MS-101 : Microsoft 365 Mobility and Security : Part 04
MS-101 : Microsoft 365 Mobility and Security : Part 04
-
HOTSPOT
You have a Microsoft 365 E5 tenant that contains two users named User1 and User2 and the groups shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 04 Q01 067 You have a Microsoft Intune enrollment policy that has the following settings:
MDM user scope: Some
– Groups: Group1
MAM user scope: Some
– Groups: Group2You purchase the devices shown in the following table.
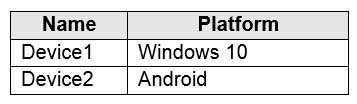
MS-101 Microsoft 365 Mobility and Security Part 04 Q01 068 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 04 Q01 069 Question 
MS-101 Microsoft 365 Mobility and Security Part 04 Q01 069 Answer -
HOTSPOT
You have a Microsoft 365 tenant that contains devices enrolled in Microsoft Intune. The devices are configured as shown in the following table.
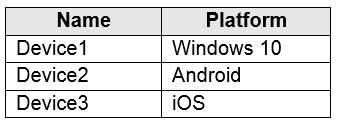
MS-101 Microsoft 365 Mobility and Security Part 04 Q02 070 You plan to perform the following device management tasks in Microsoft Endpoint Manager:
Deploy a VPN connection by using a VPN device configuration profile.
Configure security settings by using an Endpoint Protection device configuration profile.You need to identify which devices will support the management tasks.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MS-101 Microsoft 365 Mobility and Security Part 04 Q02 071 Question 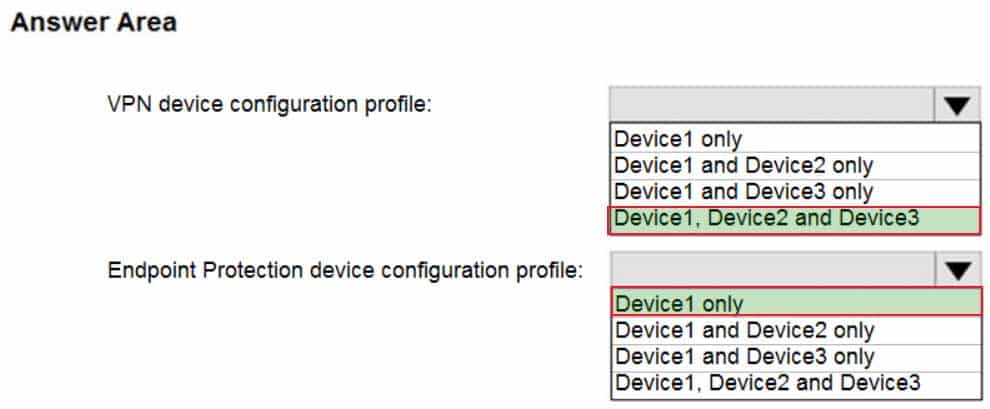
MS-101 Microsoft 365 Mobility and Security Part 04 Q02 071 Answer -
DRAG DROP
You have a Microsoft 365 E5 tenant that contains 500 Android devices enrolled in Microsoft Intune.
