AZ-304 : Microsoft Azure Architect Design : Part 04
AZ-304 : Microsoft Azure Architect Design : Part 04
-
HOTSPOT
Your company has 20 web APIs that were developed in-house.
The company is developing 10 web apps that will use the web APIs. The web apps and the APIs are registered in the company’s Azure Active Directory (Azure AD) tenant. The web APIs are published by using Azure API Management.
You need to recommend a solution to block unauthorized requests originating from the web apps from reaching the web APIs. The solution must meet the following requirements:
– Use Azure AD-generated claims.
– Minimize configuration and management effort.What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-304 Microsoft Azure Architect Design Part 04 Q01 047 Question 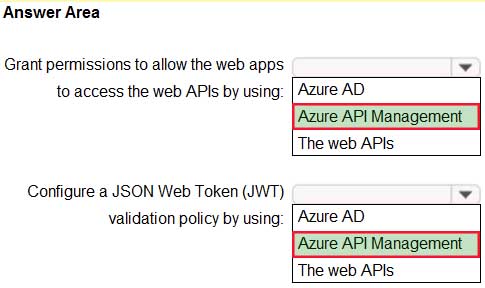
AZ-304 Microsoft Azure Architect Design Part 04 Q01 047 Answer -
HOTSPOT
You need to design a resource governance solution for an Azure subscription. The solution must meet the following requirements:
Ensure that all ExpressRoute resources are created in a resource group named RG1.
Delegate the creation of the ExpressRoute resources to an Azure Active Directory (Azure AD) group named Networking.
Use the principle of least privilege.What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-304 Microsoft Azure Architect Design Part 04 Q02 048 Question 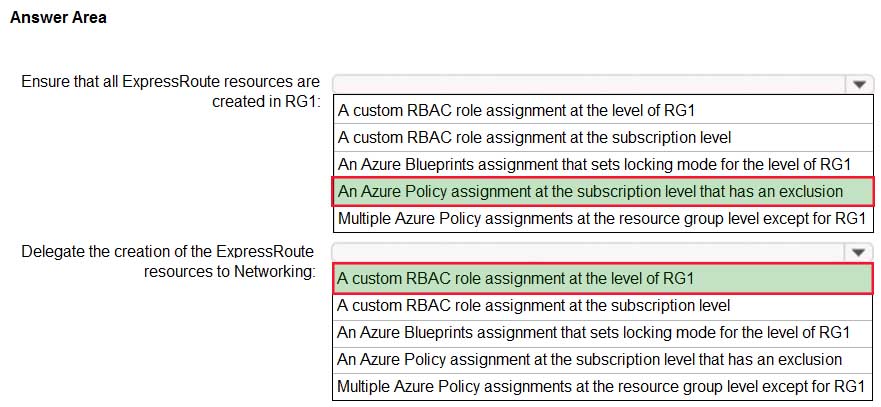
AZ-304 Microsoft Azure Architect Design Part 04 Q02 048 Answer Explanation:Box 1: An Azure policy assignment at the subscription level that has an exclusion
Box 2: A custom RBAC role assignment at the level of RG1
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope. -
You have an Azure Active Directory (Azure AD) tenant and Windows 10 devices.
You configure a conditional access policy as shown in the exhibit. (Click the Exhibit tab.)
