MS-101 : Microsoft 365 Mobility and Security : Part 07
MS-101 : Microsoft 365 Mobility and Security : Part 07
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription.
You create an account for a new security administrator named SecAdmin1.
You need to ensure that SecAdmin1 can manage Office 365 Advanced Threat Protection (ATP) settings and policies for Microsoft Teams, SharePoint, and OneDrive.
Solution: From the Microsoft 365 admin center, you assign SecAdmin1 the SharePoint admin role.
Does this meet the goal?
- Yes
- No
Explanation:
You need to assign the Security Administrator role. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription.
You create an account for a new security administrator named SecAdmin1.
You need to ensure that SecAdmin1 can manage Office 365 Advanced Threat Protection (ATP) settings and policies for Microsoft Teams, SharePoint, and OneDrive.
Solution: From the Azure Active Directory admin center, you assign SecAdmin1 the Teams Service Administrator role.
Does this meet the goal?
- Yes
- No
Explanation:
You need to assign the Security Administrator role. -
You have a Microsoft 365 subscription.
You need to be notified if users receive email containing a file that has a virus.
What should you do?
- From the Exchange admin center, create an in-place eDiscovery & hold.
- From the Security & Compliance admin center, create a data governance event.
- From the Exchange admin center, create an anti-malware policy.
- From the Exchange admin center, create a mail flow rule.
-
You implement Microsoft Azure Advanced Threat Protection (Azure ATP).
You have an Azure ATP sensor configured as shown in the following exhibit.

MS-101 Microsoft 365 Mobility and Security Part 07 Q04 118 How long after the Azure ATP cloud service is updated will the sensor update?
- 72 hours
- 12 hours
- 48 hours
- 7 days
- 20 hours
-
HOTSPOT
Your company uses Microsoft Defender Advanced Threat Protection (ATP). Microsoft Defender ATP contains the device groups shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 07 Q05 119 You onboard computers to Microsoft Defender ATP as shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 07 Q05 120 Of which groups are Computer1 and Computer2 members? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 07 Q05 121 Question 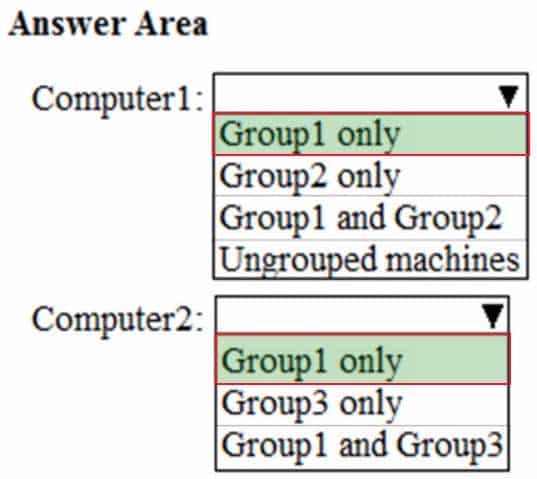
MS-101 Microsoft 365 Mobility and Security Part 07 Q05 121 Answer Explanation:When a device is matched to more than one group, it is added only to the highest ranked group.
-
You have Windows 10 devices that are managed by using Microsoft Endpoint Manager.
You need to configure the security settings in Microsoft Edge.
What should you create in Microsoft Endpoint Manager?
- an app configuration policy
- an app
- a device configuration profile
- a device compliance policy
-
HOTSPOT
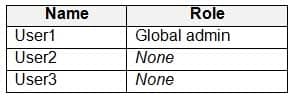
You have a Microsoft 365 E5 tenant that contains the users shown in the following table.
MS-101 Microsoft 365 Mobility and Security Part 07 Q07 122 You provision the private store in Microsoft Store for Business.
You assign Microsoft Store for Business roles to the users as shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 07 Q07 123 You need to identify which users can add apps to the private store, and which users can assign apps from Microsoft Store for Business.
