MD-101 : Managing Modern Desktops : Part 14
MD-101 : Managing Modern Desktops : Part 14
-
Your company implements Microsoft Azure Active Directory (Azure AD), Microsoft 365, Microsoft Intune, and Azure Information Protection.
The company’s security policy states the following:
– Personal devices do not need to be enrolled in Intune.
– Users must authenticate by using a PIN before they can access corporate email data.
– Users can use their personal iOS and Android devices to access corporate cloud services.
– Users must be prevented from copying corporate email data to a cloud storage service other than Microsoft OneDrive for Business.You need to configure a solution to enforce the security policy.
What should you create?
- a data loss prevention (DLP) policy from the Microsoft 365 Compliance admin center
- an insider risk management policy from the Microsoft 365 Compliance admin center
- an app protection policy from the Endpoint Management admin center
- a device configuration profile from the Endpoint Management admin center
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has an Azure Active Directory (Azure AD) tenant named contoso.com that contains several Windows 10 devices.
When you join new Windows 10 devices to contoso.com, users are prompted to set up a four-digit pin.
You need to ensure that the users are prompted to set up a six-digit pin when they join the Windows 10 devices to contoso.com.
Solution: From the Azure Active Directory admin center, you configure the Authentication methods.
Does this meet the goal?
- Yes
- No
Explanation:
Instead, from the Azure Active Directory admin center, you configure automatic mobile device management (MDM) enrollment. From the Endpoint Management admin center, you configure the Windows Hello for Business enrollment options. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has an Azure Active Directory (Azure AD) tenant named contoso.com that contains several Windows 10 devices.
When you join new Windows 10 devices to contoso.com, users are prompted to set up a four-digit pin.
You need to ensure that the users are prompted to set up a six-digit pin when they join the Windows 10 devices to contoso.com.
Solution: From the Azure Active Directory admin center, you configure automatic mobile device management (MDM) enrollment. From the Endpoint Management admin center, you configure the Windows Hello for Business enrollment options.
Does this meet the goal?
- Yes
- No
Explanation:Hello for Business is an alternative sign-in method that uses Active Directory or an Azure Active Directory account to replace a password, smart card, or a virtual smart card. It lets you use a user gesture to sign in, instead of a password. A user gesture might be a PIN, biometric authentication such as Windows Hello, or an external device such as a fingerprint reader.
Intune integrates with Hello for Business in two ways:
– An Intune policy can be created under Device enrollment. This policy targets the entire organization (tenant-wide). It supports the Windows AutoPilot out-of-box-experience (OOBE) and is applied when a device enrolls.
– An identity protection profile can be created under Device configuration. This profile targets assigned users and devices, and is applied during check-in. -
You enable controlled folder access in audit mode for several computers that run Windows 10.
You need to review the events audited by controlled folder access.
Which Event Viewer log should you view?
- Applications and Services\Microsoft\Windows\Windows Defender\Operational
- Windows\Security
- Applications and Services\Microsoft\Windows\Known Folders\Operational
-
HOTSPOT
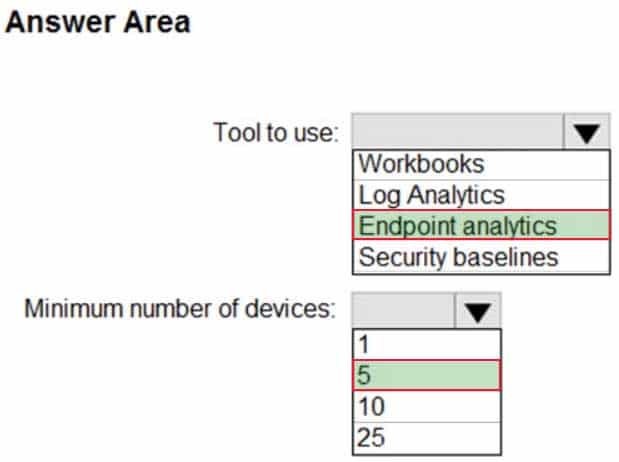
You have a Microsoft 365 tenant that uses Microsoft Intune.
From the Microsoft Endpoint Manager admin center, you plan to create a baseline to monitor the Startup score and the App reliability score of enrolled Windows 10 devices.
You need to identify which tool to use to create the baseline and the minimum number of devices required to create the baseline.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
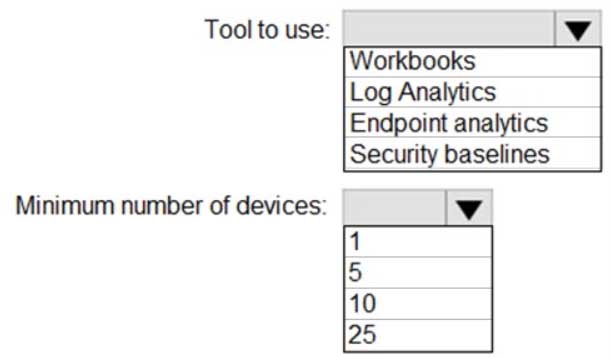
MD-101 Managing Modern Desktops Part 14 Q05 203 Question -
Your company has a Microsoft 365 tenant.
Users sign in to Windows 10 devices by using their Microsoft 365 account.
On a computer, you open Sync your settings as shown in the exhibit. (Click the Exhibit tab.)
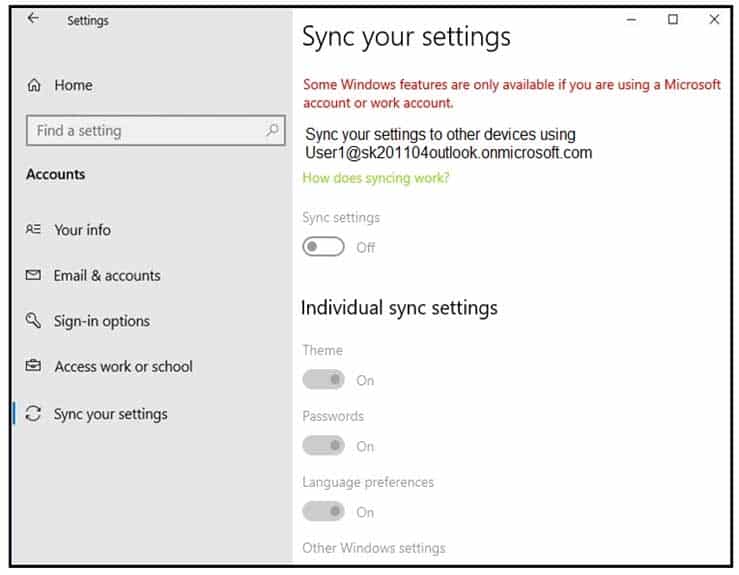
MD-101 Managing Modern Desktops Part 14 Q06 204 You need to set Sync settings to On.
