MS-500 : Microsoft 365 Security Administration : Part 05
MS-500 : Microsoft 365 Security Administration : Part 05
-
Your network contains an on-premises Active Directory domain. The domain contains servers that run Windows Server and have advanced auditing enabled.
The security logs of the servers are collected by using a third-party SIEM solution.
You purchase a Microsoft 365 subscription and plan to deploy Azure Advanced Threat Protection (ATP) by using standalone sensors.
You need to ensure that you can detect when sensitive groups are modified and when malicious services are created.
What should you do?
- Turn off Delayed updates for the Azure ATP sensors.
- Configure auditing in the Office 365 Security & Compliance center.
- Turn on Delayed updates for the Azure ATP sensors.
- Integrate SIEM and Azure ATP.
Explanation:
Note:
There are several versions of this question in the exam. The questions in the exam have two different correct answers:
1. Integrate SIEM and Azure ATP.
2. Configure Event Forwarding on the domain controllersOther incorrect answer options you may see on the exam include the following:
1. Configure Azure ATP notifications
2. Modify the Domain synchronizer candidate settings on the Azure ATP sensors
3. Enable the Audit account management Group Policy setting for the servers. -
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) connector and a Microsoft Office 365 connector.
You need to use a Fusion rule template to detect multistage attacks in which users sign in by using compromised credentials, and then delete multiple files from Microsoft OneDrive.
Based on the Fusion rule template, you create an active rule that has the default settings.
What should you do next?
- Add data connectors.
- Add a workbook.
- Add a playbook.
- Create a custom rule template.
-
You have a Microsoft 365 subscription that uses a default domain name of fabrikam.com.
You create a safe links policy, as shown in the following exhibit.
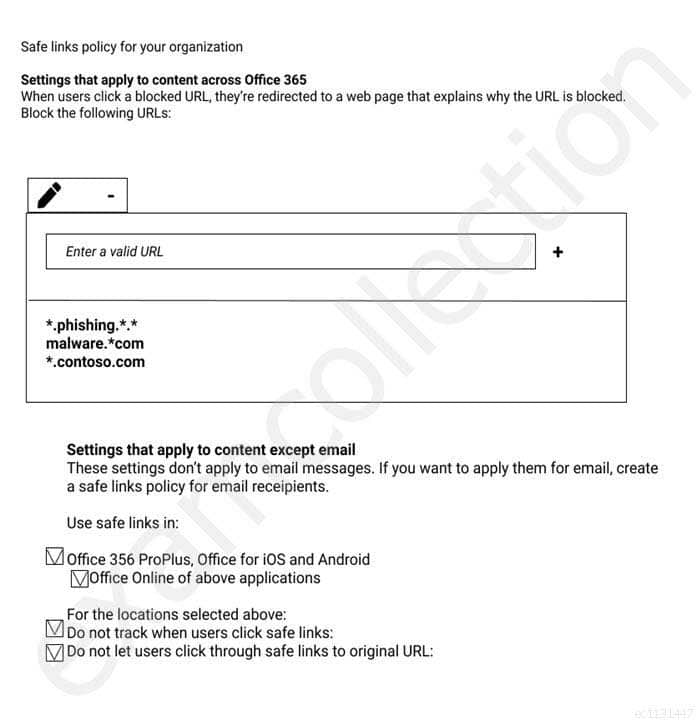
MS-500 Microsoft 365 Security Administration Part 05 Q03 107 Which URL can a user safely access from Microsoft Word Online?
- fabrikam.phishing.fabrikam.com
- malware.fabrikam.com
- fabrikam.contoso.com
- www.malware.fabrikam.com
-
HOTSPOT
You have a Microsoft 365 tenant.
You create an attack surface reduction policy that uses an application control profile as shown in the following exhibit.
