MD-100 : Windows 10 : Part 02
MD-100 : Windows 10 : Part 02
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has an on-premises network that contains an Active Directory domain. The domain is synced to Microsoft Azure Active Directory (Azure AD). All computers in the domain run Windows 10 Enterprise.
You are logged on as the local administrator on a Computer named Computer1.
A user named Mia Hamm has a computer named Computer2. Mia Hamm reports that she is experiencing problems with Computer2.
You want to use Event Viewer on Computer1 to view the event logs on Computer2.
What should you do?
- On Computer1, run the Connect-WSMan -ComputerName “Computer1” cmdlet.
- On Computer1, run the Get-Eventlog -List -ComputerName “Computer1” cmdlet.
- On Computer1, log on as a domain administrator, then open Event Viewer and select the Connect to another computer … option.
- On Computer1, open the Windows Defender Firewall and enable the Remote Event Log Management inbound rule.
Explanation:
You are logged on as a local administrator. You need the required permissions to access Event Viewer logs on all remote Windows computers.
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam times as you would like to complete each case. However, there may be additional studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
Fabrikam, Inc. is a distribution company that has 500 employees and 100 contractors.
Existing Environment
Active Directory
The network contains an Active Directory forest named fabrikam.com. The forest is synced to Microsoft Azure Active Directory (Azure AD). All the employees are assigned Microsoft 365 E3 licenses.
The domain contains a user account for an employee named User10.
Client Computers
All the employees have computers that run Windows 10 Enterprise. All the computers are installed without Volume License Keys. Windows 10 license keys are never issued.
All the employees register their computer to Azure AD when they first receive the computer.
User10 has a computer named Computer10.
All the contractors have their own computer that runs Windows 10. None of the computers are joined to Azure AD.
Operational Procedures
Fabrikam has the following operational procedures:
*Updates are deployed by using Windows Update for Business.
*When new contractors are hired, administrators must help the contactors configure the following settings on their computer:
– User certificates
– Browser security and proxy settings
– Wireless network connection settingsSecurity Policies
The following security policies are enforced on all the client computers in the domain:
-All the computers are encrypted by using BitLocker Drive Encryption (BitLocker). BitLocker recovery information is stored in Active Directory and Azure AD.
-The local Administrators group on each computer contains an enabled account named LocalAdmin.
-The LocalAdmin account is managed by using Local Administrator Password Solution (LAPS).Problem Statements
Fabrikam identifies the following issues:
-Employees in the finance department use an application named Application1. Application1 frequently crashes due to a memory error. When Application1 crashes, an event is written to the application log and an administrator runs a script to delete the temporary files and restart the application.
-When employees attempt to connect to the network from their home computer, they often cannot establish a VPN connection because of misconfigured VPN settings.
-An employee has a computer named Computer11. Computer11 has a hardware failure that prevents the computer from connecting to the network.
-User10 reports that Computer10 is not activated.Technical Requirements
Fabrikam identifies the following technical requirements for managing the client computers:
-Provide employees with a configuration file to configure their VPN connection.
-Use the minimum amount of administrative effort to implement the technical requirements.
-Identify which employees’ computers are noncompliant with the Windows Update baseline of the company.
-Ensure that the service desk uses Quick Assist to take remote control of an employee’s desktop during support calls.
-Automate the configuration of the contractors’ computers. The solution must provide a configuration file that the contractors can open from a Microsoft SharePoint site to apply the required configurations.-
HOTSPOT
You need to implement a solution to configure the contractors’ computers.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 02 Q02 006 
MD-100 Windows 10 Part 02 Q02 007 Explanation:The requirement states: Automate the configuration of the contractors’ computers. The solution must provide a configuration file that the contractors can open from a Microsoft SharePoint site to apply the required configurations.
The ‘configuration file’ in this case is known as a ‘provisioning package’.
A provisioning package (.ppkg) is a container for a collection of configuration settings. With Windows 10, you can create provisioning packages that let you quickly and efficiently configure a device without having to install a new image.
