MS-100 : Microsoft 365 Identity and Services : Part 16
MS-100 : Microsoft 365 Identity and Services : Part 16
-
Your on-premises network contains the web applications shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 16 Q01 221 You purchase Microsoft 365, and then implement directory synchronization.
You plan to publish the web applications.
You need to ensure that all the applications are accessible by using the My Apps portal. The solution must minimize administrative effort.
What should you do first?
- Deploy one conditional access policy.
- Deploy one Application Proxy connector.
- Create four application registrations.
- Create a site-to-site VPN from Microsoft Azure to the on-premises network.
Explanation:
The Application Proxy connector is what connects the on-premises environment to the Azure Application Proxy.
Application Proxy is a feature of Azure AD that enables users to access on-premises web applications from a remote client. Application Proxy includes both the Application Proxy service which runs in the cloud, and the Application Proxy connector which runs on an on-premises server. Azure AD, the Application Proxy service, and the Application Proxy connector work together to securely pass the user sign-on token from Azure AD to the web application.
-
You have a Microsoft 365 E5 subscription.
All users are assigned a license to Microsoft 365 Apps for enterprise.
The users report that they do not have the option to install Microsoft 365 apps on their device as shown in the following exhibit.
MS-100 Microsoft 365 Identity and Services Part 16 Q02 222 You need to ensure that the users can install Microsoft 365 apps from the Office 365 portal.
What should you do?
- From the Microsoft 365 admin center, modify the user license settings.
- From the Microsoft Endpoint Manager admin center, create a Microsoft 365 Apps app and assign the app to the devices.
- From the Microsoft Endpoint Manager admin center, create a Microsoft 365 Apps app and assign the app to the users.
- From the Microsoft 365 admin center, modify the Services & add-ins settings.
-
Your network contains an Active Directory domain named contoso.com.
You have a Microsoft 365 subscription.
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.
You implement directory synchronization.
The developers at your company plan to build an app named App1. App1 will connect to the Microsoft Graph API to provide access to several Microsoft Office 365 services.
You need to provide the URI for the authorization endpoint that App1 must use.
What should you provide?
- https://login.microsoftonline.com/
- https://contoso.com/contoso.onmicrosoft.com/app1
- https://login.microsoftonline.com/contoso.onmicrosoft.com/
- https://myapps.microsoft.com
Explanation:
In a single tenant application, sign-in requests are sent to the tenant’s sign-in endpoint. For example, for contoso.onmicrosoft.com the endpoint would be: https://login.microsoftonline.com/contoso.onmicrosoft.com. Requests sent to a tenant’s endpoint can sign in users (or guests) in that tenant to applications in that tenant. -
DRAG DROP
Your company has a hybrid deployment of Azure Active Directory (Azure AD).
You purchase a Microsoft 365 subscription.
You plan to migrate the Home folder of each user to Microsoft 365 during several weeks. Each user has a device that runs Windows 10.
You need to recommend a solution to migrate the Home folder of five administrative users as quickly as possible.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

MS-100 Microsoft 365 Identity and Services Part 16 Q04 223 Question 
MS-100 Microsoft 365 Identity and Services Part 16 Q04 223 Answer Explanation:You need to configure a Group Policy Object (GPO) with the OneDrive settings required to redirect the Home folder of each user to Microsoft 365.
Before you can configure the Group Policy, you need to download the OneDrive Administrative Templates. These templates add the required OneDrive settings to Group Policy so you can configure the settings as required.
After the OneDrive settings have been configured in Group Policy, you can run the gpupdate /force command on the five computers to apply the new Group Policy settings immediately.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has a main office and three branch offices. All the branch offices connect to the main office by using a WAN link. The main office has a high-speed Internet connection. All the branch offices connect to the Internet by using the main office connection.
Users use Microsoft Outlook 2016 to connect to a Microsoft Exchange Server mailbox hosted in the main office.
The users report that when the WAN link in their office becomes unavailable, they cannot access their mailbox.
You create a Microsoft 365 subscription, and then migrate all the user data to Microsoft 365.
You need to ensure that all the users can continue to use Outlook to receive email messages if a WAN link fails.
Solution: For each device, you configure an additional Outlook profile that uses IMAP.