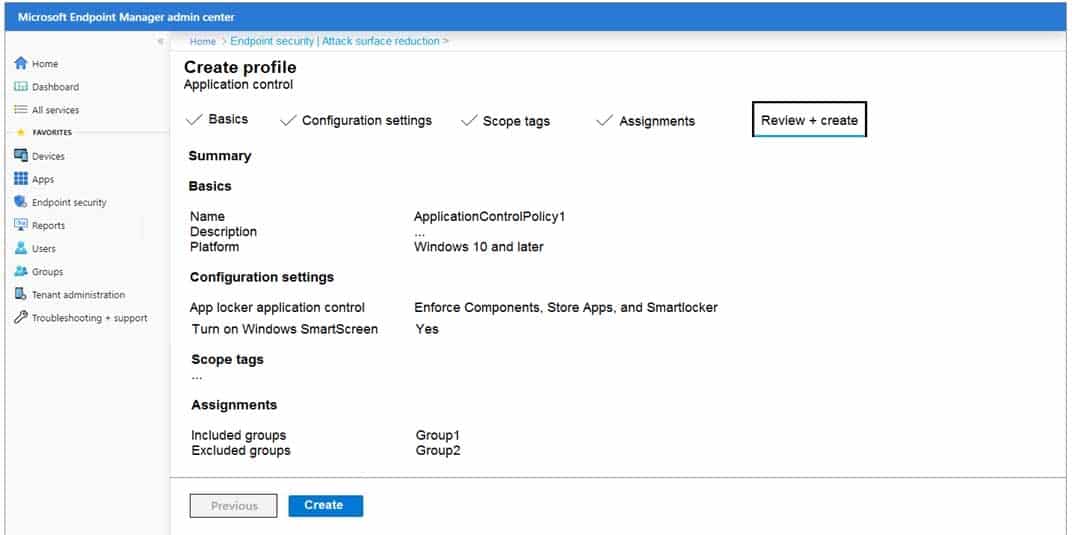
MS-500 Microsoft 365 Security Administration Part 05 Q04 108 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
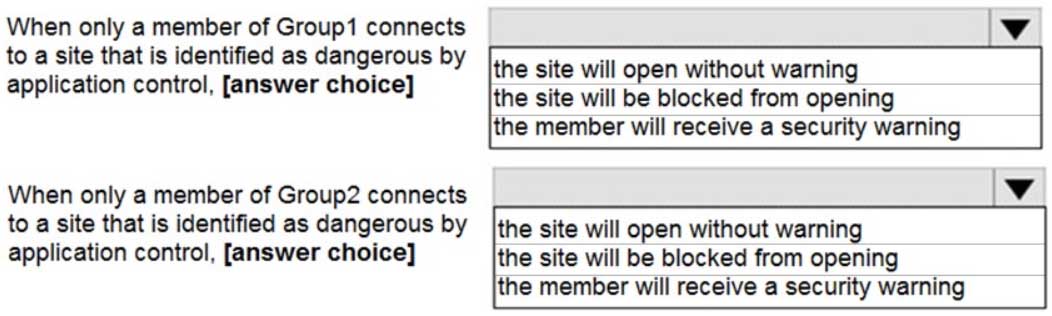
MS-500 Microsoft 365 Security Administration Part 05 Q04 109 Question 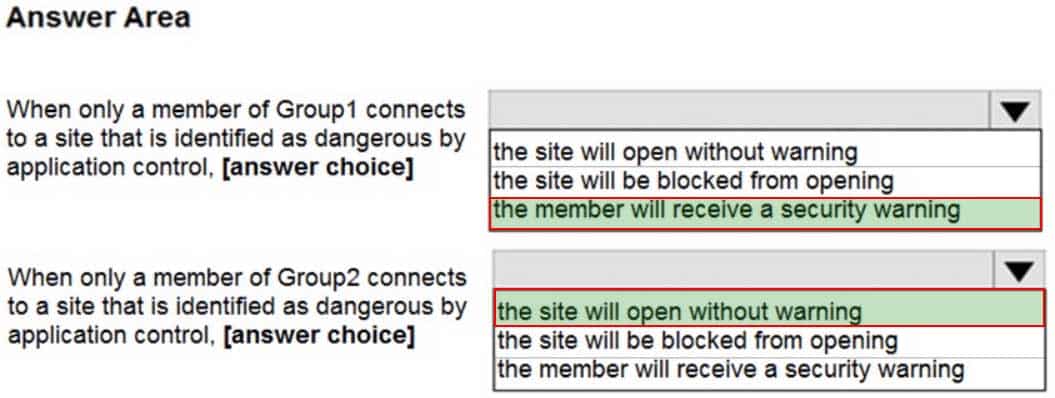
MS-500 Microsoft 365 Security Administration Part 05 Q04 109 Answer Explanation:Box 1: the member will receive a security warning.
