MS-101 : Microsoft 365 Mobility and Security : Part 12
MS-101 : Microsoft 365 Mobility and Security : Part 12
-
You have a Microsoft 365 subscription.
You need to grant a user named User1 access to download compliance reports from the Security & Compliance admin center. The solution must use the principle of least privilege.
What should you do?
- Add User1 to the Service Assurance User role group.
- Create a new role group that has the Preview role and add User1 to the role group.
- Add User1 to the Compliance Administrator role group.
- Add User1 to the Security Reader role group.
-
You have a Microsoft 365 subscription.
Some users have iPads that are managed by your company.
You plan to prevent the iPad users from copying corporate data in Microsoft Word and pasting the data into other applications.
What should you create?
- A conditional access policy.
- A compliance policy.
- An app protection policy.
- An app configuration policy.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a new Microsoft 365 subscription.
You need to prevent users from sending email messages that contain Personally Identifiable Information (PII).
Solution: From the Azure portal, you create a Microsoft Azure Information Protection label and an Azure Information Protection policy.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
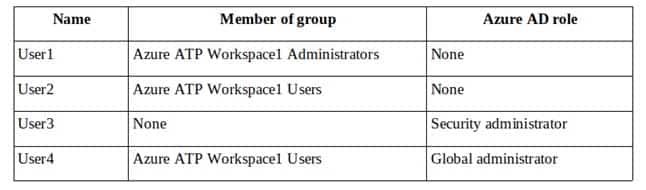
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You create an Azure Advanced Threat Protection (ATP) workspace named Workspace1.
The tenant contains the users shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 12 Q04 212 You need to modify the configuration of the Azure ATP sensors.
Solution: You instruct User1 to modify the Azure ATP sensor configuration.
Does this meet the goal?
- Yes
- No
Explanation:
Only Azure ATP administrators can modify the sensors. -
