CAPM : Certified Associate in Project Management (PMI-100) : Part 39
CAPM : Certified Associate in Project Management (PMI-100) : Part 39
-
What is the minimum a project schedule must include?
- Variance analysis
- A planned start date and a planned finish date for each schedule activity
- A critical path diagram
- Critical chain analysis
-
What is the tool and technique used to request seller responses?
- Procurement documents
- Expert judgment
- Bidder conferences
- Contract types
Explanation:
12.2.2.1 Bidder Conferences
Bidder conferences (sometimes called contractor conferences, vendor conferences, and pre-bid conferences) are meetings between the buyer and all prospective sellers prior to submittal of a bid or proposal.
They are used to ensure that all prospective sellers have a clear and common understanding of the procurement requirements, and that no bidders receive preferential treatment.
To be fair, buyers should take great care to ensure that all prospective sellers hear every question from any individual prospective seller and every answer from the buyer.
Typically fairness is addressed by techniques such as collecting questions from bidders or arranging field visits in advance of the bidder conference. Responses to questions can be incorporated into the procurement documents as amendments. -
What process determines which risks might affect the project?
- Qualitative risk analysis
- Identify Risks
- Plan Risk Management
- Quantitative risk analysis
Explanation:Process: 11.2 Identify Risks
Definition: The process of determining which risks may affect the project and documenting their characteristics.
Key Benefit: The key benefit of this process is the documentation of existing risks and the knowledge and ability it provides to the project team to anticipate events.Inputs
1. Risk management plan
2. Cost management plan
3. Schedule management plan
4. Quality management plan
5. Human resource management plan
6. Scope baseline
7. Activity cost estimates
8. Activity duration estimates
9. Stakeholder register
10. Project documents
11. Procurement documents
12. Enterprise environmental factors
13. Organizational process assets
Tools & Techniques
1. Documentation reviews
2. Information gathering techniques
3. Checklist analysis
4. Assumptions analysis
5. Diagramming techniques
6. SWOT analysis
7. Expert judgmentOutputs
1. Risk register11.2.3.1 Risk Register
The primary output from Identify Risks is the initial entry into the risk register. The risk register is a document in which the results of risk analysis and risk response planning are recorded. It contains the outcomes of the other risk management processes as they are conducted, resulting in an increase in the level and type of information contained in the risk register over time. The preparation of the risk register begins in the Identify Risks process with the following information, and then becomes available to other project management and risk management processes:
– List of identified risks. The identified risks are described in as much detail as is reasonable. A structure for describing risks using risk statements may be applied, for example, EVENT may occur causing IMPACT, or If CAUSE exists, EVENT may occur leading to EFFECT. In addition to the list of identified risks, the root causes of those risks may become more evident. These are the fundamental conditions or events that may give rise to one or more identified risks. They should be recorded and used to support future risk identification for this and other projects.
– List of potential responses. Potential responses to a risk may sometimes be identified during the Identify Risks process. These responses, if identified in this process, should be used as inputs to the Plan Risk Responses process. -
What scope definition technique is used to generate different approaches to execute and perform the work of the project?
- Build vs. buy
- Expert judgment
- Alternatives identification
- Product analysis
-
When a control chart is used to monitor performance of a process, which of the following will be set by the project manager and the appropriate stakeholders to reflect the point(s) at which corrective action will be taken to prevent exceeding the specification limits?
- Upper and lower control limits
- Upper and lower specification limits
- Process mean
- Data points
-
Where are product requirements and characteristics documented?
- Product scope description
- Project charter
- Preliminary project scope statement
- Communications management plan
Explanation:
Product scope description. The product scope description documents the characteristics of the product, service, or results that the project will be undertaken to create. The description should also document the relationship between the products, services, or results being created and the business need that the project will address. -
Which Activity Duration Estimating technique incorporates additional timing for contingency purposes?
