MD-100 : Windows 10 : Part 07
MD-100 : Windows 10 : Part 07
-
You have a workgroup computer that runs Windows 10.
You need to set the minimum password length to 12 characters.
What should you use?
- Local Group Policy Editor
- User Accounts in Control Panel
- System Protection in System Properties
- Sign-in options in the Settings app
Explanation:
You can set the password length on computers that are not domain joined by using the Local Security Policy or the Local Group Policy Editor.
Note:
1.There are several versions of this question in the exam. The question has two possible correct answers:
2.Local Group Policy Editor
3.Local Security PolicyOther incorrect answer options you may see on the exam include the following:
1.Credential Manager in Control Panel
2.Email & accounts in the Settings app
3.Local Users and Groups in Computer Management -
HOTSPOT
Your network contains an Active Directory domain named adatum.com. The domain contains the users shown in the following table.
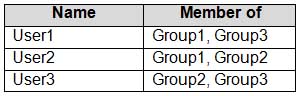
MD-100 Windows 10 Part 07 Q02 150 The domain contains a computer named Computer1 that runs Windows10. Computer1 has a file named File1.txt that has the permissions shown in the exhibit. (Click the Exhibit tab.)
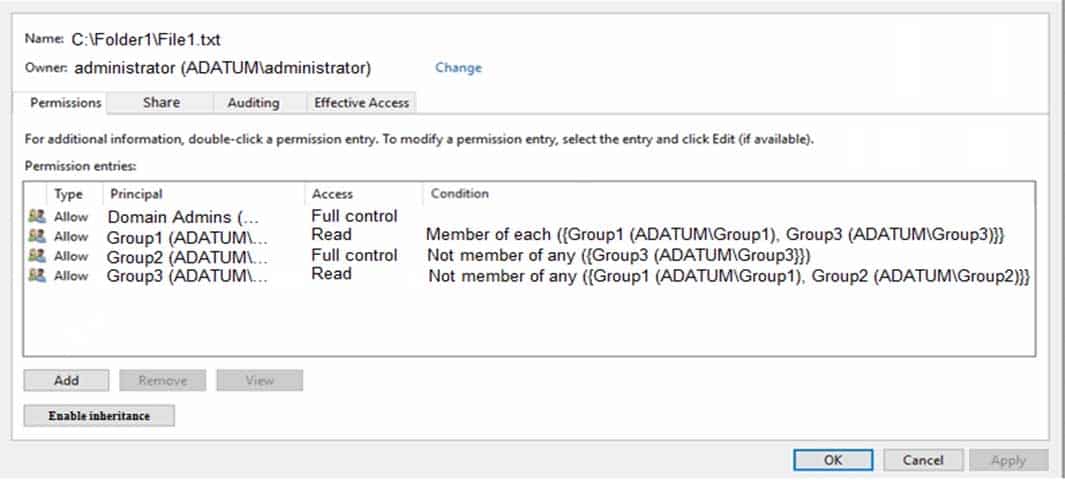
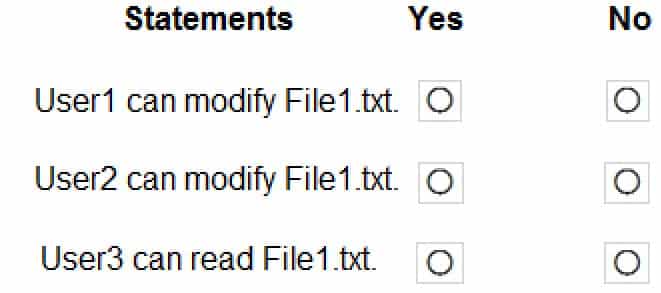
MD-100 Windows 10 Part 07 Q02 151 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
MD-100 Windows 10 Part 07 Q02 152 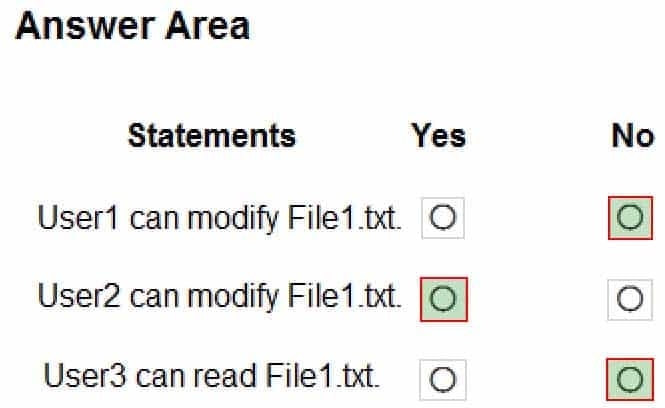
MD-100 Windows 10 Part 07 Q02 153 Explanation:Box 1: No
User1 only has Read access to the file.Box 2: Yes
User2 is in Group2 which has full control. The condition states that if the user is also a member of Group3, the permission would not apply. However, User2 is not in Group3 so the full control permission does apply.Box 3: No
User3 is in Group3 which does have Read access. However, the condition states that if the user is also in Group1 or Group2 then the permission does not apply. User3 is in Group2 so the Read permission granted to Group3 does not apply to User3. -
HOTSPOT
Your network contains an Active Directory domain that contains the objects shown in the following table.
