MD-100 : Windows 10 : Part 08
-
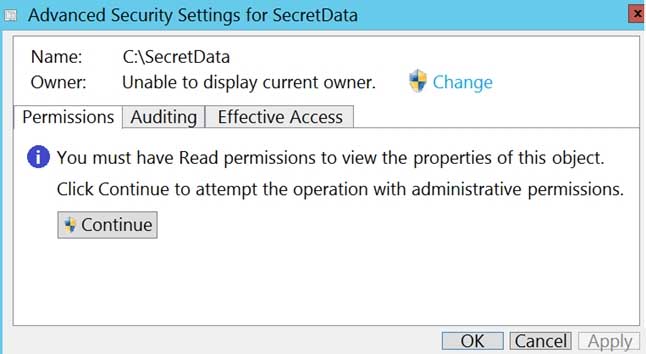
User1 is a member of the Administrators group on a computer that runs Windows 10.
When User1 attempts to view the security settings of a folder named C:\SecretData, the user receives the message in the Security exhibit. (Click the Security tab.)

MD-100 Windows 10 Part 07 Q20 195 On the computer, you sign in as a member of the Administrators group and view the permissions to C:\SecretData as shown in the Permissions exhibit. (Click the Permissions tab.)
MD-100 Windows 10 Part 07 Q20 196 You need to restore Use1’s access to C:\SecretData.
What should you do first?
- From the Permissions tab of Advanced Security Settings for SecretData, select Change to take ownership of the folder.
- From the Permissions tab of Advanced Security Settings for SecretData, select Continue to attempt the operation by using administrative privileges.
- Assign User1 Full control permissions to the C folder and set the inheritance to This folder, subfolders and files.
- From an elevated command prompt, run cacls.exe c:\secretdata /g user1:F.
-
HOTSPOT
Your network contains an Active Directory domain. The domain contains the users shown in the following table.
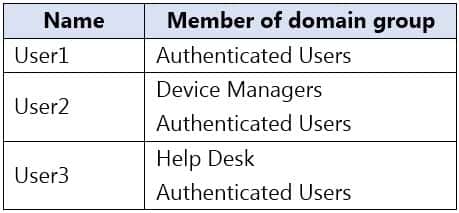
MD-100 Windows 10 Part 08 Q02 197 The Authenticated Users group has the Add workstations to domain user right in the Default Domain Controllers Policy.
The Device Managers and Help Desk groups are granted the Create Computer objects permission for the Computers container of the domain.
You have 15 workgroup computers that run Windows 10. Each computer contains a local user account named LocalAdmin1 that is a member of the following groups:
-Administrators
-Device Owners
-Authenticated UsersFor each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 08 Q02 198 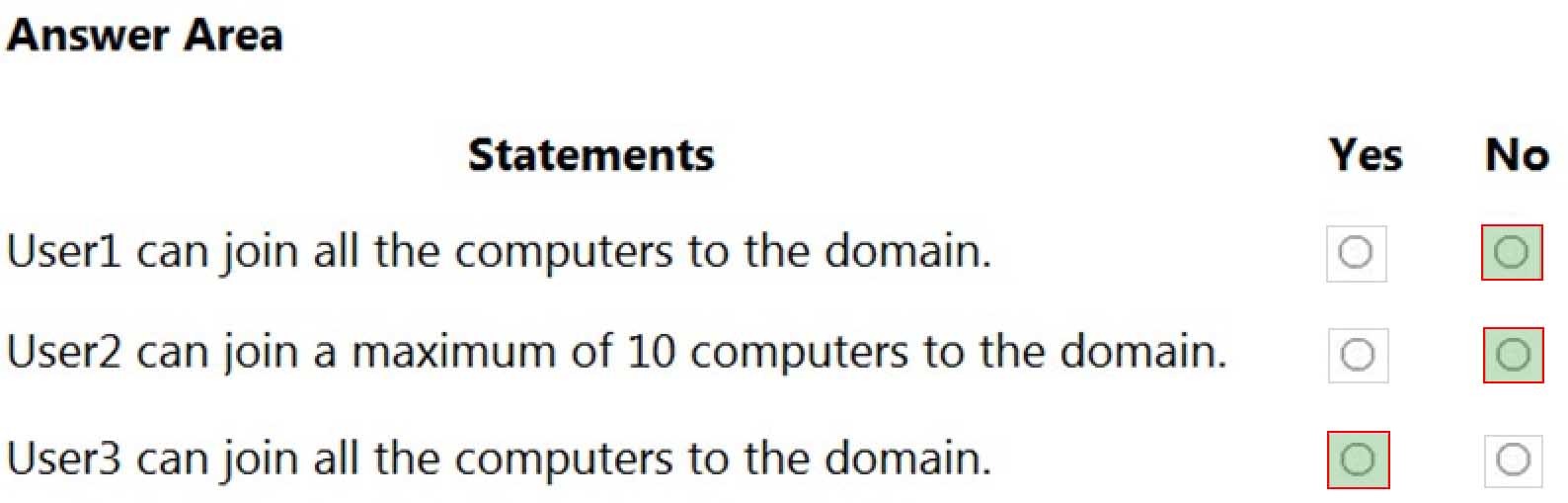
MD-100 Windows 10 Part 08 Q02 199 Explanation:Box 1: No
User1 is a member of the Authenticated Users group which has the Add workstations to domain user right. However, with the Add workstations to domain user right, you are restricted to joining a maximum of 10 computers to the domain.Box 2: No
User2 is a member of the Authenticated Users group which has the Add workstations to domain user right. User2 is also a member of the Device Managers group which is granted the Create Computer objects permission for the Computers container of the domain. The Create Computer objects permission overrides the 10-computer limit imposed by the Add workstations to domain user right so User2 can join more than 10 computers to the domain.Box 3. Yes
User3 is a member of the Authenticated Users group which has the Add workstations to domain user right. User3 is also a member of the Help Desk group which is granted the Create Computer objects permission for the Computers container of the domain. The Create Computer objects permission overrides the 10-computer limit imposed by the Add workstations to domain user right so User3 can join all the computers to the domain. -
You have a computer named Computer1 that runs Windows 10. Computer1 is in a workgroup.