Which users should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 07 Q07 124 Question 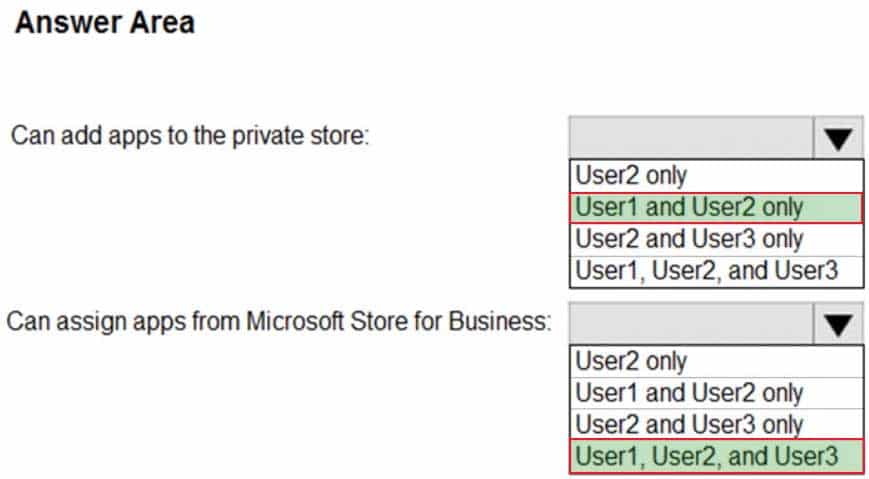
MS-101 Microsoft 365 Mobility and Security Part 07 Q07 124 Answer -
DRAG DROP
You have a Microsoft 365 subscription.
You have the devices shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 07 Q08 125 You need to onboard the devices to Microsoft Defender Advanced Threat Protection (ATP). The solution must avoid installing software on the devices whenever possible.
Which onboarding method should you use for each operating system? To answer, drag the appropriate methods to the correct operating systems. Each method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 07 Q08 126 Question 
MS-101 Microsoft 365 Mobility and Security Part 07 Q08 126 Answer -
The users at your company use Dropbox Business to store documents. The users access Dropbox Business by using the MyApps portal.
You need to ensure that user access to Dropbox Business is authenticated by using a Microsoft 365 identity. The documents must be protected if the data is downloaded to a device that is not trusted.
What should you do?
- From the Azure Active Directory admin center, configure conditional access settings.
- From the Azure Active Directory admin center, configure the device settings.
- From the Azure Active Directory admin center, configure organizational relationships settings.
- From the Endpoint Manager admin center, configure device enrollment settings.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization.
You need to be notified if the SharePoint sharing policy is modified in the future.
Solution: From the SharePoint admin center, you modify the sharing settings.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You need to prevent users from accessing your Microsoft SharePoint Online sites unless the users are connected to your on-premises network.
Solution: From the Device Management admin center, you create a trusted location and a compliance policy
Does this meet the goal?
- Yes
- No
Explanation:
Conditional Access in SharePoint Online can be configured to use an IP Address white list to allow access. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You need to prevent users from accessing your Microsoft SharePoint Online sites unless the users are connected to your on-premises network.
Solution: From the Microsoft 365 admin center, you configure the Organization profile settings.
Does this meet the goal?
- Yes
- No
Explanation:
Conditional Access in SharePoint Online can be configured to use an IP Address white list to allow access. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You need to prevent users from accessing your Microsoft SharePoint Online sites unless the users are connected to your on-premises network.
Solution: From the Azure Active Directory admin center, you create a trusted location and a conditional access policy.
Does this meet the goal?
- Yes
- No
Explanation:
Conditional Access in SharePoint Online can be configured to use an IP Address white list to allow access. -
HOTSPOT
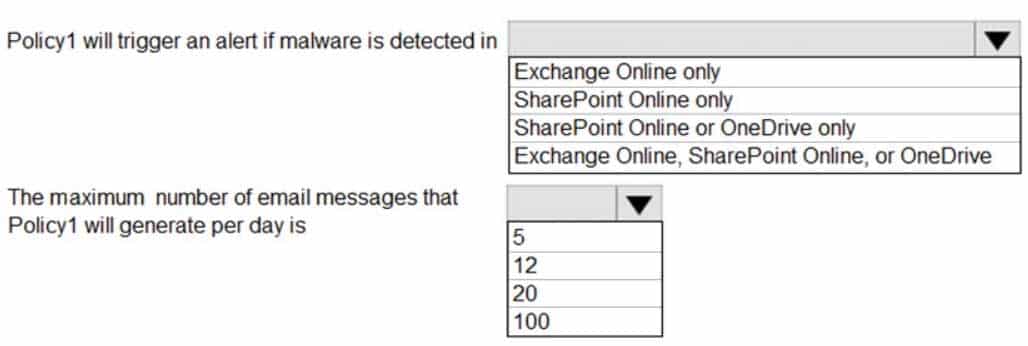
You have Microsoft 365 subscription.