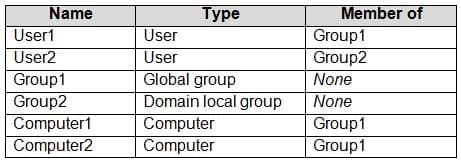
MD-100 Windows 10 Part 07 Q03 154 Computer1 contains the shared folders shown in the following table.

MD-100 Windows 10 Part 07 Q03 155 The computers have the network configurations shown in the following table.

MD-100 Windows 10 Part 07 Q03 156 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 07 Q03 157 
MD-100 Windows 10 Part 07 Q03 158 Explanation:Box 1: Yes
User1 is in Group1 which has permission to access the share so the share will be visible.Box 2: No
User2 is in Group2 which does not have permission to access Share1. Access-based enumeration is enabled so Share1 will not be listed as User2 does not have permission to access it.Box 3: No
Share2$ is a hidden share (dollar sign appended) so the share will never be listed. -
HOTSPOT
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 10.
The domain contains the users shown in the following table.
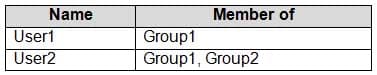
MD-100 Windows 10 Part 07 Q04 159 Computer1 contains the shared folders shown in the following table.
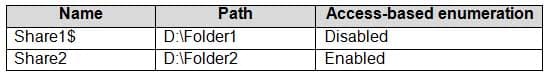
MD-100 Windows 10 Part 07 Q04 160 The shared folders have the permissions shown in the following table.

MD-100 Windows 10 Part 07 Q04 161 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 07 Q04 162 
MD-100 Windows 10 Part 07 Q04 163 Explanation:Box 1: No
Share1$ is a hidden share (dollar sign appended) so the share will never be visible.Box 2: Yes
User2 is in Group1 and Group2. Both groups have access to Share1$. Therefore, the contents of the shared folder will be visible.Box 3: No
User1 is in Group1. Group1 does not have the necessary security permission to access Share2. You need both security permissions (NTFS permissions) AND share permissions to view the contents of a shared folder. User1 has the necessary share permissions (Everyone: Read), but not the security permission. -
You customize the Start menu on a computer that runs Windows 10 as shown in the following exhibit.

MD-100 Windows 10 Part 07 Q05 164 You need to add Remote Desktop Connection to Group1 and remove Group3 from the Start menu.
Which two actions should you perform from the Start menu customizations? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- Unlock Group1.
- Remove Command Prompt from Group1.
- Delete Group3.
- Add Remote Desktop Connection to Group1.
- Rename Group3 as Group1.
Explanation:
A: You have to unlock Group1 before you can make any changes to it.
D: If you drag the Remote Desktop Connection from Group3 to Group1, Group3 will disappear. -
You have a computer named Computer1 that runs Windows 10.
On Computer1, you turn on File History.
You need to protect a folder named D:\Folder1 by using File History.
What should you do?
- From File Explorer, add D:\Folder1 to the Documents library
- From the Settings app, configure the Recovery settings
- From Backup and Restore (Windows 7), modify the backup settings
- From File History in Control Panel, configure the Advanced settings
Explanation:File History only backs up copies of files that are in your libraries (i.e., Documents, Music, Pictures, Videos, and Desktop folders) and the OneDrive files available offline on your PC. If you have files or folders elsewhere that you want backed up, you can add them to one of these folders.
-
HOTSPOT
You have a computer named Computer 1 that runs Windows 10.
You turn on System Protection and create a restore point named Point1.
You perform the following changes:
Add four files named File1.txt, File2.dll, File3.sys, and File4.exe to the desktop.
Run a configuration script that adds the following four registry keys:
– Key1 to HKEY_CURRENT_USER
– Key2 to HKEY_CLASSES_ROOT
– Key3 to HKEY_LOCAL_MACHINE\SYSTEM
– Key4 to HKEY_CURRENT_CONFIGYou restore Point1.