Computer1 contains the local users shown in the following table.
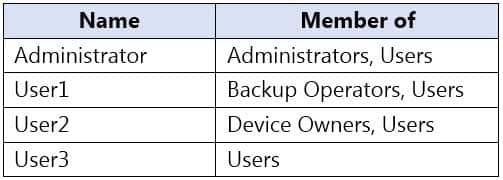
MD-100 Windows 10 Part 08 Q03 200 The Users group has Modify permissions to a folder named D:\Folder1.
User3 creates a file named File1.docx in Folder1.
Which users can take ownership of File1.docx?
- Administrator and User1 only
- Administrator only
- Administrator, User1, and User2
- Administrator and User2 only
Explanation:
Only a member of the Administrator’s group can take ownership of a file or folder. -
HOTSPOT
You have two workgroup computers named Computer1 and Computer2 that run Windows 10. The Guest account is enabled on both computers.
The computers contain the users shown in the following table.

MD-100 Windows 10 Part 08 Q03 201 The computers contain the shared folders shown in the following table.

MD-100 Windows 10 Part 08 Q03 202 Computer1 has password-protected sharing turned on. Computer2 has password-protected sharing turned off.
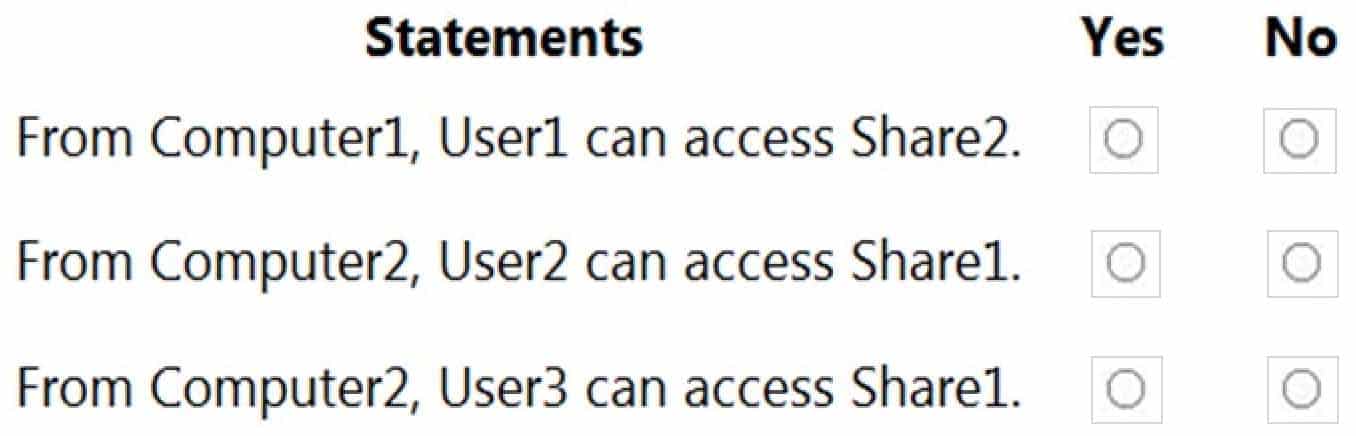
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
MD-100 Windows 10 Part 08 Q03 203 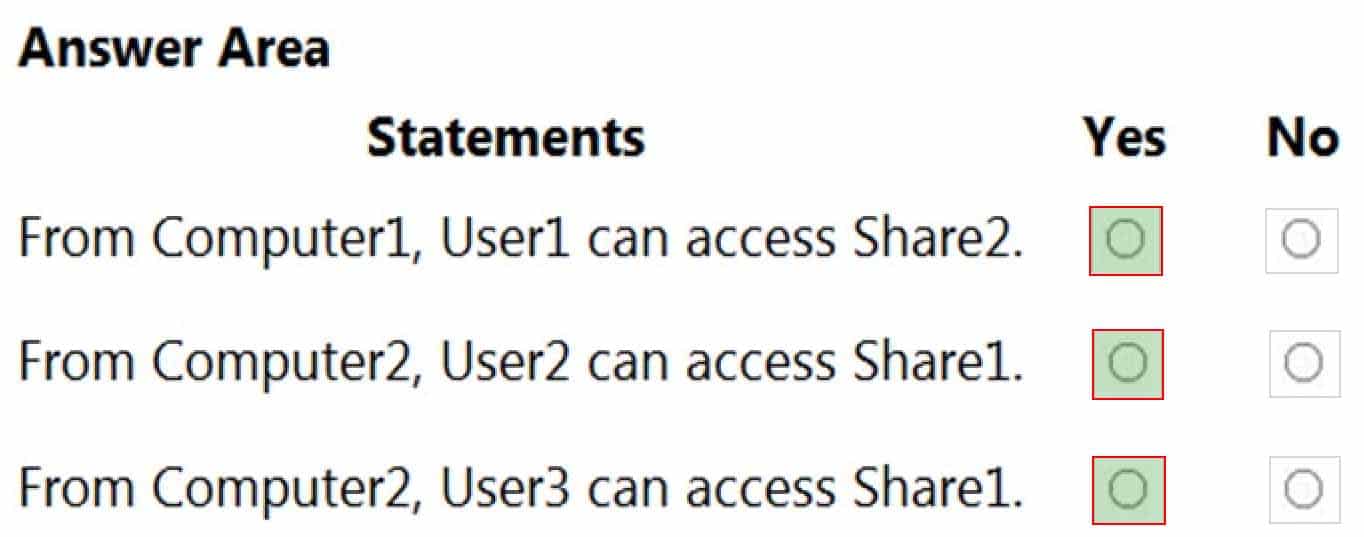
MD-100 Windows 10 Part 08 Q03 204 Explanation:When password protected sharing is turned on, only people who have a user account and password on your computer can access shared files.
Box 1: Yes
Password protected sharing is turned off on Computer2 so User1 can access Share2 from Computer1.Box 2: Yes
Password protected sharing is turned on on Computer1. User2 has an account on Computer1 so User2 can access Share1 from Computer2.Box 3: Yes
The answer to this question depends on which version of Windows 10 is running on the computers. This isn’t specified in the question so it’s likely that the question will be updated in future.Password protected sharing is turned on on Computer1. User3 does not have an account on Computer1 so User3 cannot access Share1 from Computer2. However, the Guest account is enabled which could provide access depending on which version of Windows 10 is running. If it is Windows 10 Home or Pro, then the answer to this question is Yes. The Guest account does provide access. However, in later versions of Windows 10 Enterprise and Windows 10 Education (from build 1709 onwards), the Guest account does not enable access to the shared folder.
-
You need to enable BitLocker Drive Encryption (BitLocker) on a computer named Computer1 that runs Windows 10. Computer1 has the following configurations:
-Contains only one 200-GB NTFS volume named C:\
-Contains 50 GB of unallocated disk space
-Is the member of a workgroup
-Has TPM enabledWhat should you do first?
- Create a VHD.
- Disable TPM.