What should you do?
- Enable User Experience Virtualization (UE-V).
- Enable Windows Mobility Center.
- Disable Windows Hello for Business.
- Enable Enterprise State Roaming.
-
HOTSPOT
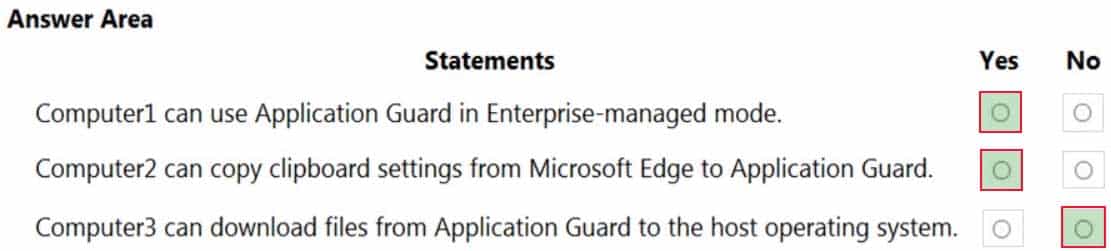
Your network contains an Active Directory domain. The domain contains the computers shown in the following table.
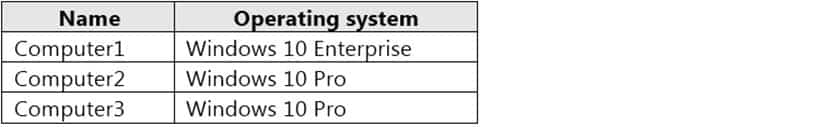
MD-101 Managing Modern Desktops Part 14 Q07 205 Microsoft Defender Application Guard is installed on the computers.
Application Guard Group Policy settings are applied to the computers as shown in the following table.
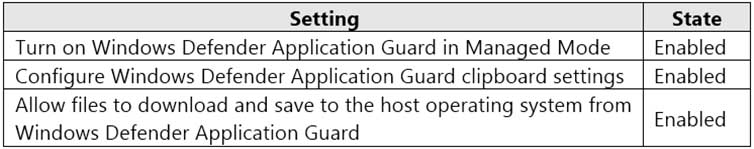
MD-101 Managing Modern Desktops Part 14 Q07 206 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
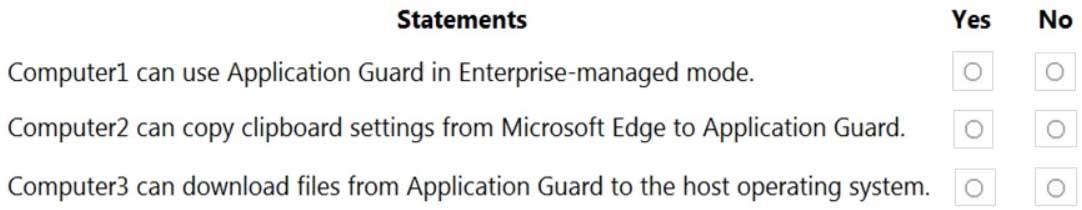
MD-101 Managing Modern Desktops Part 14 Q07 207 Question -
You have a Microsoft 365 tenant that contains the Windows 10 devices shown in the following table.
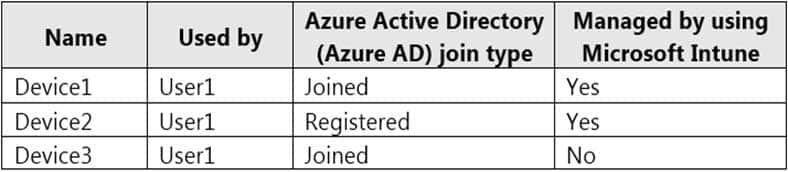
MD-101 Managing Modern Desktops Part 14 Q08 207a You enable Enterprise State Roaming.
You need to ensure that User1 can sync Windows settings across the devices.
What should you do?
- Remove Device1 and Device2 from Intune.
- Join Device2 to Azure AD.
- Add a Microsoft account to each device.
- Enroll Device3 in Intune.
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and branch offices in Seattle and New York.
Contoso has a Microsoft 365 E5 subscription.
Environment
Network Environment
The network contains an on-premises Active Directory domain named contoso.com. The domain contains the servers shown in the following table.
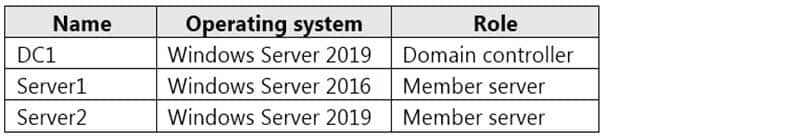
MD-101 Managing Modern Desktops Part 14 Q09 208 Contoso has a hybrid Azure Active Directory (Azure AD) tenant named contoso.com.
Contoso has a Microsoft Store for Business instance.
Users and Groups
The contoso.com tenant contains the users shown in the following table.
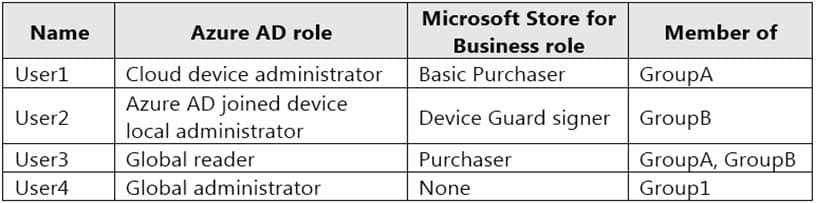
MD-101 Managing Modern Desktops Part 14 Q09 209 All users are assigned a Microsoft Office 365 license and an Enterprise Mobility + Security E3 license.
Enterprise State Roaming is enabled for Group1 and GroupA.
Group1 and Group2 have a Membership type of Assigned.
Devices
Contoso has the Windows 10 devices shown in the following table.
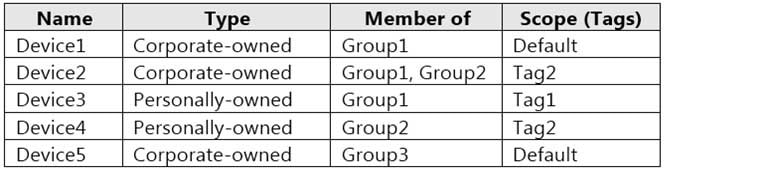
MD-101 Managing Modern Desktops Part 14 Q09 210 The Windows 10 devices are joined to Azure AD and enrolled in Microsoft Intune.
