MD-100 : Windows 10 : Part 09
MD-100 : Windows 10 : Part 09
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
General Overview
Litware, Inc. is a consulting company that has a main office in Montreal and branch offices in Seattle and New York.
Environment
Existing Environment
The network contains an on-premises Active Directory domain named litware.com. The domain contains the computers shown in the following table.

MD-100 Windows 10 Part 09 Q01 231 The network that uses 192.168.10.0/24 connects to the internet by using a Network Address Translation (NAT) device.
Windows Admin Center is installed on Server1.
The domain contains the groups shown in the following table.
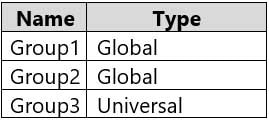
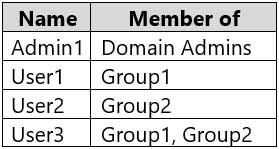
MD-100 Windows 10 Part 09 Q01 232 The domain contains the users shown in the following table.
MD-100 Windows 10 Part 09 Q01 233 Computer1 Configuration
Computer1 contains the local user accounts shown in the following table.
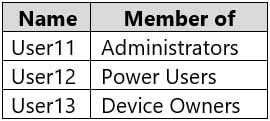
MD-100 Windows 10 Part 09 Q01 234 Computer1 contains a folder named D:\Folder1 that has permission inheritance disabled.
Computer1 contains a file named D:\Folder1\Report.docx that has the permissions shown in the following table.
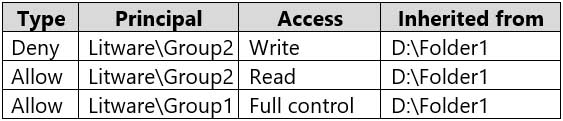
MD-100 Windows 10 Part 09 Q01 235 D:\Folder1\Report.docx has auditing configured as shown in the following table.
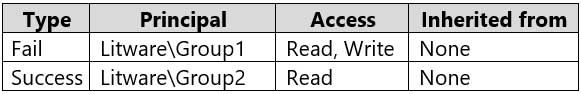
MD-100 Windows 10 Part 09 Q01 236 The Local Computer Policy for Computer1 is configured as shown in the following table.
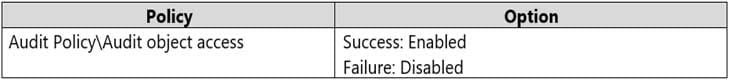
MD-100 Windows 10 Part 09 Q01 237 Windows Defender Firewall for Computer1 has the rules shown in the following table.

MD-100 Windows 10 Part 09 Q01 238 Computer2 Configuration
Computer2 contains the local user accounts shown in the following table.
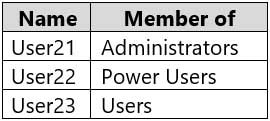
MD-100 Windows 10 Part 09 Q01 239 Group1 and Group2 are members of the Remote Desktop Users group.
The Local Computer Policy for Computer2 is configured as shown in the following table.
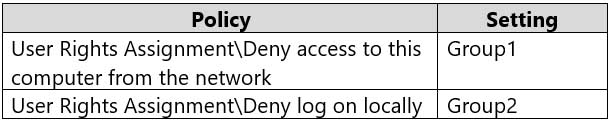
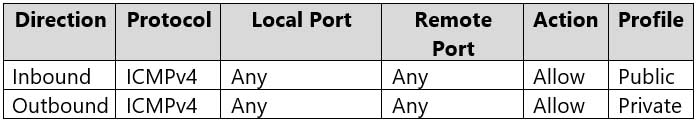
MD-100 Windows 10 Part 09 Q01 240 Windows Defender Firewall for Computer2 has the rules shown in the following table.
MD-100 Windows 10 Part 09 Q01 241 Computer3 Configuration
Computer3 contains the local user accounts shown in the following table.
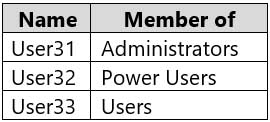
MD-100 Windows 10 Part 09 Q01 242 Windows Defender Firewall for Computer3 has the rules shown in the following table.

MD-100 Windows 10 Part 09 Q01 243 Requirements and Planned Changes
Planned Changes
Litware plans to make the following changes on Computer1:
-Grant User1 Allow Full control permissions to D:\Folder1\Report.docx.
-Grant User2 Allow Full control permissions to D:\Folder1\Report.docx.
-Grant User3 Allow Full control permissions to D:\Folder1.Technical Requirements
Litware identifies the following technical requirements:
-Configure custom Visual Effect performance settings for Computer1.
-Manage Computer2 by using Windows Admin Center.
-Minimize administrative effort.Delivery Optimization on the computers that run Windows 10 must be configured to meet the following requirements:
-Content must be downloaded only from an original source.
-Downloading content from peer cache clients must be prevented.
