MS-900 : Microsoft 365 Fundamentals : Part 10
MS-900 : Microsoft 365 Fundamentals : Part 10
-
A company has a Microsoft 365 subscription that includes Office apps.
A user has identified a new issue while working with an app. When the user attempts to create a support request, the following message displays:

MS-900 Microsoft 365 Fundamentals Part 10 Q01 082 You need to determine the cause of the error message.
What is the cause?
- The user account is disabled.
- The user does not have a license assigned for the app.
- The user account is not a member of the global admin role.
- The company does not have Premier support.
-
Your company purchases Microsoft 365 E3 and Azure AD P2 licenses.
You need to provide identity protection against login attempts by unauthorized users.
What should you implement?
- Azure AD Identity Protection
- Azure AD Privileged Identity Management
- Azure Information Protection
- Azure Identity and Access Management
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
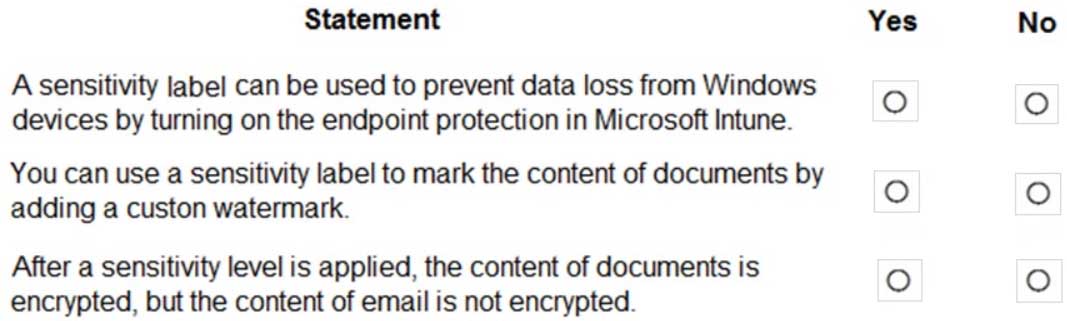
MS-900 Microsoft 365 Fundamentals Part 10 Q03 083 Question 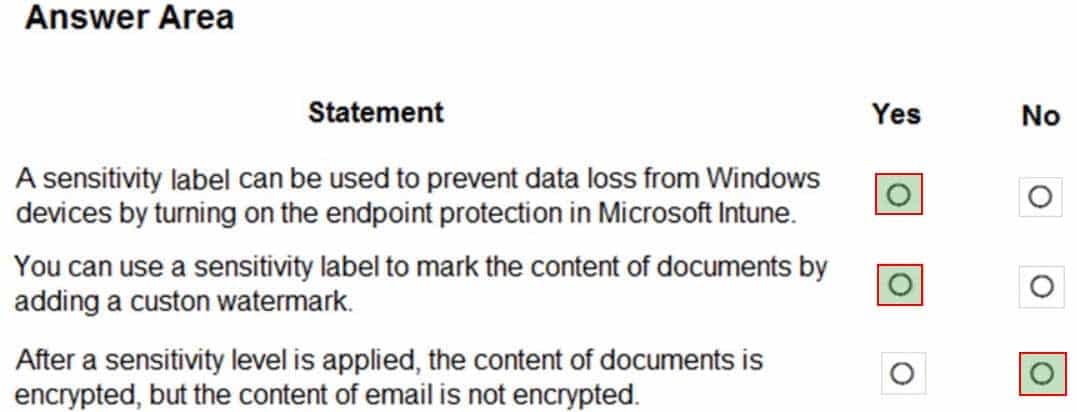
MS-900 Microsoft 365 Fundamentals Part 10 Q03 083 Answer -
You are a Microsoft 365 administrator for a company. Employees use Microsoft Office 365 ProPlus to create documents.
You need to implement document classification and protection by using Microsoft Azure Information Protection.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Add an Azure subscription to your Microsoft 365 tenant
- Install the Azure Information Protection client
- Create a custom Azure Information Protection policy with the Confidential label
- Enable the default Azure Information Protection policy
- Install the Rights Management Service client
-
DRAG DROP
Your company has a Microsoft 365 subscription.
You need to implement security policies to ensure that sensitive data is protected.
