Networking Essentials (Version 2) – Modules 17 – 20: Introduction to Cisco Networking Group Exam Answers
Networking Essentials (Version 2) – Modules 17 – 20: Introduction to Cisco Networking Group Exam Answers Full 100% 2021
-
What type of cable is used to connect a workstation serial port to a Cisco router console port?
- crossover
- rollover
- straight-through
- coaxial
Answers Explanation & Hints: UTP cable wire pairs can be terminated in different configurations for use in different applications. To use a UTP cable for consoling into a Cisco router from a PC serial port, it must be terminated as a rollover or console cable.
-
What are two requirements when using out-of-band configuration of a Cisco IOS network device? (Choose two.)
- HTTP access to the device
- a terminal emulation client
- Telnet or SSH access to the device
- a direct connection to the console or AUX port
- a connection to an operational network interface on the device
Answers Explanation & Hints: A connection to an operational network interface on the device, and Telnet, SSH, or HTTP access are required for in-band management of Cisco IOS networking devices.
-
When is an IP address required to be configured on a Cisco LAN switch?
- when the switch is connected to another switch
- when the switch must forward LAN traffic
- when the switch needs to be managed through an in-band connection
- when the switch is configured from a computer connected to the console port
Answers Explanation & Hints: A LAN switch uses Layer 2 addresses to determine how to forward packets. An IP address is only necessary if the switch needs to be remotely managed through an in-band connection on the network.
-
When a router is powered on, where will the router first search for a valid IOS image to load by default?
- RAM
- ROM
- flash memory
- NVRAM
Answers Explanation & Hints: By default, if no boot system commands are in the configuration, a router will load the first valid Cisco IOS image in flash memory and run it. RAM is active memory that is not used to store image files. NVRAM stores configuration files. ROM stores a minimal version of the Cisco IOS image that can be used to provide limited functions if a valid IOS image is not available in flash memory.
-
Following default settings, what two tasks are performed first in the router boot sequence? (Choose two.)
- Perform the POST routine.
- Locate and load the startup-config file from NVRAM.
- Load the bootstrap program from ROM.
- Load the running-config file from RAM.
- Locate and load the operating system.
Answers Explanation & Hints: There are three major steps to the router boot sequence:
- Perform Power-On-Self-Test (POST) and load the bootstrap program.
- Load the IOS from Flash or TFTP server.
- Load the startup configuration file from NVRAM.
-
Match the configuration mode with the command that is available in that mode. (Not all options are used.)
