MS-100 : Microsoft 365 Identity and Services : Part 07
MS-100 : Microsoft 365 Identity and Services : Part 07
-
HOTSPOT
You have a new Microsoft 365 subscription.
A user named User1 has a mailbox in Microsoft Exchange Online.
You need to log any changes to the mailbox folder permissions of User1.
Which command should you run? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 07 Q01 056 Question 
MS-100 Microsoft 365 Identity and Services Part 07 Q01 056 Answer Explanation:To enable auditing for a single mailbox use this PowerShell command: Set-Mailbox username -AuditEnabled $true
-
Your company has a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You sign up for Microsoft Store for Business.
The tenant contains the users shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 07 Q02 057 Microsoft Store for Business has the following Shopping behavior settings:
– Allow users to shop is set to On.
– Make everyone a Basic Purchaser is set to Off.You need to identify which users can install apps from the Microsoft for Business private store.
Which users should you identify?
- A. user1, User2, User3, User4, and User5
- User1 only
- User1 and User2 only
- User3 and User4 only
- User1, User2, User3, and User4 only
Explanation:Allow users to shop controls the shopping experience in Microsoft Store for Education. When this setting is on, Purchasers and Basic Purchasers can purchase products and services from Microsoft Store for Education.
-
You have a Microsoft 365 subscription that contains a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
In the tenant, you create a user named User1.
You need to ensure that User1 can publish retention labels from the Security & Compliance admin center. The solution must use the principle of least privilege.
To which role group should you add User1?
- Security Administrator
- Records Management
- Compliance Administrator
- eDiscovery Manager
Explanation:
Members of your compliance team who will create retention labels need permissions to the Security & Compliance Center. By default, your tenant admin has access to this location and can give compliance officers and other people access to the Security & Compliance Center, without giving them all of the permissions of a tenant admin. To do this, we recommend that you go to the Permissions page of the Security & Compliance Center, edit the Compliance Administrator role group, and add members to that role group. -
HOTSPOT
You have a Microsoft 365 subscription.
You are configuring permissions for Security & Compliance.
You need to ensure that the users can perform the tasks shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 07 Q04 058 The solution must use the principle of least privilege.
To which role should you assign each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
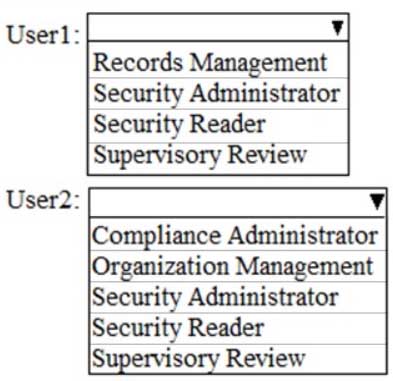
MS-100 Microsoft 365 Identity and Services Part 07 Q04 059 Question 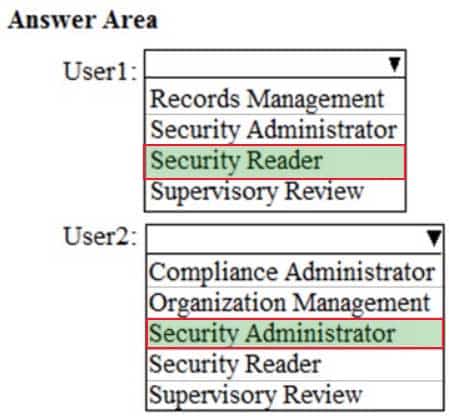
MS-100 Microsoft 365 Identity and Services Part 07 Q04 059 Answer Explanation:Security Reader: Members can manage security alerts (view only), and also view reports and settings of security features.
Security Administrator, Compliance Administrator and Organization Management can manage alerts. However, Security Administrator has the least privilege.
-
Your company has a Microsoft 365 E5 subscription.
Users in the research department work with sensitive data.
You need to prevent the research department users from accessing potentially unsafe websites by using hyperlinks embedded in email messages and documents. Users in other departments must not be restricted.
What should you do from the Security & Compliance admin center?
- Create a data loss prevention (DLP) policy that has a Content contains condition.
- Create a data loss prevention (DLP) policy that has a Content is shared condition.
- Modify the default safe links policy.
- Create a new safe links policy.
