MS-101 : Microsoft 365 Mobility and Security : Part 10
MS-101 : Microsoft 365 Mobility and Security : Part 10
-
HOTSPOT
You have a Microsoft 365 subscription.
Your network uses an IP address space of 51.40.15.0/24.
An Exchange Online administrator recently created a role named Role1 from a computer on the network.
You need to identify the name of the administrator by using an audit log search.
For which activities should you search and by which field should you filter in the audit log search? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
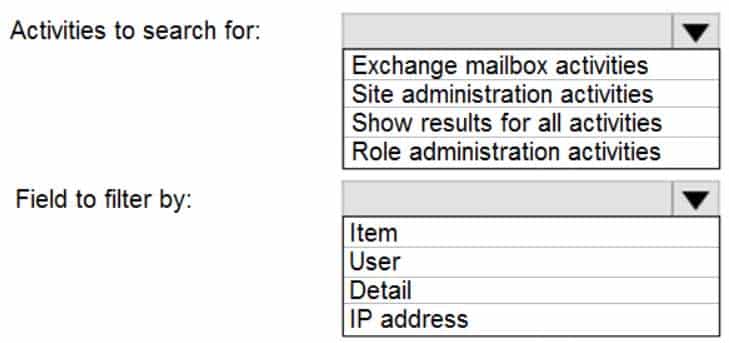
MS-101 Microsoft 365 Mobility and Security Part 10 Q01 168 Question 
MS-101 Microsoft 365 Mobility and Security Part 10 Q01 168 Answer -
You have a Microsoft 365 subscription that uses Security & Compliance retention policies.
You implement a preservation lock on a retention policy that is assigned to all executive users.
Which two actions can you perform on the retention policy? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point?
- Add locations to the policy
- Reduce the duration of policy
- Remove locations from the policy
- Extend the duration of the policy
- Disable the policy
-
You have a Microsoft 365 subscription.
Your company has a customer ID associated to each customer. The customer IDs contain 10 numbers followed by 10 characters. The following is a sample customer ID: 12-456-7890-abc-de-fghij.
You plan to create a data loss prevention (DLP) policy that will detect messages containing customer IDs.
What should you create to ensure that the DLP policy can detect the customer IDs?
- a sensitive information type
- a sensitivity label
- a PowerShell script
- a retention label
-
You have a Microsoft 365 subscription that contains a user named User1.
You need to ensure that User1 can search the Microsoft 365 audit logs from the Security & Compliance admin center.
Which role should you assign to User1?
- View-Only Audit Logs in the Security & Compliance admin center
- View-Only Audit Logs in the Exchange admin center
- Security reader in the Azure Active Directory admin center
- Security Reader in the Security & Compliance admin center
-
From the Security & Compliance admin center, you create a content export as shown in the exhibit. (Click the Exhibit tab.)
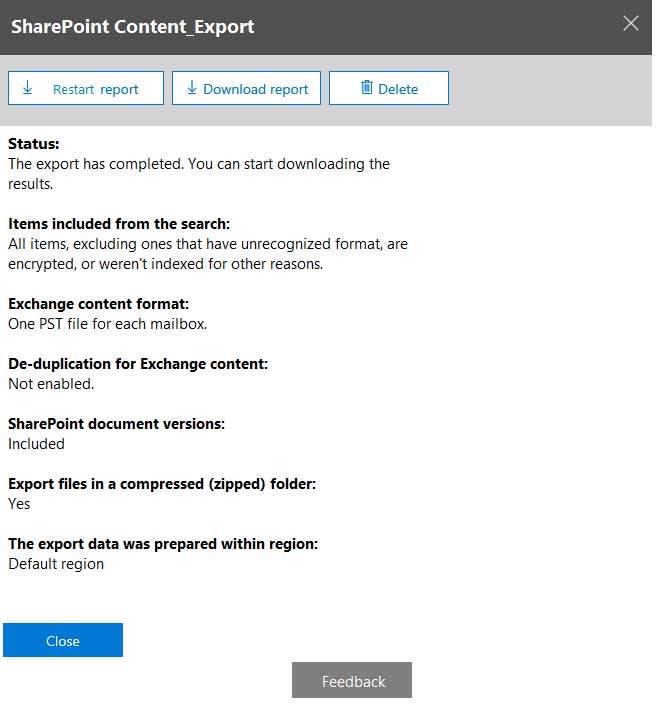
MS-101 Microsoft 365 Mobility and Security Part 10 Q05 169 What will be excluded from the export?