You need to use Microsoft Endpoint Manager to deploy a managed Google Play app to the devices.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

MS-101 Microsoft 365 Mobility and Security Part 04 Q03 072 Question 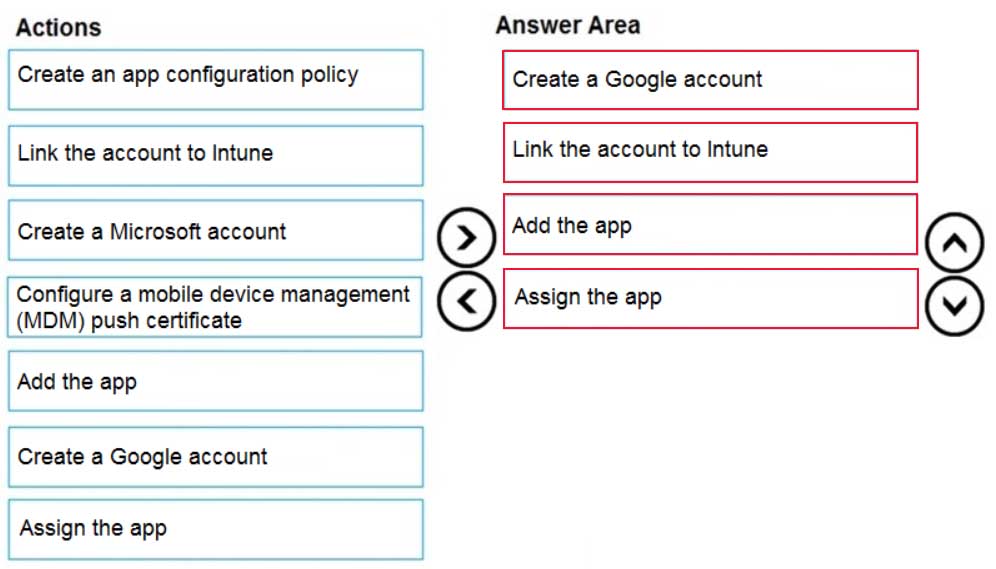
MS-101 Microsoft 365 Mobility and Security Part 04 Q03 072 Answer -
You have a Microsoft 365 E5 tenant that contains four devices enrolled in Microsoft Intune as shown in the following table.
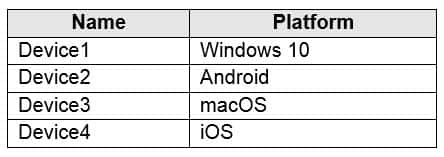
MS-101 Microsoft 365 Mobility and Security Part 04 Q04 073 You plan to deploy Microsoft 365 Apps for enterprise by using Microsoft Endpoint Manager.
To which devices can you deploy Microsoft 365 Apps for enterprise?
- Device1 only
- Device1 and Device3 only
- Device2 and Device4 only
- Device1, Device2, and Device3 only
- Device1, Device2, Device3, and Device4
-
You have a Microsoft 365 E5 tenant that contains the devices shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 04 Q05 074 You plan to review device startup performance issues by using Endpoint analytics.
Which devices can you monitor by using Endpoint analytics?
- Device1 only
- Device1 and Device2 only
- Device1, Device2, and Device3 only
- Device1, Device2, and Device4 only
- Device1, Device2, Device3, and Device4
-
You have a Microsoft 365 E5 tenant that contains 100 Windows 10 devices.
You plan to deploy a Windows 10 Security Baseline profile that will protect secrets stored in memory.
What should you configure in the profile?
- Microsoft Defender Credential Guard
- BitLocker Drive Encryption (BitLocker)
- Microsoft Defender
- Microsoft Defender Exploit Guard
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer that runs Windows 10.
You need to verify which version of Windows 10 is installed.
Solution: From Device Manager, you view the computer properties.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer that runs Windows 10.
You need to verify which version of Windows 10 is installed.
Solution: At a command prompt, you run the winver.exe command.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer that runs Windows 10.
You need to verify which version of Windows 10 is installed.
Solution: From the Settings app, you select Update & Security to view the update history.
Does this meet the goal?
- Yes
- No
-
Case Study
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
The company has the employees and devices shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 04 Q10 075 Contoso recently purchased a Microsoft 365 E5 subscription.
Existing Environment
The network contains an on-premises Active Directory forest named contoso.com. The forest contains the servers shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 04 Q10 076 All servers run Windows Server 2016. All desktops and laptops run Windows 10 Enterprise and are joined to the domain.
The mobile devices of the users in the Montreal and Seattle offices run Android. The mobile devices of the users in the New York office run iOS.
The domain is synced to Azure Active Directory (Azure AD) and includes the users shown in the following table.
