MS-500 : Microsoft 365 Security Administration : Part 03
MS-500 : Microsoft 365 Security Administration : Part 03
-
HOTSPOT
You have a Microsoft 365 E5 subscription that uses Microsoft Endpoint Manager.
The Compliance policy settings are configured as shown in the following exhibit.

MS-500 Microsoft 365 Security Administration Part 03 Q01 048 On February 25, 2020, you create the device compliance policies shown in the following table.
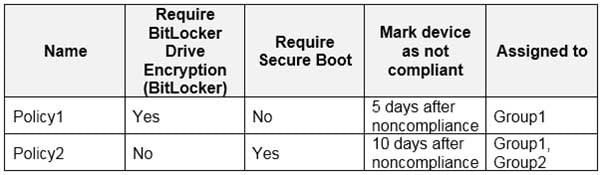
MS-500 Microsoft 365 Security Administration Part 03 Q01 049 On March 1. 2020, users enroll Windows 10 devices in Microsoft Endpoint Manager as shown in the following table
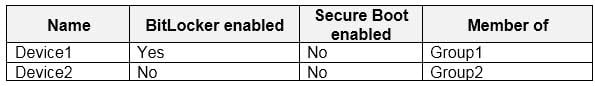
MS-500 Microsoft 365 Security Administration Part 03 Q01 050 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-500 Microsoft 365 Security Administration Part 03 Q01 051 Question 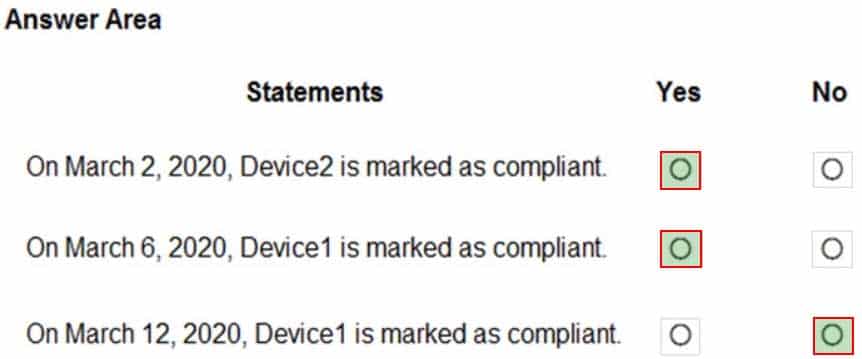
MS-500 Microsoft 365 Security Administration Part 03 Q01 051 Answer Explanation:Box 1: Yes
Device2 is in Group2 so Policy2 applies.
Device2 is not compliant with Policy2. However, the device won’t be marked as non-compliant until 10 days after the device was enrolled.Box 2: Yes
Device1 is in Group1 and Group2 so both Policy1 and Policy2 apply.
Device1 is compliant with Policy1 but non-compliant with Policy2. However, the device won’t be marked as non-compliant until 10 days after the device was enrolled.Box 3: No
Device1 is in Group1 and Group2 so both Policy1 and Policy2 apply.
Device1 is compliant with Policy1 but non-compliant with Policy2.
March 12th is more than 10 days after the device was enrolled so it will now be marked as non-compliant by Policy2. -
You have a Microsoft 365 tenant.
From the Azure Active Directory admin center, you review the Risky sign-ins report as shown in the following exhibit.
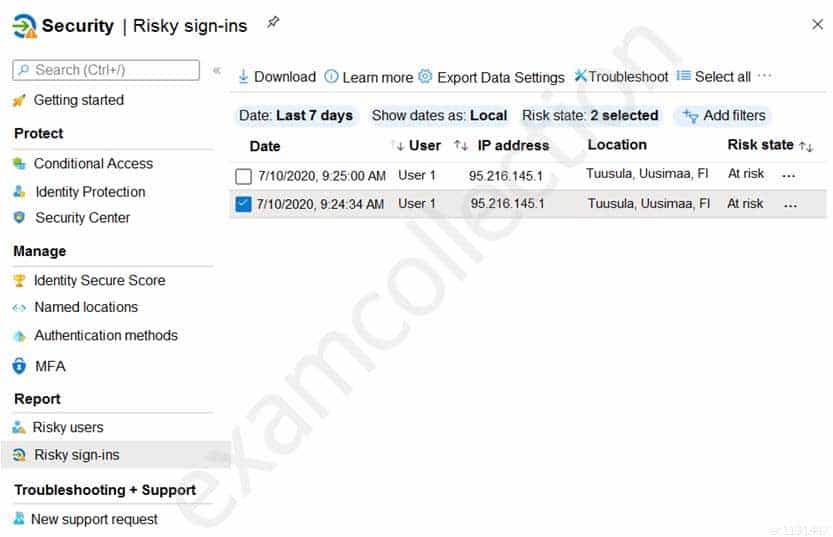
MS-500 Microsoft 365 Security Administration Part 03 Q02 052 You need to ensure that you can see additional details including the risk level and the risk detection type.
What should you do?
- Purchase Microsoft 365 Enterprise E5 licenses.
- Activate an instance of Microsoft Defender for Identity.
- Configure Diagnostic settings in Azure Active Directory (Azure AD).
- Deploy Azure Sentinel and add a Microsoft Office 365 connector.
-
You have a Microsoft 365 E5 subscription.
You plan to create a conditional access policy named Policy1.
You need to be able to use the sign-in risk level condition in Policy1.
What should you do first?
- Connect Microsoft Endpoint Manager and Microsoft Defender for Endpoint.
- From the Azure Active Directory admin center, configure the Diagnostics settings.
- From the Endpoint Management admin center, create a device compliance policy.
- Onboard Azure Active Directory (Azure AD) Identity Protection.
-
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
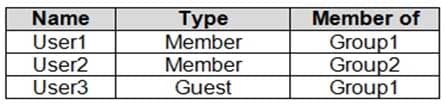
MS-500 Microsoft 365 Security Administration Part 03 Q04 053 You assign an enterprise application named App1 to Group1 and User2.
You configure an Azure AD access review of App1. The review has the following settings:
– Review name: Review1
– Start date: 01–15–2020
– Frequency: One time
– End date: 02–14–2020
– Users to review: Assigned to an application
– Scope: Everyone
– Applications: App1
– Reviewers: Members (self)
– Auto apply results to resource: Enable
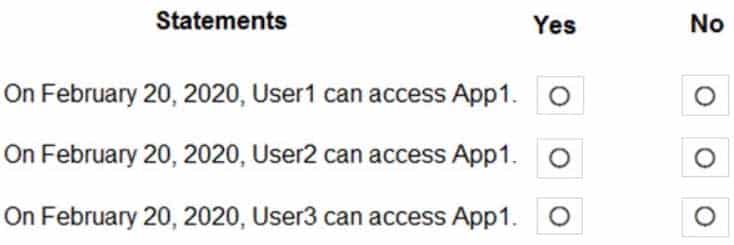
– Should reviewer not respond: Take recommendationsOn February 15, 2020, you review the access review report and see the entries shown in the following table:

MS-500 Microsoft 365 Security Administration Part 03 Q04 054 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
MS-500 Microsoft 365 Security Administration Part 03 Q04 055 Question 
MS-500 Microsoft 365 Security Administration Part 03 Q04 055 Answer -
Overview
Fabrikam, Inc. is manufacturing company that sells products through partner retail stores. Fabrikam has 5,000 employees located in offices throughout Europe.
