MS-203 : Microsoft 365 Messaging : Part 08
MS-203 : Microsoft 365 Messaging : Part 08
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
Fabrikam, Inc. is a consulting company that has a main office in Montreal.
Fabrikam has a partnership with a company named Litware, Inc.
Existing Environment
Network Environment
The on-premises network of Fabrikam contains an Active Directory domain named fabrikam.com.
Fabrikam has a Microsoft 365 tenant named fabrikam.com. All users have Microsoft 365 Enterprise E5 licenses.
User accounts sync between Active Directory Domain Services (AD DS) and the Microsoft 365 tenant.
Fabrikam.com contains the users and devices shown in the following table.
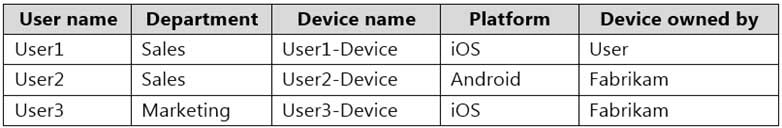
MS-203 Microsoft 365 Messaging Part 08 Q01 104 Fabrikam currently leases mobile devices from several mobile operators.
Microsoft Exchange Online Environment
All users are assigned an Outlook Web App policy named Files Policy.
In-Place Archiving is disabled for Exchange Online.
You have the users shown in the following table.
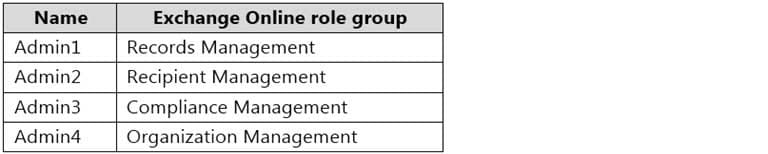
MS-203 Microsoft 365 Messaging Part 08 Q01 105 User1 and User3 use Microsoft Outlook for iOS and Android to access email from their mobile device. User2 uses a native Android email app.
A Safe Links policy in Microsoft Defender for Office 365 is applied to the fabrikam.com tenant.
The marketing department uses a mail-enabled public folder named FabrikamProject.
Default MRM Policy is disabled for the fabrikam.com tenant.
Problem Statements
Fabrikam identifies the following issues:
Users report that they receive phishing emails containing embedded links.
Users download and save ASPX files when they use Outlook on the web.
Email between Fabrikam and Litware is unencrypted during transit.
User2 reports that he lost his mobile device.Requirements
Planned Changes
Fabrikam plans to implement the following changes:
– Configure FilesPolicy to prevent Outlook on the web users from downloading attachments that have the ASPX extension.
– Purchase a new smartboard and configure the smartboard as a booking resource in Exchange Online.
– Ensure that the new smartboard can only be booked for a maximum of one hour.
– Allow only Admin1 to accept or deny booking requests for the new smartboard.
– Standardize mobile device costs by moving to a single mobile device operator.
– Migrate the FabrikamProject public folder to Microsoft SharePoint Online.
– Enable In-Place Archiving for users in the marketing department.
– Encrypt all email between Fabrikam and Litware.Technical Requirements
Fabrikam identifies the following technical requirements:
– Ensure that the planned Sharepoint site for FabrikamProject only contains content that was created during the last 12 months.
– Any existing file types that are currently configured as blocked or allowed in the FilesPolicy policy must remain intact.
– When users leave the company, remove their licenses and ensure that their mailbox is accessible to Admin1 and Admin2.
– Generate a report that identifies mobile devices and the mobile device operator of each device.
– Use the principle of least privilege.
– Minimize administrative effort.Retention Requirements
Fabrikam identifies the following retention requirements for all users:
– Enable users to tag items for deletion after one year.
– Enable users to tag items for deletion after two years.
– Enable users to tag items to be archived after one year.
– Automatically delete items in the Junk Email folder after 30 days.
– Automatically delete items in the Sent Items folder after 300 days.
– Ensure that any items without a retention tag are moved to the Archive mailbox two years after they were created and permanently deleted seven years after they were created.-
You need to identify the contents of the FabrikamProject public folder to meet the technical requirements.
Which PowerShell cmdlet should you run?
- Get-PublicFolderStatistics
- Get-PublicFolderItemStatistics
- Get-PublicFolderMailboxDiagnostics
- Get-PublicFolder
-
-
HOTSPOT
You manage a Microsoft Exchange Online subscription.
You use Advanced Threat Protection (ATP).
A partner company sends daily invoices to your company. The invoices are always named AdatumInvoice.xlsx.
Some users report that sometimes they cannot find the invoices in their Inbox folder.
You need to identify whether the invoices are identified as malicious by Microsoft 365.
Which two blades should you use? To answer, select the appropriate blades in the answer area.
NOTE: Each correct selection is worth one point.

MS-203 Microsoft 365 Messaging Part 08 Q02 106 Question 
MS-203 Microsoft 365 Messaging Part 08 Q02 106 Answer -
You have an Exchange Online tenant.