The tool for creating provisioning packages is renamed Windows Configuration Designer, replacing the Windows Imaging and Configuration Designer (ICD) tool. -
You need to ensure that User10 can activate Computer10.
What should you do?
- Request that a Windows 10 Enterprise license be assigned to User10, and then activate Computer10.
- From the Microsoft Deployment Toolkit (MDT), add a Volume License Key to a task sequence, and then redeploy Computer10.
- From System Properties on Computer10, enter a Volume License Key, and then activate Computer10.
- Request that User10 perform a local AutoPilot Reset on Computer10, and then activate Computer10.
Explanation:The case study states: User10 reports that Computer10 is not activated.
The solution is to perform a local AutoPilot Reset on the computer. This will restore the computer settings to a fully-configured or known IT-approved state. When User10 signs in to the computer after the reset, the computer should activate.
You can use Autopilot Reset to remove personal files, apps, and settings from your devices. The devices remain enrolled in Intune and are returned to a fully-configured or known IT-approved state. You can Autopilot Reset a device locally or remotely from the Intune for Education portal.
Incorrect Answers:
A: All users have Microsoft 365 E3 licenses. This license includes Windows 10 Enterprise so we don’t need to assign a Windows 10 Enterprise license to User10.
B: Volume License Keys aren’t required.
C: Volume License Keys aren’t required.
-
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
Contoso has IT, human resources (HR), and finance departments.
Contoso recently opened a new branch office in San Diego. All the users in the San Diego office work from home.
Existing environment
Contoso uses Microsoft 365.
The on-premises network contains an Active Directory domain named contoso.com. The domain is synced to Microsoft Azure Active Directory (Azure AD).
All computers run Windows 10 Enterprise.
You have four computers named Computer1, Computer2, Computer3, and ComputerA. ComputerA is in a workgroup on an isolated network segment and runs the Long Term Servicing Channel version of Windows 10. ComputerA connects to a manufacturing system and is business critical. All the other computers are joined to the domain and run the Semi-Annual Channel version of Windows 10.
In the domain, you create four groups named Group1, Group2, Group3, and Group4.
Computer2 has the local Group Policy settings shown in the following table.

MD-100 Windows 10 Part 02 Q03 008 The computers are updated by using Windows Update for Business.
The domain has the users shown in the following table.

MD-100 Windows 10 Part 02 Q03 009 Computer1 has the local users shown in the following table.

MD-100 Windows 10 Part 02 Q03 010 Requirements
Planned Changes
Contoso plans to purchase computers preinstalled with Windows 10 Pro for all the San Diego office users.
Technical requirements
Contoso identifies the following technical requirements:
-The computers in the San Diego office must be upgraded automatically to Windows 10 Enterprise and must be joined to Azure AD the first time a user starts each new computer. End users must not be required to accept the End User License Agreement (EULA).
-Helpdesk users must be able to troubleshoot Group Policy object (GPO) processing on the Windows 10 computers. The helpdesk users must be able to identify which Group Policies are applied to the computers.
-Users in the HR department must be able to view the list of files in a folder named D:\Reports on Computer3.
-ComputerA must be configured to have an Encrypting File System (EFS) recovery agent.
-Quality update installations must be deferred as long as possible on ComputerA.
-Users in the IT department must use dynamic lock on their primary device.
-User6 must be able to connect to Computer2 by using Remote Desktop.
-The principle of least privilege must be used whenever possible.
-Administrative effort must be minimized whenever possible.
-Kiosk (assigned access) must be configured on Computer1.-
You need to meet the technical requirements for the San Diego office computers.
Which Windows 10 deployment method should you use?
- wipe and load refresh
- in-place upgrade
- provisioning packages
- Windows Autopilot
Explanation:The requirement states: The computers in the San Diego office must be upgraded automatically to Windows 10 Enterprise and must be joined to Azure AD the first time a user starts each new computer. End users must not be required to accept the End User License Agreement (EULA).
Windows Autopilot is a collection of technologies used to set up and pre-configure new devices, getting them ready for productive use. You can also use Windows Autopilot to reset, repurpose and recover devices.
