SY0-601 : CompTIA Security+ 2021 : Part 01
SY0-601 : CompTIA Security+ 2021 : Part 01
-
SIMULATION
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
Deny cleartext web traffic.
Ensure secure management protocols are used.
Resolve issues at the DR site.The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
SY0-601 Part 01 Q01 001 
SY0-601 Part 01 Q01 002 
SY0-601 Part 01 Q01 003 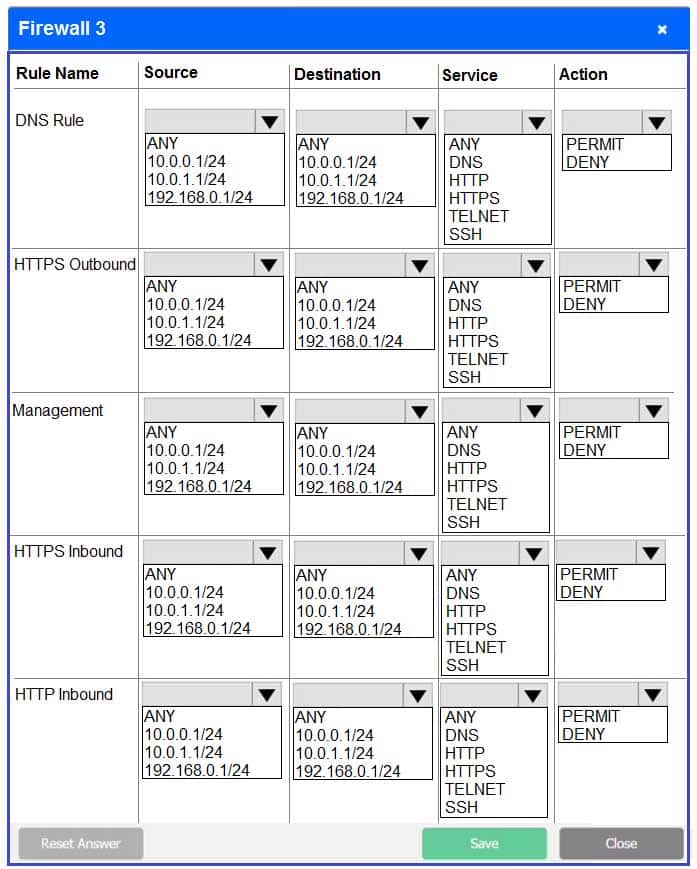
SY0-601 Part 01 Q01 004 - See explanation below.
Explanation:
Firewall 1:DNS Rule – ANY –> ANY –> DNS –> PERMIT
HTTPS Outbound – 10.0.0.1/24 –> ANY –> HTTPS –> PERMIT
Management – ANY –> ANY –> SSH –> PERMIT
HTTPS Inbound – ANY –> ANY –> HTTPS –> PERMIT