-Downloads must be optimized by using the Delivery Optimization cloud service.-
HOTSPOT
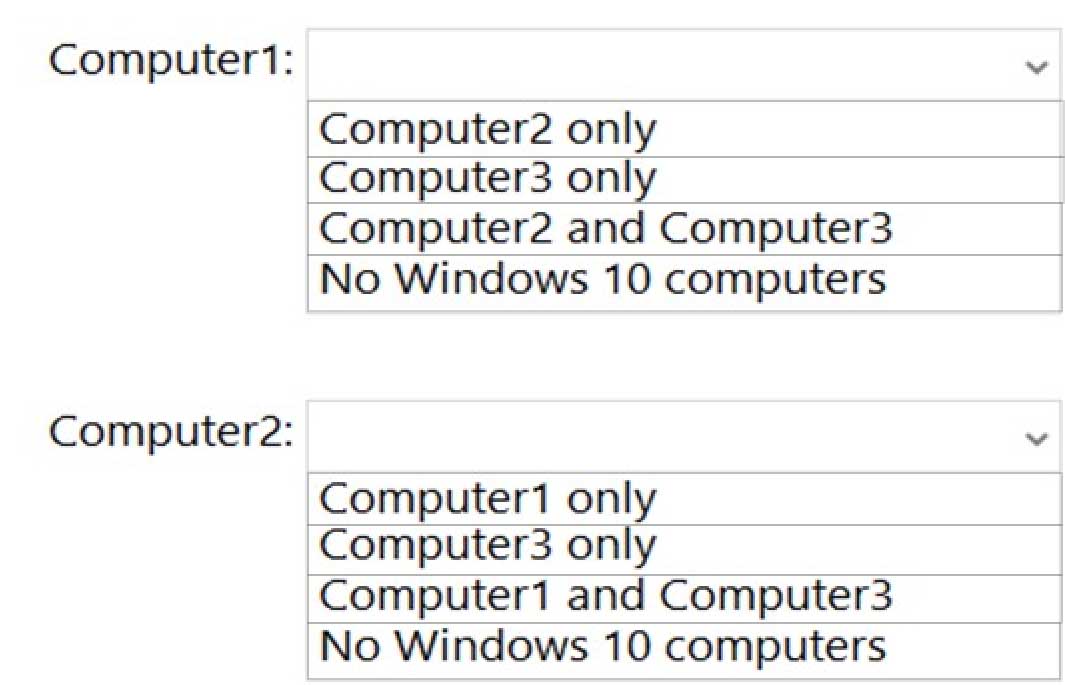
Which Windows 10 computers can you ping successfully from Computer1 and Computer2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
MD-100 Windows 10 Part 09 Q01 244 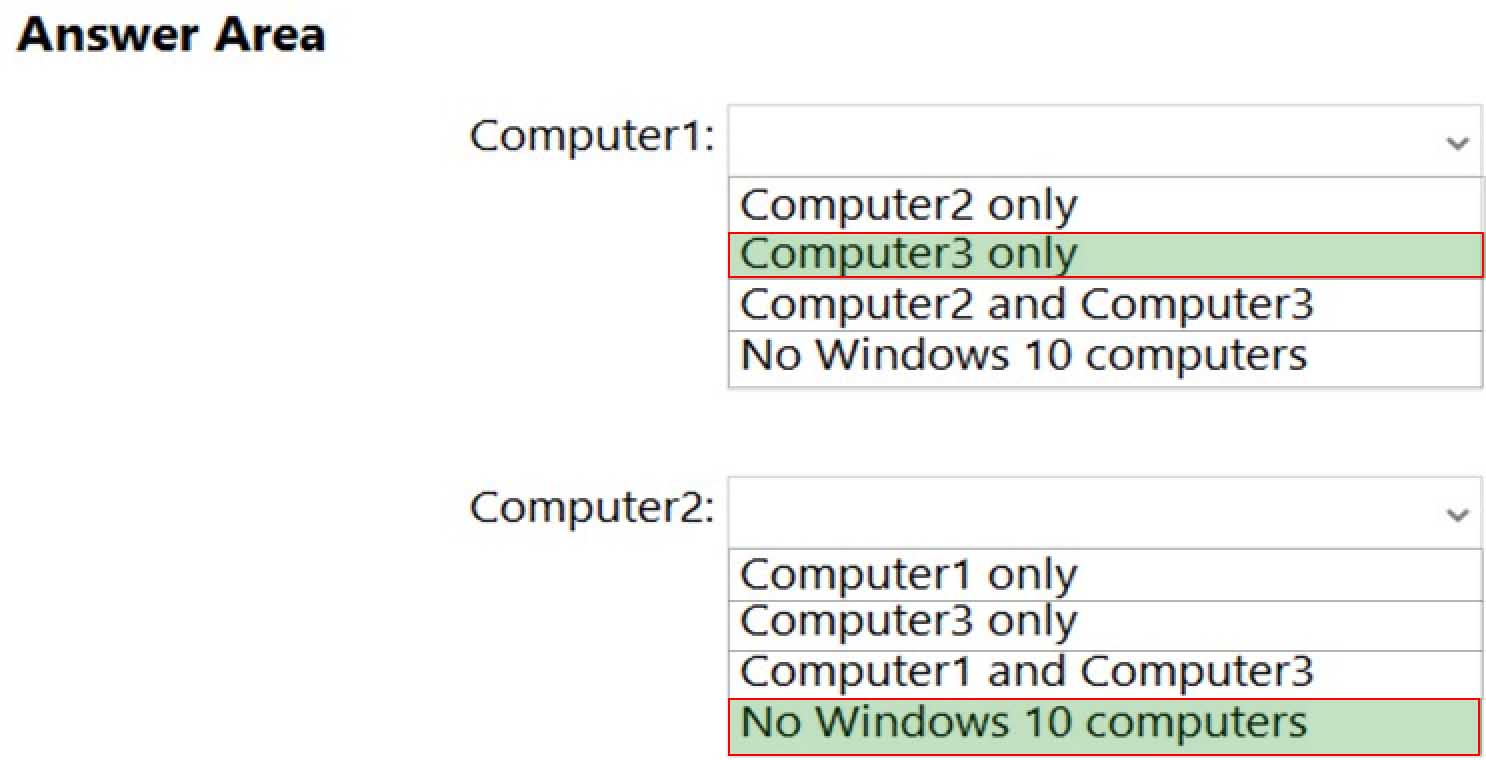
MD-100 Windows 10 Part 09 Q01 245 Explanation:Box 1: Computer3 only.
Computer1 and Computer2 are domain joined so both will be using the Domain profile. The firewall rules on Computer1 allow outbound ICMP on all profiles so outbound ICMP will be allowed on the Domain profile.
The firewall rules on Computer2 allow inbound ICMP on the Public profile only, so it will be blocked on the domain profile. Therefore, Computer2 cannot be pinged.
The firewall rules on Computer3 allow inbound ICMP on all profiles. Therefore, Computer3 will not block the inbound pings.Box 2: No Windows 10 computers.
The firewall rules on Computer2 allow outbound ICMP on the Private profile only, so it will be blocked on the domain profile. Therefore, Computer2 cannot ping any computers. -
HOTSPOT
You implement the planned changes for Computer1.
