SC-200 : Microsoft Security Operations Analyst : Part 04
SC-200 : Microsoft Security Operations Analyst : Part 04
-
You provision Azure Sentinel for a new Azure subscription.
You are configuring the Security Events connector.
While creating a new rule from a template in the connector, you decide to generate a new alert for every event.
You create the following rule query.
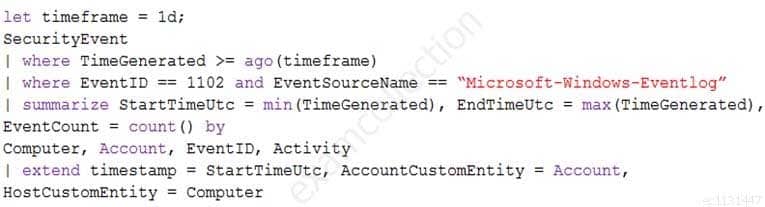
SC-200 Microsoft Security Operations Analyst Part 04 Q01 043 By which two components can you group alerts into incidents? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- user
- resource group
- IP address
- computer
-
Your company stores the data of every project in a different Azure subscription. All the subscriptions use the same Azure Active Directory (Azure AD) tenant.
Every project consists of multiple Azure virtual machines that run Windows Server. The Windows events of the virtual machines are stored in a Log Analytics workspace in each machine’s respective subscription.
You deploy Azure Sentinel to a new Azure subscription.
You need to perform hunting queries in Azure Sentinel to search across all the Log Analytics workspaces of all the subscriptions.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Add the Security Events connector to the Azure Sentinel workspace.
- Create a query that uses the workspace expression and the union operator.
- Use the alias statement.
- Create a query that uses the resource expression and the alias operator.
- Add the Azure Sentinel solution to each workspace.
-
You have an Azure Sentinel workspace.
You need to test a playbook manually in the Azure portal.
From where can you run the test in Azure Sentinel?
- Playbooks
- Analytics
- Threat intelligence
- Incidents
-
You have a custom analytics rule to detect threats in Azure Sentinel.
You discover that the analytics rule stopped running. The rule was disabled, and the rule name has a prefix of AUTO DISABLED.
What is a possible cause of the issue?
- There are connectivity issues between the data sources and Log Analytics.
- The number of alerts exceeded 10,000 within two minutes.
- The rule query takes too long to run and times out.
- Permissions to one of the data sources of the rule query were modified.
-
Your company uses Azure Sentinel.
A new security analyst reports that she cannot assign and resolve incidents in Azure Sentinel.
You need to ensure that the analyst can assign and resolve incidents. The solution must use the principle of least privilege.
Which role should you assign to the analyst?
- Azure Sentinel Responder
- Logic App Contributor
- Azure Sentinel Contributor
- Azure Sentinel Reader
-
You recently deployed Azure Sentinel.
You discover that the default Fusion rule does not generate any alerts. You verify that the rule is enabled.
You need to ensure that the Fusion rule can generate alerts.
What should you do?
- Disable, and then enable the rule.
- Add data connectors
- Create a new machine learning analytics rule.
- Add a hunting bookmark.
-
DRAG DROP
Your company deploys Azure Sentinel.
You plan to delegate the administration of Azure Sentinel to various groups.
You need to delegate the following tasks:
– Create and run playbooks
– Create workbooks and analytic rules.The solution must use the principle of least privilege.
Which role should you assign for each task? To answer, drag the appropriate roles to the correct tasks. Each role may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
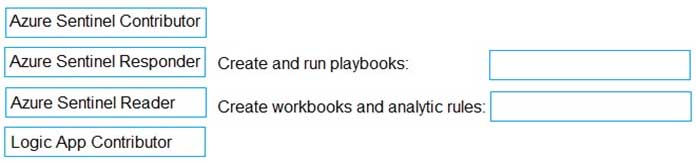
SC-200 Microsoft Security Operations Analyst Part 04 Q07 044 Question 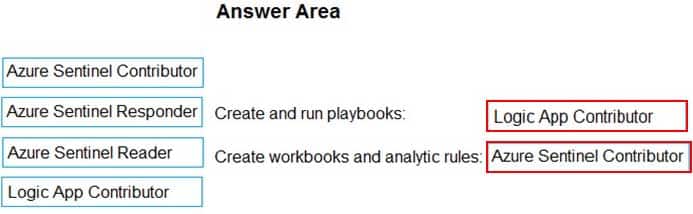
SC-200 Microsoft Security Operations Analyst Part 04 Q07 044 Answer -
A company uses Azure Sentinel.
You need to create an automated threat response.
What should you use?