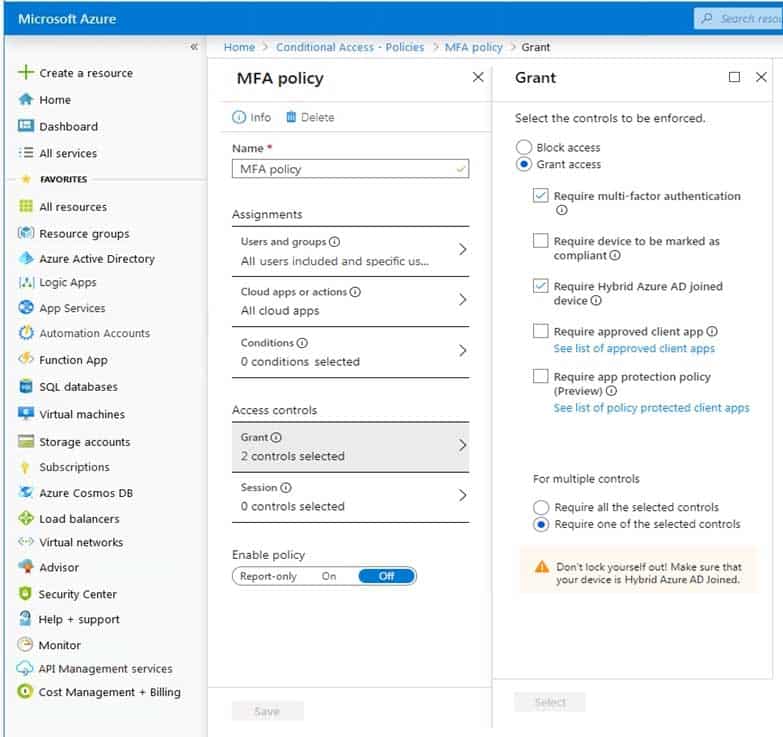
AZ-304 Microsoft Azure Architect Design Part 04 Q03 049 What is the result of the policy?
- All users will always be prompted for multi-factor authentication (MFA).
- Users will be prompted for multi-factor authentication (MFA) only when they sign in from devices that are NOT joined to Azure AD.
- All users will be able to sign in without using multi-factor authentication (MFA).
- Users will be prompted for multi-factor authentication (MFA) only when they sign in from devices that are joined to Azure AD.
Explanation:
Either the device should be joined to Azure AD or MFA must be used. -
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant.
You plan to use Azure Monitor to monitor user sign-ins and generate alerts based on specific user sign-in events.
You need to recommend a solution to trigger the alerts based on the events.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
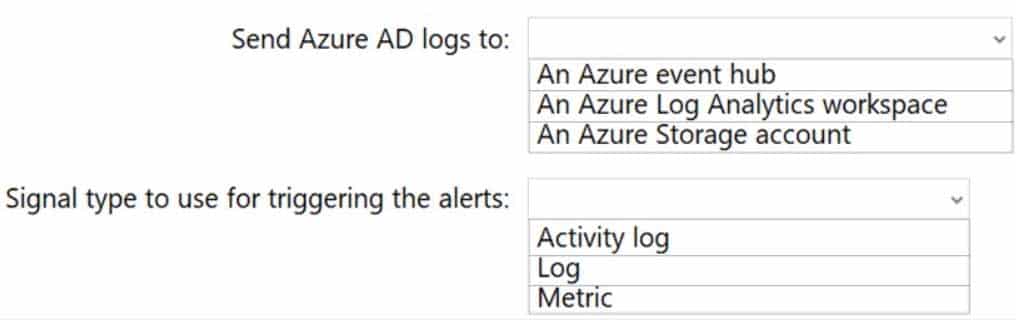
AZ-304 Microsoft Azure Architect Design Part 04 Q04 050 Question 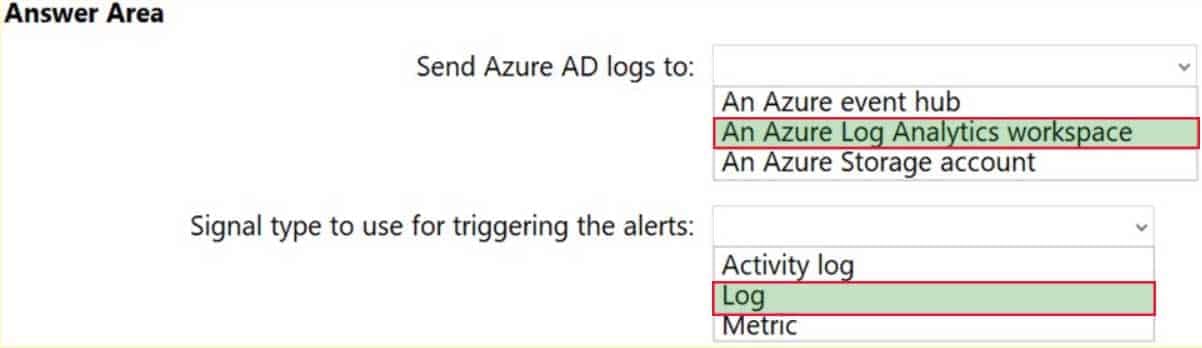
AZ-304 Microsoft Azure Architect Design Part 04 Q04 050 Answer Explanation:Box 1: An Azure Log Analytics workspace
To be able to create an alert we send the Azure AD logs to An Azure Log Analytics workspace.Note: You can forward your AAD logs and events to either an Azure Storage Account, an Azure Event Hub, Log Analytics, or a combination of all of these.