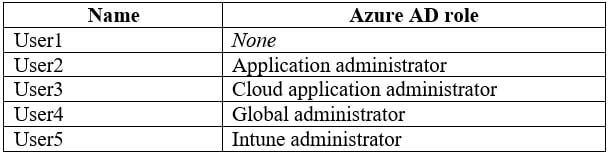
MS-101 Microsoft 365 Mobility and Security Part 04 Q10 077 The domain also includes a group named Group1.
Requirements
Planned Changes
Contoso plans to implement the following changes:
– Implement Microsoft 365.
– Manage devices by using Endpoint Manager.
– Implement Azure Advanced Threat Protection (ATP).
– Update computers in Seattle and Montreal with the fall Semi-Annual Channel feature update.
– Update computers in the New York office with the spring Semi-Annual Channel feature update.Technical Requirements
Contoso identifies the following technical requirements:
– When a Windows 10 device is joined to Azure AD, the device must enroll to Endpoint Manager automatically.
– Dedicated support technicians must enroll all the Montreal office mobile devices in Endpoint Manager.
– Each dedicated support technician must be assigned only a single Device Enrollment Manager (DEM) account.
– User1 must be able to enroll all the New York office mobile devices in Endpoint Manager.
– Azure ATP sensors must be installed and must NOT use port mirroring.
– Whenever possible, the principle of least privilege must be used.
– A Microsoft Store for Business must be created.Compliance Requirements
Contoso identifies the following compliance requirements:
– Ensure that the users in Group1 can only access Microsoft Exchange Online from devices that are enrolled in Endpoint Manager and configured in accordance with the corporate policy.
– Configure Windows Information Protection (WIP) for the Windows 10 devices.-
You need to ensure that the support technicians can meet the technical requirement for the Montreal office mobile devices.
What is the minimum of dedicated support technicians required?
- 1
- 4
- 7
- 31
