MS-900 : Microsoft 365 Fundamentals : Part 09
MS-900 : Microsoft 365 Fundamentals : Part 09
-
HOTSPOT
A company deploys Microsoft Intune.
An employee loses a Windows 10 device that contains corporate data.
You need to ensure that the corporate data on the device is secured as quickly as possible.
Which four options can you use? To answer, select the appropriate actions in the answer area.
NOTE: Each correct selection is worth one point.
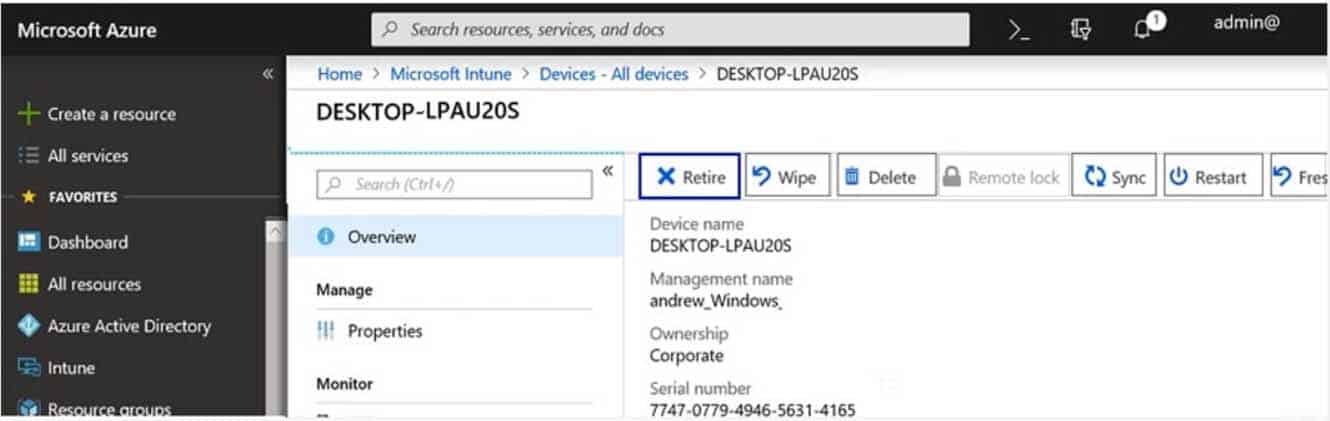
MS-900 Microsoft 365 Fundamentals Part 09 Q01 070 Question 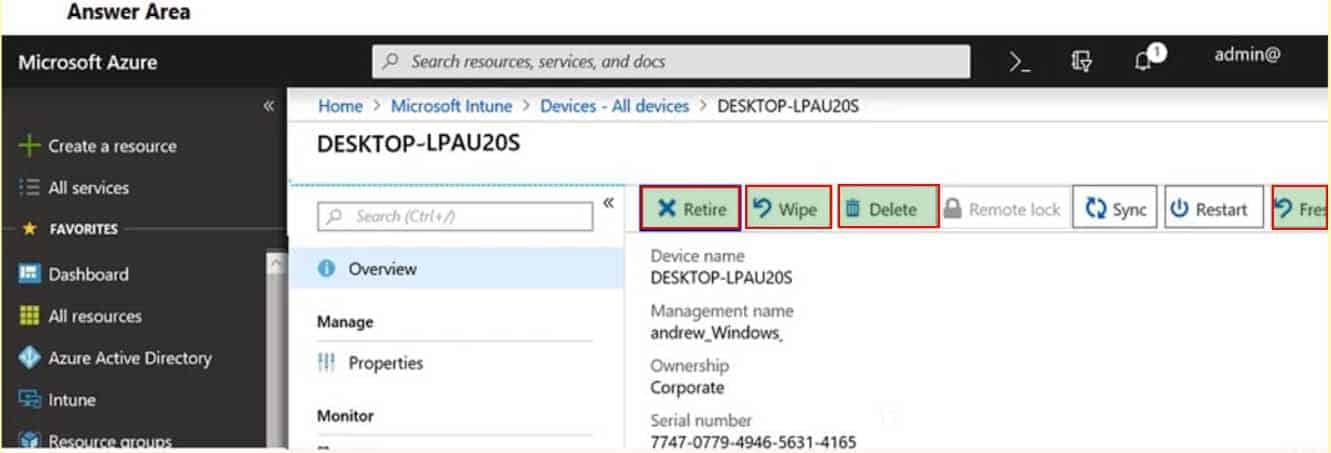
MS-900 Microsoft 365 Fundamentals Part 09 Q01 070 Answer -
You are the Microsoft 365 administrator for a company.
