MS-100 : Microsoft 365 Identity and Services : Part 04
MS-100 : Microsoft 365 Identity and Services : Part 04
-
Your company has a Microsoft 365 subscription.
You upload several archive PST files to Microsoft 365 by using the Security & Compliance admin center.
A month later, you attempt to run an import job for the PST files.
You discover that the PST files were deleted from Microsoft 365.
What is the most likely cause of the files being deleted? More than one answer choice may achieve the goal. Select the BEST answer.
- The PST files were corrupted and deleted by Microsoft 365 security features.
- PST files are deleted automatically from Microsoft 365 after 30 days.
- The size of the PST files exceeded a storage quota and caused the files to be deleted.
- Another administrator deleted the PST files.
Explanation:
You can use the Office 365 Import Service to bulk-import PST files to Office 365 mailboxes.
When you use the network upload method to import PST files, you upload them to an Azure blob container named ingestiondata. If there are no import jobs in progress on the Import page in the Security & Compliance Center), then all PST files in the ingestiondata container in Azure are deleted 30 days after the most recent import job was created in the Security & Compliance Center.
-
Your company has a main office and 20 branch offices in North America and Europe. Each branch connects to the main office by using a WAN link. All the offices connect to the Internet and resolve external host names by using the main office connections.
You plan to deploy Microsoft 365 and to implement a direct Internet connection in each office.
You need to recommend a change to the infrastructure to provide the quickest possible access to Microsoft 365 services.
What is the best recommendation to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.
- For all the client computers in the branch offices, modify the MTU setting by using a Group Policy object (GPO).
- In each branch office, deploy a proxy server that has user authentication enabled.
- In each branch office, deploy a firewall that has packet inspection enabled.
- In the branch offices, configure name resolution so that all queries for external host names are redirected to public DNS servers directly.
Explanation:Being a cloud service, Office 365 would be classed as an external host to the office computers.
All the offices connect to the Internet and resolve external host names by using the main office connections. This means that all branch office computers perform DNS lookups and connect to the Internet over the WAN link.
Each branch office will have a direct connection to the Internet so the quickest possible access to Microsoft 365 services would be by using the direct Internet connections. However, the DNS lookups would still go over the WAN links to main office. The solution to provide the quickest possible access to Microsoft 365 services is to configure DNS name resolution so that the computers use public DNS servers for external hosts. That way DNS lookups for Office 365 and the connections to Office 365 will use the direct Internet connections.
-
Your network contains an Active Directory forest named adatum.local. The forest contains 500 users and uses adatum.com as a UPN suffix.
You deploy a Microsoft 365 tenant.
You implement directory synchronization and sync only 50 support users.
You discover that five of the synchronized users have usernames that use a UPN suffix of onmicrosoft.com.
You need to ensure that all synchronized identities retain the UPN set in their on-premises user account.
What should you do?
- From the Microsoft 365 admin center, add adatum.com as a custom domain name.
- From Windows PowerShell, run the Set-ADDomain –AllowedDNSSuffixes adatum.com command.
- From Active Directory Users and Computers, modify the UPN suffix of the five user accounts.
- From the Microsoft 365 admin center, add adatum.local as a custom domain name.
Explanation:
The question states that only five of the synchronized users have usernames that use a UPN suffix of onmicrosoft.com. Therefore the other 45 users have the correct UPN suffix. This tells us that the adatum.com domain has already been added to Office 365 as a custom domain.
The forest is named adatum.local and uses adatum.com as a UPN suffix. User accounts in the domain will have adatum.local as their default UPN suffix. To use adatum.com as the UPN suffix, each user account will need to be configured to use adatum.com as the UPN suffix.
Any synchronized user account that has adatum.local as a UPN suffix will be configured to use a UPN suffix of onmicrosoft.com because adatum.local cannot be added to Office 365 as a custom domain.