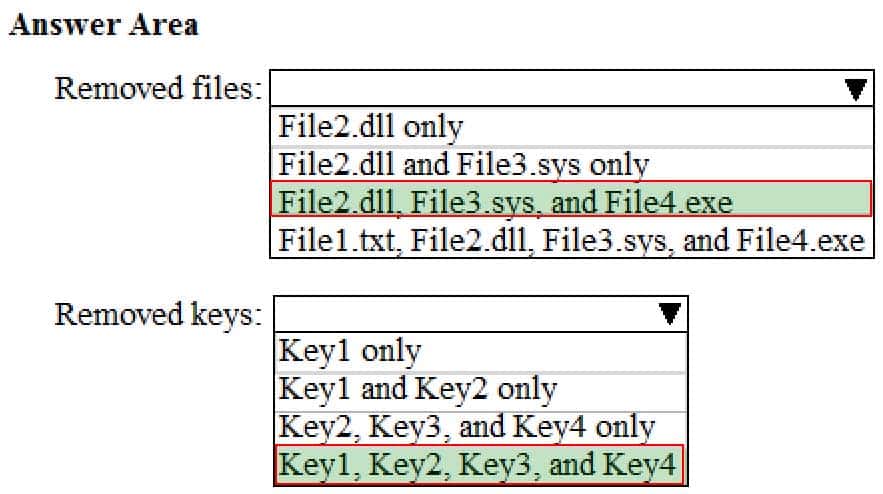
Which files and registry keys are removed? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
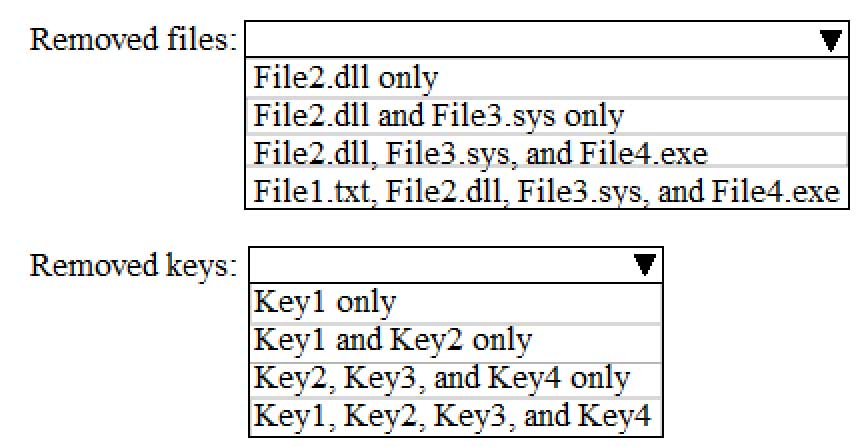
MD-100 Windows 10 Part 07 Q07 165 -
HOTSPOT
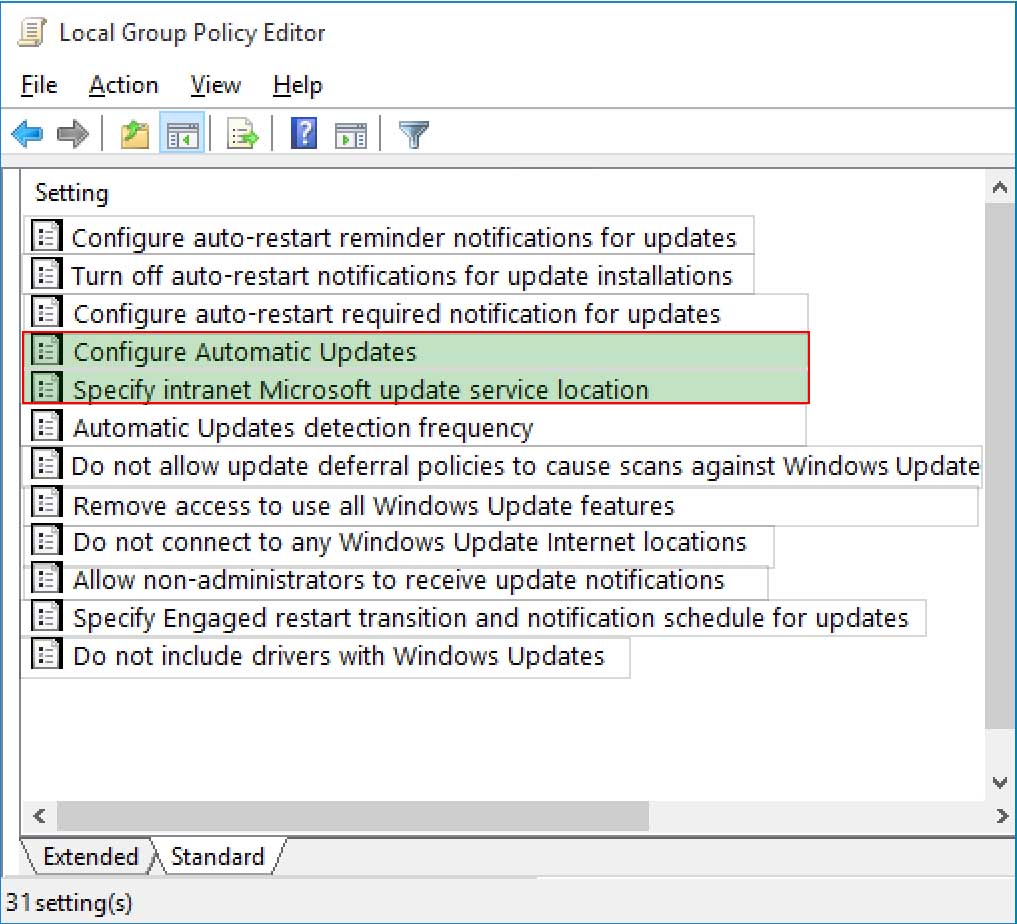
You have 10 computers that run Windows 10.
You have a Windows Server Update Services (WSUS) server.
You need to configure the computers to install updates from WSUS.