The OEM Windows 10 installation on the new computers can be transformed into a “business-ready” state, applying settings and policies, installing apps, and even changing the edition of Windows 10 being used (e.g. from Windows 10 Pro to Windows 10 Enterprise) to support advanced features.
The only interaction required from the end user is to connect to a network and to verify their credentials. Everything beyond that is automated.
-
HOTSPOT
You need to meet the technical requirement for Computer1.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 02 Q03 011 
MD-100 Windows 10 Part 02 Q03 012
-
-
You plan to deploy Windows 10 to 100 secure computers.
You need to select a version of Windows 10 that meets the following requirements:
-Uses Microsoft Edge as the default browser
-Minimizes the attack surface of the computer
-Supports joining Microsoft Azure Active Directory (Azure AD)
-Only allows the installation of applications from the Microsoft StoreWhat is the best version to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.
- Windows 10 Pro in S mode
- Windows 10 Home in S mode
- Windows 10 Pro
- Windows 10 Enterprise
Explanation:Windows 10 in S mode is a version of Windows 10 that’s streamlined for security and performance, while providing a familiar Windows experience. To increase security, it allows only apps from the Microsoft Store, and requires Microsoft Edge for safe browsing.
Azure AD Domain join is available for Windows 10 Pro in S mode and Windows 10 Enterprise in S mode. It’s not available in Windows 10 Home in S mode.
-
DRAG DROP
You have a computer named Computer1 that runs Windows 8.1. Computer1 has a local user named User1 who has a customized profile.
On Computer1, you perform a clean installation of Windows 10 without formatting the drives.
You need to migrate the settings of User1 from Windows 8.1 to Windows 10.
Which two actions should you perform? To answer, drag the appropriate actions to the correct targets. Each action may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
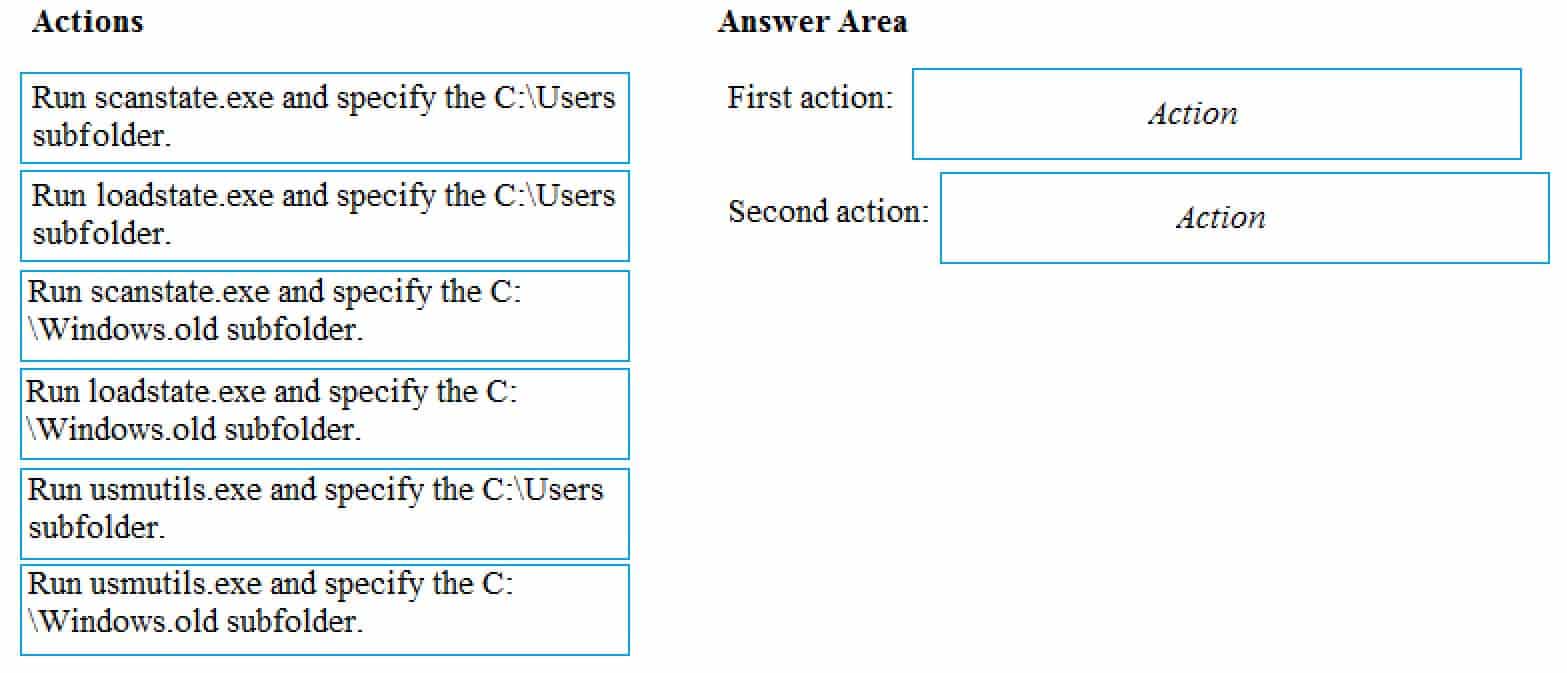
MD-100 Windows 10 Part 02 Q05 013 
MD-100 Windows 10 Part 02 Q05 014 Explanation:Explanation:
The User State Migration Tool (USMT) includes two tools that migrate settings and data: ScanState and LoadState. ScanState collects information from the source computer, and LoadState applies that information to the destination computer. In this case the source and destination will be the same computer.
As we have performed a clean installation of Windows 10 without formatting the drives, User1’s customized Windows 8.1 user profile will be located in the \Windows.old folder. Therefore, we need to run scanstate.exe on the \Windows.old folder.
