MD-100 : Windows 10 : Part 11
MD-100 : Windows 10 : Part 11
-
HOTSPOT
Your network contains an Active Directory domain. The domain contains the users shown in the following table.

MD-100 Windows 10 Part 11 Q01 304 You have a server named Server1 that runs Windows Server 2019 and has the Windows Deployment Services role installed. Server1 contains an x86 boot image and three Windows 10 install images. The install images are shown in the following table.

MD-100 Windows 10 Part 11 Q01 305 You purchase a computer named Computer1 that is compatible with the 64-bit version of Windows 10.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 11 Q01 306 -
Your network contains an Active Directory domain. The domain contains 10 computers that run Windows 10. Users in the finance department use the computers.
You have a computer named Computer1 that runs Windows 10.
From Computer1, you plan to run a script that executes Windows PowerShell commands on the finance department computers.
You need to ensure that you can run the PowerShell commands on the finance department computers from Computer1.
What should you do on the finance department computers?
- From the local Group Policy, enable the Allow Remote Shell Access setting.
- From the local Group Policy, enable the Turn on Script Execution setting.
- From the Windows PowerShell, run the
Enable-MMAgent cmdlet. - From the Windows PowerShell, run the
Enable-PSRemoting cmdlet.
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
General Overview
Litware, Inc. is a consulting company that has a main office in Montreal and branch offices in Seattle and New York.
Environment
Existing Environment
The network contains an on-premises Active Directory domain named litware.com. The domain contains the computers shown in the following table.

MD-100 Windows 10 Part 11 Q03 308 The network that uses 192.168.10.0/24 connects to the internet by using a Network Address Translation (NAT) device.
Windows Admin Center is installed on Server1.
The domain contains the groups shown in the following table.

MD-100 Windows 10 Part 11 Q03 309 The domain contains the users shown in the following table.

MD-100 Windows 10 Part 11 Q03 310 Computer1 Configuration
Computer1 contains the local user accounts shown in the following table.
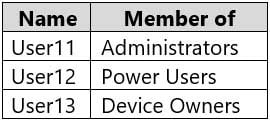
MD-100 Windows 10 Part 11 Q03 311 Computer1 contains a folder named D:\Folder1 that has permission inheritance disabled.
Computer1 contains a file named D:\Folder1\Report.docx that has the permissions shown in the following table.

MD-100 Windows 10 Part 11 Q03 312 D:\Folder1\Report.docx has auditing configured as shown in the following table.

MD-100 Windows 10 Part 11 Q03 313 The Local Computer Policy for Computer1 is configured as shown in the following table.

MD-100 Windows 10 Part 11 Q03 314 Windows Defender Firewall for Computer1 has the rules shown in the following table.

MD-100 Windows 10 Part 11 Q03 315 Computer2 Configuration
Computer2 contains the local user accounts shown in the following table.
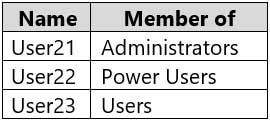
MD-100 Windows 10 Part 11 Q03 316 Group1 and Group2 are members of the Remote Desktop Users group.
The Local Computer Policy for Computer2 is configured as shown in the following table.

MD-100 Windows 10 Part 11 Q03 317 Windows Defender Firewall for Computer2 has the rules shown in the following table.

MD-100 Windows 10 Part 11 Q03 317 Computer3 Configuration
Computer3 contains the local user accounts shown in the following table.

MD-100 Windows 10 Part 11 Q03 318 Windows Defender Firewall for Computer3 has the rules shown in the following table.