Which two settings should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
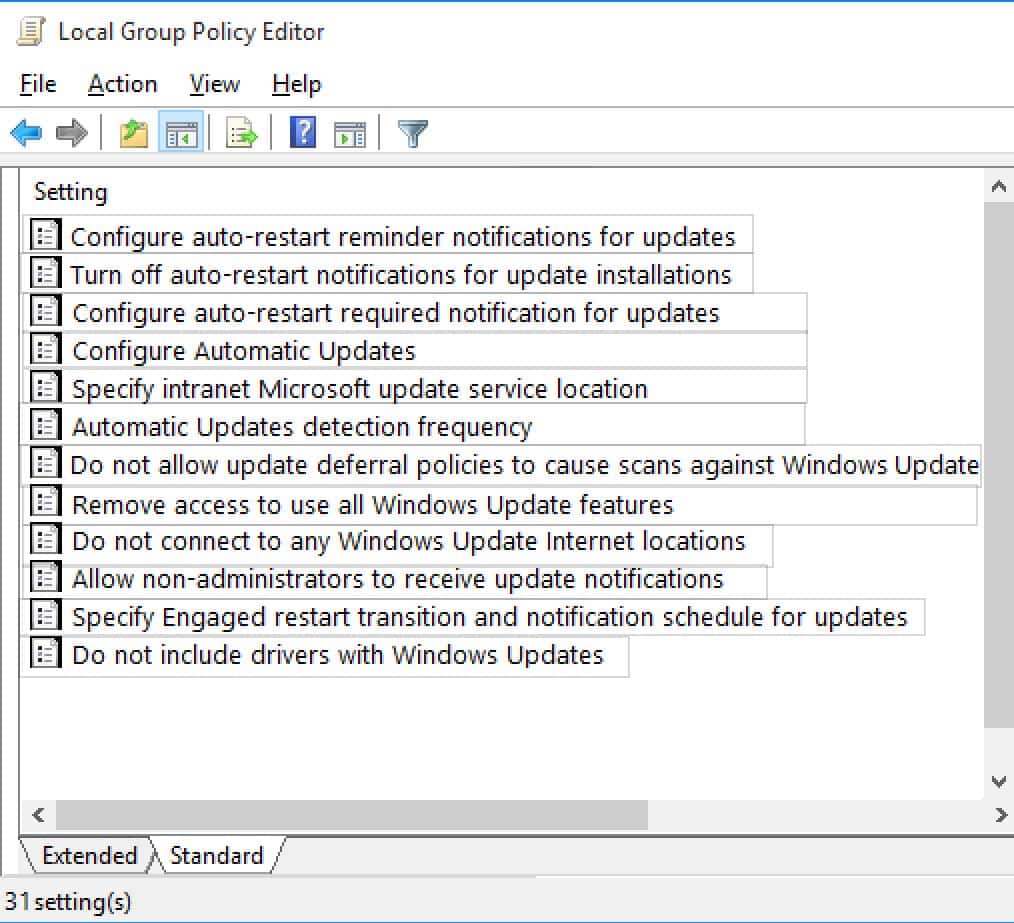
MD-100 Windows 10 Part 07 Q08 167 -
You have a Microsoft 365 Enterprise E3 license.
You have a computer named Computer1 that runs Windows 10.
You need to ensure that you can access the files on Computer1 by using a web browser on another computer.
What should you configure?
- Sync your settings in the Settings app
- the File Explorer desktop app
- the Microsoft OneDrive desktop app
- Default apps in the Settings app
-
You have computers that run Windows 10 and are configured as shown in the following table.

MD-100 Windows 10 Part 07 Q10 169 You have a removable USB drive named USBDrive1 that is encrypted by using BitLocker to Go.
You plan to use USBDrive1 on Computer1, Computer2, and Computer3.
You need to identify on which computers you can enable automatic unlocking of BitLocker on USBDrive1.
Which computers should you identify?
- Computer2 and Computer3 only
- Computer3 only
- Computer1 and Computer3 only
- Computer1, Computer2, and Computer3
Explanation:
The BitLocker key is stored in the registry when you enable auto-unlock but only if the operating system drive is encrypted with BitLocker. A TPM is not required. -
HOTSPOT
You have a computer named Computer1 that runs Windows 10 and has the users shown in the following table.
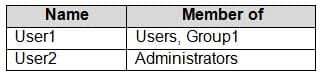
MD-100 Windows 10 Part 07 Q11 170 Computer1 contains the folders shown in the following table.
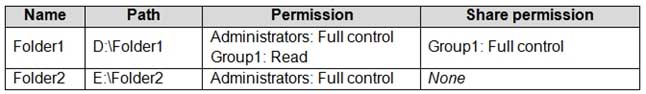
MD-100 Windows 10 Part 07 Q11 171 You move Folder1 into Folder2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 07 Q11 172 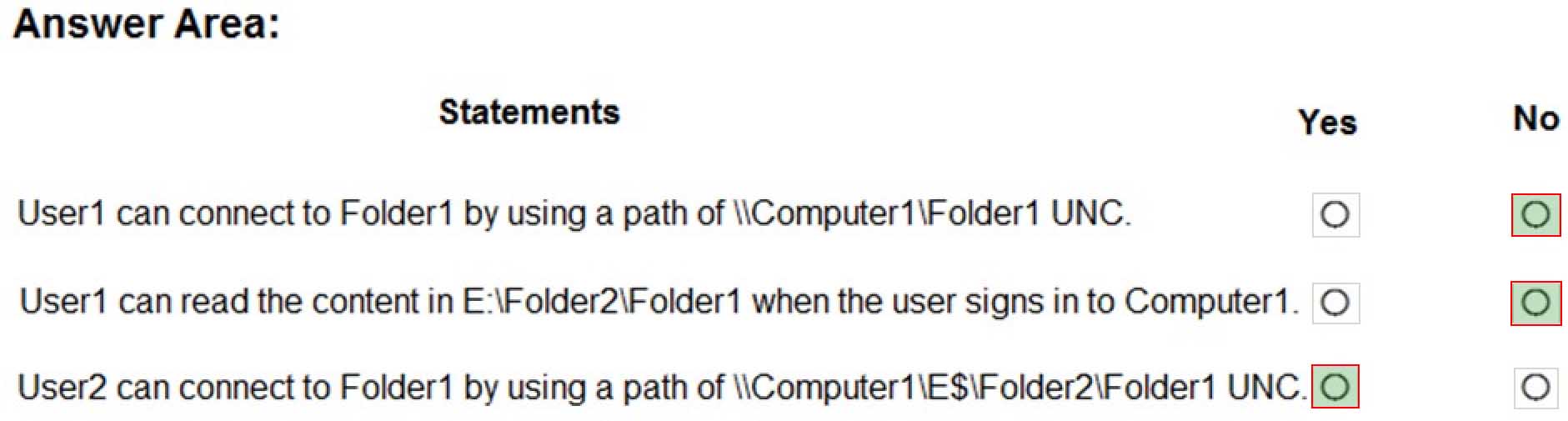
MD-100 Windows 10 Part 07 Q11 173 Explanation:Box 1: No
If you move a shared folder, the share will no longer work.Box 2: No
Folder1 will inherit the permissions of Folder2. User1 does not have permission to access Folder2.Box 3: Yes
User2 is a member of the Administrators group so he can access the administrative share \\Computer1\E$.