Existing Environment
Network Infrastructure
The network contains an Active Directory forest named fabrikam.com. Fabrikam has a hybrid Microsoft Azure Active Directory (Azure AD) environment.The company maintains some on-premises servers for specific applications, but most end-user applications are provided by a Microsoft 365 E5 subscription.
Problem Statements
Fabrikam identifies the following issues:– Since last Friday, the IT team has been receiving automated email messages that contain “Unhealthy Identity Synchronization Notification” in the subject line.
– Several users recently opened email attachments that contained malware. The process to remove the malware was time consuming.Requirements
Planned Changes
Fabrikam plans to implement the following changes:– Fabrikam plans to monitor and investigate suspicious sign-ins to Active Directory
– Fabrikam plans to provide partners with access to some of the data stored in Microsoft 365Application Administration
Fabrikam identifies the following application requirements for managing workload applications:– User administrators will work from different countries
– User administrators will use the Azure Active Directory admin center
– Two new administrators named Admin1 and Admin2 will be responsible for managing Microsoft Exchange Online onlySecurity Requirements
Fabrikam identifies the following security requirements:– Access to the Azure Active Directory admin center by the user administrators must be reviewed every seven days. If an administrator fails to respond to an access request within three days, access must be removed
– Users who manage Microsoft 365 workloads must only be allowed to perform administrative tasks for up to three hours at a time. Global administrators must be exempt from this requirement
– Users must be prevented from inviting external users to view company data. Only global administrators and a user named User1 must be able to send invitations
– Microsoft Defender for Identity must capture security group modifications for sensitive groups, such as Domain Admins in Active Directory
– Workload administrators must use multi-factor authentication (MFA) when signing in from an anonymous or an unfamiliar location
– The location of the user administrators must be audited when the administrators authenticate to Azure AD
– Email messages that include attachments containing malware must be delivered without the attachment
– The principle of least privilege must be used whenever possible-
HOTSPOT
You need to recommend an email malware solution that meets the security requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
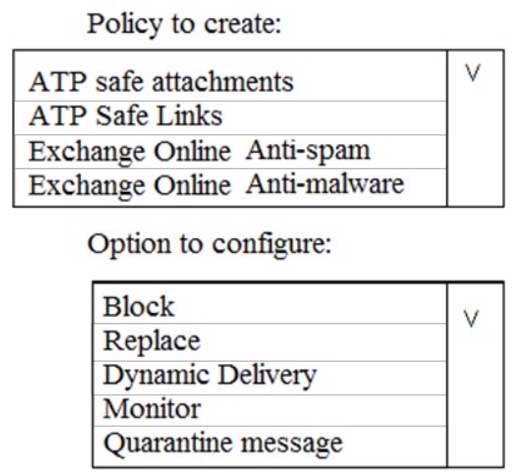
MS-500 Microsoft 365 Security Administration Part 03 Q05 056 Question 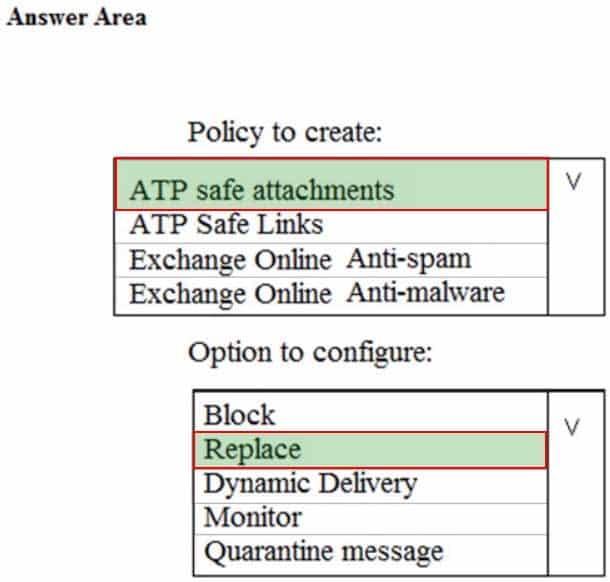
MS-500 Microsoft 365 Security Administration Part 03 Q05 056 Answer -
HOTSPOT
You install Microsoft Defender for Identity sensors on domain controllers.
You add a member to the Domain Admins group. You view the timeline in Microsoft Defender for Identity and discover that information regarding the membership change is missing.
You need to meet the security requirements for Microsoft Defender for Identity reporting.
What should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
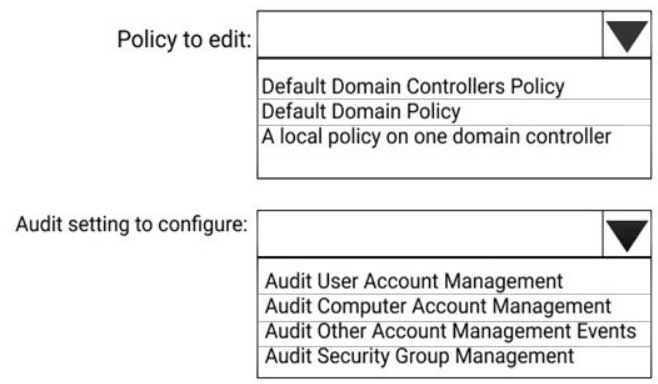
MS-500 Microsoft 365 Security Administration Part 03 Q05 057 Question 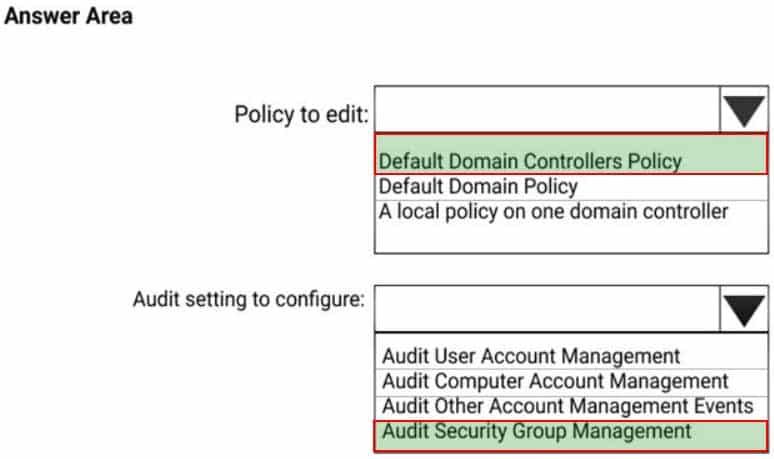
MS-500 Microsoft 365 Security Administration Part 03 Q05 057 Answer
-
-
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
Litware, Inc. is a financial company that has 1,000 users in its main office in Chicago and 100 users in a branch office in San Francisco.
Existing Environment
Internal Network Infrastructure
The network contains a single domain forest. The forest functional level is Windows Server 2016.Users are subject to sign-in hour restrictions as defined in Active Directory.
The network has the IP address ranges shown in the following table.