Does this meet the goal?
- Yes
- No
Explanation:The question states that the branch offices connect to the Internet by using the main office connections. Therefore, all Internet traffic goes over the WAN link between the branch office and main office.
After the migration, the users connect to their mailboxes hosted in Exchange Online over the Internet and therefore over the WAN link.If the WAN link goes down, the branch office users will not be able to connect to the Internet and therefore will not be able to access their email using Outlook.
Using IMAP to access the mailboxes would still use the WAN link so this answer does achieve the goal.
The solution is to add a direct connection to the Internet from the branch offices, so their Internet traffic does not go over the WAN link.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has a main office and three branch offices. All the branch offices connect to the main office by using a WAN link. The main office has a high-speed Internet connection. All the branch offices connect to the Internet by using the main office connection.
Users use Microsoft Outlook 2016 to connect to a Microsoft Exchange Server mailbox hosted in the main office.
The users report that when the WAN link in their office becomes unavailable, they cannot access their mailbox.
You create a Microsoft 365 subscription, and then migrate all the user data to Microsoft 365.
You need to ensure that all the users can continue to use Outlook to receive email messages if a WAN link fails.
Solution: In each branch office, you add a direct connection to the Internet.
Does this meet the goal?
- Yes
- No
Explanation:The question states that the branch offices connect to the Internet by using the main office connections. Therefore, all Internet traffic goes over the WAN link between the branch office and main office.
After the migration, the users connect to their mailboxes hosted in Exchange Online over the Internet and therefore over the WAN link.If the WAN link goes down, the branch office users will not be able to connect to the Internet and therefore will not be able to access their email using Outlook.
Adding a direct connection to the Internet from the branch offices would mean that the Internet traffic does not go over the WAN link. Therefore, if the WAN link fails, the users would still be able to access their email. Therefore, this solution does ensure that all the users can continue to use Outlook to receive email messages if a WAN link fails.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has a main office and three branch offices. All the branch offices connect to the main office by using a WAN link. The main office has a high-speed Internet connection. All the branch offices connect to the Internet by using the main office connection.
Users use Microsoft Outlook 2016 to connect to a Microsoft Exchange Server mailbox hosted in the main office.
The users report that when the WAN link in their office becomes unavailable, they cannot access their mailbox.
You create a Microsoft 365 subscription, and then migrate all the user data to Microsoft 365.
You need to ensure that all the users can continue to use Outlook to receive email messages if a WAN link fails.
Solution: You deploy a site-to-site VPN from each branch office to Microsoft Azure.
Does this meet the goal?
- Yes
- No
Explanation:The question states that the branch offices connect to the Internet by using the main office connections. Therefore, all Internet traffic goes over the WAN link between the branch office and main office.
After the migration, the users connect to their mailboxes hosted in Exchange Online over the Internet and therefore over the WAN link.If the WAN link goes down, the branch office users will not be able to connect to the Internet and therefore will not be able to access their email using Outlook.
A site-to-site VPN from each branch office to Microsoft Azure would still use the WAN link so this answer does achieve the goal.
The solution is to add a direct connection to the Internet from the branch offices, so their Internet traffic does not go over the WAN link.
-
You have an on-premises web application that is published by using a URL of https://app.contoso.local.
You purchase a Microsoft 365 subscription.
Several external users must be able to connect to the web application.
You need to recommend a solution for external access to the application. The solution must support multi-factor authentication.
Which two actions should you recommend? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- From an on-premises server, install a connector, and then publish the app.
- From the Azure Active Directory admin center, enable an Application Proxy.
- From the Azure Active Directory admin center, create a conditional access policy.
- From an on-premises server, install an Authentication Agent.
- Republish the web application by using https://app.contoso.com.
Explanation:
Azure Active Directory (Azure AD) has an Application Proxy service that enables users to access on-premises applications by signing in with their Azure AD account. The application proxy enables you to take advantage of Azure AD security features like Conditional Access and Multi-Factor Authentication.
To use Application Proxy, install a connector on each Windows server you’re using with the Application Proxy service. The connector is an agent that manages the outbound connection from the on-premises application servers to Application Proxy in Azure AD. -
HOTSPOT
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
A user named User1 has files on a Windows 10 device as shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 16 Q09 224 In Azure Information Protection, you create a label named Label1 that is configured to apply automatically. Label1 is configured as shown in the following exhibit.

