MS-203 : Microsoft 365 Messaging : Part 10
MS-203 : Microsoft 365 Messaging : Part 10
-
You have a Microsoft Exchange Online tenant that contains a retention policy named Policy1 and a user named User1.
Policy1 is assigned to all users and contains the retention tags shown in the following table.
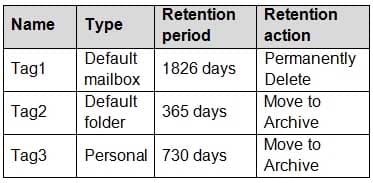
MS-203 Microsoft 365 Messaging Part 10 Q01 127 Tag3 is applied to an email message in the inbox of User1.
You remove Tag3 from Policy1.
What will occur to the message?
- The existing retention tag will be retained.
- The existing retention tag will be removed.
- The default mailbox retention tag will apply.
- The default folder retention tag will apply.
-
You have a Microsoft Exchange Online tenant.
You need to perform an In-Place eDiscovery search. The solution must meet the following requirements:
– Minimize administrative effort.
– Search both public folders and mailboxes.
– Use an In-Place Hold to place the search results on hold.What should you do in the Microsoft 365 compliance center?
- Search the public folders and the mailboxes in a single search, and then place the results on In-Place Hold.
- Search the public folders first, and then place the results on In-Place Hold. Search the mailboxes second, and then place the results on In-Place Hold.
- Search the public folders and the mailboxes in a single search. Once the search completes, place only the mailboxes that contain results and the public folders on In-Place Hold.
-
DRAG DROP
You have a Microsoft 365 subscription.
You need to modify the anti-spam settings to meet the following requirements:
– Quarantine spam for 30 days.
– Notify administrators if users are blocked for sending spam.
– Every three days, provide users with a report that details which email messages were identified as spam.Which spam filter policy should you modify to meet each requirement? To answer, drag the appropriate policies to the correct requirements. Each policy may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

MS-203 Microsoft 365 Messaging Part 10 Q03 128 Question 
MS-203 Microsoft 365 Messaging Part 10 Q03 128 Answer -
You have a Microsoft 365 subscription that uses a default domain named contoso.com.
Users report that email messages from a domain named fabrikam.com are identified as spam even though the messages are legitimate.
You need to prevent messages from fabrikam.com from being identified as spam.
What should you do?
- Enable the Zero-hour auto purge (ZAP) email protection feature.
- Enable the safe list on a connection filter.
- Edit the default mail flow rule to bypass the spam filter.
- Modify the IP Allow list of a connection filter policy.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft Exchange Server 2019 hybrid deployment. All user mailboxes are hosted in Microsoft 365. All outbound SMTP email is routed through the on-premises Exchange organization.
A corporate security policy requires that you must prevent credit card numbers from being sent to internet recipients by using email.
You need to configure the deployment to meet the security policy requirement.
Solution: From Microsoft 365, you create a supervision policy.
Does this meet the goal?
- Yes
- No
Explanation:
You should create a Data Loss Prevention (DLP) policy. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft Exchange Online tenant that contains 1,000 mailboxes.
All the users in the sales department at your company are in a group named Sales.
The company is implementing a new policy to restrict the use of email attachments for the users in the Sales group.
You need to prevent all email messages that contain attachments from being delivered to the users in the Sales group.
Solution: You create a mail flow rule.
Does this meet the goal?
- Yes
- No
-
You have a Microsoft Exchange Server 2019 organization.
You need to ensure that a user named User1 can prevent mailbox content from being deleted if the content contains the words Fabrikam and Confidential.
What should you do?
- Assign the Legal Hold and Mailbox Import Export management roles to User1.
- Assign the Mailbox Search and Mailbox Import Export management roles to User1.
- Add User1 to the Security Administrator role group.
- Assign the Mailbox Search and Legal Hold management roles to User1.
