Networking Essentials 3.0: Course Final Exam Answers Full 100% 2023 2024
Networking Essentials 3.0: Course Final Exam Answers Full 100% 2023 2024
This Networking Essentials 3.0: Course Final Exam Answers is provided with the correct answers to 100% of the questions. This Final Exam Answers is used for the Cisco SkillsForAll platform which is the latest version just released in 2023 2024. Review all the questions and answers here, then you will meet randomly 60 questions from all here.
-
Which three types of nodes should be assigned static IP addresses on a network? (Choose three.)
- printers
- servers
- tablets
- mobile laptops
- gateways
- desktop PCs
Answers Explanation & Hints:
The three types of nodes that should be assigned static IP addresses on a network are:
- Printers: Printers are often accessed by multiple users, and assigning a static IP address to a printer ensures that it can always be found at the same network location.
- Servers: Servers are critical components of a network and should have a static IP address to ensure that they can always be found and accessed by clients.
- Gateways: Gateways are the entry and exit points of a network and are responsible for directing traffic between different networks. Assigning a static IP address to a gateway ensures that other devices on the network can always find it.
Note that while desktop PCs can also benefit from having a static IP address, it is not always necessary or practical to assign them one, especially in larger networks where IP address management can become more complex. Similarly, while tablets and mobile laptops may benefit from having a static IP address in some cases, they are typically assigned dynamic IP addresses by default.
-
Refer to the exhibit. An administrator is troubleshooting connectivity on the office network. PC1 is able to send print jobs to Printer1, but is unable to access File Server1. Which action would correct the problem?
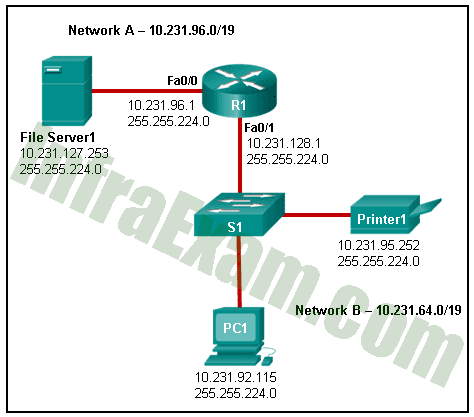
Networking Essentials 3.0 Course Final Exam Answers 07 - Change the R1 Fa0/0 interface subnet mask to 255.255.0.0.
- Change the R1 Fa0/1 interface IP address to 10.231.64.1.
- Change the PC1 IP address to 10.231.64.115.
- Change the File Server1 IP address to 10.231.96.253.
-
Answers Explanation & Hints:
Network B – 10.231.64.0/19
Network ID: 10.231.64.0
Usable IP Range: 10.231.64.1 – 10.231.95.254
Broadcast IP: 10.231.95.255
According to the exhibit, R1 => f0/1: 10.231.128.1 is out of the Network B range, so we have to change it to one of IP that is in the Network B range.
Based on the answer choices, 10.231.64.1 is the first IP in the Network B Range.
-
Which two statements are correct in a comparison of IPv4 and IPv6 packet headers? (Choose two.)
- The Source Address field name from IPv4 is kept in IPv6.
- The Destination Address field is new in IPv6.
- The Version field from IPv4 is not kept in IPv6.
- The Time-to-Live field from IPv4 has been replaced by the Hop Limit field in IPv6.
- The Header Checksum field name from IPv4 is kept in IPv6.
-
Answers Explanation & Hints:
- The Source Address field name is kept in IPv6 and is used to indicate the IPv6 address of the source node or device sending the packet.
- The Destination Address field is new in IPv6 and is used to indicate the IPv6 address of the destination node or device for the packet.
- The Version field from IPv4 is not kept in IPv6, as IPv6 uses a separate 4-bit field called the “Version” field in its header.
- The Time-to-Live field from IPv4 has been replaced by the Hop Limit field in IPv6, which serves a similar purpose of preventing packets from circulating indefinitely in the network.
- The Header Checksum field name from IPv4 is not kept in IPv6, as IPv6 uses a different mechanism for ensuring data integrity called the “Authentication Header” (AH) and “Encapsulating Security Payload” (ESP).
-
Which statement is true regarding the UDP client process during a session with a server?
- Application servers have to use port numbers above 1024 in order to be UDP capable.
- A three-way handshake takes place before the transmission of data begins.
- A session must be established before datagrams can be exchanged.
- Datagrams that arrive in a different order than that in which they were sent are not placed in order.
-
Answers Explanation & Hints:
- UDP (User Datagram Protocol) is a transport layer protocol that is connectionless, meaning it does not establish a session or perform a three-way handshake before transmitting data.
- Unlike TCP (Transmission Control Protocol), UDP does not guarantee delivery or order of datagrams. If datagrams are lost or arrive out of order, it is up to the application layer to handle any necessary retransmissions or reordering of data.
- Both the client and server processes using UDP can use any port number, and there is no requirement for applications to use ports above 1024. However, some well-known services such as DNS use specific port numbers.
- In summary, while a session does not need to be established before datagrams can be exchanged, and a three-way handshake does not take place, UDP does not guarantee delivery or order of datagrams.
-
Match the definition to the type of cloud.
- made up of two or more distinct cloud infrastructures bound together by technology ==> hybrid cloud
- intended for a specific organization or entity, such as the government ==> private cloud
- intended for exclusive use by multiple organizations with shared functional needs ==> community
- services made available to the general population ==> public cloud
-
Answers Explanation & Hints:
- Public cloud: A public cloud is a type of cloud environment in which computing resources are made available to the general public over the internet. These resources are typically owned and operated by a third-party provider, such as Amazon Web Services (AWS), Google Cloud Platform, or Microsoft Azure. Public clouds are often used by companies or individuals who want to run applications or services on infrastructure that they do not own or manage.
- Private cloud: A private cloud is a type of cloud environment that is intended for a specific organization or entity. Private clouds are typically built and maintained by the organization’s IT department, and the infrastructure may be physically located on-premises or in a third-party data center. Private clouds offer more control and customization options than public clouds, but they require more upfront investment in terms of hardware, software, and personnel.
- Community cloud: A community cloud is a type of cloud environment that is intended for exclusive use by multiple organizations with shared functional needs. Community clouds may be owned and managed by one or more of the participating organizations, or they may be provided by a third-party vendor. Community clouds offer a way for organizations to share computing resources while maintaining greater control and security than they would have in a public cloud.
- Hybrid cloud: A hybrid cloud is a type of cloud environment that is made up of two or more distinct cloud infrastructures bound together by technology. This can include a combination of public and private clouds, as well as on-premises infrastructure. Hybrid clouds offer a way for organizations to take advantage of the scalability and flexibility of public clouds while maintaining greater control over sensitive data and applications.
-
What are two characteristics of RAM on a Cisco device? (Choose two.)
- RAM is able to store multiple versions of IOS and configuration files.
- RAM is a component in Cisco switches but not in Cisco routers.
- The configuration that is actively running on the device is stored in RAM.
- The contents of RAM are lost during a power cycle.
- RAM provides nonvolatile storage.