User2 has Full Control permission to Folder2 so he can access \\Computer1\E$\Folder2.
Folder1 will inherit the permissions of Folder2 so User2 can access \\Computer1\E$\Folder2\Folder1. -
HOTSPOT
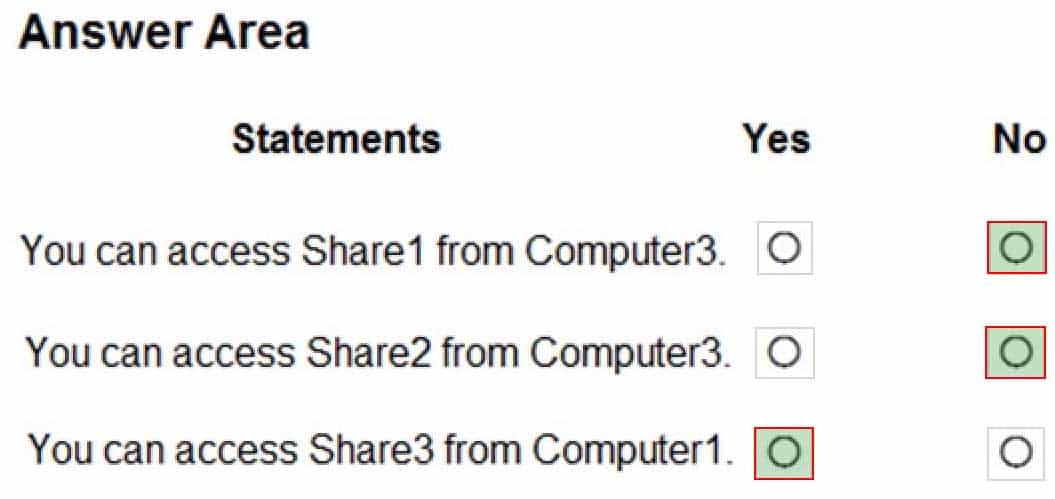
Your network contains the segments shown in the following table.

MD-100 Windows 10 Part 07 Q12 174 You have computers that run Windows 10 and are configured as shown in the following table.
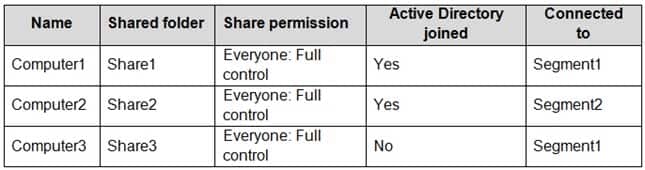
MD-100 Windows 10 Part 07 Q12 175 Windows Defender Firewall has the File and Printer Sharing allowed apps rule shown in the following table.