All staff must use Microsoft Outlook to access corporate email. When users access Outlook on mobile devices, they must use a PIN to open the application.
You need to implement a Microsoft Intune policy to enforce the security requirements.
Which policy should you use?
- device compliance
- device configuration
- app protection
- app configuration
-
HOTSPOT
You need to configure a data governance solution for your company. The solution must meet the following requirements:
– Classify documents
– Ensure that classifications are enforced
– Delete documents that are no longer usedWhich actions should you perform? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
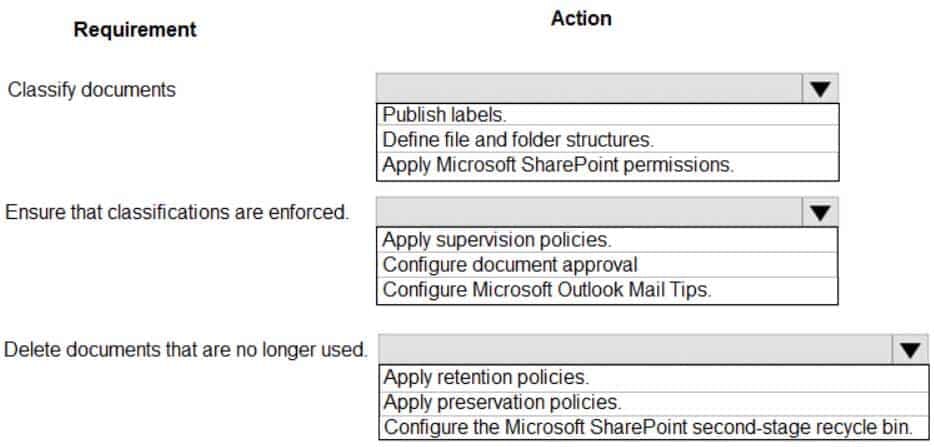
MS-900 Microsoft 365 Fundamentals Part 09 Q03 071 Question 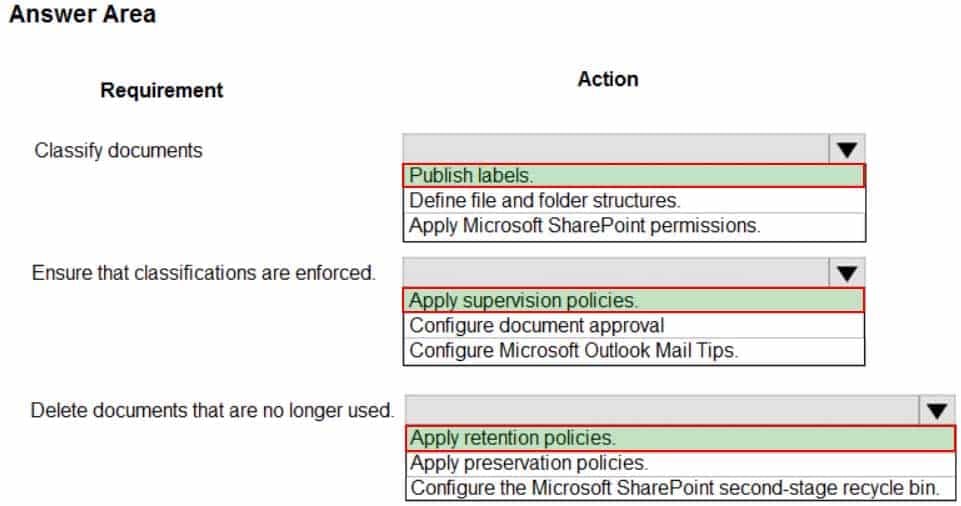
MS-900 Microsoft 365 Fundamentals Part 09 Q03 071 Answer -
DRAG DROP
You are the Microsoft 365 administrator for a company.
