MS-900 : Microsoft 365 Fundamentals : Part 08
MS-900 : Microsoft 365 Fundamentals : Part 08
-
You need to ensure that the process by which users sign in to Microsoft 365 confirms the identity of the user.
Which feature should you use?
- mobile application management (MAM)
- Microsoft Defender for Office 365
- Multi-Factor Authentication (MFA)
- data loss prevention (DLP) policies
Explanation:
Multi-Factor Authentication (MFA) is a two-step identity verification system that can be used to authenticate users.
-
You are a Microsoft 365 administrator for a company.
You need to ensure that company documents are marked as confidential. You must prevent employees from sharing documents with people outside the company.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Validate outbound emails by using DomainKeys Identified Mail (DKIM)
- Create sensitive information types
- Configure Secure/Multipurpose Internet Mail Extensions (S/MIME) settings for Outlook
- Create a data-loss prevention policy
- Apply sensitivity labels to documents
Explanation:B: Sensitive information types can also be used with the Azure Information Protection scanner to classify and protect files on premises. Sensitive information types define how the automated process recognizes specific information types such as health service numbers and credit card numbers.
E: With sensitivity labels you can classify and help protect your sensitive content. Protection options include labels, watermarks, and encryption.
-
DRAG DROP
An organization plans to deploy Microsoft 365 in a hybrid scenario.
You need to provide a recommendation based on some common identity and access management scenarios. The solution must minimize costs.
Match each solution to its appropriate scenario. To answer, drag the appropriate solutions from the column on the left to the scenarios on the right. Each solution may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.

MS-900 Microsoft 365 Fundamentals Part 08 Q03 062 Question 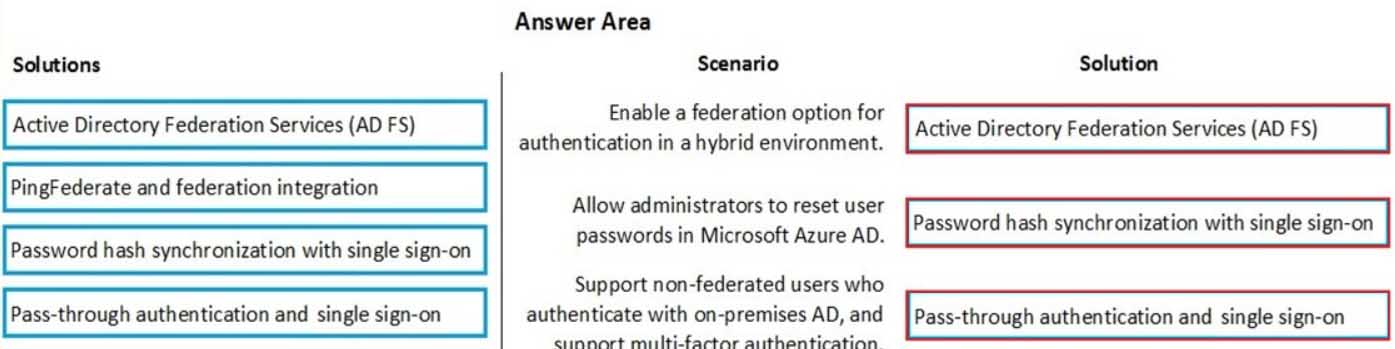
MS-900 Microsoft 365 Fundamentals Part 08 Q03 062 Answer -
You are the Microsoft 365 administrator for a company.
An employee requests personal data under General Data Protection Regulation (GDPR) guidelines.
You need to retrieve data for the employee.
What should you do?
- Create a data subject request case.
- Create a retention policy.
- Create a data-loss prevention policy.
- Create a GDPR assessment.
-
HOTSPOT
A company plans to deploy Microsoft Intune.
Which scenarios can you implement by using Intune? To answer, select the appropriate answer for the given scenarios.
NOTE: Each correct selection is worth one point.