HOTSPOT
You have a data loss prevention (DLP) policy.
You need to increase the likelihood that the DLP policy will apply to data that contains medical terms from the International Classification of Diseases (ICD-9-CM). The solution must minimize the number of false positives.
Which two settings should you modify? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
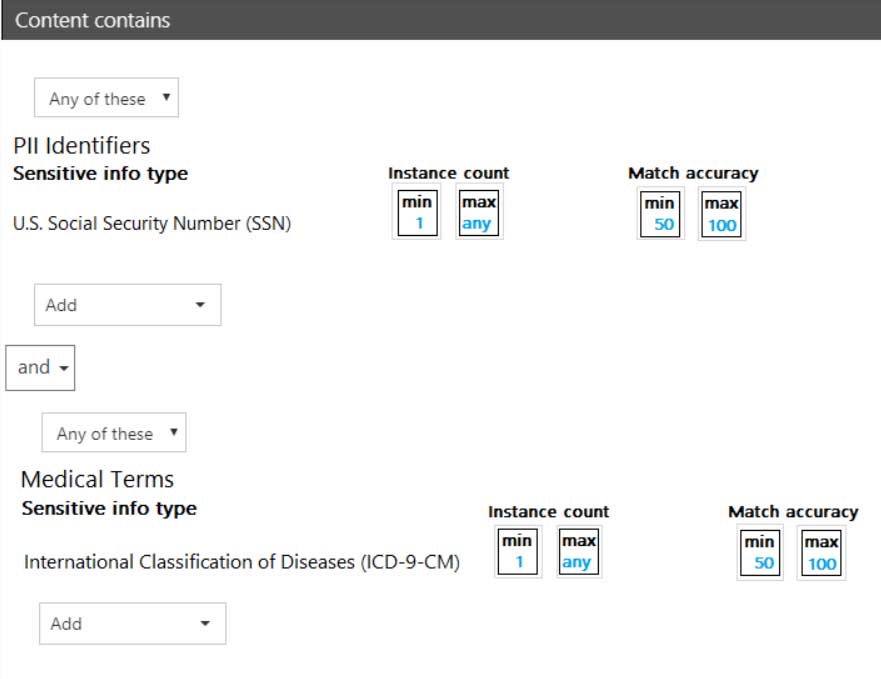
MS-101 Microsoft 365 Mobility and Security Part 12 Q05 213 Question 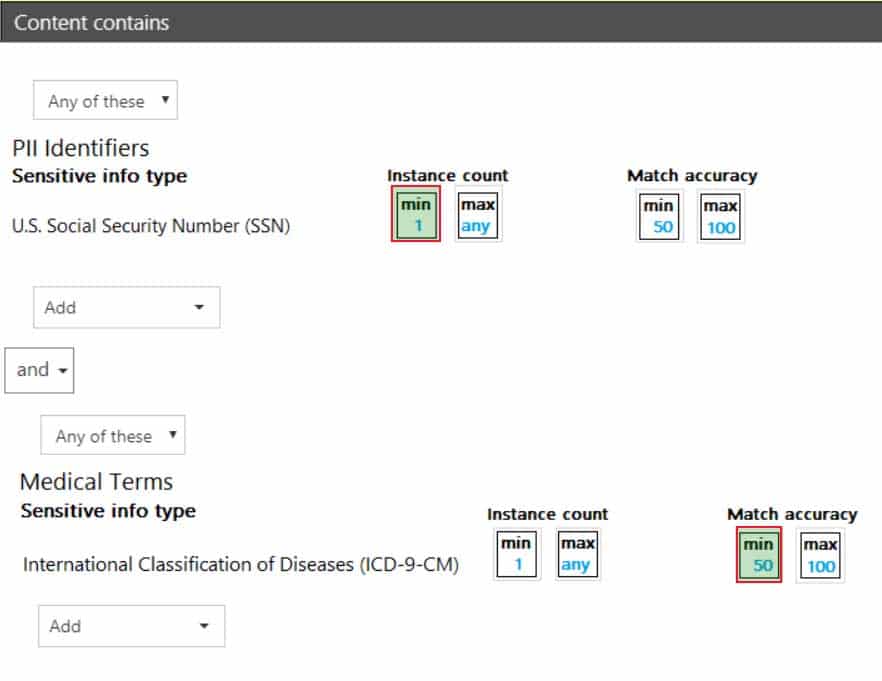
MS-101 Microsoft 365 Mobility and Security Part 12 Q05 213 Answer -
HOTSPOT
From the Security & Compliance admin center, you create a retention policy named Policy1.
You need to prevent all users from disabling the policy or reducing the retention period.
Which command should you run? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 12 Q06 214 Question 
MS-101 Microsoft 365 Mobility and Security Part 12 Q06 214 Answer -
You create a new Microsoft 365 subscription and assign Microsoft 365 E3 licenses to 100 users.
From the Security & Compliance admin center, you enable auditing.
You are planning the auditing strategy.
Which three activities will be audited by default? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- An administrator creates a new Microsoft SharePoint site collection.
- An administrator creates a new mail flow rule.
- A user shares a Microsoft SharePoint folder with an external user.
- A user delegates permissions to their mailbox.
- A user purges messages from their mailbox.
-
HOTSPOT
You have a Microsoft 365 tenant.
You create a retention label as shown in the Retention Label exhibit. (Click the Retention Label tab.)

MS-101 Microsoft 365 Mobility and Security Part 12 Q08 215 You create a label policy as shown in the Label Policy Exhibit. (Click the Label Policy tab.)