Box 2: Log
Ensure Resource Type is an analytics source like Log Analytics or Application Insights and signal type as Log. -
HOTSPOT
You configure OAuth2 authorization in API Management as shown in the following exhibit.
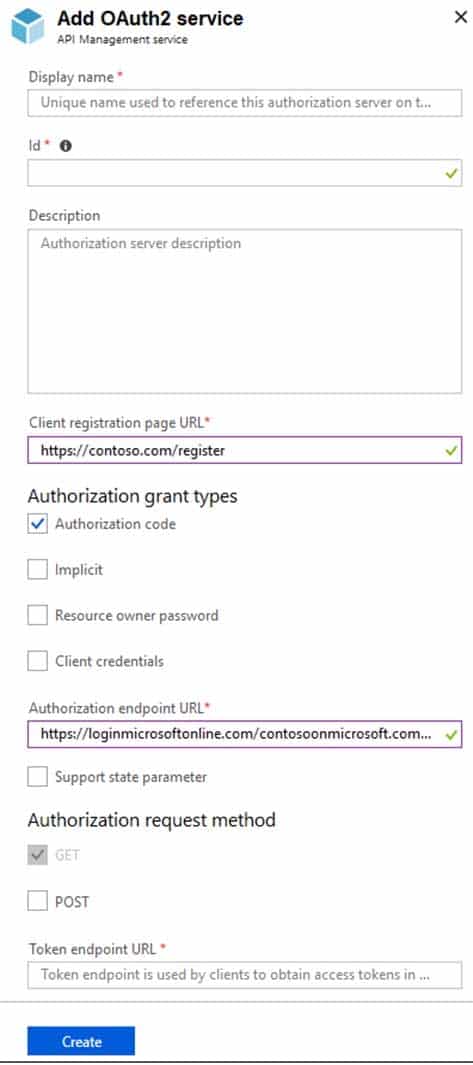
AZ-304 Microsoft Azure Architect Design Part 04 Q05 051 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

AZ-304 Microsoft Azure Architect Design Part 04 Q05 052 Question 
AZ-304 Microsoft Azure Architect Design Part 04 Q05 052 Answer Explanation:Box 1: Web applications
The Authorization Code Grant Type is used by both web apps and native apps to get an access token after a user authorizes an app.Note: The Authorization Code grant type is used by confidential and public clients to exchange an authorization code for an access token.
After the user returns to the client via the redirect URL, the application will get the authorization code from the URL and use it to request an access token.
Incorrect Answers:
Not Headless device authentication:
A headless system is a computer that operates without a monitor, graphical user interface (GUI) or peripheral devices, such as keyboard and mouse.Headless computers are usually embedded systems in various devices or servers in multi-server data center environments. Industrial machines, automobiles, medical equipment, cameras, household appliances, airplanes, vending machines and toys are among the myriad possible hosts of embedded systems.