Therefore, the reason that the five synchronized users have usernames with a UPN suffix of onmicrosoft.com is because their accounts were not configured to use the UPN suffix of contoso.com. -
HOTSPOT
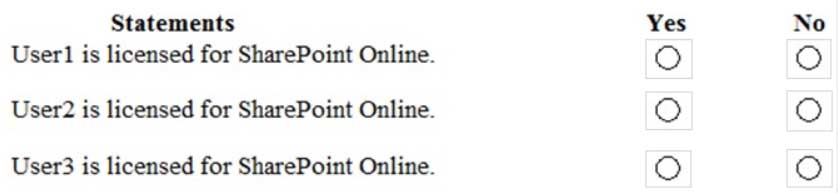
Your company has a Microsoft Office 365 subscription that contains the groups shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 04 Q04 004 You have the licenses shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 04 Q04 005 Another administrator removes User1 from Group1 and adds Group2 to Group1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
MS-100 Microsoft 365 Identity and Services Part 04 Q04 006 Question 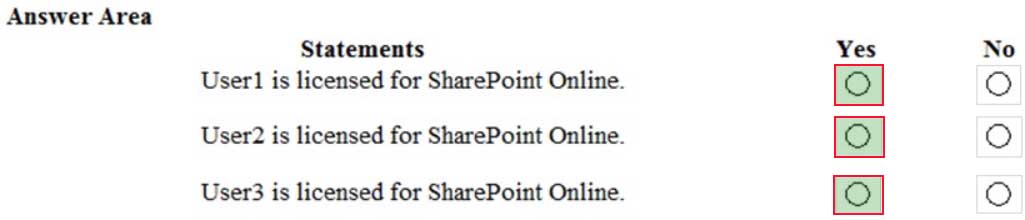
MS-100 Microsoft 365 Identity and Services Part 04 Q04 006 Answer Explanation:User1, User2 and User3 have each been assigned a SharePoint license directly. Therefore, they are all licensed for SharePoint Online.
Changing the group memberships will only affect whether or not they are licensed for Exchange Online because the Exchange Online licenses are assigned to Group1. -
Your company has on-premises servers and a Microsoft Azure Active Directory (Azure AD) tenant.
Several months ago, the Azure AD Connect Health agent was installed on all the servers.
You review the health status of all the servers regularly.
Recently, you attempted to view the health status of a server named Server1 and discovered that the server is NOT listed on the Azure Active Directory Connect Servers list.
You suspect that another administrator removed Server1 from the list.
You need to ensure that you can view the health status of Server1.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- From Windows PowerShell, run the
Register-AzureADConnectHealthSyncAgent cmdlet. - From Azure Cloud shell, run the Connect-AzureAD cmdlet.
- From Server1, change the Azure AD Connect Health services Startup type to Automatic (Delayed Start).
- From Server1, change the Azure AD Connect Health services Startup type to Automatic.
- From Server1, reinstall the Azure AD Connect Health agent.
Explanation:
question states that another administrator removed Server1 from the list. To view the health status of Server1, you need to re-register the AD Connect Health Sync Agent. You can do this manually by running the Register-AzureADConnectHealthSyncAgent cmdlet. Alternatively, you can reinstall the Azure AD Connect Health agent. The Azure AD Connect Health agent is registered as part of the installation. - From Windows PowerShell, run the
-
You have a Microsoft 365 subscription.
You suspect that several Microsoft Office 365 applications or services were recently updated.
You need to identify which applications or services were recently updated.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- From the Microsoft 365 admin center, review the Message center blade.
- From the Office 365 Admin mobile app, review the messages.
- From the Microsoft 365 admin center, review the Products blade.
- From the Microsoft 365 admin center, review the Service health blade.
Explanation:
The Message center in the Microsoft 365 admin center is where you would go to view a list of the features that were recently updated in the tenant. This is where Microsoft posts official messages with information including new and changed features, planned maintenance, or other important announcements.
The messages displayed in the Message center can also be viewed by using the Office 365 Admin mobile app. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has a Microsoft Office 365 tenant.
You suspect that several Office 365 features were recently updated.
You need to view a list of the features that were recently updated in the tenant.
Solution: You use Monitoring and reports from the Compliance admin center.
Does this meet the goal?
- Yes
- No
Explanation:Depending on what your organization’s Office 365 subscription includes, the Dashboard in Security & Compliance includes several widgets, such as Threat Management Summary, Threat Protection Status, Global Weekly Threat Detections, Malware, etc. The Compliance admin center in Microsoft 365 contains much of the same information but also includes additional entries focusing on alerts, data insights.
The Monitoring and reports section from the Compliance admin center does not display a list of the features that were recently updated in the tenant so this solution does not meet the goal.
To meet the goal, you need to use Message center in the Microsoft 365 admin center.
-
DRAG DROP
Your network contains an on-premises Active Directory domain named contoso.com that is synced to a Microsoft Azure Active Directory (Azure AD) tenant. The on-premises domain contains a server named Server1 that runs Windows Server 2016 and 200 client computers that run Windows 10.