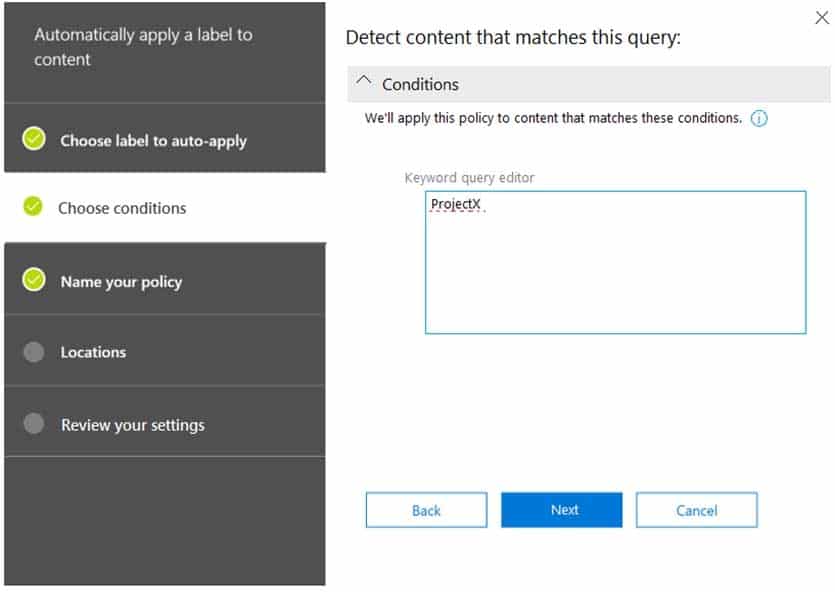
MS-101 Microsoft 365 Mobility and Security Part 12 Q08 216 The label policy is configured as shown in the following table.
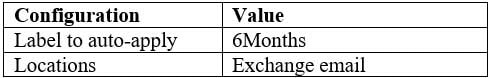
MS-101 Microsoft 365 Mobility and Security Part 12 Q08 217 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
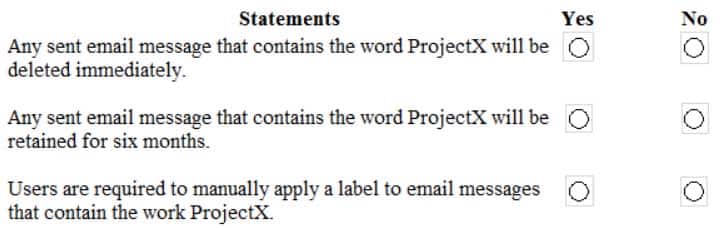
MS-101 Microsoft 365 Mobility and Security Part 12 Q08 218 Question 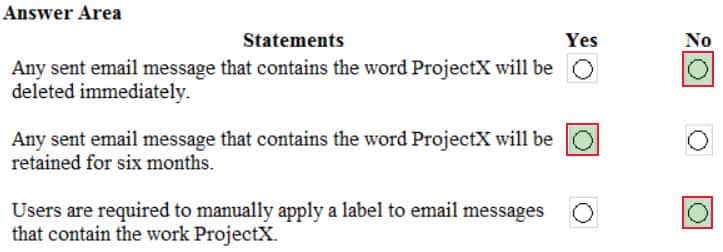
MS-101 Microsoft 365 Mobility and Security Part 12 Q08 218 Answer -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You create an Azure Advanced Threat Protection (ATP) workspace named Workspace1.
The tenant contains the users shown in the following table.
MS-101 Microsoft 365 Mobility and Security Part 12 Q09 219 You need to modify the configuration of the Azure ATP sensors.
Solution: You instruct User2 to modify the Azure ATP sensor configuration.
Does this meet the goal?
- Yes
- No
-
HOTSPOT
You purchase a new Microsoft 365 subscription.
You create 100 users who are assigned Microsoft 365 E3 licenses.
A manager sends you an email message asking the following questions:
– Question1: Who created a team named Team1 14 days ago?
– Question2: Who signed in to the mailbox of User1 30 days ago?
– Question3: Who modified the list of site collection administrators of a site 60 days ago?For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 12 Q10 220 Question 
MS-101 Microsoft 365 Mobility and Security Part 12 Q10 220 Answer -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
From the Security & Compliance admin center, you create a role group named US eDiscovery Managers by copying the eDiscovery Manager role group.
You need to ensure that the users in the new role group can only perform content searches of mailbox content for users in the United States.
Solution: From the Azure Active Directory admin center, you create a conditional access policy.
Does this meet the goal?
- Yes
- No
-
From the Security & Compliance admin center, you create a content export as shown in the exhibit. (Click the Exhibit tab.)