Explanation:Contoso identifies the following technical requirements:
– Dedicated support technicians must enroll all the Montreal office mobile devices in Endpoint Manager.
– Each dedicated support technician must be assigned only a single Device Enrollment Manager (DEM) account.You can enroll up to 1,000 mobile devices with a single Azure Active Directory account by using a device enrollment manager (DEM) account. We have 3,100 devices; hence we will need 4 DEMs at a minimum.
-
You need to create the Microsoft Store for Business.
Which user can create the store?
- User2
- User3
- User4
- User5
-
HOTSPOT
You need to meet the Intune requirements for the Windows 10 devices.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
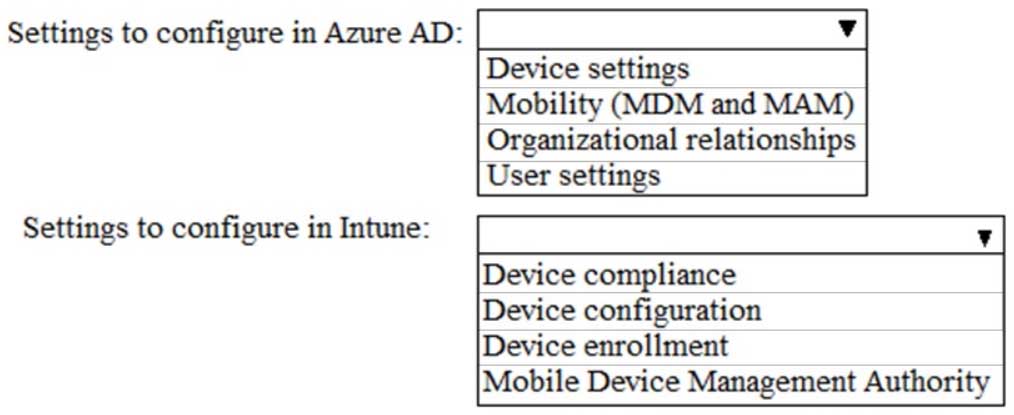
MS-101 Microsoft 365 Mobility and Security Part 04 Q10 078 Question 
MS-101 Microsoft 365 Mobility and Security Part 04 Q10 078 Answer -
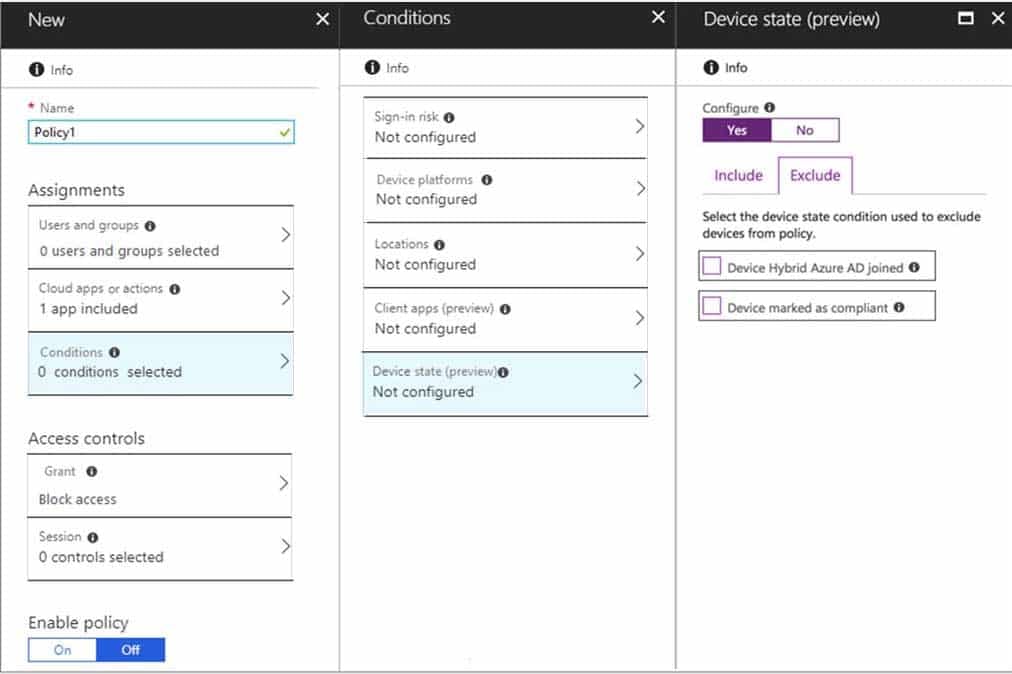
HOTSPOT
You need to configure a conditional access policy to meet the compliance requirements.
You add Exchange Online as a cloud app.
Which two additional settings should you configure in Policy1? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
MS-101 Microsoft 365 Mobility and Security Part 04 Q10 079 Question 
MS-101 Microsoft 365 Mobility and Security Part 04 Q10 079 Answer -
HOTSPOT
As of March, how long will the computers in each office remain supported by Microsoft? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 04 Q10 080 Question 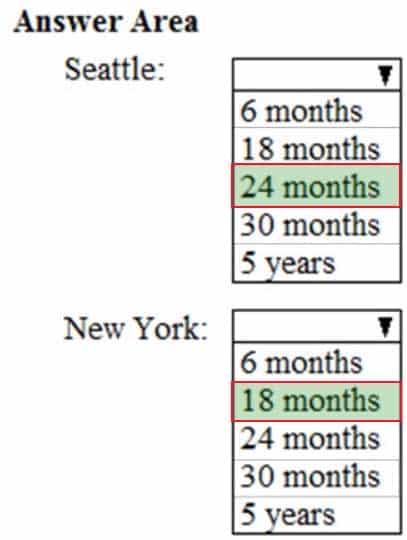
MS-101 Microsoft 365 Mobility and Security Part 04 Q10 080 Answer Explanation:Contoso plans to implement the following changes:
- Update computers in Seattle and Montreal with the fall Semi-Annual Channel feature update.