-
Answers Explanation & Hints:
RAM stands for Random Access Memory, which is volatile memory and stores the running configuration file, routing tables, ARP cache, packet buffers, and other temporary data. RAM provides fast access to data but does not provide permanent storage, so its contents are lost when the device is powered off or restarted. Cisco routers and switches both use RAM for temporary storage. RAM does not provide nonvolatile storage, as it is volatile memory.
-
Which statement describes the use of powerline networking technology?
- New “smart” electrical cabling is used to extend an existing home LAN.
- Wireless access points use powerline adapters to distribute data through the home LAN.
- A device connects to an existing home LAN using an adapter and an existing electrical outlet.
- A home LAN is installed without the use of physical cabling.
-
Answers Explanation & Hints:
Powerline networking technology allows network signals to be transmitted over the existing electrical wiring in a building. With this technology, a device can be connected to an existing home LAN by using an adapter that plugs into a wall socket, allowing network signals to be transmitted over the electrical wiring in the building. This technology is often used in situations where it is difficult or impossible to run physical network cables or where wireless signals are unreliable.
-
An employee is having connectivity issues. Why might a network technician try to ping the default gateway from the employee laptop?
- to verify that the SVI interface on the switch is configured correctly
- to verify connectivity with the device that provides access to remote networks
- to verify that an IP address was provided by the DHCP server
- to determine if the laptop address is included in the DNS server
-
Answers Explanation & Hints:
The default gateway is the device that enables communication between devices on the local network and devices on remote networks. If a device is having connectivity issues, one of the first steps a technician might take is to verify that the device can communicate with the default gateway. By pinging the default gateway from the employee laptop, the technician can determine if the issue is related to connectivity with the device that provides access to remote networks. If the ping is successful, then the connectivity issue may be related to other factors such as DNS or DHCP, which can be further investigated.
-
Refer to the exhibit. A switch with a default configuration connects four hosts. The ARP table for host A is shown. What happens when host A wants to send an IP packet to host D?
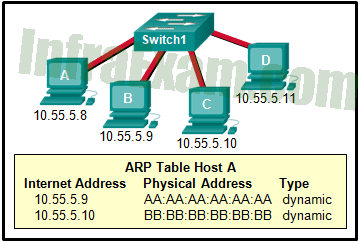
Networking Essentials 3.0 Course Final Exam Answers 08 - Host A sends an ARP request to the MAC address of host D.
- Host A sends out a broadcast of FF:FF:FF:FF:FF:FF. Every other host connected to the switch receives the broadcast and host D responds with its MAC address.
- Host D sends an ARP request to host A.
- Host A sends out the packet to the switch. The switch sends the packet only to the host D, which in turn responds.
-
Answers Explanation & Hints:
Host A sends out an ARP request to the MAC address of host D. Since the IP address of host D is not listed in the ARP table of host A, host A will need to send an ARP request to determine the MAC address of host D. Once host A receives the MAC address of host D from the ARP response, it can use that information to send the IP packet to host D.
-
Which type of static route creates a gateway of last resort?
- default static route
- floating static route
- summary static route
- standard static route
-
Answers Explanation & Hints:
A default static route is a type of static route that creates a gateway of last resort. It is used to route traffic to any destination that is not in the routing table, and is typically used when a router has only one path to the outside network. The default static route is also known as the 0.0.0.0/0 route, which means that it matches any destination address (0.0.0.0) with any subnet mask (/0). When a packet is received by the router that does not match any other route in the routing table, the router will forward the packet to the next hop specified in the default route. This is useful for routers that do not have specific knowledge of all the networks they might encounter, such as border routers or routers that connect to the internet.
-
Refer to the exhibit. If all devices are using a subnet mask of 255.255.255.0, which laptop would have an IP address with the same network number as the server?
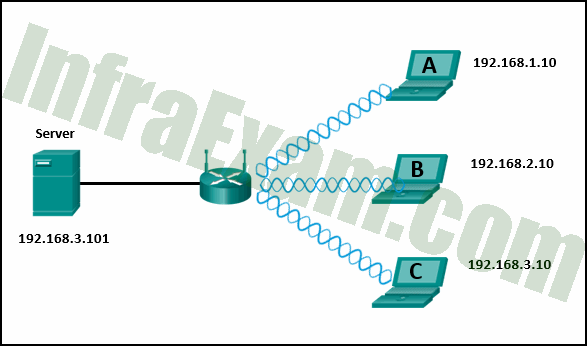
Networking Essentials 3.0 Course Final Exam Answers 09 - B
- A
- C
-
Answers Explanation & Hints:
Laptop C (192.168.3.10) would have the same network number (192.168.3.0) as the server (192.168.3.101) because they both have the same network portion (the first three octets) in their IP addresses.
-
Which two scenarios would benefit the user the most by adding quality of service (QoS) to the network? (Choose two.)
- A student is communicating via Skype with a friend in another country.
- Students are updating information about their sport activities on the class Facebook page.
- A student is sending emails to a friend.
- Students are watching a lecture from a YouTube site.
-
Answers Explanation & Hints:
In both scenarios, real-time communication and streaming video are involved, which require a reliable and fast network with minimal delay, jitter, and packet loss. Implementing QoS can prioritize and manage the network traffic to ensure that these applications receive the necessary bandwidth and resources, while less critical traffic is given lower priority. This can improve the overall user experience and prevent issues such as choppy audio or video, dropped calls, and slow response times.
-
An attacker is sitting in front of a store and wirelessly copies emails and contact lists from nearby unsuspecting user devices. What type of attack is this?
- bluejacking
- bluesnarfing
- smishing
- RF jamming
-
Answers Explanation & Hints:
The attack described is called bluesnarfing. Bluesnarfing is a type of wireless attack in which an attacker gains unauthorized access to a Bluetooth-enabled device such as a mobile phone, laptop, or tablet and steals personal data such as contact lists, emails, and messages. This type of attack can be carried out with software tools that allow attackers to search for and connect to Bluetooth devices without the knowledge or permission of the device owner.
To protect against bluesnarfing and other Bluetooth-related attacks, users should ensure that their devices are not discoverable to other Bluetooth devices when they are not in use, use strong and unique PINs or passwords to authenticate Bluetooth connections, and avoid connecting to unknown or suspicious devices. Network administrators can also implement security measures such as Bluetooth scanning, access controls, and intrusion detection systems to monitor and prevent unauthorized access to Bluetooth-enabled devices on their networks.
-
What type of attack targets an SQL database using the input field of a user?
- XML injection
- SQL injection
- Cross-site scripting
- buffer overflow
-
Answers Explanation & Hints:
The type of attack that targets an SQL database using the input field of a user is called SQL injection. In this type of attack, an attacker attempts to inject malicious SQL code into a web application’s input field, which the application then sends to a backend database. This can allow the attacker to access or modify the contents of the database, bypass authentication, or execute other unauthorized actions. SQL injection attacks can be prevented by input validation and sanitization of user input, as well as using prepared statements and parameterized queries in code.
-
What is an example of cloud computing?