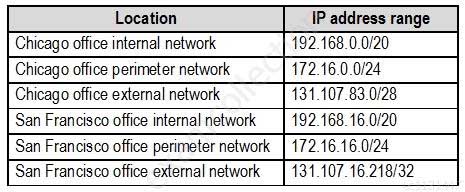
MS-500 Microsoft 365 Security Administration Part 03 Q06 058 The offices connect by using Multiprotocol Label Switching (MPLS).
The following operating systems are used on the network:
– Windows Server 2016
– Windows 10 Enterprise
– Windows 8.1 EnterpriseThe internal network contains the systems shown in the following table.
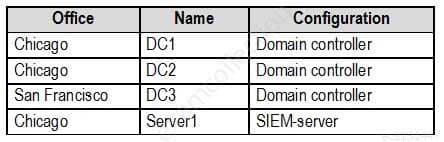
MS-500 Microsoft 365 Security Administration Part 03 Q06 059 Litware uses a third-party email system.
Cloud Infrastructure
Litware recently purchased Microsoft 365 subscription licenses for all users.Microsoft Azure Active Directory (Azure AD) Connect is installed and uses the default authentication settings. User accounts are not yet synced to Azure AD.
You have the Microsoft 365 users and groups shown in the following table.
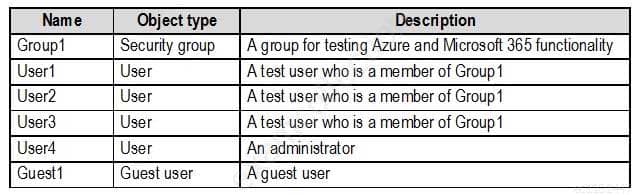
MS-500 Microsoft 365 Security Administration Part 03 Q06 060 Requirements
Planned Changes
Litware plans to implement the following changes:– Migrate the email system to Microsoft Exchange Online
– Implement Azure AD Privileged Identity ManagementSecurity Requirements
Litware identifies the following security requirements:
– Create a group named Group3 that will be used for publishing sensitivity labels to pilot users. Group3 must only contain user accounts
– Use Microsoft Defender for Identity to detect any security threats that target the forest
Prevent users locked out of Active Directory from signing in to Azure AD and Active Directory
– Implement a permanent eligible assignment of the Compliance administrator role for User1
– Configure domain-joined servers to ensure that they report sensor data to Microsoft Defender for Endpoint
– Prevent access to Azure resources for the guest user accounts by default
– Ensure that all domain-joined computers are registered to Azure ADMulti-factor authentication (MFA) Requirements
Security features of Microsoft Office 365 and Azure will be tested by using pilot Azure user accounts.
You identify the following requirements for testing MFA:
– Pilot users must use MFA unless they are signing in from the internal network of the Chicago office. MFA must NOT be used on the Chicago office internal network.
– If an authentication attempt is suspicious, MFA must be used, regardless of the user location.
– Any disruption of legitimate authentication attempts must be minimized.General Requirements
Litware wants to minimize the deployment of additional servers and services in the Active Directory forest.-
You need to enable and configure Microsoft Defender for Endpoint to meet the security requirements. What should you do?
- Configure port mirroring
- Create the ForceDefenderPassiveMode registry setting
- Download and install the Microsoft Monitoring Agent
- Run WindowsDefenderATPLocalOnboardingScript.cmd
-
DRAG DROP
You need to configure threat detection for Active Directory. The solution must meet the security requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
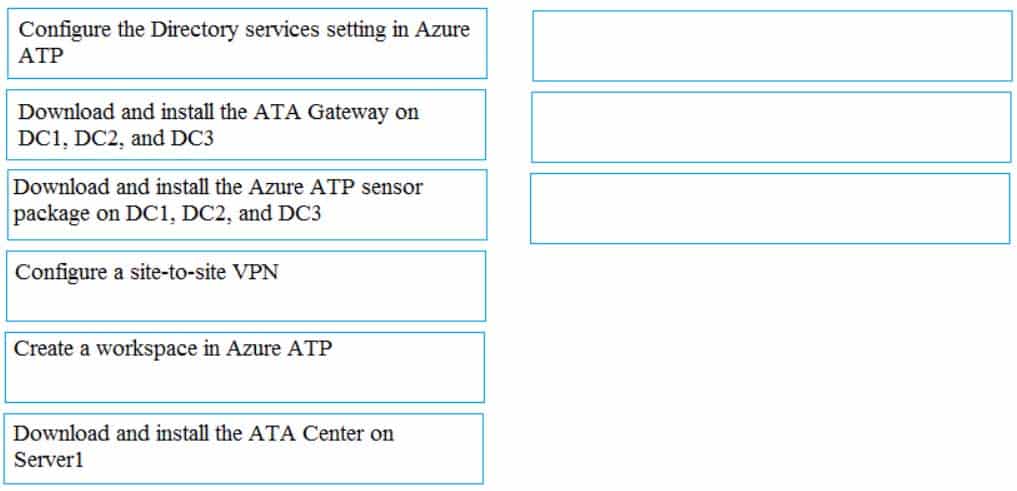
MS-500 Microsoft 365 Security Administration Part 03 Q06 061 Question 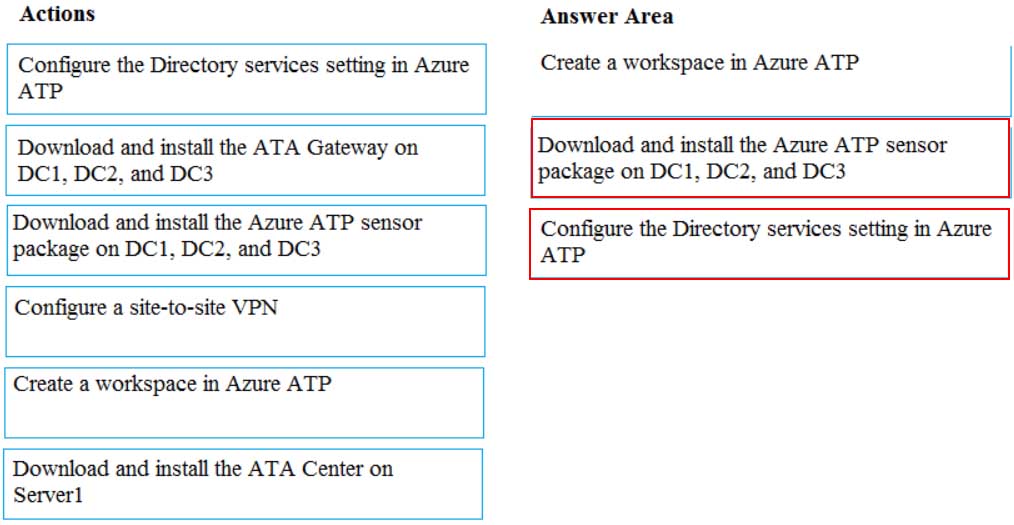
MS-500 Microsoft 365 Security Administration Part 03 Q06 061 Answer -
You need to enable and configure Microsoft Defender for Endpoint to meet the security requirements. What should you do?