The Windows 10 devices are configured as shown in the following table.
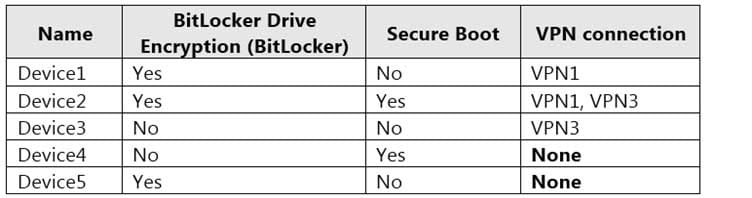
MD-101 Managing Modern Desktops Part 14 Q09 211 All the Azure AD joined devices have an executable file named C:\AppA.exe and a folder named D:\Folder1.
Microsoft Endpoint Manager Configuration
Microsoft Endpoint Manager has the compliance policies shown in the following table.
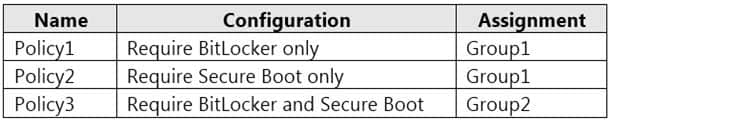
MD-101 Managing Modern Desktops Part 14 Q09 212 The Compliance policy settings are shown in the following exhibit.
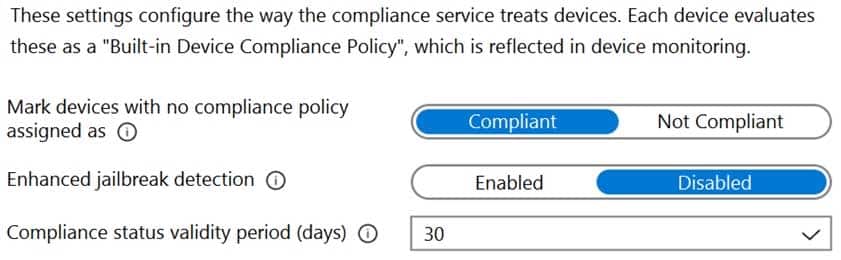
MD-101 Managing Modern Desktops Part 14 Q09 213 The Automatic Enrollment settings have the following configurations:
– MDM user scope: GroupA
– MAM user scope: GroupBYou have an Endpoint protection configuration profile that has the following Controlled folder access settings:
– Name: Protection1
– Folder protection: Enable
– List of apps that have access to protected folders: C:\*\AppA.exe
– List of additional folders that need to be protected: D:\Folder1
– Assignments:
– Included groups: Group2, GroupBWindows Autopilot Configuration
Contoso has a Windows Autopilot deployment profile configured as shown in the following exhibit.
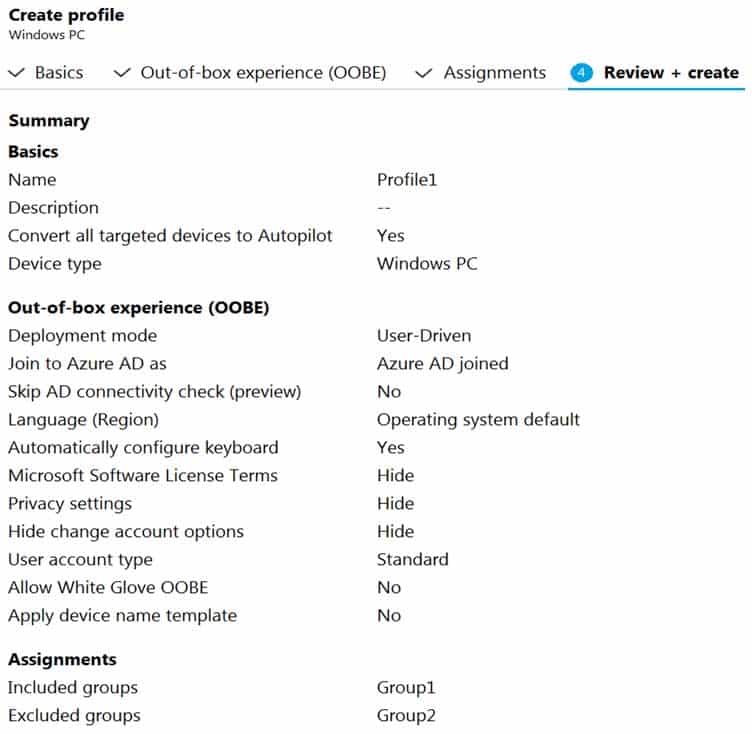
MD-101 Managing Modern Desktops Part 14 Q09 214 Currently, there are no devices deployed by using Window Autopilot.
The Intune connector for Active Directory is installed on Server1.
Requirements
Planned Changes
Contoso plans to implement the following changes:
– Purchase a new Windows 10 device named Device6 and enroll the device in Intune.
– New computers will be deployed by using Windows Autopilot and will be hybrid Azure AD joined.
– Deploy a network boundary configuration profile that will have the following settings:
– Name: Boundary1
– Network boundary: 192.168.1.0/24
– Scope tags: Tag1
– Assignments:
– – Included groups: Group1, Group2– Deploy two VPN configuration profiles named Connection1 and Connection2 that will have the following settings:
– Name: Connection1
– Connection name: VPN1
– Connection type: L2TP
– Assignments:
– – Included groups: Group1, Group2, GroupA
– – Excluded groups: —– Name: Connection2
– Connection name: VPN2
– Connection type: IKEv2
– Assignments:
– – Included groups: GroupA
– – Excluded groups: GroupB– Purchase an app named App1 that is available in Microsoft Store for Business and to assign the app to all the users.
Technical Requirements
Contoso must meet the following technical requirements:
– Users in GroupA must be able to deploy new computers.
– Administrative effort must be minimized.-
Which users can purchase and assign App1?
- User3 only
- User1 and User3 only
- User1, User2, User3, and User4
- User1, User3, and User4 only
- User3 and User4 only
-
- This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.General Overview
Litware, Inc. is an international manufacturing company that has 3,000 employees. The company has sales, marketing, research, human resources (HR), development, and IT departments.
Litware has two main offices in New York and Los Angeles. Litware has five branch offices in Asia.
Existing Environment
Current Business Model
The Los Angeles office has 500 developers. The developers work flexible hours ranging from 11 AM to 10 PM.