Your company purchases a Microsoft 365 subscription.
On Server1, you create a file share named Share1. You extract the Microsoft Office Deployment Tool (ODT) to Share1.
You need to deploy Microsoft 365 Apps for enterprise and the French language pack from Share1 to the Windows 10 computers.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
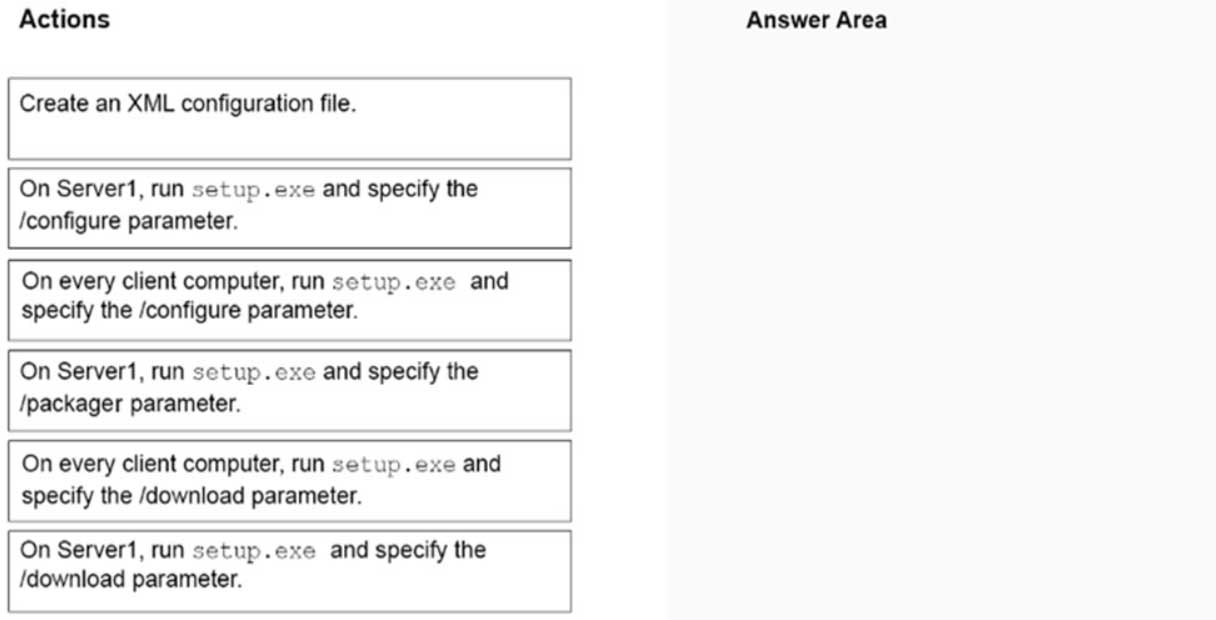
MS-100 Microsoft 365 Identity and Services Part 04 Q08 007 Question 
MS-100 Microsoft 365 Identity and Services Part 04 Q08 007 Answer Explanation:Note:
Step 1: Create an XML configuration file with the source path and download path for the installation files.
Step 2: On the deployment server, run the ODT executable in download mode and with a reference to the XML configuration file.
Step 3: Create another XML configuration file with the source path to the installation files.
Step 4: On the client computer, run the ODT executable in configure mode and with a reference to the XML configuration file. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD).
You manage Windows 10 devices by using Microsoft System Center Configuration Manager (Current Branch).
You configure a pilot for co-management.
You add a new device named Device1 to the domain. You install the Configuration Manager client on Device1.
You need to ensure that you can manage Device1 by using Microsoft Intune and Configuration Manager.
Solution: You add Device1 to an Active Directory group.
Does this meet the goal?
- Yes
- No
Explanation:
Device1 has the Configuration Manager client installed so you can manage Device1 by using Configuration Manager.
To manage Device1 by using Microsoft Intune, the device has to be enrolled in Microsoft Intune. In the Co-management Pilot configuration, you configure a Configuration Manager Device Collection that determines which devices are auto-enrolled in Microsoft Intune. You need to add Device1 to the Device Collection, not an Active Directory Group. Therefore, this solution does not meet the requirements. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD).
You manage Windows 10 devices by using Microsoft System Center Configuration Manager (Current Branch).