- a 10-MB XLSX file
- a 5-MB MP3 file
- a 5-KB RTF file
- an 80-MB PPTX file
Explanation:Unrecognized file formats are excluded from the search.
Certain types of files, such as Bitmap or MP3 files, don’t contain content that can be indexed. As a result, the search indexing servers in Exchange and SharePoint don’t perform full-text indexing on these types of files. These types of files are considered to be unsupported file types.
-
You are testing a data loss prevention (DLP) policy to protect the sharing of credit card information with external users.
During testing, you discover that a user can share credit card information with external users by using email. However, the user is prevented from sharing files that contain credit card information by using Microsoft SharePoint Online.
You need to prevent the user from sharing the credit card information by using email and SharePoint.
What should you configure?
- the locations of the DLP policy
- the user overrides of the DLP policy rule
- the status of the DLP policy
- the conditions of the DLP policy rule
-
You have a Microsoft 365 subscription.
You need to view the IP address from which a user synced a Microsoft SharePoint Online library.
What should you do?
- From the SharePoint Online admin center, view the usage reports.v
- From the Security & Compliance admin center, perform an audit log search.
- From the Microsoft 365 admin center, view the usage reports.
- From the Microsoft 365 admin center, view the properties of the user’s user account.
-
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains the file servers shown in the following table.
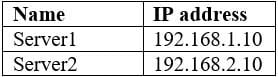
MS-101 Microsoft 365 Mobility and Security Part 10 Q08 170 A file named File1.abc is stored on Server1. A file named File2.abc is stored on Server2. Three apps named App1, App2, and App3 are installed on a Windows 10 device named Device1. All open files have the .abc file extension.
You implement Windows Information Protection (WIP) by creating a policy named Policy1 that uses the following configurations:
– Exempt apps: App2
– Protected apps: App1
– Windows Information Protection mode: Block
– Network boundary: IPv4 range of: 192.168.1.1-192.168.1.255You ensure that Policy1 applies to Device1.
You need to identify the apps from which you can open File1.abc.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 10 Q08 171 Question 
MS-101 Microsoft 365 Mobility and Security Part 10 Q08 171 Answer -
In Microsoft 365, you configure a data loss prevention (DLP) policy named Policy1. Policy1 detects the sharing of United States (US) bank account numbers in email messages and attachments.
Policy1 is configured as shown in the exhibit. (Click the Exhibit tab.)
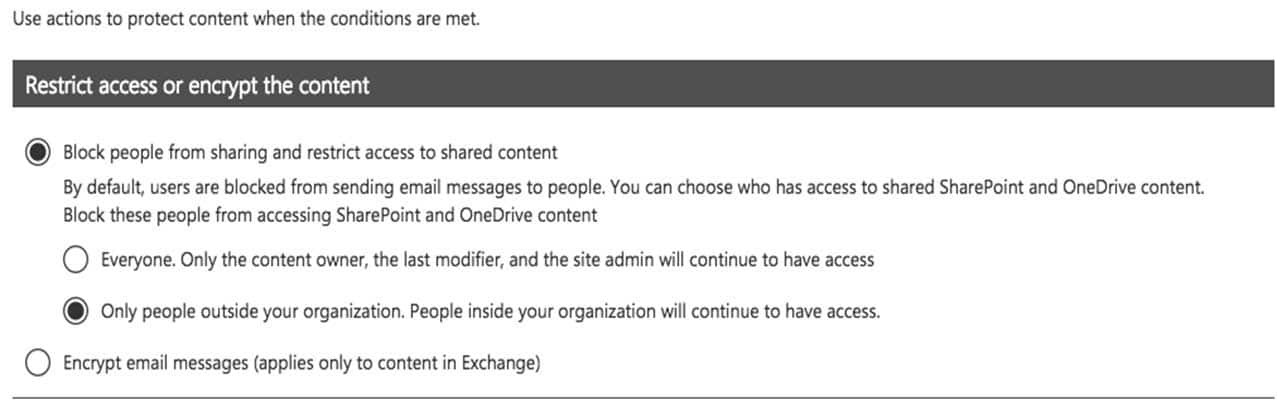
MS-101 Microsoft 365 Mobility and Security Part 10 Q09 172 You need to ensure that internal users can email documents that contain US bank account numbers to external users who have an email suffix of contoso.com.