You need to ensure that the users in your company’s finance department can select email messages that will be deleted automatically one year later. The solution must apply only to the finance department users.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Publish a label to the finance department.
- Create a data loss prevention (DLP) policy that uses the sensitive information type.
- For each mailbox in the finance department, configure the retention policy settings.
- Create a label that has a retention setting of one year.
- For each mailbox in the finance department, configure Message Delivery Restrictions.
Explanation:
Create a retention label and publish it to the finance department users. -
DRAG DROP
You have a Microsoft Exchange Server 2019 organization.
You need to identify which accounts in Active Directory are assigned permissions to dismount mailbox databases.
How should you complete the command? To answer, drag the appropriate values to the correct targets. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

MS-203 Microsoft 365 Messaging Part 08 Q04 107 Question 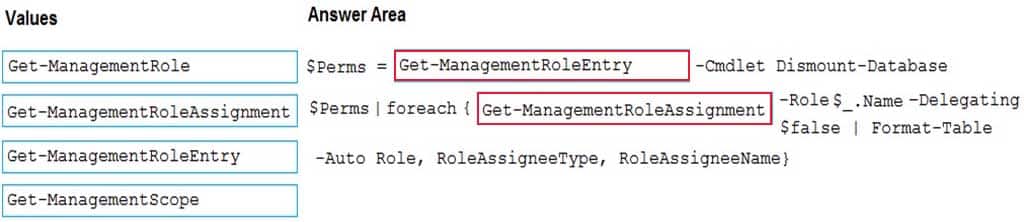
MS-203 Microsoft 365 Messaging Part 08 Q04 107 Answer -
You have a Microsoft 365 subscription.
A safe attachments policy that uses Dynamic Delivery is applied to all recipients who match your SMTP domains.
You need to prevent attachments from being scanned when internal users send email to one another.
What should you do?
- From the Exchange admin center, create a transport rule.
- From the Exchange admin center, modify the malware filter.
- From the Security & Compliance admin center, modify the safe attachments policy.
- From the Security & Compliance admin center, modify the Service assurance settings.
Explanation:
Create a transport rule (or mail flow rule as they are called nowadays) to configure the message header: X-MS-Exchange-Organization-SkipSafeAttachmentProcessing. -
You have a Microsoft 365 E5 subscription.
A user attempts to send an email message to an external recipient and receives the following error message: “Your message couldn’t be delivered because you weren’t recognized as a valid sender. The most common reason for this is that your email address is suspected of sending spam and it’s no longer allowed to send messages outside of your organization. Contact your email admin for assistance. Remove Server returned ‘550 5.1.8 Access denied, bad outbound sender’.”
You need to ensure that the user can send email to external recipients.
What should you use?
- Threat management in the Security & Compliance admin center.
- Data loss prevention in the Security & Compliance admin center.
- compliance management in the Exchange admin center
- action center in the Exchange admin center
-
Your company has a Microsoft Exchange Server 2019 organization.
You are auditing the Litigation Hold on the mailboxes of the company’s research and development department.
You discover that the mailbox of a user named User1 has a Litigation Hold enabled.
You need to discover who placed the Litigation Hold on the mailbox of User1, and when the Litigation Hold was enabled.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- From the Exchange admin center, run a per-mailbox Litigation Hold report.
- From PowerShell, run the Get-Mailbox cmdlet.
- From PowerShell, run the Get-MailboxStatistics cmdlet.
- From the Exchange admin center, run an In-place eDiscovery and Hold report.
-
You have a Microsoft Exchange Server 2019 organization. You create a retention policy.
You need to ensure that all email older than one year is moved to an archive mailbox.
What should you use?
- a personal tag
- a data loss prevention (DLP) policy
- a default policy tag
- a retention policy tag
-
You have a Microsoft Exchange Server 2019 organization.
You need to provide a user named User1 with the ability to create and manage transport rules.
To which management role group should you add User1?
- Server Management
- Compliance Management
- Records Management
- Hygiene Management
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft Exchange Online tenant that contains 1,000 mailboxes.
All the users in the sales department at your company are in a group named Sales.
The company is implementing a new policy to restrict the use of email attachments for the users in the Sales group.
You need to prevent all email messages that contain attachments from being delivered to the users in the Sales group.
Solution: You modify the permissions granted to the Sales group.
Does this meet the goal?
- Yes
- No
Explanation:
Create a mail flow rule -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft Exchange Online tenant that contains 1,000 mailboxes.
All the users in the sales department at your company are in a group named Sales.
The company is implementing a new policy to restrict the use of email attachments for the users in the Sales group.
You need to prevent all email messages that contain attachments from being delivered to the users in the Sales group.
Solution: You configure a mailbox quota.
Does this meet the goal?
- Yes
- No
Explanation:
Create a mail flow rule. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft Exchange Online tenant that contains 1,000 mailboxes.
All the users in the sales department at your company are in a group named Sales.