- Configure port mirroring
- Create the ForceDefenderPassiveMode registry setting
- Download and install the Microsoft Monitoring Agent
- Run WindowsDefenderATPOnboardingScript.cmd
-
-
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
The company has the offices shown in the following table.
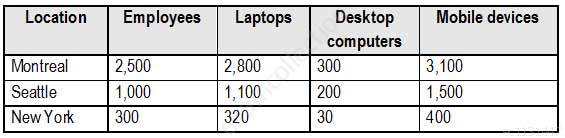
MS-500 Microsoft 365 Security Administration Part 03 Q07 062 Contoso has IT, human resources (HR), legal, marketing, and finance departments. Contoso uses Microsoft 365.
Existing Environment
Infrastructure
The network contains an Active Directory domain named contoso.com that is synced to a Microsoft Azure Active Directory (Azure AD) tenant. Password writeback is enabled.
The domain contains servers that run Windows Server 2016. The domain contains laptops and desktop computers that run Windows 10 Enterprise.
Each client computer has a single volume.
Each office connects to the Internet by using a NAT device. The offices have the IP addresses shown in the following table.
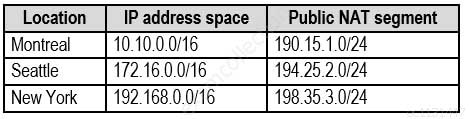
MS-500 Microsoft 365 Security Administration Part 03 Q07 063 Named locations are defined in Azure AD as shown in the following table.
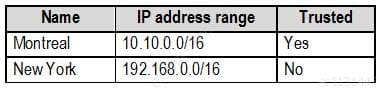
MS-500 Microsoft 365 Security Administration Part 03 Q07 064 From the Multi-Factor Authentication page, an address space of 198.35.3.0/24 is defined in the trusted IPs list.
Azure Multi-Factor Authentication (MFA) is enabled for the users in the finance department.
The tenant contains the users shown in the following table.
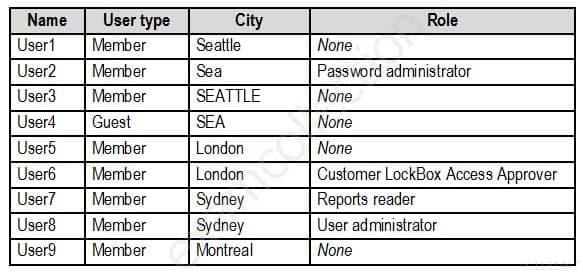
MS-500 Microsoft 365 Security Administration Part 03 Q07 065 The tenant contains the groups shown in the following table.
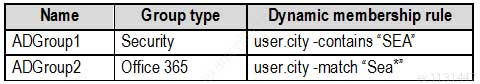
MS-500 Microsoft 365 Security Administration Part 03 Q07 066 Customer Lockbox is enabled in Microsoft 365.
Microsoft Endpoint Manager Configuration
The devices enrolled in Microsoft Endpoint Manager are configured as shown in the following table.
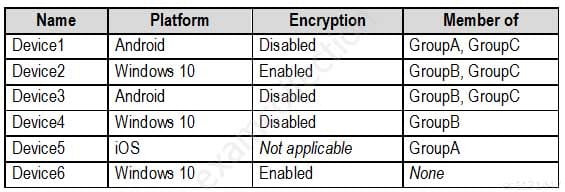
MS-500 Microsoft 365 Security Administration Part 03 Q07 067 The device compliance policies in Microsoft Endpoint Manager are configured as shown in the following table.
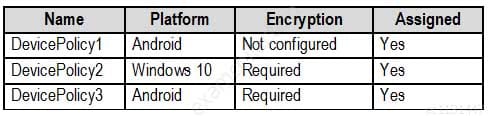
MS-500 Microsoft 365 Security Administration Part 03 Q07 068 The device compliance policies have the assignments shown in the following table.
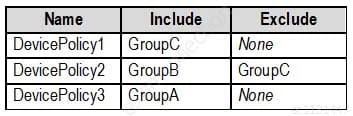
MS-500 Microsoft 365 Security Administration Part 03 Q07 069 The Mark devices with no compliance policy assigned as setting is set to Compliant.
Requirements
Technical Requirements
Contoso identifies the following technical requirements:
– Use the principle of least privilege
– Enable User1 to assign the Reports reader role to users
– Ensure that User6 approves Customer Lockbox requests as quickly as possible
– Ensure that User9 can enable and configure Azure AD Privileged Identity Management-
HOTSPOT
You are evaluating which devices are compliant in Endpoint Manager.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
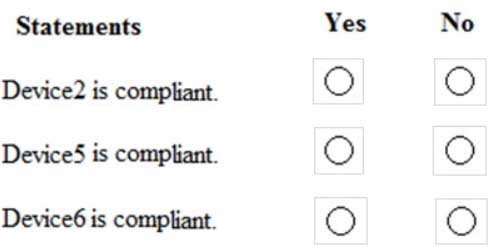
MS-500 Microsoft 365 Security Administration Part 03 Q07 070 Question 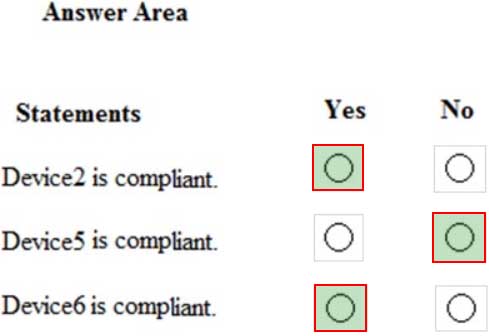
MS-500 Microsoft 365 Security Administration Part 03 Q07 070 Answer -
HOTSPOT
Which policies apply to which devices? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
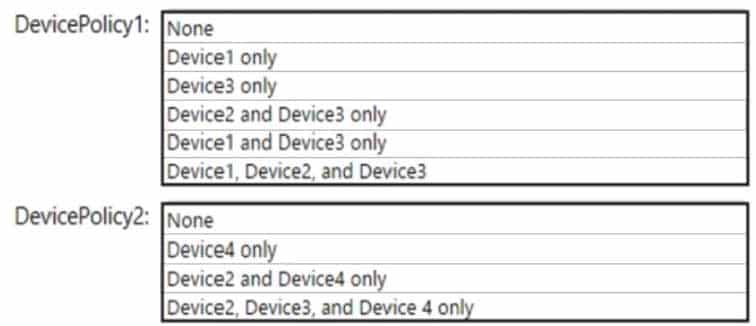
MS-500 Microsoft 365 Security Administration Part 03 Q07 071 Question 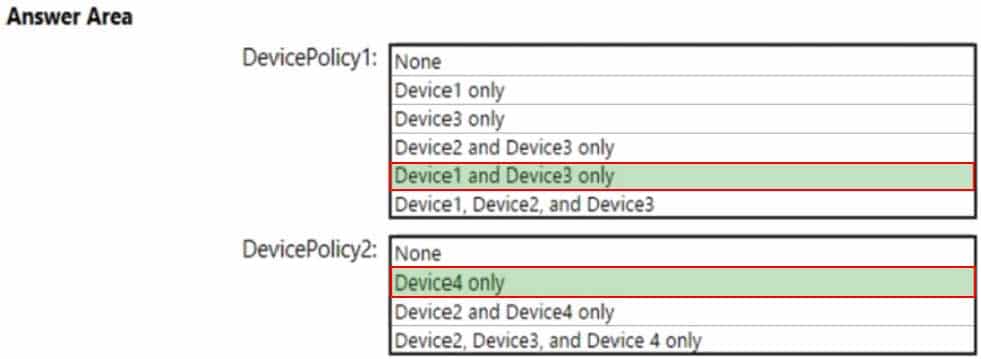
MS-500 Microsoft 365 Security Administration Part 03 Q07 071 Answer
-
-
You have a Microsoft 365 subscription that contains several Windows 10 devices. The devices are managed by using Microsoft Endpoint Manager.
