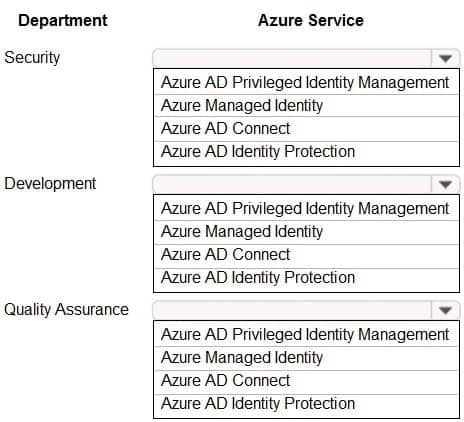
AZ-304 Microsoft Azure Architect Design Part 02 Q18 035 Question 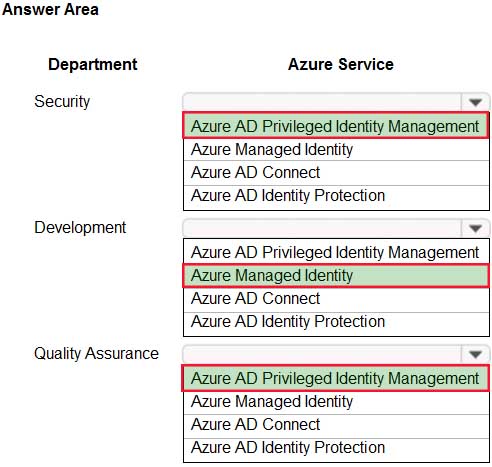
AZ-304 Microsoft Azure Architect Design Part 02 Q18 035 Answer -
Your network contains an on-premises Active Directory forest.
You discover that when users change jobs within your company, the membership of the user groups are not being updated. As a result, the users can access resources that are no longer relevant to their job.
You plan to integrate Active Directory and Azure Active Directory (Azure AD) by using Azure AD Connect.
You need to recommend a solution to ensure that group owners are emailed monthly about the group memberships they manage.
What should you include in the recommendation?
- Azure AD Identity Protection
- Azure AD access reviews
- Tenant Restrictions
- conditional access policies
-
HOTSPOT
You have five .NET Core applications that run on 10 Azure virtual machines in the same subscription.
You need to recommend a solution to ensure that the applications can authenticate by using the same Azure Active Directory (Azure AD) identity. The solution must meet the following requirements:
– Ensure that the applications can authenticate only when running on the 10 virtual machines.
– Minimize administrative effort.What should you include in the recommendation? To answer, select the appropriate options in the answer area.

AZ-304 Microsoft Azure Architect Design Part 02 Q20 036 Question 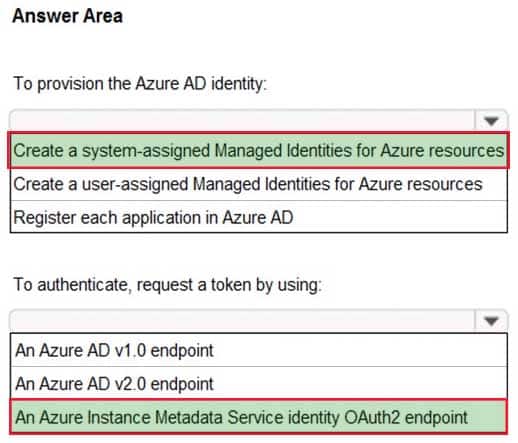
AZ-304 Microsoft Azure Architect Design Part 02 Q20 036 Answer Explanation:Box 1: Create a system-assigned Managed Identities for Azure resource
The managed identities for Azure resources feature in Azure Active Directory (Azure AD) feature provides Azure services with an automatically managed identity in Azure AD. You can use the identity to authenticate to any service that supports Azure AD authentication, including Key Vault, without any credentials in your code.A system-assigned managed identity is enabled directly on an Azure service instance. When the identity is enabled, Azure creates an identity for the instance in the Azure AD tenant that’s trusted by the subscription of the instance. After the identity is created, the credentials are provisioned onto the instance.
Box 2: An Azure Instance Metadata Service Identity
See step 3 and 5 below.How a system-assigned managed identity works with an Azure VM
1. Azure Resource Manager receives a request to enable the system-assigned managed identity on a VM.
2. Azure Resource Manager creates a service principal in Azure AD for the identity of the VM. The service principal is created in the Azure AD tenant that’s trusted by the subscription.
3. Azure Resource Manager configures the identity on the VM by updating the Azure Instance Metadata Service identity endpoint with the service principal client ID and certificate.
4. After the VM has an identity, use the service principal information to grant the VM access to Azure resources. To call Azure Resource Manager, use role-based access control (RBAC) in Azure AD to assign the appropriate role to the VM service principal. To call Key Vault, grant your code access to the specific secret or key in Key Vault.
5. Your code that’s running on the VM can request a token from the Azure Instance Metadata service endpoint, accessible only from within the VM