What should you configure?
- an exception
- an action
- a condition
- a group
Explanation:
You need to add an exception. In the Advanced Settings of the DLP policy, there is an ‘Add Exception’ button. This gives you several options that you can select as the exception. One of the options is ‘except when recipient domain is’. Select that option and enter the domain name: contoso.com. -
HOTSPOT
You have a document in Microsoft OneDrive that is encrypted by using Microsoft Azure Information Protection as shown in the following exhibit.

MS-101 Microsoft 365 Mobility and Security Part 10 Q10 173 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
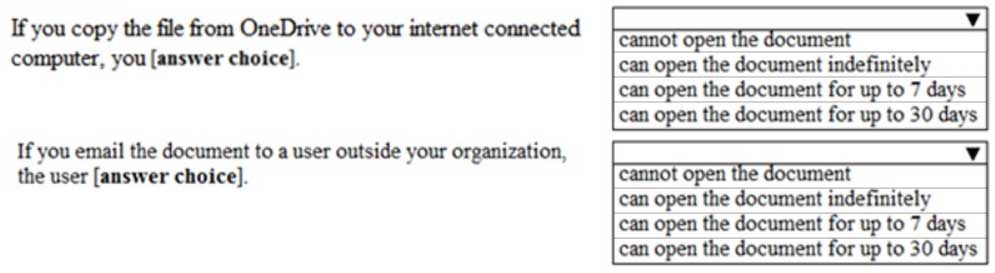
MS-101 Microsoft 365 Mobility and Security Part 10 Q10 174 Question 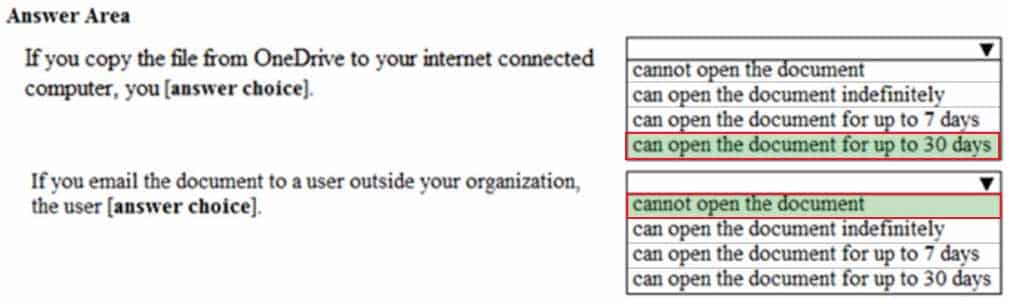
MS-101 Microsoft 365 Mobility and Security Part 10 Q10 174 Answer -
HOTSPOT
You have a Microsoft Office 365 subscription.
You need to delegate eDiscovery tasks as shown in the following table.
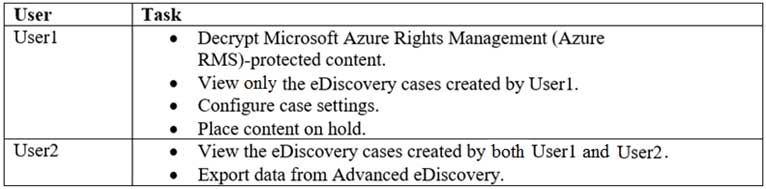
MS-101 Microsoft 365 Mobility and Security Part 10 Q11 175 The solution must follow the principle of the least privilege.
To which role group should you assign each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
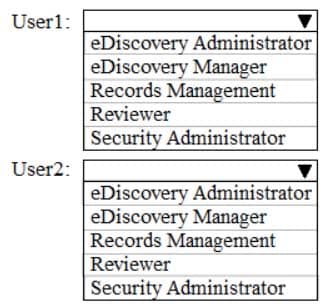
MS-101 Microsoft 365 Mobility and Security Part 10 Q11 176 Question 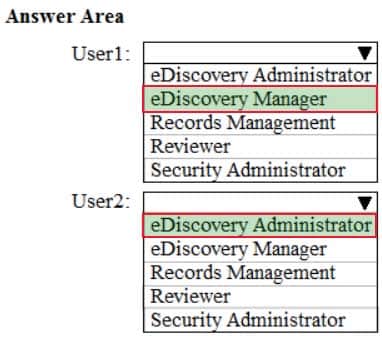
MS-101 Microsoft 365 Mobility and Security Part 10 Q11 176 Answer -
You have a Microsoft 365 subscription.