You need to identify available cloud security features.
Match each feature to the correct description. To answer, drag the appropriate feature from the column on the left to its description on the right. Each feature may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.
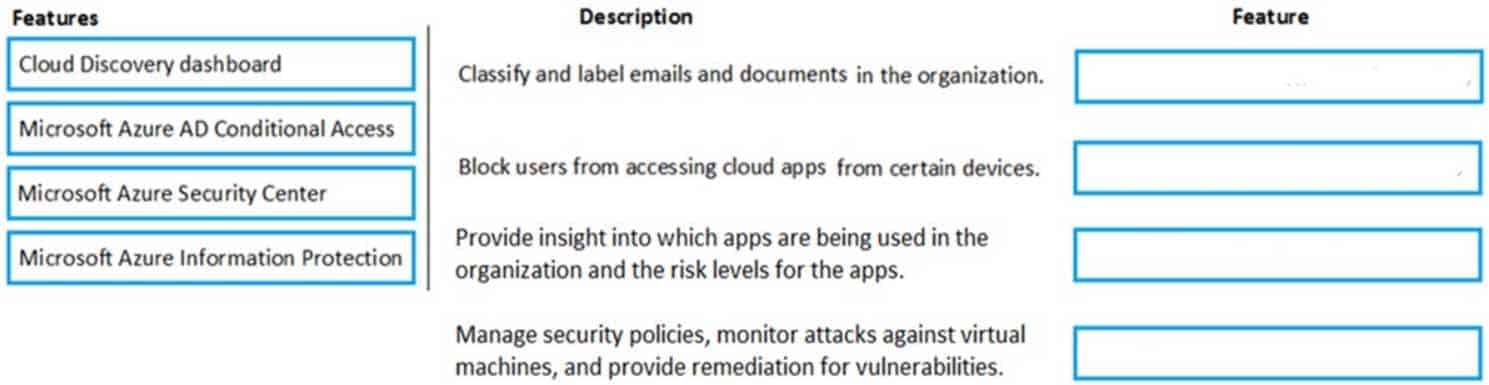
MS-900 Microsoft 365 Fundamentals Part 09 Q04 072 Question 
MS-900 Microsoft 365 Fundamentals Part 09 Q04 072 Answer -
A company deploys Exchange Online and SharePoint Online.
You must audit and assessment reports for the Microsoft 365 cloud services that the company uses.
You need to provide the required documents.
Which Microsoft site should you use to obtain this information?
- Compliance Manager
- Service Trust Portal
- Office 365 Security and Compliance Center
- Azure portal
-
HOTSPOT
A company uses Microsoft 365 Business to address its compliance needs. A customer requests a complete disclosure of all personal data that relates to them.
You need to create a new data subject request (DSR) case and ensure that compliance managers can view all DSR case findings.