Which tools should you use? To answer, drag the appropriate tools to the correct scenarios. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
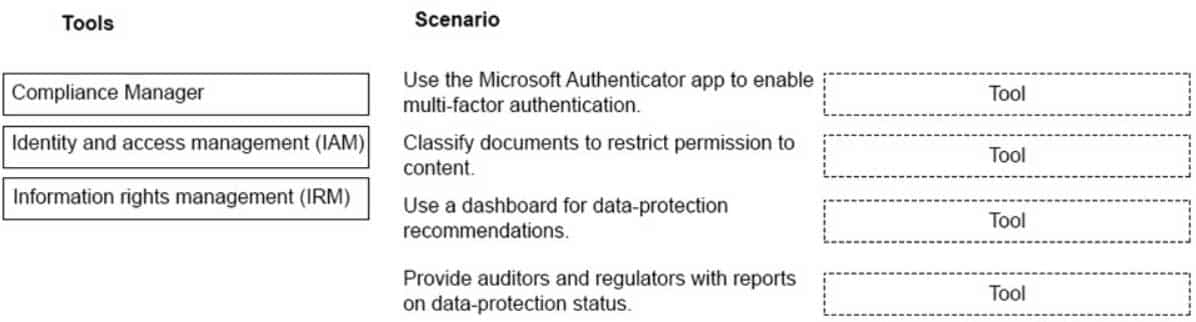
MS-900 Microsoft 365 Fundamentals Part 10 Q05 084 Question 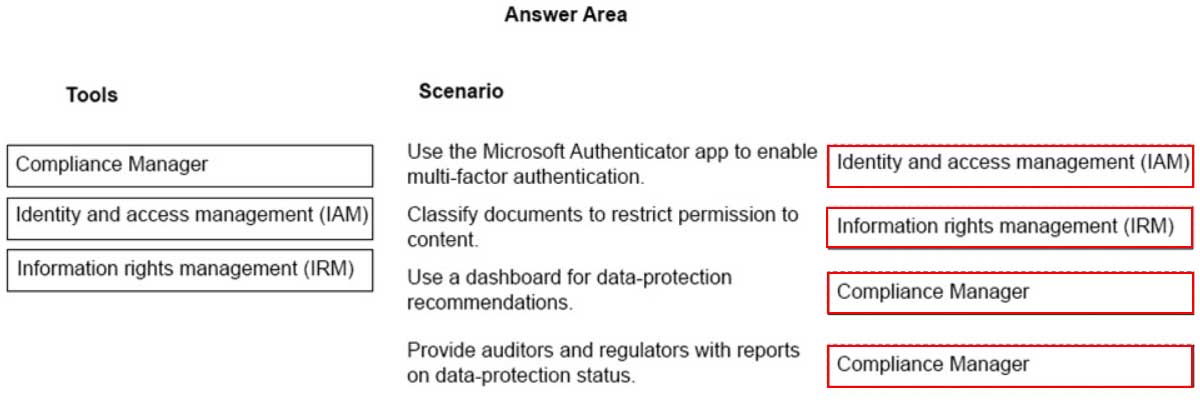
MS-900 Microsoft 365 Fundamentals Part 10 Q05 084 Answer -
HOTSPOT
You are planning a Microsoft Azure AD solution for a company.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-900 Microsoft 365 Fundamentals Part 10 Q06 085 Question 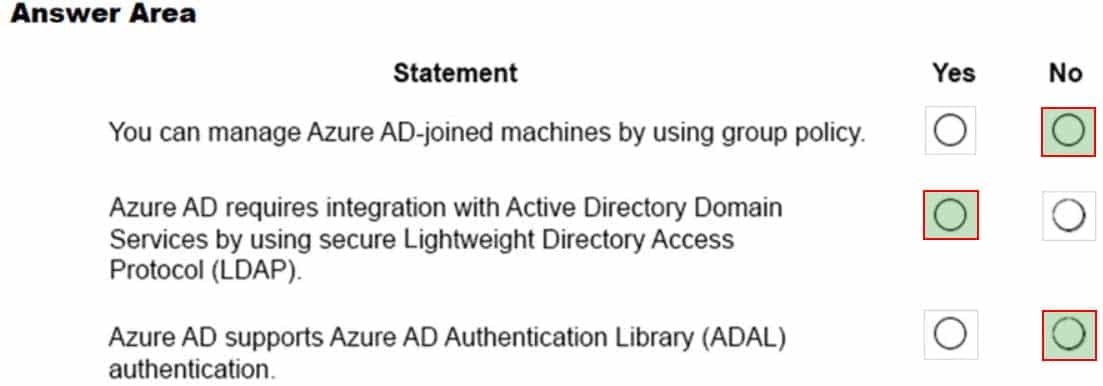