MS-100 Microsoft 365 Identity and Services Part 16 Q09 225 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
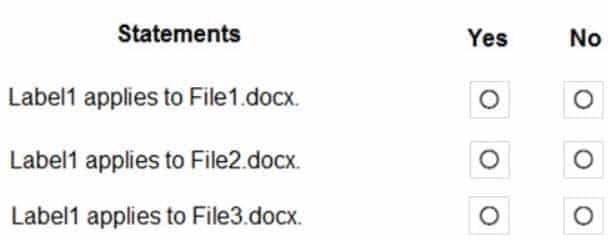
MS-100 Microsoft 365 Identity and Services Part 16 Q09 226 Question 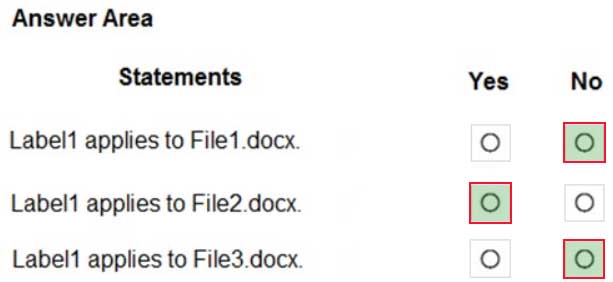
MS-100 Microsoft 365 Identity and Services Part 16 Q09 226 Answer Explanation:The phrase to match is “im” and it is case sensitive. The phrase must also appear at least twice.
Box 1: No
File1.docx contain the word “import” once onlyBox 2: Yes
File2.docx contains two occurrences of the word “import” as well as the word “imported”Box 3: No
File3.docx contains “IM” but his is not the correct letter case. -
HOTSPOT
You have a Microsoft 365 subscription that uses a default named contoso.com.
Three files were created on February 1, 2019, as shown in the following table.

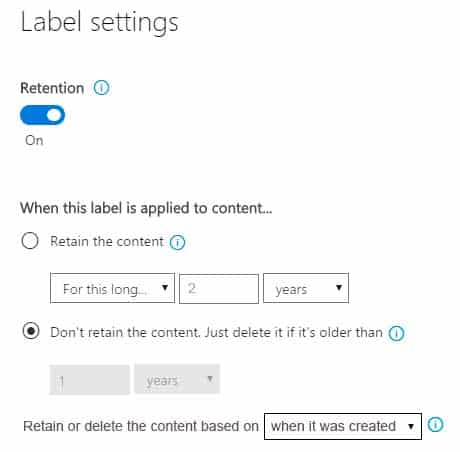
MS-100 Microsoft 365 Identity and Services Part 16 Q10 227 On March 1, 2019, you create two retention labels named Label1 and label2.
The settings for Label1 are configured as shown in the Label1 exhibit.
Label 1

MS-100 Microsoft 365 Identity and Services Part 16 Q10 228 The settings for Label2 are configured as shown in the Label1 exhibit.
Label 2
MS-100 Microsoft 365 Identity and Services Part 16 Q10 229 You apply the retention labels to Exchange email, SharePoint sites, and OneDrive accounts.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 16 Q10 230 Question 
MS-100 Microsoft 365 Identity and Services Part 16 Q10 230 Answer Explanation:Box 1: No
Retention overrides deletion.Box 2: No
Content in a document library will be moved to the first-stage Recycle Bin within 7 days of disposition, and then permanently deleted another 93 days after that. Thus 100 days in total.Box 3: No
Items in an Exchange mailbox will be permanently deleted within 14 days of disposition. -
You manage multiple devices by using Microsoft Endpoint Manager. The devices run on the following operating systems:
– Android 8.0, Android 8.1.0, and Android 9
– iOS 12 and iOS 13
– MacOS 10.14
– Windows 10You need to deploy Microsoft 365 apps to the devices.
From the Microsoft Endpoint Manager admin center, what is the minimum number of apps you should create?