- a service that offers on-demand access to shared resources
- a network infrastructure that spans a large geographic area
- a continuous interaction between people, processes, data, and things
- an architectural style of the World Wide Web
-
Answers Explanation & Hints:
An example of cloud computing is a service that offers on-demand access to shared resources over the Internet. This could include services such as cloud storage, cloud-based software applications, and cloud-based virtual machines. Cloud computing allows users to access computing resources on an as-needed basis, without the need to invest in and maintain physical hardware and infrastructure. This makes it a flexible and cost-effective solution for businesses and individuals alike.
-
Which two criteria are used to help select a network medium for a network? (Choose two.)
- the types of data that need to be prioritized
- the distance the selected medium can successfully carry a signal
- the environment where the selected medium is to be installed
- the cost of the end devices that are used in the network
- the number of intermediate devices that are installed in the network
-
Answers Explanation & Hints:
The distance a medium can carry a signal is important in determining the type of medium to be used. For example, fiber optic cables can carry signals over longer distances than copper cables. The environment where the medium is to be installed is also an important consideration, as some media are more suitable for certain environments than others. For example, wireless networks may be more suitable in environments where physical cabling is difficult to install or may not be feasible. The types of data that need to be prioritized, the cost of the end devices used in the network, and the number of intermediate devices installed are not as critical in determining the type of network medium to be used.
-
Refer to the exhibit. A web designer calls to report that the web server web-s1.cisco.com is not reachable through a web browser. The technician uses command line utilities to verify the problem and to begin the troubleshooting process. Which two things can be determined about the problem? (Choose two.)
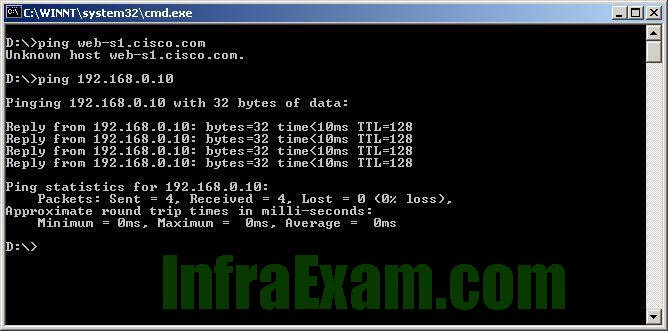
Networking Essentials 3.0 Course Final Exam Answers 10 - A router is down between the source host and the server web-s1.cisco.com.
- There is a problem with the web server software on web-s1.cisco.com.
- The default gateway between the source host and the server at 192.168.0.10 is down.
- The web server at 192.168.0.10 is reachable from the source host.
- DNS cannot resolve the IP address for the server web-s1.cisco.com.
-
Answers Explanation & Hints:
The output of the
pingcommand provides some useful information for troubleshooting network connectivity issues.In this particular case, the technician first attempted to ping the hostname “web-s1.cisco.com” but received the message “Unknown host web-s1.cisco.com”, indicating that the DNS (Domain Name System) server was unable to resolve the hostname to an IP address. This suggests that the problem may be related to DNS resolution.
Next, the technician pinged the IP address 192.168.0.10 and received four successful replies, indicating that the web server at that IP address is reachable from the source host. This rules out any issues with connectivity between the source host and the web server.
Based on these two pieces of information, it can be determined that the problem is likely related to DNS resolution, and specifically with the DNS server being used by the source host. The technician may need to investigate the configuration of the DNS server settings on the source host to ensure that they are configured correctly.
-
Which command would a technician use to display network connections on a host computer?
- ipconfig
- nslookup
- netstat
- tracert
-
Answers Explanation & Hints:
The command that a technician would use to display network connections on a host computer is
netstat. This command is used to show active network connections, routing tables, and other network statistics. By default, it displays all active TCP connections, both incoming and outgoing, and also UDP connections. Thenetstatcommand is available on both Windows and Unix-based operating systems. The output of thenetstatcommand can be used to troubleshoot network connectivity issues and identify potential security threats.
-
Which type of network model describes the functions that must be completed at a particular layer, but does not specify exactly how each protocol should work?
- reference model
- protocol model
- hierarchical design model
- TCP/IP model
-
Answers Explanation & Hints:
The type of network model that describes the functions that must be completed at a particular layer, but does not specify exactly how each protocol should work is a reference model. The most well-known reference model is the OSI (Open Systems Interconnection) model, which divides network communication into seven layers, each of which performs specific functions necessary for communication. The OSI model provides a framework for how network protocols should interact and communicate with each other, but it does not define the actual protocols used to accomplish these tasks.
-
Which three IPv4 header fields have no equivalent in an IPv6 header? (Choose three.)
- protocol
- TTL
- fragment offset
- flag
- identification
- version
-
Answers Explanation & Hints:
The three IPv4 header fields that have no equivalent in an IPv6 header are:
- Fragment offset – IPv6 does not support fragmentation at the router level, so this field is no longer needed.
- Identification – Instead of using the identification field, IPv6 uses a combination of the Source Address, Destination Address, and Flow Label fields to identify and reassemble fragmented packets.
- TTL – In IPv6, the TTL field is replaced with a Hop Limit field, which functions in the same way, but with a different name.
Therefore, the correct answer is:
- Fragment offset
- Identification
- TTL
-
How are port numbers used in the TCP/IP encapsulation process?
- Source port and destination port numbers are randomly generated.
- Destination port numbers are assigned automatically and cannot be changed.
- If multiple conversations occur that are using the same service, the source port number is used to track the separate conversations.
- Source port numbers and destination port numbers are not necessary when UDP is the transport layer protocol being used for the communication.
-
Answers Explanation & Hints:
In the TCP/IP encapsulation process, port numbers are used to identify the processes or applications on the source and destination devices that are communicating with each other. The source device randomly generates a source port number, and the destination device uses a well-known port number for the service that it provides. The source and destination port numbers together create a unique identifier for the communication, allowing multiple conversations using the same service to occur simultaneously without interfering with each other. In UDP, the source and destination port numbers are also used to identify the processes on the source and destination devices, and they are necessary to direct the data to the correct application.
-
What is the key difference between a type 1 hypervisor and a type 2 hypervisor?
- A type 1 hypervisor runs on specialized systems and a type 2 hypervisor runs on desktop computers.
- A type 1 hypervisor supports all server OS virtualization and a type 2 hypervisor supports Linux and Mac virtualization.
- A type 1 hypervisor supports server virtualizations and a type 2 hypervisor only supports workstation virtualization.
- A type 1 hypervisor runs directly on the system hardware and a type 2 hypervisor requires a host OS to run.
-
Answers Explanation & Hints:
The key difference between a type 1 hypervisor and a type 2 hypervisor is that a type 1 hypervisor runs directly on the system hardware while a type 2 hypervisor requires a host operating system to run. Type 1 hypervisors are also known as bare-metal hypervisors and are installed directly on the server hardware. They have direct access to the underlying system hardware and manage the resources of the physical host, allowing multiple guest virtual machines to run on top. Type 2 hypervisors, on the other hand, run on top of a host operating system, such as Windows or Linux, and are also known as hosted hypervisors. They use the host OS to manage system resources and create a layer of abstraction between the guest virtual machines and the physical host.
