MS-101 : Microsoft 365 Mobility and Security : Part 05
MS-101 : Microsoft 365 Mobility and Security : Part 05
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1.
Your company purchases a Microsoft 365 subscription.
You need to ensure that User1 is assigned the required role to create file policies and manage alerts in the Cloud App Security admin center.
Solution: From the Security & Compliance admin center, you assign the Security Administrator role to User1.
Does this meet the goal?
- Yes
- No
Explanation:
Security Administrator has the required permissions, but it is not assigned from the Security and Compliance Center. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1.
Your company purchases a Microsoft 365 subscription.
You need to ensure that User1 is assigned the required role to create file policies and manage alerts in the Cloud App Security admin center.
Solution: From the Azure Active Directory admin center, you assign the Security administrator role to User1.
Does this meet the goal?
- Yes
- No
Explanation:
The Security administrator has Full access with full permissions in Cloud App Security. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1.
Your company purchases a Microsoft 365 subscription.
You need to ensure that User1 is assigned the required role to create file policies and manage alerts in the Cloud App Security admin center.
Solution: From the Azure Active Directory admin center, you assign the Compliance administrator role to User1.
Does this meet the goal?
- Yes
- No
Explanation:
The Compliance administrator has read-only permissions and can manage alerts, can create and modify file policies, allow file governance actions, and view all the built-in reports under Data Management, but cannot access Security recommendations for cloud platforms. -
HOTSPOT
Your company purchases a cloud app named App1.
You plan to publish App1 by using a conditional access policy named Policy1.
You need to ensure that you can control access to App1 by using a Microsoft Cloud App Security session policy.
Which two settings should you modify in Policy1? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 05 Q04 085 Question 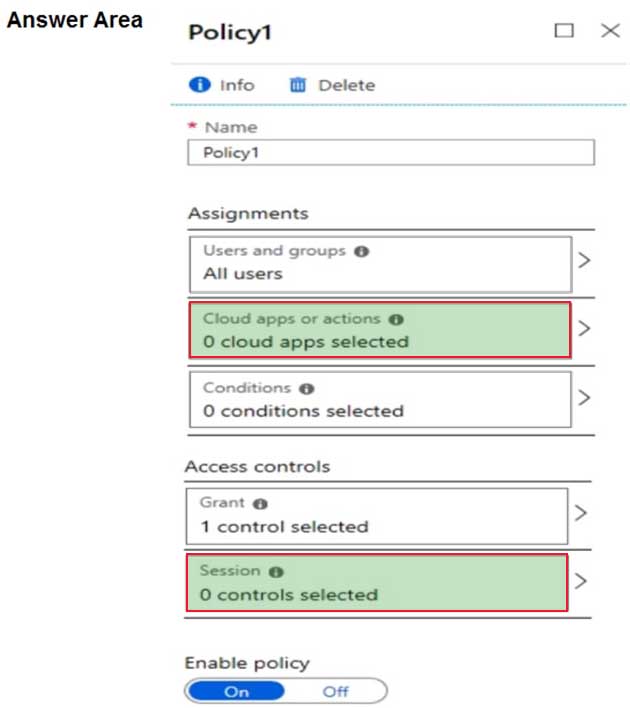
MS-101 Microsoft 365 Mobility and Security Part 05 Q04 085 Answer -
HOTSPOT
Your company uses Microsoft Defender Advanced Threat Protection (ATP). Microsoft Defender ATP includes the machine groups shown in the following table.
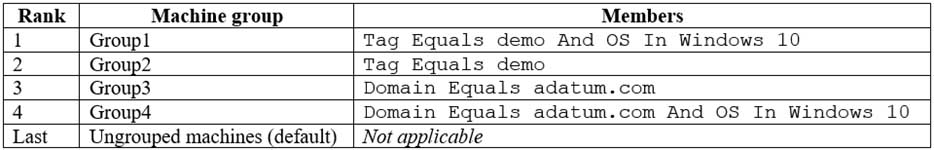
MS-101 Microsoft 365 Mobility and Security Part 05 Q05 086 You onboard a computer named computer1 to Microsoft Defender ATP as shown in the following exhibit.

MS-101 Microsoft 365 Mobility and Security Part 05 Q05 087 Use the drop-down menus to select the answer choice that completes each statement.
NOTE: Each correct selection is worth one point.