MS-900 Microsoft 365 Fundamentals Part 10 Q06 085 Answer -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
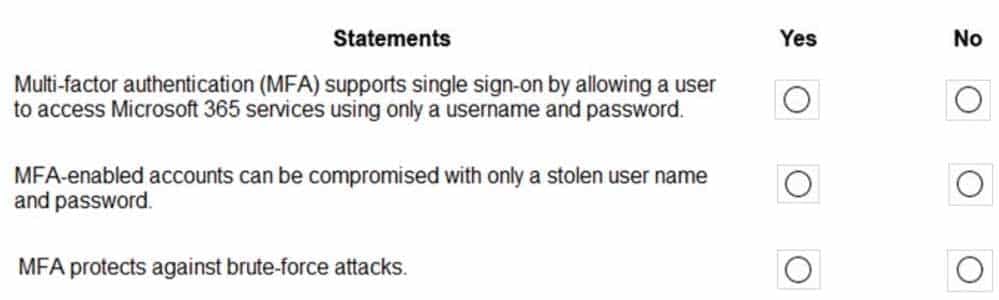
MS-900 Microsoft 365 Fundamentals Part 10 Q07 086 Question 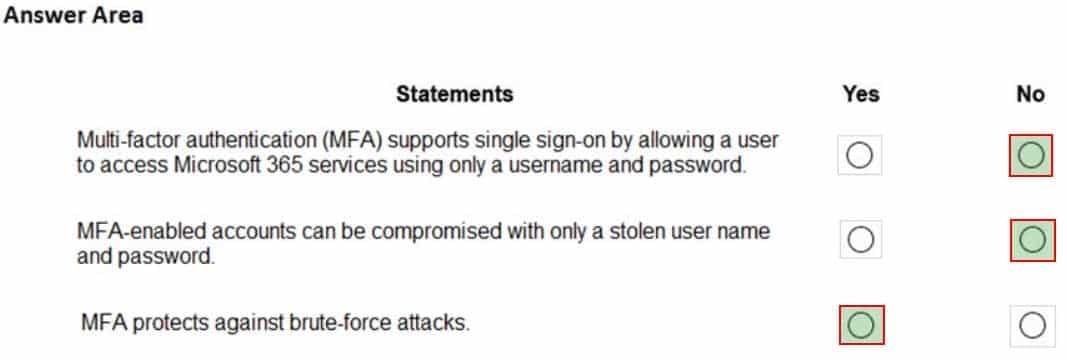
MS-900 Microsoft 365 Fundamentals Part 10 Q07 086 Answer -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
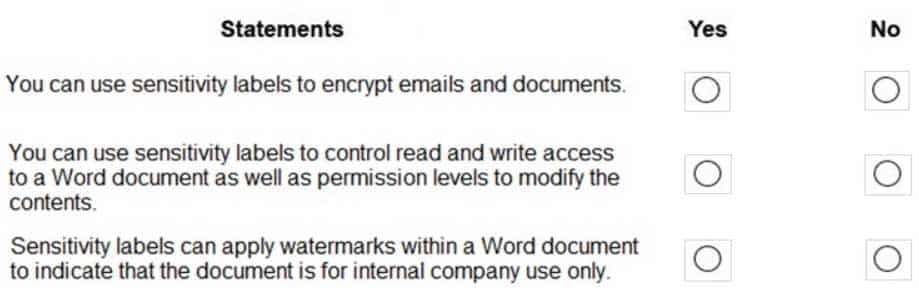
MS-900 Microsoft 365 Fundamentals Part 10 Q08 087 Question 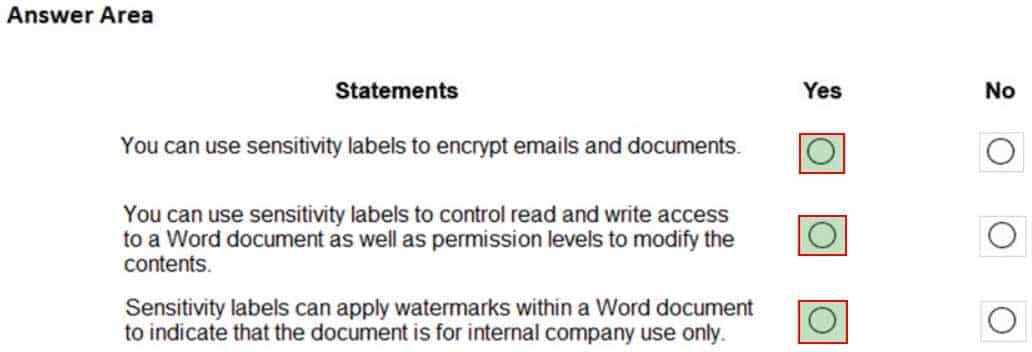
MS-900 Microsoft 365 Fundamentals Part 10 Q08 087 Answer -
A company uses Microsoft 365.