-
Refer to the exhibit. Which protocol was responsible for building the table that is shown?
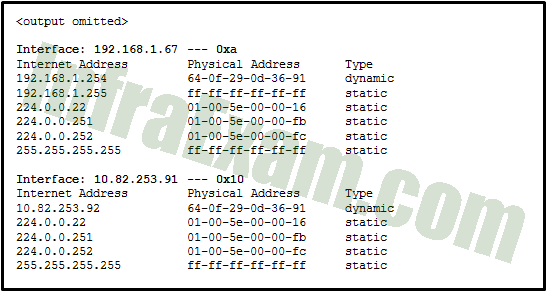
Networking Essentials 3.0 Course Final Exam Answers 06 - DNS
- ARP
- DHCP
- ICMP
-
Answers Explanation & Hints:
The table in the exhibit shows the mapping of IP addresses to physical addresses on a local network segment. This mapping is accomplished through a protocol called Address Resolution Protocol (ARP). When a device needs to communicate with another device on the same local network segment, it uses ARP to determine the physical address (also known as the MAC address) of the destination device based on its IP address. Once the physical address is known, the source device can create a frame with the appropriate source and destination MAC addresses and transmit it over the local network to the destination device. ARP is a protocol that operates at the data link layer of the OSI model.
-
Which two types of messages are used in place of ARP for address resolution in IPv6? (Choose two.)
- neighbor solicitation
- neighbor advertisement
- broadcast
- echo reply
- echo request
- anycast
-
Answers Explanation & Hints:
In IPv6, ARP (Address Resolution Protocol) has been replaced with two messages, Neighbor Solicitation (NS) and Neighbor Advertisement (NA), which are used for address resolution. These two messages help nodes determine the link-layer (MAC) address of a neighbor on the same network segment. An NS message is used to query the link-layer address of a neighbor, while an NA message is used to respond to a query or to announce the link-layer address of the sender. The use of broadcast is also replaced with multicast addressing. Echo request and echo reply are messages used in ICMP (Internet Control Message Protocol) for ping tests, and anycast is a type of addressing used for routing packets to the nearest of a group of potential destination hosts.
-
A PC has sent an RS message to an IPv6 router attached to the same network. Which two pieces of information will the router send to the client? (Choose two.)
- DNS server IP address
- subnet mask in dotted decimal notation
- prefix
- administrative distance
- domain name
- prefix length
-
Answers Explanation & Hints:
An RS (Router Solicitation) message is used by an IPv6 client to obtain its own global unicast address by sending a multicast message to all routers on the network. When a router receives an RS message from a client, it will respond with an RA (Router Advertisement) message that includes the following information:
- Prefix: The prefix to be used for the network segment.
- Prefix length: The length of the prefix.
Therefore, the correct answers to this question are:
- Prefix
- Prefix length
-
Refer to the exhibit. Which term correctly identifies the device type that is included in the area B?
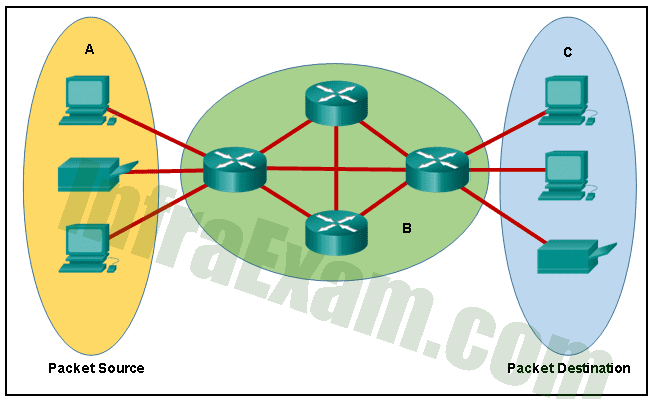
Networking Essentials 3.0 Course Final Exam Answers 05 - transfer
- source
- intermediary
- end
-
Answers Explanation & Hints:
In the given exhibit, the area B is the middle circle that contains three interconnected routers. This indicates that the routers in this area are functioning as intermediary devices. An intermediary device is a networking device that acts as a bridge between multiple networks or devices, providing connectivity and forwarding data packets between them. In this case, the routers in area B are responsible for routing packets between the devices in areas A and C. The routers in area B may perform additional functions such as filtering, security, and quality of service (QoS) to optimize the network traffic flow.
-
A user can access a file share resource on a server located in the same office but cannot access the internet. What is the possible cause?
- The switch is malfunctioning.
- The default gateway address is misconfigured on the PC.
- The DHCP server is disconnected.
- The IPv4 address and subnet mask are misconfigured on the PC.
-
Answers Explanation & Hints:
The possible cause for a user to be able to access a file share resource on a server located in the same office but not access the internet is that the default gateway address is misconfigured on the PC. The default gateway is the IP address of the router that provides access to networks outside of the local network. If the default gateway is misconfigured or unavailable, the PC cannot access resources outside of the local network, such as the internet. However, it can still communicate with devices on the same local network. To resolve the issue, the default gateway address on the PC needs to be correctly configured.
-
Refer to the exhibit. Host H2 sends a unicast message to host H6. Which destination IP address is contained in the header of the packet when it reaches host H6?
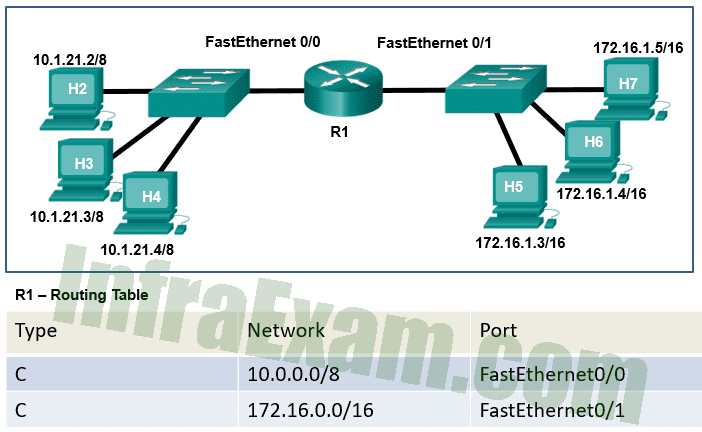
Networking Essentials 3.0 Course Final Exam Answers 04 - the IP address of the FastEthernet0/0 interface on router R1
- the IP address of the FastEthernet0/1 interface on router R1
- the IP address assigned to the network adapter on host H6
- the IP address assigned to the network adapter on host H2
-
Answers Explanation & Hints:
The destination IP address contained in the header of the packet when it reaches host H6 would be the IP address assigned to the network adapter on host H6, which is 172.16.1.4/16.
-
Refer to the exhibit. How many bits are represented by each group of four hexadecimal values contained between the colons in an IPv6 address?

Networking Essentials 3.0 Course Final Exam Answers 03 - 32
- 16
- 64
- 4
- 8
-
Answers Explanation & Hints:
Each group of four hexadecimal values contained between the colons in an IPv6 address represents 16 bits.