Explanation:
ATP Safe Links, a feature of Office 365 Advanced Threat Protection (ATP), can help protect your organization from malicious links used in phishing and other attacks. If you have the necessary permissions for the Office 365 Security & Compliance Center, you can set up ATP Safe Links policies to help ensure that when people click web addresses (URLs), your organization is protected. Your ATP Safe Links policies can be configured to scan URLs in email and URLs in Office documents. -
HOTSPOT
You have a Microsoft Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 07 Q06 060 Your company uses Windows Defender Advanced Threat Protection (ATP). Windows Defender ATP contains the roles shown in the following table.
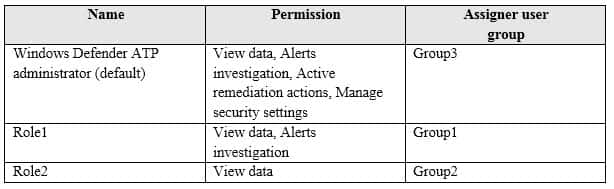
MS-100 Microsoft 365 Identity and Services Part 07 Q06 061 Windows Defender ATP contains the device groups shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 07 Q06 062 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 07 Q06 063 Question 
MS-100 Microsoft 365 Identity and Services Part 07 Q06 063 Answer Explanation:Box 1:
Yes. User1 is in Group1 which is assigned to Role1. Device1 is in the device group named ATP1 which Group1 has access to. Role1 gives Group1 (and User1) View Data Permission. This is enough to view Device1 in Windows Security Center.Box 2:
Yes. User2 is in Group2 which is assigned to Role2. Role2 gives Group2 (and User2) View Data Permission. This is enough to sign in to Windows Security Center.Box 3:
Yes. User3 is in Group3 which is assigned the Windows ATP Administrator role. Someone with a Microsoft Defender ATP Global administrator role has unrestricted access to all machines, regardless of their machine group association and the Azure AD user groups assignments. -
A user receives the following message when attempting to sign in to https://myapps.microsoft.com:
"Your sign-in was blocked. We've detected something unusual about this sign-in. For example, you might be signing in from a new location, device, or app. Before you can continue, we need to verify your identity. Please contact your admin."
Which configuration prevents the users from signing in?
- Security & Compliance supervision policies
- Security & Compliance data loss prevention (DLP) policies
- Microsoft Azure Active Directory (Azure AD) conditional access policies
- Microsoft Azure Active Directory (Azure AD) Identity Protection policies
Explanation:
The user is being blocked due to a ‘risky sign-in’. This can be caused by the user logging in from a device that hasn’t been used to sign in before or from an unknown location.
Integration with Azure AD Identity Protection allows Conditional Access policies to identify risky sign-in behavior. Policies can then force users to perform password changes or multi-factor authentication to reduce their risk level or be blocked from access until an administrator takes manual action. -
HOTSPOT
You have several devices enrolled in Microsoft Intune.
You have a Microsoft Azure Active Directory (Azure AD) tenant that includes the users shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 07 Q08 064 The device type restrictions in Intune are configured as shown in the following table.
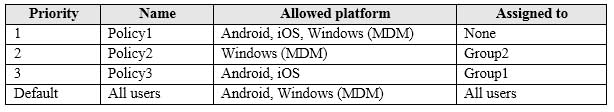
MS-100 Microsoft 365 Identity and Services Part 07 Q08 065 You add User3 as a device enrollment manager in Intune.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 07 Q08 066 Question 
MS-100 Microsoft 365 Identity and Services Part 07 Q08 066 Answer Explanation:Box 1:
No. User1 is in Group1. The two device type policies that apply to Group1 are Policy3 and the Default (All Users) policy. However, Policy3 has a higher priority than the default policy so Policy3 is the only effective policy. Policy3 allows the enrolment of Android and iOS devices only, not Windows.Box 2:
No. User2 is in Group1 and Group2. The device type policies that apply to Group1 and Group2 are Policy2, Policy3 and the Default (All Users) policy. However, Policy2 has a higher priority than Policy 3 and the default policy so Policy2 is the only effective policy. Policy2 allows the enrolment of Windows devices only, not Android.Box 3:
Yes. User3 is a device enrollment manager. Device restrictions to not apply to a device enrollment manager. -
HOTSPOT
You have the Microsoft Azure Active Directory (Azure AD) users shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 07 Q09 067 Your company uses Microsoft Intune.
Several devices are enrolled in Intune as shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 07 Q09 068 The device compliance policies in Intune are configured as shown in the following table.