- Analogous Estimating
- Expert Judgment
- Optimistic Estimates
- Reserve Analysis
Explanation:
6.5.2.6 Reserve Analysis
Duration estimates may include contingency reserves, sometimes referred to as time reserves or buffers, into the project schedule to account for schedule uncertainty. Contingency reserves are the estimated duration within the schedule baseline, which is allocated for identified risks that are accepted and for which contingent or mitigation responses are developed. Contingency reserves are associated with the “known-unknowns,” which may be estimated to account for this unknown amount of rework.
As more precise information about the project becomes available, the contingency reserve may be used, reduced, or eliminated. Contingency should be clearly identified in schedule documentation.
[..]
Estimates may also be produced for the amount of management reserve of time for the project. Management reserves are a specified amount of the project duration withheld for management control purposes and are reserved for unforeseen work that is within scope of the project. Management reserves are intended to address the “unknown-unknowns” that can affect a project. Management reserve is not included in the schedule baseline, but it is part of the overall project duration requirements. Depending on contract terms, use of management reserves may require a change to the schedule baseline. -
Which characteristic is unique to project work and does not apply to operational work?
- Performed by individuals
- Limited by constraints
- Temporary
- Performed to achieve organizational objectives
-
Which document describes the procurement item in sufficient detail to allow prospective sellers to determine if they are capable of providing the products, services, or results?
- Procurement management plan
- Procurement statement of work
- Request for proposal
- Request for quote
Explanation:
12.1.3.2 Procurement Statement of Work
The statement of work (SOW) for each procurement is developed from the project scope baseline and defines only that portion of the project scope that is to be included within the related contract. The procurement SOW describes the procurement item in sufficient detail to allow prospective sellers to determine if they are capable of providing the products, services, or results. Sufficient detail can vary based on the nature of the item, the needs of the buyer, or the expected contract form. Information included in a SOW can include specifications, quantity desired, quality levels, performance data, period of performance, work location, and other requirements.
The procurement SOW is written to be clear, complete, and concise. It includes a description of any collateral services required, such as performance reporting or post-project operational support for the procured item. In some application areas, there are specific content and format requirements for a procurement SOW. Each individual procurement item requires a SOW; however, multiple products or services can be grouped as one procurement item within a single SOW.
The procurement SOW can be revised and refined as required as it moves through the procurement process until incorporated into a signed agreement. -
Which is a tool used in monitoring and controlling project work?
- Work performance information
- Project management information system (PMIS)
- Activity duration estimates
- Scheduled network analysis
-
Which is an input to the Scope Verification Process?
- Performance report
- Work breakdown structure
- Requested changes
- Project scope statement
Explanation:
The project team must complete a scope statement for developing a common understanding of the project scope among stakeholders. This lists project deliverables – summary level sub-products, whose full and satisfactory delivery marks the completion of the project -
Which is the document that presents a hierarchical project organization?
- WBS
- CPI
- OBS
- BOM
-
Which knowledge area employs the processes required to ensure timely and appropriate generation, collection, distribution, storage, retrieval, and ultimate disposition of project information?
- Project Risk Management
- Project Integration Management
- Project Communications Management
- Project Quality Management
Explanation:
PROJECT COMMUNICATIONS MANAGEMENT
Project Communications Management includes the processes that are required to ensure timely and appropriate planning, collection, creation, distribution, storage, retrieval, management, control, monitoring, and the ultimate disposition of project information. Project managers spend most of their time communicating with team members and other project stakeholders, whether they are internal (at all organizational levels) or external to the organization.
Effective communication creates a bridge between diverse stakeholders who may have different cultural and
organizational backgrounds, different levels of expertise, and different perspectives and interests, which impact or have an influence upon the project execution or outcome. -
Which of following could be organizational process assets?