-
Which wireless technology allows a customer to connect to a payment terminal in the store with a smartphone?
- Wi-Fi
- GPS
- Bluetooth
- NFC
-
Answers Explanation & Hints:
The wireless technology that allows a customer to connect to a payment terminal in the store with a smartphone is Near Field Communication (NFC). NFC is a short-range wireless technology that enables two devices to communicate with each other when they are in close proximity, typically within a few centimeters. It is widely used for contactless payments, ticketing, and access control systems. The technology is based on radio frequency identification (RFID) technology and operates on the 13.56 MHz frequency band. Unlike Wi-Fi and Bluetooth, NFC does not require pairing or a network connection, which makes it more convenient and secure for mobile payments.
-
What data encoding technology is used in copper cables?
- modulation of light rays
- pulses of light
- electrical pulses
- modulation of specific frequencies of electromagnetic waves
-
Answers Explanation & Hints:
Data encoding is the process of transforming digital information into a format suitable for transmission over a communication channel. In copper cables, the data is encoded using electrical pulses. Electrical pulses are used to represent binary digits, which can be transmitted over the copper cable as electrical signals.
The most commonly used data encoding technique for copper cables is called Non-Return-to-Zero (NRZ) encoding. In this technique, a high voltage represents a binary 1, and a low voltage represents a binary 0. The electrical pulses are transmitted over the copper cable using a specific protocol, such as Ethernet, which defines how the data is organized and transmitted.
Other data encoding techniques that can be used with copper cables include Manchester encoding, Differential Manchester encoding, and Bipolar encoding. These techniques are used to reduce errors and increase data transmission rates over the copper cable.
-
Which two TCP header fields are used to confirm receipt of data? (Choose two.)
- preamble
- acknowledgment number
- FCS
- checksum
- sequence number
-
Answers Explanation & Hints:
The two TCP header fields used to confirm receipt of data are:
- Acknowledgment Number: This field contains the sequence number of the next byte of data that the receiver is expecting from the sender. When the receiver receives a TCP segment, it sends an acknowledgment back to the sender with this field set to the next expected sequence number.
- Checksum: This field is used to ensure the integrity of the TCP segment. It is a 16-bit field that contains a checksum value calculated over the entire TCP segment. The sender calculates this value and includes it in the TCP segment header. The receiver recalculates the checksum and compares it to the value in the header to confirm that the segment was not corrupted in transit.
-
What are two characteristics of multicast transmission? (Choose two.)
- A single packet can be sent to a group of hosts.
- Computers use multicast transmission to request IPv4 addresses.
- Multicast messages map lower layer addresses to upper layer addresses.
- Multicast transmission can be used by routers to exchange routing information.
- The source address of a multicast transmission is in the range of 224.0.0.0 to 224.0.0.255.
-
Answers Explanation & Hints:
The correct characteristics of multicast transmission are:
- A single packet can be sent to a group of hosts.
- Multicast transmission can be used by routers to exchange routing information.
The other options are incorrect:
- Computers use multicast transmission to request IPv4 addresses: this is not true, DHCP is used to assign IPv4 addresses.
- Multicast messages map lower layer addresses to upper layer addresses: this statement is not correct, mapping of lower layer addresses to upper layer addresses is not related to multicast transmission.
- The source address of a multicast transmission is in the range of 224.0.0.0 to 224.0.0.255: This statement is not accurate, the source address of a multicast transmission can be any valid unicast or multicast IP address. However, the destination IP address for multicast transmission must be in the range of 224.0.0.0 to 239.255.255.255.
-
Which troubleshooting tool can be used to determine the current TCP open connections on a PC?
- netstat
- nslookup
- tracrt
- ping
- ipconfig
-
Answers Explanation & Hints:
The
netstatcommand is a network diagnostic tool that can be used to display various information about network connections on a computer. One of the pieces of information it can provide is the current TCP open connections on the PC.When you run the
netstatcommand, it will display a list of all the active network connections on your computer, along with information about the local and remote IP addresses and port numbers, the state of the connection, and the process ID (PID) of the application that is using the connection. By examining this information, you can determine which applications are using the most network resources, troubleshoot network connectivity issues, and monitor your network for unusual activity.
-
By having narrow viewing angles, an ATM mitigates what kind of attacks?
- quid pro quo
- identity fraud
- dumpster diving
- shoulder surfing
-
Answers Explanation & Hints:
By having narrow viewing angles, an ATM mitigates shoulder surfing attacks. Shoulder surfing is a form of direct observation attack in which an attacker looks over the shoulder of the victim to obtain sensitive information, such as PINs, passwords, or other confidential information. By limiting the viewing angles, an ATM makes it difficult for an attacker to observe the information entered by the user on the ATM screen or keypad. This reduces the risk of successful shoulder surfing attacks and helps to improve the security of ATM transactions.
-
Match the IPv6 field with its description.
- Payload Length ==> This 16-bit field indicates the length of the data portion of the IPv6 packet.
- Hop Limit ==> This 8-bit field uses a decremental counter to generate an IPv6 Time Exceeded message for the unsuccessful delivery of the message.
- Version ==> This field contains a 4-bit binary value set to 0110 that identifies this as an IP version 6 packet.
- Flow Label ==> This 20-bit flow label field in the IPv6 header is used by the source to label those packets for which the source requests special handling by the IPv6 routers.
- Next Header ==> This field indicates the data payload type that the packet is carrying, enabling the network layer to pass the data to the appropriate upper-layer protocol.
- Traffic Class ==> This 8-bit field is equivalent to the IPv4 Differentiated Services (DS) field.
-
Answers Explanation & Hints:
IPv6 is the latest version of the Internet Protocol (IP), and it is designed to address the limitations of IPv4, which is the current version of IP that most networks use today. IPv6 has a much larger address space than IPv4, allowing for the creation of more unique addresses, which is important as the number of internet-connected devices continues to grow.
One of the key features of IPv6 is the addition of several new header fields that provide additional functionality compared to IPv4. These header fields include the Payload Length, Hop Limit, Version, Flow Label, Next Header, and Traffic Class fields.
The Payload Length field is a 16-bit field that indicates the length of the data portion of the IPv6 packet, excluding the IPv6 header. This field allows the receiving device to know how much data to expect in the packet.
The Hop Limit field is an 8-bit field that uses a decremental counter to generate an IPv6 Time Exceeded message for the unsuccessful delivery of the message. This field is similar to the Time to Live (TTL) field in IPv4, but the Hop Limit field is incremented at each hop, while the TTL field is decremented.
The Version field is a 4-bit binary value set to 0110 that identifies the packet as an IPv6 packet. This field is used to differentiate IPv6 packets from IPv4 packets.
The Flow Label field is a 20-bit field that is used by the source to label those packets for which the source requests special handling by the IPv6 routers. This field is used to provide Quality of Service (QoS) guarantees for specific traffic flows.
The Next Header field is an 8-bit field that indicates the type of data payload that the packet is carrying, enabling the network layer to pass the data to the appropriate upper-layer protocol.
The Traffic Class field is an 8-bit field that is equivalent to the IPv4 Differentiated Services (DS) field. This field is used to provide different levels of service for different types of traffic.