Explanation:
The Legal Hold management role is required to place a mailbox on Litigation Hold or In-Place Hold. But to create a query-based In-Place Hold, you must also be assigned the Mailbox Search role. Users that have been added to the Discovery Management role-based access control (RBAC) role group (or assigned the Legal Hold and Mailbox Search roles) can place users hold and create a query-based In-Place Hold. -
HOTSPOT
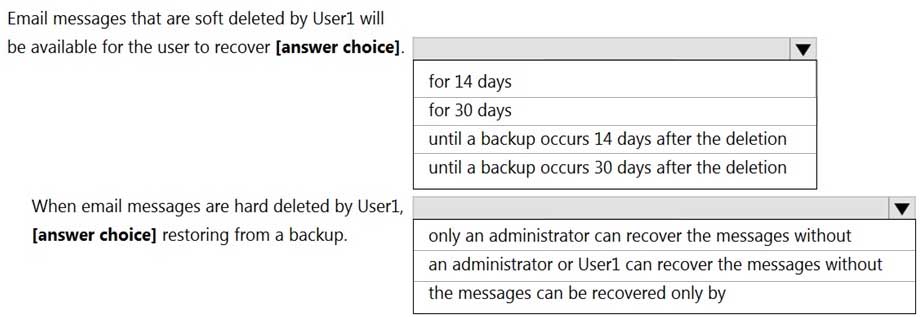
You have a Microsoft Exchange Server 2019 organization.
The recovery options for a user named User1 are configured as shown in the following exhibit.

MS-203 Microsoft 365 Messaging Part 10 Q08 129 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
MS-203 Microsoft 365 Messaging Part 10 Q08 130 Question 
MS-203 Microsoft 365 Messaging Part 10 Q08 130 Answer -
HOTSPOT
Your company has a Microsoft 365 subscription.
All users are assigned Microsoft 365 E5 licenses.
The users receive email messages that appear to come from managers at the company. However, the messages are not from the managers and often include links to malicious websites.
You need to provide a solution to protect the mailboxes of the managers and to inform the users when phishing occurs.
Which two settings should you modify in the anti-phishing policy? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.

MS-203 Microsoft 365 Messaging Part 10 Q09 131 Question 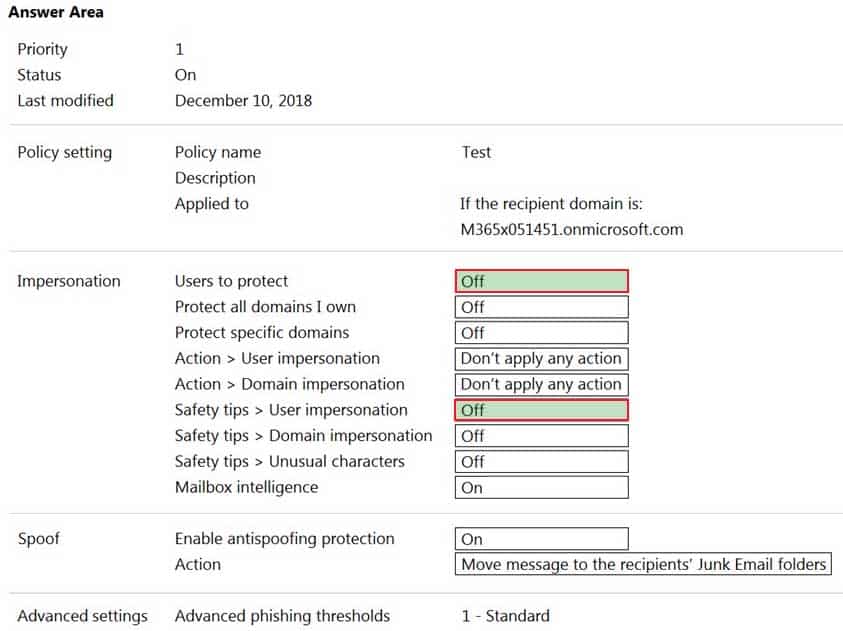
MS-203 Microsoft 365 Messaging Part 10 Q09 131 Answer -
You have a Microsoft Exchange Online tenant and the devices shown in the following table.
