MS-100 : Microsoft 365 Identity and Services : Part 05
MS-100 : Microsoft 365 Identity and Services : Part 05
-
From the Microsoft Azure Active Directory (Azure AD) Identity Protection dashboard, you view the risk events shown in the exhibit.

MS-100 Microsoft 365 Identity and Services Part 05 Q01 015 You need to reduce the likelihood that the sign-ins are identified as risky.
What should you do?
- From the Security & Compliance admin center, add the users to the Security Readers role group.
- From the Conditional access blade in the Azure Active Directory admin center, create named locations.
- From the Azure Active Directory admin center, configure the trusted IPs for multi-factor authentication.
- From the Security & Compliance admin center, create a classification label.
Explanation:
A named location can be configured as a trusted location. Typically, trusted locations are network areas that are controlled by your IT department. In addition to Conditional Access, trusted named locations are also used by Azure Identity Protection and Azure AD security reports to reduce false positives for risky sign-ins. -
DRAG DROP
You have a Microsoft 365 subscription.
You have the devices shown in the following table.
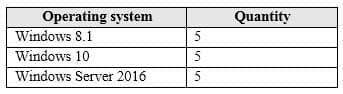
MS-100 Microsoft 365 Identity and Services Part 05 Q02 016 You need to onboard the devices to Windows Defender Advanced Threat Protection (ATP). The solution must avoid installing software on the devices whenever possible.
Which onboarding method should you use for each operating system? To answer, drag the appropriate methods to the correct operating systems. Each method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
MS-100 Microsoft 365 Identity and Services Part 05 Q02 017 Question 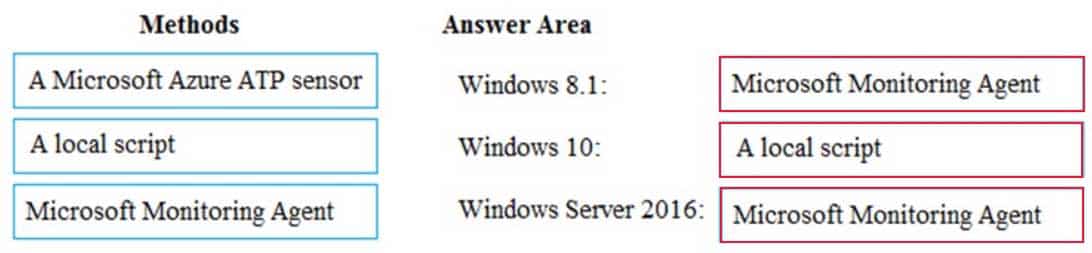
MS-100 Microsoft 365 Identity and Services Part 05 Q02 017 Answer Explanation:Box 1:
To onboard down-level Windows client endpoints to Microsoft Defender ATP, you’ll need to:
Configure and update System Center Endpoint Protection clients.
Install and configure Microsoft Monitoring Agent (MMA) to report sensor data to Microsoft Defender ATPBox 2:
For Windows 10 clients, the following deployment tools and methods are supported:
Group Policy
System Center Configuration Manager
Mobile Device Management (including Microsoft Intune)
Local scriptBox 3:
Windows Server 2016 can be onboarded by using Azure Security Centre. When you add servers in the Security Centre, the Microsoft Monitoring Agent is installed on the servers. -
HOTSPOT
You have a Microsoft 365 subscription.
You need to implement Windows Defender Advanced Threat Protection (ATP) for all the supported devices enrolled devices enrolled on mobile device management (MDM).