User1’s Windows 10 profile will be in the C:\Users folder so we need to run loadstate.exe to apply the changes in the C:\Users folder. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows10.
A service named Application1 is configured as shown in the exhibit.

MD-100 Windows 10 Part 02 Q06 015 You discover that a user used the Service1 account to sign in to Computer1 and deleted some files.
You need to ensure that the identity used by Application1 cannot be used by a user to sign in to sign in to the desktop on Computer1. The solution must use the principle of least privilege.
Solution: On Computer1, you configure Application1 to sign in as the LocalSystem account and select the Allow service to interact with desktop check box. You delete the Service1 account.
Does this meet the goal?
- Yes
- No
Explanation:Configuring Application1 to sign in as the LocalSystem account would ensure that the identity used by Application1 cannot be used by a user to sign in to the desktop on Computer1. However, this does not use the principle of least privilege. The LocalSystem account has full access to the system. Therefore, this solution does not meet the goal.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows 10.
A service named Application1 is configured as shown in the exhibit.

MD-100 Windows 10 Part 02 Q07 016 You discover that a user used the Service1 account to sign in to Computer1 and deleted some files.
You need to ensure that the identity used by Application1 cannot be used by a user to sign in to sign in to the desktop on Computer1. The solution must use the principle of least privilege.
Solution: On Computer1, you assign Service1 the Deny log on locally user right.
Does this meet the goal?
- Yes
- No
Explanation:By using the Service1 account as the identity used by Application1, we are applying the principle of least privilege as required in this question.
However, the Service1 account could be used by a user to sign in to the desktop on the computer. To sign in to the desktop on the computer, an account needs the log on locally right which all user accounts have by default. Therefore, we can prevent this by assigning Service1 the deny log on locally user right. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows 10.
A service named Application1 is configured as shown in the exhibit.

MD-100 Windows 10 Part 02 Q08 017 You discover that a user used the Service1 account to sign in to Computer1 and deleted some files.
You need to ensure that the identity used by Application1 cannot be used by a user to sign in to sign in to the desktop on Computer1. The solution must use the principle of least privilege.
Solution: On Computer1, you assign Service1 the Deny log on as a service user right.
Does this meet the goal?