You need to enable Windows Defender Exploit Guard (Windows Defender EG) on the devices.
Which type of device configuration profile should you use?
- Endpoint protection
- Device restrictions
- Identity protection
- Windows Defender ATP
-
DRAG DROP
You have a Microsoft 365 E5 subscription.
All computers run Windows 10 and are onboarded to Microsoft Defender for Endpoint.
You create a Microsoft Defender for Endpoint machine group named MachineGroup1.
You need to enable delegation for the security settings of the computers in MachineGroup1.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
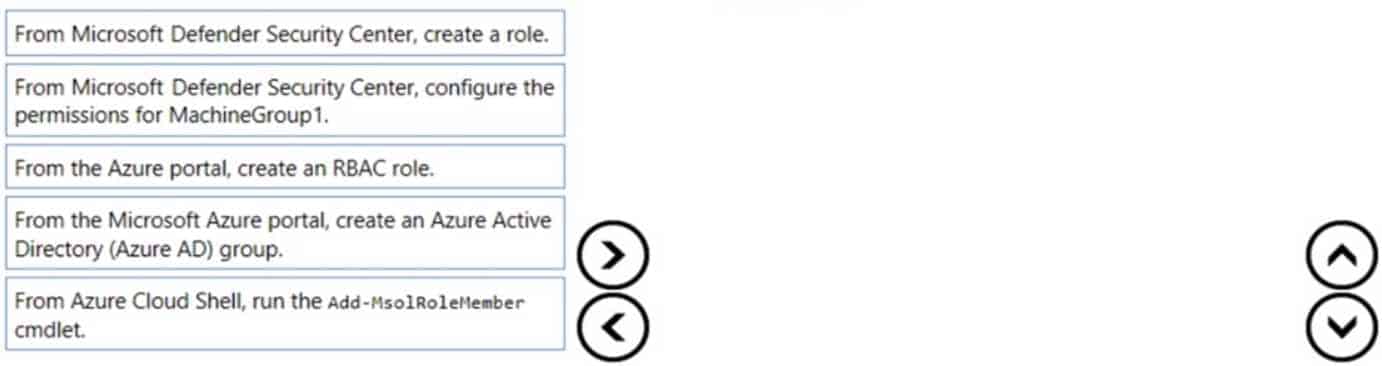
MS-500 Microsoft 365 Security Administration Part 03 Q09 072 Question 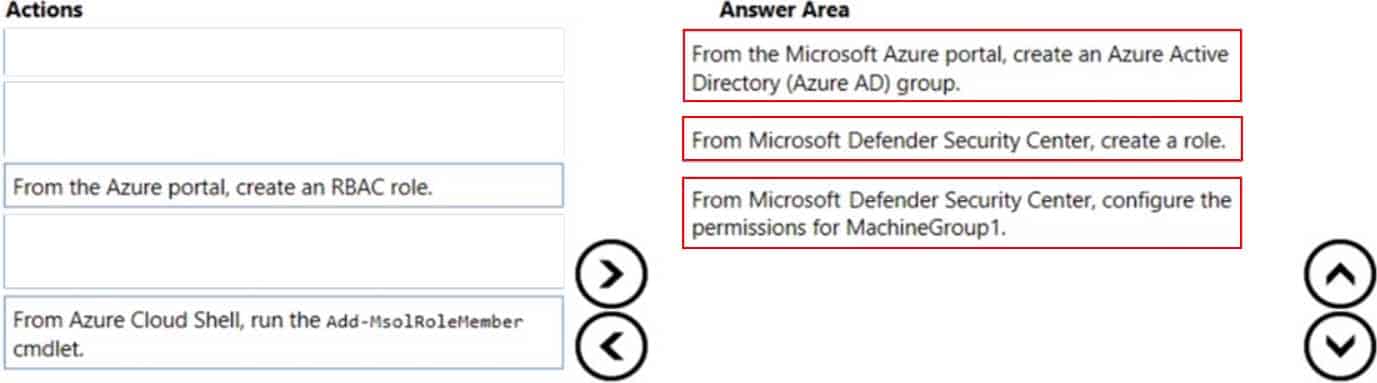
MS-500 Microsoft 365 Security Administration Part 03 Q09 072 Answer -
You have a hybrid Microsoft Exchange Server organization. All users have Microsoft 365 E5 licenses.
You plan to implement a Microsoft Defender for Office 365 anti-phishing policy.
You need to enable mailbox intelligence for all users.
What should you do first?
- Configure attribute filtering in Microsoft Azure Active Directory Connect (Azure AD Connect)
- Purchase the Microsoft Defender for Office 365 add-on
- Select Directory extension attribute sync in Microsoft Azure Active Directory Connect (Azure AD Connect)
- Migrate the on-premises mailboxes to Exchange Online
-
HOTSPOT
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
Four Windows 10 devices are joined to the tenant as shown in the following table.
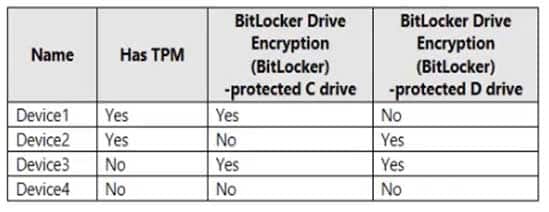
MS-500 Microsoft 365 Security Administration Part 03 Q11 073 On which devices can you use BitLocker To Go and on which devices can you turn on auto-unlock? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
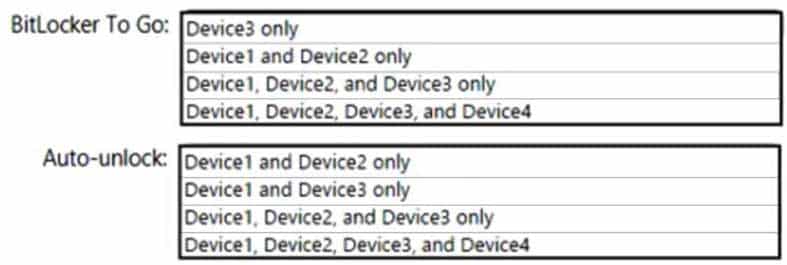
MS-500 Microsoft 365 Security Administration Part 03 Q11 074 Question 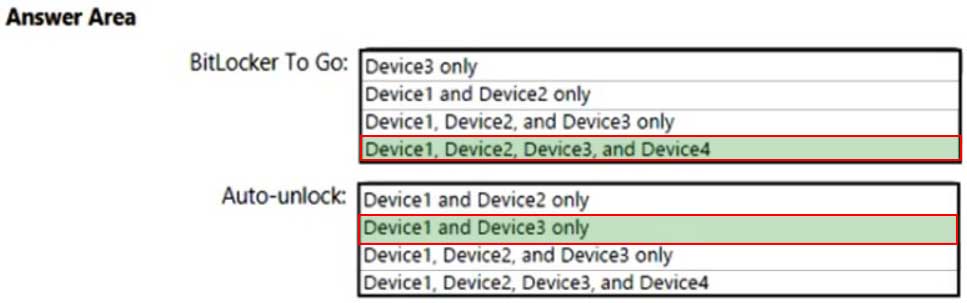
MS-500 Microsoft 365 Security Administration Part 03 Q11 074 Answer -
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
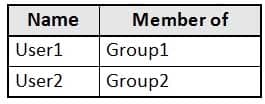
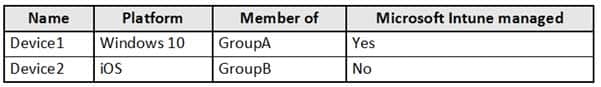
MS-500 Microsoft 365 Security Administration Part 03 Q12 075 You register devices in contoso.com as shown in the following table.