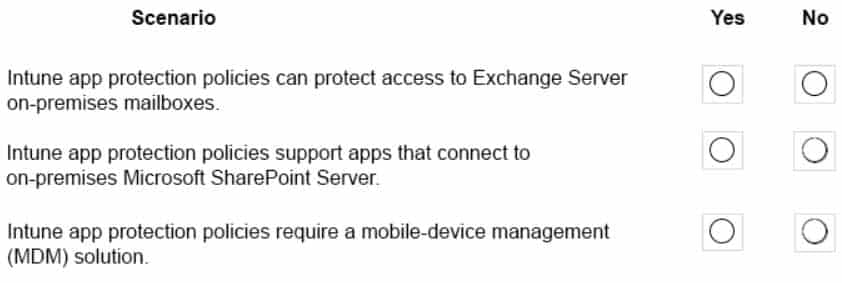
MS-900 Microsoft 365 Fundamentals Part 08 Q05 063 Question 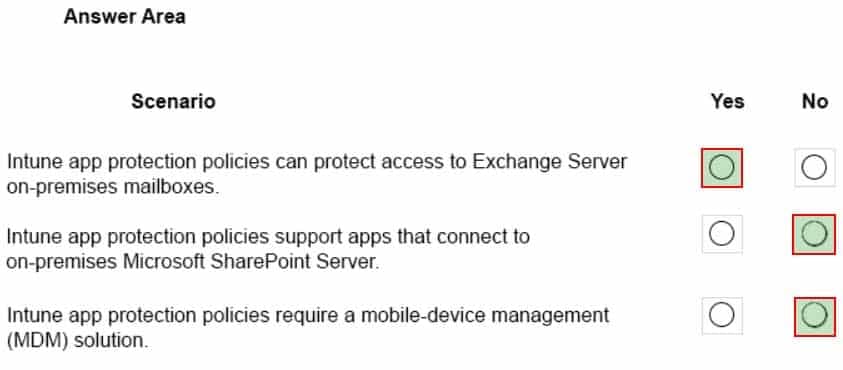
MS-900 Microsoft 365 Fundamentals Part 08 Q05 063 Answer Explanation:Box 1: Yes
You can protect access to Exchange on-premises mailboxes by creating Intune app protection policies for Outlook for iOS/iPadOS and Android enabled with hybrid Modern Authentication.Box 2: No
App protection policies are not supported for other apps that connect to on-premises Exchange or SharePoint services.Box 3: No
App protection policies can be configured for apps that run on devices that are not enrolled in any mobile device management solution: These devices are typically employee owned devices that aren’t managed or enrolled in Intune or other MDM solutions. -
DRAG DROP
You have a hybrid environment that includes Microsoft Azure AD. On-premises applications use Active Directory Domain Services (AD DS) for authentication.
You need to determine which authentication methods to use.
Match each feature to its authentication source. To answer, drag the appropriate authentication sources from the column on the left to the features on the right. Each authentication source may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.
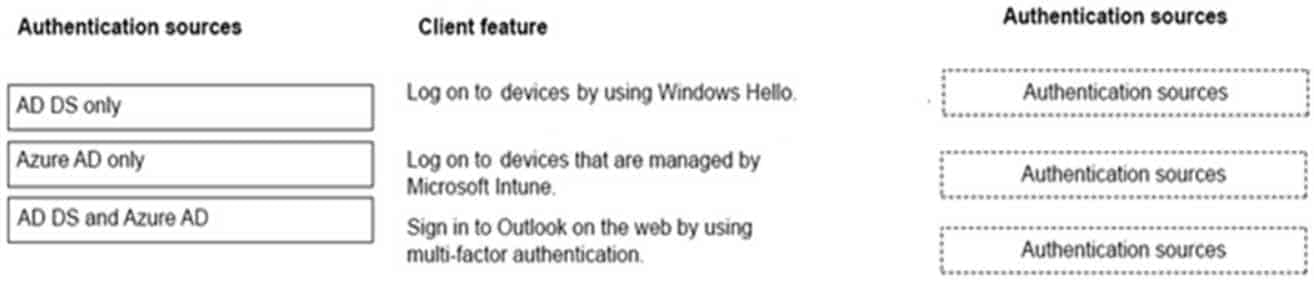
MS-900 Microsoft 365 Fundamentals Part 08 Q06 064 Question 
MS-900 Microsoft 365 Fundamentals Part 08 Q06 064 Answer -
A company has a Microsoft 365 subscription. Employees use personal devices to access company data in the cloud.
You need to restrict employees from copying data to personal OneDrive folders.
What should you use?
- Information Rights Management
- Microsoft Azure Security Center
- Office 365 Advanced Threat Protection
- Microsoft Endpoint Manager
-
You are the network administrator of a company.
The Microsoft 365 tenant contains sensitive information. Employees must verify their identities when they sign into Microsoft 365 by providing information in addition to their Azure AD password.
You need to select the tools that employees can use to verify their identities.