You configure a pilot for co-management.
You add a new device named Device1 to the domain. You install the Configuration Manager client on Device1.
You need to ensure that you can manage Device1 by using Microsoft Intune and Configuration Manager.
Solution: Define a Configuration Manager device collection as the pilot collection. Add Device1 to the collection.
Does this meet the goal?
- Yes
- No
Explanation:
Device1 has the Configuration Manager client installed so you can manage Device1 by using Configuration Manager.
To manage Device1 by using Microsoft Intune, the device has to be enrolled in Microsoft Intune. In the Co-management Pilot configuration, you configure a Configuration Manager Device Collection that determines which devices are auto-enrolled in Microsoft Intune. You need to add Device1 to the Device Collection so that it auto-enrols in Microsoft Intune. You will then be able to manage Device1 using Microsoft Intune. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD).
You manage Windows 10 devices by using Microsoft System Center Configuration Manager (Current Branch).
You configure a pilot for co-management.
You add a new device named Device1 to the domain. You install the Configuration Manager client on Device1.
You need to ensure that you can manage Device1 by using Microsoft Intune and Configuration Manager.
Solution: You create a device configuration profile from the Intune admin center.
Does this meet the goal?
- Yes
- No
Explanation:
Device1 has the Configuration Manager client installed so you can manage Device1 by using Configuration Manager.
To manage Device1 by using Microsoft Intune, the device has to be enrolled in Microsoft Intune. In the Co-management Pilot configuration, you configure a Configuration Manager Device Collection that determines which devices are auto-enrolled in Microsoft Intune. You need to add Device1 to the Device Collection. You do not need to create a device configuration profile from the Intune admin center. Therefore, this solution does not meet the requirements. -
HOTSPOT
You have a Microsoft 365 subscription.
You create an alert policy as shown in the following exhibit.

MS-100 Microsoft 365 Identity and Services Part 04 Q12 008 Use the drop-down menus to select the answer choice that completes each statement based on the information in the graphic.
NOTE: Each correct selection is worth one point.
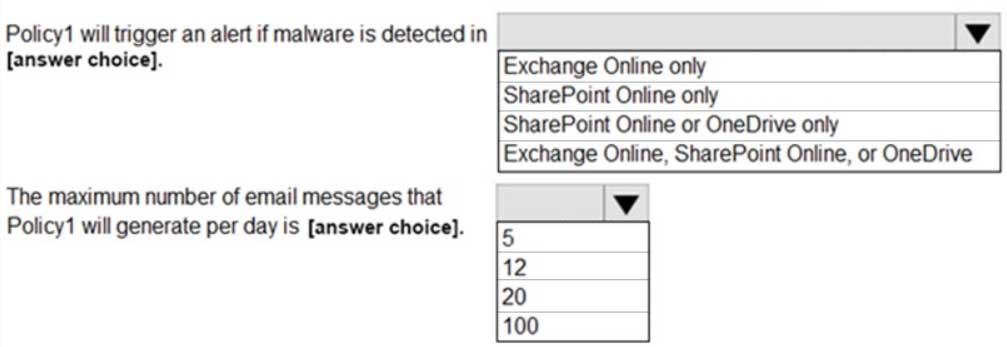
MS-100 Microsoft 365 Identity and Services Part 04 Q12 009 Question 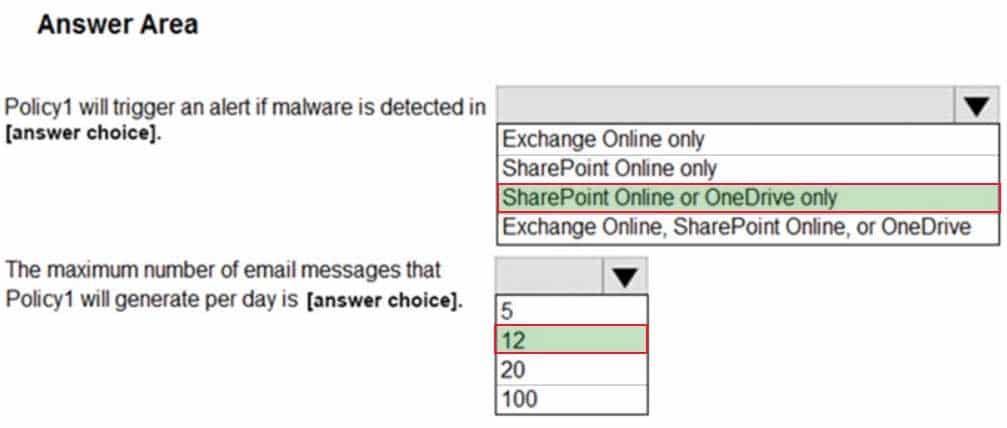
MS-100 Microsoft 365 Identity and Services Part 04 Q12 009 Answer Explanation:The ‘Activity is’ setting is configured as ‘Detected malware in file’. This setting means the policy is applied to files stored in SharePoint or OneDrive.