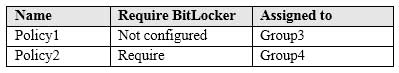
MS-100 Microsoft 365 Identity and Services Part 07 Q09 069 You create a conditional access policy that has the following settings:
The Assignments settings are configured as follows:
– Users and groups: Group1
– Cloud apps: Exchange Online
– Conditions: Include All device state, exclude Device marked as compliant
Access controls is set to Block access.For each of the following statements, select yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 07 Q09 070 Question 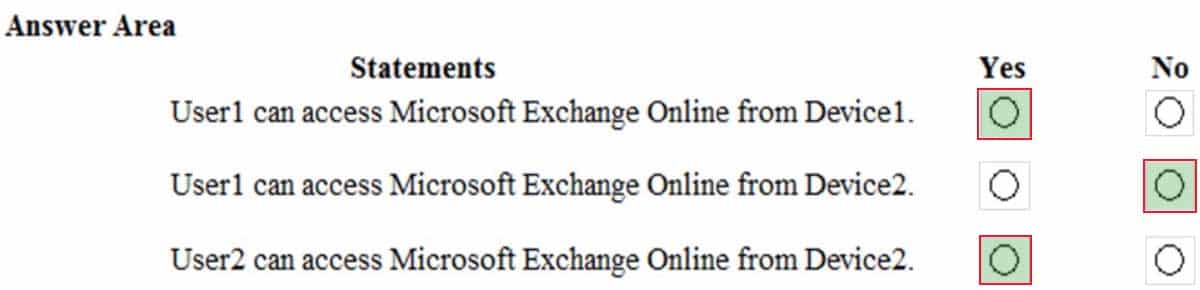
MS-100 Microsoft 365 Identity and Services Part 07 Q09 070 Answer Explanation:Box 1:
Yes. User1 is in Group1. The Conditional Access Policy applies to Group1. The Conditional Access Policy blocks access unless the device is marked as compliant.
BitLocker is disabled for Device1. Device1 is in Group3 which is assigned device Policy1. The BitLocker policy in Policy1 is ‘not configured’ so BitLocker is not required.
Therefore, Device1 is compliant so User1 can access Exchange online from Device1.Box 2:
No. User1 is in Group1. The Conditional Access Policy applies to Group1. The Conditional Access Policy blocks access unless the device is marked as compliant.
BitLocker is disabled for Device2. Device2 is in Group4 which is assigned device Policy2. The BitLocker policy in Policy2 is ‘Required so BitLocker is required.
Therefore, Device2 is not compliant so User1 cannot access Exchange online from Device2.Box3:
Yes. User2 is in Group2. The Conditional Access Policy applies to Group1. The Conditional Access Policy does not apply to Group2. So even though Device2 is non-compliant, User2 can access Exchange Online using Device2 because there is no Conditional Access Policy preventing him/her from doing so. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain.
You deploy a Microsoft Azure Active Directory (Azure AD) tenant.
Another administrator configures the domain to synchronize to Azure AD.
You discover that 10 user accounts in an organizational unit (OU) are NOT synchronized to Azure AD. All the other user accounts synchronized successfully.
You review Azure AD Connect Health and discover that all the user account synchronizations completed successfully.
You need to ensure that the 10 user accounts are synchronized to Azure AD.
Solution: From the Synchronization Rules Editor, you create a new outbound synchronization rule.
Does this meet the goal?
- Yes
- No
Explanation:
The question states that “all the user account synchronizations completed successfully”. Therefore, the synchronization rule is configured correctly. It is likely that the 10 user accounts are being excluded from the synchronization cycle by a filtering rule. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain.
You deploy a Microsoft Azure Active Directory (Azure AD) tenant.
Another administrator configures the domain to synchronize to Azure AD.
You discover that 10 user accounts in an organizational unit (OU) are NOT synchronized to Azure AD. All the other user accounts synchronized successfully.
You review Azure AD Connect Health and discover that all the user account synchronizations completed successfully.
You need to ensure that the 10 user accounts are synchronized to Azure AD.
Solution: You run idfix.exe and export the 10 user accounts.
Does this meet the goal?
- Yes
- No
Explanation:
The question states that “all the user account synchronizations completed successfully”. If there were problems with the 10 accounts that needed fixing with idfix.exe, there would have been synchronization errors in Azure AD Connect Health.
It is likely that the 10 user accounts are being excluded from the synchronization cycle by a filtering rule. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain.