You need to identify which administrative users performed eDiscovery searches during the past week.
What should you do from the Security & Compliance admin center?
- Perform a content search
- Create a supervision policy
- Create an eDiscovery case
- Perform an audit log search
-
HOTSPOT
You configure a data loss prevention (DLP) policy named DLP1 as shown in the following exhibit.

MS-101 Microsoft 365 Mobility and Security Part 10 Q13 177 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 10 Q13 178 Question 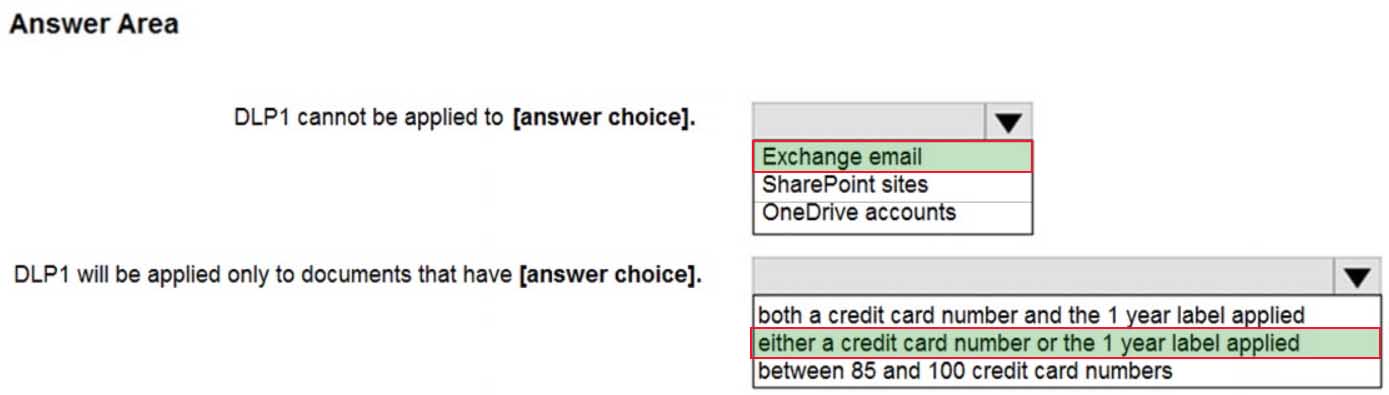
MS-101 Microsoft 365 Mobility and Security Part 10 Q13 178 Answer Explanation:Using a retention label in a policy is only supported for items in SharePoint Online and OneDrive for Business.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
From the Security & Compliance admin center, you create a role group named US eDiscovery Managers by copying the eDiscovery Manager role group.
You need to ensure that the users in the new role group can only perform content searches of mailbox content for users in the United States.
Solution: From Windows PowerShell, you run the New-ComplianceSecurityFilter cmdlet with the appropriate parameters.
Does this meet the goal?
- Yes
- No
-
HOTSPOT
You have a Microsoft 365 subscription that uses a default domain named contoso.com. The domain contains the users shown in the following table.
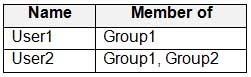
MS-101 Microsoft 365 Mobility and Security Part 10 Q15 179 The domain contains the devices shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 10 Q15 180 The domain contains conditional access policies that control access to a cloud app named App1. The policies are configured as shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 10 Q15 181MS-101 Microsoft 365 Mobility and Security Part 10 Q15 181 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 10 Q15 182 Question 
MS-101 Microsoft 365 Mobility and Security Part 10 Q15 182 Answer Explanation:Note: Block access overrides Grant access
-
You have a Microsoft 365 subscription.
You need to create a data loss prevention (DLP) policy that is configured to use the Set headers action.
To which location can the policy be applied?
- OneDrive accounts
- Exchange email
- Teams chat and channel messages
- SharePoint sites
-
You enable the Azure AD Identity Protection weekly digest email.
You create the users shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 10 Q17 183 Which users will receive the weekly digest email automatically?