- Create an additional volume.
- Join Computer1 to an Azure Active Directory (Azure AD) tenant.
Explanation:Two partitions are required to run BitLocker because pre-startup authentication and system integrity verification must occur on a separate partition from the encrypted operating system drive. This configuration helps protect the operating system and the information in the encrypted drive.
-
You have a workgroup computer that runs Windows 10.
You need to set the minimum password length to 12 characters.
What should you use?
- User Accounts in Control Panel
- Local Security Policy
- Credential Manager in Control Panel
- Email & accounts in the Settings app
Explanation:You can set the password length on computers that are not domain joined by using the Local Security Policy or the Local Group Policy Editor.
Note:
There are several versions of this question in the exam. The question has two possible correct answers:
1.Local Group Policy Editor
2.Local Security PolicyOther incorrect answer options you may see on the exam include the following:
1.System Protection in System Properties
2.Local Users and Groups in Computer Management
3.Sign-in options in the Settings app -
You have 20 computers that run Windows 10. The computers are in a workgroup.
You need to create a local user named User1 on all the computers. User1 must be a member of the Remote Management Users group.
What should you do?
- From Windows Configuration Designer, create a provisioning package, and then run the provisioning package on each computer.
- Create a script that runs the New-ADUser cmdlet and the Set-AdGroup cmdlet.
- Create a Group Policy object (GPO) that contains the Local User Group Policy preference.
- Create a script that runs the New-MsolUser cmdlet and the Add-ADComputerServiceAccount cmdlet.
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer that runs Windows 10. The computer contains a folder named D:\Scripts. D:\Scripts contains several PowerShell scripts.
You need to ensure that you can run the PowerShell scripts without specifying the full path to the scripts. The solution must persist between PowerShell sessions.
Solution: From System Properties, you add D:\Scripts to the PATH environment variable.
Does this meet the goal?
- Yes
- No
-
You have several computers that run Windows 10. The computers are in a workgroup and have BitLocker Drive Encryption (BitLocker) enabled.
You join the computers to Microsoft Azure Active Directory (Azure AD).
You need to ensure that you can recover the BitLocker recovery key for the computers from Azure AD.
What should you do first?
- Disable BitLocker.
- Add a BitLocker key protector.