The company is implementing a new policy to restrict the use of email attachments for the users in the Sales group.
You need to prevent all email messages that contain attachments from being delivered to the users in the Sales group.
Solution: You modify the Exchange Online Protection (EOP) settings.
Does this meet the goal?
- Yes
- No
Explanation:
You can block common attachments (attachments commonly used as malware) in EOP but not all attachments as required in this question. Instead, you should create a mail flow rule. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has an Exchange Online tenant that contains 2,000 mailboxes.
A partner company named Fabrikam, Inc. uses a third-party messaging solution. The outbound SMTP server for Fabrikam uses an IP address of 131.107.2.22.
You discover that several email messages from the fabrikam.com domain are erroneously marked as spam.
You need to ensure that all the email messages sent from the fabrikam.com domain are delivered successfully to the user mailboxes of your company.
Solution: You create a spam filter policy.
Does this meet the goal?
- Yes
- No
Explanation:
Add Fabrikam.com to the ‘Domain allow list’ in a spam filter policy. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has an Exchange Online tenant that contains 2,000 mailboxes.
A partner company named Fabrikam, Inc. uses a third-party messaging solution. The outbound SMTP server for Fabrikam uses an IP address of 131.107.2.22.
You discover that several email messages from the fabrikam.com domain are erroneously marked as spam.
You need to ensure that all the email messages sent from the fabrikam.com domain are delivered successfully to the user mailboxes of your company.
Solution: You create a connection filter.
Does this meet the goal?
- Yes
- No
Explanation:
You can allow the server IP address in the Connection Filter. This would achieve the objective of ensuring all email from Fabrikam.com is delivered. However, it would also allow any other company that uses the third-party email server to bypass the spam filter.
The fact that the question specifies that Fabrikam uses a “third-party messaging solution” suggests that the answer to this question should be No although technically it would work. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has an Exchange Online tenant that contains 2,000 mailboxes.
A partner company named Fabrikam, Inc. uses a third-party messaging solution. The outbound SMTP server for Fabrikam uses an IP address of 131.107.2.22.
You discover that several email messages from the fabrikam.com domain are erroneously marked as spam.
You need to ensure that all the email messages sent from the fabrikam.com domain are delivered successfully to the user mailboxes of your company.
Solution: You create a remote domain.
Does this meet the goal?
- Yes
- No
-
You have a Microsoft Exchange Server 2019 organization.
You plan to migrate all mailboxes to Exchange Online.
You need to provide a user with the ability to perform the mailbox migrations. The solution must use the principle of least privilege.
Which role should you assign to the user?
- Recipient Management
- Server Management
- Help Desk
- Organization Management
-
HOTSPOT
You have a Microsoft Exchange Server 2019 hybrid deployment.
You use Advanced Threat Protection (ATP).
You have safe attachments policies configured as shown in the following table.

MS-203 Microsoft 365 Messaging Part 08 Q17 108 You have the users shown in the following table.
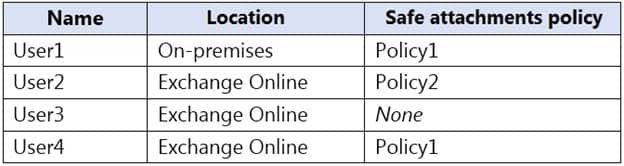
MS-203 Microsoft 365 Messaging Part 08 Q17 109 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-203 Microsoft 365 Messaging Part 08 Q17 110 Question 
MS-203 Microsoft 365 Messaging Part 08 Q17 110 Answer Explanation:Box 1: No
Dynamic Delivery cannot make changes to on-premise mailboxes after the message has been delivered.Box 2: Yes
Policy2 applies to User2. Policy2 has a block action so the message will be placed in quarantine.Box 3: No
User3 does not have a policy assigned so the attachment will be forwarded without being scanned. -
You deploy a Microsoft Exchange Server 2019 organization.
You need to ensure that users of all new mailboxes are prevented from editing their personal information.
What should you do?
- From the Exchange admin center, create a new role assignment policy.
- From PowerShell, run the New-Ro1eAssignmentPolicy cmdlet and specify the
-isDefault parameter. - From the Exchange admin center, create a new role group and assign the role group to Domain Users.
- From PowerShell, run the New-RoleGroup cmdlet and specify the
-CustomRecipientWriteScope parameter.
-
You have a Microsoft Exchange Online tenant.
You discover that a virus has infected the mailboxes of several users. The users are currently spreading the virus by emailing attachments that contain the virus.
You need to temporarily prevent all users from emailing attachments while you remove the virus from all the mailboxes.
What should you configure?
- a connection filter
- a mail flow rule
- a connector
- a spam fitter
-
Your company has a partnership with another company named contoso.com.
You need to ensure that all email messages containing the word sensitive and sent to the users at contoso.com are encrypted automatically.
You enable Azure Information Protection.
What should you do next?
- Create a data loss prevention (DLP) policy.
- Create a mail flow rule.
- Configure a remote domain.
- Configure an Outbound connector.