What should you include in the device configuration profile? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
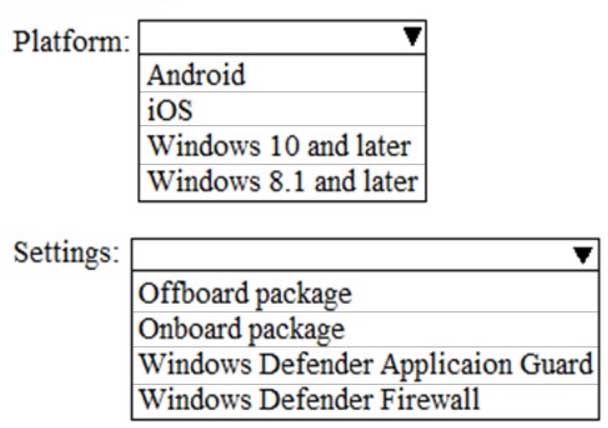
MS-100 Microsoft 365 Identity and Services Part 05 Q03 018 Question 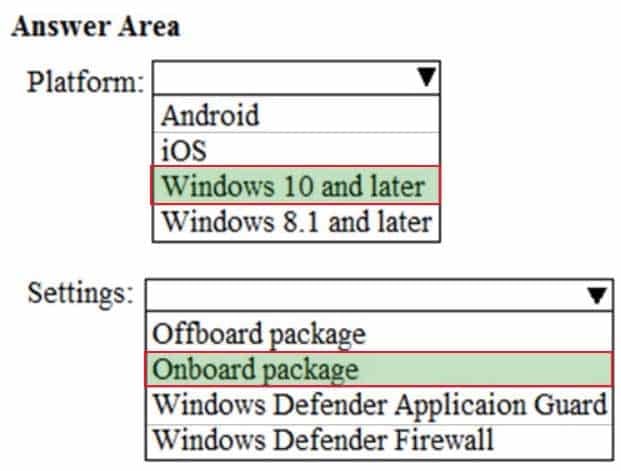
MS-100 Microsoft 365 Identity and Services Part 05 Q03 018 Answer Explanation:You can integrate Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP) with Microsoft Intune as a Mobile Threat Defense solution. Integration can help you prevent security breaches and limit the impact of breaches within an organization. Microsoft Defender ATP works with devices that run Windows 10 or later.
When you establish a connection from Intune to Microsoft Defender ATP, Intune receives a Microsoft Defender ATP onboarding configuration package from Microsoft Defender ATP. This package is deployed to devices by using a device configuration profile.
-
You have a Microsoft 365 tenant.
You have a line-of-business application named App1 that users access by using the My Apps portal.
After some recent security breaches, you implement a conditional access policy for App1 that uses Conditional Access App Control.
You need to be alerted by email if impossible travel is detected for a user of App1. The solution must ensure that alerts are generated for App1 only.
What should you do?
- From Microsoft Cloud App Security, modify the impossible travel alert policy.
- From Microsoft Cloud App Security, create a Cloud Discovery anomaly detection policy.
- From the Azure Active Directory admin center, modify the conditional access policy.
- From Microsoft Cloud App Security, create an app discovery policy.
Explanation:
Impossible travel detection identifies two user activities (is a single or multiple sessions) originating from geographically distant locations within a time period shorter than the time it would have taken the user to travel from the first location to the second.
We need to modify the policy so that it applies to App1 only. -
Your network contains an on-premises Active Directory domain.
Your company has a security policy that prevents additional software from being installed on domain controllers.
You need to monitor a domain controller by using Microsoft Azure Advanced Threat Protection (ATP).
What should you do? More than once choice may achieve the goal. Select the BEST answer.
- Deploy an Azure ATP standalone sensor, and then configure port mirroring.
- Deploy an Azure ATP standalone sensor, and then configure detections.
- Deploy an Azure ATP sensor, and then configure detections.
- Deploy an Azure ATP sensor, and then configure port mirroring.
Explanation:
If you’re installing on a domain controller, you don’t need a standalone ATP sensor. You need to configure the detections to detect application installations. With an ATP sensor (non-standalone), you don’t need to configure port mirroring. -
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains 1,000 Windows 10 devices.
You perform a proof of concept (PoC) deployment of Windows Defender Advanced Threat Protection (ATP) for 10 test devices. During the onboarding process, you configure Windows Defender ATP-related data to be stored in the United States.
