AZ-900 : Microsoft Azure Fundamentals : Part 08
AZ-900 : Microsoft Azure Fundamentals : Part 08
-
You have an Azure environment that contains 10 virtual networks and 100 virtual machines.
You need to limit the amount of inbound traffic to all the Azure virtual networks.
What should you create?
- one application security group (ASG)
- 10 virtual network gateways
- 10 Azure ExpressRoute circuits
- one Azure firewall
Explanation:
You can restrict traffic to multiple virtual networks with a single Azure firewall.
Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It’s a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability.
You can centrally create, enforce, and log application and network connectivity policies across subscriptions and virtual networks. Azure Firewall uses a static public IP address for your virtual network resources allowing outside firewalls to identify traffic originating from your virtual network. -
This question requires that you evaluate the underlined text to determine if it is correct.
Azure Key Vault is used to store secrets for Azure Active Directory (Azure AD) user accounts.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed”. If the statement is incorrect, select the answer choice that makes the statement correct.
- No change is needed
- Azure Active Directory (Azure AD) administrative accounts
- Personally Identifiable Information (PII)
- server applications
Explanation:
Key Vault is designed to store configuration secrets for server apps. It’s not intended for storing data belonging to your app’s users, and it shouldn’t be used in the client-side part of an app.
-
Your company plans to automate the deployment of servers to Azure.
Your manager is concerned that you may expose administrative credentials during the deployment.
You need to recommend an Azure solution that encrypts the administrative credentials during the deployment.
What should you include in the recommendation?
- Azure Key Vault
- Azure Information Protection
- Azure Security Center
- Azure Multi-Factor Authentication (MFA)
Explanation:Azure Key Vault is a secure store for storage various types of sensitive information. In this question, we would store the administrative credentials in the Key Vault. With this solution, there is no need to store the administrative credentials as plain text in the deployment scripts.
All information stored in the Key Vault is encrypted.
Azure Key Vault can be used to Securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets.
Secrets and keys are safeguarded by Azure, using industry-standard algorithms, key lengths, and hardware security modules (HSMs). The HSMs used are Federal Information Processing Standards (FIPS) 140-2 Level 2 validated.Access to a key vault requires proper authentication and authorization before a caller (user or application) can get access. Authentication establishes the identity of the caller, while authorization determines the operations that they are allowed to perform.
-
You plan to deploy several Azure virtual machines.
You need to control the ports that devices on the Internet can use to access the virtual machines.
What should you use?
- a network security group (NSG)
- an Azure Active Directory (Azure AD) role
- an Azure Active Directory group
- an Azure key vault
Explanation:A network security group works like a firewall. You can attach a network security group to a virtual network and/or individual subnets within the virtual network. You can also attach a network security group to a network interface assigned to a virtual machine. You can use multiple network security groups within a virtual network to restrict traffic between resources such as virtual machines and subnets.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
-
HOTSPOT
To complete the sentence, select the appropriate option in the answer area.

AZ-900 Microsoft Azure Fundamentals Part 08 Q05 076 Question 
AZ-900 Microsoft Azure Fundamentals Part 08 Q05 076 Answer Explanation:When you create a virtual machine, the default setting is to create a Network Security Group attached to the network interface assigned to a virtual machine.
A network security group works like a firewall. You can attach a network security group to a virtual network and/or individual subnets within the virtual network. You can also attach a network security group to a network interface assigned to a virtual machine. You can use multiple network security groups within a virtual network to restrict traffic between resources such as virtual machines and subnets.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
In this question, we need to add a rule to the network security group to allow the connection to the virtual machine on port 8080.
-
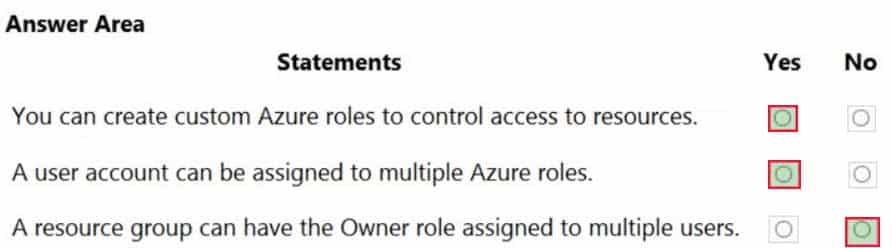
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
AZ-900 Microsoft Azure Fundamentals Part 08 Q06 077 Question -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
Solution: You modify a network security group (NSG).