Box 2: Client Credentials
How to include additional client data
In case you need to store additional details about a client that don’t fit into the standard parameter set the custom data parameter comes to help:POST /c2id/clients HTTP/1.1
Host: demo.c2id.com
Content-Type: application/json
Authorization: Bearer ztucZS1ZyFKgh0tUEruUtiSTXhnexmd6{
“redirect_uris” : [ “https://myapp.example.com/callback” ],
“data” : { “reg_type” : “3rd-party”,
“approved” : true,
“author_id” : 792440 }
}
The data parameter permits arbitrary content packaged in a JSON object. To set it you will need the master registration token or a one-time access token with a client-reg:data scope.Incorrect Answers:
Authorization protocols provide a state parameter that allows you to restore the previous state of your application. The state parameter preserves some state object set by the client in the Authorization request and makes it available to the client in the response. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has deployed several virtual machines (VMs) on-premises and to Azure. Azure ExpressRoute has been deployed and configured for on-premises to Azure connectivity.
Several VMs are exhibiting network connectivity issues.
You need to analyze the network traffic to determine whether packets are being allowed or denied to the VMs.
Solution: Use Azure Network Watcher to run IP flow verify to analyze the network traffic.
Does the solution meet the goal?
- Yes
- No
Explanation:The Network Watcher Network performance monitor is a cloud-based hybrid network monitoring solution that helps you monitor network performance between various points in your network infrastructure. It also helps you monitor network connectivity to service and application endpoints and monitor the performance of Azure ExpressRoute.
Note:
IP flow verify checks if a packet is allowed or denied to or from a virtual machine. The information consists of direction, protocol, local IP, remote IP, local port, and remote port. If the packet is denied by a security group, the name of the rule that denied the packet is returned. While any source or destination IP can be chosen, IP flow verify helps administrators quickly diagnose connectivity issues from or to the internet and from or to the on-premises environment.IP flow verify looks at the rules for all Network Security Groups (NSGs) applied to the network interface, such as a subnet or virtual machine NIC. Traffic flow is then verified based on the configured settings to or from that network interface. IP flow verify is useful in confirming if a rule in a Network Security Group is blocking ingress or egress traffic to or from a virtual machine.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has deployed several virtual machines (VMs) on-premises and to Azure. Azure ExpressRoute has been deployed and configured for on-premises to Azure connectivity.
Several VMs are exhibiting network connectivity issues.
You need to analyze the network traffic to determine whether packets are being allowed or denied to the VMs.
Solution: Use the Azure Advisor to analyze the network traffic.
Does the solution meet the goal?
- Yes
- No
Explanation:Instead use Azure Network Watcher to run IP flow verify to analyze the network traffic.
Note: Advisor is a personalized cloud consultant that helps you follow best practices to optimize your Azure deployments. It analyzes your resource configuration and usage telemetry and then recommends solutions that can help you improve the cost effectiveness, performance, high availability, and security of your Azure resources.
With Advisor, you can:
Get proactive, actionable, and personalized best practices recommendations.
Improve the performance, security, and high availability of your resources, as you identify opportunities to reduce your overall Azure spend.
Get recommendations with proposed actions inline. -
You have 500 Azure web apps in the same Azure region. The apps use a premium Azure key vault for authentication.
A developer reports that some authentication requests are being throttled.
You need to recommend a solution to increase the available throughput of the key vault. The solution must minimize costs.
What should you recommend?
- Change the pricing tier.
- Configure geo-replication.
- Configure load balancing for the apps.
- Increase the number of key vaults in the subscription.
Explanation:
To maximize your Key Vault through put rates, here are some recommended guidelines/best practices for maximizing your throughput:
1. Ensure you have throttling in place. Client must honor exponential back-off policies for 429’s and ensure you are doing retries as per the guidance below.
2. Divide your Key Vault traffic amongst multiple vaults and different regions. Use a separate vault for each security/availability domain. If you have five apps, each in two regions, then we recommend 10 vaults each containing the secrets unique to app and region. -
DRAG DROP
Your on-premises network contains a server named Server1 that runs an ASP.NET application named App1.
You have a hybrid deployment of Azure Active Directory (Azure AD).
You need to recommend a solution to ensure that users sign in by using their Azure AD account and Azure Multi-Factor Authentication (MFA) when they connect to App1 from the internet.