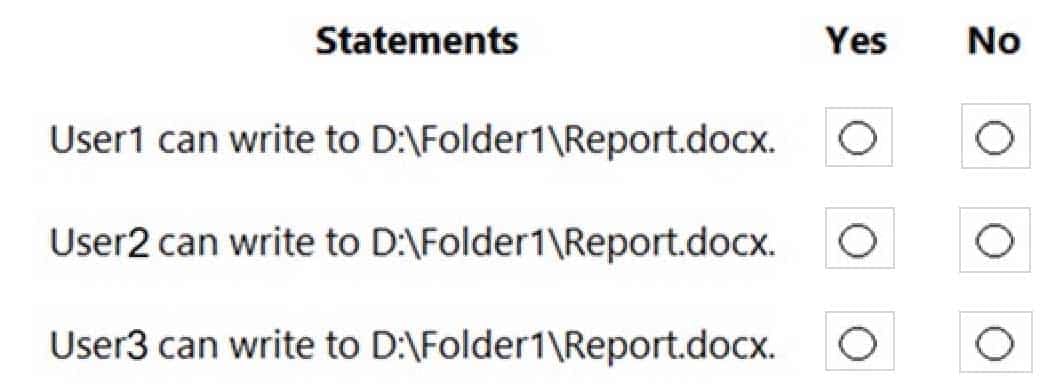
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
MD-100 Windows 10 Part 09 Q01 246 
MD-100 Windows 10 Part 09 Q01 245 Explanation:Box 1: Yes
User1 already has full control access through membership of Group1. Therefore, User1 can write to the file.Box 2: No
The planned changes will grant User2 full control access to the file. However, User2 is a member of Group2 which has Deny/Write access. The Deny permission will always take precedence. Therefore, User2 will not be able to write to the file.Box 3: No
The planned changes will grant User3 full control access to the folder. That permission will be inherited by the file. However, User3 is a member of Group2 which has Deny/Write access. The Deny permission will always take precedence. Therefore, User3 will not be able to write to the file.
-
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam times as you would like to complete each case. However, there may be additional studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
Fabrikam, Inc. is a distribution company that has 500 employees and 100 contractors.
Existing Environment
Active Directory
The network contains an Active Directory forest named fabrikam.com. The forest is synced to Microsoft Azure Active Directory (Azure AD). All the employees are assigned Microsoft 365 E3 licenses.
The domain contains a user account for an employee named User10.
Client Computers
All the employees have computers that run Windows 10 Enterprise. All the computers are installed without Volume License Keys. Windows 10 license keys are never issued.
All the employees register their computer to Azure AD when they first receive the computer.
User10 has a computer named Computer10.
All the contractors have their own computer that runs Windows 10. None of the computers are joined to Azure AD.
Operational Procedures
Fabrikam has the following operational procedures:
Updates are deployed by using Windows Update for Business.
When new contractors are hired, administrators must help the contactors configure the following settings on their computer:
– User certificates
– Browser security and proxy settings
– Wireless network connection settingsSecurity Policies
The following security policies are enforced on all the client computers in the domain:
-All the computers are encrypted by using BitLocker Drive Encryption (BitLocker). BitLocker recovery information is stored in Active Directory and Azure AD.
-The local Administrators group on each computer contains an enabled account named LocalAdmin.
-The LocalAdmin account is managed by using Local Administrator Password Solution (LAPS).Problem Statements
Fabrikam identifies the following issues:
-Employees in the finance department use an application named Application1. Application1 frequently crashes due to a memory error. When Application1 crashes, an event is written to the application log and an administrator runs a script to delete the temporary files and restart the application.
-When employees attempt to connect to the network from their home computer, they often cannot establish a VPN connection because of misconfigured VPN settings.
-An employee has a computer named Computer11. Computer11 has a hardware failure that prevents the computer from connecting to the network.
-User10 reports that Computer10 is not activated.Technical Requirements
Fabrikam identifies the following technical requirements for managing the client computers:
-Provide employees with a configuration file to configure their VPN connection.
-Use the minimum amount of administrative effort to implement the technical requirements.
-Identify which employees’ computers are noncompliant with the Windows Update baseline of the company.
-Ensure that the service desk uses Quick Assist to take remote control of an employee’s desktop during support calls.
-Automate the configuration of the contractors’ computers. The solution must provide a configuration file that the contractors can open from a Microsoft SharePoint site to apply the required configurations.-
You need to recommend a solution to configure the employee VPN connections.
What should you include in the recommendation?
- Remote Access Management Console
- Group Policy Management Console (GPMC)
- Connection Manager Administration Kit (CMAK)
- Microsoft Intune
-
You need to take remote control of an employee’s computer to troubleshoot an issue.
What should you send to the employee to initiate a remote session?
- a numeric security code
- a connection file
- an Easy Connect request
- a password
-
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
Contoso has IT, human resources (HR), and finance departments.
Contoso recently opened a new branch office in San Diego. All the users in the San Diego office work from home.
Existing environment
Contoso uses Microsoft 365.
The on-premises network contains an Active Directory domain named contoso.com. The domain is synced to Microsoft Azure Active Directory (Azure AD).
All computers run Windows 10 Enterprise.
You have four computers named Computer1, Computer2, Computer3, and ComputerA. ComputerA is in a workgroup on an isolated network segment and runs the Long Term Servicing Channel version of Windows 10. ComputerA connects to a manufacturing system and is business critical. All the other computers are joined to the domain and run the Semi-Annual Channel version of Windows 10.
In the domain, you create four groups named Group1, Group2, Group3, and Group4.
Computer2 has the local Group Policy settings shown in the following table.

MD-100 Windows 10 Part 09 Q03 249 The computers are updated by using Windows Update for Business.
The domain has the users shown in the following table.
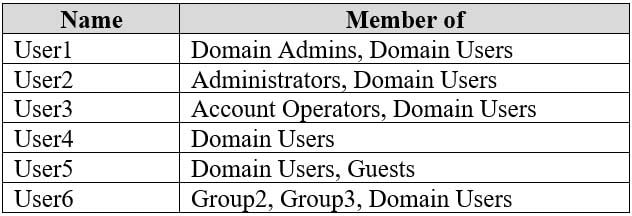
MD-100 Windows 10 Part 09 Q03 248 Computer1 has the local users shown in the following table.

MD-100 Windows 10 Part 09 Q03 247 Requirements
Planned Changes
Contoso plans to purchase computers preinstalled with Windows 10 Pro for all the San Diego office users.
Technical requirements
Contoso identifies the following technical requirements:
-The computers in the San Diego office must be upgraded automatically to Windows 10 Enterprise and must be joined to Azure AD the first time a user starts each new computer. End users must not be required to accept the End User License Agreement (EULA).
-Helpdesk users must be able to troubleshoot Group Policy object (GPO) processing on the Windows 10 computers. The helpdesk users must be able to identify which Group Policies are applied to the computers.
-Users in the HR department must be able to view the list of files in a folder named D:\Reports on Computer3.
-ComputerA must be configured to have an Encrypting File System (EFS) recovery agent.
-Quality update installations must be deferred as long as possible on ComputerA.
-Users in the IT department must use dynamic lock on their primary device.
-User6 must be able to connect to Computer2 by using Remote Desktop.