Group1 is included in the policy so SmartScreen will be enabled. SmartScreen will display a warning.Box 2: the site will open without warning.
Group2 is excluded from the policy so SmartScreen will not be enabled. Therefore, no warning will be displayed. -
DRAG DROP
You have an on-premises Hyper-V infrastructure that contains the following:
– An Active Directory domain
– A domain controller named Server1
– A member server named Server2A security policy specifies that Server1 cannot connect to the Internet. Server2 can connect to the Internet.
You need to implement Azure Advanced Threat Protection (ATP) to monitor the security of the domain.
What should you configure on each server? To answer, drag the appropriate components to the correct servers. Each component may only be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
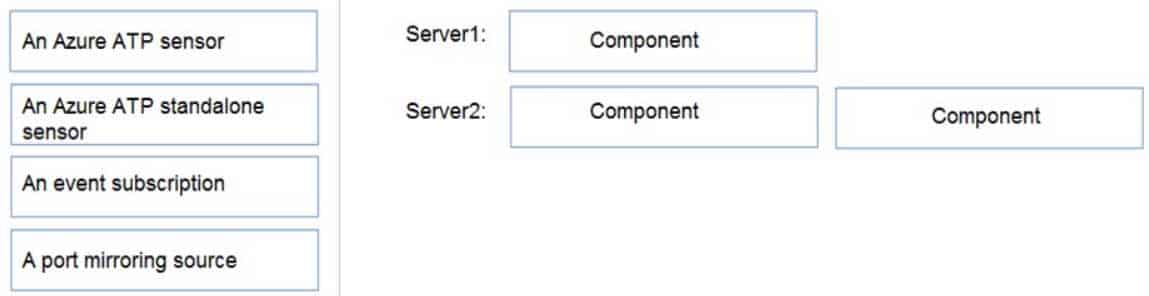
MS-500 Microsoft 365 Security Administration Part 05 Q05 110 Question 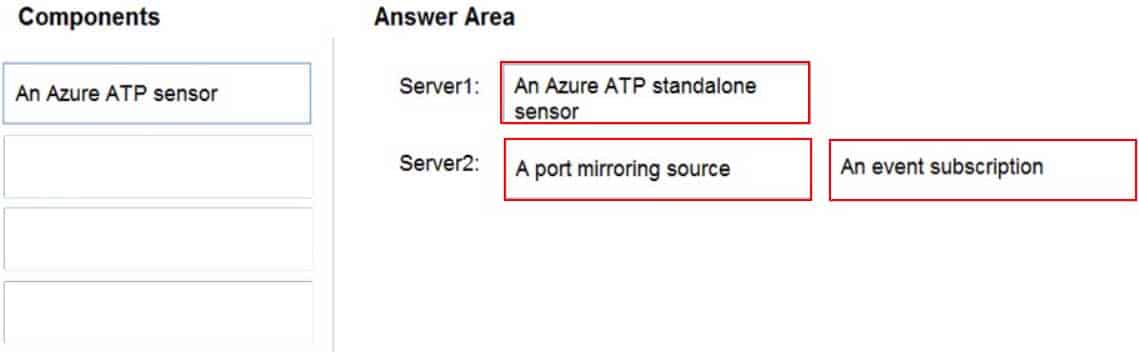
MS-500 Microsoft 365 Security Administration Part 05 Q05 110 Answer -
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
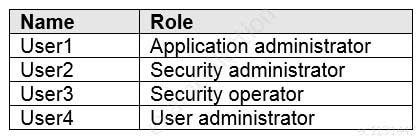
MS-500 Microsoft 365 Security Administration Part 05 Q06 111 You need to identify which user can enable Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP) roles.
Which user should you identify?
- User1
- User4
- User3
- User2
-
You have an Azure Sentinel workspace.
You need to manage incidents based on alerts generated by Microsoft Cloud App Security.
What should you do first?