- 1
- 3
- 4
- 7
-
HOTSPOT
You have retention policies in Microsoft 365 as shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 16 Q12 231 Policy1 is configured as shown in the Policy1 exhibit.
Policy1

MS-100 Microsoft 365 Identity and Services Part 16 Q12 232 Policy1 is configured as shown in the Policy2 exhibit.
Policy2

MS-100 Microsoft 365 Identity and Services Part 16 Q12 233 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
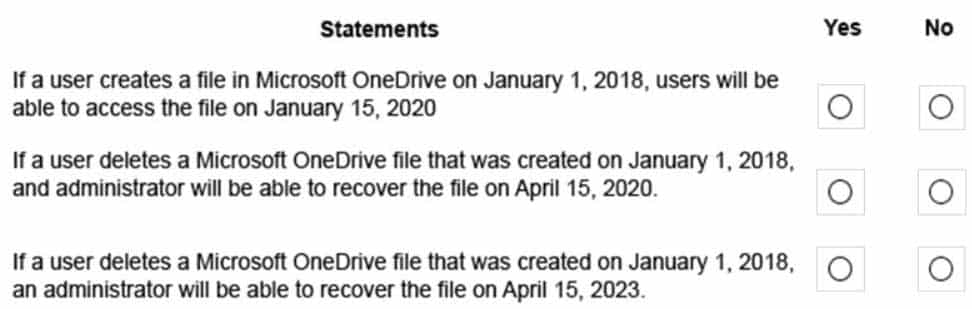
MS-100 Microsoft 365 Identity and Services Part 16 Q12 234 Question 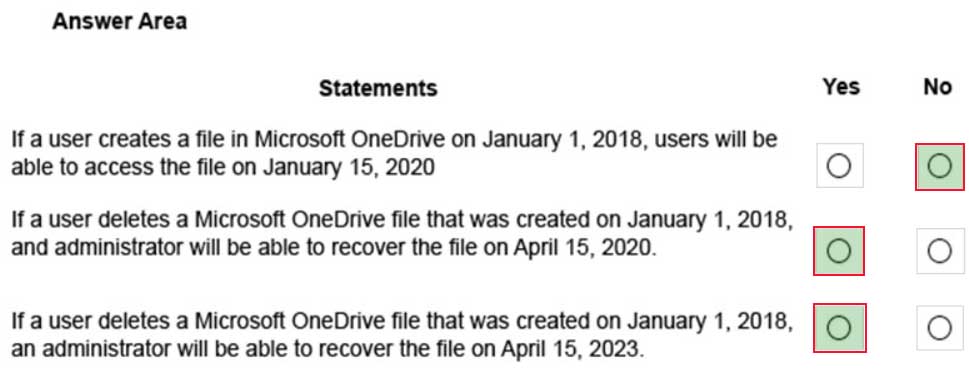
MS-100 Microsoft 365 Identity and Services Part 16 Q12 234 Answer Explanation:1. Retention wins over deletion. Suppose that one retention policy says to delete Exchange email after three years, but another retention policy says to retain Exchange email for five years and then delete it. Any content that reaches three years old will be deleted and hidden from the users’ view, but still retained in the Recoverable Items folder until the content reaches five years old, when it is permanently deleted.
2. The longest retention period wins. If content is subject to multiple policies that retain content, it will be retained until the end of the longest retention period.Box 1: No.
The file will be deleted and hidden from the users’ view, but still retained in the Recoverable Items folder. An administrator would need to recover the file.Box 2: Yes.
The file will be deleted and hidden from the users’ view, but still retained in the Recoverable Items folder. An administrator will be able to recover the file.Box 3: Yes.
2018 to 2023 is five years. Policy2 has a retention period of four years. However, Policy2 is configured to not delete the files after the four-year retention period. -
HOTSPOT
You have a Microsoft SharePoint Online site and an on-premises file server.
The site contains the files shown in the following table.
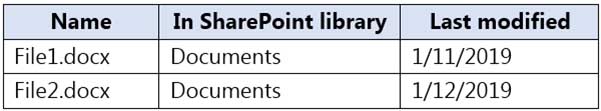
MS-100 Microsoft 365 Identity and Services Part 16 Q13 235 The file server contains the files shown in the following table.