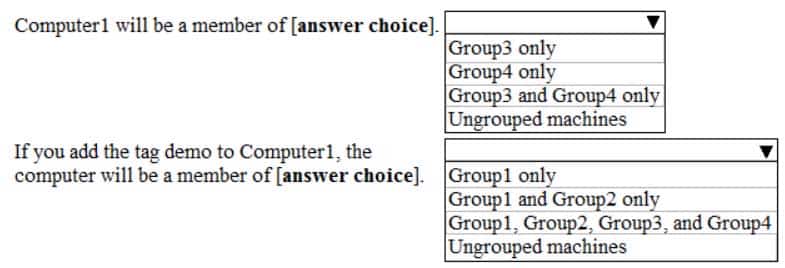
MS-101 Microsoft 365 Mobility and Security Part 05 Q05 088 Question 
MS-101 Microsoft 365 Mobility and Security Part 05 Q05 088 Answer -
HOTSPOT
You have a Microsoft 365 subscription.
You are planning a threat management solution for your organization.
You need to minimize the likelihood that users will be affected by the following threats:
– Opening files in Microsoft SharePoint that contain malicious content
– Impersonation and spoofing attacks in email messagesWhich policies should you create in the Security & Compliance admin center? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 05 Q06 089 Question 
MS-101 Microsoft 365 Mobility and Security Part 05 Q06 089 Answer Explanation:Box 1: ATP Safe Attachments
ATP Safe Attachments provides zero-day protection to safeguard your messaging system, by checking email attachments for malicious content. It routes all messages and attachments that do not have a virus/malware signature to a special environment, and then uses machine learning and analysis techniques to detect malicious intent. If no suspicious activity is found, the message is forwarded to the mailbox.Box 2: ATP anti-phishing
ATP anti-phishing protection detects attempts to impersonate your users and custom domains. It applies machine learning models and advanced impersonation-detection algorithms to avert phishing attacks.ATP Safe Links provides time-of-click verification of URLs, for example, in emails messages and Office files. Protection is ongoing and applies across your messaging and Office environment. Links are scanned for each click: safe links remain accessible and malicious links are dynamically blocked.
-
You have a Microsoft 365 subscription.
All users have their email stored in Microsoft Exchange Online.
In the mailbox of a user named User1, you need to preserve a copy of all the email messages that contain the word ProjectX.
What should you do first?
- From Microsoft Cloud App Security, create an access policy.
- From the Security & Compliance admin center, create an eDiscovery case.
- From Microsoft Cloud App Security, create an activity policy.
- From the Security & Compliance admin center, create a data loss prevention (DLP) policy.
Explanation:
A DLP policy contains a few basic things:
Where to protect the content: locations such as Exchange Online, SharePoint Online, and OneDrive for Business sites, as well as Microsoft Teams chat and channel messages.
When and how to protect the content by enforcing rules comprised of:
Conditions the content must match before the rule is enforced. For example, a rule might be configured to look only for content containing Social Security numbers that’s been shared with people outside your organization.
Actions that you want the rule to take automatically when content matching the conditions is found. For example, a rule might be configured to block access to a document and send both the user and compliance officer an email notification. -
You have a Microsoft 365 subscription.
From the subscription, you perform an audit log search, and you download all the results.
You plan to review the audit log data by using Microsoft Excel.
You need to ensure that each audited property appears in a separate Excel column.
What should you do first?
- From Power Query Editor, transform the JSON data.
- Format the Operations column by using conditional formatting.
- Format the AuditData column by using conditional formatting.
- From Power Query Editor, transform the XML data.
Explanation:
After you search the Office 365 audit log and download the search results to a CSV file, the file contains a column named AuditData, which contains additional information about each event. The data in this column is formatted as a JSON object, which contains multiple properties that are configured as property:value pairs separated by commas. You can use the JSON transform feature in the Power Query Editor in Excel to split each property in the JSON object in the AuditData column into multiple columns so that each property has its own column. This lets you sort and filter on one or more of these properties -
You have a Microsoft 365 subscription.
You need to be notified if users receive email containing a file that has a virus.
What should you do?
- From the Exchange admin center, create a spam filter policy.
- From the Security & Compliance admin center, create a data governance event.
- From the Security & Compliance admin center, create an alert policy.
- From the Exchange admin center, create a mail flow rule.
Explanation:You can create alert policies to track malware activity and data loss incidents. We’ve also included several default alert policies that help you monitor activities such as assigning admin privileges in Exchange Online, malware attacks, phishing campaigns, and unusual levels of file deletions and external sharing.