-
Which nslookup command would return the DNS information of www.cisco.com?
- nslookup = cisco
- nslookup -type=mx www.cisco.com
- nslookup
- nslookup www.cisco.com
-
Answers Explanation & Hints:
To return the DNS information of www.cisco.com using the nslookup command, you can simply enter “nslookup www.cisco.com” in your command prompt or terminal. This will perform a DNS lookup for the domain and provide you with the relevant information.
Here’s an example of how the command would look:
nslookup www.cisco.com
Executing this command will display the DNS information for the specified domain, including the IP address associated with it.
-
Match the applications protocols to their respective transport protocols.
- HTTP ==> TCP
- SMTP ==> TCP
- FTP ==> TCP
- TFTP ==> UDP
-
Answers Explanation & Hints:
Application protocols are used to specify how data should be formatted, transmitted, and received between applications. These protocols operate at the application layer of the OSI model, which is the topmost layer responsible for application-to-application communication.
Transport protocols, on the other hand, operate at the transport layer of the OSI model and are responsible for the end-to-end delivery of data between hosts. There are two main transport protocols: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
HTTP (Hypertext Transfer Protocol) is an application protocol that is used for transmitting data over the World Wide Web. HTTP typically runs over TCP.
SMTP (Simple Mail Transfer Protocol) is an application protocol used to transmit electronic mail messages between servers. SMTP typically runs over TCP.
FTP (File Transfer Protocol) is an application protocol used for transferring files over the Internet. FTP can run over both TCP and UDP, but is more commonly used with TCP.
TFTP (Trivial File Transfer Protocol) is a simpler version of FTP, used mainly for booting diskless workstations. TFTP runs over UDP.
-
Refer to the exhibit. Host A wants to send a packet to host D. Before sending the packet; host A needs to find out if host D is on the same local network. How does the source host find out if it has the same network portion as the destination host?
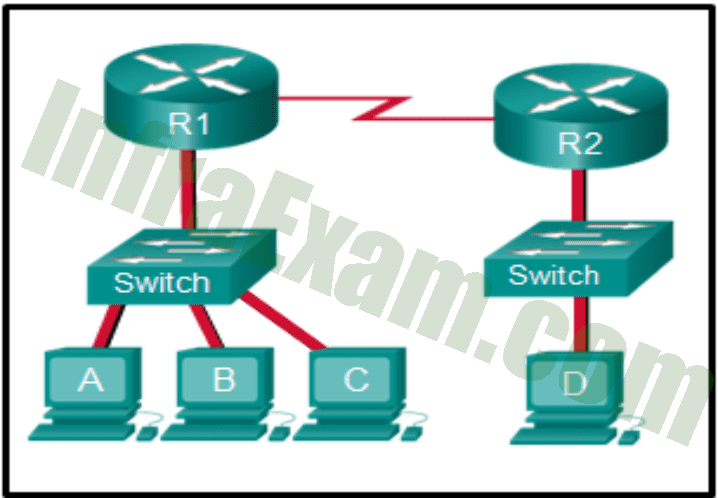
Networking Essentials 3.0 Course Final Exam Answers 02 - a binary anding between the R1 default gateway IP address and the R2 default gateway IP address
- a binary anding between the subnet mask of host A and the R2 default gateway IP address
- a binary anding between the subnet mask of host A and the host D IP destination address
- a binary anding between the subnet mask of host A and the R1 default gateway IP address
-
Answers Explanation & Hints:
The source host (Host A) will perform a binary AND operation between its own IP address and subnet mask, and the IP address of the destination host (Host D). This will give the network address of the destination host, and the source host will compare it to its own network address. If they match, the destination host is on the same local network as the source host, and the source host can send the packet directly to the destination host using ARP to resolve the MAC address. If they do not match, the source host will send the packet to its default gateway (Router R1), which will forward the packet to the next hop towards the destination host.
-
Which two addressing schemes use hexadecimal numbers? (Choose two.)
- IPv6 addresses
- IPv4 multicast addresses
- MAC addresses
- IPv4 broadcast addresses
- destination port numbers
-
Answers Explanation & Hints:
The two addressing schemes that use hexadecimal numbers are:
- MAC addresses – MAC addresses are 48-bit addresses used to identify devices on a local network, and are expressed in hexadecimal format.
- IPv6 addresses – IPv6 addresses are 128-bit addresses used to identify devices on a network and are also expressed in hexadecimal format.
-
Which two application protocols retrieve emails from remote servers? (Choose two.)
- SSH
- IMAP
- POP
- SMTP
- FTP
-
Answers Explanation & Hints:
IMAP (Internet Message Access Protocol) and POP (Post Office Protocol) are two email retrieval protocols used to access emails stored on a remote email server.
IMAP allows a user to view and manipulate email messages as if they were stored locally on the user’s device. The email messages remain on the server and can be accessed and managed from different devices or email clients. IMAP also supports multiple mailboxes and folders, allowing users to organize and manage their emails more efficiently.
POP, on the other hand, downloads email messages from the server onto the user’s device and removes them from the server. Once downloaded, the email messages can only be accessed on that specific device. POP does not support multiple mailboxes or folders, making it less flexible than IMAP.
Both protocols use port numbers to communicate with the email server. IMAP uses port number 143 for unencrypted connections and port number 993 for encrypted connections (IMAP over SSL/TLS). POP uses port number 110 for unencrypted connections and port number 995 for encrypted connections (POP over SSL/TLS).
-
Which network connection type provides the highest data link speed?
- DSL
- fiber
- cable
- satellite
-
Answers Explanation & Hints:
Fiber provides the highest data link speed among the four network connection types mentioned. This is because fiber optic cables use light signals to transmit data, which can travel at very high speeds over long distances with minimal signal degradation. Compared to DSL, cable, and satellite connections, fiber optic connections can offer higher bandwidth and faster data transfer rates, making them ideal for high-speed Internet access and other bandwidth-intensive applications.
-
What are the two functions of the physical layer? (Choose two.)
- It adds the sending and destination IP addresses to the message.
- It scans incoming and outgoing signals for potential security breaches.
- It provides a connection to the network through the local media.
- It provides information about the type of user application used in the transmission.
- It encodes the signal to be transported based on the requirements of the local media.
-
Answers Explanation & Hints:
The physical layer of the OSI model is responsible for the following two functions:
- It provides a physical connection to the network through the local media. This includes the transmission of bits over a communication channel, the physical components used to transmit the signals (such as cables, connectors, and repeaters), and the characteristics of the physical media (such as the maximum transmission distance and the data transfer rate).
- It encodes the signal to be transported based on the requirements of the local media. This involves transforming the digital data into a format that can be transmitted over the specific physical medium being used. The encoding method depends on the type of medium being used (such as copper wire, fiber optic cable, or wireless radio waves).
-
Refer to the exhibit. The router receives a packet with the destination IP address of 172.17.10.14. What will the router do with this packet?