- Historical information
- Industry standards
- Organization infrastructure
- Marketplace conditions
Explanation:
2.1.4 Organizational Process Assets
Organizational process assets are the plans, processes, policies, procedures, and knowledge bases specific to and used by the performing organization. They include any artifact, practice, or knowledge from any or all of the organizations involved in the project that can be used to perform or govern the project. The process assets also include the organization’s knowledge bases such as lessons learned and historical information. Organizational process assets may include completed schedules, risk data, and earned value data. Organizational process assets are inputs to most planning processes. Throughout the project, the project team members may update and add to the organizational process assets as necessary. Organizational process assets may be grouped into two categories: (1) processes and procedures, and (2) corporate knowledge base. -
Which of the following are documented directions to perform an activity that can reduce the probability of negative consequences associated with project risks?
- Recommended corrective actions
- Recommended preventive actions
- Risk audits
- Risk reassessments
Explanation:
11.6.3.2 Change Requests
Implementing contingency plans or workarounds sometimes results in a change request. Change requests are prepared and submitted to the Perform Integrated Change Control process (Section 4.5). Change requests can include recommended corrective and preventive actions as well.
– Recommended corrective actions. These are activities that realign the performance of the project work with the project management plan. They include contingency plans and workarounds. The latter are responses that were not initially planned, but are required to deal with emerging risks that were previously unidentified or accepted passively.
– Recommended preventive actions. These are activities that ensure that future performance of the project work is aligned with the project management plan. -
Which of the following are examples of interactive communication?
- Intranet sites
- Voice mails
- Video conferences
- Press releases
-
Which of the following are the components of the scope baseline?
- Project charter, project scope statement, and work breakdown structure (WBS)
- Project charter, project management plan, and plan procurement
- Project scope statement, work breakdown structure (WBS), and WBS dictionary
- Project management plan, plan procurement, and contract administration
Explanation:
5.4.3.1 Scope Baseline
The scope baseline is the approved version of a scope statement, work breakdown structure (WBS), and its
associated WBS dictionary, that can be changed only through formal change control procedures and is used as a
basis for comparison. It is a component of the project management plan. Components of the scope baseline include:
– Project scope statement. The project scope statement includes the description of the project scope, major deliverables, assumptions, and constraints.
– WBS. The WBS is a hierarchical decomposition of the total scope of work to be carried out by the project team to accomplish the project objectives and create the required deliverables. Each descending level of the WBS represents an increasingly detailed definition of the project work. The WBS is finalized by assigning each work package to a control account and establishing a unique identifier for that work package from a code of accounts. These identifiers provide a structure for hierarchical summation of costs, schedule, and resource information. A control account is a management control point where scope, budget, actual cost, and schedule are integrated and compared to the earned value for performance measurement. Control accounts are placed at selected management points in the WBS. Each control account may include one or more work packages, but each of the work packages should be associated with only one control account. A control account may include one or more planning packages. A planning package is a work breakdown structure component below the control account with known work content but without detailed schedule activities.
– WBS dictionary. The WBS dictionary is a document that provides detailed deliverable, activity, and scheduling information about each component in the WBS. The WBS dictionary is a document that supports the WBS. Information in the WBS dictionary may include, but is not limited to:
– Code of account identifier,
– Description of work,
– Assumptions and constraints,
– Responsible organization,
– Schedule milestones,
– Associated schedule activities,
– Resources required,
– Cost estimates,
– Quality requirements,
– Acceptance criteria,
– Technical references, and
– Agreement information. -
Which of the following buffers protects the target finish date from slippage along the critical chain?
- Critical buffer
- Project buffer
- Duration buffer
- Feeding buffer
Explanation:6.6.2.3 Critical Chain Method
The critical chain method (CCM) is a schedule method that allows the project team to place buffers on any project schedule path to account for limited resources and project uncertainties. It is developed from the critical path method approach and considers the effects of resource allocation, resource optimization, resource leveling, and activity duration uncertainty on the critical path determined using the critical path method. To do so, the critical chain method introduces the concept of buffers and buffer management. The critical chain method uses activities with durations that do not include safety margins, logical relationships, and resource availability with statistically determined buffers composed of the aggregated safety margins of activities at specified points on the project schedule path to account for limited resources and project uncertainties. The resource-constrained critical path is known as the critical chain.