- From the Cloud App Security admin center, configure security extensions.
- From the Cloud App Security admin center, configure app connectors.
- From the Cloud App Security admin center, configure log collectors.
- From the Microsoft 365 compliance center, add and configure a data connector.
-
Your network contains an on-premises Active Directory domain. The domain contains servers that run Windows Server and have advanced auditing enabled.
The security logs of the servers are collected by using a third-party SIEM solution.
You purchase a Microsoft 365 subscription and plan to deploy Azure Advanced Threat Protection (ATP) by using standalone sensors.
You need to ensure that you can detect when sensitive groups are modified and when malicious services are created.
What should you do?
- Configure Event Forwarding on the domain controllers.
- Configure auditing in the Office 365 Security & Compliance center.
- Turn on Delayed updates for the Azure ATP sensors.
- Enable the Audit account management Group Policy setting for the servers.
Explanation:Note:
There are several versions of this question in the exam. The questions in the exam have two different correct answers:
1. Integrate SIEM and Azure ATP.
2. Configure Event Forwarding on the domain controllersOther incorrect answer options you may see on the exam include the following:
1. Configure Azure ATP notifications
2. Modify the Domain synchronizer candidate settings on the Azure ATP sensors -
Several users in your Microsoft 365 subscription report that they received an email message without the attachment.
You need to review the attachments that were removed from the messages.
Which two tools can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- the Exchange admin center
- the Azure ATP admin center
- Outlook on the web
- the Security & Compliance admin center
- Microsoft Azure Security Center
-
You have a hybrid Microsoft 365 deployment that contains the Windows 10 devices shown in the following table.
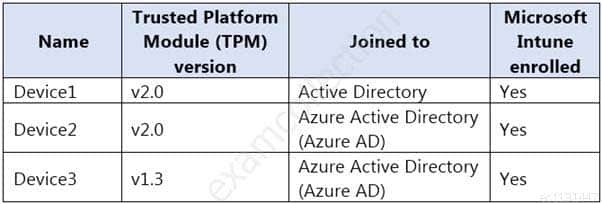
MS-500 Microsoft 365 Security Administration Part 05 Q10 112 You assign a Microsoft Endpoint Manager disk encryption policy that automatically and silently enables BitLocker Drive Encryption (BitLocker) on all the devices.
Which devices will have BitLocker enabled?
- Device1, Device2, and Device3
- Device2 only
- Device1 and Device2 only
- Device2 and Device3 only
Explanation:To silently enable BitLocker, the device must be Azure AD Joined or Hybrid Azure AD Joined and the device must contain TPM (Trusted Platform Module) 2.0.
Incorrect Answers:
A: Device1 is not Azure AD Joined or Hybrid Azure AD Joined, and the TPM version on Device3 is only 1.3. To silently enable BitLocker, the device must be Azure AD Joined or Hybrid Azure AD Joined and the device must contain TPM (Trusted Platform Module) 2.0.
C: Device1 is not Azure AD Joined or Hybrid Azure AD Joined. To silently enable BitLocker, the device must be Azure AD Joined or Hybrid Azure AD Joined.
D: The TPM version on Device3 is only 1.3. To silently enable BitLocker, the device must contain TPM (Trusted Platform Module) 2.0. -
HOTSPOT
You have an Azure Sentinel workspace.
You configure a rule to generate Azure Sentinel alerts when Azure Active Directory (Azure AD) Identity Protection detects risky sign-ins. You develop an Azure Logic Apps solution to contact users and verify whether reported risky sign-ins are legitimate.
You need to configure the workspace to meet the following requirements:
– Call the Azure logic app when an alert is triggered for a risky sign-in.