The Aggregation settings has a 120 minute window. This means that if there 20 detections in 120 minutes, an email will be generated. Therefore, the maximum number of emails generated in 24 hours is 12.
-
HOTSPOT
Your company is based in the United Kingdom (UK).
Users frequently handle data that contains Personally Identifiable Information (PII).
You create a data loss prevention (DLP) policy that applies to users inside and outside the company. The policy is configured as shown in the following exhibit.

MS-100 Microsoft 365 Identity and Services Part 04 Q13 010 Use the drop-down menus to select the answer choice that completes each statement based in the information presented in the information presented in the graphic.
NOTE: Each correct selection is worth one point.
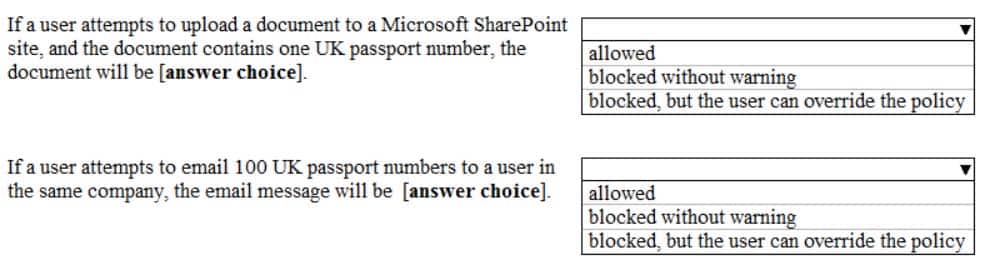
MS-100 Microsoft 365 Identity and Services Part 04 Q13 011 Question 
MS-100 Microsoft 365 Identity and Services Part 04 Q13 011 Answer Explanation:The text in the Policy Settings section of the exhibit explains what will happen.
If a user sends between 1 and 10 instances of the sensitive info (passport number), then a notification email and will be sent to the user and a policy tip will be displayed. The email will not be blocked though. Therefore, it will be allowed.
If a user sends more than 10 instances of the sensitive info (passport number), the email will be blocked and a high-severity alert generated. However, the user can override the block.
-
HOTSPOT
You have a Microsoft Azure Active Directory (Azure AD) tenant.
Your company implements Windows Information Protection (WIP).
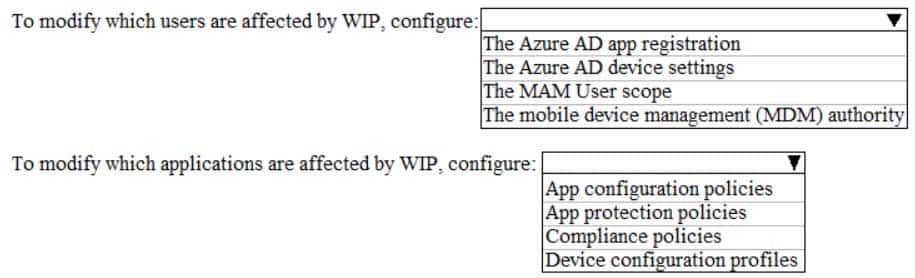
You need to modify which users and applications are affected by WIP.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MS-100 Microsoft 365 Identity and Services Part 04 Q14 012 Question 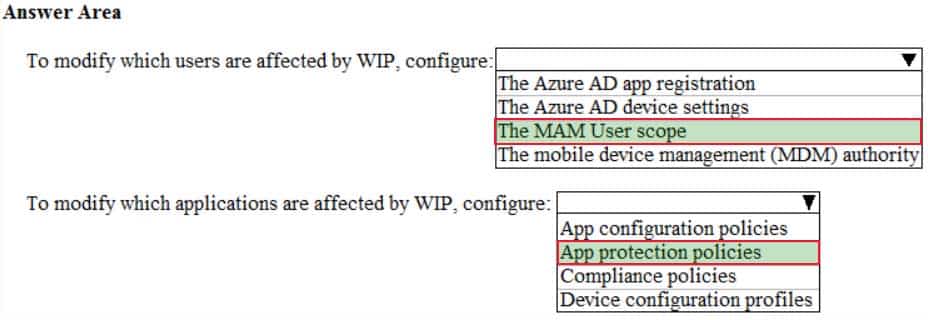
MS-100 Microsoft 365 Identity and Services Part 04 Q14 012 Answer Explanation:Microsoft Intune has an easy way to create and deploy a Windows Information Protection (WIP) policy. You can choose which apps to protect, the level of protection, and how to find enterprise data on the network. The devices can be fully managed by Mobile Device Management (MDM), or managed by Mobile Application Management (MAM), where Intune manages only the apps on a user’s personal device.