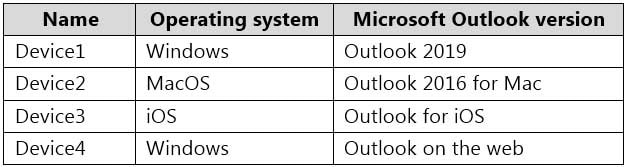
MS-203 Microsoft 365 Messaging Part 10 Q10 132 You plan to implement sensitivity labels for users to apply to email messages.
Which Microsoft Outlook versions will support sensitivity labels without requiring additional software?
- Outlook 2019 and Outlook on the web only
- Outlook on the web only
- Outlook 2019, Outlook 2016 for Mac, Outlook for iOS, and Outlook on the web
- Outlook for iOS and Outlook on the web only
- Outlook 2019 only
-
HOTSPOT
You have a Microsoft Exchange Online tenant.
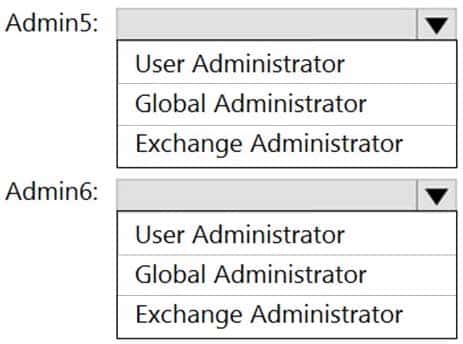
You recently hired two new administrators named Admin5 and Admin6.
You need to grant the following permissions to the new administrators:
– Admin5 must be able to assign licenses to users.
– Admin6 must be able to modify the email SPAM settings of all users.
– Admin5 must be able to configure the email forwarding settings of all users.
– Admin5 and Admin6 must be able to manage the mailbox permissions of all users.The solution must use the principle of least privilege.
Which role should you assign to each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MS-203 Microsoft 365 Messaging Part 10 Q11 133 Question 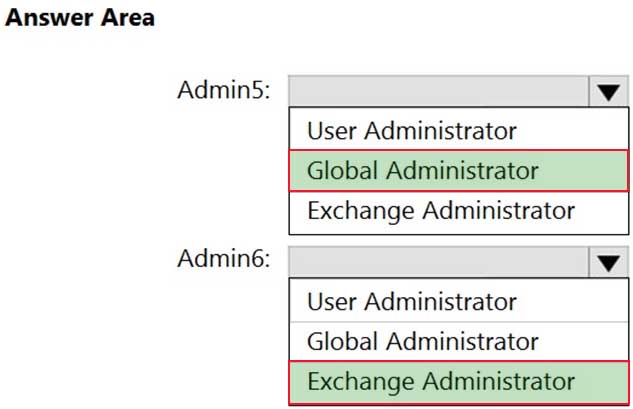
MS-203 Microsoft 365 Messaging Part 10 Q11 133 Answer -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has a Microsoft 365 subscription.
Several users in the finance department of the company recently accessed unsafe websites by clicking on links in email messages.
Users in the marketing department of the company report that they must be able to access all the links embedded in email messages.
You need to reduce the likelihood of the finance department users accessing unsafe websites. The solution must affect only the finance department users.
Solution: You modify the Global settings Safe Links policy.
Does this meet the goal?
- Yes
- No
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
General Overview
Contoso, Ltd. is a national freight company in the United States. The company has 15,000 employees.
Physical Locations
Contoso has a main office in Houston and 10 branch offices that each contain 1,000 employees.
Existing Environment
Active Directory and Microsoft Exchange Server Environments
The network contains an Active Directory forest named contoso.com. The forest contains one root domain named contoso.com and 10 child domains. All domain controllers run Windows Server 2019.