– To the Azure Sentinel portal, add a custom dashboard that displays statistics for risky sign-ins that are detected and resolved.What should you configure in Azure Sentinel to meet each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MS-500 Microsoft 365 Security Administration Part 05 Q11 113 Question 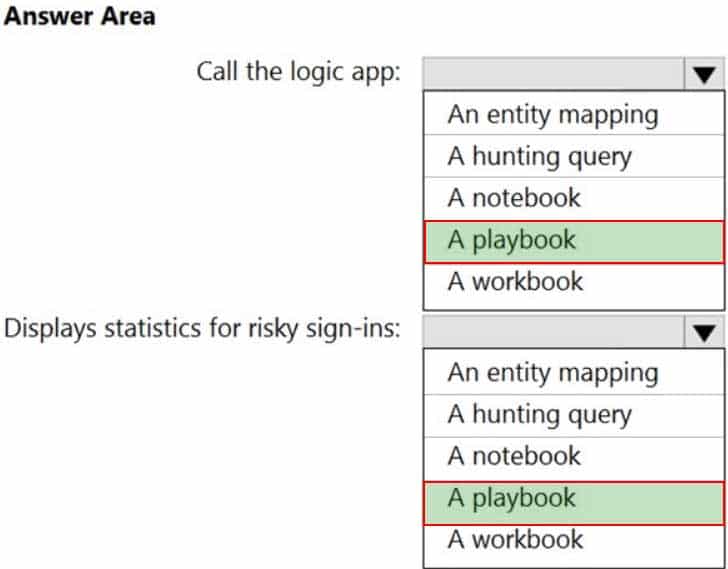
MS-500 Microsoft 365 Security Administration Part 05 Q11 113 Answer -
DRAG DROP
You have an Azure subscription and a Microsoft 365 subscription.
You need to perform the following actions:
– Deploy Azure Sentinel.
– Collect the Microsoft 365 activity log by using Azure Sentinel.Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
MS-500 Microsoft 365 Security Administration Part 05 Q12 114 Question 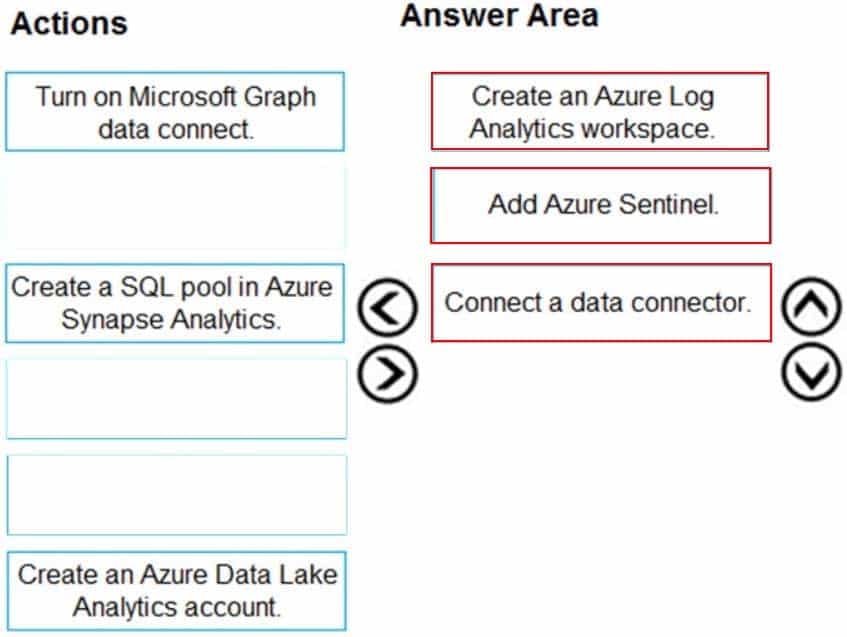
MS-500 Microsoft 365 Security Administration Part 05 Q12 114 Answer -
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.Overview
Fabrikam, Inc. is manufacturing company that sells products through partner retail stores. Fabrikam has 5,000 employees located in offices throughout Europe.
Existing Environment
Network Infrastructure
The network contains an Active Directory forest named fabrikam.com. Fabrikam has a hybrid Microsoft Azure Active Directory (Azure AD) environment.
The company maintains some on-premises servers for specific applications, but most end-user applications are provided by a Microsoft 365 E5 subscription.
Problem Statements
Fabrikam identifies the following issues:
– Since last Friday, the IT team has been receiving automated email messages that contain “Unhealthy Identity Synchronization Notification” in the subject line.