Does this meet the goal?
- Yes
- No
Explanation:A network security group works like a firewall. You can attach a network security group to a virtual network and/or individual subnets within the virtual network. You can also attach a network security group to a network interface assigned to a virtual machine. You can use multiple network security groups within a virtual network to restrict traffic between resources such as virtual machines and subnets.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
In this question, we need to add a rule to the network security group to allow the connection to the virtual machine on port 80 (HTTP).
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
Solution: You modify a DDoS protection plan.
Does this meet the goal?
- Yes
- No
Explanation:DDoS is a form of attack on a network resource. A DDoS protection plan is used to protect against DDoS attacks; it does not provide connectivity to a virtual machine.
To ensure that a virtual machine named VM1 is accessible from the Internet over HTTP, you need to modify a network security group or Azure Firewall.
-
You need to collect and automatically analyze security events from Azure Active Directory (Azure AD).
What should you use?
- Azure Sentinel
- Azure Synapse Analytics
- Azure AD Connect
- Azure Key Vault
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
Solution: You modify an Azure firewall.
Does this meet the goal?
- Yes
- No
Explanation:Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It’s a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability.
In this question, we need to add a rule to Azure Firewall to allow the connection to the virtual machine on port 80 (HTTP).
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
Solution: You modify an Azure Traffic Manager profile.
Does this meet the goal?
- Yes
- No
Explanation:Azure Traffic Manager is a DNS-based load balancing solution. It is not used to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
To ensure that a virtual machine named VM1 is accessible from the Internet over HTTP, you need to modify a network security group or Azure Firewall.
In this question, we need to add a rule to a network security group or Azure Firewall to allow the connection to the virtual machine on port 80 (HTTP).
-
Your company plans to deploy several web servers and several database servers to Azure.
You need to recommend an Azure solution to limit the types of connections from the web servers to the database servers.
What should you include in the recommendation?
- network security groups (NSGs)
- Azure Service Bus
- a local network gateway
- a route filter
Explanation:A network security group works like a firewall. You can attach a network security group to a virtual network and/or individual subnets within the virtual network. You can also attach a network security group to a network interface assigned to a virtual machine. You can use multiple network security groups within a virtual network to restrict traffic between resources such as virtual machines and subnets.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
-
HOTSPOT
To complete the sentence, select the appropriate option in the answer area.

AZ-900 Microsoft Azure Fundamentals Part 08 Q13 078 Question 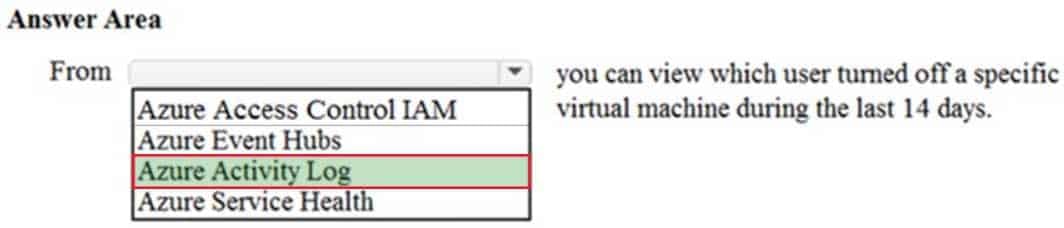
AZ-900 Microsoft Azure Fundamentals Part 08 Q13 078 Answer Explanation:You would use the Azure Activity Log, not Access Control to view which user turned off a specific virtual machine during the last 14 days.
Activity logs are kept for 90 days. You can query for any range of dates, as long as the starting date isn’t more than 90 days in the past.
In this question, we would create a filter to display shutdown operations on the virtual machine in the last 14 days.
-
Which service provides network traffic filtering across multiple Azure subscriptions and virtual networks?