The forest has Active Directory Certificate Services (AD CS) and Active Directory Federation Services (AD FS) deployed.
You have a hybrid deployment of Exchange Server 2019 and Microsoft 365.
There are 2,000 user mailboxes in Exchange Online.
Each office contains two domain controllers and two Mailbox servers. The main office also contains an Edge Transport server.
The organization contains 100 public folders. The folders contain 80 GB of content.
All email messages sent to contoso.com are delivered to Exchange Online. All messages sent to on-premises mailboxes are routed through the Edge Transport server.
Microsoft Defender for Office 365 is enabled and configured for the Microsoft 365 tenant.
Network Infrastructure
Each office connects directly to the Internet by using a local connection. The offices connect to each other by using a WAN link.
Requirements
Planned Changes
Contoso plans to implement the following changes:
– For all new users in the on-premises organization, provide an email address that uses the value of the Last Name attribute and the first two letters of the First Name attribute as a prefix.
– Decommission the public folders and replace the folders with a Microsoft 365 solution that maintains web access to the content.Technical Requirements
Contoso identifies the following technical requirements:
– All email messages sent from an SMTP domain named adatum.com must never be identified as spam.
– Any solution to replace the public folders must include the ability to collaborate with shared calendars.Security Requirements
Contoso identifies the following security requirements:
– The principle of least privilege must be applied to all users and permissions.
– All email messages sent from an SMTP domain named fabrikam.com to contoso.com must be encrypted.
– All users must be protected from accessing unsecure websites when they click on URLs embedded in email messages.
– If a user attempts to send an email message to a distribution group that contains more than 15 members by using Outlook, the user must receive a warning before sending the message.Problem Statements
Recently, a user named HelpdeskUser1 erroneously created several mailboxes. HelpdeskUser1 is a member of the Recipient Management management role group.
Users who have a mailbox in Exchange Online report that it takes a long time for email messages containing attachments to be delivered.
Exhibit
Exchange Online Connector
You configure a connector as shown in the following exhibit.
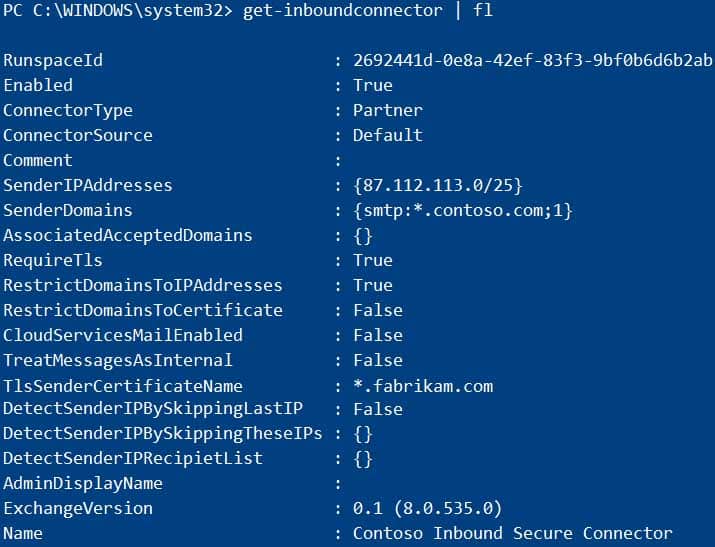
MS-203 Microsoft 365 Messaging Part 10 Q13 134 -
You need to resolve the email delivery delay issue.
What should you do?
- From the Security & Compliance admin center, modify the safe attachments policy.
- From the Exchange admin center in Exchange Online, modify the antimalware policy.
- From the Exchange admin center in Exchange Online, modify the spam filter policy.
- From the Security & Compliance admin center, create a supervision policy.
-
You need to recommend an Office 365 solution that meets the technical requirements for email from adatum.com.