– Several users recently opened email attachments that contained malware. The process to remove the malware was time consuming.Requirements
Planned Changes
Fabrikam plans to implement the following changes:
– Fabrikam plans to monitor and investigate suspicious sign-ins to Active Directory
– Fabrikam plans to provide partners with access to some of the data stored in Microsoft 365Application Administration
Fabrikam identifies the following application requirements for managing workload applications:
– User administrators will work from different countries
– User administrators will use the Azure Active Directory admin center
– Two new administrators named Admin1 and Admin2 will be responsible for managing Microsoft Exchange Online onlySecurity Requirements
Fabrikam identifies the following security requirements:
– Access to the Azure Active Directory admin center by the user administrators must be reviewed every seven days. If an administrator fails to respond to an access request within three days, access must be removed
– Users who manage Microsoft 365 workloads must only be allowed to perform administrative tasks for up to three hours at a time. Global administrators must be exempt from this requirement
– Users must be prevented from inviting external users to view company data. Only global administrators and a user named User1 must be able to send invitations
– Microsoft Defender for Identity must capture security group modifications for sensitive groups, such as Domain Admins in Active Directory
– Workload administrators must use multi-factor authentication (MFA) when signing in from an anonymous or an unfamiliar location
– The location of the user administrators must be audited when the administrators authenticate to Azure AD
– Email messages that include attachments containing malware must be delivered without the attachment
– The principle of least privilege must be used whenever possible-
You need to recommend a solution that meets the technical and security requirements for sharing data with the partners.
What should you include in the recommendation? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Create an access review
- Assign the Global administrator role to User1
- Assign the Guest inviter role to User1
- Modify the External collaboration settings in the Azure Active Directory admin center
-
-
You have a Microsoft 365 subscription that includes a user named User1.
You have a conditional access policy that applies to Microsoft Exchange Online. The conditional access policy is configured to use Conditional Access App Control.
You need to create a Microsoft Cloud App Security policy that blocks User1 from printing from Exchange Online.
Which type of Cloud App Security policy should you create?
- an app permission policy
- an activity policy
- a Cloud Discovery anomaly detection policy
- a session policy
-
HOTSPOT
You have a Microsoft 365 E5 subscription.
From Microsoft Azure Active Directory (Azure AD), you create a security group named Group1. You add 10 users to Group1.
You need to apply app enforced restrictions to the members of Group1 when they connect to Microsoft Exchange Online from non-compliant devices, regardless of their location.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
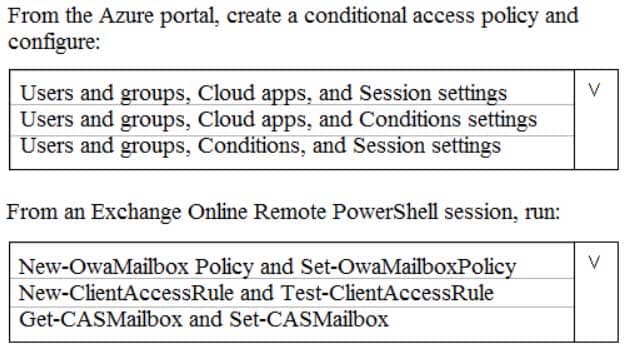
MS-500 Microsoft 365 Security Administration Part 05 Q15 115 Question 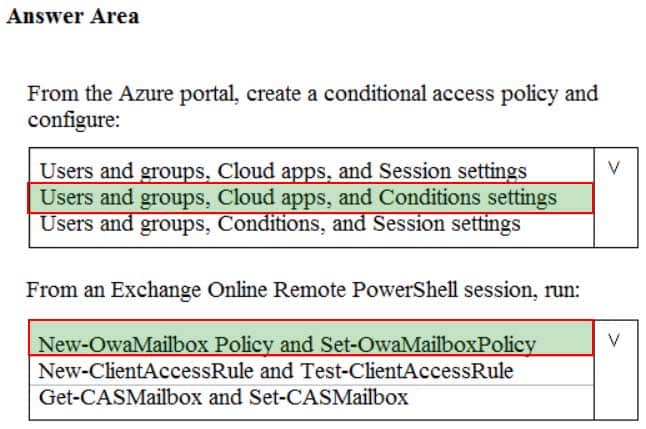
MS-500 Microsoft 365 Security Administration Part 05 Q15 115 Answer -
SIMULATION
You discover that Microsoft SharePoint content is shared with users from multiple domains.