Litware has a Microsoft Endpoint Configuration Manager deployment.
During discovery, the company discovers a process where users are emailing bank account information of its customers to internal and external recipients.
Current Environment
The network contains an Active Directory domain that is synced to Microsoft Azure Active Directory (Azure AD). The functional level of the forest and the domain is Windows Server 2012 R2. All domain controllers run Windows Server 2012 R2.
Litware has the computers shown in the following table.
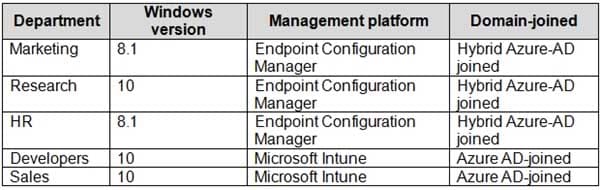
MD-101 Managing Modern Desktops Part 14 Q10 215 The development department uses projects in Azure DevOps to build applications.
Most of the employees in the sales department are contractors. Each contractor is assigned a computer that runs Windows 10. At the end of each contract, the computer is assigned to a different contractor. Currently, the computers are re-provisioned manually by the IT department.
Problem Statements
Litware identifies the following issues on the network:
– Employees in sales department computers is too time the Los Angeles office report slow Internet performance when updates are downloading. The employees also report that the updates frequently consume considerable resources when they are installed. The Update settings are configured as shown in the Updates exhibit. (Click the Updates button.)
– Management suspects that the source code for the proprietary applications in Azure DevOps in being shared externally.
Re-provisioning theconsuming.Requirements
Business Goals
Litware plans to transition to co-management for all the company-owned Windows 10 computers. Whenever possible, Litware wants to minimize hardware and software costs.
Device Management Requirements
Litware identifies the following device management requirements:
– Prevent the sales department employees from forwarding email that contains bank account information.
– Ensure that Microsoft Edge Favorites are accessible from all computers to which the developers sign in.
– Prevent employees in the research department from copying patented information from trusted applications to untrusted applications.Technical Requirements
Litware identifies the following technical requirements for the planned deployment:
– Re-provision the sales department computers by using Windows AutoPilot.
– Ensure that the projects in Azure DevOps can be accessed from the corporate network only.
– Ensure that users can sign in to the Azure AD-joined computers by using a PIN. The PIN must expire every 30 days.
– Ensure that the company name and logo appears during the Out of Box Experience (OOBE) when using Windows AutoPilot.Exhibits
Updates
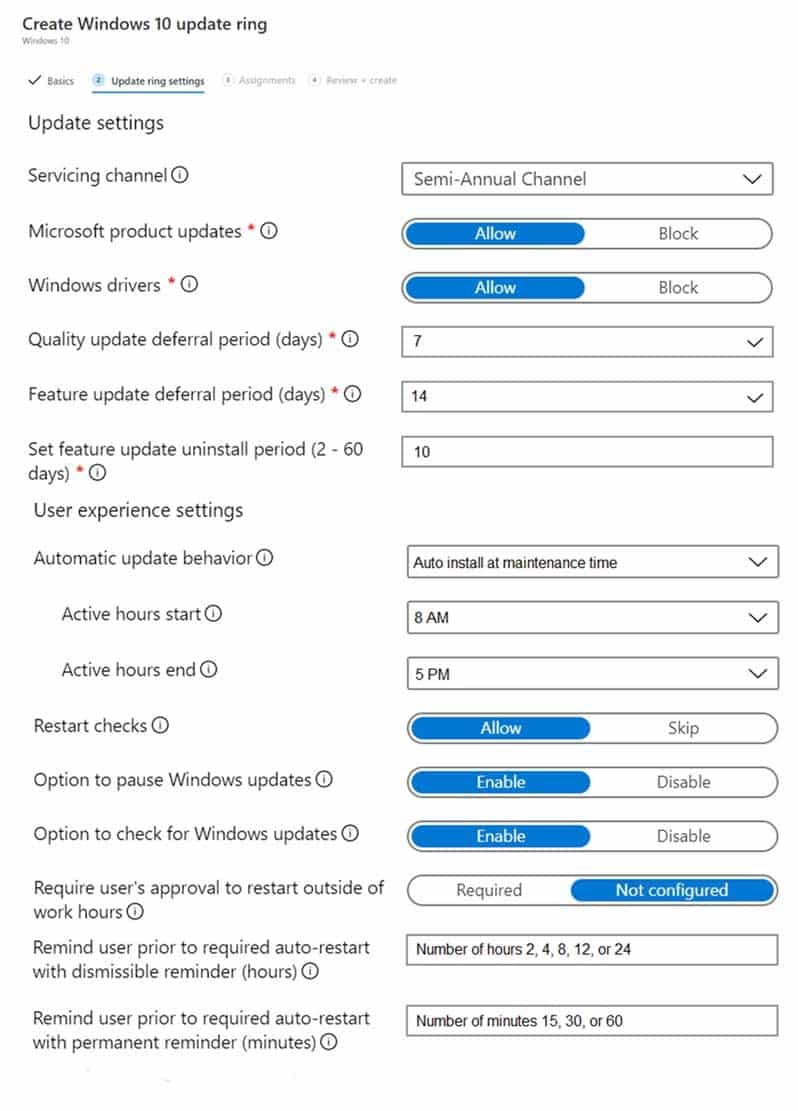
MD-101 Managing Modern Desktops Part 14 Q10 216 -
HOTSPOT
You need to recommend a solution to meet the device management requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
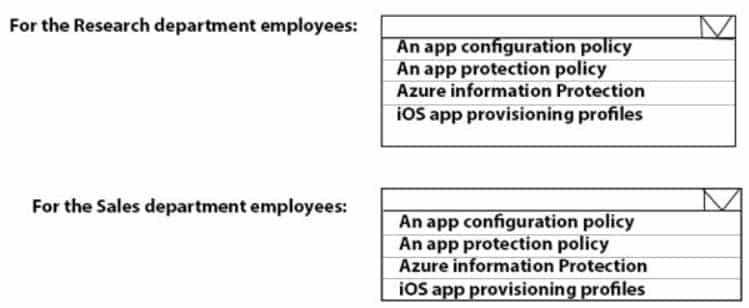
MD-101 Managing Modern Desktops Part 14 Q10 217 Question 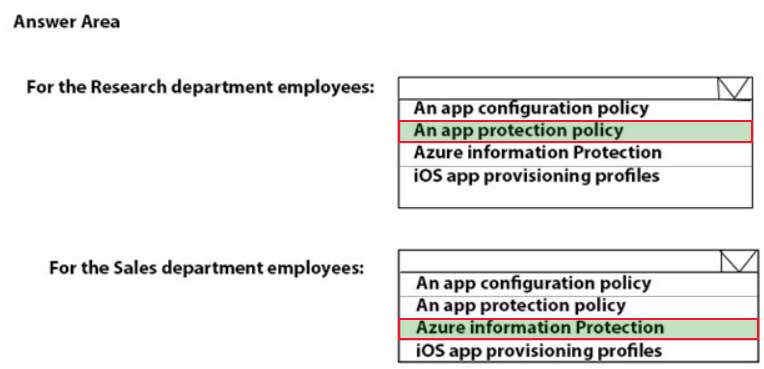
MD-101 Managing Modern Desktops Part 14 Q10 217 Answer Explanation:Explanation:
From the scenario:
Litware identifies the following device management requirements:– Prevent the sales department employees from forwarding email that contains bank account information.