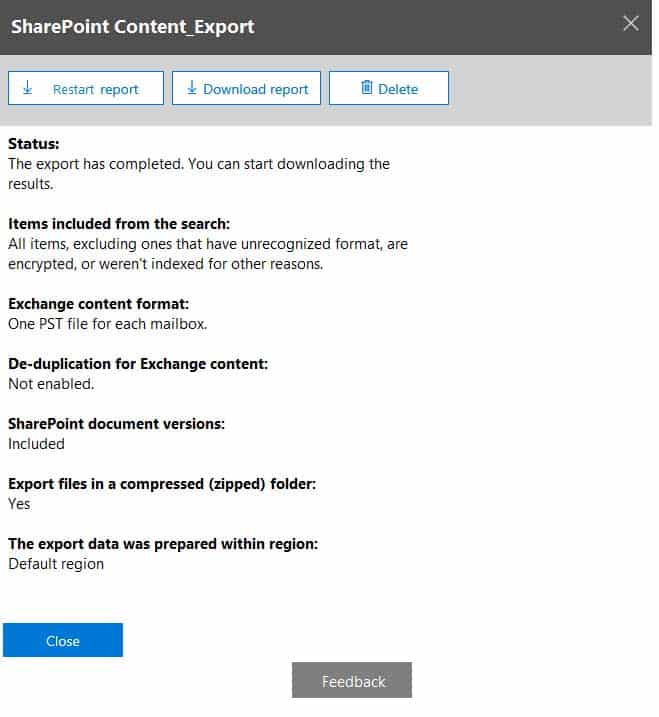
MS-101 Microsoft 365 Mobility and Security Part 12 Q12 221 What will be excluded from the export?
- a 60-MB DOCX file
- a 12-MB BMP file
- a 5-KB RTF file
- an 80-MB PPTX file
Explanation:Unrecognized file formats are excluded from the search.
Certain types of files, such as Bitmap or MP3 files, don’t contain content that can be indexed. As a result, the search indexing servers in Exchange and SharePoint don’t perform full-text indexing on these types of files. These types of files are considered to be unsupported file types.
Incorrect Answers:
A: DOCX is a supported Microsoft PowerPoint file format.
C: RTF is a supported Rich Text File format.
D: PPTX is a supported Microsoft PowerPoint file format. -
You have a Microsoft 365 subscription.
From the Security & Compliance admin center, you create a content search of a mailbox.
You need to view the content of the mail messages found by the search as quickly as possible.
What should you select from the Content search settings?
- Export report
- Export results
- Re-run
- View results
Explanation:
There is no ‘View Results” option. You can preview results but that will only show up to 100 emails. To guarantee you’re getting all results, you’ll need to export them to a PST file. -
HOTSPOT
From the Security & Compliance admin center, you create a retention policy named Policy1.
You need to prevent all users from disabling the policy or reducing the retention period.
How should you configure the Azure PowerShell command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 12 Q14 222 Question 
MS-101 Microsoft 365 Mobility and Security Part 12 Q14 222 Answer -
Your company has a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com.
A user named User1 is a member of a dynamic group named Group1.
User1 reports that he cannot access documents shared to Group1.
You discover that User1 is no longer a member of Group1.
You suspect that an administrator made a change that caused User1 to be removed from Group1.
You need to identify which administrator made the change.
Which audit log activity should you search in the Security & Compliance admin center?
- Azure AD group administration activities – Removed member from group
- User administration activities – Updated user
- Azure AD group administration activities – Updated group
-
You have a Microsoft 365 E5 tenant.
You need to evaluate compliance with European Union privacy regulations for customer data.
What should you do in the Microsoft 365 compliance center?
- Create a Data Subject Request (DSR)
- Create a data loss prevention (DLP) policy for General Data Protection Regulation (GDPR) data
- Create an assessment based on the EU GDPR assessment template
- Create an assessment based on the Data Protection Baseline assessment template
-
You have a Microsoft 365 E5 tenant.
You need to be notified when emails with attachments that contain sensitive personal data are sent to external recipients.