The company needs to label emails and documents that contain confidential text.
You need to identify a feature that meets this requirement.
Which feature should you choose?
- Customer Key
- Sensitivity label
- Microsoft Outlook rule
- Retention label
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MS-900 Microsoft 365 Fundamentals Part 10 Q10 088 Question 
MS-900 Microsoft 365 Fundamentals Part 10 Q10 088 Answer -
DRAG DROP
A company uses Microsoft 365.
You need to identify the appropriate report for each definition.
Which report should you choose for each definition? To answer, drag the appropriate reports to the correct definitions. Each report may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
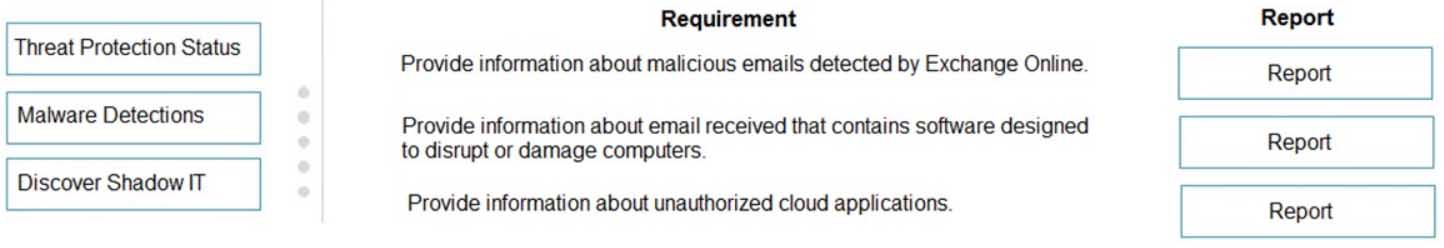
MS-900 Microsoft 365 Fundamentals Part 10 Q11 089 Question 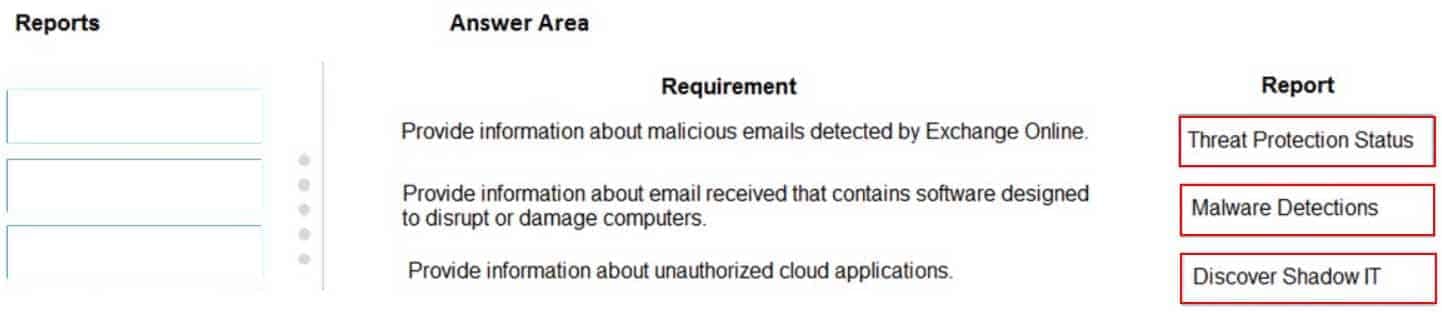
MS-900 Microsoft 365 Fundamentals Part 10 Q11 089 Answer -
A company deploys Microsoft Azure AD. You run the Identity Secure Score report. The report displays five security items.