– Ensure that Microsoft Edge Favorites are accessible from all computers to which the developers sign in.
– Prevent employees in the research department from copying patented information from trusted applications to untrusted applications.Box 1:
Employees in the research department must be prevented from copying patented information from trusted applications to untrusted applications. This requires an App protection policy.– App protection policies make sure that the app-layer protections are in place. For example, you can:
– Require a PIN to open an app in a work context
– Control the sharing of data between apps
– Prevent the saving of company app data to a personal storage locationBox 2:
Employees in the sales department must be prevented from forwarding email that contains bank account information.– Azure Information Protection is a cloud-based solution that helps an organization to classify and optionally, protect its documents and emails by applying labels. Labels can be applied automatically by administrators who define rules and conditions, manually by users, or a combination where users are given recommendations.
-
- This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
Contoso, Ltd., is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
Contoso has the users and computers shown in the following table.
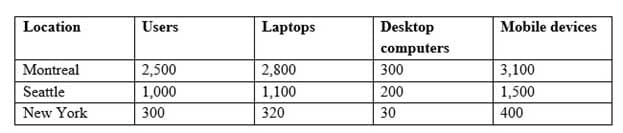
MD-101 Managing Modern Desktops Part 14 Q11 218 The company has IT, human resources (HR), legal (LEG), marketing (MKG) and finance (FIN) departments.
Contoso uses Microsoft Store for Business and recently purchased a Microsoft 365 subscription.
The company is opening a new branch office in Phoenix. Most of the users in the Phoenix office will work from home.
Existing Environment
The network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD).All member servers run Windows Server 2016. All laptops and desktop computers run Windows 10 Enterprise.
The computers are managed by using Microsoft Endpoint Configuration Manager. The mobile devices are managed by using Microsoft Intune.
The naming convention for the computers is the department acronym, followed by a hyphen, and then four numbers, for example, FIN-6785. All the computers are joined to the on-premises Active Directory domain.
Each department has an organizational unit (OU) that contains a child OU named Computers. Each computer account is in the Computers OU of its respective department.
Intune Configuration
The domain has the users shown in the following table.
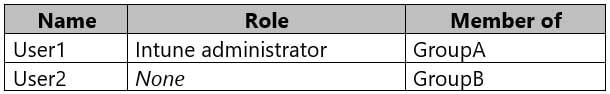
MD-101 Managing Modern Desktops Part 14 Q11 219 User2 is a device enrollment manager (DEM) in Intune.
The devices enrolled in Intune are shown in the following table.
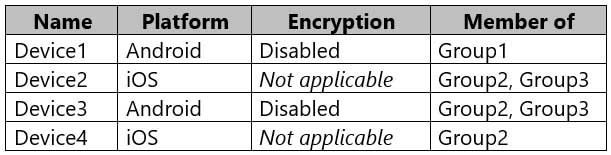
MD-101 Managing Modern Desktops Part 14 Q11 220 The device compliance policies in Intune are configured as shown in the following table.
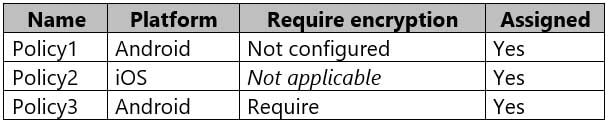
MD-101 Managing Modern Desktops Part 14 Q11 221 The device compliance policies have the assignments shown in the following table.
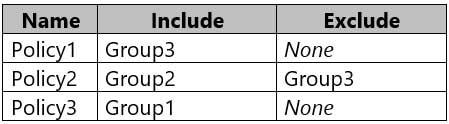
MD-101 Managing Modern Desktops Part 14 Q11 222 The device limit restrictions in Intune are configured as shown in the following table.
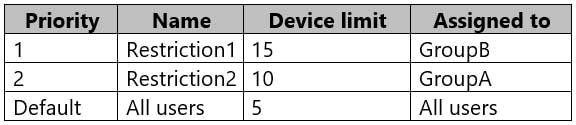
MD-101 Managing Modern Desktops Part 14 Q11 223 Requirements
Planned Changes
Contoso plans to implement the following changes:– Provide new computers to the Phoenix office users. The new computers have Windows 10 Pro preinstalled and were purchased already.
– Start using a free Microsoft Store for Business app named App1.
– Implement co-management for the computers.Technical Requirements
Contoso must meet the following technical requirements:– Ensure that the users in a group named Group4 can only access Microsoft Exchange Online from devices that are enrolled in Intune.
– Deploy Windows 10 Enterprise to the computers of the Phoenix office users by using Windows Autopilot.
– Monitor the computers in the LEG department by using Windows Analytics.
– Create a provisioning package for new computers in the HR department.
– Block iOS devices from sending diagnostic and usage telemetry data.
– Use the principle of least privilege whenever possible.
– Enable the users in the MKG department to use App1.
– Pilot co-management for the IT department.-
You need to meet the requirements for the MKG department users.
What should you do?
- Assign the MKG department users the Purchaser role in Microsoft Store for Business
- Download the APPX file for App1 from Microsoft Store for Business
- Add App1 to the private store
- Assign the MKG department users the Basic Purchaser role in Microsoft Store for Business
- Acquire App1 from Microsoft Store for Business
-
-
Your company has a main office and six branch offices. The branch offices connect to the main office by using a WAN link. All offices have a local Internet connection and a Hyper-V host cluster.
The company has a Microsoft Endpoint Configuration Manager deployment. The main office is the primary site. Each branch office has a distribution point.
All computers that run Windows 10 are managed by using both Configuration Manager and Microsoft Intune.
You plan to deploy the latest build of Microsoft Office 365 ProPlus to all the computers.
