FC0-U61 : CompTIA IT Fundamentals : Part 07
FC0-U61 : CompTIA IT Fundamentals : Part 07
-
Which of the following BEST describes a technology that allows multiple users to create and edit reports at the same time?
- Text file on a shared drive
- Managed relational database
- Informational intranet page
- Locally installed productivity software
-
A company has installed an application that only requires a workstation to function. Which of the following architecture types is this application using?
- One-tier
- Two-tier
- Three-tier
- n-tier
-
A global variable called “age” will be created in a program and incremented through the use of a function. Which of the following data types should be defined with the age variable?
- Integer
- Float
- Double
- String
-
Meaningful and accurate reporting is essential to retailers in making business decisions while managing inventory. Which of the following offers the BEST assistance in generating reports?
- Data capture and collections
- Asset inventory inputs
- Sales statistics
- Average loss output
-
A business would like to create an employee portal that employees will have access to when they are at work. The employees will not be able to connect to the portal from home without a VPN connection. Which of the following types of application does this describe?
- Local application
- Intranet application
- Extranet application
- Internet application
-
A computer technician is assigned a ticket to install a laptop for a new employee. Due to the arrangement of the workspace, the employee requests that the laptop be installed with the cover closed. Which of the following would be required to satisfy this request? (Choose two.)
- Printer
- Mouse
- Webcam
- External hard drive
- Speakers
- Display
-
A company wants its employee to use an email client that downloads and removes messages from the email server. Which of the following protocols must be configured in the email client to facilitate this?
- POP3
- IMAP
- ICMP
- SMTP
-
Consider the following statements:

FC0-U61 Part 07 Q08 003 Given the input (userin) of “analyst”, to which of the following would the clearance variable be set?
- topsecret
- normal
- analyst
- restricted
-
Which of the following is a reason why complex passwords are required?
- To encourage password variety
- To prevent someone from guessing them
- To make them harder to remember
- To reduce social engineering attacks
-
A technician is troubleshooting an error message and tests the same program on a separate, identical machine. Which of the following troubleshooting methodology steps is this an example of?
- Duplicate the problem
- Gather information
- Question users
- Divide and conquer
-
Which of the following storage types is MOST vulnerable to magnetic damage?
- Flash
- SSD
- Optical
- HDD
-
When developing a game, a developer creates a boss object that has the ability to jump. Which of the following programming concepts does jump represent?
- Method
- Object
- Property
- Attribute
-
Concerned with vulnerabilities on a home network, an administrator replaces the wireless router with a recently released new device. After configuring the new device utilizing the old SSID and key, some light switches are no longer communicating. Which of the following is the MOST likely cause?
- The light switches do not support WPA2.
- The router is operating on a different channel.
- The key does not meet password complexity requirements.
- The SSID is not being broadcast.
-
Given the following pseudocode:
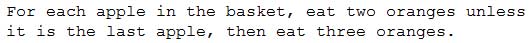
FC0-U61 Part 07 Q14 004 If there are seven apples in the basket, which of the following would be the number of oranges a person eats?
- 10
- 14
- 15
- 17
-
Which of the following are the primary functions of an operating system? (Choose two.)
- Provide structure for file and data management.
- Provide protection against malware and viruses.
- Provide peer-to-peer networking capability.
- Provide user data encryption.
- Provide virtual desktop capability.
- Provide system resources.
-
SQL databases use primary and foreign keys to enable which of the following?
- Rows
- Fields
- Schemas
- Relationships
-
Which of the following is a logical structure for storing files?
- Folder
- Extension
- Permissions
- Shortcut
-
Which of the following is both an input and output device?
- Microphone
- Speaker
- Touch-screen monitor
- Keyboard
-
A technician has successfully verified full system functionality after implementing the solution to a problem. Which of the following is the NEXT troubleshooting step the technician should do?
- Determine if anything has changed.
- Document lessons learned.
- Establish a theory of probable cause.
- Duplicate the problem, if possible.
-
A large payment website was breached recently. A user is concerned that the breach will affect account security on other sites. Which of the following password best practices would mitigate this risk?
- Password history
- Password reuse
- Password expiration
- Password age
-
A company is concerned with ensuring its databases are highly available. Which of the following can be used to increase database availability?
- Backups
- Prioritization
- Indexes
- Failover
-
A user revisits a website and receives a message that the site may not be secure. The user is prompted to click a link to continue to the site. Which of the following would MOST likely identify the issue?
- Checking the proxy settings
- Checking that caching is enabled
- Checking browser add-ons
- Checking certificate validity
-
A user wants to ensure port 3389 is open for remote desktop on a PC. Which of the following describes where the user should verify the port is open?
- Antivirus
- Anti-malware
- Device Manager
- Host firewall
-
Which of the following contains exactly four copper wires?
- RJ45
- VGA
- RJ11
- USB
-
A technician replaces the video card in a user’s PC. The user reports the resolution on the display seems very low, but the operating system will not let the user adjust it any higher. Which of the following steps would MOST likely fix this problem?
- Replace the user’s display.
- Update the PC’s operating system.
- Replace the video cable.
- Install new video drivers.
-
All users have access to an application at a company. The data from the application is stored on a centralized device located on the network. Which of the following devices would MOST likely be used to store the data?
- Server
- Tape library
- External HDD
- Workstation