In which two areas must you perform actions? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MS-900 Microsoft 365 Fundamentals Part 09 Q06 073 Question 
MS-900 Microsoft 365 Fundamentals Part 09 Q06 073 Answer -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
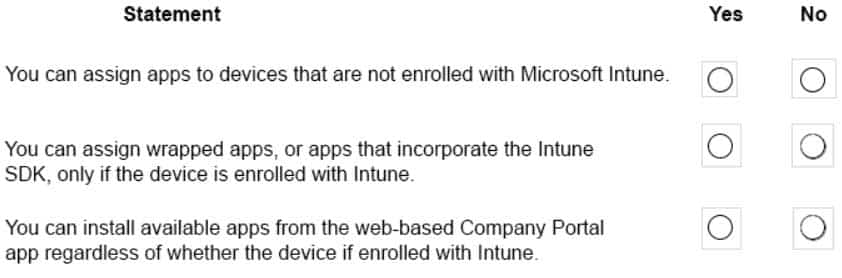
MS-900 Microsoft 365 Fundamentals Part 09 Q07 074 Question 
MS-900 Microsoft 365 Fundamentals Part 09 Q07 074 Answer -
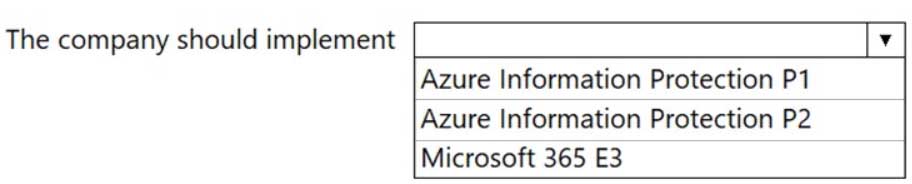
HOTSPOT
A company needs to protect documents and emails by automatically applying classifications and labels. You must minimize costs.
What should the company implement? To answer, select the appropriate option in the answer area.
MS-900 Microsoft 365 Fundamentals Part 09 Q08 075 Question 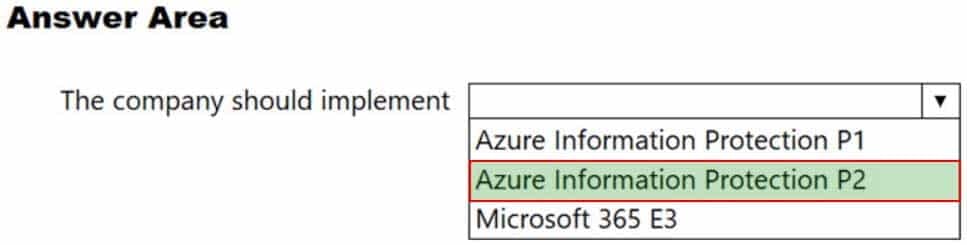
MS-900 Microsoft 365 Fundamentals Part 09 Q08 075 Answer -
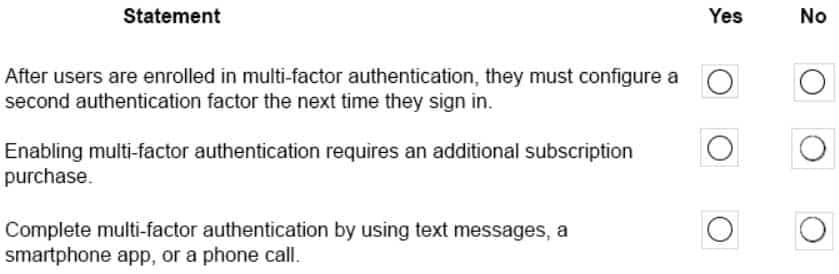
HOTSPOT
An organization has a Microsoft 365 subscription. You plan to implement multi-factor authentication.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
MS-900 Microsoft 365 Fundamentals Part 09 Q09 076 Question 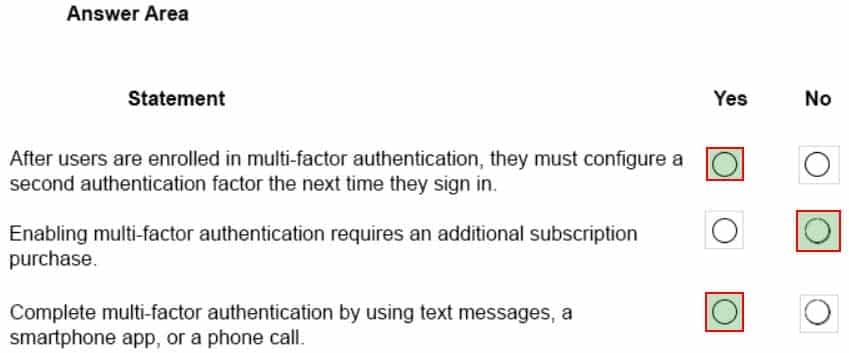
MS-900 Microsoft 365 Fundamentals Part 09 Q09 076 Answer -
DRAG DROP
A company has Microsoft 365 and uses Microsoft Endpoint Manager.