Which two tools should you select? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Customer Lockbox for Office 365
- Azure Security Center
- Windows Hello for Business
- Microsoft Authenticator
Explanation:
Two-step authentication can be implemented by using Windows Hello for Business or Microsoft Authenticator. -
You need to move videos to a Microsoft 365 tenant and ensure that the contents are automatically transcribed.
Which Microsoft 365 service should you use?
- Yammer
- Stream
- Flow
Explanation:Microsoft Stream is used for video services, and includes deep search within automatic audio transcription.
-
An organization uses Microsoft 365 Business to secure their data.
Many users install the organization’s data on their personal tablets and phones.
You need to protect the organization’s data stored on users’ devices.
Which three features support device security? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Remotely wiping company data
- Enabling Advanced Threat Protection for users
- Disabling the device remotely
- Automatically deleting files after 90 days of inactivity
- Requiring users to have a PIN on their device
Explanation:You can manage many of the Microsoft 365 Business security features in the admin center, which gives you a simplified way to turn these features on or off. In the admin center, you can do the following:
– Set application management settings for Android or iOS devices.
These settings include deleting files from an inactive device after a set period, encrypting work files, requiring that users set a PIN, and so on.
– Set application protection settings for Windows 10 devices.
These settings can be applied to company data on both company-owned, or personally owned devices.
– Set device protection settings for Windows 10 devices.
You can enable BitLocker encryption to help protect data in case a device is lost or stolen, and enable Windows Exploit Guard to provide advanced protection against ransomware.
– Remove company data from devices.
You can remotely wipe company data if a device is lost, stolen, or an employee leaves your company.
– Reset Windows 10 devices to their factory settings.
You can reset any Windows 10 devices that have device protection settings applied to them. -
This question requires that you evaluate the underlined text to determine if it is correct.
You use Microsoft Intune for device management. You must determine how many devices run each operating system.
You must launch Intune and navigate to the Mobile Apps blade.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- Device configuration
- Device compliance
- No change is needed
- Devices
-
HOTSPOT
A company has a Microsoft 365 E5 subscription. The company plans to use eDiscovery to meet legal discovery requirements.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
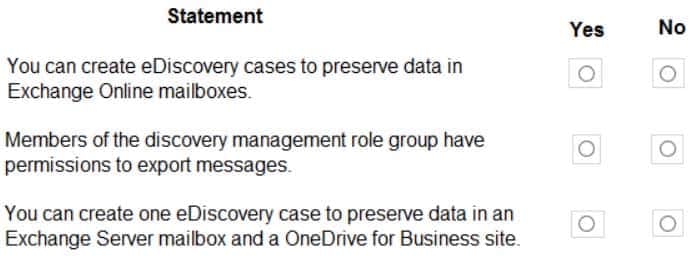
MS-900 Microsoft 365 Fundamentals Part 08 Q12 065 Question 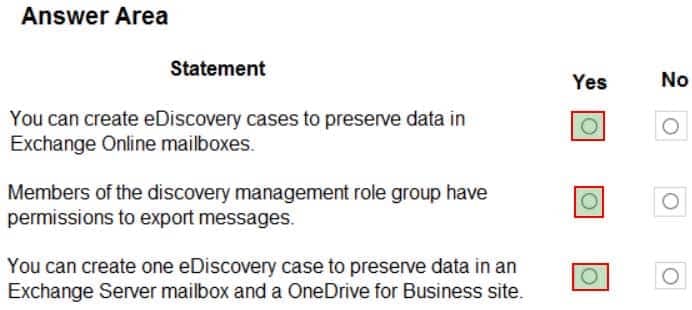
MS-900 Microsoft 365 Fundamentals Part 08 Q12 065 Answer -
You are the Microsoft 365 administrator for a company.
You need to ensure that users receive a warning message if they select links in emails that might be unsafe.
What should you do?
- Use Windows PowerShell to install the latest antimalware engine updates
- Enable Microsoft Office 365 Advanced Threat Protection
- Use the Microsoft Exchange Admin Center to configure a new spam-filter policy
- Use the Microsoft Exchange Admin Center to create a new antimalware policy
-
A business acquaintance from another company sends you a document that is encrypted by Azure Information Protection (AIP).
You are unable to open the document because the user account cannot be authenticated by the company’s Azure Active Directory.
You need to access the document.
What should you do?
- Implement Azure Rights Management (RMS) for individuals for the user account.
- Implement Information Rights Management (IRM) for the Office application.
- Upgrade your account to include AIP for Office 365.
-
A company deploys Microsoft Azure AD. You enable multi-factor authentication.
You need to inform users about the multi-factor authentication methods that they can use.