Which two policies can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- a data loss prevention (DLP) policy
- a sensitivity label policy
- a Microsoft Cloud App Security file policy
- a communication compliance policy
- a retention label policy
-
You have a Microsoft 365 E5 tenant.
You create an auto-labeling policy to encrypt emails that contain a sensitive info type. You specify the locations where the policy will be applied.
You need to deploy the policy.
What should you do first?
- Review the sensitive information in Activity explorer
- Turn on the policy
- Run the policy in simulation mode
- Configure Azure Information Protection analytics
-
You have a Microsoft 365 tenant and a LinkedIn company page.
You plan to archive data from the LinkedIn page to Microsoft 365 by using the LinkedIn connector.
Where can you store data from the LinkedIn connector?
- a Microsoft OneDrive for Business folder
- a Microsoft SharePoint Online document library
- a Microsoft 365 mailbox
- Azure Files
-
HOTSPOT
You have a Microsoft 365 E5 tenant that contains 500 Windows 10 devices and a Windows 10 compliance policy.
You deploy a third-party antivirus solution to the devices.
You need to ensure that the devices are marked as compliant.
Which three settings should you modify in the compliance policy? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 12 Q20 223 Question 
MS-101 Microsoft 365 Mobility and Security Part 12 Q20 223 Answer -
HOTSPOT
You have a Microsoft 365 E5 tenant that contains a Microsoft SharePoint Online site named Site1. Site1 contains the files shown in the following table.
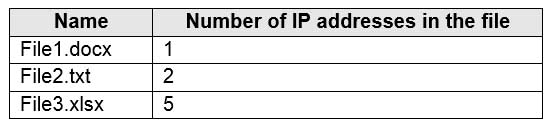
MS-101 Microsoft 365 Mobility and Security Part 12 Q21 224 You create a sensitivity label named Sensitivity1 and an auto-label policy that has the following configurations:
– Name: AutoLabel1
– Label to auto-apply: Sensitivity1
– Rules for SharePoint Online sites: Rule1-SPO
– Choose locations where you want to apply the label: Site1Rule1-SPO is configured as shown in the following exhibit.
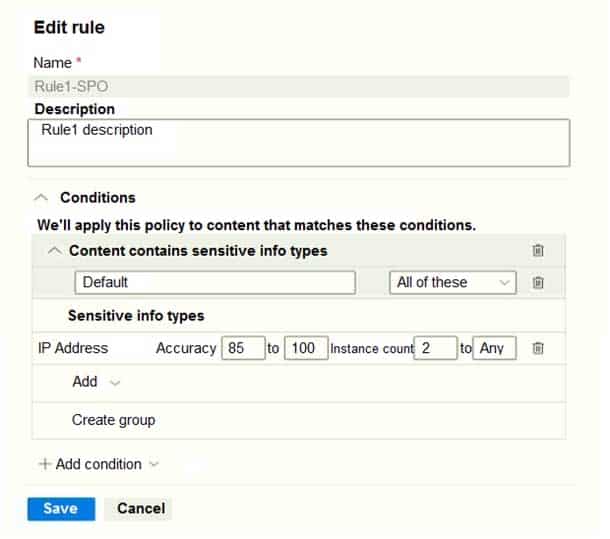
MS-101 Microsoft 365 Mobility and Security Part 12 Q21 225 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
MS-101 Microsoft 365 Mobility and Security Part 12 Q21 226 Question 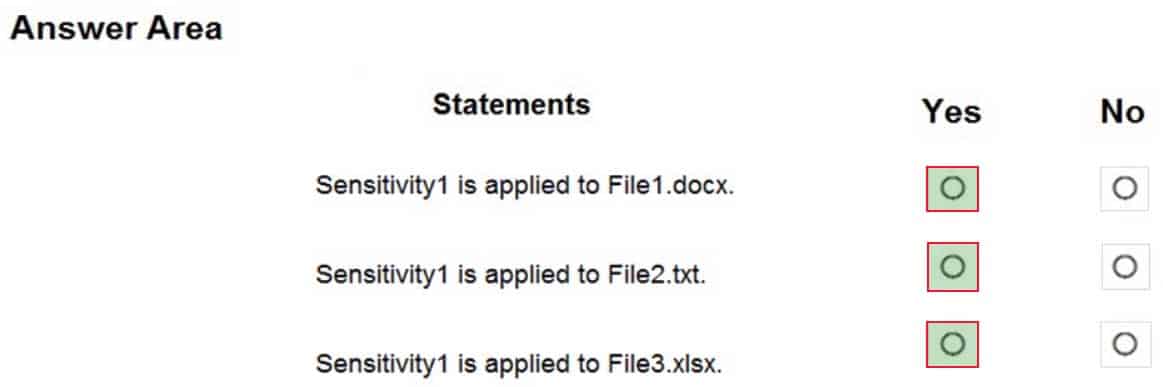
MS-101 Microsoft 365 Mobility and Security Part 12 Q21 226 Answer -
Case Study
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
The company has the employees and devices shown in the following table.