- Yes
- No
Explanation:A service account needs the log on as a service user right. When you assign an account to be used by a service, that account is granted the log on as a service user right. Therefore, assigning Service1 the deny log on as a service user right would mean the service would not function.
To sign in to the desktop on the computer, an account needs the log on locally right which all user accounts have by default. To meet the requirements of this question, we need to assign Service1 the deny log on locally user right, not the deny log on as a service user right.
-
You have a Microsoft Azure Active Directory (Azure AD) tenant.
Some users sign in to their computer by using Windows Hello for Business.
A user named User1 purchases a new computer and joins the computer to Azure AD.
User1 is not able to use Windows Hello for Business on his computer. User1 sign-in options are shown on the exhibit. (Click the Exhibit tab.)
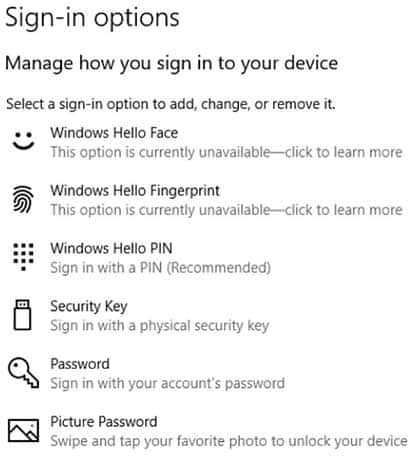
MD-100 Windows 10 Part 02 Q09 018 You open Device Manager and confirm that all the hardware works correctly.
You need to ensure that User1 can use Windows Hello for Business facial recognition to sign in to the computer.
What should you do first?
- Purchase an infrared (IR) camera.
- Upgrade the computer to Windows 10 Enterprise.
- Enable UEFI Secure Boot.
- Install a virtual TPM driver.
Explanation:Windows Hello facial recognition requires an infrared (IR) camera. If your device does not have an infrared camera (or any other biometric device such as a fingerprint scanner), you will see the message shown in the exhibit. The question states that Device Manager shows all hardware is working properly. Therefore, it is not the case that the computer has an IR camera but it isn’t working properly. The problem must be that the computer does not have an IR camera.
Incorrect Answers:
B: Windows 10 Enterprise is not required for Windows Hello. Windows Hello also works on Windows 10 Pro.
C: UEFI Secure Boot is not required for Windows Hello.
D: A virtual TPM driver is not required for Windows Hello. -
Your company uses Microsoft Deployment Toolkit (MDT) to deploy Windows 10 to new computers.
The company purchases 1,000 new computers.
You need to ensure that the Hyper-V feature is enabled on the computers during the deployment.
What are two possible ways to achieve this goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- Add a task sequence step that adds a provisioning package.
- In a Group Policy object (GPO), from Computer Configuration, configure Application Control Policies.
- Add a custom command to the Unattend.xml file.
- Add a configuration setting to Windows Deployment Services (WDS).
- Add a task sequence step that runs dism.exe.
Explanation:A common way to add a feature such as Hyper-V in MDT is to use the Install Roles and Features task sequence action. However, that is not an option in this question.
The two valid options are to a command to the Unattend.xml file or to add a task sequence step that runs dism.exe.
To add Hyper-V using dism.exe, you would run the following dism command:
DISM /Online /Enable-Feature /All /FeatureName:Microsoft-Hyper-V
-
Your network contains an Active Directory domain that is synced to a Microsoft Azure Active Directory (Azure AD) tenant.
Your company purchases a Microsoft 365 subscription.
You need to migrate the Documents folder of users to Microsoft OneDrive for Business.
What should you configure?
- One Drive Group Policy settings
- roaming user profiles
- Enterprise State Roaming
- Folder Redirection Group Policy settings
Explanation:You need to configure a Group Policy Object (GPO) with the OneDrive settings required to redirect the Documents folder of each user to Microsoft 365.
Importing the OneDrive group policy template files into Group Policy adds OneDrive related settings that you can configure in your Group Policy.
One of the group policy settings enables you to redirect “Known Folders” to OneDrive for business. Known folders are Desktop, Documents, Pictures, Screenshots, and Camera Roll.