Which two components should you recommend configuring from the Exchange admin center in Exchange Online? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- a malware filter
- a connection filter
- data loss prevention (DLP) policies
- DKIM signatures
- a spam filter
-
You must preview HelpDeskUser1 from repeating the same mistake.
You need to identify which management role provided HelpDeskUser1 with the necessary permissions to make the mistake identified in the problem statement.
Which two cmdlets should you run? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Get-ManagementRoleEntry
- Get-RoleGroupMember
- Get-ManagementRole
- Get-MangementRoleAssignment
- Get-RoleGroup
-
You need to recommend a solution that meets the security requirements for protecting users.
What should you recommend?
- From the Security & Compliance admin center, create an ATP safe attachments policy.
- From the Security & Compliance admin center, create an ATP Safe Links policy.
- From the Security & Compliance admin center, create an ATP anti-phishing policy.
- From the Exchange admin center in Exchange Online, create a spam filter policy.
Explanation:
– All users must be protected from accessing unsecure websites when they click on URLs embedded in email messages. -
You need to configure the Exchange organization to meet the security requirements for sending email messages to distribution groups.
Which cmdlet should you run?
- Set-Mailbox
- Set-DistributionGroup
- New-PolicyTipConfig
- Set-OrganizationConfig
-
You must prevent HelpDeskUser1 from repeating the same mistake.
You need to identify which management role provided HelpDeskUser1 with the necessary permissions to make the mistake identified in the problem statement.
Which two cmdlets should you run? Each correct answer presents part of the solution.
- Get-ManagementRoleAssignment
- Get-ManagementRoleEntry
- Get-ManagementRole
- Get-RoleGroup
- Get-RoleGroupMember
-
HOTSPOT
You need to configure the environment to support the planned changes for email addresses.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-203 Microsoft 365 Messaging Part 10 Q13 135 Question 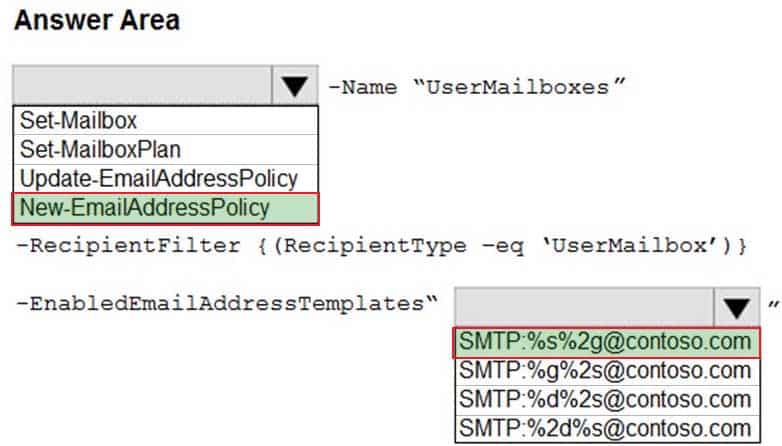
MS-203 Microsoft 365 Messaging Part 10 Q13 135 Answer
-
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
General Overview
Litware, Inc. is a food service supplier in Europe.
Physical Locations
Litware has a main office in Paris and branch offices in Munich, London, Brussels, Vienna, and Rome.
Each branch office has its own compliance officer.
Existing Environment
Active Directory Environment
The network contains one Active Directory forest named litware.com. The forest contains a single Active Directory domain. Each office is configured as an Active Directory site.
Each branch office is represented as a separate organizational unit (OU) in an OU named Offices in Active Directory.
Each branch office has a special Administrators group that contains the delegated administrators for that office. Each Administrators group is named based on its location in a format of RegionalAdmins_Brussels, RegionalAdmins_Munich, RegionalAdmins_London, RegionalAdmins_Vienna and RegionalAdmins_Rome.
Network Infrastructure
Each office contains two domain controllers from the litware.com domain. All the domain controllers are configured as DNS servers. All client computers connect only to the DNS servers in their respective office.