- a data connector
- a playbook
- a workbook
- a Microsoft incident creation rule
-
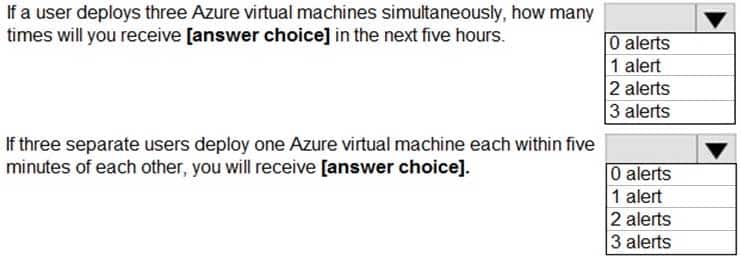
HOTSPOT
You use Azure Sentinel to monitor irregular Azure activity.
You create custom analytics rules to detect threats as shown in the following exhibit.
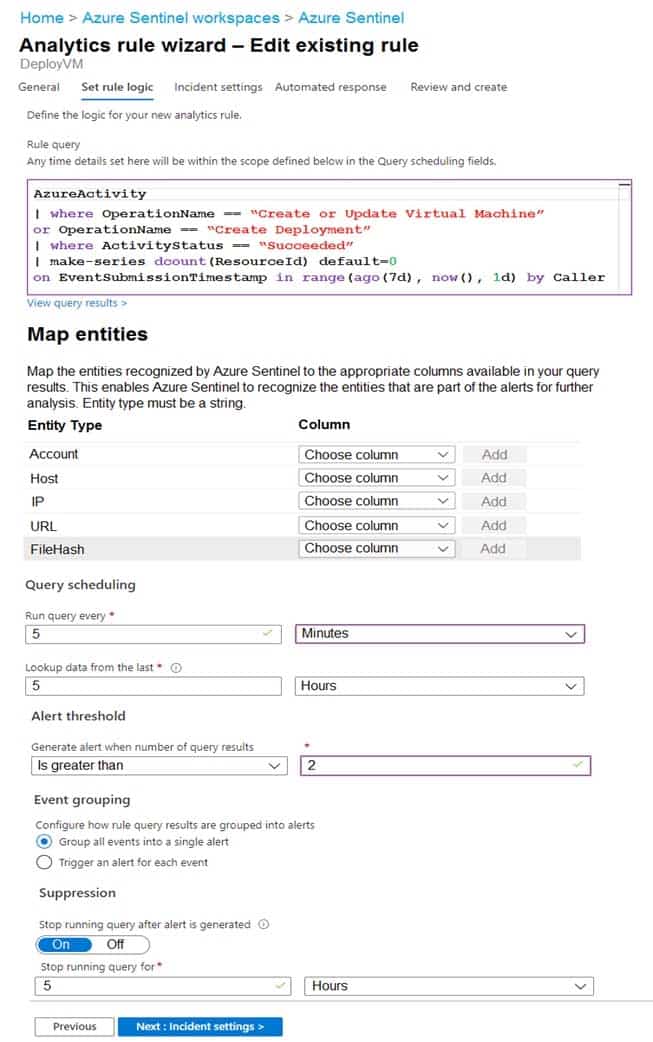
SC-200 Microsoft Security Operations Analyst Part 04 Q09 045 You do NOT define any incident settings as part of the rule definition.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
SC-200 Microsoft Security Operations Analyst Part 04 Q09 046 Question 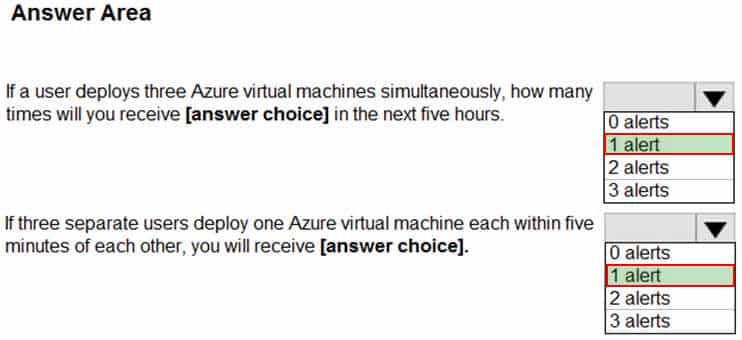
SC-200 Microsoft Security Operations Analyst Part 04 Q09 046 Answer -
You have an Azure Sentinel deployment in the East US Azure region.
You create a Log Analytics workspace named LogsWest in the West US Azure region.
You need to ensure that you can use scheduled analytics rules in the existing Azure Sentinel deployment to generate alerts based on queries to LogsWest.