- Azure Firewall
- an application security group
- Azure DDoS protection
- a network security group (NSG)
Explanation:You can restrict traffic to multiple virtual networks in multiple subscriptions with a single Azure firewall.
Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It’s a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability.
You can centrally create, enforce, and log application and network connectivity policies across subscriptions and virtual networks. Azure Firewall uses a static public IP address for your virtual network resources allowing outside firewalls to identify traffic originating from your virtual network. -
Which Azure service should you use to store certificates?
- Azure Security Center
- an Azure Storage account
- Azure Key Vault
- Azure Information Protection
Explanation:Azure Key Vault is a secure store for storage various types of sensitive information including passwords and certificates.
Azure Key Vault can be used to Securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets.
Secrets and keys are safeguarded by Azure, using industry-standard algorithms, key lengths, and hardware security modules (HSMs). The HSMs used are Federal Information Processing Standards (FIPS) 140-2 Level 2 validated.Access to a key vault requires proper authentication and authorization before a caller (user or application) can get access. Authentication establishes the identity of the caller, while authorization determines the operations that they are allowed to perform.
-
Which Azure service can you use as a security information and event management (SIEM) solution?
- Azure Analysis Services
- Azure Sentinel
- Azure Information Protection
- Azure Cognitive Services
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-900 Microsoft Azure Fundamentals Part 08 Q17 079 Question -
DRAG DROP
Match the Azure Services service to the correct descriptions.
Instructions: To answer, drag the appropriate service from the column on the left to its description on the right. Each service may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
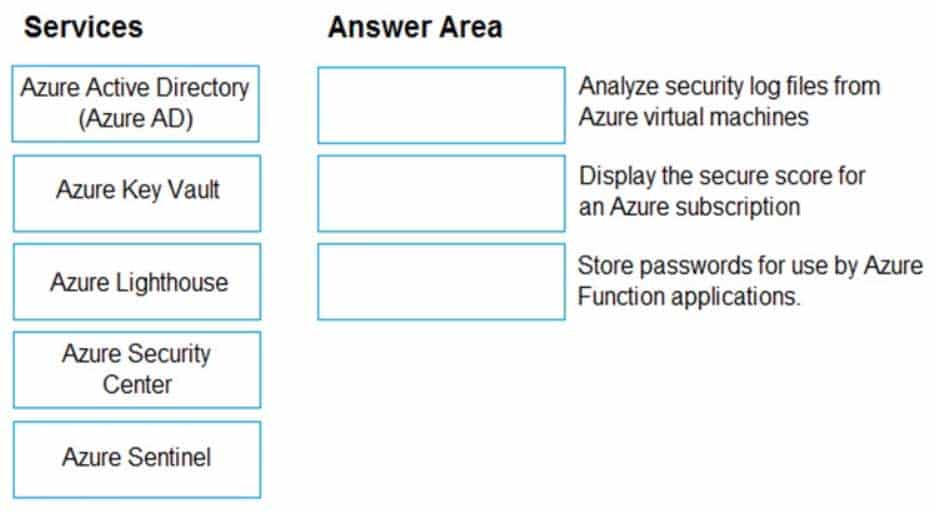
AZ-900 Microsoft Azure Fundamentals Part 08 Q18 080 Question 
AZ-900 Microsoft Azure Fundamentals Part 08 Q18 080 Answer Explanation:Box 1: Azure Sentinel