MS-101 Microsoft 365 Mobility and Security Part 12 Q22 227 Contoso recently purchased a Microsoft 365 E5 subscription.
Existing Environment
The network contains an on-premises Active Directory forest named contoso.com. The forest contains the servers shown in the following table.
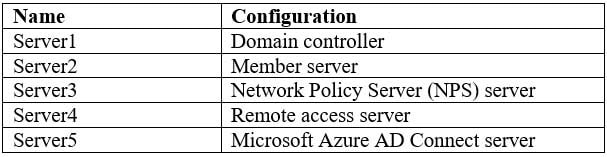
MS-101 Microsoft 365 Mobility and Security Part 12 Q22 228 All servers run Windows Server 2016. All desktops and laptops run Windows 10 Enterprise and are joined to the domain.
The mobile devices of the users in the Montreal and Seattle offices run Android. The mobile devices of the users in the New York office run iOS.
The domain is synced to Azure Active Directory (Azure AD) and includes the users shown in the following table.
The domain also includes a group named Group1.
Requirements
Planned Changes
Contoso plans to implement the following changes:
– Implement Microsoft 365.
– Manage devices by using Endpoint Manager.
– Implement Azure Advanced Threat Protection (ATP).
– Update computers in Seattle and Montreal with the fall Semi-Annual Channel feature update.
– Update computers in the New York office with the spring Semi-Annual Channel feature update.Technical Requirements
Contoso identifies the following technical requirements:
– When a Windows 10 device is joined to Azure AD, the device must enroll to Endpoint Manager automatically.
– Dedicated support technicians must enroll all the Montreal office mobile devices in Endpoint Manager.
– Each dedicated support technician must be assigned only a single Device Enrollment Manager (DEM) account.
– User1 must be able to enroll all the New York office mobile devices in Endpoint Manager.
– Azure ATP sensors must be installed and must NOT use port mirroring.
– Whenever possible, the principle of least privilege must be used.
– A Microsoft Store for Business must be created.Compliance Requirements
Contoso identifies the following compliance requirements:
– Ensure that the users in Group1 can only access Microsoft Exchange Online from devices that are enrolled in Endpoint Manager and configured in accordance with the corporate policy.
– Configure Windows Information Protection (WIP) for the Windows 10 devices.-
You need to meet the compliance requirements for the Windows 10 devices.
What should you create from the Endpoint Management admin center?
- a device compliance policy
- a device configuration profile
- an app protection policy
- an app configuration policy
-
-
Case Study
Overview
ADatum Corporation is an international financial services company that has 5,000 employees.
ADatum has six offices: a main office in New York and five branch offices in Germany, the United Kingdom, France, Spain, and Italy.
All the offices are connected to each other by using a WAN link. Each office connects directly to the Internet.
Existing Environment
Current Infrastructure
ADatum recently purchased a Microsoft 365 subscription.
All user files are migrated to Microsoft 365.
All mailboxes are hosted in Microsoft 365. The users in each office have email suffixes that include the country of the user, for example, user1@us.adatum.com or user2@uk.adatum.com.