- Suspend BitLocker.
- Disable the TMP chip.
-
HOTSPOT
You have two workgroup computers named Computer1 and Computer2 that run Windows 10. The computers contain the local security principals shown in the following table.

MD-100 Windows 10 Part 08 Q10 205 Which security principals can be members of GroupA and GroupC? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 08 Q10 206 -
A user purchases a new computer that has Windows 10 Home preinstalled. The computer has a biometric fingerprint reader.
You need to ensure that the user can use the fingerprint reader to sign in to the computer by using an Azure Active Directory (Azure AD) account.
What should you do first?
- Register the computer to Azure AD.
- Install the latest feature updates on the computer.
- Upgrade the computer to Windows 10 Enterprise.
- Upgrade the computer to Windows 10 Pro.
-
HOTSPOT
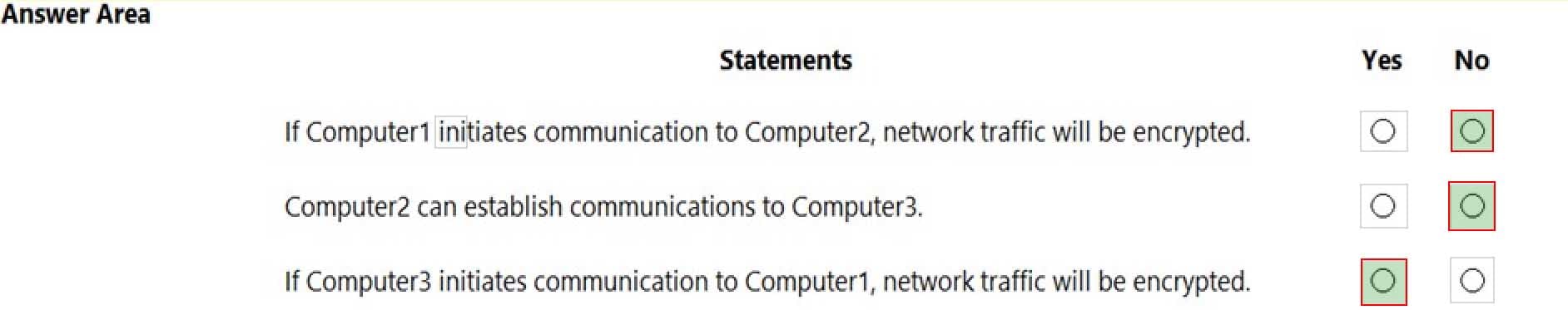
Your network contains an Active Directory domain. The domain contains three computers named Computer1, Computer2, and Computer3 that run Windows 10. The computers are on the same network and have network connectivity.
Windows Defender Firewall on Computer1 has the server-to-server connection security rule shown in the following table.

MD-100 Windows 10 Part 08 Q12 208 Windows Defender Firewall on Computer2 has the server-to-server connection security rule shown in the following table.

MD-100 Windows 10 Part 08 Q12 209 Windows Defender Firewall on Computer3 has the server-to-server connection security rule shown in the following table.

MD-100 Windows 10 Part 08 Q12 210 All the connection security rules are enabled and configured to use only the Computer (Kerberos V5) authentication method.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
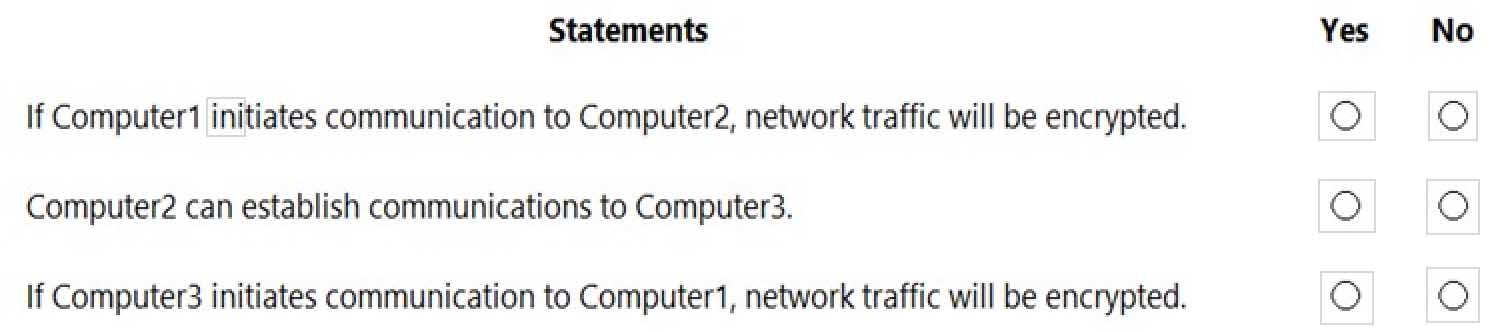
MD-100 Windows 10 Part 08 Q12 211 -
HOTSPOT
You have a workgroup computer named Computer1 that runs Windows 10 and has the users shown in the following table.
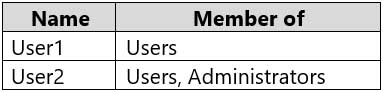
MD-100 Windows 10 Part 08 Q13 213 Computer1 contains an image file named C:\Folder\Image.jpg.