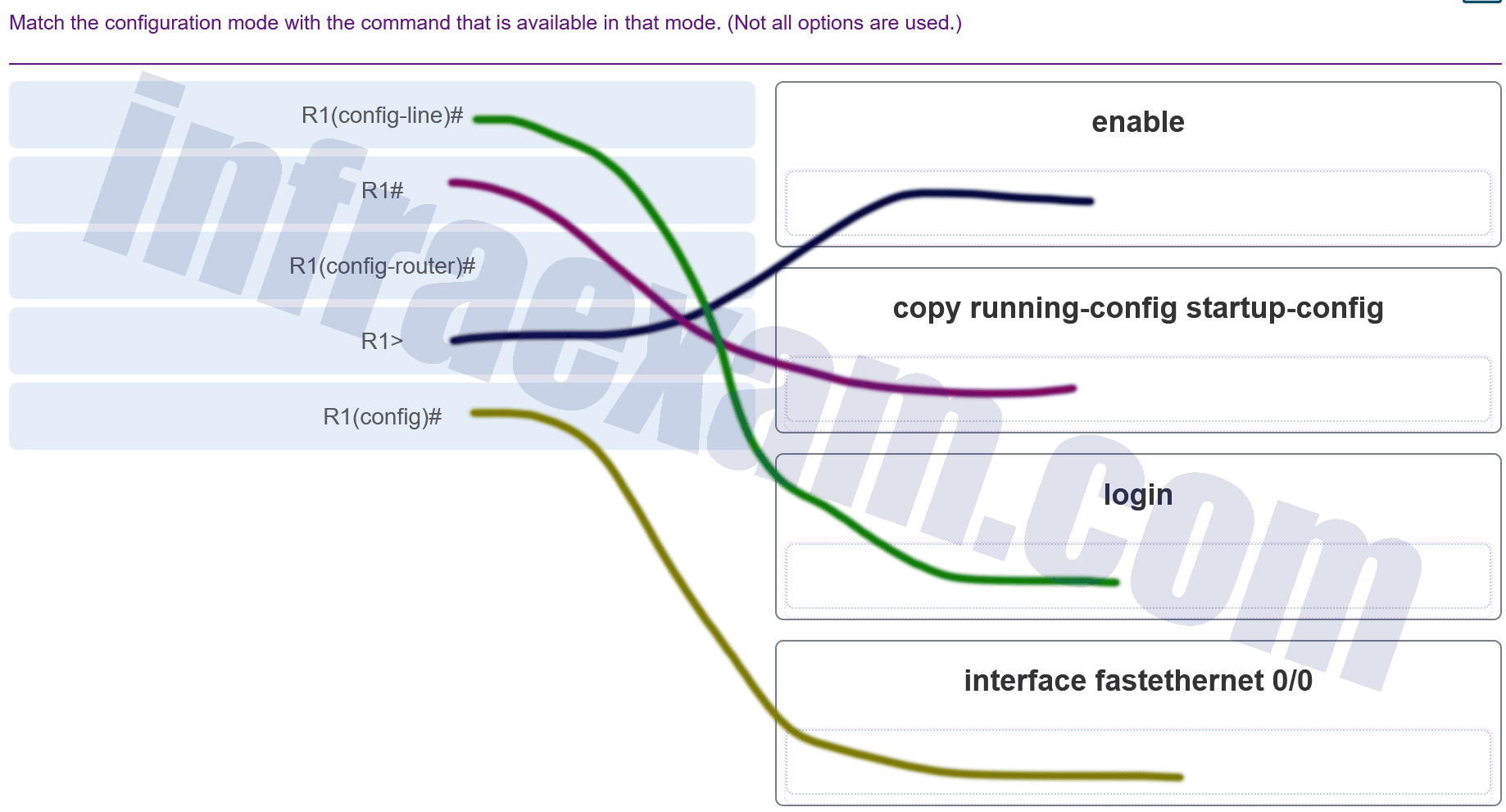
Modules 17 – 20 Introduction to Cisco Networking Group Exam Answers 001 Answers Explanation & Hints: The enable command is entered at the R1> prompt. The login command is entered at the R1(config-line)# prompt. The copy running-config startup-config command is entered at the R1# prompt. The interface fastethernet 0/0 command is entered at the R1(config)# prompt.
-
A network administrator is working on a Cisco router. The CLI prompt is Router1(config-if)#. Which operation is the administrator likely to configure next?
- the vty lines
- a LAN interface
- the console port
- the password that is required to access the privileged EXEC mode
Answers Explanation & Hints: Cisco IOS uses different prompts to identify the specific configuration modes. The prompt Router1(config-if)# is a subconfiguration mode of Router(config)#. This mode indicates that the configuration commands that follow are applied to a LAN or WAN interface.
-
To save time, IOS commands may be partially entered and then completed by typing which key or key combination?
- Tab
- Ctrl-P
- Ctrl-N
- Up Arrow
- Right Arrow
- Down Arrow
-
A network administrator issues the Switch# show running-config command on a Cisco switch. Which term is used to describe the part ” running-config” in the command?
- hot key
- keyword
- argument
- command
Answers Explanation & Hints: The running-config is a keyword of the show command.
-
Refer to the exhibit. Which element of IOS syntax is the expression MainOffice ?

- a command
- a keyword
- an argument
- a subcommand
Answers Explanation & Hints: An argument of a CLI command is generally not a predefined word, but rather is a value defined by the user. Keywords, however, describe specific parameters of a command that are predefined words that are known to the command interpreter.
-
A network administrator is troubleshooting inter-connection issues between routers. Which show command can be used to check the bandwidth and MTU settings of an interface?
- show arp
- show ip route
- show protocols
- show interfaces
Answers Explanation & Hints: The show interfaces command displays the hardware settings of each interface, such as MTU, MAC address, and bandwidth.
-
What is the purpose of assigning an IP address to the VLAN1 interface on a Cisco Layer 2 switch?
- to create a new IP local network on the switch
- to permit IP packets to be forwarded by the switch
- to enable remote access to the switch to manage it
- to enable the switch to route packets between networks
Answers Explanation & Hints: The VLAN 1 on a Cisco Layer 2 switch is a virtual interface. By default, VLAN 1 is assigned as the management interface for remote access (Telnet or SSH) to the device for management tasks. In order to allow remote access through the network, a valid IP address configuration is needed on VLAN 1.
-
Match the type of password on a Cisco device to the function.