You need to identify the endpoint management tool associated with each action.
Which tool should you identify for each action? To answer, drag the appropriate tools to the correct actions. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

MS-900 Microsoft 365 Fundamentals Part 09 Q10 077 Question 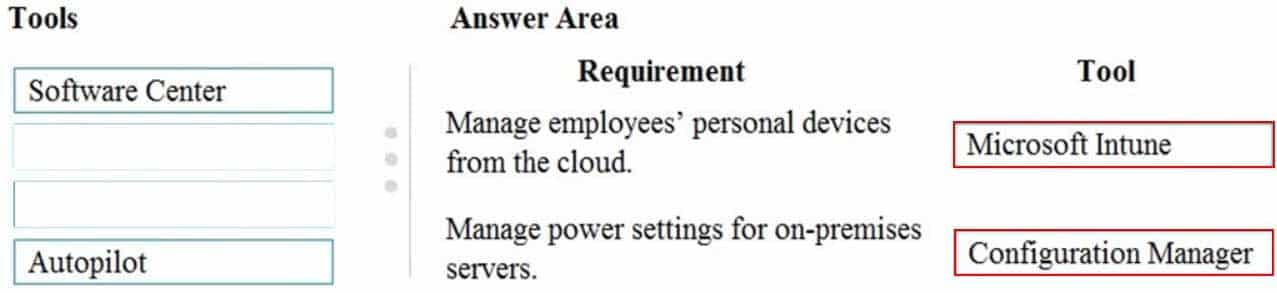
MS-900 Microsoft 365 Fundamentals Part 09 Q10 077 Answer -
A company is planning to use Microsoft 365 Defender.
The company needs to protect Windows 10 client computers from malicious viruses. The company also needs to identify unauthorized cloud apps that are used by end users.
You need to identify the Microsoft 365 Defender solutions that meet the requirements.
Which two solutions should you choose? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Microsoft Defender for Identity
- Microsoft Defender for Endpoint
- Microsoft Defender for Office 365
- Microsoft Cloud App Security
-
A company has Microsoft 365.
The company needs to secure their environment. They start by identifying the highest risks to security according to Microsoft.
You need to identify the security changes that are recommended by Microsoft 365.
Which tool should you choose?
- Microsoft Intune
- Microsoft Secure Score
- Azure Information Protection scanner
- Advanced Threat Analytics
- Microsoft 365 compliance center
-
DRAG DROP
A company plans to deploy a compliance solution in Microsoft 365.
Match each compliance solution to its description. To answer, drag the appropriate compliance solution from the column on the left to its description on the right. Each compliance solution may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.

MS-900 Microsoft 365 Fundamentals Part 09 Q13 078 Question 
MS-900 Microsoft 365 Fundamentals Part 09 Q13 078 Answer -
DRAG DROP
A company deploys Microsoft 365.
You need to identify the appropriate cloud service for each requirement.
Which cloud service should you choose for each requirement? To answer, drag the appropriate cloud services to the correct requirements. Each cloud service may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

MS-900 Microsoft 365 Fundamentals Part 09 Q14 079 Question 
MS-900 Microsoft 365 Fundamentals Part 09 Q14 079 Answer -
A company uses Microsoft 365.
The company wants users to be prompted for additional verification when they access a federated third-party application. However, users must not be prompted for additional verification when they access Microsoft Outlook.
You need to identify a solution that meets the requirements.
Which solution should you choose?
- Conditional Access
- Multi-factor authentication (MFA)
- Active Directory Federation Services (AD FS)
- Self-service password reset (SSPR)
-
A company plans to migrate to Microsoft 365.
You need to advise the company about how Microsoft provides protection in a multitenancy environment.
What are three ways that Microsoft provides protection? Each correct answer presents part of the solution. (Choose three.)