Computer1 has the Local Computer\Administrators Policy shown in the following table.
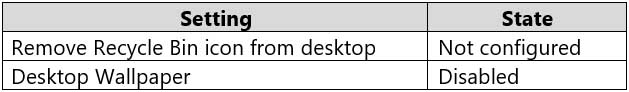
MD-100 Windows 10 Part 08 Q13 214 Computer1 has the Local Computer\Non-Administrators Policy shown in the following table.

MD-100 Windows 10 Part 08 Q13 215 Computer1 has the local computer policy shown in the following table.
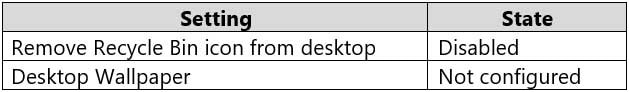
MD-100 Windows 10 Part 08 Q13 216 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 08 Q13 217 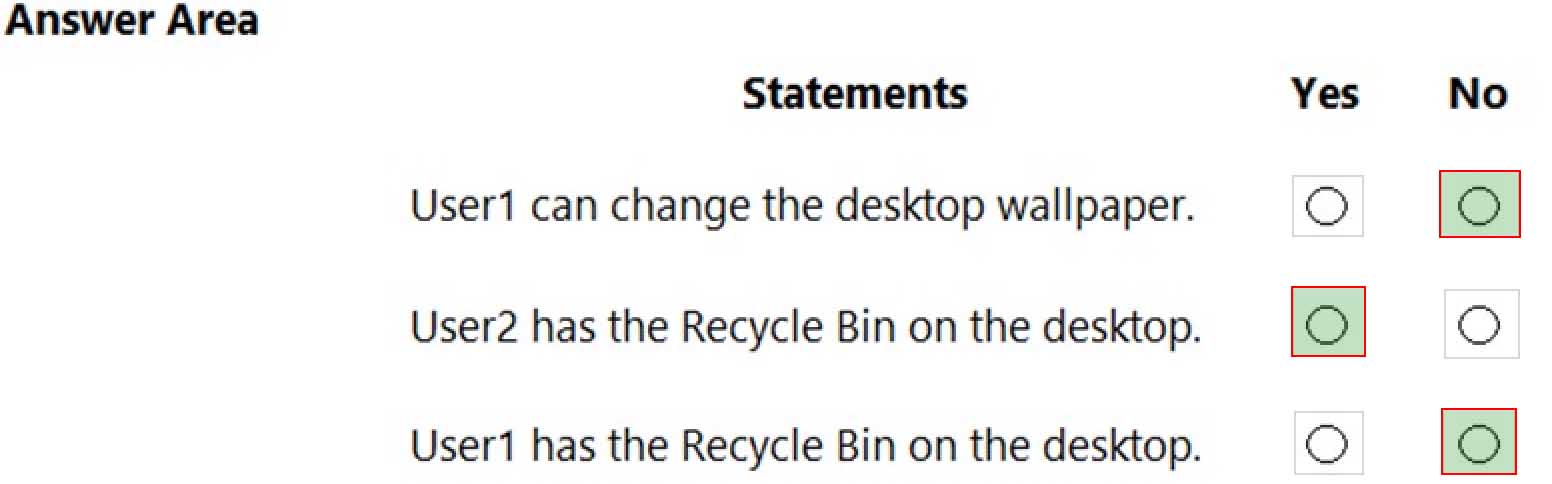
MD-100 Windows 10 Part 08 Q13 218 Explanation:Box 1: No
The Desktop Wallpaper setting in the Local Computer\Non-Administrators Policy specifies the path to the wallpaper image. Therefore, User1 will not be able to change the wallpaper.Box 2: Yes
The Remove Recycle Bin from desktop setting in the Local Computer\Administrators Policy is Not Configured which means it will not overwrite the setting in the Local Computer Policy. The Remove Recycle Bin from desktop setting in the Local Computer Policy is Disabled. Therefore, the Recycle Bin icon is not removed. In other words, it will be visible on the desktop.Box 3: No
The Remove Recycle Bin from desktop setting in the Local Computer\Non-Administrators Policy is enabled. Therefore, the Recycle Bin will be removed for User1 -
Your network contains an Active Directory domain. The domain contains 1,000 computers that run Windows 10.
You configure Microsoft Edge settings by using domain and local Group Policy Objects (GPOs).
You need to generate a report that contains all the Microsoft Edge policy settings applied to a computer.
What should you do?
- From PowerShell, run the Get-GPO cmdlet.
- From PowerShell, run the Get-GPOReport cmdlet.
- From Microsoft Edge, open edge://policy.
- From Microsoft Edge, open edge://settings.
Explanation:The Get-GPOReport cmdlet would generate a report for all domain group policy objects. However, this would not display the settings that are applied by local group policy objects.s
To display the settings applied by both domain and local GPOs, you would have to open Microsoft Edge and enter edge://policy in the address bar.
-
HOTSPOT
You have a computer named Computer1 that runs Windows 10.