Which of the following methods is NOT a valid multi-factor authentication method in Microsoft 365?
- Receive an automated call on the desk phone that includes a verification code
- Insert a small card in to a desktop computer and provide a PIN code when prompted
- Receive a call on a mobile phone and select the pound sign (#) when prompted
- Receive an SMS text message that includes a verification code
-
DRAG DROP
Match each tool to its definition.
Instructions: To answer, drag the appropriate tool from the column on the left to its definition on the right. Each tool may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.

MS-900 Microsoft 365 Fundamentals Part 08 Q16 066 Question 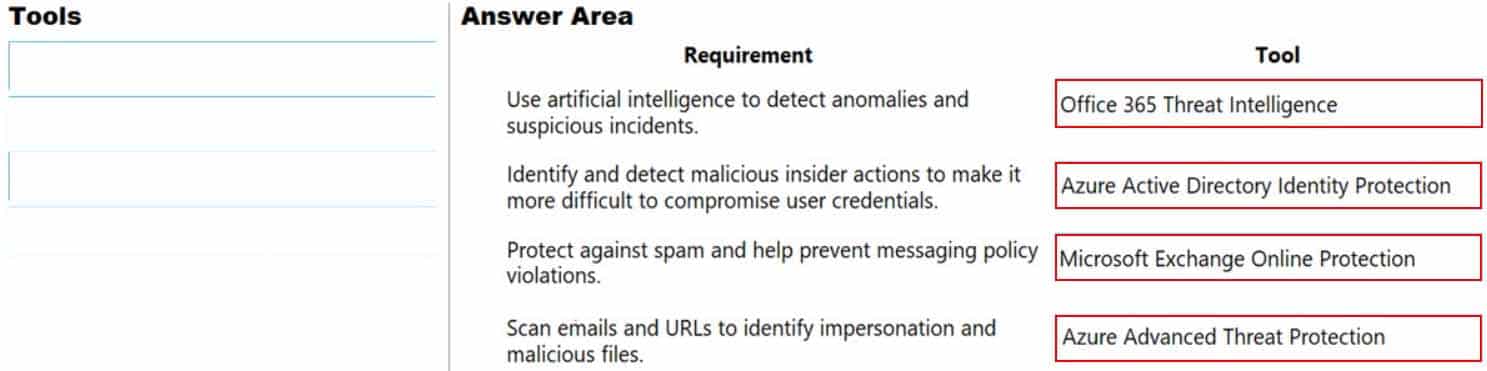
MS-900 Microsoft 365 Fundamentals Part 08 Q16 066 Answer -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
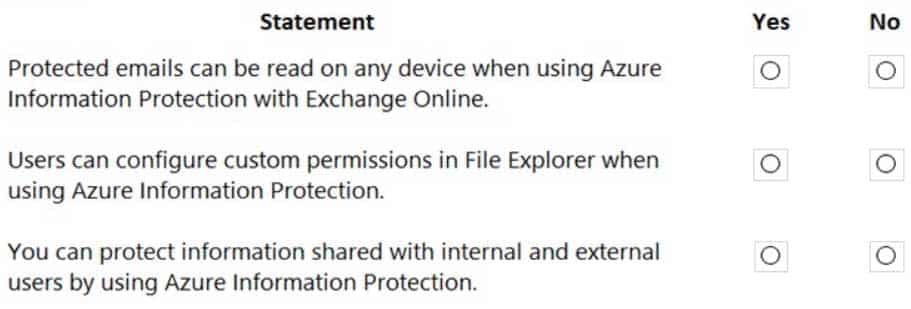
MS-900 Microsoft 365 Fundamentals Part 08 Q17 067 Question 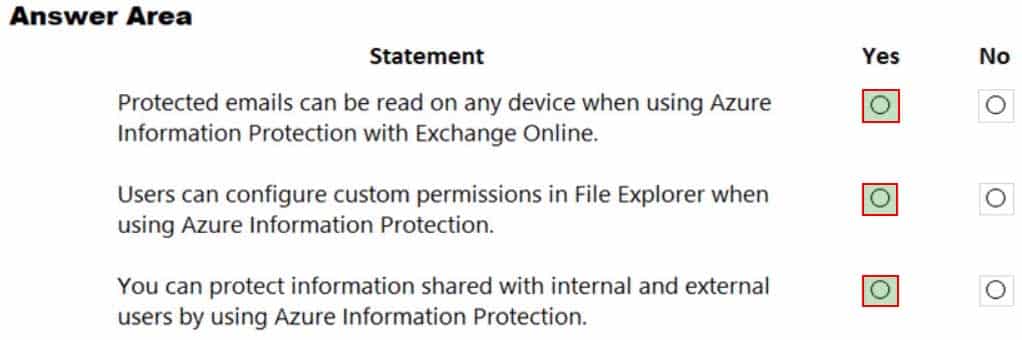
MS-900 Microsoft 365 Fundamentals Part 08 Q17 067 Answer -
HOTSPOT
You implement Compliance Manager.