You plan to onboard all the devices to Windows Defender ATP data in Europe.
What should you do first?
- Create a workspace
- Offboard the test devices
- Delete the workspace
- Onboard a new device
Explanation:
When onboarding Windows Defender ATP for the first time, you can choose to store your data in Microsoft Azure datacenters in the European Union, the United Kingdom, or the United States. Once configured, you cannot change the location where your data is stored.
The only way to change the location is to offboard the test devices then onboard them again with the new location. -
You implement Microsoft Azure Advanced Threat Protection (Azure ATP).
You have an Azure ATP sensor configured as shown in the following exhibit.
Updates

MS-100 Microsoft 365 Identity and Services Part 05 Q07 019 How long after the Azure ATP cloud service is updated will the sensor update?
- 1 hour
- 7 days
- 48 hours
- 12 hours
- 72 hours
-
Your company has a Microsoft 365 E3 subscription.
All devices run Windows 10 Pro and are joined to Microsoft Azure Active Directory (Azure AD).
You need to change the edition of Windows 10 to Enterprise the next time users sign in to their computer. The solution must minimize downtime for the users.
What should you use?
- Subscription Activation
- Windows Update
- Windows Autopilot
- an in-place upgrade
Explanation:
When initially deploying new Windows devices, Windows Autopilot leverages the OEM-optimized version of Windows 10 that is preinstalled on the device, saving organizations the effort of having to maintain custom images and drivers for every model of device being used. Instead of re-imaging the device, your existing Windows 10 installation can be transformed into a “business-ready” state, applying settings and policies, installing apps, and even changing the edition of Windows 10 being used (e.g. from Windows 10 Pro to Windows 10 Enterprise) to support advanced features. -
HOTSPOT
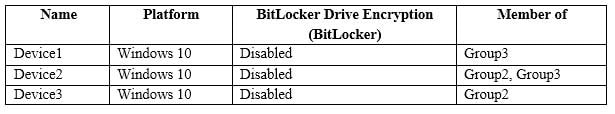
You have three devices enrolled in Microsoft Intune as shown in the following table.
MS-100 Microsoft 365 Identity and Services Part 05 Q09 020 The device compliance policies in Intune are configured as shown in the following table.

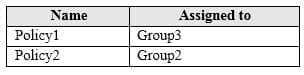
MS-100 Microsoft 365 Identity and Services Part 05 Q09 021 The device compliance policies have the assignment shown in the following table.
MS-100 Microsoft 365 Identity and Services Part 05 Q09 022 For each of the following statements, select Yes if the statement is true. Otherwise, select No.

MS-100 Microsoft 365 Identity and Services Part 05 Q09 022 NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 05 Q09 023 Question 
MS-100 Microsoft 365 Identity and Services Part 05 Q09 023 Answer Explanation:Device 1:
No because Device1 is in group3 which has Policy1 assigned which requires BitLocker.Device 2:
No because Device2 is in group3 which has Policy1 assigned which requires BitLocker. Device2 is also in Group2 which has Policy2 assigned but the BitLocker requirement is not configured in Policy2.Device3:
Yes because Device3 is in Group2 which has Policy2 assigned but the BitLocker requirement is not configured in Policy2. -
HOTSPOT
Your company has a Microsoft 365 tenant.
You plan to allow users from the engineering department to enroll their mobile device in mobile device management (MDM).