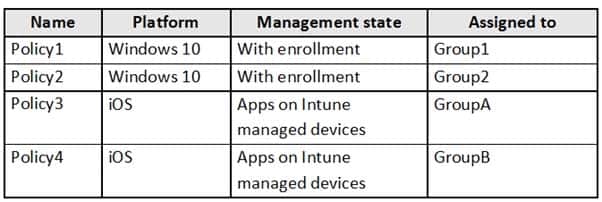
MS-500 Microsoft 365 Security Administration Part 03 Q12 076 You create app protection policies in Intune as shown in the following table.
MS-500 Microsoft 365 Security Administration Part 03 Q12 077 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
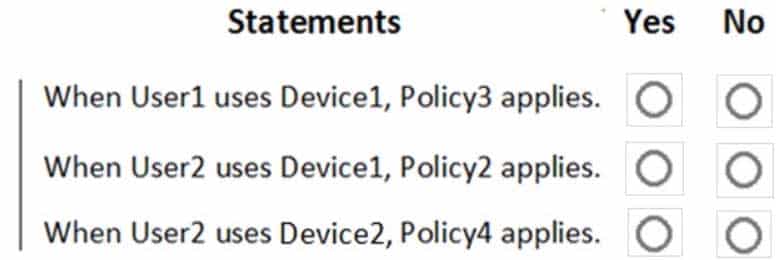
MS-500 Microsoft 365 Security Administration Part 03 Q12 078 Question 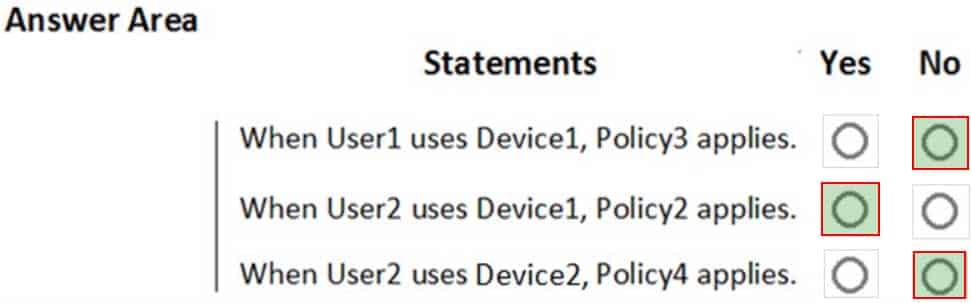
MS-500 Microsoft 365 Security Administration Part 03 Q12 078 Answer -
DRAG DROP
You have a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. All the devices in the tenant are managed by using Microsoft Endpoint Manager.
You purchase a cloud app named App1 that supports session controls.
You need to ensure that access to App1 can be reviewed in real time.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
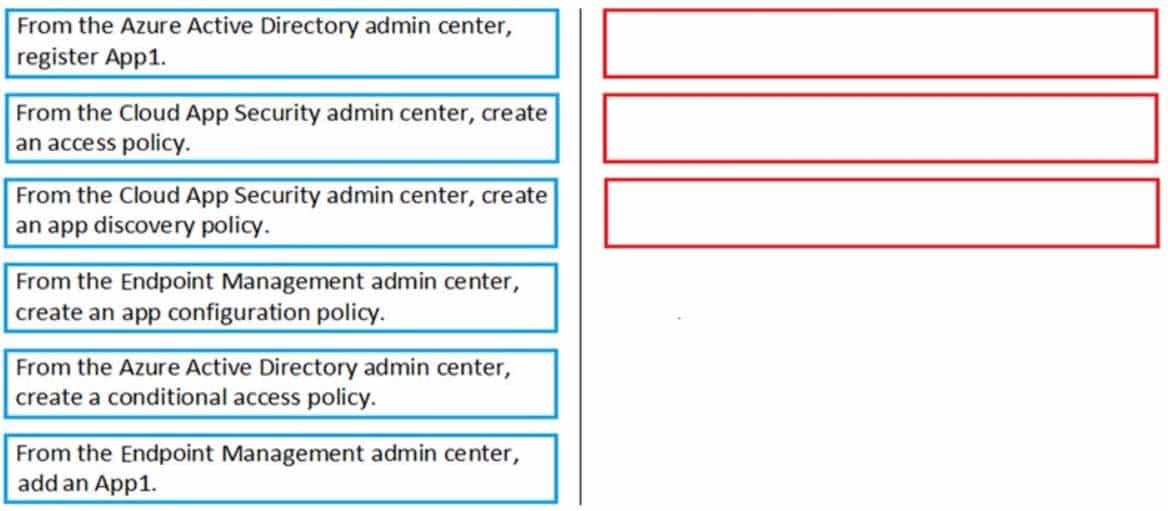
MS-500 Microsoft 365 Security Administration Part 03 Q13 079 Question 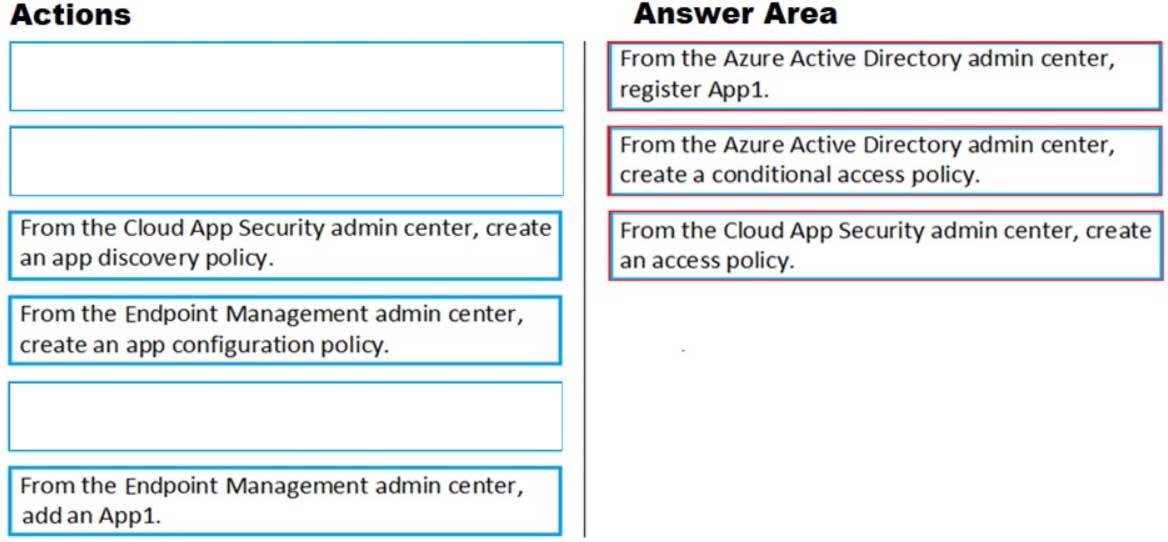
MS-500 Microsoft 365 Security Administration Part 03 Q13 079 Answer -
You configure several Microsoft Defender for Office 365 policies in a Microsoft 365 subscription.