-The principle of least privilege must be used whenever possible.
-Administrative effort must be minimized whenever possible.
-Kiosk (assigned access) must be configured on Computer1.-
You need to meet the technical requirement for User6.
What should you do?
- Add User6 to the Remote Desktop Users group in the domain.
- Remove User6 from Group2 in the domain.
- Add User6 to the Remote Desktop Users group on Computer2.
- And User6 to the Administrators group on Computer2.
-
You need to meet the technical requirement for the IT department users.
What should you do first?
- Issue computer certificates
- Distribute USB keys to the IT department users.
- Enable screen saver and configure a timeout.
- Turn on Bluetooth.
-
-
You have an Azure Active Directory (Azure AD) tenant that contains a user named user1@contoso.com.
You have a computer named Computer1 that runs Windows 10.
You join Computer1 to Azure AD. You enable Remote Desktop on Computer1.
User1@contoso.com attempts to connect to Computer1 by using Remote Desktop and receives the following error message: “The logon attempt failed.”
You need to ensure that the user can connect to Computer1 by using Remote Desktop.
What should you do first?
- In Azure AD, assign user1@contoso.com the Cloud device administrator role.
- From the local Group Policy, modify the Allow log on through Remote Desktop Services user right.
- In Azure AD, assign user1@contoso.com the Security administrator role.
- On Computer1, create a local user and add the new user to the Remote Desktop Users group.
-
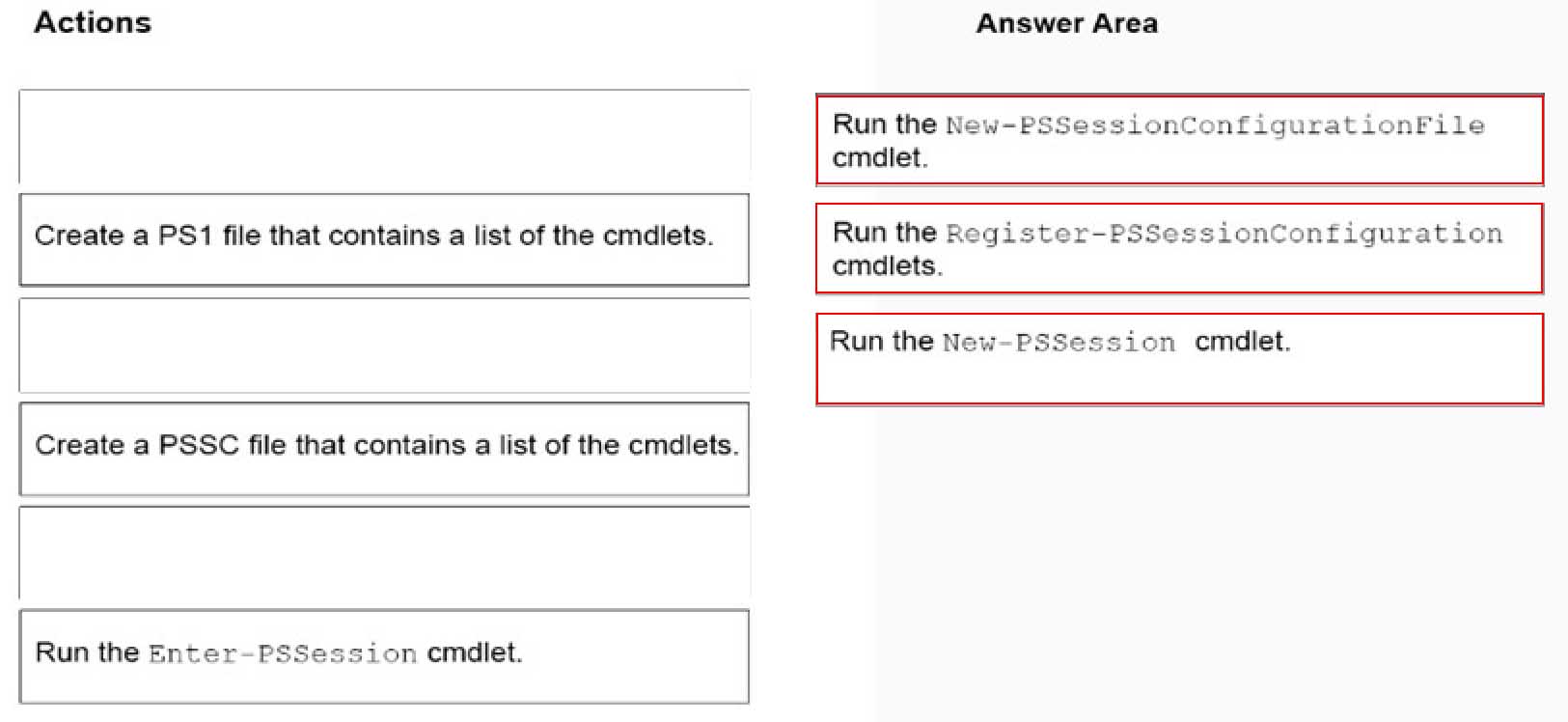
DRAG DROP
You enable Windows PowerShell remoting on a computer that runs Windows 10.
You need to limit which PowerShell cmdlets can be used in a remote session.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

MD-100 Windows 10 Part 09 Q05 250 -
You have a VPN server that accepts PPTP and L2TP connections and is configured as shown in the following exhibit.

MD-100 Windows 10 Part 09 Q06 252 A user named User1 has a computer that runs Windows 10 and has a VPN connection configured as shown in the following exhibit.
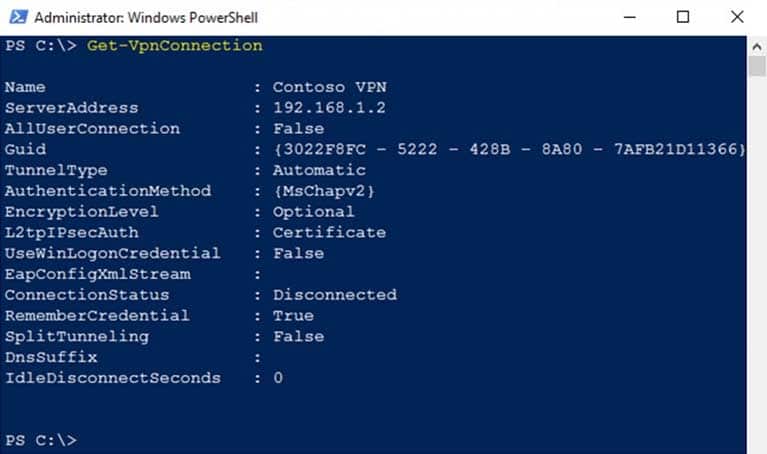
MD-100 Windows 10 Part 09 Q06 253 User1 fails to establish a VPN connection when connected to a home network.