The device type restrictions are configured as shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 05 Q10 024 The device limit restrictions are configured as shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 05 Q10 025 What is the effective configuration for the members of the Engineering group? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 05 Q10 026 Question 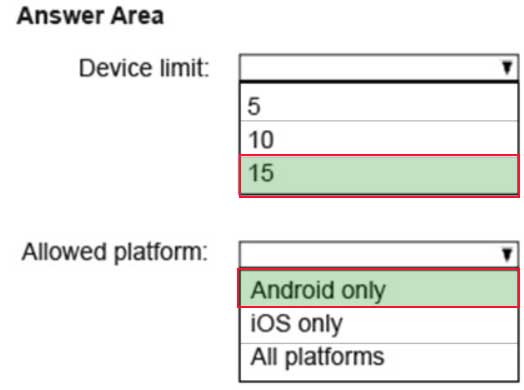
MS-100 Microsoft 365 Identity and Services Part 05 Q10 026 Answer Explanation:When multiple policies are applied to groups that users are a member of, only the highest priority (lowest number) policy applies.
In this case, the Engineering users are assigned two device type policies (the default policy and the priority 2 policy). The priority 2 policy has a higher priority than the default policy so the Engineers’ allowed platform is Android only.
The engineers have two device limit restrictions policies applied them. The priority1 policy is a higher priority than the priority2 policy so the priority1 policy device limit (15) applies.
-
Your network contains an Active Directory domain named contoso.com. The domain contains 1000 Windows 8.1 devices.
You plan to deploy a custom Windows 10 Enterprise image to the Windows 8.1 devices.
You need to recommend a Windows 10 deployment method.
What should you recommend?
- Wipe and load refresh
- Windows Autopilot
- a provisioning package
- an in-place upgrade
Explanation:
To deploy a custom image, you must use the wipe and load refresh method. You cannot deploy a custom image by using an in-place upgrade, Windows Autopilot or a provisioning package. -
You use Microsoft System Center Configuration manager (Current Branch) to manage devices.
Your company uses the following types of devices:
– Windows 10
– Windows 8.1
– Android
– iOSWhich devices can be managed by using co-management?
- Windows 10 and Windows 8.1 only
- Windows 10, Android, and iOS only
- Windows 10 only
- Windows 10, Windows 8.1, Android, and iOS
Explanation:You can manage only Windows 10 devices by using co-management.
When you concurrently manage Windows 10 devices with both Configuration Manager and Microsoft Intune, this configuration is called co-management. When you manage devices with Configuration Manager and enroll to a third-party MDM service, this configuration is called coexistence.
-
HOTSPOT
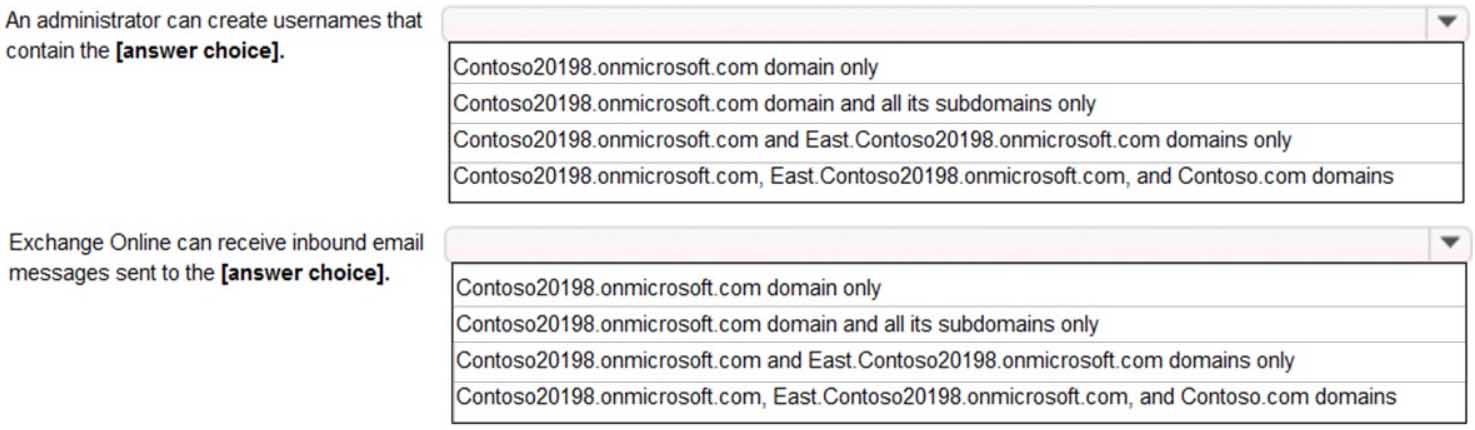
You company has a Microsoft 365 subscription that contains the domains shown in the following exhibit.