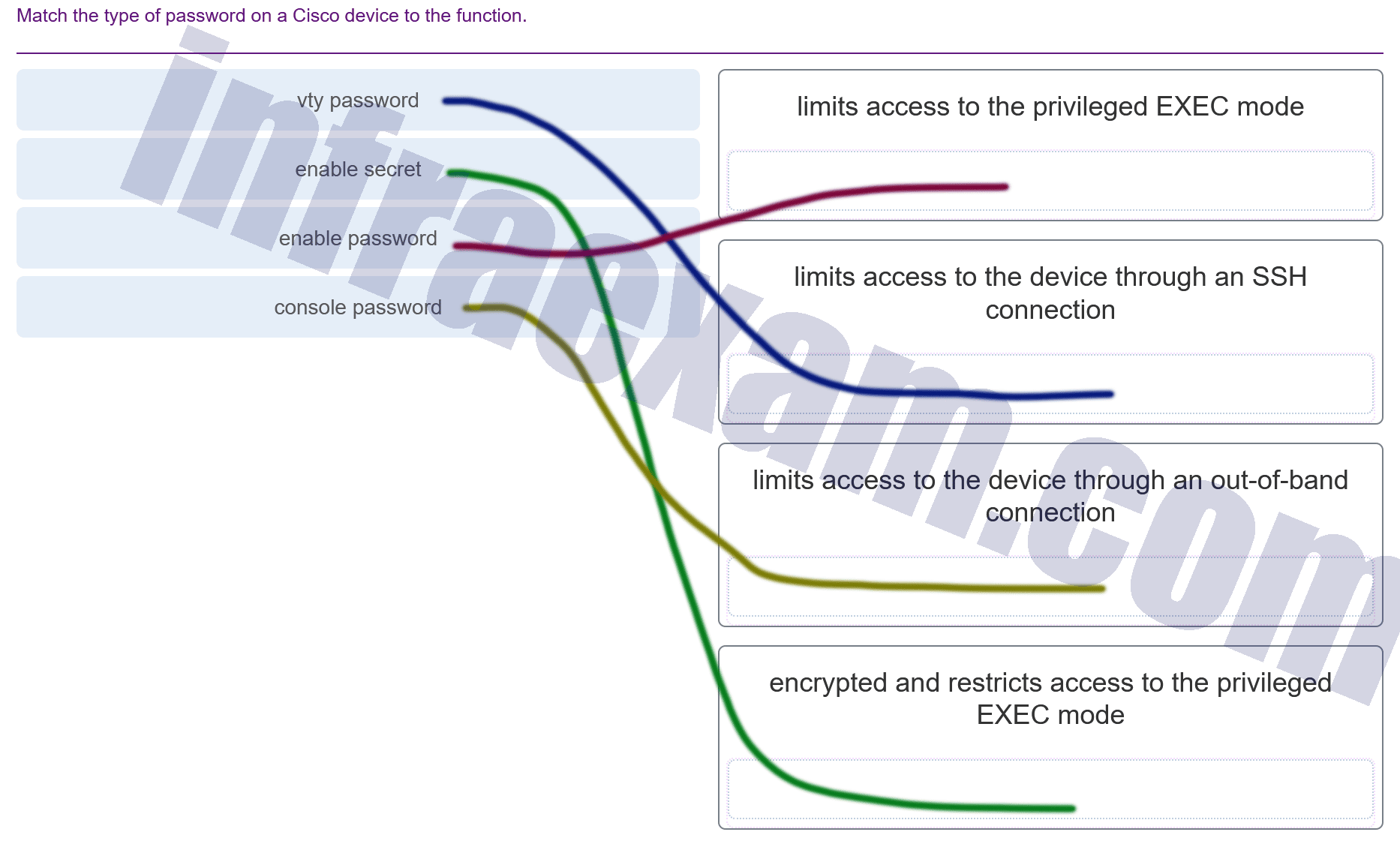
Modules 17 – 20 Introduction to Cisco Networking Group Exam Answers 002 -
Which statement regarding the service password-encryption command is true?
- It is configured in privileged EXEC mode.
- It encrypts only line mode passwords.
- As soon as the service password-encryption command is entered, all currently set passwords formerly displayed in plain text are encrypted.
- To see the passwords encrypted by the service password-encryption command in plain text, issue the no service password-encryption command.
Answers Explanation & Hints: The command service password-encryption is used to encrypt all the clear text passwords in the running-configuration file.
-
Passwords can be used to restrict access to all or parts of the Cisco IOS. Select the modes and interfaces that can be protected with passwords. (Choose three.)