Box 2: Azure Security Center
Box 3: Azure Key Vault
Incorrect Answer:
– Azure Active Directory (Azure AD)
Azure AD is an identity and access management service, which helps your employees sign in and access resources– Azure Lighthouse
Azure Lighthouse is used for cross- and multi-tenant management. -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-900 Microsoft Azure Fundamentals Part 08 Q19 081 Question 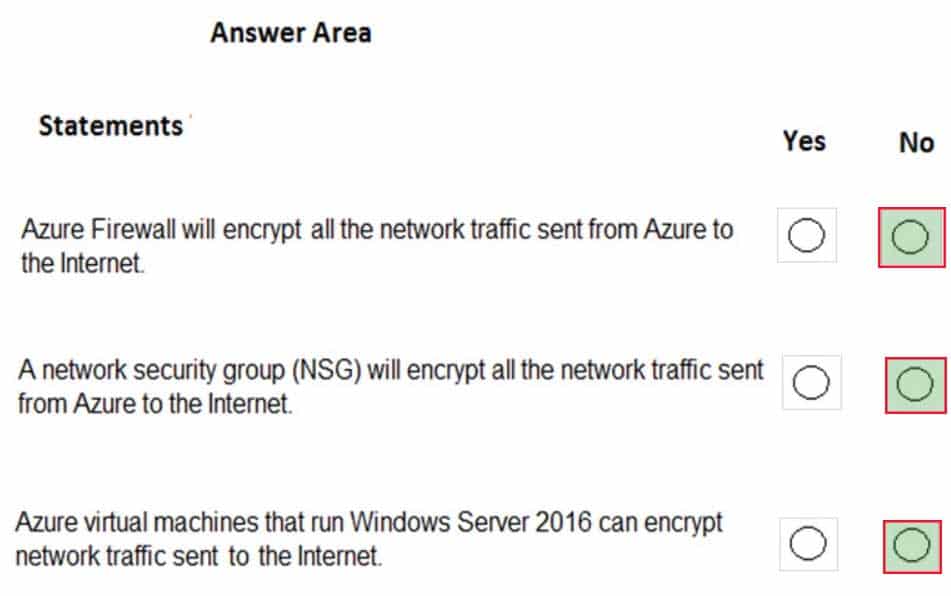
AZ-900 Microsoft Azure Fundamentals Part 08 Q19 081 Answer Explanation:Box 1: No
Azure firewall does not encrypt network traffic. It is used to block or allow traffic based on source/destination IP address, source/destination ports and protocol.Box 2: No
A network security group does not encrypt network traffic. It works in a similar way to a firewall in that it is used to block or allow traffic based on source/destination IP address, source/destination ports and protocol.Box 3: No
The question is rather vague as it would depend on the configuration of the host on the Internet. Windows Server does come with a VPN client and it also supports other encryption methods such IPSec encryption or SSL/TLS so it could encrypt the traffic if the Internet host was configured to require or accept the encryption. However, the VM could not encrypt the traffic to an Internet host that is not configured to require the encryption. -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

AZ-900 Microsoft Azure Fundamentals Part 08 Q20 082 Question 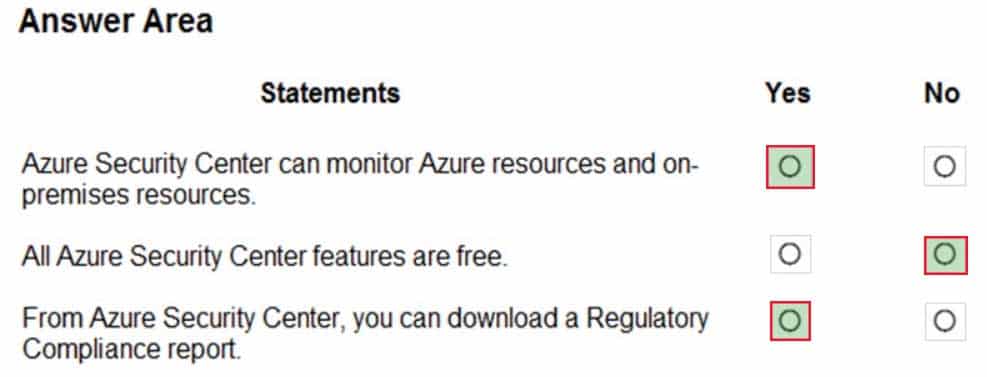
AZ-900 Microsoft Azure Fundamentals Part 08 Q20 082 Answer Explanation:Box 1: Yes
Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers, and provides advanced threat protection across your hybrid workloads in the cloud – whether they’re in Azure or not – as well as on premises.Box 2: No
Only two features: Continuous assessment and security recommendations, and Azure secure score, are free.Box 3: Yes
The advanced monitoring capabilities in Security Center also let you track and manage compliance and governance over time. The overall compliance provides you with a measure of how much your subscriptions are compliant with policies associated with your workload.