You need to minimize the amount of network traffic on the company’s Internet links for the planned deployment.
What should you include in the deployment plan?
- From Intune, configure app assignments for the Office 365 ProPlus suite. In each office, copy the Office 365 distribution files to a Microsoft Deployment Toolkit (MDT) deployment share.
- From Intune, configure app assignments for the Office 365 ProPlus suite. In each office, copy the Office 365 distribution files to a Configuration Manager distribution point.
- From Endpoint Configuration Manager, create an application deployment. In each office, copy the Office 365 distribution files to a Configuration Manager distribution point.
-
HOTSPOT
Your company has a computer named Computer1 that runs Windows 10 Pro.
The company develops a proprietary Universal Windows Platform (UWP) app named App1. App1 is signed with a certificate from a trusted certification authority (CA).
You need to sideload App1 to Computer1.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MD-101 Managing Modern Desktops Part 14 Q13 224 Question -
DRAG DROP
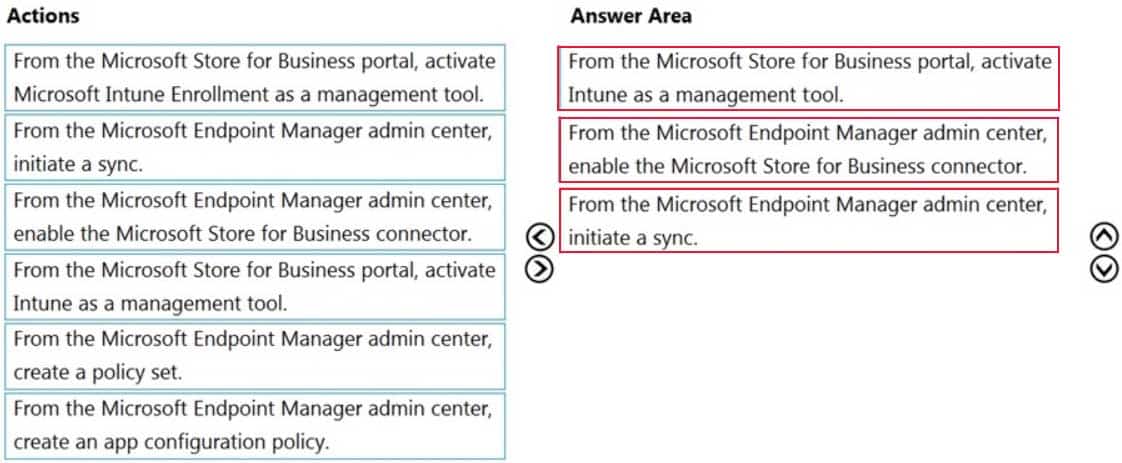
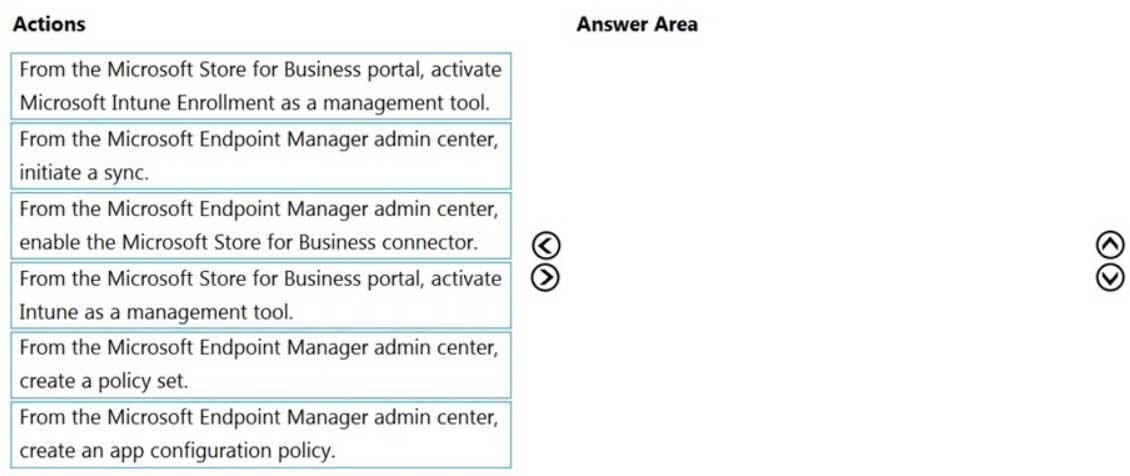
Your company uses Microsoft Intune. You have a Microsoft Store for Business account.
You need to ensure that you can deploy Microsoft Store for Business apps by using Intune.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
NOTE: More than one order of answer choices is correct. You will receive credit for any of the correct orders you select.
MD-101 Managing Modern Desktops Part 14 Q14 225 Question -
Your company has a Microsoft 365 subscription.
All the users in the finance department own personal devices that run iOS or Android. All the devices are enrolled in Microsoft Intune.
The finance department adds new users each month.
The company develops a mobile application named App1 for the finance department users.
You need to ensure that only the finance department users can download App1.
What should you do first?
- Add App1 to Intune.
- Add App1 to a Microsoft Deployment Toolkit (MDT) deployment share.
- Add App1 to Microsoft Store for Business.
- Add App1 to the vendor stores for iOS and Android applications.