MD-100 Windows 10 Part 11 Q03 319 Requirements and Planned Changes
Planned Changes
Litware plans to make the following changes on Computer1:
-Grant User1 Allow Full control permissions to D:\Folder1\Report.docx.
-Grant User2 Allow Full control permissions to D:\Folder1\Report.docx.
-Grant User3 Allow Full control permissions to D:\Folder1.Technical Requirements
Litware identifies the following technical requirements:
-Configure custom Visual Effect performance settings for Computer1.
-Manage Computer2 by using Windows Admin Center.
-Minimize administrative effort.Delivery Optimization on the computers that run Windows 10 must be configured to meet the following requirements:
-Content must be downloaded only from an original source.
-Downloading content from peer cache clients must be prevented.
-Downloads must be optimized by using the Delivery Optimization cloud service.-
Which users can sign in to Computer3 when the computer starts in Safe Mode?
- User31 only
- User31 and User32 only
- User31 and Admin1 only
- User31, User 32, User33, and Admin1
- User31, User32, and User33 only
Explanation:Only users with membership of the local Administrators group can log on to a computer in safe mode. Admin1 cannot log in because Computer3 is not joined to the domain.
-
You need to ensure that you can manage Computer2 by using Windows Admin Center on Server1.
What should you do on Computer2?
- Install the Remote Server Administration Tool (RSAT) optional features.
- Run the winrm quickconfig command.
- Set the Windows Management Service Startup type to Automatic and start the service.
- Run the Set-Location cmdlet.
-
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam times as you would like to complete each case. However, there may be additional studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
Fabrikam, Inc. is a distribution company that has 500 employees and 100 contractors.
Existing Environment
Active Directory
The network contains an Active Directory forest named fabrikam.com. The forest is synced to Microsoft Azure Active Directory (Azure AD). All the employees are assigned Microsoft 365 E3 licenses.
The domain contains a user account for an employee named User10.
Client Computers
All the employees have computers that run Windows 10 Enterprise. All the computers are installed without Volume License Keys. Windows 10 license keys are never issued.
All the employees register their computer to Azure AD when they first receive the computer.
User10 has a computer named Computer10.
All the contractors have their own computer that runs Windows 10. None of the computers are joined to Azure AD.
Operational Procedures
Fabrikam has the following operational procedures:
*Updates are deployed by using Windows Update for Business.
*When new contractors are hired, administrators must help the contactors configure the following settings on their computer:
– User certificates
– Browser security and proxy settings
– Wireless network connection settingsSecurity Policies
The following security policies are enforced on all the client computers in the domain:
-All the computers are encrypted by using BitLocker Drive Encryption (BitLocker). BitLocker recovery information is stored in Active Directory and Azure AD.
-The local Administrators group on each computer contains an enabled account named LocalAdmin.
-The LocalAdmin account is managed by using Local Administrator Password Solution (LAPS).Problem Statements
Fabrikam identifies the following issues:
-Employees in the finance department use an application named Application1. Application1 frequently crashes due to a memory error. When Application1 crashes, an event is written to the application log and an administrator runs a script to delete the temporary files and restart the application.
-When employees attempt to connect to the network from their home computer, they often cannot establish a VPN connection because of misconfigured VPN settings.
-An employee has a computer named Computer11. Computer11 has a hardware failure that prevents the computer from connecting to the network.
-User10 reports that Computer10 is not activated.Technical Requirements
Fabrikam identifies the following technical requirements for managing the client computers:
Provide employees with a configuration file to configure their VPN connection.
-Use the minimum amount of administrative effort to implement the technical requirements.
-Identify which employees’ computers are noncompliant with the Windows Update baseline of the company.
-Ensure that the service desk uses Quick Assist to take remote control of an employee’s desktop during support calls.
-Automate the configuration of the contractors’ computers. The solution must provide a configuration file that the contractors can open from a Microsoft SharePoint site to apply the required configurations.-
You need to recommend a solution to monitor update deployments.
What should you include in the recommendation?
- Windows Server Update Services (WSUS)
- the Update Management solution in Azure Automation
- the Update Compliance solution in Azure Log Analytics
- the Azure Security Center
-
HOTSPOT
You need to reduce the amount of time it takes to restart Application1 when the application crashes.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 11 Q04 318
-
-
Case Study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
Contoso has IT, human resources (HR), and finance departments.
Contoso recently opened a new branch office in San Diego. All the users in the San Diego office work from home.
Existing environment
Contoso uses Microsoft 365.
The on-premises network contains an Active Directory domain named contoso.com. The domain is synced to Microsoft Azure Active Directory (Azure AD).
All computers run Windows 10 Enterprise.
You have four computers named Computer1, Computer2, Computer3, and ComputerA. ComputerA is in a workgroup on an isolated network segment and runs the Long Term Servicing Channel version of Windows 10. ComputerA connects to a manufacturing system and is business critical. All the other computers are joined to the domain and run the Semi-Annual Channel version of Windows 10.
In the domain, you create four groups named Group1, Group2, Group3, and Group4.
Computer2 has the local Group Policy settings shown in the following table.

MD-100 Windows 10 Part 11 Q05 320 The computers are updated by using Windows Update for Business.
The domain has the users shown in the following table.