What should you do first?
- Deploy Azure Data Catalog to the West US Azure region.
- Modify the workspace settings of the existing Azure Sentinel deployment.
- Add Azure Sentinel to a workspace.
- Create a data connector in Azure Sentinel.
-
You create a custom analytics rule to detect threats in Azure Sentinel.
You discover that the rule fails intermittently.
What are two possible causes of the failures? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- The rule query takes too long to run and times out.
- The target workspace was deleted.
- Permissions to the data sources of the rule query were modified.
- There are connectivity issues between the data sources and Log Analytics
Explanation:
Incorrect Answers:
B: This would cause it to fail every time, not just intermittently.
C: This would cause it to fail every time, not just intermittently. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring Azure Sentinel.
You need to create an incident in Azure Sentinel when a sign-in to an Azure virtual machine from a malicious IP address is detected.
Solution: You create a scheduled query rule for a data connector.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring Azure Sentinel.
You need to create an incident in Azure Sentinel when a sign-in to an Azure virtual machine from a malicious IP address is detected.
Solution: You create a hunting bookmark.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring Azure Sentinel.
You need to create an incident in Azure Sentinel when a sign-in to an Azure virtual machine from a malicious IP address is detected.
Solution: You create a Microsoft incident creation rule for a data connector.
Does this meet the goal?
- Yes
- No
-
You plan to create a custom Azure Sentinel query that will track anomalous Azure Active Directory (Azure AD) sign-in activity and present the activity as a time chart aggregated by day.
You need to create a query that will be used to display the time chart.
What should you include in the query?
-
extend
-
bin -
makeset
-
workspace
-
-
You are configuring Azure Sentinel.
You need to send a Microsoft Teams message to a channel whenever a sign-in from a suspicious IP address is detected.
Which two actions should you perform in Azure Sentinel? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Add a playbook.
- Associate a playbook to an incident.
- Enable Entity behavior analytics.
- Create a workbook.
- Enable the Fusion rule.
-
You need to visualize Azure Sentinel data and enrich the data by using third-party data sources to identify indicators of compromise (IoC).
What should you use?
- notebooks in Azure Sentinel
- Microsoft Cloud App Security
- Azure Monitor
- hunting queries in Azure Sentinel
-
You plan to create a custom Azure Sentinel query that will provide a visual representation of the security alerts generated by Azure Security Center.
You need to create a query that will be used to display a bar graph.
What should you include in the query?
-
extend
-
bin
-
count -
workspace
-
-
You use Azure Sentinel.
You need to receive an immediate alert whenever Azure Storage account keys are enumerated.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Create a livestream
- Add a data connector
- Create an analytics rule
- Create a hunting query.
- Create a bookmark.
-
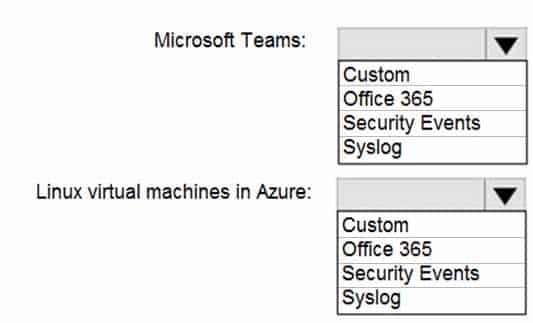
HOTSPOT
You deploy Azure Sentinel.
You need to implement connectors in Azure Sentinel to monitor Microsoft Teams and Linux virtual machines in Azure. The solution must minimize administrative effort.
Which data connector type should you use for each workload? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
SC-200 Microsoft Security Operations Analyst Part 04 Q20 047 Question 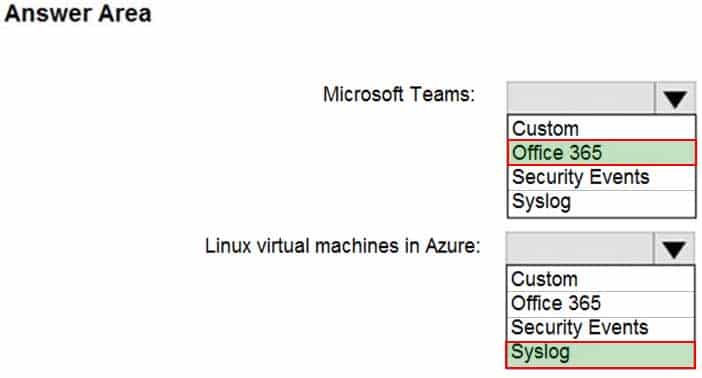
SC-200 Microsoft Security Operations Analyst Part 04 Q20 047 Answer