You create an alert policy as shown in the following exhibit.

MS-101 Microsoft 365 Mobility and Security Part 07 Q14 127 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
MS-101 Microsoft 365 Mobility and Security Part 07 Q14 128 Question 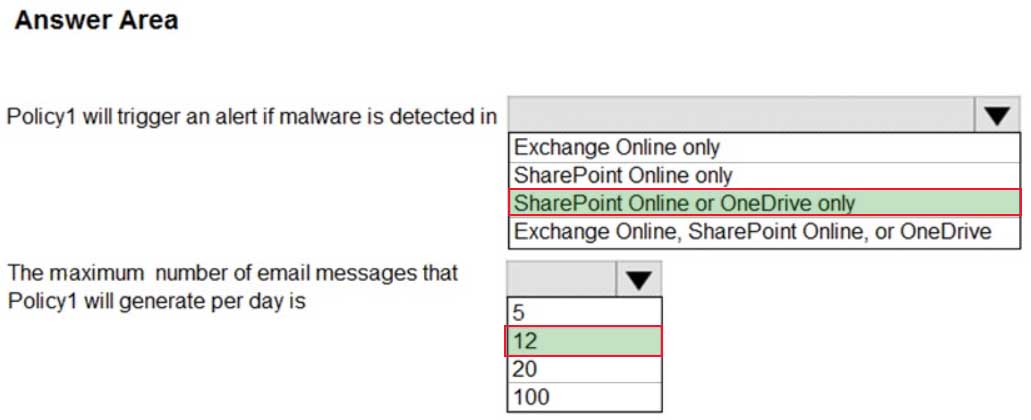
MS-101 Microsoft 365 Mobility and Security Part 07 Q14 128 Answer Explanation:
Note: The Aggregation settings has a 120 minute window -
You have a Microsoft 365 subscription.
All users have their email stored in Microsoft Exchange Online.
In the mailbox of a user named User1, you need to preserve a copy of all the email messages that contain the word ProjectX.
What should you do?
- From the Security & Compliance admin center, create a label and a label policy.
- From the Exchange admin center, create a mail flow rule.
- From the Security & Compliance admin center, start a message trace.
- From Exchange admin center, start a mail flow message trace.
-
HOTSPOT
You have a new Microsoft 365 subscription.
A user named User1 has a mailbox in Microsoft Exchange Online.
You need to log any changes to the mailbox folder permissions of User1.
Which command should you run? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 07 Q16 129 Question 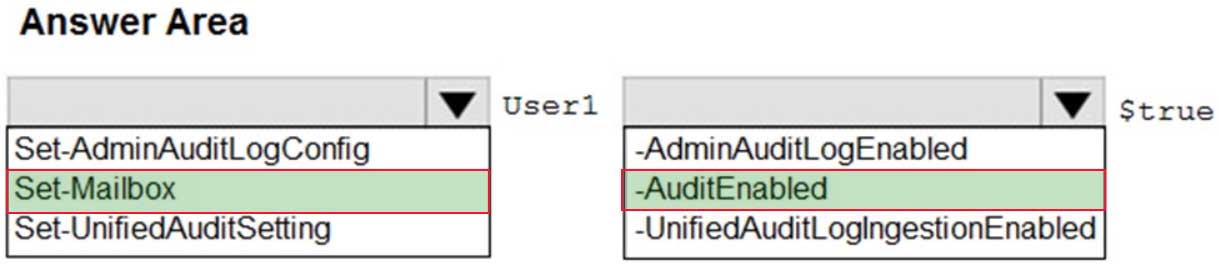
MS-101 Microsoft 365 Mobility and Security Part 07 Q16 129 Answer Explanation:To enable auditing for a single mailbox (in this example, belonging to Holly Sharp), use this PowerShell command: Set-Mailbox username -AuditEnabled $true
-
You have a Microsoft 365 subscription.
You recently configured a Microsoft SharePoint Online tenant in the subscription.
You plan to create an alert policy.
You need to ensure that an alert is generated only when malware is detected in more than five documents stored in SharePoint Online during a period of 10 minutes.
What should you do first?
- Enable Microsoft Office 365 Cloud App Security.