You deploy a Microsoft Azure Active Directory (Azure AD) tenant.
Another administrator configures the domain to synchronize to Azure AD.
You discover that 10 user accounts in an organizational unit (OU) are NOT synchronized to Azure AD. All the other user accounts synchronized successfully.
You review Azure AD Connect Health and discover that all the user account synchronizations completed successfully.
You need to ensure that the 10 user accounts are synchronized to Azure AD.
Solution: From Azure AD Connect, you modify the Azure AD credentials.
Does this meet the goal?
- Yes
- No
Explanation:
The question states that “all the user account synchronizations completed successfully”. Therefore, the Azure AD credentials are configured correctly in Azure AD Connect. It is likely that the 10 user accounts are being excluded from the synchronization cycle by a filtering rule. -
HOTSPOT
You have a Microsoft Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 07 Q13 071 You enable self-service password reset for all users. You set Number of methods required to reset to 1, and you set Methods available to users to Security questions only.
What information must be configured for each user before the user can perform a self-service password reset? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
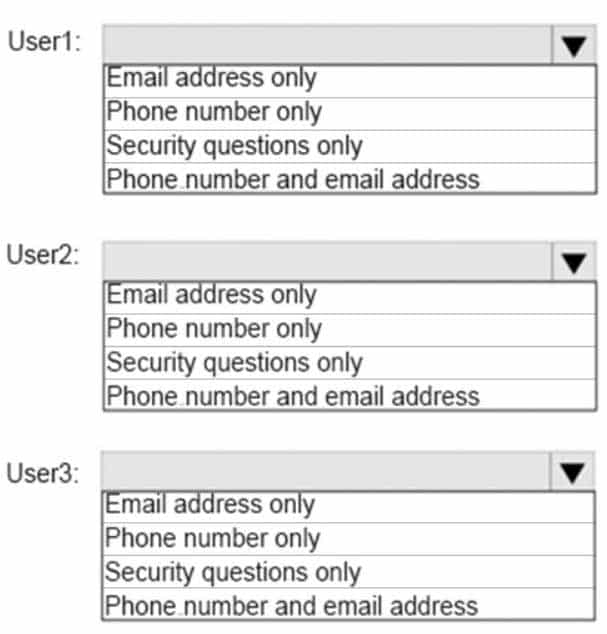
MS-100 Microsoft 365 Identity and Services Part 07 Q13 072 Question 
MS-100 Microsoft 365 Identity and Services Part 07 Q13 072 Answer Explanation:Microsoft enforces a strong default two-gate password reset policy for any Azure administrator role. This policy may be different from the one you have defined for your users and cannot be changed. You should always test password reset functionality as a user without any Azure administrator roles assigned.
With a two-gate policy, administrators don’t have the ability to use security questions.
The two-gate policy requires two pieces of authentication data, such as an email address, authenticator app, or a phone number.User3 is not assigned to an Administrative role so the configured method of Security questions only applies to User3.
-
HOTSPOT
You have a Microsoft 365 subscription.
You need to provide an administrator named Admin1 with the ability to place holds on mailboxes, SharePoint Online sites, and OneDrive for Business locations. The solution must use the principle of least privilege.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 07 Q14 073 Question 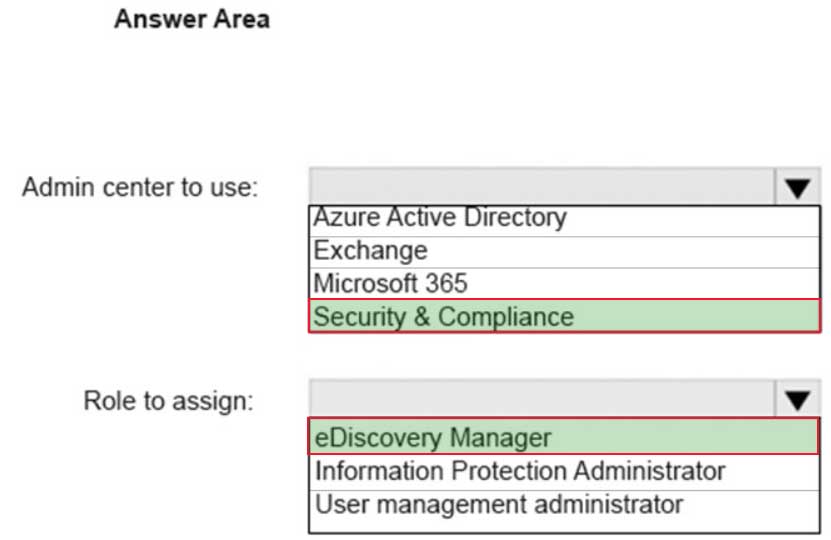
MS-100 Microsoft 365 Identity and Services Part 07 Q14 073 Answer Explanation:The Office 365 Security & Compliance Center lets you grant permissions to people who perform compliance tasks like device management, data loss prevention, eDiscovery, retention, and so on.