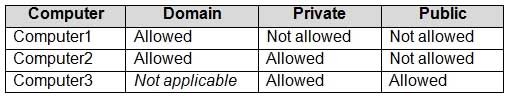
MD-100 Windows 10 Part 07 Q12 176 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
MD-100 Windows 10 Part 07 Q12 177 -
HOTSPOT
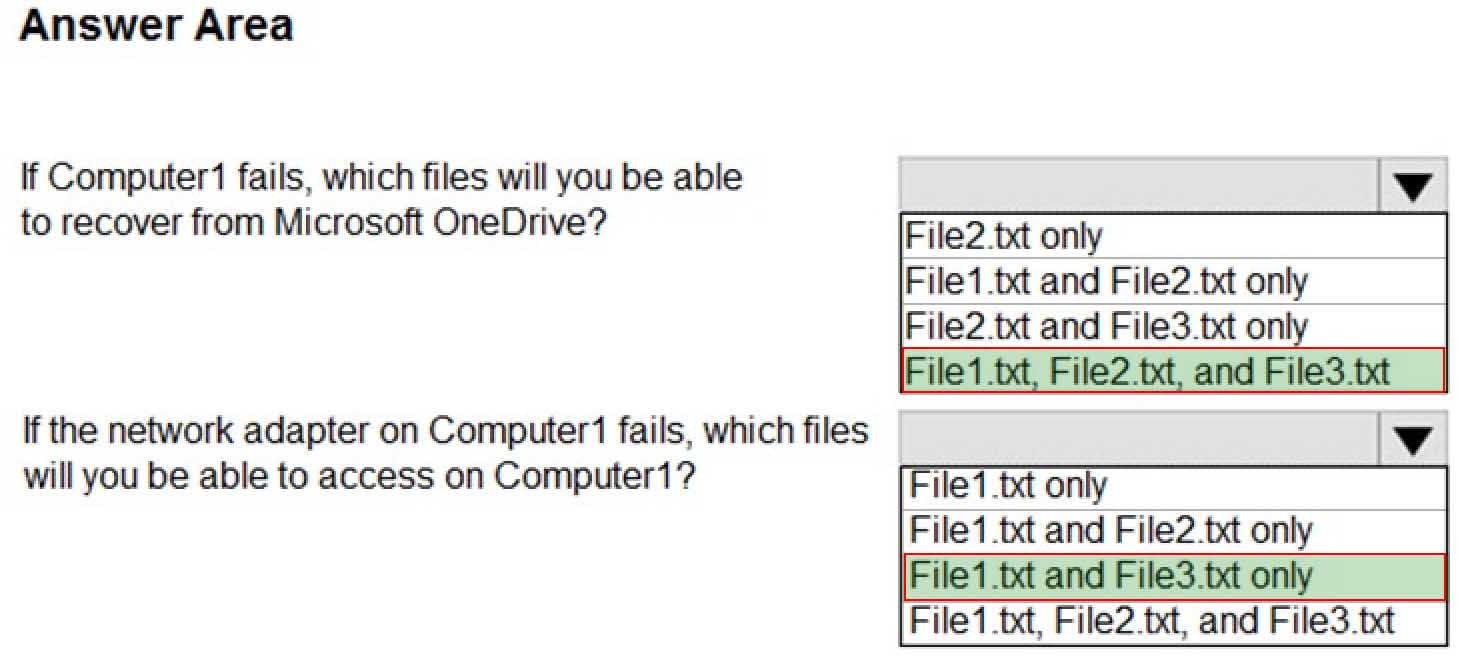
You have a workgroup computer named Computer1 that runs Windows 10. From File Explorer, you open OneDrive as shown in the following exhibit.
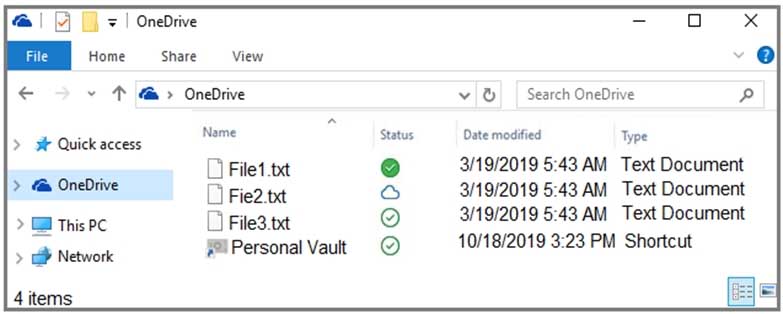
MD-100 Windows 10 Part 07 Q13 179 Use the drop-down menus to select the answer choice that answers each question based on the information presented on the graphic.
NOTE: Each correct selection is worth one point.
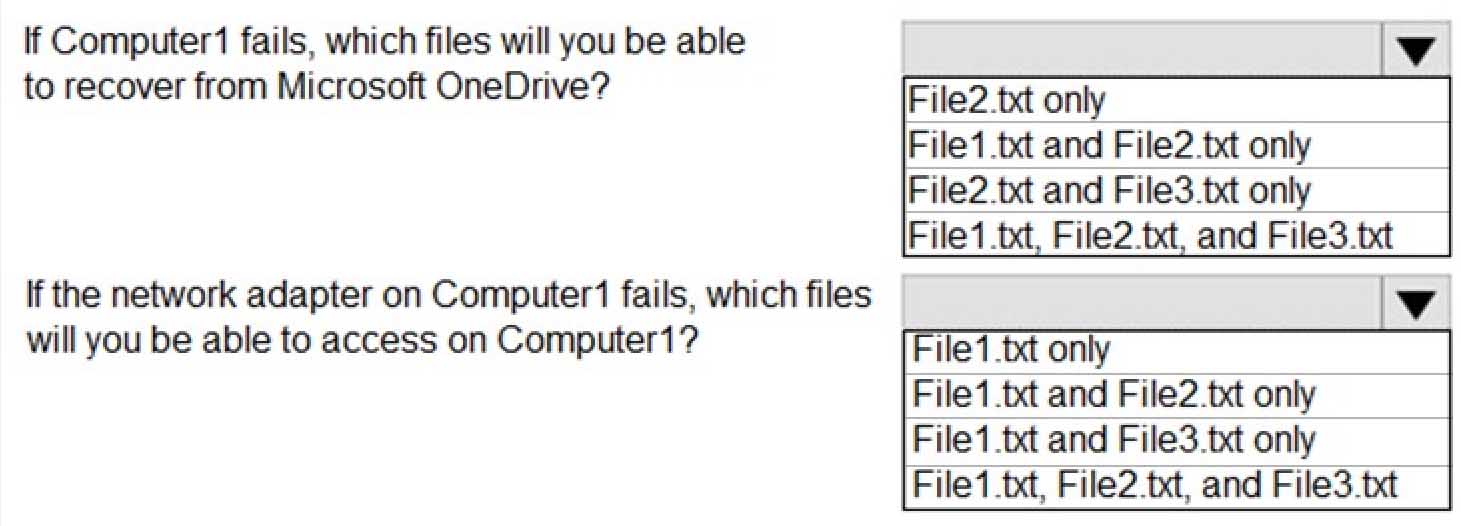
MD-100 Windows 10 Part 07 Q13 180 -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a workgroup computer that runs Windows 10. The computer contains the local user accounts shown in the following table.