You need to identify which VPN client setting must be modified.
What should you identify?
- ServerAddress
- TunnelType
- AuthenticationMethod
- L2tpIPsecAuth
- EncryptionLevel
Explanation:
The server address is a private IP address. This needs to be the public IP address of the VPN server. -
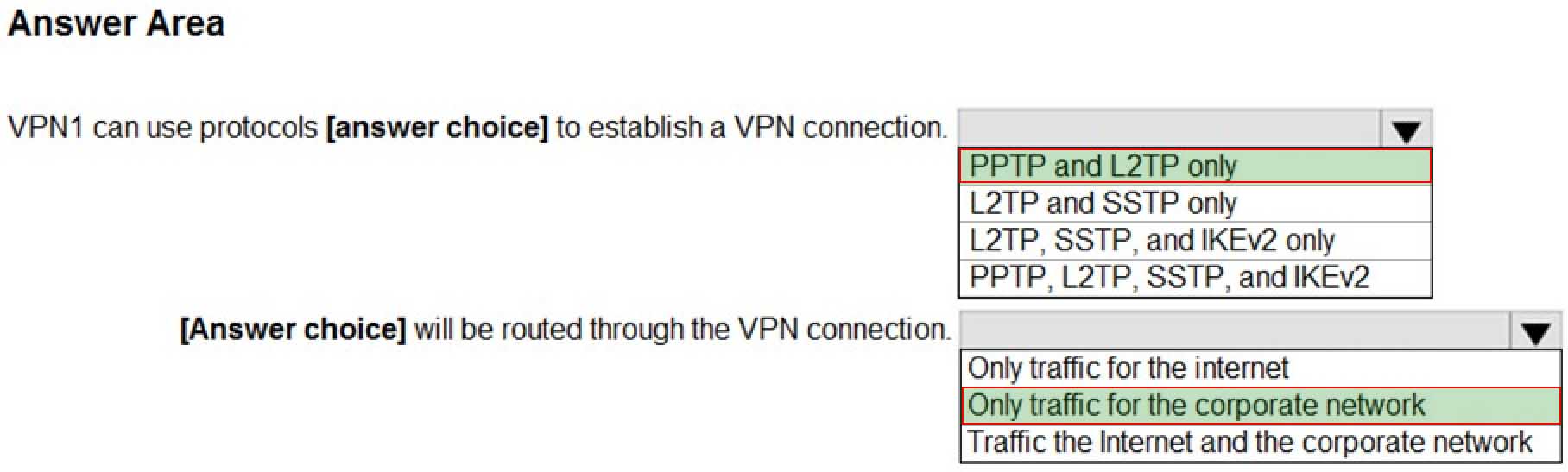
HOTSPOT
You have a computer named Computer1 that runs Windows 10.
On Computer1, you create a VPN connection as shown in the following exhibit.
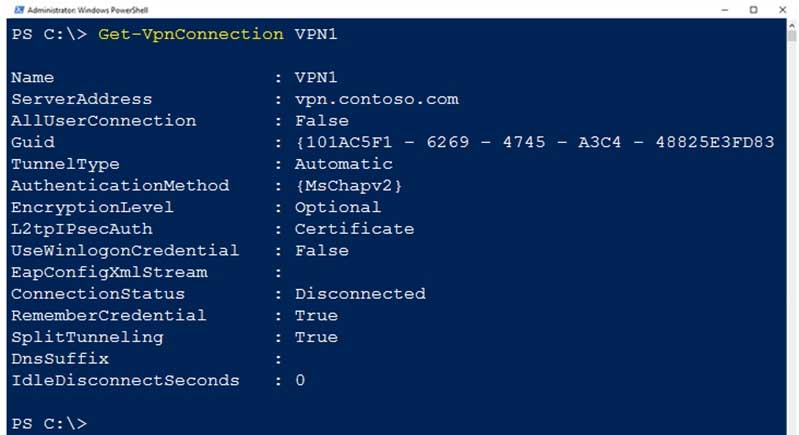
MD-100 Windows 10 Part 09 Q07 254 The corporate network contains a single IP subnet.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 09 Q07 255 -
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains a user named UserA.
You have two computers named Computer1 and Computer2 that run Windows 10 and are joined to contoso.com.
You need to ensure that UserA can connect to Computer2 from Computer1 by using Remote Desktop.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- On Computer1, modify the registry.
- On Computer2, modify the registry.
- On Computer1, modify the properties of UserA.
- On Computer1, enable Remote Desktop.
- On Computer2, modify the properties of UserA.
- On Computer 2, enable Remote Desktop.
- On Computer2, add the Everyone group to the Remote Desktop Users group.
- On Computer1, add the Everyone group to the Remote Desktop Users group.