MS-100 Microsoft 365 Identity and Services Part 05 Q13 027 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
MS-100 Microsoft 365 Identity and Services Part 05 Q13 028 Question 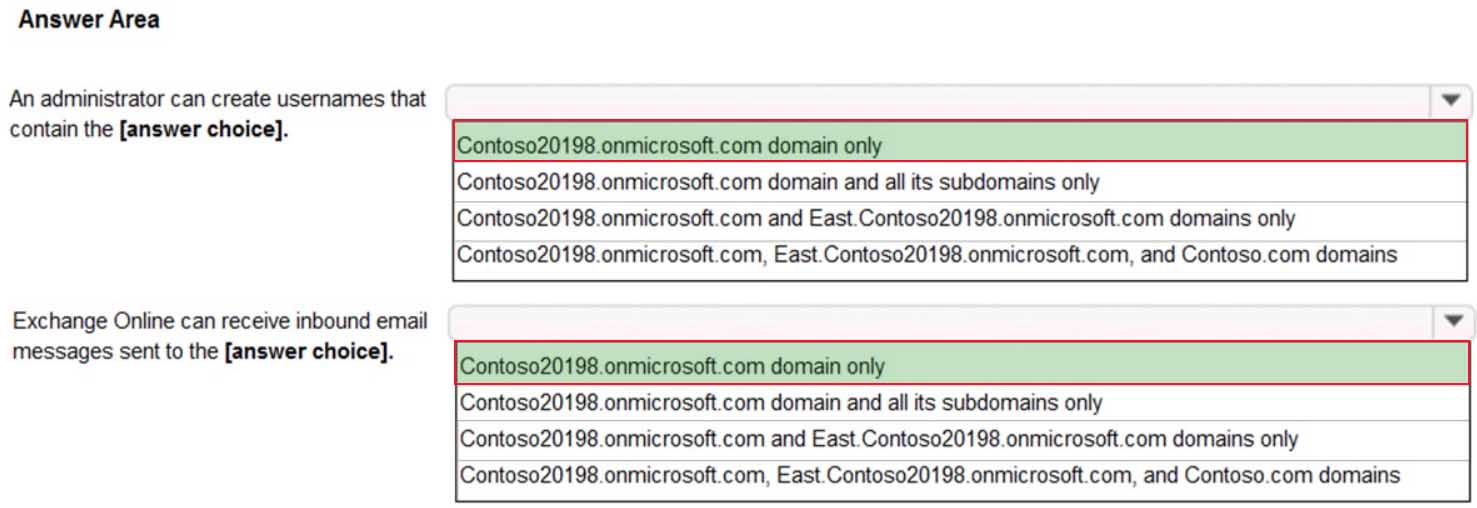
MS-100 Microsoft 365 Identity and Services Part 05 Q13 028 Answer Explanation:Only the Contoso20198.onmicrosoft.com domain has a status of Setup Complete. The other two statuses mean that the domain setup is not complete or has issues that need to be corrected before they can be used.
-
Your company has 20 employees. Each employee has a mailbox hosted in Outlook.com.
The company purchases a Microsoft 365 subscription.
You plan to migrate all the mailboxes to Microsoft 365.
You need to recommend which type of migration to use for the mailboxes.
What should you recommend?
- staged migration
- cutover migration
- minimal hybrid migration
- IMAP migration
Explanation:To migrate mailboxes from Outlook.com to Office 365, you need to use the IMAP migration method.
After you’ve added your users to Office 365, you can use Internet Message Access Protocol (IMAP) to migrate email for those users from their IMAP-enabled email servers.