-
HOTSPOT
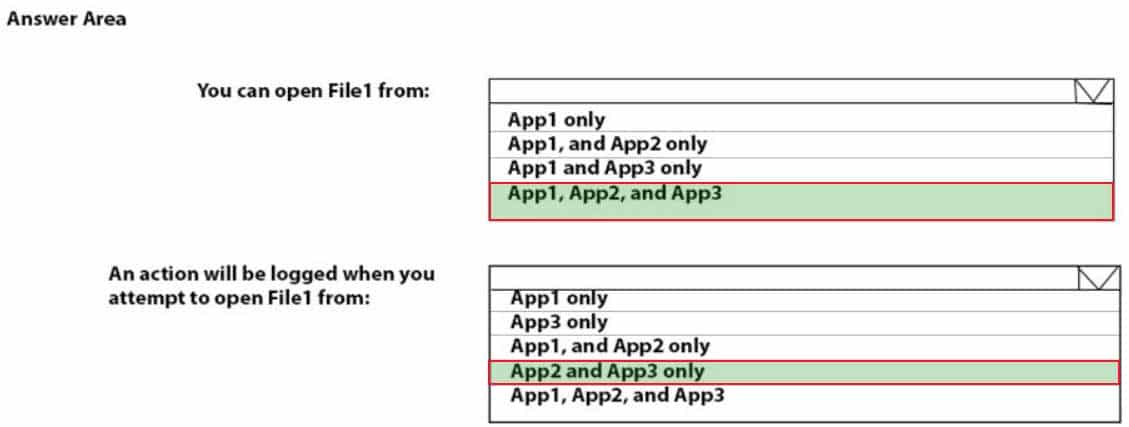
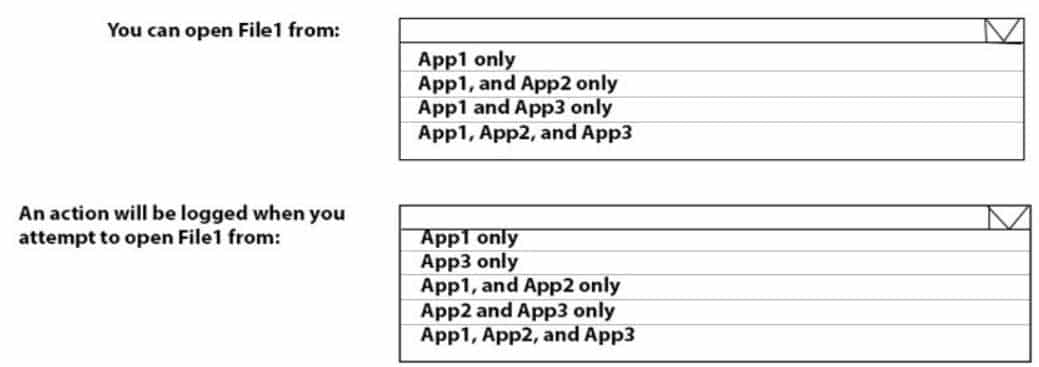
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. All Windows 10 devices have apps named App1, App2 and App3 installed and are enrolled in Microsoft Intune.
You configure the following settings in Windows Information Protection (WIP):
– Protected apps: App1
– Exempt apps: App2
– Windows Information Protection mode: SilentApp1, App2, and App3 use the same file format.
You create a file named File1 in App1.
You need to identify which apps can open File1.
What apps should you identify? To answer, select the appropriate options in the answer area,
NOTE: Each correct selection is worth one point.
MD-101 Managing Modern Desktops Part 14 Q16 226 Question -
You have devices enrolled in Microsoft Intune as shown in the following table.
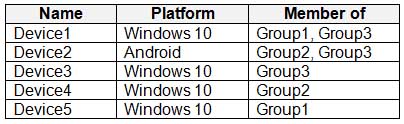
MD-101 Managing Modern Desktops Part 14 Q17 227 You create an app protection policy named Policy1 that has the following settings:
– Platform: Windows 10
– Protected apps: App1
– Exempt apps: App2
– Network boundary: Cloud resources, IPv4 rangesYou assign Policy1 to Group1 and Group2. You exclude Group3 from Policy1.
Which devices will apply Policy1?
- Device1, Device2, Device4, and Device5
- Device1, Device4, and Device5 only
- Device4 and Device5 only
- Device1, Device3, Device4 and Device5
Explanation:Intune device configuration profiles let you include and exclude groups from profile assignment. Exclusion takes precedence over inclusion in same group types.
Policy1 excludes Group3 and Group3 includes Device1, Device2, and Device3.
Incorrect Answers:
A, B, D: Device1, Device2, and Device3 are members of Group3. Policy1 excludes Group3. Exclusion takes precedence over inclusion. -
HOTSPOT
Your network contains an Active Directory domain that is synced to Microsoft Azure Active Directory (Azure AD).
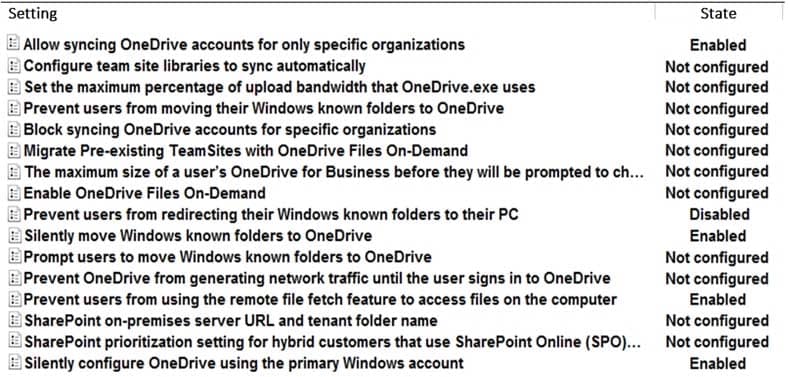
You have a Microsoft Office 365 subscription. All computers are joined to the domain and have the latest Microsoft OneDrive sync client (OneDrive.exe) installed.
On all the computers, you configure the OneDrive settings as shown in the following exhibit.