All offices have a high-speed connection to the Internet. Each office connects to the Internet by using a VPN appliance.
Each office has the following servers and client computers:
– One reverse proxy appliance
– One Microsoft Exchange Server 2019 server
– One Windows Server Update Services (WSUS) server
– Computers that run Windows 10 and have Microsoft Office 2019 installedThe office in Brussels contains an Exchange Server 2016 server that has the Unified Messaging role installed and hosted voicemail configured.
Mailboxes are hosted on all the Exchange servers. Public folders are hosted only on an Exchange server in the main office. Litware uses a disjointed namespace to access the servers.
Each user has an archive mailbox. Archiving is configured to use the default settings.
Exchange services are published to the Internet by using a reverse proxy in each office.
A full backup of Exchange is performed nightly. Incremental backups occur every six hours.
All the users in the transport department connect to network resources by using a connection in the main office.
Requirements
Planned Changes
Litware plans to implement the following changes:
– Implement calendar sharing to partner companies.
– Implement a solution that prevents malware from being delivered to end users.
– Use personal archives to eliminate the need for PST files.
– Ensure that the branch office administrators can configure the properties of the mailboxes in their respective offices only.
– Close the Brussels office and move all the users in the Brussels office to the main office. All the mailboxes in the Brussels office will be moved to a server in the main office.
– Implement a compliance solution to ensure that items deleted from public folders are retained. If an item in a public folder is modified, the original version of the item must be available.Technical Requirements
Litware identifies the following technical requirements:
– Minimize administrative effort.
– Use the principle of least privilege.
– Ensure that junk email is deleted automatically after 14 days.
– Ensure that sent items and deleted items are deleted automatically after 30 days.
– Ensure that users in the customer service department can open multiple mailboxes.
– Ensure that all the former Brussels office users always maintain access to hosted voicemail.
– Ensure that the staff in the IT department can manage the email environment without end-user involvement.
– Ensure that users cannot recover email messages that are deleted from the Junk Email folder and the Deleted Items.
– Ensure that if an email message has a spam confidence level (SCL) of 3 or higher, the message automatically moves to the Junk Email folder.Problem Statements
The transport department users report that accessing a public folder named Transport PF is sometimes very slow.
Users in the customer service department report that Microsoft Outlook sometimes hangs when many mailboxes are open.
-
You need to configure the required objects for the branch office administrators.
What should you create for each administrator?
- a management role assignment policy and a management role group
- a management role and a management role assignment policy
- a management role scope and a management role assignment
- a management role scope and a management role group
-
HOTSPOT
You need to implement a solution that meets the technical requirements for the retention of junk email, sent items, and deleted items.
What is the minimum number of retention policies and retention tags you should use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-203 Microsoft 365 Messaging Part 10 Q14 136 Question 
MS-203 Microsoft 365 Messaging Part 10 Q14 136 Answer Explanation:Box 1: 3
A Retention Policy Tag (RPT) is a type of retention tag that you can apply to default folders in a mailbox, such as Inbox and Deleted Items.
We need three retention policy tags, one for Junk, one for Deleted Items and one for Sent items.Box 2: 3
You can only add one RPT for a particular default folder to a Retention Policy. For example, if a retention policy has an Inbox tag, you can’t add another RPT of type Inbox to that retention policy. Therefore, we need three retention policies, each containing one RPT. -
You need to implement a solution to support the planned changes for the branch office administrators.
What should you do?
- Assign the Mail Recipients role to the branch office administrators and use a default management scope.
- Assign the Mail Recipients role to the branch office administrators and create a custom management scope.
- Assign the Recipient Policies role to the branch office administrators and use a default management scope.
- Assign the Recipient Policies role to the branch office administrators and create a custom management scope.