You need to allow a user named User1 to view Microsoft Defender for Office 365 reports in the Threat management dashboard.
Which role provides User1 with the required role permissions?
- Security reader
- Compliance administrator
- Information Protection administrator
- Exchange administrator
-
You have a Microsoft 365 Enterprise E5 subscription.
You use Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP). You plan to use Microsoft Office 365 Attack simulator.
What is a prerequisite for running Attack simulator?
- Enable multi-factor authentication (MFA)
- Configure Office 365 Advanced Threat Protection (ATP)
- Create a Conditional Access App Control policy for accessing Office 365
- Integrate Office 365 Threat Intelligence and Microsoft Defender ATP
-
You have a Microsoft 365 E5 subscription and a hybrid Microsoft Exchange Server organization.
Each member of a group named Executive has an on-premises mailbox. Only the Executive group members have multi-factor authentication (MFA) enabled. Each member of a group named Research has a mailbox in Exchange Online.
You need to use Microsoft Office 365 Attack simulator to model a spear-phishing attack that targets the Research group members.
The email addresses that you intend to spoof belong to the Executive group members.
What should you do first?
- From the Azure ATP admin center, configure the primary workspace settings
- From the Microsoft Azure portal, configure the user risk policy settings in Azure AD Identity Protection
- Enable MFA for the Research group members
- Migrate the Executive group members to Exchange Online
-
You have a Microsoft 365 E5 subscription.
You implement Advanced Threat Protection (ATP) safe attachments policies for all users.
User reports that email messages containing attachments take longer than expected to be received.
You need to reduce the amount of time it takes to receive email messages that contain attachments. The solution must ensure that all attachments are scanned for malware. Attachments that have malware must be blocked.
What should you do from ATP?
- Set the action to Block
- Add an exception
- Add a condition
- Set the action to Dynamic Delivery
-
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains a VPN server named VPN1 that runs Windows Server 2016 and has the Remote Access server role installed.
You have a Microsoft Azure subscription.
You are deploying Microsoft Defender for Identity.
You install a Microsoft Defender for Identity standalone sensor on a server named Server1 that runs Windows Server 2016.
You need to integrate the VPN and Microsoft Defender for Identity.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
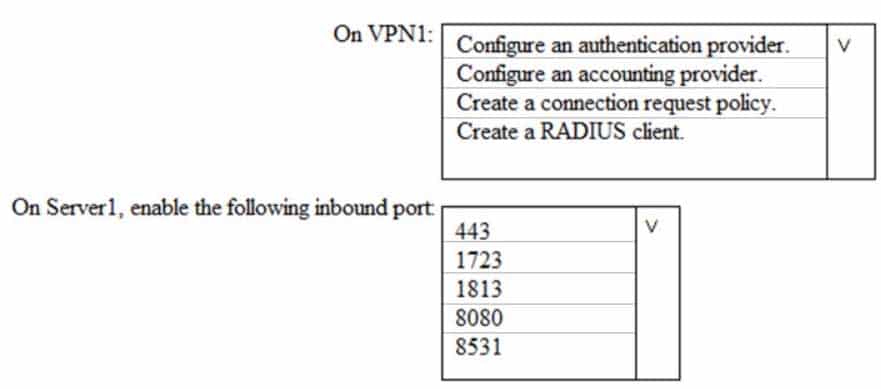
MS-500 Microsoft 365 Security Administration Part 03 Q18 080 Question 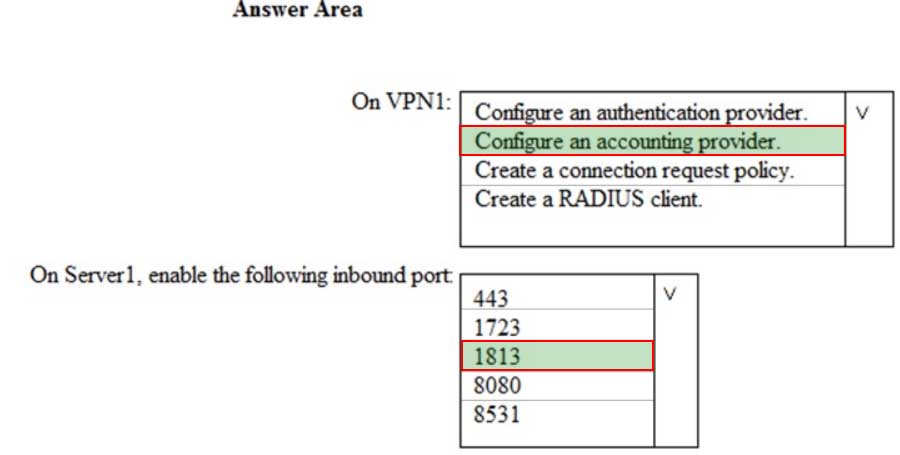
MS-500 Microsoft 365 Security Administration Part 03 Q18 080 Answer -
HOTSPOT
You have a Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP) deployment that has the custom network indicators turned on. Microsoft Defender ATP protects two computers that run Windows 10 as shown in the following table.
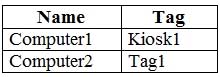
MS-500 Microsoft 365 Security Administration Part 03 Q19 081 Microsoft Defender ATP has the machine groups shown in the following table.
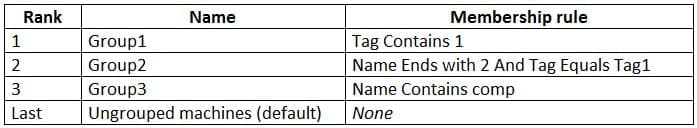
MS-500 Microsoft 365 Security Administration Part 03 Q19 082 From Microsoft Defender Security Center, you create the URLs/Domains indicators shown in the following table.