MD-100 Windows 10 Part 11 Q05 321 Computer1 has the local users shown in the following table.
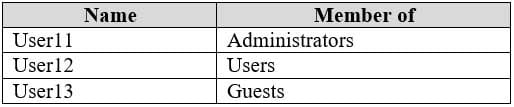
MD-100 Windows 10 Part 11 Q05 322 Requirements
Planned Changes
Contoso plans to purchase computers preinstalled with Windows 10 Pro for all the San Diego office users.
Technical requirements
Contoso identifies the following technical requirements:
-The computers in the San Diego office must be upgraded automatically to Windows 10 Enterprise and must be joined to Azure AD the first time a user starts each new computer. End users must not be required to accept the End User License Agreement (EULA).
-Helpdesk users must be able to troubleshoot Group Policy object (GPO) processing on the Windows 10 computers. The helpdesk users must be able to identify which Group Policies are applied to the computers.
-Users in the HR department must be able to view the list of files in a folder named D:\Reports on Computer3.
-ComputerA must be configured to have an Encrypting File System (EFS) recovery agent.
-Quality update installations must be deferred as long as possible on ComputerA.
-Users in the IT department must use dynamic lock on their primary device.
-User6 must be able to connect to Computer2 by using Remote Desktop.
-The principle of least privilege must be used whenever possible.
-Administrative effort must be minimized whenever possible.
-Kiosk (assigned access) must be configured on Computer1.-
You need to meet the quality update requirement for ComputerA.
For how long should you defer the updates?
- 14 days
- 10 years
- 5 years
- 180 days
- 30 days
Explanation:The LTSC servicing model prevents Windows 10 Enterprise LTSB devices from receiving the usual feature updates and provides only quality updates to ensure that device security stays up to date. It typically offers new LTSC releases every 2–3 years, and organizations can choose to install them as in-place upgrades or even skip releases over a 10-year life cycle.
-
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have two computers named Computer1 and Computer2 that run Windows 10.
You have an Azure Active Directory (Azure AD) user account named admin@contoso.com that is in the local Administrators group on each computer.
You sign in to Computer1 by using admin@contoso.com.
You need to ensure that you can use Event Viewer on Computer1 to connect to the event logs on Computer2.
Solution: On Computer2, you run the winrm quickconfig command.
Does this meet the goal?
- Yes
- No
Explanation:Windows Remote Management is a component of the Windows Hardware Management features that manage server hardware locally and remotely.
-
You deploy Windows 10 to several computers. The computers will be used by users who frequently present their desktop to other users.
You need to prevent applications from generating toast notifications in the notification area.
Which settings should you configure from the Settings app?
- Shared experiences
- Privacy
- Focus assist
- Tablet mode
Explanation:Focus Assist will automatically hide incoming notifications, so they don’t pop up and distract you while you’re playing a game, giving a presentation, or using a full-screen application.
Incorrect Answers:
A: Shared Experiences allow you to start a task on one device and finish it on another device.D: Tablet mode makes Windows 10 more touch-friendly when using your device as a tablet.
-
HOTSPOT
Your network contains an Active Directory domain named adatum.com. The domain contains two computers named Computer1 and Computer2 that run Windows 10.
The domain contains the user accounts shown in the following table.

MD-100 Windows 10 Part 11 Q08 323 Computer2 contains the local groups shown in the following table.

MD-100 Windows 10 Part 11 Q08 324 The relevant user rights assignments for Computer2 are shown in the following table.

MD-100 Windows 10 Part 11 Q08 325 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 11 Q08 326 
MD-100 Windows 10 Part 11 Q08 327 Explanation:Box 1: Yes
User1 is an administrator and has the Allow log on through Remote Desktop Services.Box 2: No
User2 is a member of Group2 which has the Deny log on through Remote Desktop Services.Box 3: Yes
User3 is a member of the administrators group and has the Allow log on through Remote Desktop Services.Note: Deny permissions take precedence over Allow permissions. If a user belongs to two groups, and one of them has a specific permission set to Deny, that user is not able to perform tasks that require that permission even if they belong to a group that has that permission set to Allow.
-
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password

MD-100 Windows 10 Part 11 Q09 328 Use the following login credentials as needed:
To enter your password, place your cursor in the Enter password box and click on the password below.
Username: Contoso/Administrator
Password: Passw0rd!The following information is for technical support purposes only:
Lab Instance: 10921597
MD-100 Windows 10 Part 11 Q09 329 You need to ensure that Client3 starts in safe mode automatically the next time the computer restarts. After completing the task, you must NOT restart Client3.
To complete this task, sign in to the required computer or computers.
- See explanation below.
Explanation:
1. From Client3, open the System Configuration utility by pressing the Windows & R keys simultaneously to display the Run box .
2. Type “msconfig” into the box, and then click OK.
MD-100 Windows 10 Part 11 Q09 330 3. In the “System Configuration” window, switch to the “Boot” tab.
4. Enable the “Safe Boot” check box, and then make sure the “Minimal” option below that is selected. Click the “OK” button when you’re done.
MD-100 Windows 10 Part 11 Q09 332 5. You will be prompted to Restart or Exit without restart. Click Exit without restart.