You need to modify the Security Settings of Computer1 to meet the following requirements:
-A local group named Branch_Admins must be able to view and clear the Security log.
-Local users must be prompted to change their password three days before the password expires.Which two nodes of the Local Group Policy Editor should you access to configure the settings? To answer, select the appropriate nodes in the answer area.
NOTE: Each correct selection is worth one point.
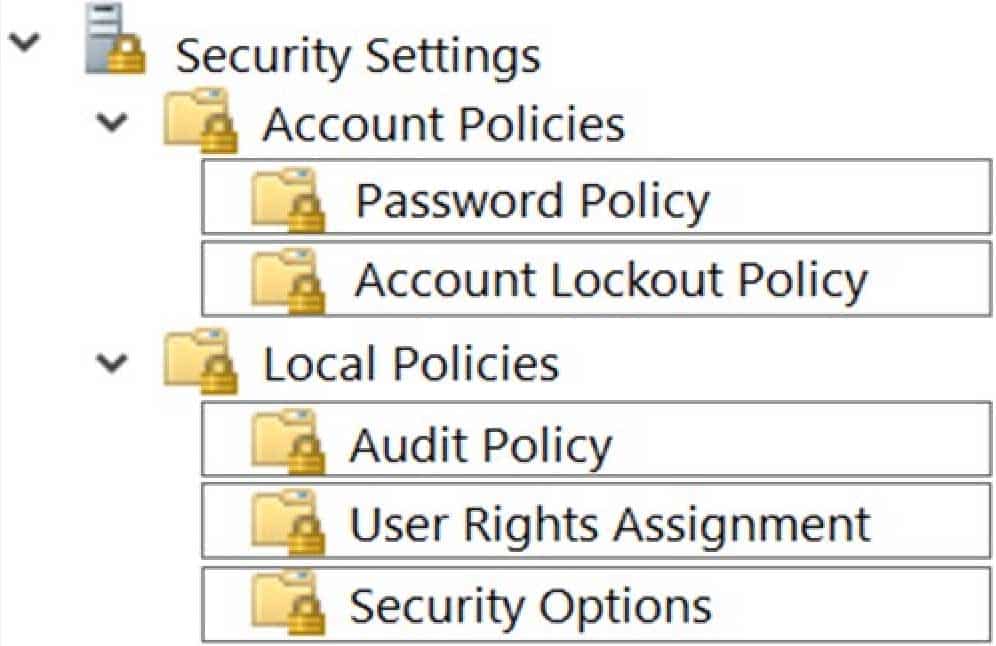
MD-100 Windows 10 Part 08 Q15 219 -
You have a computer that runs Windows 10 Pro. The computer contains the users shown in the following table.

MD-100 Windows 10 Part 08 Q16 221 You need to use a local Group Policy Object (GPO) to configure one group of settings for all the members of the local Administrators group and another group of settings for all non-administrators.
What should you do?
- Use the runas command to open Gpedit.msc as each user.
- Run mmc as User1 and add the Group Policy Object Editor snap-in twice.
- Open Gpedit.msc as User1 and add two Administrative Templates.
- Run mmc as User1 and add the Security Templates snap-in twice.
Explanation:
Add the Group Policy Object Editor snap-in twice. Select Browse > Users > Administrators when you add the first snap-in and select Browse > Users > Non-Administrators when you add the second snap-in. -
Your network contains an Active Directory domain. The domain contains 1,000 computers that run Windows 10.
You configure Microsoft Edge settings by using domain and local Group Policy Objects (GPOs).
You need to generate a report that contains all the Microsoft Edge policy settings applied to a computer.
What should you do?
- From PowerShell, run the Get-GPO cmdlet.
- From PowerShell, run the Get-GPOReport cmdlet.
- From Microsoft Edge, open edge://policy.
- From the Start menu, select Group Policy Object Editor.
Explanation:The Get-GPOReport cmdlet would generate a report for all domain group policy objects. However, this would not display the settings that are applied by local group policy objects.
To display the settings applied by both domain and local GPOs, you would have to open Microsoft Edge and enter edge://policy in the address bar.
-
HOTSPOT
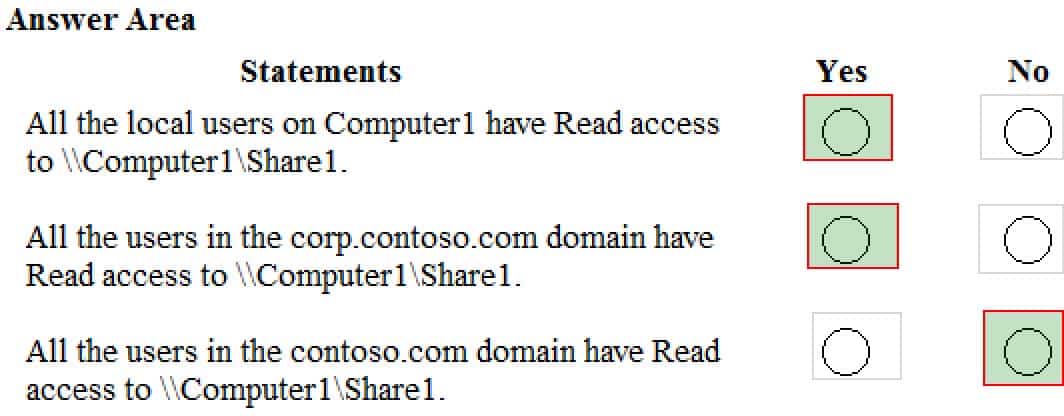
Your network contains an Active Directory forest. The forest contains a root domain named contoso.com and a child domain named corp.contoso.com.