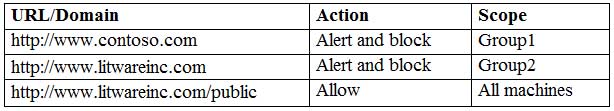
MS-500 Microsoft 365 Security Administration Part 03 Q19 083 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
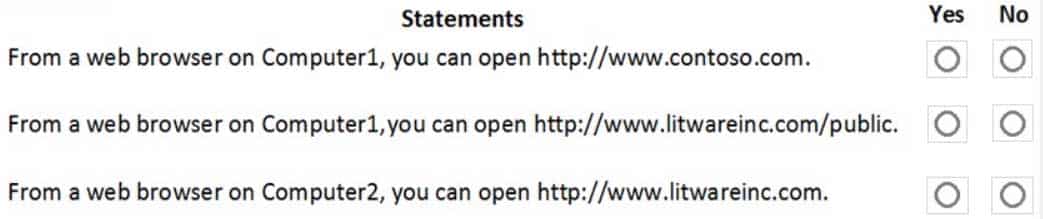
MS-500 Microsoft 365 Security Administration Part 03 Q19 084 Question 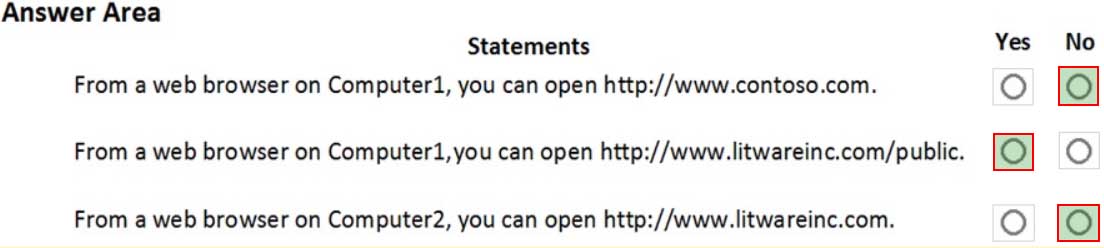
MS-500 Microsoft 365 Security Administration Part 03 Q19 084 Answer -
SIMULATION
You need to ensure that a user named Allan Deyoung uses multi-factor authentication (MFA) for all authentication requests.
To complete this task, sign in to the Microsoft 365 admin center.
- See explanation below.
Explanation:1. Open the Admin Center and go to Users > Active Users
2. Open Multi-factor authenticationDon’t select any user yet, just open the Multi-factor authentication screen. You will find the button in the toolbar.
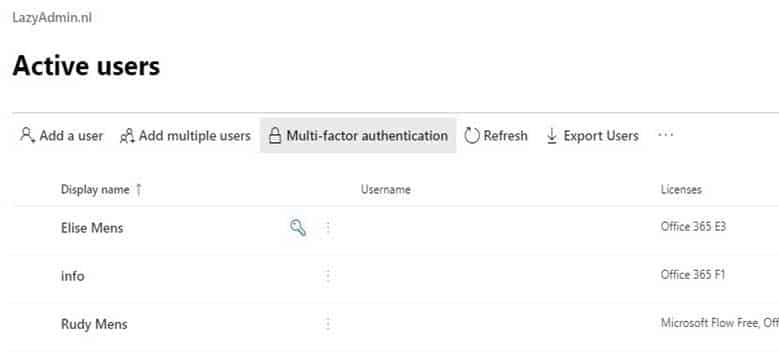
MS-500 Microsoft 365 Security Administration Part 03 Q20 085 3. Open the Service settings
Before we start enabling MFA for the users, we first go through the service settings. The button to the settings screen doesn’t stand out, but it’s just below the title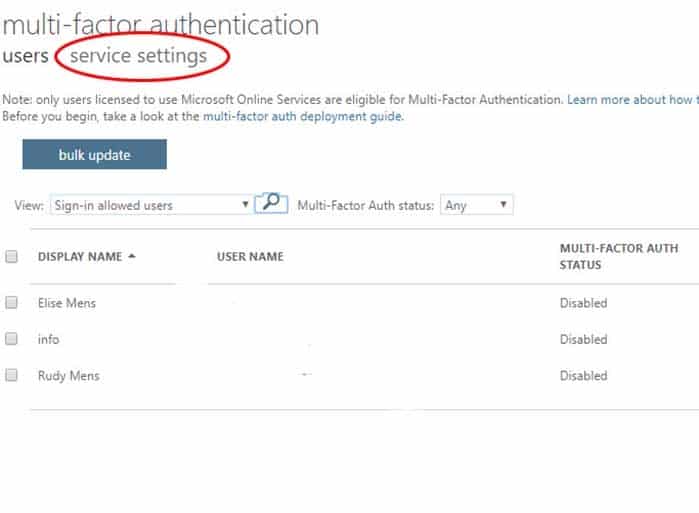
MS-500 Microsoft 365 Security Administration Part 03 Q20 086 4. Setup MFA Office 365
A few settings are important here:
– Make sure you check the App password. Otherwise, users can’t authenticate in some applications (like the default mail app in Android).
– Also, take a look at the remember function. By default, it is set to 14 days.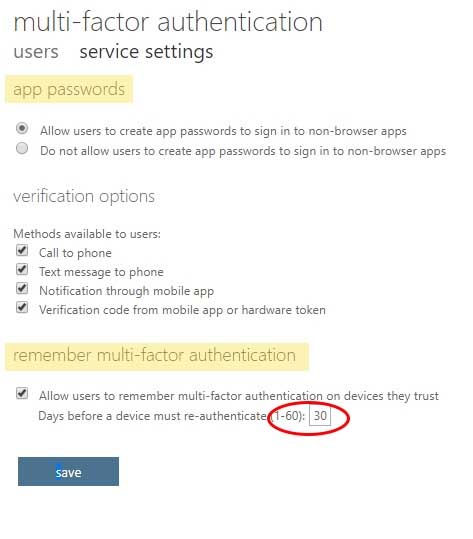
MS-500 Microsoft 365 Security Administration Part 03 Q20 087 5. Enable MFA for Office 365 users
After you have set the settings to your liking click on save and then on users (just below the title Multi-factor authentication).
You see the list of your users again. Here you can select single or multiple users to enable MFA.
At the moment you enable Office 365 MFA for a user it can get the setup screen as soon as the users browse to one of the Office 365 products.
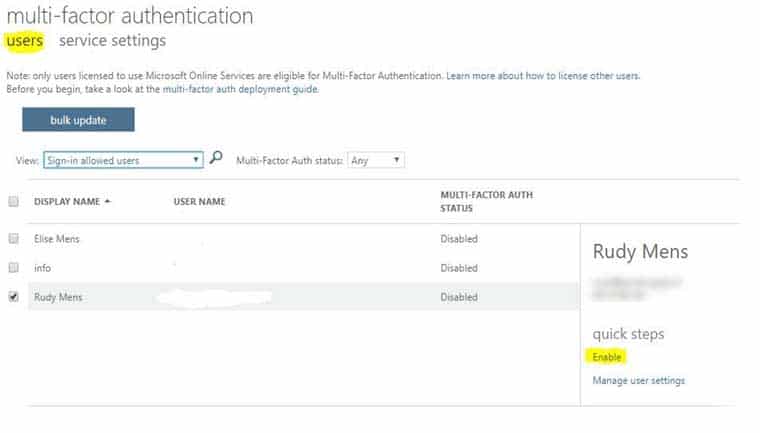
MS-500 Microsoft 365 Security Administration Part 03 Q20 088