The Email messages containing malware removed after delivery default alert generates an alert when any messages containing malware are delivered to mailboxes in your organization.
Incorrect answers:
A: A spam filter policy includes selecting the action to take on messages that are identified as spam. Spam filter policy settings are applied to inbound messages.B: A data governance event commences when an administrator creates it, following which background processes look for content relating to the event and take the retention action defined in the label. The retention action can be to keep or remove items, or to mark them for manual disposition.
D: You can inspect email attachments in your Exchange Online organization by setting up mail flow rules. Exchange Online offers mail flow rules that provide the ability to examine email attachments as a part of your messaging security and compliance needs. However, mail flow rules are not used to detect malware in emails.
-
DRAG DROP
You have the Microsoft Azure Advanced Threat Protection (ATP) workspace shown in the Workspace exhibit. (Click the Workspace tab.)

MS-101 Microsoft 365 Mobility and Security Part 05 Q10 090 The sensors settings for the workspace are configured as shown in the Sensors exhibit. (Click the Sensors tab.)

MS-101 Microsoft 365 Mobility and Security Part 05 Q10 091 You need to ensure that Azure ATP stores data in Asia.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

MS-101 Microsoft 365 Mobility and Security Part 05 Q10 092 Question 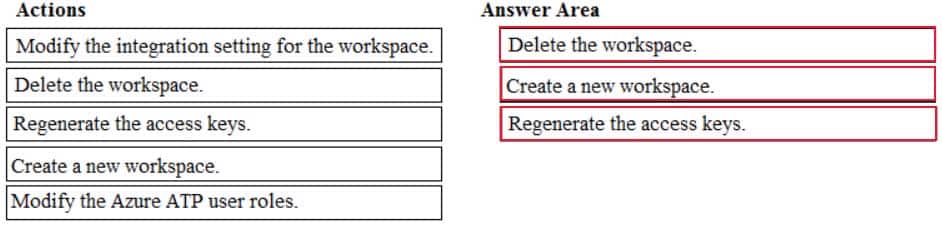
MS-101 Microsoft 365 Mobility and Security Part 05 Q10 092 Answer -
Your company has five security information and event management (SIEM) appliances. The traffic logs from each appliance are saved to a file share named Logs.
You need to analyze the traffic logs.
What should you do from Microsoft Cloud App Security?
- Click Investigate, and then click Activity log.
- Click Control, and then click Policies. Create a file policy.
- Click Discover, and then click Create snapshot report.
- Click Investigate, and then click Files.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1.
Your company purchases a Microsoft 365 subscription.
You need to ensure that User1 is assigned the required role to create file policies and manage alerts in the Cloud App Security admin center.
Solution: From the Cloud App Security admin center, you assign the App/instance admin role for all Microsoft Online Services to User1.
Does this meet the goal?
- Yes
- No
Explanation:
App/instance admin: Has full or read-only permissions to all of the data in Microsoft Cloud App Security that deals exclusively with the specific app or instance of an app selected. -
Your company has a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com.
The tenant is configured to use Azure AD Identity Protection.
You plan to use an application named App1 that creates reports of Azure AD Identity Protection usage.
You register App1 in the tenant.
You need to ensure that App1 can read the risk event information of contoso.com.
To which API should you delegate permissions?
- Windows Azure Service Management API
- Windows Azure Active Directory
- Microsoft Graph
- Office 365 Management
-
Your company has a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains computers that run Windows 10 Enterprise and are managed by using Microsoft Intune. The computers are configured as shown in the following table.
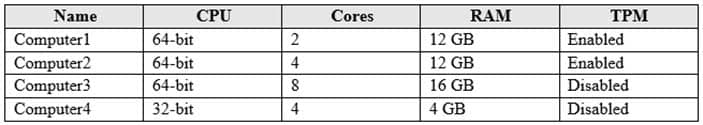
MS-101 Microsoft 365 Mobility and Security Part 05 Q14 093 You plan to implement Windows Defender Application Guard for contoso.com.
You need to identify on which two Windows 10 computers Windows Defender Application Guard can be installed.
Which two computers should you identify? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Computer1
- Computer3
- Computer2
- Computer4
-
HOTSPOT
Your company uses Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
The devices onboarded to Microsoft Defender ATP are shown in the following table.