- Deploy Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP)
- Enable Microsoft Office 365 Analytics.
-
DRAG DROP
Your company has a Microsoft 365 E5 tenant.
Users access resources in the tenant by using both personal and company-owned Android devices. Company policies requires that the devices have a threat level of medium or lower to access Microsoft Exchange Online mailboxes.
You need to recommend a solution to identify the threat level of the devices and to control access of the devices to the resources.
What should you include in the solution for each device type? To answer, drag the appropriate components to the correct devices. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
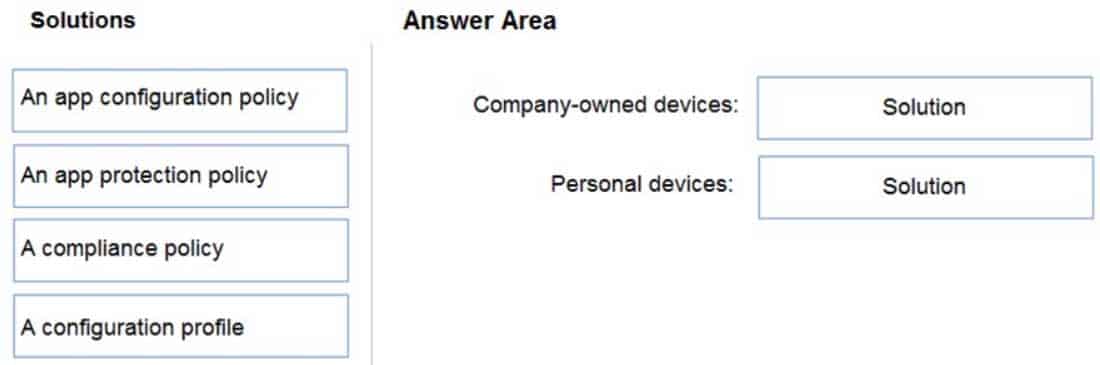
MS-101 Microsoft 365 Mobility and Security Part 07 Q18 130 Question 
MS-101 Microsoft 365 Mobility and Security Part 07 Q18 130 Answer -
HOTSPOT
You have a Microsoft 365 E5 tenant that contains five devices enrolled in Microsoft Intune as shown in the following table.
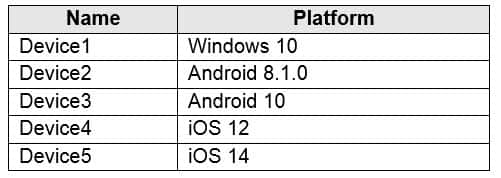
MS-101 Microsoft 365 Mobility and Security Part 07 Q19 131 All the devices have an app named App1 installed.
You need to prevent users from copying data from App1 and pasting the data into other apps.
Which policy should you create in Microsoft Endpoint Manager, and what is the minimum number of required policies? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
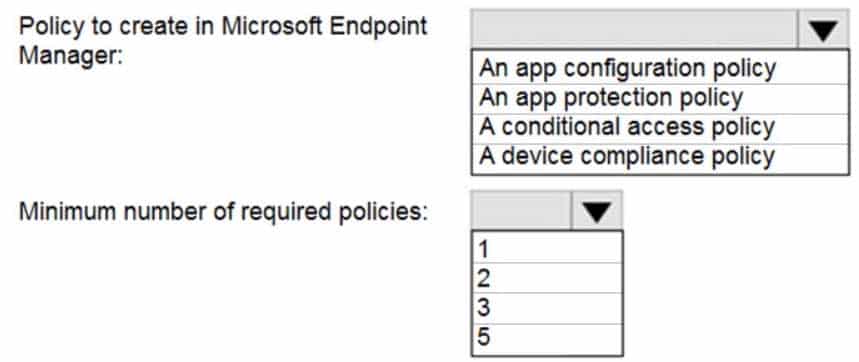
MS-101 Microsoft 365 Mobility and Security Part 07 Q19 132 Question 
MS-101 Microsoft 365 Mobility and Security Part 07 Q19 132 Answer -
You have a Microsoft 365 tenant.
You plan to manage incidents in the tenant by using the Microsoft 365 security center.
Which Microsoft service source will appear on the Incidents page of the Microsoft 365 security center?
- Microsoft Cloud App Security
- Azure Sentinel
- Azure Web Application Firewall
- Azure Defender