Which three Azure services should you recommend be deployed and configured in sequence? To answer, move the appropriate services from the list of services to the answer area and arrange them in the correct order.
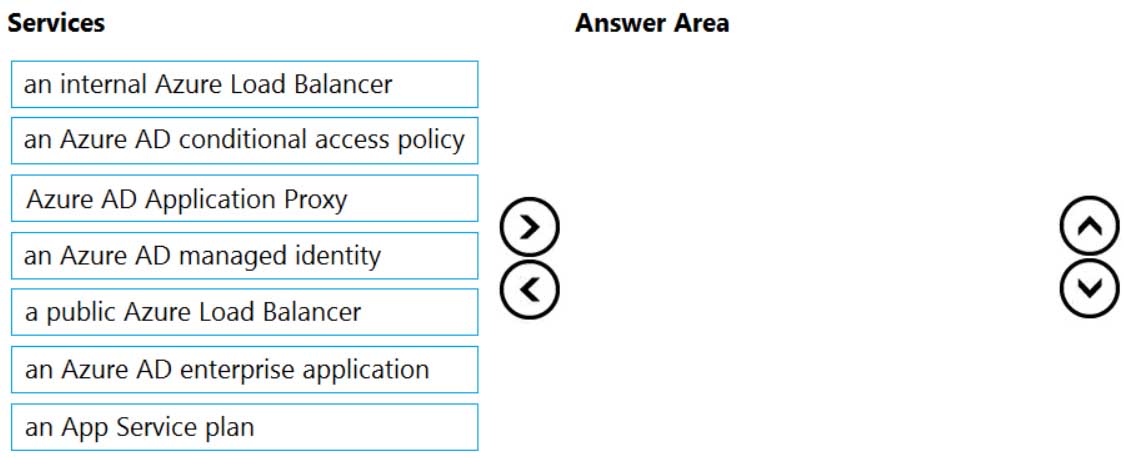
AZ-304 Microsoft Azure Architect Design Part 04 Q09 053 Question 
AZ-304 Microsoft Azure Architect Design Part 04 Q09 053 Answer Explanation:Step 1: Azure AD Application proxy
Azure AD Application Proxy is a prerequisite for a scenario with an on-premises legacy applications published for cloud access,Note: Application Proxy is a feature of Azure AD that enables users to access on-premises web applications from a remote client. Application Proxy includes both the Application Proxy service which runs in the cloud, and the Application Proxy connector which runs on an on-premises server.
Step 2: an Azure AD managed identity
Microsoft’s identity solutions span on-premises and cloud-based capabilities. These solutions create a common user identity for authentication and authorization to all resources, regardless of location. We call this hybrid identity.Step 3: an Azure AD conditional access policy
Conditional Access is the tool used by Azure Active Directory to bring signals together, to make decisions, and enforce organizational policies. Conditional Access is at the heart of the new identity driven control plane.With hybrid identity to Azure AD and hybrid identity management these scenarios become possible.
-
A company named Contoso, Ltd. has an Azure Active Directory (Azure AD) tenant that is integrated with Microsoft 365 and an Azure subscription.
Contoso has an on-premises identity infrastructure. The infrastructure includes servers that run Active Directory Domain Services (AD DS), Active Directory Federation Services (AD FS), Azure AD Connect, and Microsoft Identity Manager (MIM).
Contoso has a partnership with a company named Fabrikam, Inc. Fabrikam has an Active Directory forest and a Microsoft 365 tenant. Fabrikam has the same on-premises identity infrastructure components as Contoso.
A team of 10 developers from Fabrikam will work on an Azure solution that will be hosted in the Azure subscription of Contoso. The developers must be added to the Contributor role for a resource group in the Contoso subscription.
You need to recommend a solution to ensure that Contoso can assign the role to the 10 Fabrikam developers. The solution must ensure that the Fabrikam developers use their existing credentials to access resources.
What should you recommend?
- Configure an AD FS relying party trust between the Fabrikam and Contoso AD FS infrastructure.
- In the Azure AD tenant of Contoso, create cloud-only user accounts for the Fabrikam developers.