- Admin2, Admin3, and Admin4 only
- Admin1, Admin2, Admin3, and Admin4
- Admin2 and Admin3 only
- Admin3 only
- Admin1 and Admin3 only
Explanation:
By default, all Global Admins receive the email. Any newly created Global Admins, Security Readers or Security Administrators will automatically be added to the recipients list. -
HOTSPOT
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
A user named User1 has files on a Windows 10 device as shown in the following table.
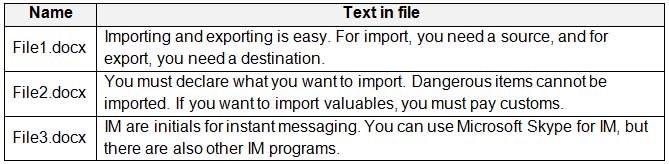
MS-101 Microsoft 365 Mobility and Security Part 10 Q18 184 In Azure Information Protection, you create a label named Label1 that is configured to apply automatically. Label1 is configured as shown in the following exhibit.

MS-101 Microsoft 365 Mobility and Security Part 10 Q18 185 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
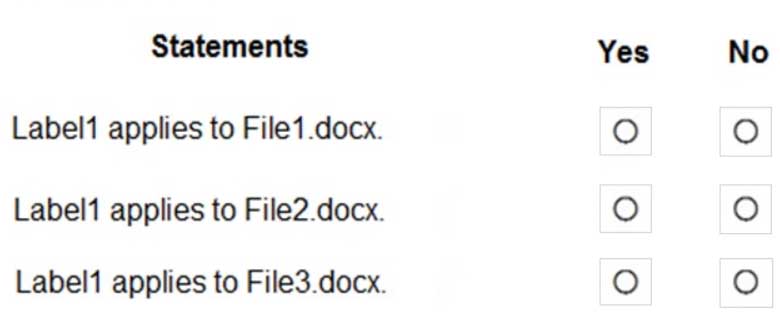
MS-101 Microsoft 365 Mobility and Security Part 10 Q18 186 Question 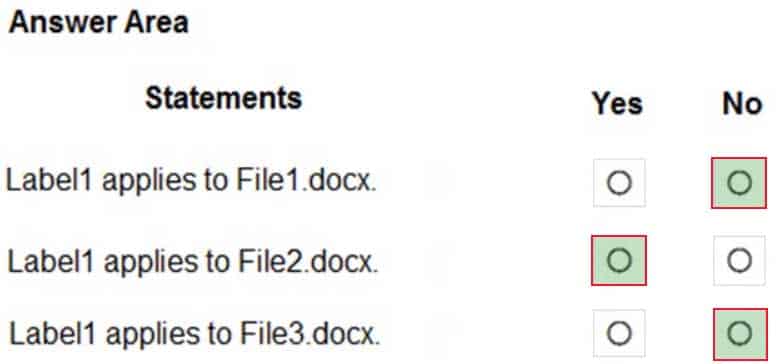
MS-101 Microsoft 365 Mobility and Security Part 10 Q18 186 Answer Explanation:The phrase to match is “im” and it is case sensitive. The phrase must also appear at least twice.
Box 1: No
File1.docx contain the word “import” once onlyBox 2: Yes
File2.docx contains two occurrences of the word “import” as well as the word “imported”Box 3: No
File3.docx contains “IM” but his is not the correct letter case. -
HOTSPOT
You have a Microsoft 365 subscription that uses a default domain named contoso.com.
Three files were created on February 1, 2019, as shown in the following table.

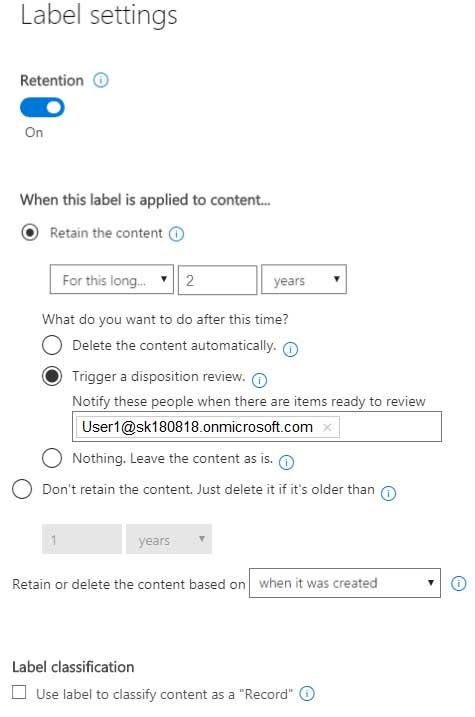
MS-101 Microsoft 365 Mobility and Security Part 10 Q19 187 On March 1, 2019, you create two retention labels named Label1 and Label2.