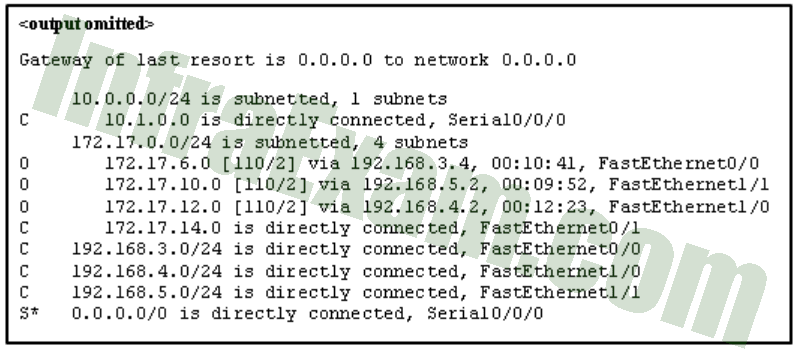
Networking Essentials 3.0 Course Final Exam Answers 01 - Forward the packet through interface FastEthernet0/1.
- Drop the packet.
- Forward the packet through interface Serial0/0/0.
- Forward the packet through interface FastEthernet1/1.
-
Answers Explanation & Hints:
Based on the routing table shown in the exhibit, the router will forward the packet through interface FastEthernet1/1 since the destination IP address 172.17.10.14 is within the subnet 172.17.10.0/24, which is directly connected to the router via the FastEthernet1/1 interface.
-
Match the IPv6 addresses to the appropriate unicast category.
- Loopback ==> 1/128
- Unspecified ==> ::/128
- Link Local ==> fe80::530:3bff:fe22:70d5
- Global Unicast ==> 2001:db8:2626:ae44:208a:8899:6060:3be6
- Unique Local ==> fc00::/7
-
Answers Explanation & Hints:
IPv6 is the latest version of the Internet Protocol (IP) that is designed to replace IPv4. It uses a 128-bit address space that allows for a large number of unique addresses to be assigned to devices on a network. IPv6 addresses are divided into different categories, each with its own characteristics and uses.
- Loopback: This is a special address that points to the device itself. The loopback address is used for testing and diagnosing network issues. In IPv6, the loopback address is represented as ::1.
- Unspecified: This address is used to represent an uninitialized or unknown address. In IPv6, the unspecified address is represented as ::.
- Link-local: This address is used for communication between devices on the same local network segment, such as a LAN. The link-local address is automatically generated based on the device’s MAC address and is represented as fe80::/10.
- Global Unicast: This address is used for communication across the Internet or other wide area networks. Global unicast addresses are routable and unique, and are assigned by Internet Assigned Numbers Authority (IANA) or a regional Internet registry. They are represented as 2000::/3.
- Unique Local: This address is similar to a private address in IPv4, and is used for communication within a private network. Unique local addresses are not routable on the public Internet, but can be used to communicate with other private networks that use the same address space. They are represented as fc00::/7.
-
Host A wants to send a message to another host on the local IPv6 network. What are the first two steps Host A will take to determine the MAC address of the receiving host? (Choose two.)
- Host A will send a neighbor solicitation message to an all-nodes multicast address (FF02::1).
- Host A will sends a neighbor advertisement message to a broadcast address.
- Host A will check its ARP table entries to see if the destination host MAC information is already in the table.
- Host A will send a router solicitation message to the all-router multicast address (FF02::2).
- Host A will review entries in its neighbor cache to see if the destination host information is already in the cache.
- Host A will send a broadcast message to all hosts on the local network.
-
Answers Explanation & Hints:
The correct options are:
- Host A will send a neighbor solicitation message to an all-nodes multicast address (FF02::1).
- Host A will review entries in its neighbor cache to see if the destination host information is already in the cache.
When a host needs to send a message to another host on the same IPv6 network, it needs to determine the MAC address of the destination host to be able to send the message on the local network. To do this, Host A will send a neighbor solicitation message to the all-nodes multicast address (FF02::1), asking the receiving host to send a neighbor advertisement message with its MAC address. The neighbor solicitation message includes the IPv6 address of the destination host.
If Host A has previously communicated with the destination host, it might have the MAC address information cached in its neighbor cache. So, Host A will review the entries in its neighbor cache to see if the destination host information is already in the cache. If the MAC address is already in the neighbor cache, Host A can use it to send the message to the destination host.
-
A user purchases a new switch for the home office to accommodate faster speeds for a newly purchased laptop. The controller has 10/100/1000 MBPS ports, and the computer comes with a 10/100 NIC. What actual bandwidth will the laptop receive if it is plugged into a port on the switch?
- 100 MBPS
- 10 MBPS
- The laptop will not connect.
- 1000 MBPS
-
Answers Explanation & Hints:
The laptop will receive a maximum bandwidth of 100 MBPS since its NIC supports speeds up to 100 MBPS, which is the maximum speed that it can transmit or receive data from the network. Although the switch has 10/100/1000 MBPS ports, the laptop’s NIC cannot support the higher speed.
-
What are the two main functions of a layer 2 switch? (Choose two.)
- To provide payload scanning on the local network.
- To connect local devices to a default gateway.
- To provide wireless connectivity to the home network.
- To connect multiple remote routers to gigabit ports.
- To connect end-user devices on the same local network.
-
Answers Explanation & Hints:
A layer 2 switch is a networking device that operates at the data link layer (layer 2) of the OSI model. Its primary function is to connect end-user devices on the same local network, allowing these devices to communicate with each other.
The layer 2 switch works by reading the destination MAC address in the incoming Ethernet frame and then forwarding the frame only to the port that is connected to the destination device. This process is known as “switching” and is much faster than traditional network bridges, which operate at the same layer.
Another key function of a layer 2 switch is to provide network segmentation, which helps to improve network performance and security. By dividing a large network into smaller, more manageable segments, layer 2 switches can reduce network congestion and prevent network broadcasts from affecting all devices on the network.
In summary, the two main functions of a layer 2 switch are to connect end-user devices on the same local network and to provide network segmentation to improve network performance and security.
-
Which switch forwarding method provides the lowest latency?
- store-and-forward
- fast-forward
- store-and-forward with error checking disabled
- fragment-free
-
Answers Explanation & Hints:
The switch forwarding method with the lowest latency is “fast-forward.”
Fast-forward switching is a method where the switch begins forwarding a packet as soon as the destination MAC address is read. The switch does not wait for the entire frame to be received before forwarding, which results in lower latency and higher throughput. This method is commonly used in switches that have a higher bandwidth than the traffic volume they need to process.
In contrast, store-and-forward switching stores the entire frame in a buffer and performs a CRC error check before forwarding. This method introduces additional latency due to the error checking and waiting for the entire frame to be received before forwarding.
Fragment-free switching is a variant of store-and-forward switching where the switch only stores the first 64 bytes of the frame, which includes the frame header. This method reduces latency compared to store-and-forward but is slower than fast-forward switching.
-
Which three solutions are examples of physical access control? (Choose three.)
- protocol
- password
- motion detector
- smart card
- mantrap-style entry system
- video camera
-
Answers Explanation & Hints:
The three solutions that are examples of physical access control are:
- Motion detector: This device detects motion and can be used to trigger an alarm or open a door only when a person is detected.