You have a computer named Computer1 that runs Windows 10. Computer1 is joined to the corp.contoso.com domain.
Computer1 contains a folder named Folder1. In the Security settings of Folder1, Everyone is assigned the Full control permission.
On Computer1, you share Folder1 as Share1 and assign the Read permissions for Share1 to the local Users group.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
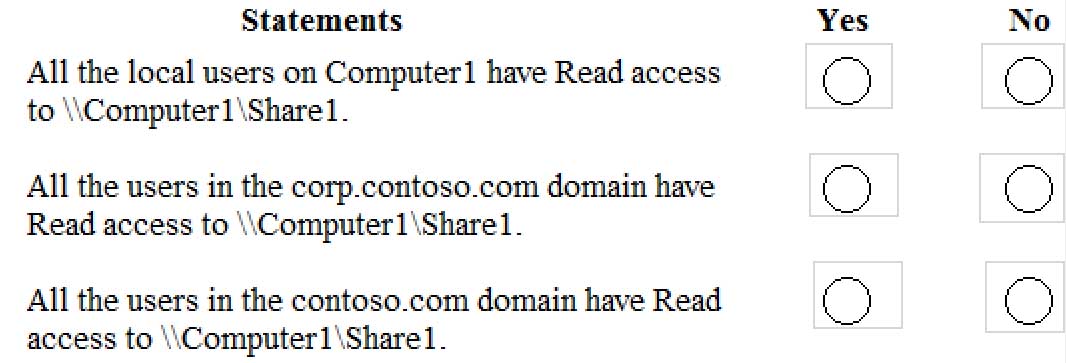
MD-100 Windows 10 Part 08 Q18 222 -
HOTSPOT
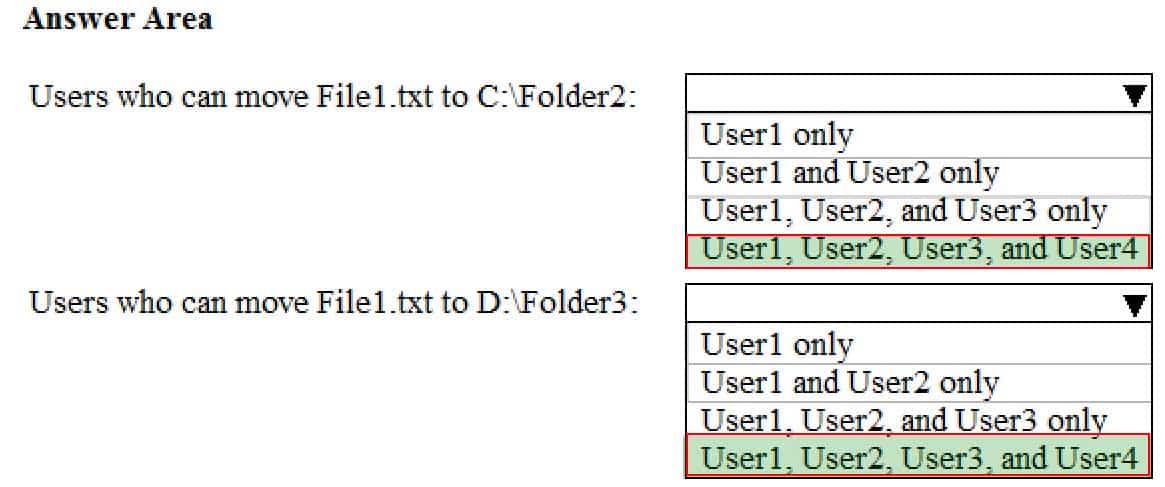
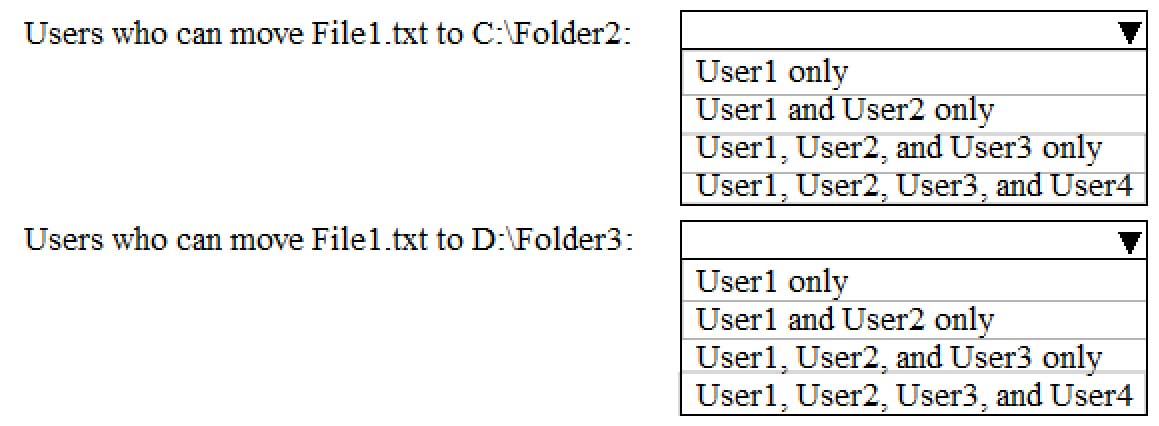
You have a computer named Computer1 that runs Windows 10. Computer1 is in a workgroup.