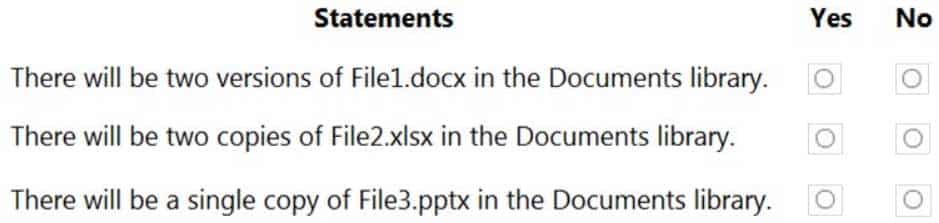
MS-100 Microsoft 365 Identity and Services Part 16 Q13 236 You migrate D:\Folder1 and D:\Folder2 to the Documents library by using the SharePoint Migration Tool as shown in the following exhibit.
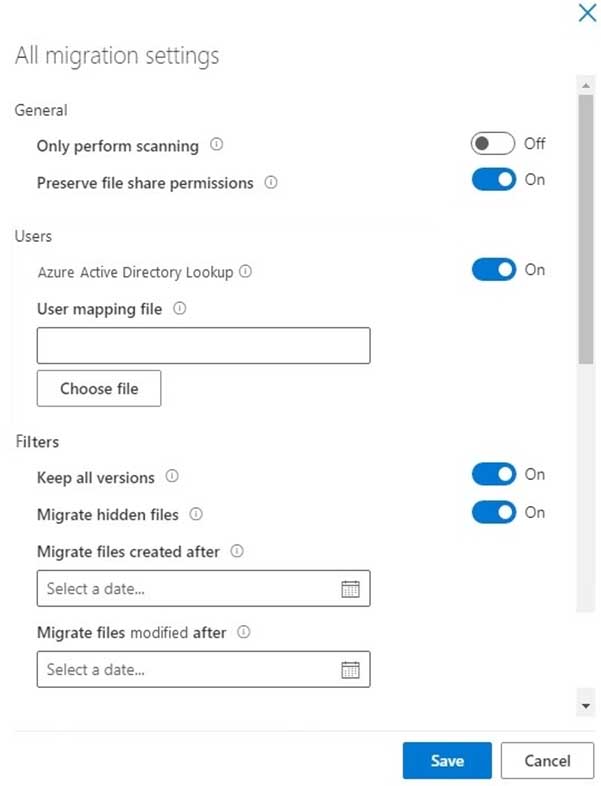
MS-100 Microsoft 365 Identity and Services Part 16 Q13 237 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
MS-100 Microsoft 365 Identity and Services Part 16 Q13 238 Question 
MS-100 Microsoft 365 Identity and Services Part 16 Q13 238 Answer Explanation:You can’t have two files with the same name and extension in a SharePoint documents library. If a file on the source server has the same and extension as an existing file in the document library, this will cause a conflict. The options for dealing with a conflict are: Skip, Merge, or Overwrite.
The “Keep all versions” setting in the exhibit is used to retain the file history for a migrated file. It does not create multiple versions of a file in a document library.
Box 1: No
File1.docx exists in the document library so this will cause a conflict.Box 2: No
Migrating two File2.xlsx files will cause a conflict.Box 3: Yes
There is only one File3.pptx in the source server and none in the document library so there will be no conflict. -
You have a Microsoft 365 subscription.
From the Security & Compliance admin center, you create a content search of all the mailboxes that contain the word ProjectX.
You need to export the results of the content search.
What do you need to download the report?
- an export key
- a password
- a user certificate
- a certification authority (CA) certificate
Explanation:
When you export a report, the data is temporarily stored in a unique Azure Storage area in the Microsoft cloud before it’s downloaded to your local computer.