MD-101 Managing Modern Desktops Part 14 Q18 228 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
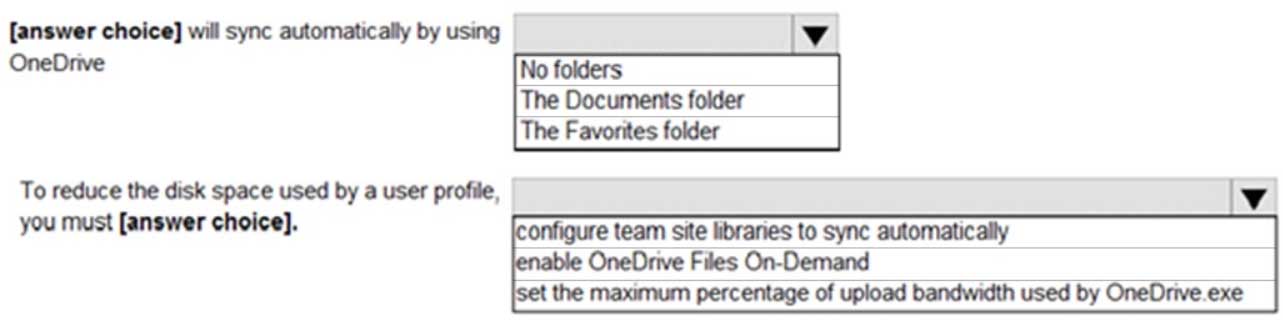
MD-101 Managing Modern Desktops Part 14 Q18 229 Question 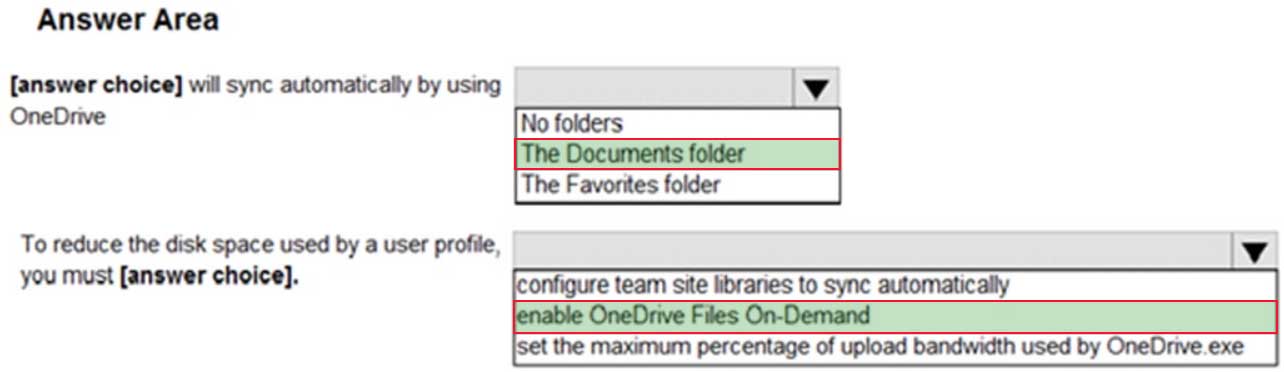
MD-101 Managing Modern Desktops Part 14 Q18 229 Answer Explanation:Box 1:
Silently move known folders to OneDrive is enabled. Known folder include:
Desktop, Documents, Pictures, Screenshots, and Camera RollBox 2:
OneDrive Files On-Demand enables users to view, search for, and interact with files stored in OneDrive from within File Explorer without downloading them and taking up space on the local hard drive. -
HOTSPOT
You have a Microsoft 365 subscription.
Users have iOS devices that are not enrolled in Microsoft 365 Device Management.
You create an app protection policy for the Microsoft Outlook app as shown in the exhibit. (Click the Exhibit tab.)
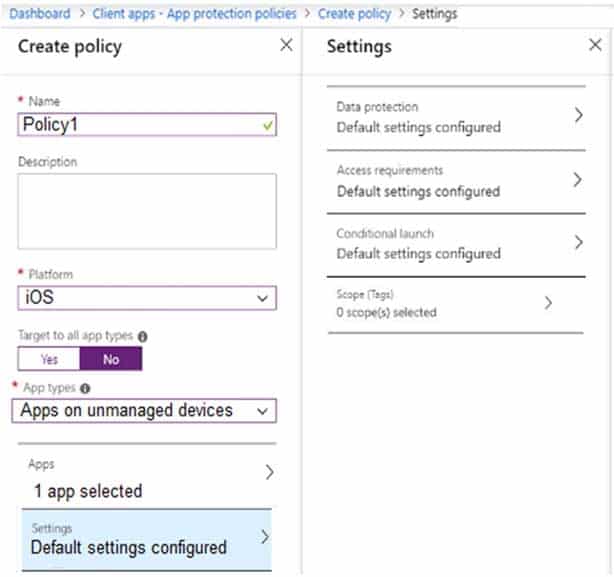
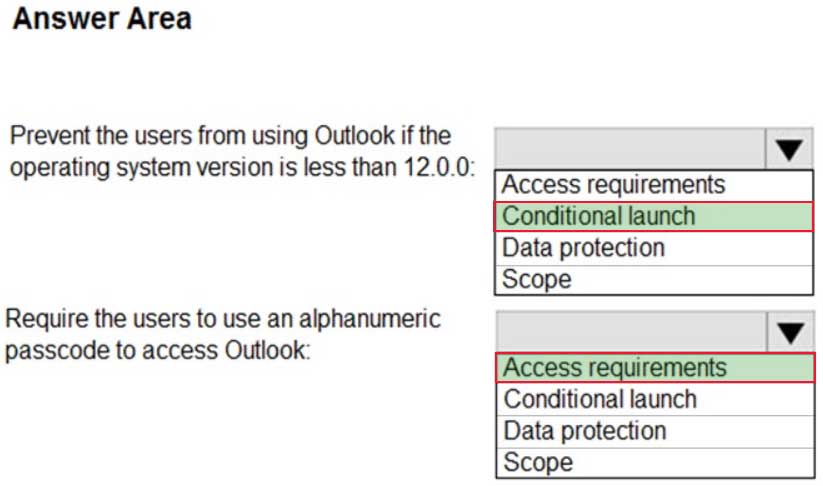
MD-101 Managing Modern Desktops Part 14 Q19 230 You need to configure the policy to meet the following requirements:
Prevent the users from using the Outlook app if the operating system version is less than 12.0.0.
Require the users to use an alphanumeric passcode to access the Outlook app.What should you configure in an app protection policy for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
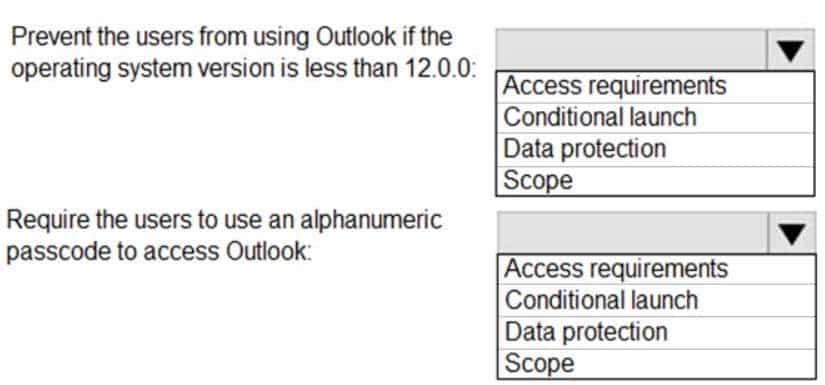
MD-101 Managing Modern Desktops Part 14 Q19 231 Question -
You manage a Microsoft 365 environment that has co-management enabled.
All computers run Windows 10 and are deployed by using the Microsoft Deployment Toolkit (MDT).
You need to recommend a solution to deploy Microsoft Office 365 ProPlus to new computers. The latest version must always be installed. The solution must minimize administrative effort.
What is the best tool to use for the deployment? More than one answer choice may achieve the goal. Select the BEST answer.
- Microsoft Intune
- Microsoft Deployment Toolkit
- Office Deployment Tool (ODT)
- a Group Policy object (GPO)
- Microsoft System Center Configuration Manager