There are two primary advantages of moving or redirecting Windows known folders to OneDrive for the users in your domain:
Your users can continue using the folders they’re familiar with. They don’t have to change their daily work habits to save files to OneDrive.
Saving files to OneDrive backs up your users’ data in the cloud and gives them access to their files from any device. -
Your network contains an Active Directory domain. The domain contains a user named User1.
User1 creates a Microsoft account.
User1 needs to sign in to cloud resources by using the Microsoft account without being prompted for credentials.
Which settings should User1 configure?
- User Accounts in Control Panel
- Email & app accounts in the Settings app
- Users in Computer Management
- Users in Active Directory Users and Computers
Explanation:Open the Setting app, select Accounts then select Email and accounts. Here you can add accounts for the cloud resources and configure the login credentials for the accounts. If you configure the accounts with the login credentials of the Microsoft account, you won’t be prompted for credentials when you open the apps.
-
HOTSPOT
Your network contains an Active Directory domain named adatum.com that uses Key Management Service (KMS) for activation.
You deploy a computer that runs Windows 10 to the domain.
The computer fails to activate.
You suspect that the activation server has an issue.
You need to identify which server hosts KMS.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 02 Q13 019 
MD-100 Windows 10 Part 02 Q13 020 -
HOTSPOT
You deploy Windows 10 to a new computer named Computer1.
You sign in to Computer1 and create a user named User1.
You create a file named LayoutModification.xml in the C:\Users\Default\AppData\Local\Microsoft\Windows\Shell\folder. LayoutModification.xml contains the following markup.

MD-100 Windows 10 Part 02 Q14 021 What is the effect of the configuration? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 02 Q14 022 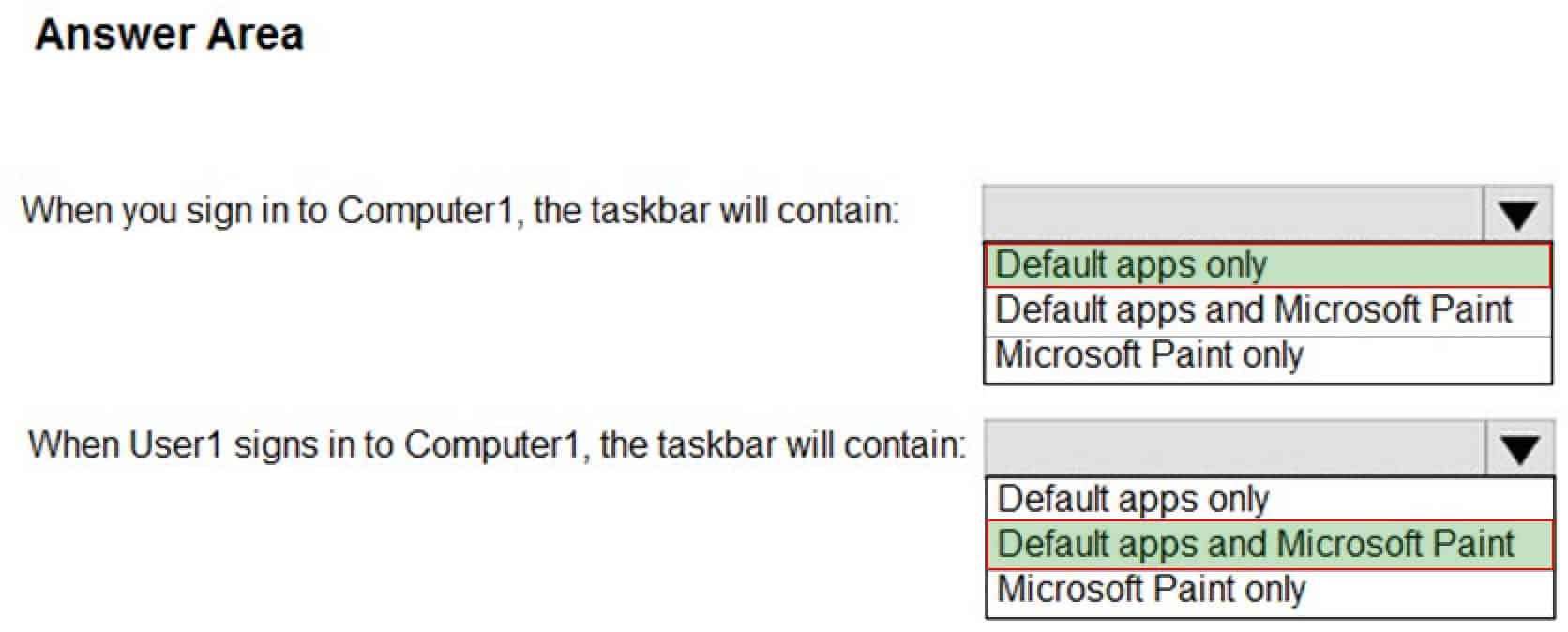
MD-100 Windows 10 Part 02 Q14 023 -
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
You have a workgroup computer named Computer1 that runs Windows 10.