The critical chain method adds duration buffers that are non-work schedule activities to manage uncertainty.
One buffer, placed at the end of the critical chain, as shown in Figure 6-19, is known as the project buffer and protects the target finish date from slippage along the critical chain. Additional buffers, known as feeding buffers, are placed at each point where a chain of dependent activities that are not on the critical chain feeds into the critical chain. Feeding buffers thus protect the critical chain from slippage along the feeding chains. The size of each buffer should account for the uncertainty in the duration of the chain of dependent activities leading up to that buffer. Once the buffer schedule activities are determined, the planned activities are scheduled to their latest possible planned start and finish dates. Consequently, instead of managing the total float of network paths, the critical chain method focuses on managing the remaining buffer durations against the remaining durations of chains of activities.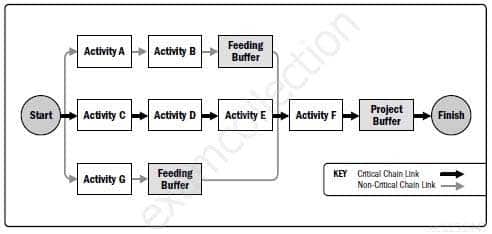
CAPM Certified Associate in Project Management (PMI-100) Part 39 Q18 025 Figure 6-19. Example of Critical Chain Method
-
Which of the following correctly describes when organizations and stakeholders are willing to accept varying degrees of risk?
- Risk analysis
- Risk tolerance
- Risk management
- Risk attitude
Explanation:11 PROJECT RISK MANAGEMENT
[..]
Organizations perceive risk as the effect of uncertainty on projects and organizational objectives. Organizations and stakeholders are willing to accept varying degrees of risk depending on their risk attitude. The risk attitudes of both the organization and the stakeholders may be influenced by a number of factors, which are broadly classifed into three themes:– Risk appetite, which is the degree of uncertainty an entity is willing to take on in anticipation of a reward.
– Risk tolerance, which is the degree, amount, or volume of risk that an organization or individual will withstand.
Risk threshold, which refers to measures along the level of uncertainty or the level of impact at which a stakeholder may have a specific interest. Below that risk threshold, the organization will accept the risk. Above that risk threshold, the organization will not tolerate the risk.
For example, an organization’s risk attitude may include its appetite for uncertainty, its threshold for risk levels that are unacceptable, or its risk tolerance at which point the organization may select a different risk response.
Positive and negative risks are commonly referred to as opportunities and threats. The project may be accepted if the risks are within tolerances and are in balance with the rewards that may be gained by taking the risks. Positive risks that offer opportunities within the limits of risk tolerances may be pursued in order to generate enhanced value. For example, adopting an aggressive resource optimization technique is a risk taken in anticipation of a reward for using fewer resources. -
Which of the following correctly lists the configuration management activities included in the Integrated Change Control process?
- Configuration definition, configuration status accounting, configuration monitoring and control
- Configuration identification, configuration status accounting, configuration verification and audit
- Configuration identification, configuration status reporting, configuration verification and audit
- Configuration definition, configuration status reporting, configuration monitoring and Control
Explanation:Configuration control is focused on the specification of both the deliverables and the processes; while change control is focused on identifying, documenting, and approving or rejecting changes to the project documents, deliverables, or baselines.
Some of the configuration management activities included in the Perform Integrated Change Control process are as follows:– Configuration identification. Identification and selection of a configuration item to provide the basis for which the product configuration is defined and verified, products and documents are labeled, changes are managed, and accountability is maintained.
– Configuration status accounting. Information is recorded and reported as to when appropriate data about the configuration item should be provided. This information includes a listing of approved configuration identification, status of proposed changes to the configuration, and the implementation status of approved changes.– Configuration verification and audit. Configuration verification and configuration audits ensure the composition of a project’s configuration items is correct and that corresponding changes are registered, assessed, approved, tracked, and correctly implemented. This ensures the functional requirements defined in the configuration documentation have been met.