- Configure an organization relationship between the Microsoft 365 tenants of Fabrikam and Contoso.
- In the Azure AD tenant of Contoso, use MIM to create guest accounts for the Fabrikam developers.
Explanation:
Azure Active Directory (Azure AD) business-to-business (B2B) collaboration is a feature within External Identities that lets you invite guest users to collaborate with your organization. With B2B collaboration, you can securely share your company’s applications and services with guest users from any other organization, while maintaining control over your own corporate data. -
You are designing an Azure governance solution.
All Azure resources must be easily identifiable based on the following operational information: environment, owner, department, and cost center.
You need to ensure that you can use the operational information when you generate reports for the Azure resources.
What should you include in the solution?
- an Azure data catalog that uses the Azure REST API as a data source
- Azure Active Directory (Azure AD) administrative units
- an Azure management group that uses parent groups to create a hierarchy
- an Azure policy that enforces tagging rules
Explanation:You use Azure Policy to enforce tagging rules and conventions. By creating a policy, you avoid the scenario of resources being deployed to your subscription that don’t have the expected tags for your organization. Instead of manually applying tags or searching for resources that aren’t compliant, you create a policy that automatically applies the needed tags during deployment.
Note: Organizing cloud-based resources is a crucial task for IT, unless you only have simple deployments. Use naming and tagging standards to organize your resources for these reasons:
Resource management: Your IT teams will need to quickly locate resources associated with specific workloads, environments, ownership groups, or other important information. Organizing resources is critical to assigning organizational roles and access permissions for resource management.
-
HOTSPOT
You are designing an access policy for your company.
Occasionally, the developers at the company must stop, start, and restart Azure virtual machines. The development team changes often.
You need to recommend a solution to provide the developers with the required access to the virtual machines. The solution must meet the following requirements:
– Provide permissions only when needed.
– Use the principle of least privilege.
– Minimize costs.What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
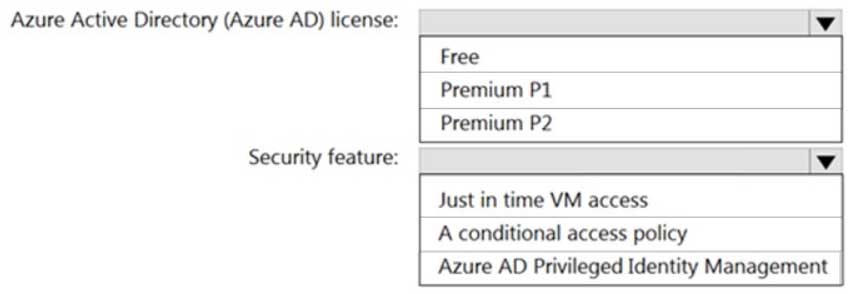
AZ-304 Microsoft Azure Architect Design Part 04 Q12 054 Question 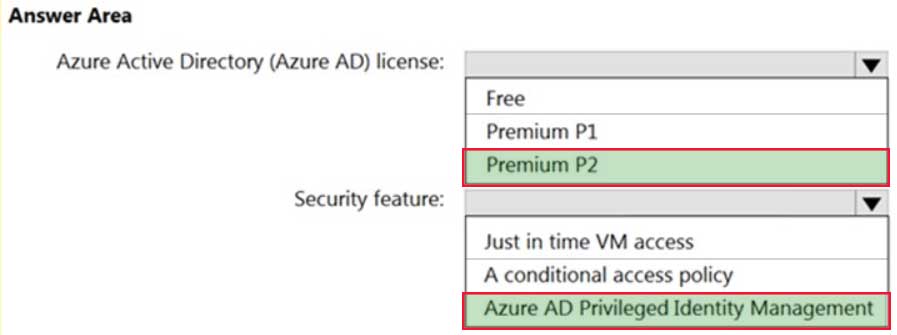
AZ-304 Microsoft Azure Architect Design Part 04 Q12 054 Answer -
HOTSPOT
You have the Free edition of a hybrid Azure Active Directory (Azure AD) tenant. The tenant uses password hash synchronization.