– Update computers in the New York office with the spring Semi-Annual Channel feature update.Box 1: 24 months
September Feature Updates (fall Semi-Annual Channel feature updates) are serviced for 30 months from release date but by March, 6 of those 30 months have lapsed; hence, 24 months remainsBox 2: 18 months
March Feature Updates (spring Semi-Annual Channel feature updates) are serviced for 18 months from release date -
You need to ensure that User1 can enroll the devices to meet the technical requirements.
What should you do?
- From the Azure Active Directory admin center, assign User1 the Cloud device administrator role.
- From the Azure Active Directory admin center, configure the Maximum number of devices per user setting.
- From the Endpoint Management admin center, add User1 as a device enrollment manager.
- From the Endpoint Management admin center, configure the Enrollment restrictions.
-
HOTSPOT
You need to meet the technical requirements and planned changes for Intune.
What should you do? To answer, select the appropriate options is the answer area.
NOTE: Each correct selection is worth one point.
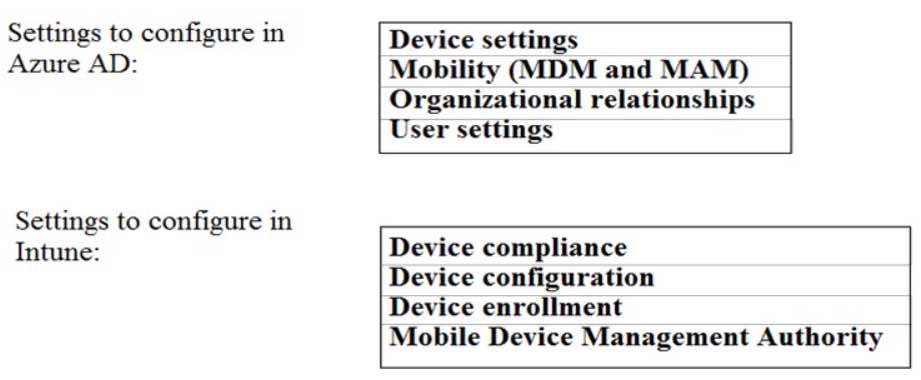
MS-101 Microsoft 365 Mobility and Security Part 04 Q10 081 Question 
MS-101 Microsoft 365 Mobility and Security Part 04 Q10 081 Answer
-
-
Case Study
Overview
ADatum Corporation is an international financial services company that has 5,000 employees.
ADatum has six offices: a main office in New York and five branch offices in Germany, the United Kingdom, France, Spain, and Italy.
All the offices are connected to each other by using a WAN link. Each office connects directly to the Internet.
Existing Environment
Current Infrastructure
ADatum recently purchased a Microsoft 365 subscription.
All user files are migrated to Microsoft 365.
All mailboxes are hosted in Microsoft 365. The users in each office have email suffixes that include the country of the user, for example, user1@us.adatum.com or user2@uk.adatum.com.
Each office has a security information and event management (SIEM) appliance. The appliance comes from three different vendors.
ADatum uses and processes Personally Identifiable Information (PII).
Problem Statements
ADatum entered into litigation. The legal department must place a hold on all the documents of a user named User1 that are in Microsoft 365.
Requirements
Business Goals
ADatum wants to be fully compliant with all the relevant data privacy laws in the regions where is operates.
ADatum wants to minimize the cost of hardware and software whenever possible.
Technical Requirements
ADatum identifies the following technical requirements:
– Centrally perform log analysis for all offices.
– Aggregate all data from the SIEM appliances to a central cloud repository for later analysis.
– Ensure that a SharePoint administrator can identify who accessed a specific file stored in a document library.
– Provide the users in the finance department with access to Service assurance information in Microsoft Office 365.
– Ensure that documents and email messages containing the PII data of European Union (EU) citizens are preserved for 10 years.
– If a user attempts to download 1,000 or more files from Microsoft SharePoint Online within 30 minutes, notify a security administrator and suspend the user’s user account.