Explanation:
Ensure that the branch office administrators can configure the properties of the mailboxes in their respective offices only. -
HOTSPOT
You need to implement a solution to meet the technical requirements for the SCL.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MS-203 Microsoft 365 Messaging Part 10 Q14 137 Question 
MS-203 Microsoft 365 Messaging Part 10 Q14 137 Answer
-
-
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
Fabrikam, Inc. is a consulting company that has a main office in Montreal.
Fabrikam has a partnership with a company named Litware, Inc.
Existing Environment
Network Environment
The on-premises network of Fabrikam contains an Active Directory domain named fabrikam.com.
Fabrikam has a Microsoft 365 tenant named fabrikam.com. All users have Microsoft 365 Enterprise E5 licenses.
User accounts sync between Active Directory Domain Services (AD DS) and the Microsoft 365 tenant.
Fabrikam.com contains the users and devices shown in the following table.
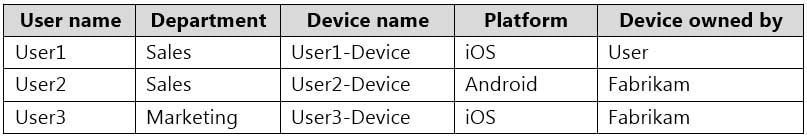
MS-203 Microsoft 365 Messaging Part 10 Q15 138 Fabrikam currently leases mobile devices from several mobile operators.
Microsoft Exchange Online Environment
All users are assigned an Outlook Web App policy named FilesPolicy.
In-Place Archiving is disabled for Exchange Online.
You have the users shown in the following table.

MS-203 Microsoft 365 Messaging Part 10 Q15 139 User1 and User3 use Microsoft Outlook for iOS and Android to access email from their mobile device. User2 uses a native Android email app.
A Safe Links policy in Microsoft Defender for Office 365 is applied to the fabrikam.com tenant.
The marketing department uses a mail-enabled public folder named FabrikamProject.
Default MRM Policy is disabled for the fabrikam.com tenant.
Problem Statements
Fabrikam identifies the following issues:
– Users report that they receive phishing emails containing embedded links.
– Users download and save ASPX files when they use Outlook on the web.
– Email between Fabrikam and Litware is unencrypted during transit.
– User2 reports that he lost his mobile device.Requirements
Planned Changes
Fabrikam plans to implement the following changes:
– Configure FilesPolicy to prevent Outlook on the web users from downloading attachments that have the ASPX extension.
– Purchase a new smartboard and configure the smartboard as a booking resource in Exchange Online.
– Ensure that the new smartboard can only be booked for a maximum of one hour.
– Allow only Admin1 to accept or deny booking requests for the new smartboard.
– Standardize mobile device costs by moving to a single mobile device operator.
– Migrate the FabrikamProject public folder to Microsoft SharePoint Online.
– Enable In-Place Archiving for users in the marketing department.
– Encrypt all email between Fabrikam and Litware.Technical Requirements
Fabrikam identifies the following technical requirements:
– Ensure that the planned Sharepoint site for FabrikamProject only contains content that was created during the last 12 months.
– Any existing file types that are currently configured as blocked or allowed in the FilesPolicy policy must remain intact.
– When users leave the company, remove their licenses and ensure that their mailbox is accessible to Admin1 and Admin2.
– Generate a report that identifies mobile devices and the mobile device operator of each device.
– Use the principle of least privilege.
– Minimize administrative effort.Retention Requirements
Fabrikam identifies the following retention requirements for all users:
– Enable users to tag items for deletion after one year.
– Enable users to tag items for deletion after two years.
– Enable users to tag items to be archived after one year.
– Automatically delete items in the Junk Email folder after 30 days.
– Automatically delete items in the Sent Items folder after 300 days.
– Ensure that any items without a retention tag are moved to the Archive mailbox two years after they were created and permanently deleted seven years after they were created.-
You need to identify which users clicked the links in the phishing emails.
What should you do?
- Run a message trace and review the results.
- Query the mailbox audit log.
- Use the URL trace reporting feature.
- Review the quarantine mailbox.
-