Users assigned to the eDiscovery Manager role can perform searches and place holds on mailboxes, SharePoint Online sites, and OneDrive for Business locations.
-
You have a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains the users shown in the following table.
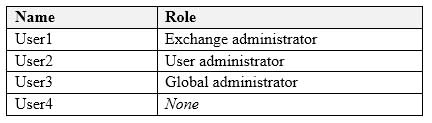
MS-100 Microsoft 365 Identity and Services Part 07 Q15 074 You add another user named User5 to the User administrator role.
You need to identify which two management tasks User5 can perform.
Which two tasks should you identify? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Delete User2 and User4 only.
- Reset the password of User2 and User4 only.
- Delete User1, User2, and User4 only.
- Delete any user in Azure AD.
- Reset the password of any user in Azure AD.
- Reset the password of User4 only.
Explanation:Users with the User Administrator role can create users and manage all aspects of users with some restrictions (see below).
Only on users who are non-admins or in any of the following limited admin roles:
– Directory Readers
– Guest Inviter
– Helpdesk Administrator
– Message Center Reader
– Reports Reader
– User Administrator -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain.
You deploy a Microsoft Azure Active Directory (Azure AD) tenant.
Another administrator configures the domain to synchronize to Azure AD.
You discover that 10 user accounts in an organizational unit (OU) are NOT synchronized to Azure AD. All the other user accounts synchronized successfully.
You review Azure AD Connect Health and discover that all the user account synchronizations completed successfully.
You need to ensure that the 10 user accounts are synchronized to Azure AD.
Solution: From Azure AD Connect, you modify the filtering settings.
Does this meet the goal?
- Yes
- No
Explanation:
The question states that “all the user account synchronizations completed successfully”. Therefore, we know that Azure AD Connect is working and configured correctly. The only thing that would prevent the 10 user accounts from being synchronized is that they are being excluded from the synchronization cycle by a filtering rule. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has 3,000 users. All the users are assigned Microsoft 365 E3 licenses.
Some users are assigned licenses for all Microsoft 365 services. Other users are assigned licenses for only certain Microsoft 365 services.
You need to determine whether a user named User1 is licensed for Exchange Online only.
Solution: You run the Get-MsolUser cmdlet.
Does this meet the goal?
- Yes
- No
Explanation:
The Get-MsolUser cmdlet will tell you if a user is licensed for Microsoft 365 but it does not tell you which licenses are assigned. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has 3,000 users. All the users are assigned Microsoft 365 E3 licenses.
Some users are assigned licenses for all Microsoft 365 services. Other users are assigned licenses for only certain Microsoft 365 services.
You need to determine whether a user named User1 is licensed for Exchange Online only.
Solution: You run the Get-MsolAccountSku cmdlet.
Does this meet the goal?
- Yes
- N0
Explanation:
The Get-MsolAccountSku cmdlet returns all the SKUs that the company owns. It does not tell you which licenses are assigned to users. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has 3,000 users. All the users are assigned Microsoft 365 E3 licenses.
Some users are assigned licenses for all Microsoft 365 services. Other users are assigned licenses for only certain Microsoft 365 services.
You need to determine whether a user named User1 is licensed for Exchange Online only.
Solution: You launch the Azure portal, and then review the Licenses blade.
Does this meet the goal?
- Yes
- No
Explanation:
In the Licenses blade, click All Products then select the E3 License. This will display a list of all users assigned an E3 license. Select User1. You’ll see how many services are assigned in the Enabled Services column. Click on the number in the Enabled Services column for User1 and you’ll be taken to the licenses page for that user. Click on the number in the Enabled Services column for User1 again and a page will open which shows you exactly which services are enabled or disabled.