-
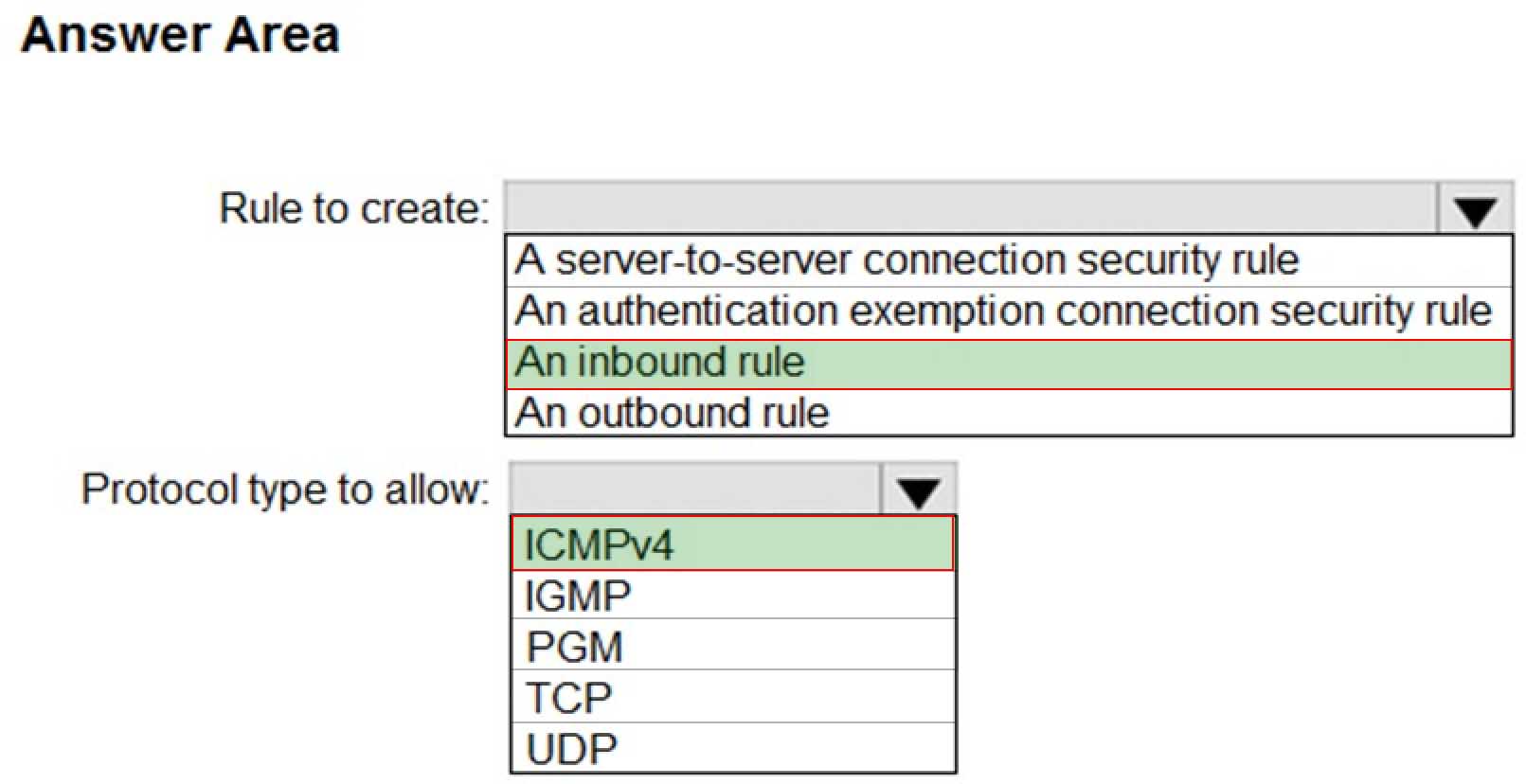
HOTSPOT
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 10.
You need to ensure that Computer1 will respond to ping requests.
How should you configure Windows Defender Firewall on Computer1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 09 Q09 257 -
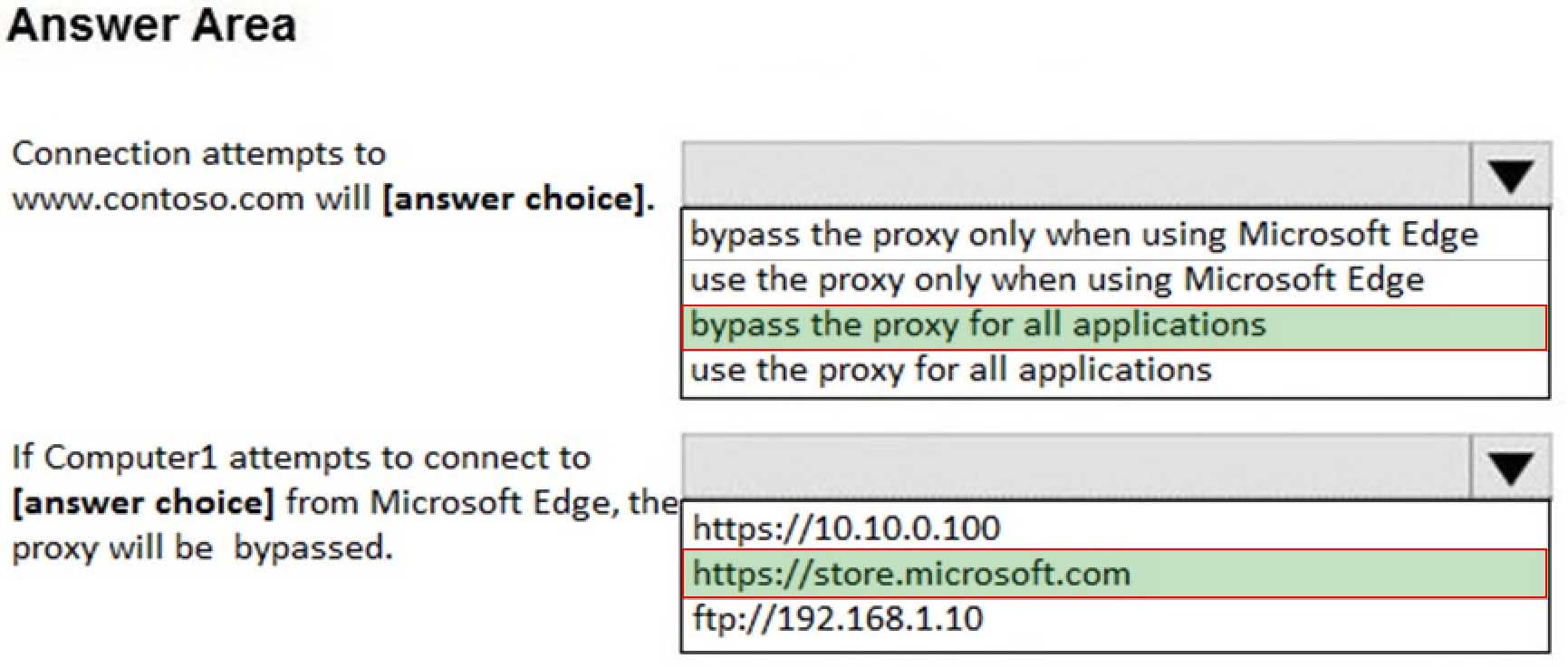
HOTSPOT
You have a computer named Computer1 that runs Windows 10. Computer1 has an IP address of 10.10.1.200 and a subnet mask of 255.255.255.0.
You configure the proxy settings on Computer1 as shown in the following exhibit.

MD-100 Windows 10 Part 09 Q10 259 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 09 Q10 260 -
You have a computer that is configured as shown in the following exhibit.