You need to add Computer1 to contoso.com.
What should you use?
- Computer Managements
- dsregcmd.exe
- the Settings app
- netdom.exe
Explanation:You join a computer to a domain, including an Azure AD domain in the Settings panel in Windows 10, under System->About
-
You have a computer that runs Windows 10.
You need to configure a picture password.
What should you do?
- From Control Panel, configure the User Accounts settings.
- From the Settings app, configure the Sign-in options.
- From the Local Group Policy Editor, configure the Account Policies settings.
- From Windows PowerShell, run the Set-LocalUser cmdlet and specify the InputObject parameter.
-
You have a workgroup computer named Computer1 that runs Windows 10.
You need to configure Windows Hello for sign-in to Computer1 by using a physical security key.
What should you use?
- a USB 3.0 device that supports BitLocker Drive Encryption (BitLocker)
- a USB device that supports FIDO2
- a USB 3.0 device that has a certificate from a trusted certification authority (CA)
- a USB device that supports RSA SecurID
-
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 10.
The domain contains the users shown in the following table.
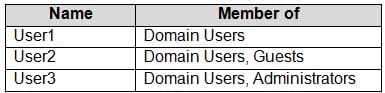
MD-100 Windows 10 Part 02 Q18 024 Computer1 has the local users shown in the following table.

MD-100 Windows 10 Part 02 Q18 025 All users have Microsoft accounts.
Which two users can be configured to sign in by using their Microsoft account? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- User1
- User2
- User3
- User4
- User5
-
HOTSPOT
You have the source files shown in the following table.
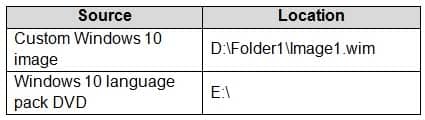
MD-100 Windows 10 Part 02 Q19 026 You mount an image from Image1.wim to a folder named C:\Mount.
You need to add the French language pack to the mounted image.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
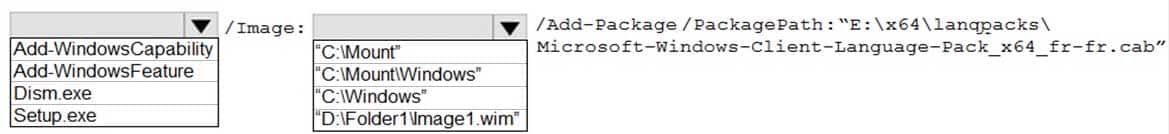
MD-100 Windows 10 Part 02 Q19 027 
MD-100 Windows 10 Part 02 Q19 028 Explanation:Note: The referenced document has the mount directory as C:\Mount\Windows. In this question, the mount directory is C:\Mount.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 8.1.
Computer1 has apps that are compatible with Windows 10.
You need to perform a Windows 10 in-place upgrade on Computer1.
Solution: You copy the Windows 10 installation media to a network share. From Windows 8.1 on Computer1, you run setup.exe from the network share.
Does this meet the goal?
- Yes
- No