To download the report from the Azure Storage Area, you need an export key. -
HOTSPOT
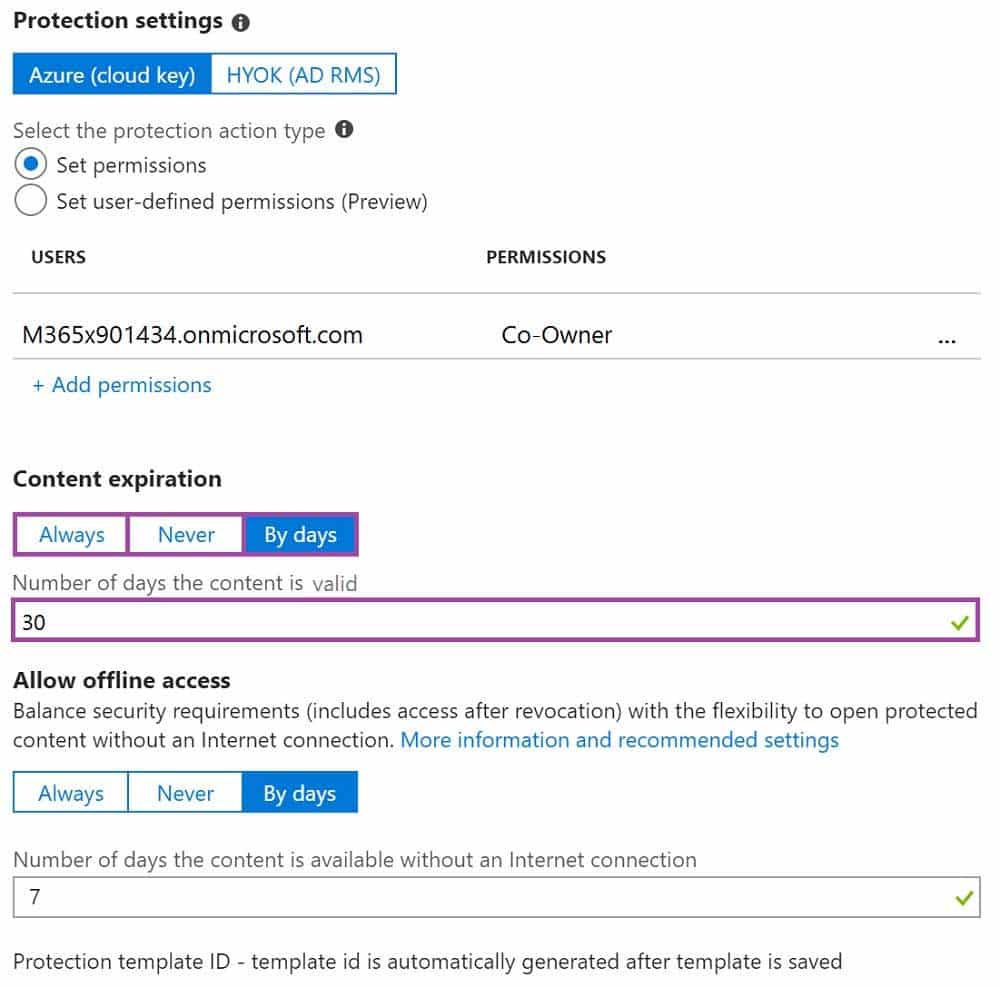
You have a document in Microsoft OneDrive that is encrypted by using Microsoft Azure Information Protection as shown in the following exhibit.
MS-100 Microsoft 365 Identity and Services Part 16 Q15 239 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 16 Q15 240 Question 
MS-100 Microsoft 365 Identity and Services Part 16 Q15 240 Answer Explanation:Box 1:
If you copy the file from OneDrive to your internet connected computer, you can open the document for up to 30 days. This is because the “Number of days the content is valid” setting is set to 30 days.Box 2:
If you email the document to a user outside your organization, the user cannot open the document. To open the document, the user would need to be added to the Users list and assigned permission. With the configuration in the exhibit, only the user listed in the Users list and the creator of the document can open the document. -
You have a Microsoft 365 subscription that contains a user named User1.
You need to ensure that User1 receives Microsoft 365 feature and service updates before the updates are released to all users.
What should you do in the Microsoft 365 admin center?
- Modify the privileged access management settings.
- Modify Office software download settings.
- Modify the Release preferences settings.
- Submit a new service request.
-
You have a Microsoft 365 subscription.
All users have their email stored in Microsoft Exchange Online
In the mailbox of a user named User, you need to preserve a copy of all the email messages that contain the word ProjectX.
What should you do first?
- From the Exchange admin center, start a mail flow message trace.