Which three security items on the report have the most impact on the score? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Enable policy to block legacy authentication.
- Enable user risk policy.
- Require multi-factor authentication for all users.
- Delete/block accounts not used in last 30 days.
- Do not expire passwords.
-
A company deploys Microsoft Azure AD. You enable multi-factor authentication.
You need to inform users about the multi-factor authentication methods that they can use.
Which of the following methods is NOT a valid multi-factor authentication method in Microsoft 365?
- Receive an automated call on the desk phone that includes a verification code.
- Use the Microsoft Authenticator mobile application to receive a notification and authenticate.
- Receive a call on a phone.
- Enter a Windows 10 PIN code when prompted.
-
You deploy Enterprise Mobility + Security E5 and assign Microsoft 365 licenses to all employees.
Employees must not be able to share documents or forward emails that contain sensitive information outside the company.
You need to enforce the file sharing restrictions.
What should you do?
- Use Microsoft Azure Information Protection to define a label. Associate the label with an Azure Rights Management template that prevents the sharing of files or emails that are marked with the label.
- Create a Microsoft SharePoint Online content type named Sensitivity. Apply the content type to other content types in Microsoft 365. Create a Microsoft Azure Rights Management template that prevents the sharing of any content where the Sensitivity column value is set to Sensitive.
- Use Microsoft Azure Information Rights Protection to define a label. Associate the label with an Active Directory Rights Management template that prevents the sharing of files or emails that are marked with the label.
- Create a label named Sensitive. Apply a Data Layer Protection policy that notifies users when their document contains personally identifiable information (PII).
-
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth pone point.
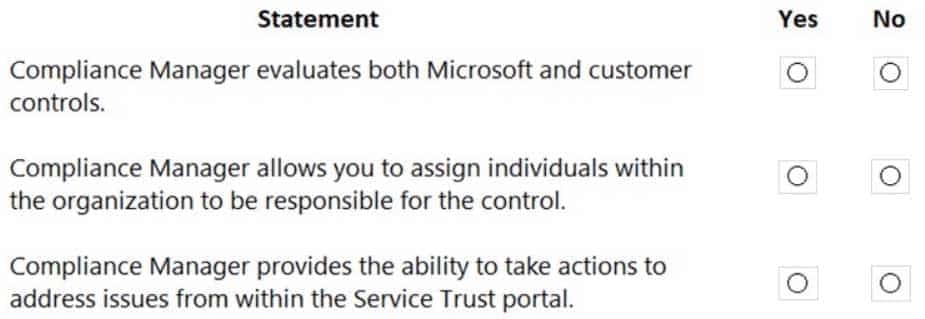
MS-900 Microsoft 365 Fundamentals Part 10 Q15 090 Question 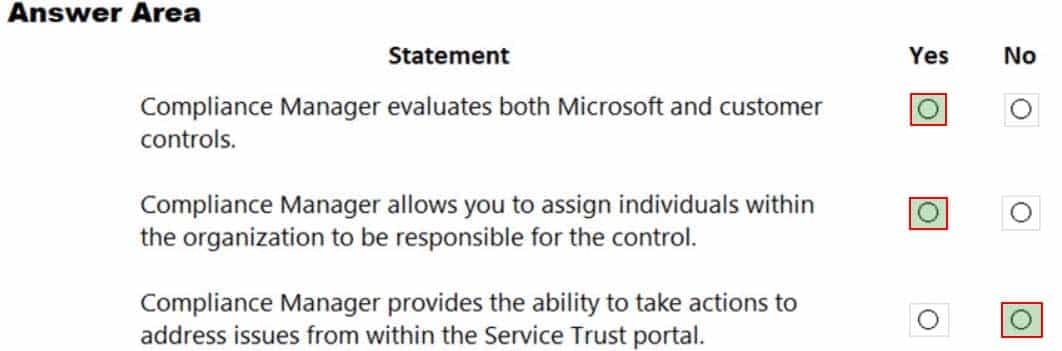
MS-900 Microsoft 365 Fundamentals Part 10 Q15 090 Answer -
HOTSPOT
You are a Microsoft 365 administrator for a company. The company implements federated authentication.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
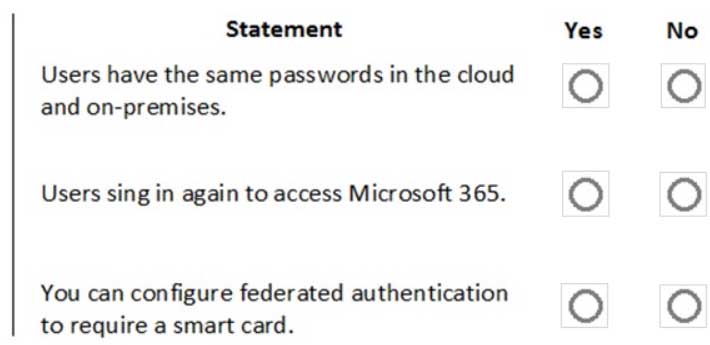
MS-900 Microsoft 365 Fundamentals Part 10 Q16 091 Question 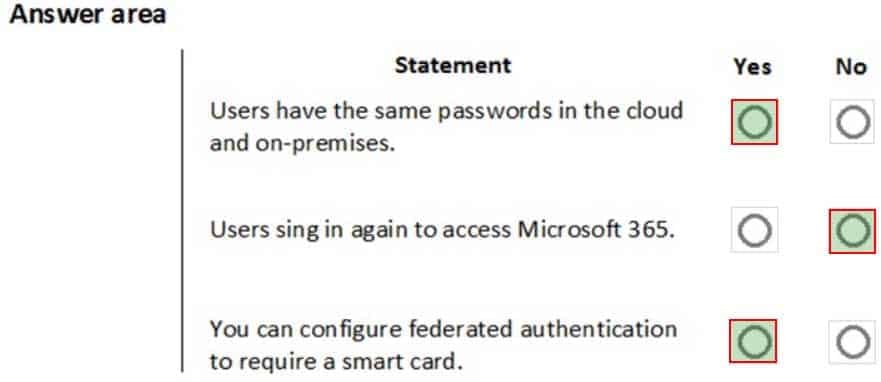
MS-900 Microsoft 365 Fundamentals Part 10 Q16 091 Answer -
DRAG DROP
A company plans to migrate to a hybrid cloud infrastructure.
You need to determine where to manage the environment after the migration is complete.
Match each item to the location where it will be managed. To answer, drag the appropriate item from the column on the left to its location on the right. Each item may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.
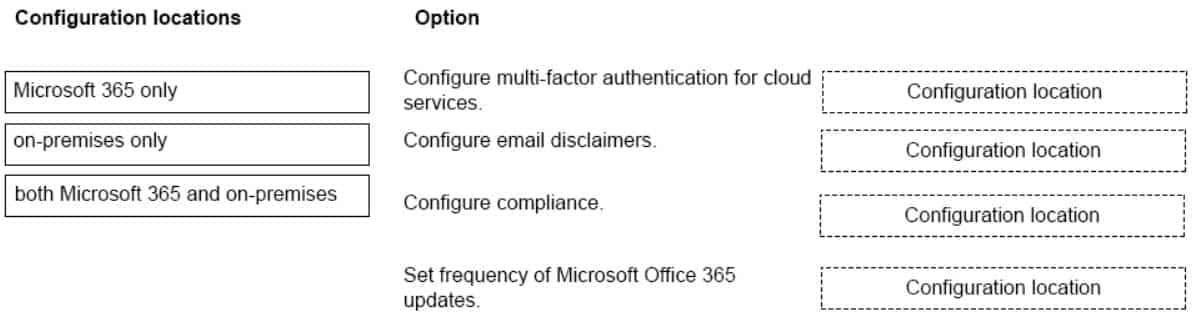
MS-900 Microsoft 365 Fundamentals Part 10 Q17 092 Question 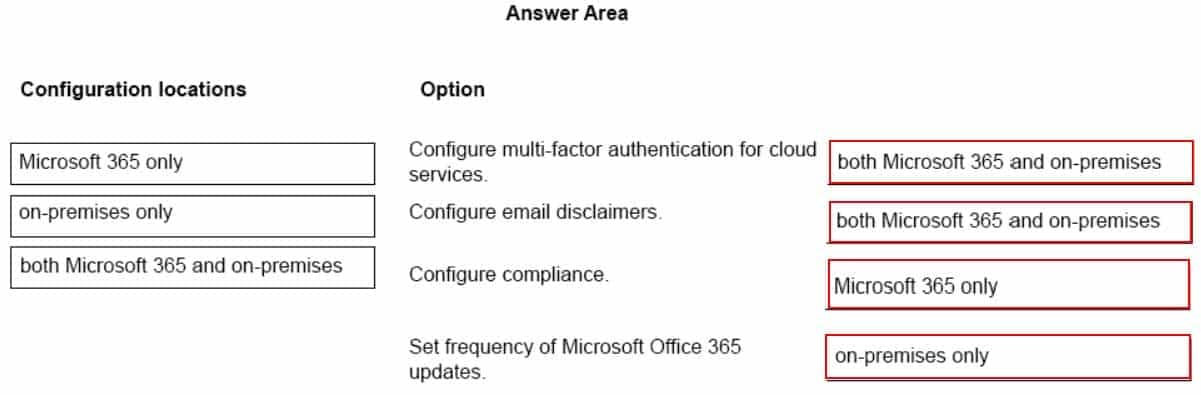
MS-900 Microsoft 365 Fundamentals Part 10 Q17 092 Answer -