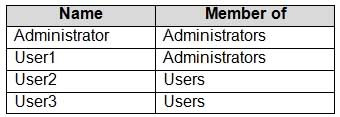
MD-100 Windows 10 Part 07 Q13 182 You need to configure the desktop background for User1 and User2 only.
Solution: You create two new local Group Policy Objects (GPOs) and apply one GPO to User1 and the other GPO to User2. You configure the Desktop Wallpaper setting in each GPO.
Does this meet the goal?
- Yes
- No
-
Your network contains an Active Directory domain. The domain contains 1,000 computers that run Windows 10.
You discover that when users are on their lock screen, they see a different background image every day, along with tips for using different features in Windows 10.
You need to disable the tips and the daily background image for all the Windows 10 computers.
Which Group Policy settings should you modify?
- Turn off the Windows Welcome Experience
- Turn off Windows Spotlight on Settings
- Do not suggest third-party content in Windows spotlight
- Turn off all Windows spotlight features
-
HOTSPOT
You have a computer named Computer1 that runs Windows 10. Computer1 contains a folder named Data on drive C. The Advanced Security Settings for the Data folder are shown in the exhibit. (Click the Exhibit tab.)
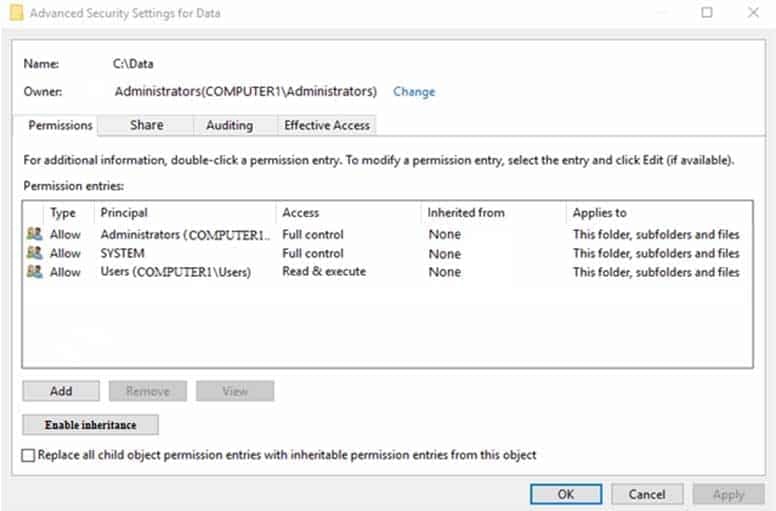
MD-100 Windows 10 Part 07 Q16 183 You share C:\Data as shown in the following table.

MD-100 Windows 10 Part 07 Q16 184 User1 is a member of the Users group.
Administrators are assigned Full control NTFS permissions to C:\Data.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 07 Q16 185 
MD-100 Windows 10 Part 07 Q16 186 Explanation:User1 cannot write files when connected to \\Computer1\Data because the Users group only has Read & Execute NTFS permission to the C:\Data folder and there are no explicit NTFS permissions for User1.
User1 cannot write files locally because the Users group only has Read & Execute NTFS permission to the C:\Data folder and there are no explicit NTFS permissions for User1.
Administrators cannot change the NTFS permissions of files and folders when connected to \\Computer1\Data because they only have Change share permission. The would need Full Control share permission. They could do it locally because they have Full Control NTFS permission.
-
You have a file named Reg1.reg that contains the following content.

MD-100 Windows 10 Part 07 Q17 187 What is the effect of importing the file?
- A key named command will be renamed as notepad.exe.
- In a key named Notepad, the command value will be set to @=”notepad.exe”.
- In a key named command, the default value will be set to notepad.exe.
-
You have a computer named Computer1 that runs Windows 10.
On Computer1, you create the local users shown in the following table.
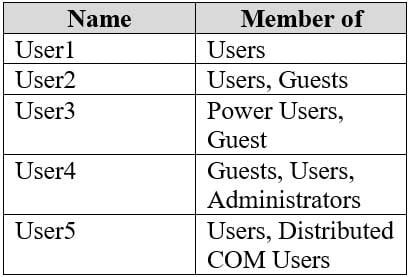
MD-100 Windows 10 Part 07 Q18 188 Which two user profiles will persist after each user signs out? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- User1
- User2
- User3
- User4
- User5
-
HOTSPOT
You have a computer that runs Windows 10. The computer is in a workgroup. The computer is used to provide visitors with access to the Internet.