The settings for Lable1 are configured as shown in the Label1 exhibit. (Click the Label1 tab.)
MS-101 Microsoft 365 Mobility and Security Part 10 Q19 188 The settings for Lable2 are configured as shown in the Label2 exhibit. (Click the Label2 tab.)

MS-101 Microsoft 365 Mobility and Security Part 10 Q19 189 You apply the retention labels to Exchange email, SharePoint sites, and OneDrive accounts.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 10 Q19 190 Question 
MS-101 Microsoft 365 Mobility and Security Part 10 Q19 190 Answer Explanation:Box 1: No
Retention overrides deletion.Box 2: No
Content in a document library will be moved to the first-stage Recycle Bin within 7 days of disposition, and then permanently deleted another 93 days after that. Thus 100 days in total.Box 3: No
Items in an Exchange mailbox will be permanently deleted within 14 days of disposition. -
DRAG DROP
You have a Microsoft 365 subscription.
In the Exchange admin center, you have a data loss prevention (DLP) policy named Policy1 that has the following configurations:
– Block emails that contain financial data.
– Display the following policy tip text: Message blocked.From the Security & Compliance admin center, you create a DLP policy named Policy2 that has the following configurations:
– Use the following location: Exchange email.
– Display the following policy tip text: Message contains sensitive data.
– When a user sends an email, notify the user if the email contains health records.What is the result of the DLP policies when the user sends an email? To answer, drag the appropriate results to the correct scenarios. Each result may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 10 Q20 191 Question 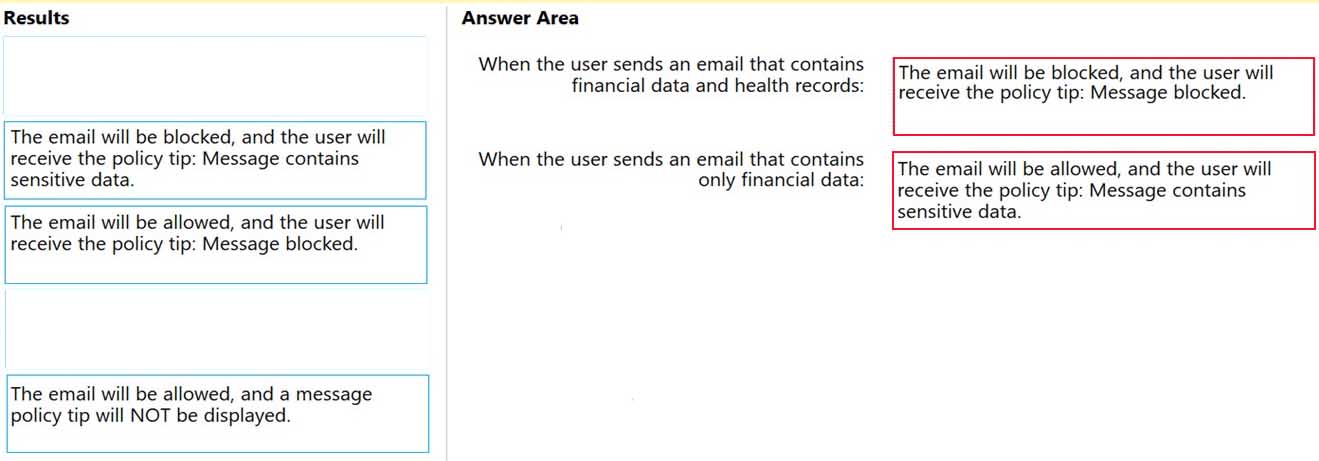
MS-101 Microsoft 365 Mobility and Security Part 10 Q20 191 Answer Explanation:Box 1: The email will be blocked, and the user will receive the policy tip: Message blocked.If you’ve created DLP policies in the Exchange admin center, those policies will continue to work side by side with any policies for email that you create in the Security & Compliance Center. But note that rules created in the Exchange admin center take precedence. All Exchange mail flow rules are processed first, and then the DLP rules from the Security & Compliance Center are processed.Box 2: The email will be allowed, and the user will receive the policy tip: Message contains sensitive data.