You need to recommend a solution to meet the following requirements:
– Prevent Active Directory domain user accounts from being locked out as the result of brute force attacks targeting Azure AD user accounts.
– Block legacy authentication attempts to Azure AD integrated apps.
– Minimize costs.What should you recommend for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

AZ-304 Microsoft Azure Architect Design Part 04 Q13 055 Question 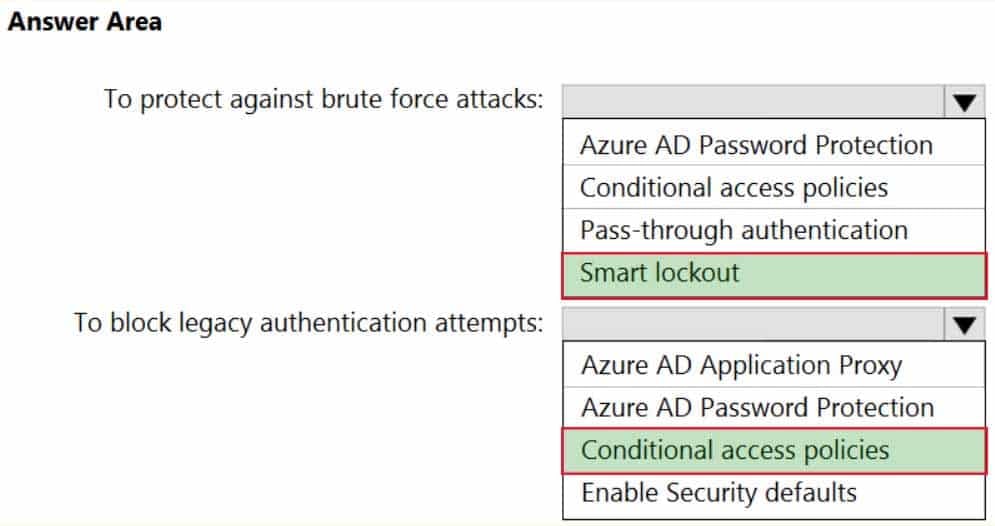
AZ-304 Microsoft Azure Architect Design Part 04 Q13 055 Answer Explanation:Box 1: Smart lockout
Smart lockout helps lock out bad actors that try to guess your users’ passwords or use brute-force methods to get in. Smart lockout can recognize sign-ins that come from valid users and treat them differently than ones of attackers and other unknown sources. Attackers get locked out, while your users continue to access their accounts and be productive.Box 2: Conditional access policies
If your environment is ready to block legacy authentication to improve your tenant’s protection, you can accomplish this goal with Conditional Access.How can you prevent apps using legacy authentication from accessing your tenant’s resources? The recommendation is to just block them with a Conditional Access policy. If necessary, you allow only certain users and specific network locations to use apps that are based on legacy authentication.
-
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains several administrative user accounts.
You need to recommend a solution to identify which administrative user accounts have NOT signed in during the previous 30 days.
Which service should you include in the recommendation?
- Azure AD Privileged Identity Management (PIM)
- Azure AD Identity Protection
- Azure Advisor
- Azure Activity Log
Explanation:
Azure AD Domain Services provides managed domain services such as domain join, group policy, LDAP, Kerberos/NTLM authentication that are fully compatible with Windows Server Active Directory. -
HOTSPOT
You are designing a software as a service (SaaS) application that will enable Azure Active Directory (Azure AD) users to create and publish online surveys. The SaaS application will have a front-end web app and a back-end web API. The web app will rely on the web API to handle updates to customer surveys.
You need to design an authorization flow for the SaaS application. The solution must meet the following requirements:
– To access the back-end web API, the web app must authenticate by using OAuth 2 bearer tokens.