You need to retrieve status information for a control task.
Which two options can you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
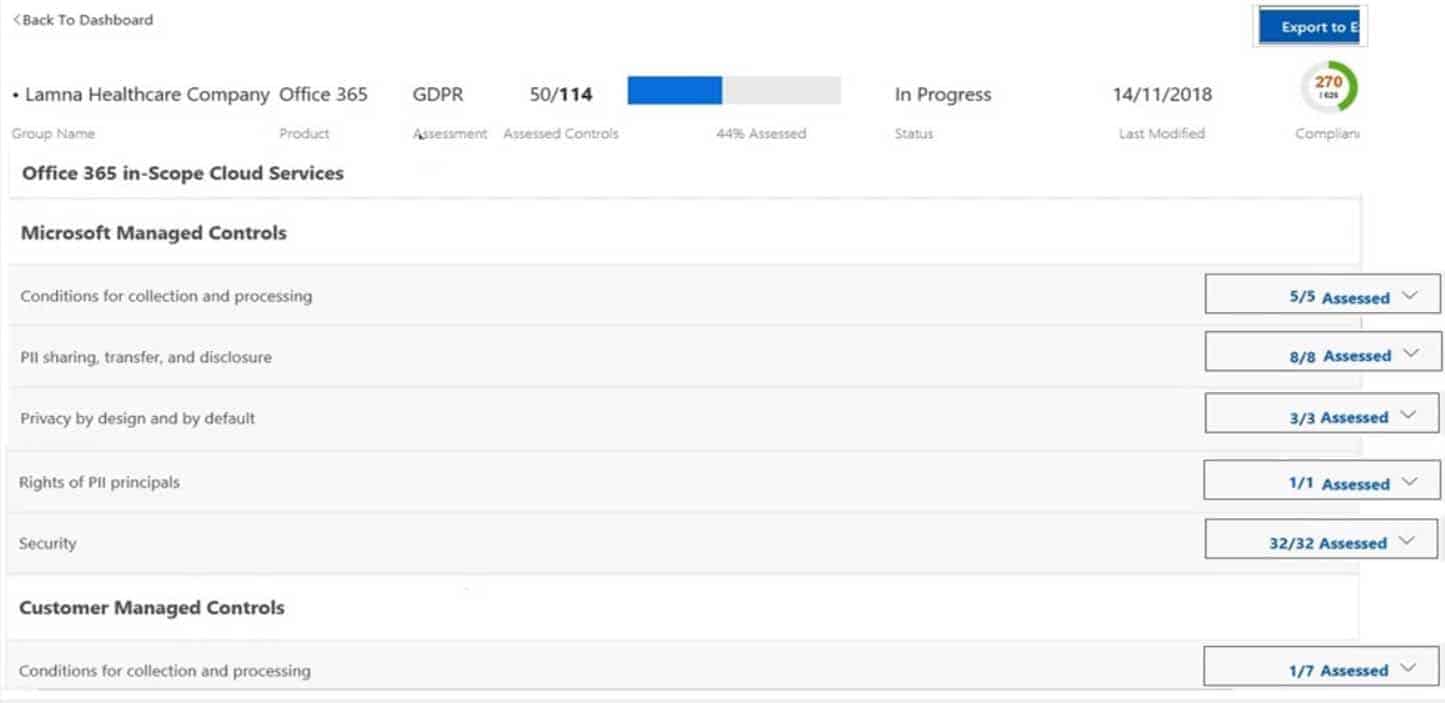
MS-900 Microsoft 365 Fundamentals Part 08 Q18 068 Question 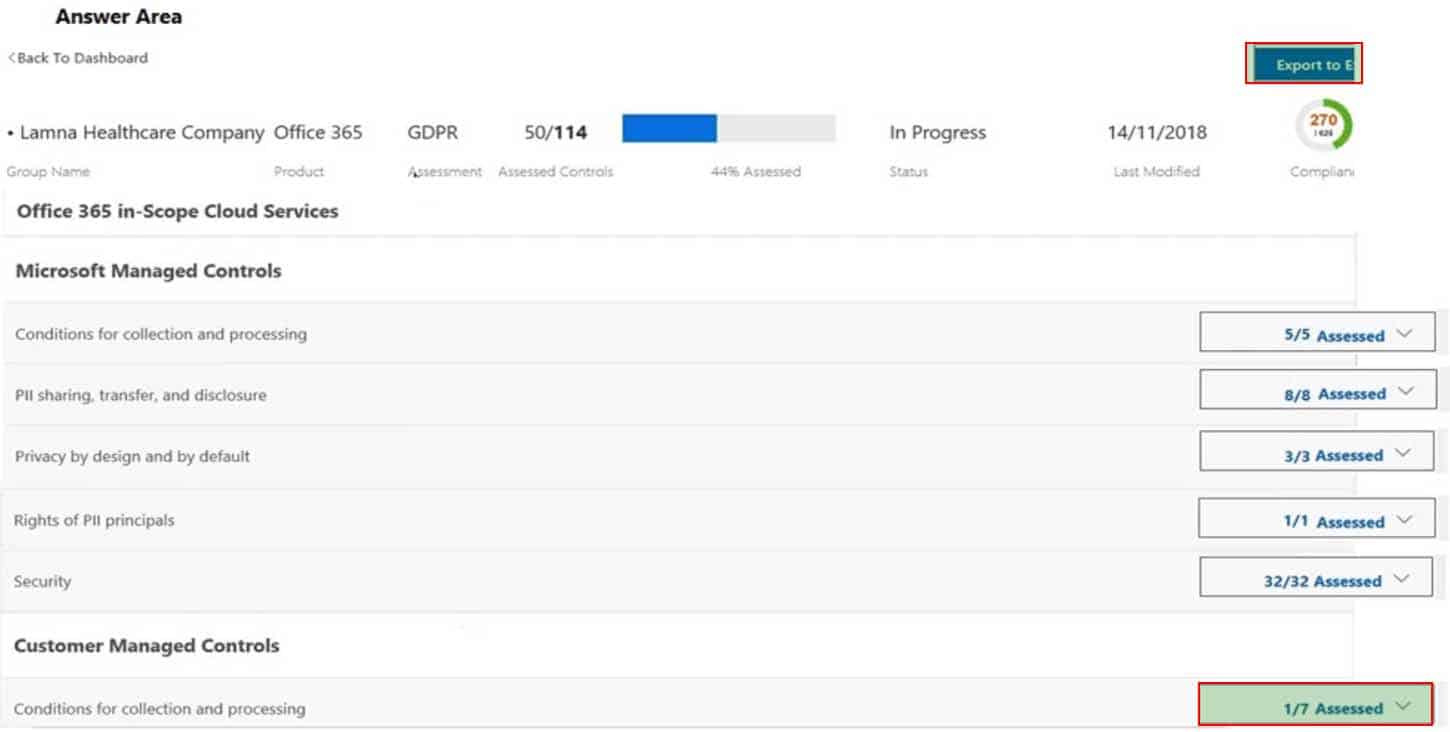
MS-900 Microsoft 365 Fundamentals Part 08 Q18 068 Answer -
You are a Microsoft 365 administrator for a company.
Several users report that they receive emails which have a PDF attachment. The PDF attachment launches malicious code.
You need to remove the message from inboxes and disable the PDF threat if an affected document is opened.
Which feature should you implement?
- Microsoft Exchange Admin Center block lists
- Sender Policy Framework
- Advanced Threat Protection anti-phishing
- zero-hour auto purge
- DKIM signed messages with mail flow rules
Explanation:In Microsoft 365 organizations with mailboxes in Exchange Online, zero-hour auto purge (ZAP) is an email protection feature that retroactively detects and neutralizes malicious phishing, spam, or malware messages that have already been delivered to Exchange Online mailboxes.
-
DRAG DROP
You are a Microsoft 365 administrator for a company.
A customer submits a data subject request (DSR) to delete customer information in compliance with General Data Protection Regulation (GDPR). You must place legal holds on related data whenever possible.
You need to respond to the request by searching for the customer’s data in various Microsoft 365 tools.
How should you search for the data? To answer, drag the appropriate search methods to the correct Microsoft 365 applications. Each search method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.

MS-900 Microsoft 365 Fundamentals Part 08 Q20 069 Question 
MS-900 Microsoft 365 Fundamentals Part 08 Q20 069 Answer