In the Microsoft 365 admin center, go to Setup > Data migration to start migrating IMAP enabled emails. The email migrations page is pre-configured for migrations from Gmail, Outlook, Hotmail and Yahoo. You can also enter your own IMAP server name and connection parameters to migrate from an email service that is not listed. -
Your network contains an on-premises Active Directory domain named contoso.com that is synced to a Microsoft Azure Active Directory (Azure AD) tenant.
The on-premises network contains a file server named Server1. Server1 has a share named Share1 that contains company documents.
Your company purchases a Microsoft 365 subscription.
You plan to migrate data from Share1 to Microsoft 365. Only data that was created or modified during the last three months will be migrated.
You need to identify all the files in Share1 that were modified or created during the last 90 days.
What should you use?
- Server Manager
- Microsoft SharePoint Migration Tool
- Resource Monitor
- Usage reports from the Microsoft 365 admin center
Explanation:
You can use the Microsoft SharePoint Migration Tool to migrate files from a file server to SharePoint Online.
The Microsoft SharePoint Migration Tool has a number of filters you can use to define which files will be migrated. One filter setting is “Migrate files modified after”. This setting will only migrate files modified after the selected date.
The first phase of a migration is to perform a scan of the source files to create a manifest of the files that will be migrated. You can use this manifest to identify all the files in Share1 that were modified or created during the last 90 days. -
Your company has two offices. The offices are located in Seattle and New York.
The company uses a third-party email system.
You implement Microsoft 365.
You move all the users in the Seattle office to Exchange Online. You configure Microsoft 365 to successfully receive all the email messages sent to the Seattle office users.
All the users in the New York office continue to use the third-party email system.
The users use the email domains shown in the following table.
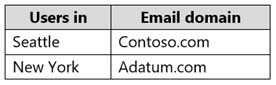
MS-100 Microsoft 365 Identity and Services Part 05 Q16 029 You need to ensure that all the email messages sent to the New York office users are delivered successfully. The solution must ensure that all the email messages for the users in both offices are routed through Microsoft 365.
You create the required DNS records and Send connectors.
What should you do next from Microsoft 365?
- From the Microsoft 365 admin center, set the default domain. From the Exchange admin center, create a transport rule for all the email messages sent to adatum.com.
- From the Microsoft 365 admin center, add the adatum.com domain. From the Exchange admin center, configure adatum.com as an internal relay domain.
- From the Microsoft 365 admin center, add the adatum.com domain. From the Exchange admin center, configure adatum.com as an authoritative domain.
- From the Microsoft 365 admin center, set the default domain. From the Exchange admin center, configure adatum.com as a remote domain.
Explanation:The first step is to configure Exchange Online to accept emails for the adatum.com domain. To do this, we add the domain in Microsoft 365. When you add your domain to Microsoft 365, it’s called an accepted domain.
The next step is to tell Exchange Online what to do with those emails. You need to configure the adatum.com domain as either an authoritative domain or an internal relay domain.
Authoritative domain means that the mailboxes for that domain are hosted in Office 365. In this question, the mailboxes for the adatum.com domain are hosted on the third-party email system. Therefore, we need to configure the adatum.com domain as an internal relay domain. For an internal relay domain, Exchange Online will receive the email for the adatum.com domain and then ‘relay’ (forward) the email on to the third-party email server.
-
HOTSPOT
Your company has a Microsoft 365 subscription that contains the following domains:
Contoso.onmicrosoft.com
Contoso.comYou plan to add the following domains to Microsoft 365 and to use them with Exchange Online:
– Sub1.contoso.onmicrosoft.com
– Sub2.contoso.com
– Fabrikam.comYou need to identify the minimum number of DNS records that must be added for Exchange Online to receive inbound email messages for the three domains.