You need to allow sharing invitations to be sent only to users in an email domain named contoso.com.
To complete this task, sign in to the Microsoft 365 portal.
- See explanation below.
Explanation:You need to configure the Sharing options in the SharePoint admin center.
1. Go to the SharePoint admin Center.
2. Navigate to Policies > Sharing.
3. In the External Sharing section, click on More external sharing settings.
4. Tick the Limit external sharing by domain checkbox.
5. Click the Add domains button.
6. Select the Allow only specific domains option and type in the domain contoso.com.
7. Click Save to save the changes. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant. You create a label named CompanyConfidential in Microsoft Azure Information Protection. You add CompanyConfidential to a global policy.
A user protects an email message by using CompanyConfidential and sends the label to several external recipients. The external recipients report that they cannot open the email message.
You need to ensure that the external recipients can open protected email messages sent to them.
You modify the encryption settings of the label.
Does that meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant. You create a label named CompanyConfidential in Microsoft Azure Information Protection. You add CompanyConfidential to a global policy.
A user protects an email message by using CompanyConfidential and sends the label to several external recipients. The external recipients report that they cannot open the email message.
You need to ensure that the external recipients can open protected email messages sent to them.
You modify the content expiration settings of the label.
Does that meet the goal?
- Yes
- No
-
HOTSPOT
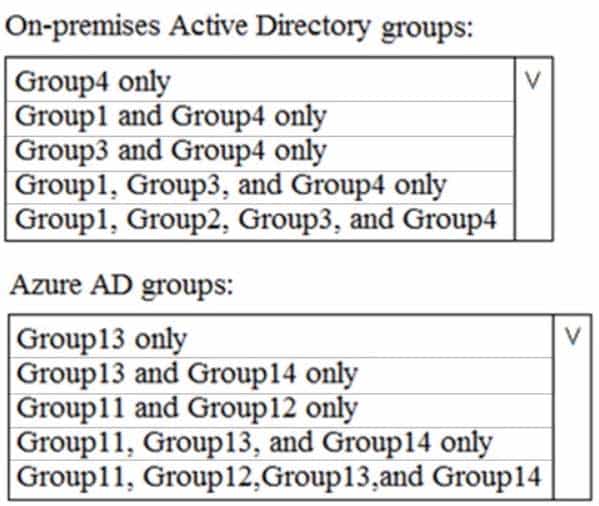
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the groups shown in the following table.
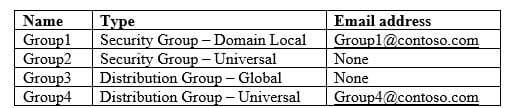
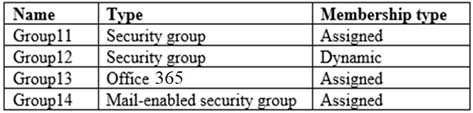
MS-500 Microsoft 365 Security Administration Part 05 Q19 116 The domain is synced to a Microsoft Azure Active Directory (Azure AD) tenant that contains the groups shown in the following table.
MS-500 Microsoft 365 Security Administration Part 05 Q19 117 You create an Azure Information Protection policy named Policy1.
You need to apply Policy1.
To which groups can you apply Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MS-500 Microsoft 365 Security Administration Part 05 Q19 118 Question 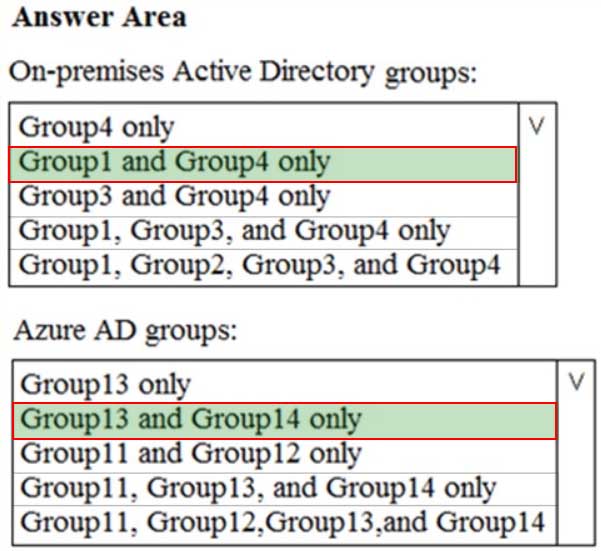
MS-500 Microsoft 365 Security Administration Part 05 Q19 118 Answer -
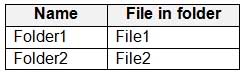
HOTSPOT
You have a Microsoft 365 subscription that contains a Microsoft SharePoint Online site named Site1. Site1 contains the folders shown in the following table.