- From the Security & Compliance admin center, start a message trace.
- From the Security & Compliance admin center, create a label and label policy.
- From the Exchange admin center, create a mail flow rule.
Explanation:
When you configure conditions for a label, you can automatically assign a label to a document or email. In this case, we would create a label to label all email messages that contain the word ProjectX. We would then create a label policy to preserve a copy of all message that have the label assigned. -
HOTSPOT
You have a Microsoft 365 subscription.
You have a group named Support. Users in the Support group frequently send email messages to external users.
The manager of the Support group wants to randomly review messages that contain attachments.
You need to provide the manager with the ability to review messages that contain attachments sent from the Support group users to external users. The manager must have access to only 10 percent of the messages.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 16 Q18 241 Question 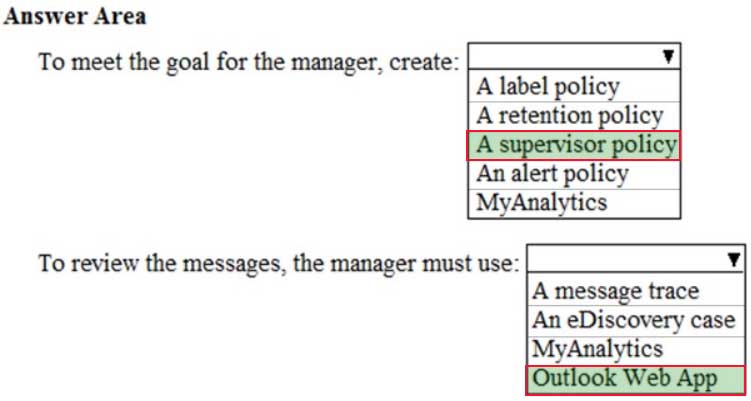
MS-100 Microsoft 365 Identity and Services Part 16 Q18 241 Answer Explanation:Supervision policies in Office 365 allow you to capture employee communications for examination by designated reviewers. You can define specific policies that capture internal and external email, Microsoft Teams, or 3rd-party communications in your organization.
You create supervision policies in the Compliance center. These policies define which communications and users are subject to review in your organization and specify who should perform reviews.
If you want to reduce the amount of content to review, you can specify a percentage of all the communications governed by a supervision policy. A real-time, random sample of content is selected from the total percentage of content that matches chosen policy conditions.
-
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains the file servers shown in the following table.

MS-100 Microsoft 365 Identity and Services Part 16 Q19 242 A file named File1.abc is stored on Server1. A file named File2.abc is stored on Server2. Three apps named App1, App2, and App3 all open files that have the .abc file extension.
You implement Windows Information Protection (WIP) by using the following configurations:
– Exempt apps: App2
– Protected apps: App1
– Windows Information Protection mode: Block
– Network boundary: IPv4 range of 192.168.1.1-192.168.1.255You need to identify the apps from which you can open File1.abc
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-100 Microsoft 365 Identity and Services Part 16 Q19 243 Question 
MS-100 Microsoft 365 Identity and Services Part 16 Q19 243 Answer Explanation:Box 1: Yes.
App1 is a protect app in the Windows Information Protection policy. File1 is stored on Server1 which is in the Network Boundary defined in the policy. Therefore, you can open File1 in App1.Box 2: Yes.
App2 is exempt in the Windows Information Protection policy. The protection mode in the policy is block so all apps that are not included in the policy cannot be used to open the file… except for exempt apps. Therefore, you can open File1 in App2.Box 3: No.
The protection mode in the policy is block so all apps that are not included in the policy as protected apps or listed as exempt from the policy cannot be used to open the file. Therefore, you cannot open File from in App3. -
You have a Microsoft Power Platform production environment that contains a custom model-driven Microsoft Power Apps app.
How many days will system backups be retained for the environment?
- 7
- 14
- 28
- 90
Explanation:
All your environments, except Trial environments (standard and subscription-based), are backed up. System backups for production environments that have been created with a database and have one or more Dynamics 365 applications installed are retained up to 28 days. System backups for production environments which do not have Dynamics 365 applications deployed in them will be retained for 7 days. System backups for sandbox environments will be retained for 7 days.