The MAM User scope determines which users are affected by WIP. App protection policies are used to configure which applications are affected by WIP. -
You have a Microsoft 365 subscription.
You configure a data loss prevention (DLP) policy.
You discover that users are incorrectly marking content as false positive and bypassing the DLP policy.
You need to prevent the users from bypassing the DLP policy.
What should you configure?
- actions
- exceptions
- incident reports
- user overrides
Explanation:
A DLP policy can be configured to allow users to override a policy tip and report a false positive.
You can educate your users about DLP policies and help them remain compliant without blocking their work. For example, if a user tries to share a document containing sensitive information, a DLP policy can both send them an email notification and show them a policy tip in the context of the document library that allows them to override the policy if they have a business justification. The same policy tips also appear in Outlook on the web, Outlook, Excel, PowerPoint, and Word.
If you find that users are incorrectly marking content as false positive and bypassing the DLP policy, you can configure the policy to not allow user overrides. -
In Microsoft 365, you configure a data loss prevention (DLP) policy named Policy1. Policy1 detects the sharing of United States (US) bank account numbers in email messages and attachments.
Policy1 is configured as shown in the exhibit.
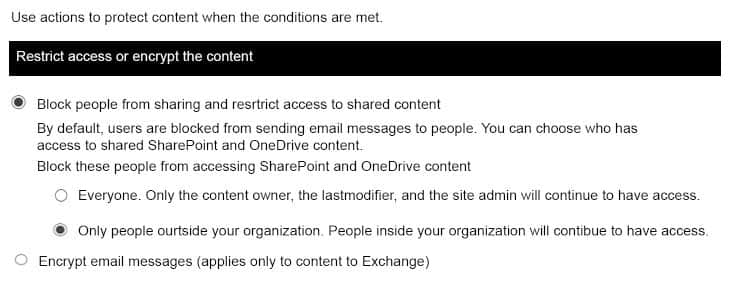
MS-100 Microsoft 365 Identity and Services Part 04 Q16 013 You need to ensure that internal users can email documents that contain US bank account numbers to external users who have an email suffix of contoso.com.
What should you configure?
- an action
- a group
- a condition
- an exception
Explanation:
You need to add an exception. In the Advanced Settings of the DLP policy, you can add a rule to configure the Conditions and Actions. There is also an ‘Add Exception’ button. This gives you several options that you can select as the exception. One of the options is ‘except when recipient domain is’. You need to select that option and enter the domain name contoso.com. -
Your company uses on-premises Windows Server File Classification Infrastructure 9FCI). Some documents on the on-premises file servers are classifies as Confidential.
You migrate the files from the on-premises file servers to Microsoft SharePoint Online.
You need to ensure that you can implement data loss prevention (DLP) policies for the uploaded files based on the Confidential classification.
What should you do first?
- From the SharePoint admin center, create a managed property.
- From the SharePoint admin center, configure hybrid search.
- From the Security & Compliance Center PowerShell, run the
New-DlpComplianceRule cmdlet. - From the Security & Compliance Center PowerShell, run the
New-DataClassification cmdlet.
Explanation:Your organization might use Windows Server FCI to identify documents with personally identifiable information (PII) such as social security numbers, and then classify the document by setting the Personally Identifiable Information property to High, Moderate, Low, Public, or Not PII based on the type and number of occurrences of PII found in the document. In Office 365, you can create a DLP policy that identifies documents that have that property set to specific values, such as High and Medium, and then takes an action such as blocking access to those files.