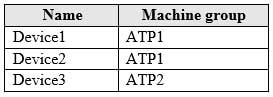
MS-101 Microsoft 365 Mobility and Security Part 05 Q15 094 The alerts visible in the Microsoft Defender ATP alerts queue are shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 05 Q15 095 You create a suppression rule that has the following settings:
Triggering IOC: Any IOC
Action: Hide alert
Suppression scope: Alerts on ATP1 machine groupFor each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 05 Q15 096 Question 
MS-101 Microsoft 365 Mobility and Security Part 05 Q15 096 Answer Explanation:A suppression rule will not affect alerts that are already in the alerts queue. Only new alerts will be suppressed.
-
HOTSPOT
Your company has a Microsoft 365 subscription.
You need to configure Microsoft 365 to meet the following requirements:
– Malware found in email attachments must be quarantined for 20 days.
– The email address of senders to your company must be verified.Which two options should you configure in the Security & Compliance admin center? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
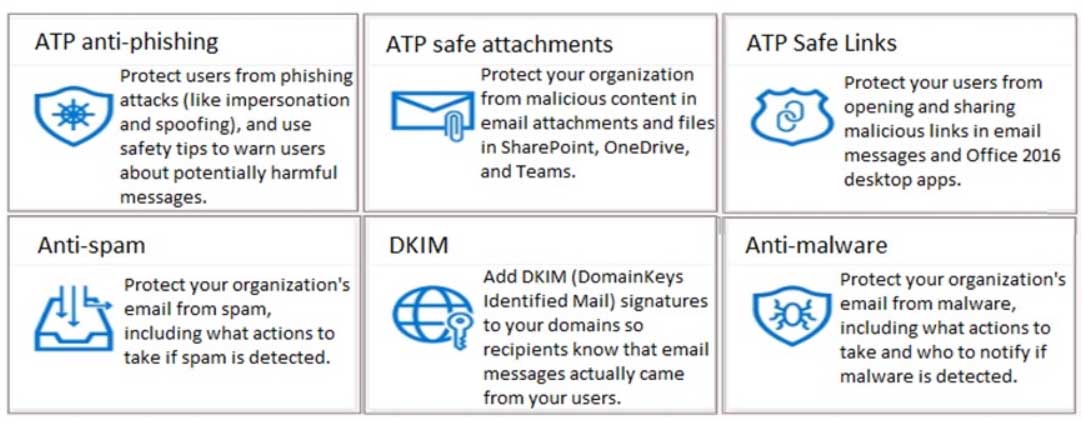
MS-101 Microsoft 365 Mobility and Security Part 05 Q16 097 Question 
MS-101 Microsoft 365 Mobility and Security Part 05 Q16 097 Answer -
You have a Microsoft 365 subscription that uses Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
All the devices in your organization are onboarded to Microsoft Defender ATP.
You need to ensure that an alert is generated if malicious activity was detected on a device during the last 24 hours.
What should you do?
- From Alerts queue, create a suppression rule and assign an alert
- From the Security & Compliance admin center, create an audit log search
- From Advanced hunting, create a query and a detection rule
- From the Security & Compliance admin center, create a data loss prevention (DLP) policy
-
You have an Azure Active Directory (Azure AD) tenant and a Microsoft 365 E5 subscription. The tenant contains the users shown in the following table.
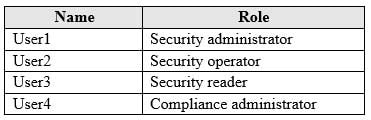
MS-101 Microsoft 365 Mobility and Security Part 05 Q18 098 You plan to implement Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
You verify that role-based access control (RBAC) is turned on in Microsoft Defender ATP.
You need to identify which user can view security incidents from the Microsoft Defender Security Center.
Which user should you identify?
- User1
- User2
- User3
- User4
-
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains 1,000 Windows 10 devices.
You perform a proof of concept (PoC) deployment of Microsoft Defender Advanced Threat Protection (ATP) for 10 test devices. During the onboarding process, you configure Microsoft Defender ATP-related data to be stored in the United States.
You plan to onboard all the devices to Microsoft Defender ATP.
You need to store the Microsoft Defender ATP data in Europe.
What should you do first?
- Create a workspace.
- Onboard a new device.
- Delete the workspace.
- Offboard the test devices.
-
You have a Microsoft 365 subscription.
You need to be notified if users receive email containing a file that has a virus.
What should you do?
- From the Exchange admin center, create an in-place eDiscovery & hold.
- From the Security & Compliance admin center, create a data loss prevention (DLP) policy.
- From the Exchange admin center, create an anti-malware policy.
- From the Exchange admin center, create a mail flow rule.