Computer1 contains the folders shown in the following table.

MD-100 Windows 10 Part 08 Q19 224 On Computer1, you create the users shown in the following table.

MD-100 Windows 10 Part 08 Q19 225 User1 encrypts a file named File1.txt that is in a folder named C:\Folder1.
What is the effect of the configuration? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MD-100 Windows 10 Part 08 Q19 226 -
HOTSPOT
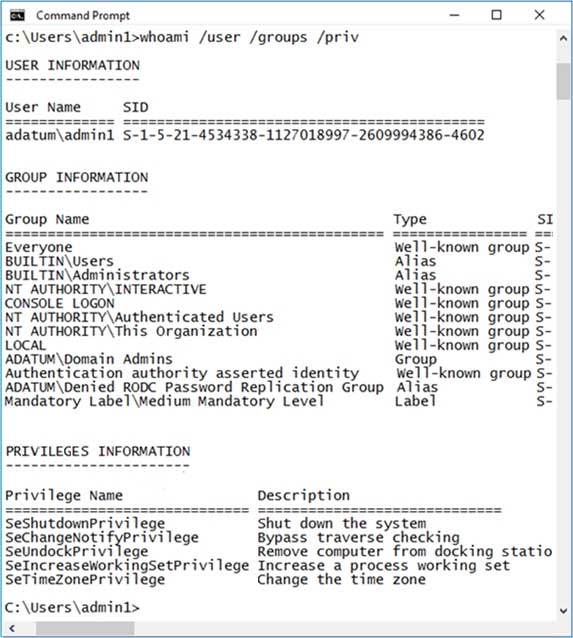
You have a computer named Computer1 that runs Windows 10 and is joined to an Active Directory domain named adatum.com.
A user named Admin1 signs in to Computer1 and runs the whoami command as shown in the following exhibit.
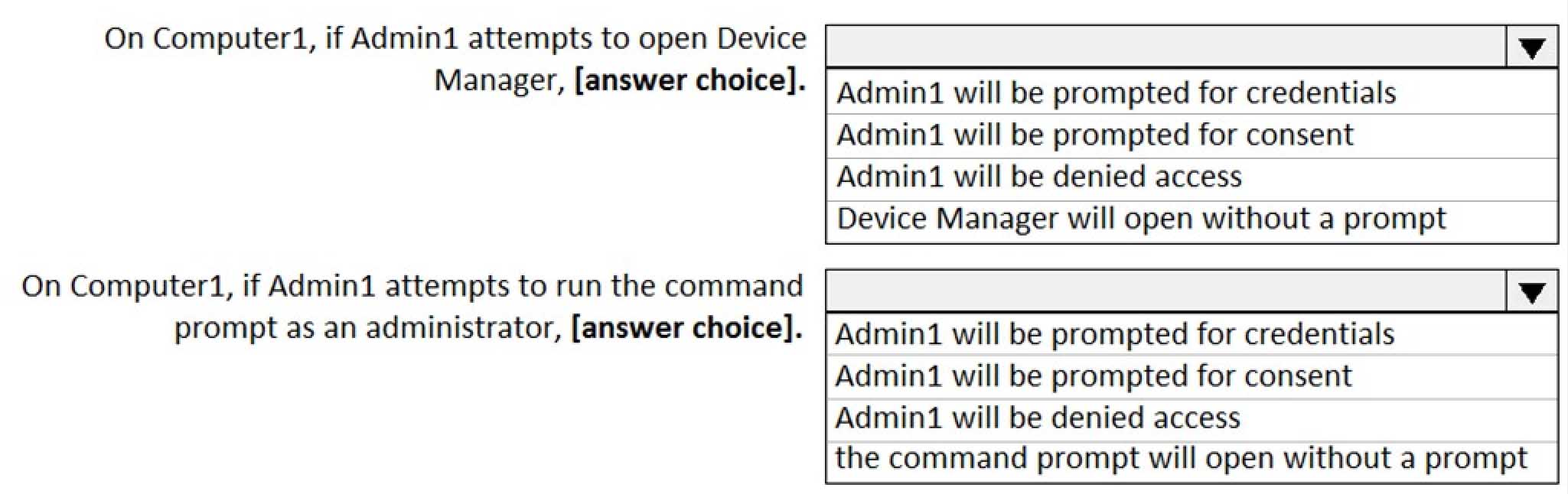
MD-100 Windows 10 Part 08 Q20 228 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
MD-100 Windows 10 Part 08 Q20 229