NOTE: Each correct selection is worth one point.
- Customer content at rest is encrypted on the server by using BitLocker.
- Microsoft Azure AD provides authorization and role-based access control at the tenant layer.
- Customer content at rest is encrypted on the server by using transport-layer security (TLS).
- Microsoft Azure AD provides authorization and role-based access control at the transport layer.
- Mailbox databases in Microsoft Exchange Online contain only mailboxes from a single tenant.
- Mailbox databases in Microsoft Exchange Online contain mailboxes from multiple tenants.
-
You are the Microsoft 365 administrator for a company.
Your company plans to open a new office in the United Kingdom.
You need to provide penetration test and security assessment reports for the new office.
Where can you locate the required reports?
- Data Governance page of the Security and Compliance portal
- Compliance Manager page of the Services Trust portal
- Data Loss Prevention page of the Security and Compliance portal
- Regional Compliance page of the Services Trust portal
-
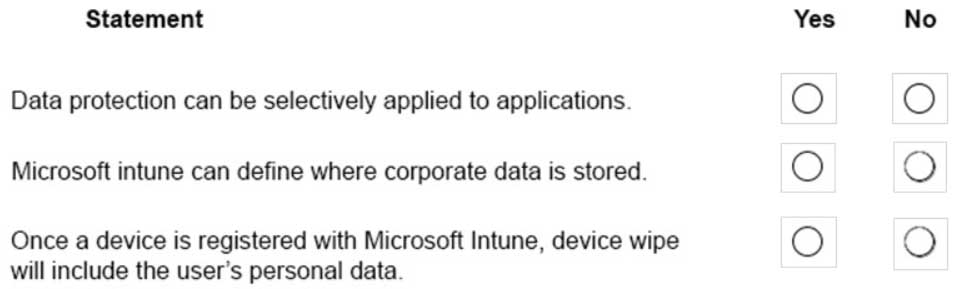
HOTSPOT
An organization plans to deploy Microsoft Intune.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
MS-900 Microsoft 365 Fundamentals Part 09 Q18 080 Question 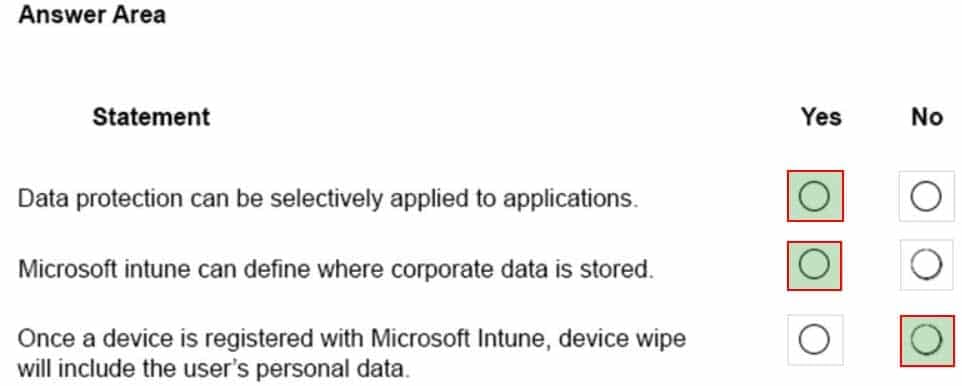
MS-900 Microsoft 365 Fundamentals Part 09 Q18 080 Answer -
You are the Microsoft Office 365 administrator for a company.
You need to perform security and compliance reviews before new updates are distributed to the entire company.
What should you implement?
- standard releases
- Microsoft 365 Enterprise Test Lab
- targeted releases
- FastTrack
-
DRAG DROP
A company purchases Microsoft 365 E5.
You need to determine which security features you should implement.
Which features should you implement? To answer, drag the appropriate features to the correct scenarios. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

MS-900 Microsoft 365 Fundamentals Part 09 Q20 081 Question 
MS-900 Microsoft 365 Fundamentals Part 09 Q20 081 Answer