MS-500 Microsoft 365 Security Administration Part 05 Q20 119 At 09:00, you create a Microsoft Cloud App Security policy named Policy1 as shown in the following exhibit.
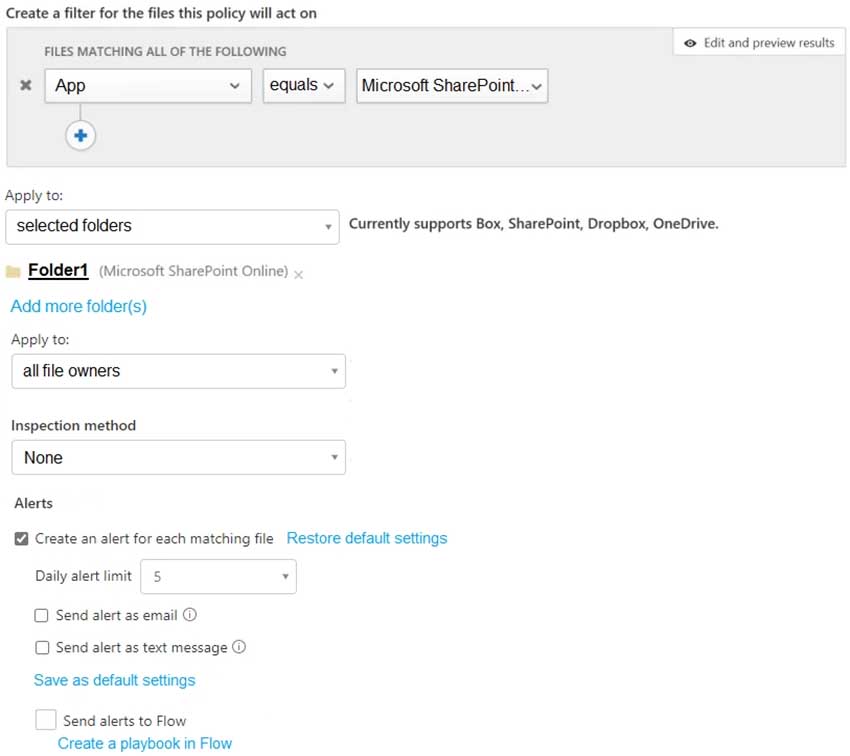
MS-500 Microsoft 365 Security Administration Part 05 Q20 120 After you create Policy1, you upload files to Site1 as shown in the following table.
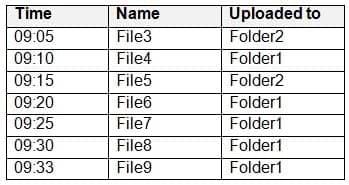
MS-500 Microsoft 365 Security Administration Part 05 Q20 121 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
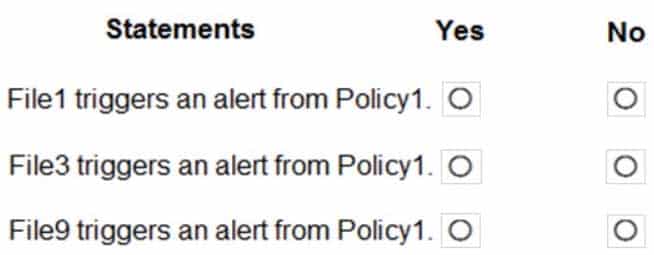
MS-500 Microsoft 365 Security Administration Part 05 Q20 122 Question 
MS-500 Microsoft 365 Security Administration Part 05 Q20 122 Answer