You need to configure the computer to meet the following requirements:
-Always sign in automatically as User1.
-Start an application named App1.exe at sign-in.What should you use to meet each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 07 Q19 189 -
HOTSPOT
You have four computers that run Windows 10. The computers are configured as shown in the following table.
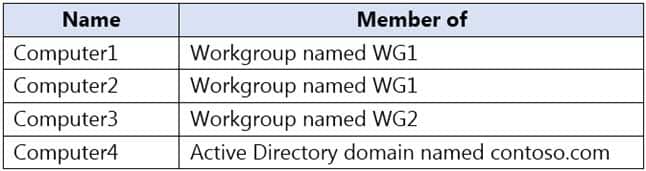
MD-100 Windows 10 Part 07 Q20 191 On Computer1, you create a user named User1. In the domain, you create a user named User2.
You create the groups shown in the following table.

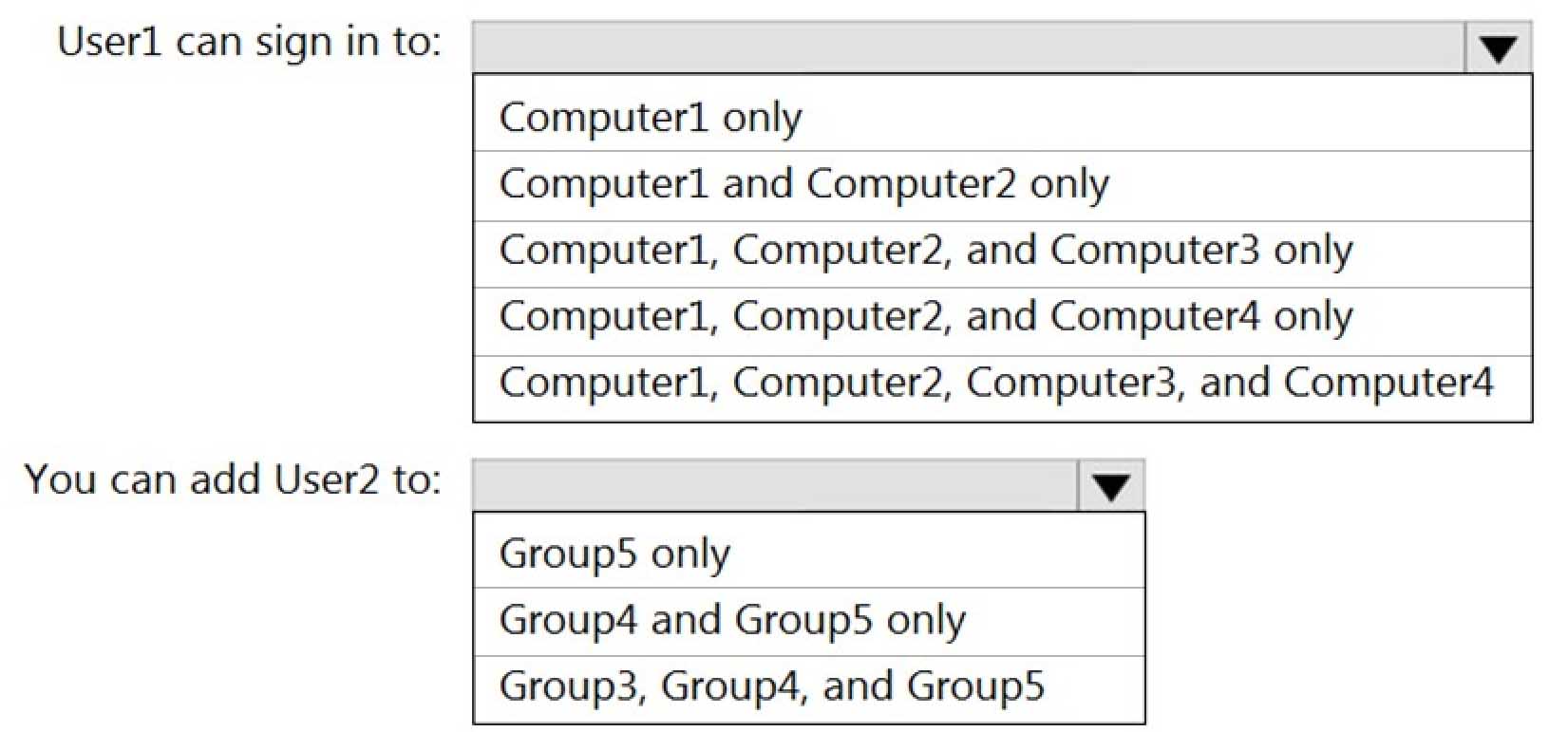
MD-100 Windows 10 Part 07 Q20 192 You need to identify to which computers User1 can sign in, and to which groups you can add User2.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MD-100 Windows 10 Part 07 Q20 193 
MD-100 Windows 10 Part 07 Q20 194 Explanation:Box 1: Computer 1 only.
User1’s account was created on Computer1. The account is a local account on Computer1. Therefore, User1 can only sign in to Computer1.Box 2: Group5 only.
User2’s account was created in the domain. A domain is a security boundary. Therefore, you can only add User2 to groups in the domain.