MD-100 Windows 10 Part 11 Q09 331
- See explanation below.
-
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password

MD-100 Windows 10 Part 11 Q10 333 Use the following login credentials as needed:
To enter your password, place your cursor in the Enter password box and click on the password below.
Username: Contoso/Administrator
Password: Passw0rd!The following information is for technical support purposes only:
Lab Instance: 10921597
MD-100 Windows 10 Part 11 Q10 334 You need to create a user account named User5 on Client2. The solution must meet the following requirements:
Prevent User5 from changing the password of the account.
Ensure that User5 can perform backups.
Use the principle of least privilege.To complete this task, sign in to the required computer or computers.
- See explanation below.
Explanation:1.On Client2, press the Win + X keys on your keyboard. Then, click or tap the Computer Management option from the menu.
2.Expand the Local Users and Groups from the left side of the window, and select Users.
3.Right-click somewhere on the blank space found in the middle section of the window, and click or tap on New User. This opens the New User window, where you can enter all the details about the new user account.
4.Type the user name and, optionally, its full name and description.
5.Type the password to be used for that user and confirm it.
6.Select the User cannot change password check box.
7.Click Create and Windows immediately creates the user account. When you are done creating user accounts, click Close in the New User window.1.Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy.
2.Expand open Local Policies in the left pane of Local Security Policy, click/tap on User Rights Assignment, and double click/tap on the Back up files and directories policy in the right pane.
3.Click/tap on the Add User or Group button.
4.Click/tap on the Object Types button.
5.Check all the boxes for Object types, and click/tap on the OK.
6.Click/tap on the Advanced button.
7.Click/tap on the Find Now button, select the name of the user or group
8.Click/tap on OK.
9.Click/tap on OK.
10.When finished, you can close Local Users and Groups. -
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password

MD-100 Windows 10 Part 11 Q11 335 Use the following login credentials as needed:
To enter your password, place your cursor in the Enter password box and click on the password below.
Username: Contoso/Administrator
Password: Passw0rd!The following information is for technical support purposes only:
Lab Instance: 10921597
MD-100 Windows 10 Part 11 Q11 336 You need to create a group named Group2 on Client2. The members of Group2 must be able to change the system time. The solution must use the principle of least privilege.
To complete this task, sign in to the required computer or computers.
- See explanation below.
Explanation:1.On Client2, Press Windows+R
2.Type lusrmgr.msc
3.Right click Groups and click New Group.
4.Type in the Group name and a description.
5.Click Add to add members to this group. Specify the name of the user or group or computer to be added.
5.Click Create and Close.1.Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy.
2.Expand open Local Policies in the left pane of Local Security Policy, click/tap on User Rights Assignment, and double click/tap on the Change the system time policy in the right pane.
3.Click/tap on the Add User or Group button.
4.Click/tap on the Object Types button.
5.Check all the boxes for Object types, and click/tap on the OK.
6.Click/tap on the Advanced button.
7.Click/tap on the Find Now button, select the name of the user or group
8.Click/tap on OK.
9.Click/tap on OK.
10.When finished, you can close Local Users and Groups. -
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password

MD-100 Windows 10 Part 11 Q12 337 Use the following login credentials as needed:
To enter your password, place your cursor in the Enter password box and click on the password below.
Username: Contoso/Administrator
Password: Passw0rd!The following information is for technical support purposes only:
Lab Instance: 11145882
MD-100 Windows 10 Part 11 Q12 338 
MD-100 Windows 10 Part 11 Q12 339 Users who attempt to sign in to the domain from Client3 report that the sign-ins fail.
You need to resolve the issue.
To complete this task, sign in to the required computer or computers.
- See explanation below.
Explanation:1.Use a local administrator account to log on to the computer.
2.Select Start, press and hold (or right-click) Computer > Properties.
3.Select Change settings next to the computer name.
4.On the Computer Name tab, select Change.
5.Under the Member of heading, select Workgroup, type a workgroup name, and then select OK.
6.When you are prompted to restart the computer, select OK.
7.On the Computer Name tab, select Change again.
8.Under the Member of heading, select Domain, and then type the domain name.
9.Select OK, and then type the credentials of the user who has permissions in the domain.
10.When you are prompted to restart the computer, select OK.
11.Restart the computer. -
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password