Each office has a security information and event management (SIEM) appliance. The appliance comes from three different vendors.
ADatum uses and processes Personally Identifiable Information (PII).
Problem Statements
ADatum entered into litigation. The legal department must place a hold on all the documents of a user named User1 that are in Microsoft 365.
Requirements
Business Goals
ADatum wants to be fully compliant with all the relevant data privacy laws in the regions where is operates.
ADatum wants to minimize the cost of hardware and software whenever possible.
Technical Requirements
ADatum identifies the following technical requirements:
– Centrally perform log analysis for all offices.
– Aggregate all data from the SIEM appliances to a central cloud repository for later analysis.
– Ensure that a SharePoint administrator can identify who accessed a specific file stored in a document library.
– Provide the users in the finance department with access to Service assurance information in Microsoft Office 365.
– Ensure that documents and email messages containing the PII data of European Union (EU) citizens are preserved for 10 years.
– If a user attempts to download 1,000 or more files from Microsoft SharePoint Online within 30 minutes, notify a security administrator and suspend the user’s user account.
– A security administrator requires a report that shown which Microsoft 365 users signed in. Based on the report, the security administrator will create a policy to require multi-factor authentication when a sign-in is high risk.
– Ensure that the users in the New York office can only send email messages that contain sensitive U.S. PII data to other New York office uses. Email messages must be monitored to ensure compliance. Auditors in the New York office must have access to reports that show the sent and received email messages containing sensitive U.S. PII data.-
Which report should the New York office auditors view?
- DLP incidents
- Top Senders and Recipients
- DLP false positives and overrides
- DLP policy matches
-
You need to meet the technical requirement for the EU PII data.
What should you create?
- a data loss prevention (DLP) policy from the Security & Compliance admin center
- a data loss prevention (DLP) policy from the Exchange admin center
- a retention policy from the Exchange admin center
- a retention policy from the Security & Compliance admin center
-
You need to protect the U.S. PII data to meet the technical requirements.
What should you create?
- a data loss prevention (DLP) policy that contains a domain exception
- a Security & Compliance retention policy that detects content containing sensitive data
- a Security & Compliance alert policy that contains an activity
- a data loss prevention (DLP) policy that contains a user override
-
DRAG DROP
You need to meet the requirement for the legal department.
Which three actions should you perform in sequence from the Security & Compliance admin center? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

MS-101 Microsoft 365 Mobility and Security Part 12 Q23 229 Question 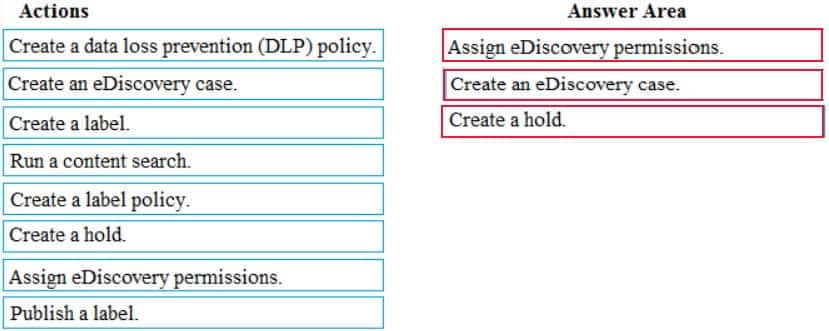
MS-101 Microsoft 365 Mobility and Security Part 12 Q23 229 Answer -
HOTSPOT
You need to meet the technical requirement for log analysis.
What is the minimum number of data sources and log collectors you should create from Microsoft Cloud App Security? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 12 Q23 230 Question 
MS-101 Microsoft 365 Mobility and Security Part 12 Q23 230 Answer -
HOTSPOT
You need to meet the technical requirement for the SharePoint administrator.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-101 Microsoft 365 Mobility and Security Part 12 Q23 231 Question 
MS-101 Microsoft 365 Mobility and Security Part 12 Q23 231 Answer
-