- Smart card: This is a physical object, similar to a credit card, that contains an embedded microchip or magnetic stripe with information about the user. The smart card can be used to gain access to a building, room or network.
- Mantrap-style entry system: This is a physical access control system that uses a series of doors or gates to control the flow of people into a secure area. A person must be granted access through each door or gate to gain entry to the secure area.
-
Which is the advantage of using an automated patch service on an enterprise network?
- Administrators can obtain reports on the updates needed by each system.
- Each computer needs to connect to the vendor’s service to download patches.
- Administrators can only approve updates with the consent of the users.
- Users can disable or circumvent updates.
-
Answers Explanation & Hints:
The advantage of using an automated patch service on an enterprise network is that administrators can obtain reports on the updates needed by each system. This helps administrators to ensure that all systems are up to date with the latest security patches and fixes, which can improve overall security and reduce the risk of data breaches or other security incidents. Automated patching can also save time and reduce the workload for IT staff, as patches can be applied quickly and easily across all systems.
-
Which Apple security feature ensures that only authentic, digitally-signed software that an Apple-notarized software developer has created is permitted to be installed?
- Gatekeeper
- XProtect
- MRT
- Security-focused hardware
-
Answers Explanation & Hints:
Gatekeeper is an Apple security feature that ensures that only authentic, digitally-signed software that an Apple-notarized software developer has created is permitted to be installed. This is done by enforcing code signing and verifying that the digital signature of an application matches the developer’s signature, or the signature of the app’s designated distribution channel. Gatekeeper provides three security levels to choose from: App Store only, App Store and identified developers, and Anywhere. The default setting is “App Store and identified developers,” which means that only applications downloaded from the App Store or signed by identified developers are allowed to run. This feature helps to protect against malware and other malicious software by limiting the sources of software that can be installed on a Mac.
-
What is a characteristic of a nftables host-based firewall?
- to use a simple virtual machine in the Linux kernel
- to use a profile-based approach to firewall functionality
- to allow Linux system administrators to configure network access rules that are part of the Linux kernel Netfilter modules
- to be a rule-based access control and logging system for Linux
-
Answers Explanation & Hints:
nftables is a rule-based access control and logging system for Linux, which is used to configure network access rules that are part of the Linux kernel Netfilter modules. It provides the ability to filter and manipulate network traffic by creating and manipulating rules and filtering criteria. Unlike iptables, nftables uses a simpler syntax and provides more functionality, such as supporting IPv6 natively, being able to use sets, maps, and expressions, and providing better logging and monitoring capabilities. Therefore, nftables is a popular choice for Linux system administrators to configure host-based firewalls.
-
Which statement describes an advanced persistent threat (APT)?
- an attack by threat actors performing unauthorized network probing and port scanning on the targeted network
- an attack that modifies the operating system through malware and creates a backdoor on the infected system
- an attack that takes advantage of algorithms in a piece of legitimate software to generate unintended behaviors
- a continuous attack that uses elaborated espionage tactics involving multiple threat actors and sophisticated malware to gain access to the targeted network
-
Answers Explanation & Hints:
An advanced persistent threat (APT) is a continuous, targeted and sophisticated attack on a network or system, often involving multiple threat actors and sophisticated malware. The attack is usually carried out over a long period of time, during which the attackers gather intelligence about the target and use this information to gain unauthorized access to sensitive data. APTs are often associated with state-sponsored attacks, although they can also be carried out by criminal organizations or other types of threat actors.
-
Which application attack replaces a Windows code file with a malicious one and launches an attack when a Windows application calls the code file?
- Replay
- XML injection
- LDAP injection
- DLL injection
-
Answers Explanation & Hints:
The application attack that replaces a Windows code file with a malicious one and launches an attack when a Windows application calls the code file is known as DLL injection.
-
Which two actions demonstrate effective active listening techniques when assisting a customer with a problem? (Choose two.)
- correcting the customer when they use incorrect technical terms or jargon
- stopping the customer so you can ask questions as you think of them
- re-asking questions the customer has already answered when describing the problem
- allowing the customer to explain the problem
- Let the customer know that you are listening by interjecting phrases such as “I understand,” “I see,” and “OK.”
-
Answers Explanation & Hints:
Allowing the customer to explain the problem and letting the customer know that you are listening by interjecting phrases such as “I understand,” “I see,” and “OK” are effective active listening techniques when assisting a customer with a problem.
-
A trouble ticket placed by a Ubuntu Linux user states that the wired network connection on the computer intermittently fails. Which command can be entered at the Linux CLI to quickly see the number of transmit and receive errors occurring on the Ethernet interface?
- ipconfig /all
- show interfaces eth0
- ifconfig
- show ip interface brief
-
Answers Explanation & Hints:
The correct command to view the number of transmit and receive errors on a Ubuntu Linux computer is:
ifconfig eth0
This command displays the network configuration of the eth0 interface, including the number of packets transmitted and received, as well as any errors that may have occurred. The user can then use this information to troubleshoot the intermittent network connection issue.
-
A user reports that the computer occasionally loses connectivity when streaming videos from the web. The technician suspects that a network hardware issue may exist in a device located between the computer and the internet edge router. Which documentation would the technician use to determine where network devices are located in the path from the user to the edge router?
- three-layer enterprise network design model
- logical topology map
- cloud service architecture diagram
- physical topology map
-
Answers Explanation & Hints:
The technician would use a physical topology map to determine where network devices are located in the path from the user to the edge router. A physical topology map provides a visual representation of the physical location of network devices and how they are connected to each other, which can help to identify the devices that are located between the user’s computer and the edge router. This information can be used to troubleshoot network connectivity issues and identify potential hardware problems.
-
Which statement accurately describes the measurement of the speed of network transmissions between a client and a server?
- Throughput equals the combined bandwidth of the links in the path from the client to the server.
- Bandwidth equals the speed at which a file can be downloaded from a server to a client.
- Internet speed tests measure the bandwidth of the links between a client and a server.
- Throughput is lower than bandwidth due to latency from client to server.
-
Answers Explanation & Hints:
Like bandwidth, throughput is the measure of the transfer of bits across the media over a given period of time. However, due to a number of factors, throughput does not usually match the specified bandwidth. Many factors influence throughput including:
- The amount of data being sent and received over the connection
- The types of data being transmitted
- The latency created by the number of network devices encountered between source and destination
Latency refers to the amount of time, including delays, for data to travel from one given point to another.
-
What are two characteristics of a remote-access SSL VPN? (Choose two.)
- clients have no awareness of the VPN
- a VPN gateway device is needed at both ends of the VPN tunnel
- the client initiates the VPN connection
- the VPN is established between the client PC and a VPN gateway
- traffic between the client and VPN gateway is sent in clear text
-
Answers Explanation & Hints:
The two characteristics of a remote-access SSL VPN are:
- The client initiates the VPN connection.
- The VPN is established between the client PC and a VPN gateway.
Clients have awareness of the VPN and a VPN gateway device is needed at only one end of the VPN tunnel. Traffic between the client and VPN gateway is encrypted, not sent in clear text.