– The web app must authenticate by using the identities of individual users.What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
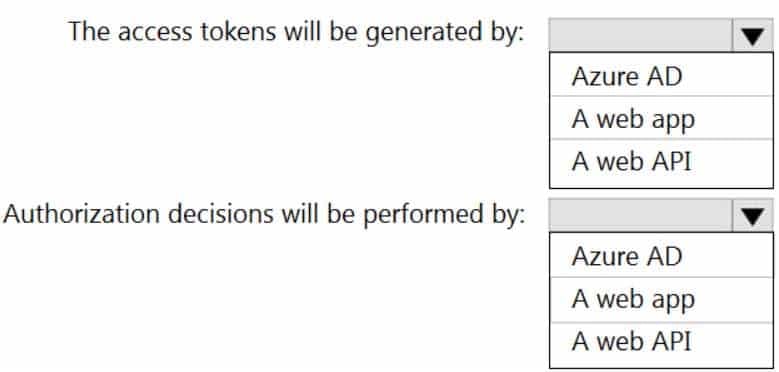
AZ-304 Microsoft Azure Architect Design Part 04 Q15 056 Question 
AZ-304 Microsoft Azure Architect Design Part 04 Q15 056 Answer -
You have a hybrid deployment of Azure Active Directory (Azure AD).
You need to recommend a solution to ensure that the Azure AD tenant can be managed only from the computers on your on-premises network.
What should you include in the recommendation?
- a conditional access policy
- Azure AD roles and administrators
- Azure AD Application Proxy
- Azure AD Privileged Identity Management
-
You plan to automate the deployment of resources to Azure subscriptions.
What is a difference between using Azure Blueprints and Azure Resource Manager templates?
- Azure Resource Manager templates remain connected to the deployed resources.
- Only Azure Resource Manager templates can contain policy definitions.
- Azure Blueprints remain connected to the deployed resources.
- Only Azure Blueprints can contain policy definitions.
Explanation:With Azure Blueprints, the relationship between the blueprint definition (what should be deployed) and the blueprint assignment (what was deployed) is preserved. This connection supports improved tracking and auditing of deployments. Azure Blueprints can also upgrade several subscriptions at once that are governed by the same blueprint.
Incorrect:
Not A: Nearly everything that you want to include for deployment in Azure Blueprints can be accomplished with a Resource Manager template. However, a Resource Manager template is a document that doesn’t exist natively in Azure – each is stored either locally or in source control. The template gets used for deployments of one or more Azure resources, but once those resources deploy there’s no active connection or relationship to the template. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains a group named Group1. Group1 contains all the administrative user accounts.
You discover several login attempts to the Azure portal from countries where administrative users do NOT work.
You need to ensure that all login attempts to the Azure portal from those countries require Azure Multi-Factor Authentication (MFA).
Solution: Implement Azure AD Privileged Identity Management.
Does this solution meet the goal?
- Yes
- No
Explanation:
Azure Active Directory (Azure AD) Privileged Identity Management (PIM) is a service that enables you to manage, control, and monitor access to important resources in your organization. -
You manage an Azure environment for a company. The environment has over 25,000 licensed users and 100 mission-critical applications.
You need to recommend a solution that provides advanced user threat detection and remediation strategies.
What should you recommend?
- Azure Active Directory (Azure AD) authentication
- Microsoft Identity Manager
- Azure Active Directory (Azure AD) Identity Protection
- Azure Active Directory Federation Services (AD FS)
- Azure Active Directory (Azure AD) Connect
-
You store web access logs data in Azure Blob storage.
You plan to generate monthly reports from the access logs.
You need to recommend an automated process to upload the data to Azure SQL Database every month.
What should you include in the recommendation?
- Data Migration Assistant
- Microsoft SQL Server Migration Assistant (SSMA)
- Azure Data Factory
- AzCopy
Explanation:
Azure Data Factory is the platform that solves such data scenarios. It is the cloud-based ETL and data integration service that allows you to create data-driven workflows for orchestrating data movement and transforming data at scale. Using Azure Data Factory, you can create and schedule data-driven workflows (called pipelines) that can ingest data from disparate data stores. You can build complex ETL processes that transform data visually with data flows or by using compute services such as Azure HDInsight Hadoop, Azure Databricks, and Azure SQL Database.