Alternatively, you can go into the user account properties directly then select Licenses. This will display the licenses blade for that user. You can then click on the number in the Enabled Services column for the user and a page will open which shows you exactly which services are enabled or disabled. -
HOTSPOT
You have an Active Directory domain named Adatum.com that is synchronized to Azure Active Directory as shown in the exhibit.

MS-100 Microsoft 365 Identity and Services Part 07 Q20 075 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
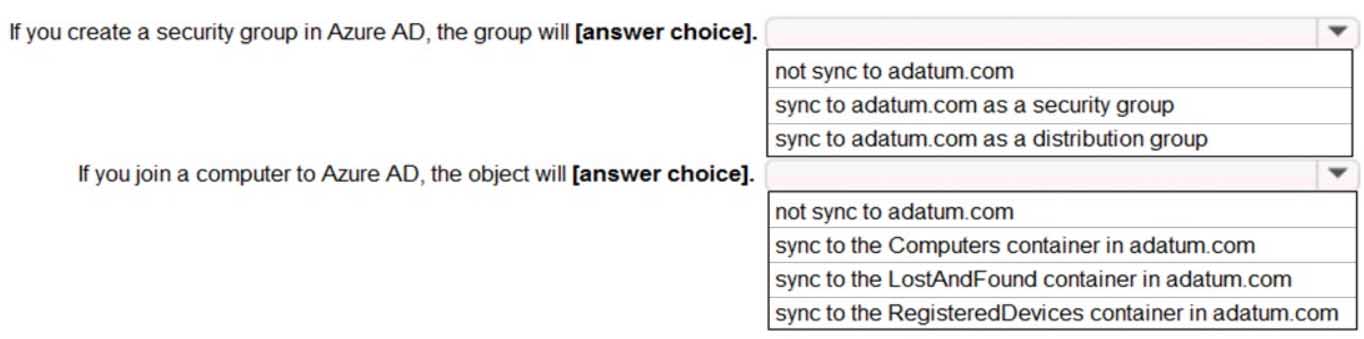
MS-100 Microsoft 365 Identity and Services Part 07 Q20 076 Question 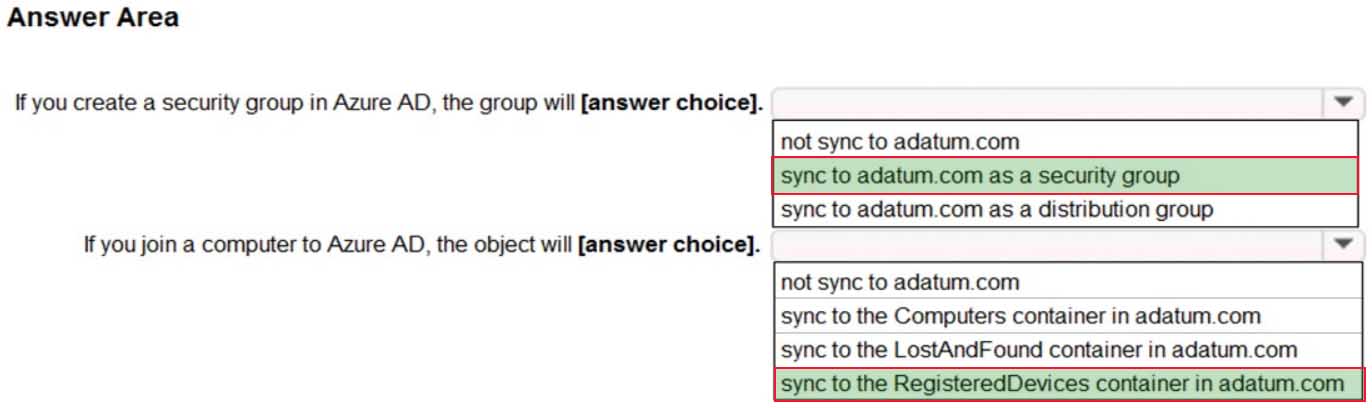
MS-100 Microsoft 365 Identity and Services Part 07 Q20 076 Answer Explanation:Group Writeback is enabled in the Azure AD Connect configuration so groups created in Azure Active Directory will be synchronized to the on-premise Active Directory. A security group created in Azure Active Directory will be synchronized to the on-premise Active Directory as a security group.
Device Writeback is enabled in the Azure AD Connect configuration so computers joined to the Azure Active Directory will be synchronized to the on-premise Active Directory. They will sync to the RegisteredDevices container in the on-premise Active Directory.