How many DNS records should you add? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 05 Q17 030 Question 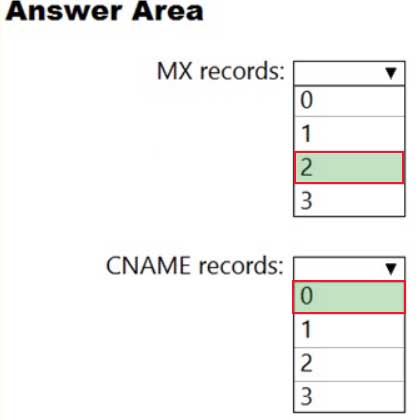
MS-100 Microsoft 365 Identity and Services Part 05 Q17 030 Answer Explanation:Box 1: 2
You don’t need to verify Sub1.contoso.onmicrosoft.com because the onmicrosoft.com domain and DNS is managed by Microsoft. You also don’t need to configure an MX record for Sub1.contoso.onmicrosoft.com because that will be done by Microsoft.For sub2.contoso.com, you don’t need to verify the domain because you have already verified its parent domain contoso.com. However, you do need an MX record to direct email for that domain to Exchange Online.
For Fabrikam.com, you will need to verify the domain. You will need an MX record to direct email for that domain to Exchange Online.
Box 2: 0
You ‘should’ create CNAME records for auto discover to point your email clients to Exchange Online to connect to the mailboxes. However, you don’t have to. You could configure the email client manually. Therefore, the minimum number of CNAME records required is zero. -
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
You may now click next to proceed to the lab.
Lab information
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
admin@LODSe426243.onmicrosoft.comMicrosoft 365 Password: 3&YWyjse-6-d
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 10887751
You plan to create 1,000 users in your Microsoft 365 subscription.
You need to ensure that all the users can use the @contoso.com suffix in their username.
Another administrator will perform the required information to your DNS zone to complete the operation.
- See explanation below.
Explanation:You need to add the contoso.com domain to Microsoft 365 then set the domain as the default.
1. In the Admin Center, click Setup then click Domains.
2. Click the ‘Add Domain’ button.
3. Type in the domain name (contoso.com) and click the ‘Use this domain’ button.
4. The question states that another administrator will perform the required information to your DNS zone. Therefore, you just need to click the ‘Verify’ button to verify domain ownership.
5. Click Finish.
6. In the domains list, select the contoso.com domain.
7. Select ‘Set as default’. -
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
You may now click next to proceed to the lab.
Lab information
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
admin@LODSe1211885.onmicrosoft.comMicrosoft 365 Password: oL9z0=?Nq@ox
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 11098651
MS-100 Microsoft 365 Identity and Services Part 05 Q19 031 You need to prevent users in your organization from receiving an email notification when they save a document that contains credit card numbers.
To answer the question, sign in to the Microsoft 365 portal.
- See explanation below.
Explanation:You need to edit the Data Loss Prevention Policy to disable the email notifications.
1. Go to https://protection.office.com or navigate to the Security & Compliance admin center.
2. In the left navigation pane, expand Data Loss Protection and select Policy.
3. Select the Data Loss Prevention policy and click the Edit Policy button.
4. Click Policy Settings in the left navigation pane of the policy.
5. Select the policy rule and click the Edit Rule button.
6. Scroll down to the ‘User notifications’ section.
7. Toggle the slider labelled “Use Notifications to inform users….” to Off.
8. Click Save to save the changes to the policy rule.
9. Click Save to save the changes to the policy. -
You have a Microsoft 365 subscription.
You add a domain named contoso.com.
When you attempt to verify the domain, you are prompted to send a verification email to admin@contoso.com.
You need to change the email address used to verify the domain.
What should you do?
- From the domain registrar, modify the contact information of the domain
- Add a TXT record to the DNS zone of the domain
- Modify the NS records for the domain
- From the Microsoft 365 admin center, change the global administrator of the Microsoft 365 subscription
Explanation:
The email address that is used to verify that you own the domain is the email address listed with the domain registrar for the registered contact for the domain.