A company deploys Microsoft 365.
The company needs to deploy a solution that meets the following requirements:
– allows access to Microsoft 365 only from corporate networks
– allows access to Microsoft 365 only from corporate-owned devices
– requires additional verification during authenticationYou need to identify a solution that meets the requirements.
What should you select?
- Multi-factor authentication
- Conditional Access
- Azure Active Directory hybrid identity
- Self-service password reset
-
DRAG DROP
Match each authentication identity to its scenario. To answer, drag the appropriate authentication identity from the column on the left to its scenario on the right. Each authentication identity may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
MS-900 Microsoft 365 Fundamentals Part 10 Q19 093 Question 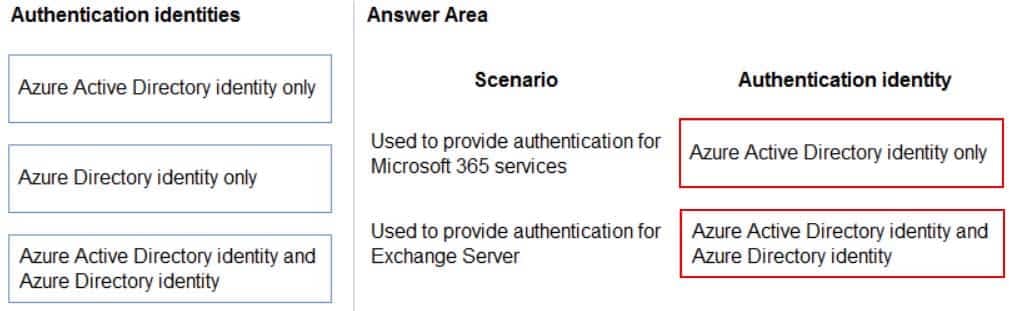
MS-900 Microsoft 365 Fundamentals Part 10 Q19 093 Answer -
After experiencing security breaches with on-premises servers, a company is considering migrating to Microsoft 365 for their security solutions.
What are three security-related benefits of moving to Microsoft 365? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Microsoft employs a full-time team of penetration testers to identify vulnerabilities.
- Microsoft 365 prevents all attackers from gaining access to company data.
- Microsoft simplifies infrastructure management to help detect and respond to threats.
- Microsoft 365 monitors all customers for threats to prevent attacks.
- Microsoft 365 can troubleshoot security issues by accessing customer data without explicit permission from the customer.