– A security administrator requires a report that shown which Microsoft 365 users signed in. Based on the report, the security administrator will create a policy to require multi-factor authentication when a sign-in is high risk.
– Ensure that the users in the New York office can only send email messages that contain sensitive U.S. PII data to other New York office uses. Email messages must be monitored to ensure compliance. Auditors in the New York office must have access to reports that show the sent and received email messages containing sensitive U.S. PII data.-
You need to recommend a solution for the security administrator. The solution must meet the technical requirements.
What should you include in the recommendation?
- Microsoft Azure Active Directory (Azure AD) Privileged Identity Management
- Microsoft Azure Active Directory (Azure AD) Identity Protection
- Microsoft Azure Active Directory (Azure AD) conditional access policies
- Microsoft Azure Active Directory (Azure AD) authentication methods
-
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization.
You need to be notified if the SharePoint sharing policy is modified in the future.
Solution: From the Security & Compliance admin center, you create a threat management policy.
Does this meet the goal?
- Yes
- No
Explanation:
From the Security & Compliance admin center, Alerts, you create a new alert policy. -
You have a Microsoft 365 subscription.
You need to be notified if users receive email containing a file that has a virus.
What should you do?
- From the Exchange admin center, create an in-place eDiscovery & hold.
- From the Security & Compliance admin center, create a safe attachments policy.
- From the Security & Compliance admin center, create a data loss prevention (DLP) policy.
- From the Security & Compliance admin center, create an alert policy.
-
You have a Microsoft Azure Active Directory (Azure AD) tenant.
The organization needs to sign up for Microsoft Store for Business. The solution must use the principle of least privilege.
Which role should you assign to the user?
- Global administrator
- Cloud application administrator
- Application administrator
- Service administrator
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization.
You need to be notified if the SharePoint sharing policy is modified in the future.
Solution: From the SharePoint site, you create an alert.
Does this meet the goal?
- Yes
- No
-
You have a Microsoft 365 subscription and an on-premises Active Directory domain named contoso.com. All client computers run Windows 10 Enterprise and are joined to the domain.
You need to enable Microsoft Defender Credential Guard on all the computers.
What should you do?
- From the Security & Compliance admin center, configure the DKIM signatures for the domain.
- From a domain controller, create a Group Policy object (GPO) that enables the Restrict delegation of credentials to remote servers setting.
- From the Security & Compliance admin center, create a device security policy.
- From a domain controller, create a Group Policy object (GPO) that enabled the Turn On Virtualization Based Security setting.
-
Your company has a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com.
The company purchases a cloud app named App1 that supports Microsoft Cloud App Security monitoring.
You configure App1 to be available from the My Apps portal.
You need to ensure that you can monitor App1 from Cloud App Security.
What should you do?
- From the Azure Active Directory admin center, create a conditional access policy.
- From the Azure Active Directory admin center, create an app registration.
- From the Endpoint Management admin center, create an app protection policy.
- From the Endpoint Management admin center, create an app configuration policy.
-
HOTSPOT
You use Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
You have the Microsoft Defender ATP machine groups shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 04 Q18 082 You plan to onboard computers to Microsoft Defender ATP as shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 04 Q18 083 To which machine group will each computer be added? To answer, select the appropriate options in the answer are.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 04 Q18 084 Question 
MS-101 Microsoft 365 Mobility and Security Part 04 Q18 084 Answer -
Your company has 5,000 Windows 10 devices. All the devices are protected by using Microsoft Defender Advanced Threat Protection (ATP).
You need to create a filtered view that displays which Microsoft Defender ATP alert events have a high severity and occurred during the last seven days.
What should you use in Microsoft Defender ATP?
- the threat intelligence API
- Automated investigations
- Threat analytics
- Advanced hunting
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You need to prevent users from accessing your Microsoft SharePoint Online sites unless the users are connected to your on-premises network.
Solution: From the Device Management admin center, you create a device configuration profile.
Does this meet the goal?
- Yes
- No