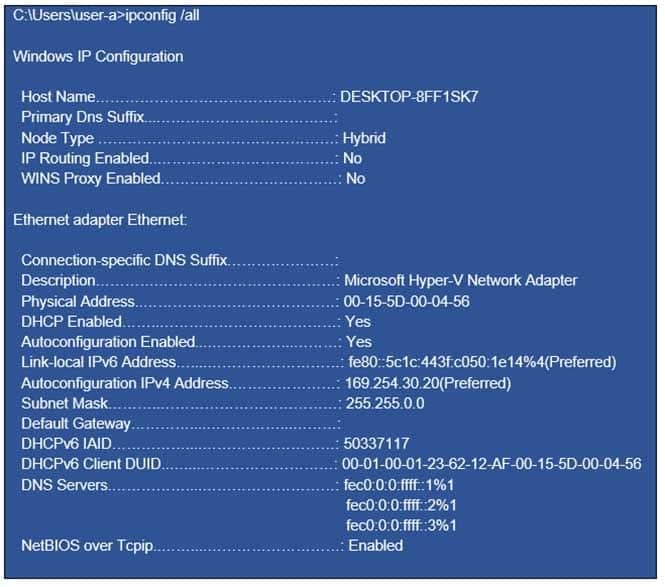
MD-100 Windows 10 Part 09 Q11 262 What can the computer connect to?
- all the local computers and the remote computers within your corporate network only
- all the local computers and the remote computers, including Internet hosts
- only other computers on the same network segment that have automatic private IP addressing (APIPA)
- only other computers on the same network segment that have an address from a class A network ID
Explanation:
The computer has IPv4 address of 169.254.30.20. 169.254.x.x is an automated APIPA address. -
Your network contains an Active Directory domain named contoso.com.
A user named User1 has a personal computer named Computer1 that runs Windows 10 Pro. User1 has a VPN connection to the corporate network.
You need to ensure that when User1 connects to the VPN, network traffic uses a proxy server located in the corporate network. The solution must ensure that User1 can access the Internet when disconnected from the VPN.
What should you do?
- From Control Panel, modify the Windows Defender Firewall settings
- From the Settings app, modify the Proxy settings for the local computer
- From Control Panel, modify the properties of the VPN connection
- From the Settings app, modify the properties of the VPN connection
Explanation:
In the Properties of the VPN you can add a proxy setting. The proxy setting will only be active when the user connects to the VPN. -
You deploy 100 computers that run Windows 10. Each computer has a cellular connection and a Wi-Fi connection.
You need to prevent the computers from using the cellular connection unless a user manually connects to the cellular network.
What should you do?
- Set the Use cellular instead of Wi-Fi setting for the cellular connection to Never
- Run the netsh wlan set hostednetwork mode=disallow command
- Clear the Let Windows manage this connection check box for the cellular connection
- Select the Let Windows manage this connection check box for the Wi-Fi connection
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a laptop named Computer1 that runs Windows 10.
When in range, Computer1 connects automatically to a Wi-Fi network named Wireless1.
You need to prevent Computer1 from automatically connecting to Wireless1.
Solution: From a command prompt, you run netsh wlan delete profile name=”Wireless1″.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a laptop named Computer1 that runs Windows 10.
When in range, Computer1 connects automatically to a Wi-Fi network named Wireless1.
You need to prevent Computer1 from automatically connecting to Wireless1.
Solution: From the Services console, you disable the Link-Layer Topology Discovery Mapper service.
Does this meet the goal?
- Yes
- No
Explanation:Link-Layer Topology Discovery is used by their Network Map feature to display a graphical representation of the local area network (LAN) or wireless LAN (WLAN), to which the computer is connected.
-
Your network contains an Active Directory domain named contoso.com. The domain contains two computers named Computer1 and Computer2 that run Windows 10.
On Computer1, you need to run the Invoke-Command cmdlet to execute several PowerShell commands on Computer2.
What should you do first?
- On Computer2, run the Enable-PSRemoting cmdlet
- From Active Directory, configure the Trusted for Delegation setting for the computer account of Computer2
- On Computer1, run the New-PSSession cmdlet
- On Computer2, add Computer1 to the Remote Management Users group
-
You have a computer named Computer1 that runs Windows 10.
You are troubleshooting connectivity issues on Computer1.
You need to view the remote addresses to which Computer1 has active TCP connections.
Which tool should you use?
- Performance Monitor
- Task Manager
- Resource Monitor
- Windows Defender Firewall with Advanced Security
-
HOTSPOT
Your office has a dedicated wireless network for guests.
You plan to provide access cards that will have a QR code for guests. The QR code will link to a network configuration file stored on a publicly accessible website and provide the wireless network settings for Windows 10 devices.