- VTY interface
- console interface
- Ethernet interface
- boot IOS mode
- privileged EXEC mode
- router configuration mode
Answers Explanation & Hints: Access to the VTY and console interfaces can be restricted using passwords. Out-of-band management of the router can be restricted in both user EXEC and privileged EXEC modes.
-
An administrator defined a local user account with a secret password on router R1 for use with SSH. Which three additional steps are required to configure R1 to accept only encrypted SSH connections? (Choose three.)
- Configure the IP domain name on the router.
- Enable inbound vty Telnet sessions.
- Generate the SSH keys.
- Configure DNS on the router.
- Enable inbound vty SSH sessions.
- Generate two-way pre-shared keys.
Answers Explanation & Hints: There are four steps to configure SSH support on a Cisco router:
Step 1: Set the domain name.
Step 2: Generate one-way secret keys.
Step 3: Create a local username and password.
Step 4: Enable SSH inbound on a vty line.
-
What advantage does SSH offer over Telnet?
- encryption
- more connection lines
- connection-oriented services
- username and password authentication
Answers Explanation & Hints: Both Telnet and SSH are used to remotely connect to a network device for management tasks. However, Telnet uses plaintext communications, whereas SSH provides security for remote connections by providing encryption of all transmitted data between devices.
-
A user can print to a printer that is on the same network, but the traffic of the user cannot reach the Internet. What is a possible cause of the problem?
- The PC default gateway address is missing or incorrect.
- The PC has an incorrect IP address.
- The network cable connected to the user PC is faulty.
- The NIC on the PC is faulty.
Answers Explanation & Hints: The default gateway IP address is used to reach other networks, including the Internet.
-
For the second time in a week, workstations on a LAN are not able to log into a specific server. The technician fixed the problem the first time, but cannot remember the steps taken to solve it. What aspect of the troubleshooting process has the technician neglected?
- identifying the problem
- asking questions of end users
- documenting the troubleshooting process
- using structured techniques to solve a problem
Answers Explanation & Hints: Proper documentation is a very important step in troubleshooting. The proper documentation can help troubleshoot the same or similar problems in the future.
-
Which utility can be used to view a list of open TCP connections on Linux or Windows systems?
- Tracert
- Ping
- Netstat
- Ipconfig
Answers Explanation & Hints: Netstat is a utility that is available for both Linux and Windows systems. It is a utility that can be used to indicate that something or someone is connected to the local host. It lists the protocol in use, the local address and port numbers, the foreign address and port numbers, and the state of the connection.
-
Which three pieces of information are revealed by the ipconfig command (without the /all switch)? (Choose three.)
- IP address
- DHCP server
- subnet mask
- default gateway
- DNS server
- MAC address
Answers Explanation & Hints: The ipconfig command is used to display the current TCP/IP network configuration values of the device. This includes the IP address; the subnet mask and the default gateway addresses. Using the ipconfig /all switch displays additional information like the physical address of the device and the DHCP server address among other things.
-
Which command can be used to verify connectivity between two host devices?
- ipconfig
- ping
- netstat
- nslookup
Answers Explanation & Hints: The ping command can be used to test end-to-end connectivity between two host devices. It measures the round-trip time for a message to get from source to destination.
-
How does an activity LED on wireless routers indicate that traffic is moving through a port?
- by flashing
- by staying turned off
- by staying a solid green color
- by staying a solid amber color
Answers Explanation & Hints: One of the first steps when using the bottom-up strategy of troubleshooting is to examine the LED lights of the device, which indicate the current state or activity of the device. LEDs may change color or flash to convey information. Although the exact configuration and meaning of LEDs varies between manufacturers and devices, a flashing light indicates flow of traffic.
-
A user experiences access and performance issues with the Internet connection from a home computer. The Internet connection is provided through a DSL line. The user calls the support line of the phone company for help. The support technician asks the user to connect the computer directly to the DSL modem. Which two pieces of information will help the technician to troubleshoot the problem? (Choose two.)
- when the problem started
- the model and vendor of the computer
- the IP address of the computer
- the MAC address of the Ethernet NIC on the computer
- the number of times that the ping command was issued
Answers Explanation & Hints: The timeline and the IP address will help the technician to troubleshoot and test to verify the problem. The timeline can be used to check the operation status of the DSL equipment in the phone company. The IP address can be used to verify if the DHCP is functional from the phone company. The MAC address of the Ethernet NIC is irrelevant because the connection is not an Ethernet connection. The technician should not assume that a client is technically savvy. If the ping command is necessary, the technician should instruct the client on how to issue the ping command.