MD-100 Windows 10 Part 11 Q13 340 Use the following login credentials as needed:
To enter your password, place your cursor in the Enter password box and click on the password below.
Username: Contoso/Administrator
Password: Passw0rd!The following information is for technical support purposes only:
Lab Instance: 11145882
MD-100 Windows 10 Part 11 Q13 341 
MD-100 Windows 10 Part 11 Q13 342 You need to ensure that Windows feature updates on Client1 are deferred for 15 days when the updates become generally available.
To complete this task, sign in to the required computer or computers.
- See explanation below.
Explanation:1.Select the Start button, then select Settings > Update & Security > Windows Update.
2.Under Update settings, select Advanced options.
3.From the boxes under Choose when updates are installed, select the number of days you would like to defer a feature update or a quality update. -
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have two computers named Computer1 and Computer2 that run Windows 10.
You have an Azure Active Directory (Azure AD) user account named admin@contoso.com that is in the local Administrators group on each computer.
You sign in to Computer1 by using admin@contoso.com.
You need to ensure that you can use Event Viewer on Computer1 to connect to the event logs on Computer2.
Solution: On Computer2, you enable the Remote Event Log Management inbound rule from Windows Defender Firewall.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have two computers named Computer1 and Computer2 that run Windows 10.
You have an Azure Active Directory (Azure AD) user account named admin@contoso.com that is in the local Administrators group on each computer.
You sign in to Computer1 by using admin@contoso.com.
You need to ensure that you can use Event Viewer on Computer1 to connect to the event logs on Computer2.
Solution: On Computer2, you create a Windows Defender Firewall rule that allows eventwr.exe.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows 10.
You test Windows updates on Computer1 before you make the updates available to other computers.
You install a quality update that conflicts with a custom device driver.
You need to remove the update from Computer1.
Solution: From an elevated command prompt, you run the wusa.exe command and specify the /uninstall parameter.
Does this meet the goal?
- Yes
- No
-
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer named Computer1 that runs Windows 10.
You test Windows updates on Computer1 before you make the updates available to other computers.
You install a quality update that conflicts with a custom device driver.
You need to remove the update from Computer1.
Solution: From System Restore, you revert the system state to a restore point that was created before the update was installed.
Does this meet the goal?
- Yes
- No
-
You have 100 computers that run Windows 10. The computers belong to a workgroup.
The computers have a low-bandwidth metered Internet connection.
You need to reduce the amount of Internet bandwidth consumed to download updates.
What should you configure?
- BranchCache in hosted mode
- BranchCache in distributed cache mode
- Delivery Optimization
- Background Intelligent Transfer Service (BITS)
-
You have 20 computers that run Windows 10.
You configure all the computers to forward all the events from all the logs to a computer named Computer1 that runs Windows 10.
When you sign in to Computer1, you cannot see any security events from other computers. You can see all the other forwarded events from the other computers.
You need to ensure that the security events are forwarded to Computer1.
What should you do?
- On each computer,
run wecutil qc /q. - On each computer, add the NETWORK SERVICE account to the Event Log Readers group.
- On each computer,
run winrm qc –q. - On Computer1, add the account of Computer1 to the Event Log Readers group.
- On each computer,
-
HOTSPOT
You have a computer named Computer1 that runs Windows 10 and contains the following files:
-C:\Folder1\File1.bat
-C:\Folder1\File1.exe
-C:\Folder1\File1.cmdA user named User1 is assigned Read & execute to all the files.
Computer1 is configured as shown in the exhibit.

MD-100 Windows 10 Part 11 Q20 343 Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

MD-100 Windows 10 Part 11 Q20 345 
MD-100 Windows 10 Part 11 Q20 344 Explanation:The command prompt will open in the user profile folder. In the exhibit, USERPROFILE is C:\Users\User1.
PathExt is an Environment Variable that stores a list of the file extensions for operation system to execute. When running a command line that does not contain an extension, the system uses the value of this environment variable to determine which extensions to look for and in what order, such as .com first, follow by .exe, .bat, .cmd, which happens to be the default value stored in the PathExt by Windows.
In the exhibit, PATHEXT shows that .exe comes before .bat and .cmd. Therefore, File1.exe will run.