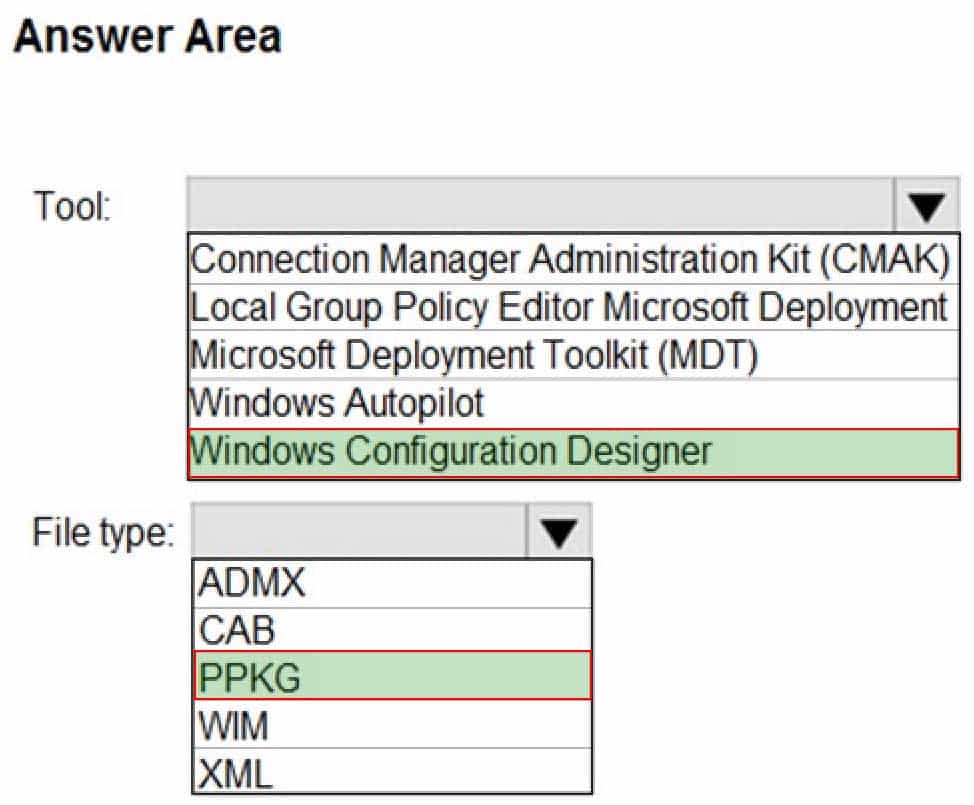
Which tool should you use to create the configuration file and which file type should you use for the configuration file? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
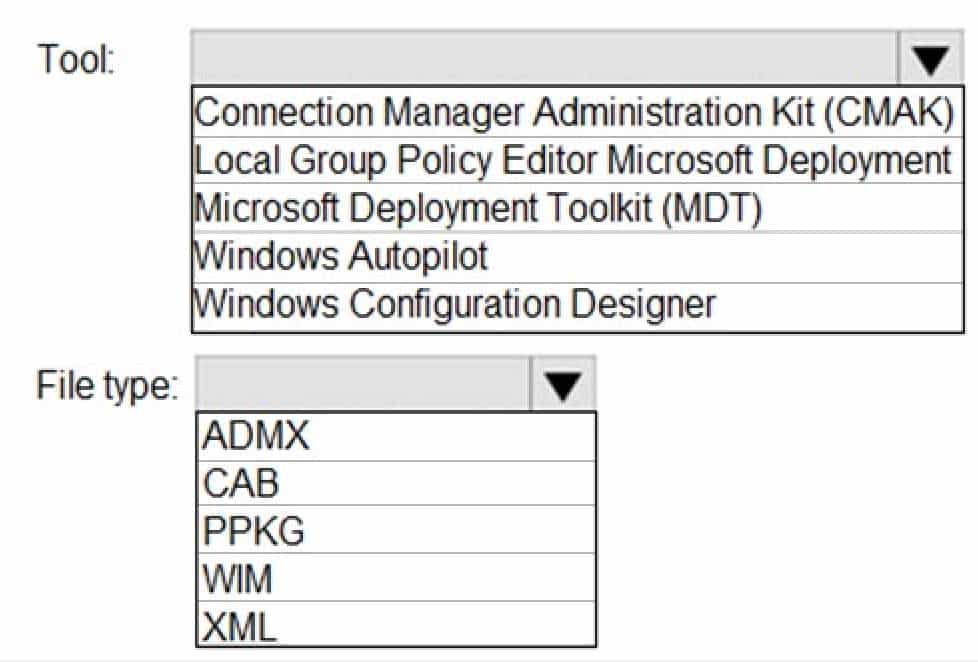
MD-100 Windows 10 Part 09 Q18 263 -
HOTSPOT
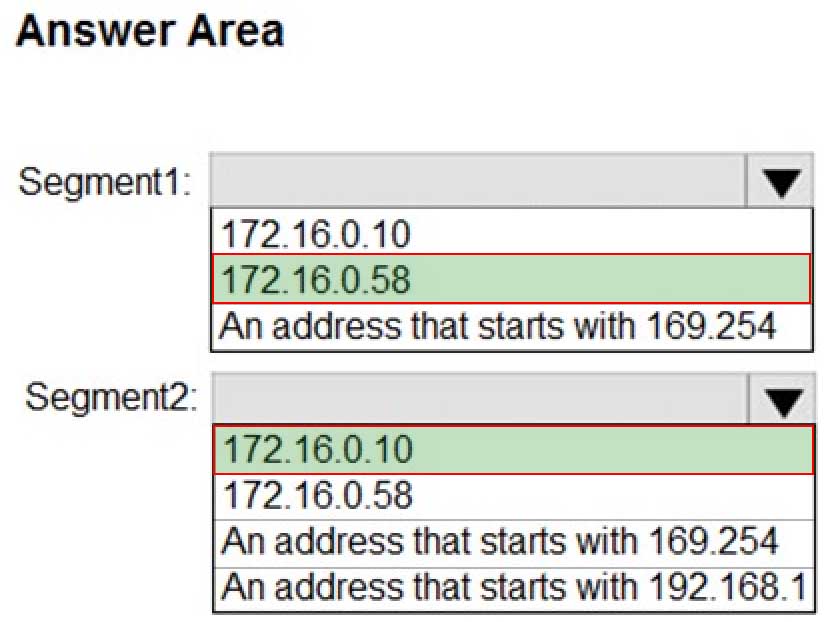
Your network contains the segments shown in the following table.

MD-100 Windows 10 Part 09 Q19 265 You have a computer that runs Windows 10.
The network interface of the computer is configured as shown in the exhibit. (Click the Exhibit tab.)

MD-100 Windows 10 Part 09 Q19 266 You need to identify which IP address the computer will have on the network when the computer connects to the segments.
Which IP address should you identify for each segment? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 09 Q19 267 -
HOTSPOT
Your network contains an Active Directory domain named adatum.com, a workgroup, and computers that run Windows 10. The computers are configured as shown in the following table.

MD-100 Windows 10 Part 09 Q20 269 The local Administrator accounts on Computer1, Computer2, and Computer3 have the same user name and password.
On Computer1, Windows Defender Firewall is configured as shown in the following exhibit.

MD-100 Windows 10 Part 09 Q20 270 The services on Computer1 have the following states.
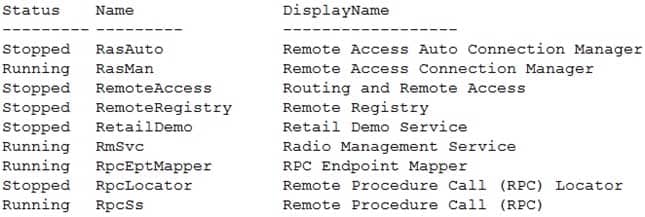
MD-100 Windows 10 Part 09 Q20 271 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 09 Q20 272 
MD-100 Windows 10 Part 09 Q20 273 Explanation:Box 1: No
Because the firewall is blocking Remote Volume Management.Box 2: No
Because the Remote Registry Service is stopped.Box 3: No
Because the Remote Registry Service is stopped. Perfmon needs both the RPC service and the Remote Registry service to be running.