Before you can use a Windows Server FCI property or other property in a DLP policy, you need to create a managed property in the SharePoint admin center.
-
HOTSPOT
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You have three applications App1, App2, App3. The Apps use files that have the same file extensions.
Your company uses Windows Information Protection (WIP). WIP has the following configurations:
– Windows Information Protection mode: Silent
– Protected apps: App1
– Exempt apps: App2From App1, you create a file named File1.
What is the effect of the configurations? To answer, select the appropriate options in the answer area.
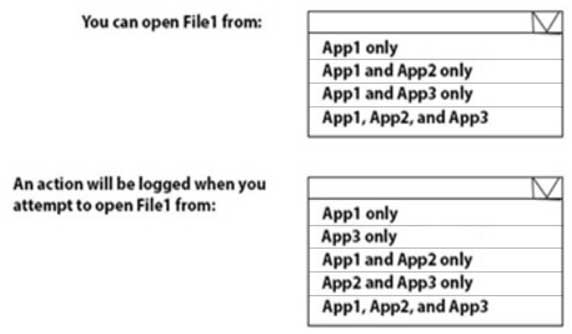
MS-100 Microsoft 365 Identity and Services Part 04 Q18 014 Question 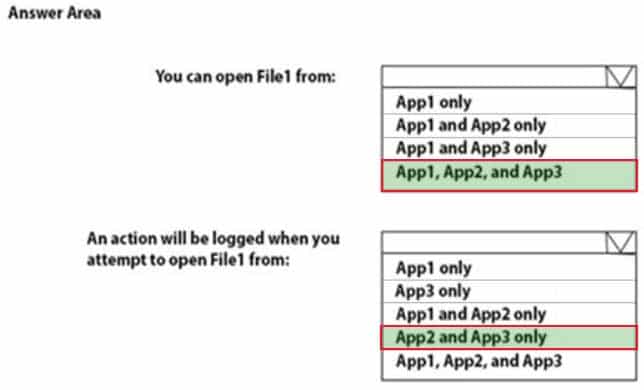
MS-100 Microsoft 365 Identity and Services Part 04 Q18 014 Answer Explanation:Exempt apps: These apps are exempt from this policy and can access corporate data without restrictions.
Windows Information Protection mode: Silent: WIP runs silently, logging inappropriate data sharing, without stopping anything that would’ve been prompted for employee interaction while in Allow overrides mode. Un allowed actions, like apps inappropriately trying to access a network resource or WIP-protected data, are still stopped.
-
Your company has 10 offices.
The network contains an Active Directory domain named contoso.com. The domain contains 500 client computers. Each office is configured as a separate subnet.
You discover that one of the offices has the following:
– Computers that have several preinstalled applications
– Computers that use nonstandard computer names
– Computers that have Windows 10 preinstalled
– Computers that are in a workgroupYou must configure the computers to meet the following corporate requirements:
– All the computers must be joined to the domain.
– All the computers must have computer names that use a prefix of CONTOSO.
– All the computers must only have approved corporate applications installed.You need to recommend a solution to redeploy the computers. The solution must minimize the deployment time.
- a provisioning package
- wipe and load refresh
- Windows Autopilot
- an in-place upgrade
Explanation:By using a provisioning package, IT administrators can create a self-contained package that contains all of the configuration, settings, and apps that need to be applied to a device.
Incorrect Answers:
C: With Windows Autopilot the user can set up pre-configured devices without the need consult their IT administrator.
D: Use the In-Place Upgrade option when you want to keep all (or at least most) existing applications. -
You have a Microsoft 365 subscription.
You recently configured a Microsoft SharePoint Online tenant in the subscription.
You plan to create an alert policy.
You need to ensure that an alert is generated only when malware is detected in more than five documents stored in SharePoint Online during a period of 10 minutes.
What should you do first?
- Enable Microsoft Office 365 Cloud App Security.
- Deploy Windows Defender Advanced Threat Protection (Windows Defender ATP).
- Enable Microsoft Office 365 Analytics.
Explanation:An alert policy consists of a set of rules and conditions that define the user or admin activity that generates an alert, a list of users who trigger the alert if they perform the activity, and a threshold that defines how many times the activity has to occur before an alert is triggered.
In this question, we would use the “Malware detected in file” activity in the alert settings then configure the threshold (5 detections) and the time window (10 minutes).
The ability to configure alert policies based on a threshold or based on unusual activity requires Advanced Threat Protection (ATP).