HTTP Inbound – ANY –> ANY –> HTTP –> DENYFirewall 2: No changes should be made to this firewall
Firewall 3:
DNS Rule – ANY –> ANY –> DNS –> PERMIT
HTTPS Outbound – 192.168.0.1/24 –> ANY –> HTTPS –> PERMIT
Management – ANY –> ANY –> SSH –> PERMIT
HTTPS Inbound – ANY –> ANY –> HTTPS –> PERMIT
HTTP Inbound – ANY –> ANY –> HTTP –> DENY -
DRAG DROP
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
SY0-601 Part 01 Q02 005 Question 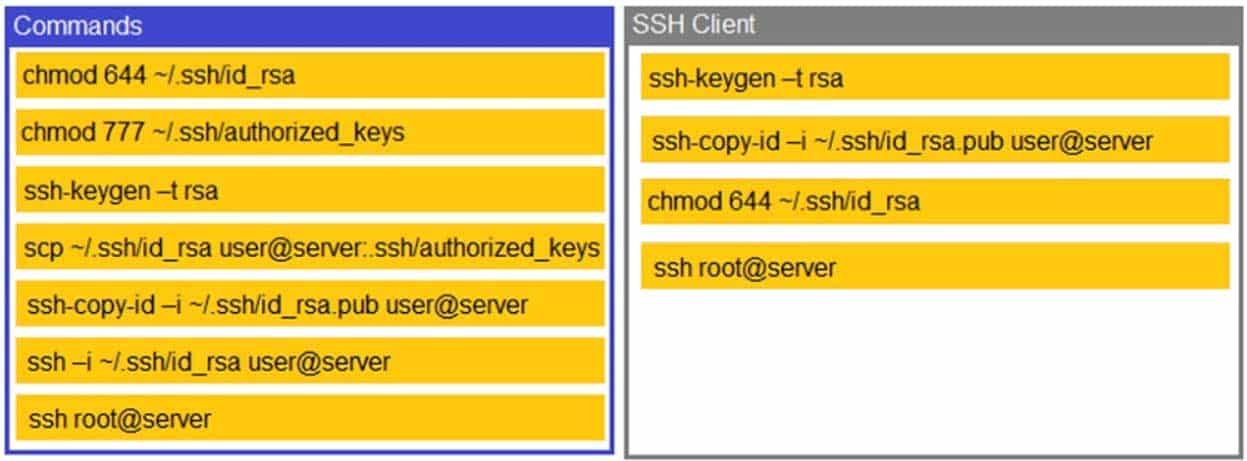
SY0-601 Part 01 Q02 005 Answer -
HOTSPOT
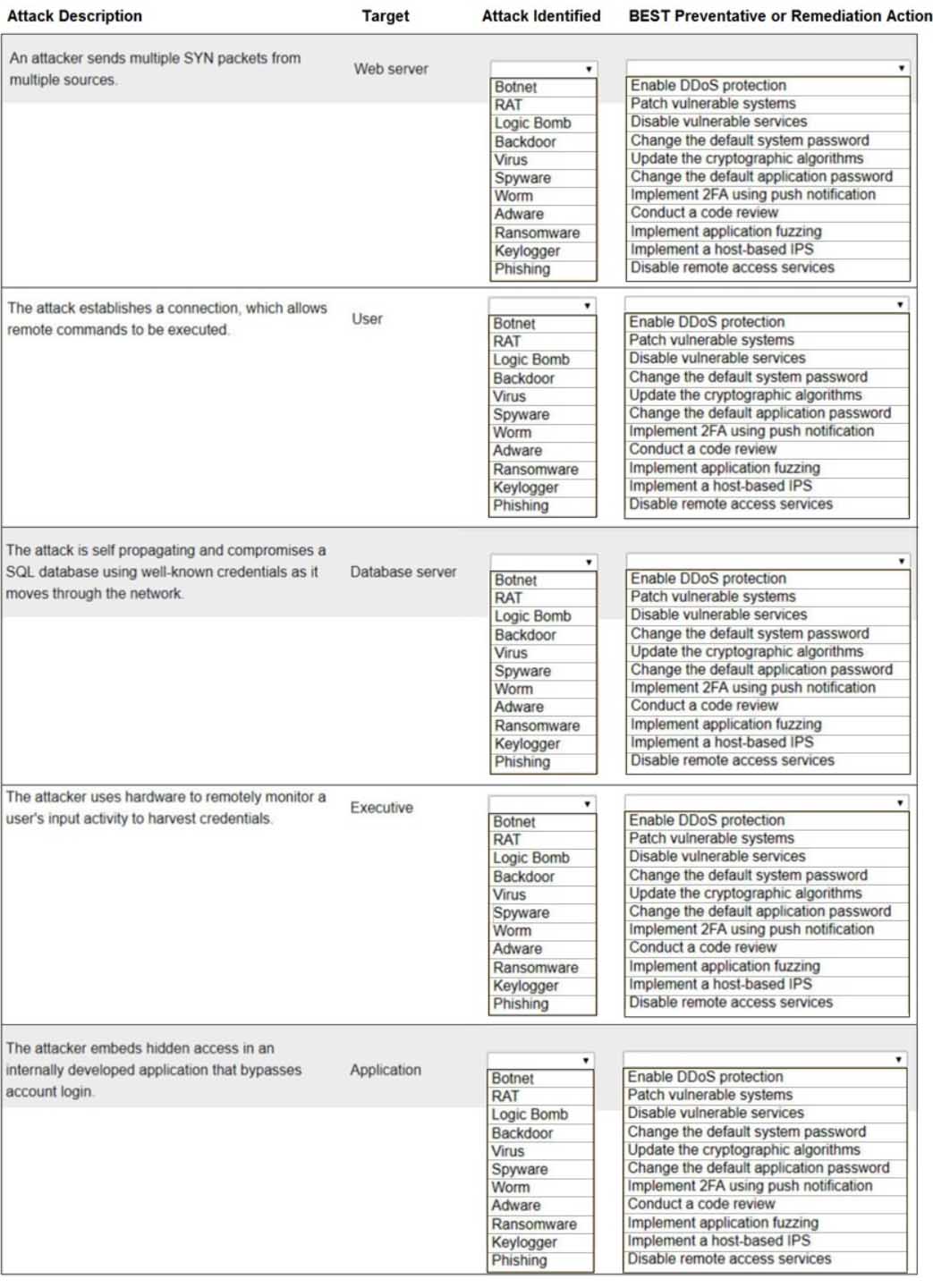
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
SY0-601 Part 01 Q03 006 Question 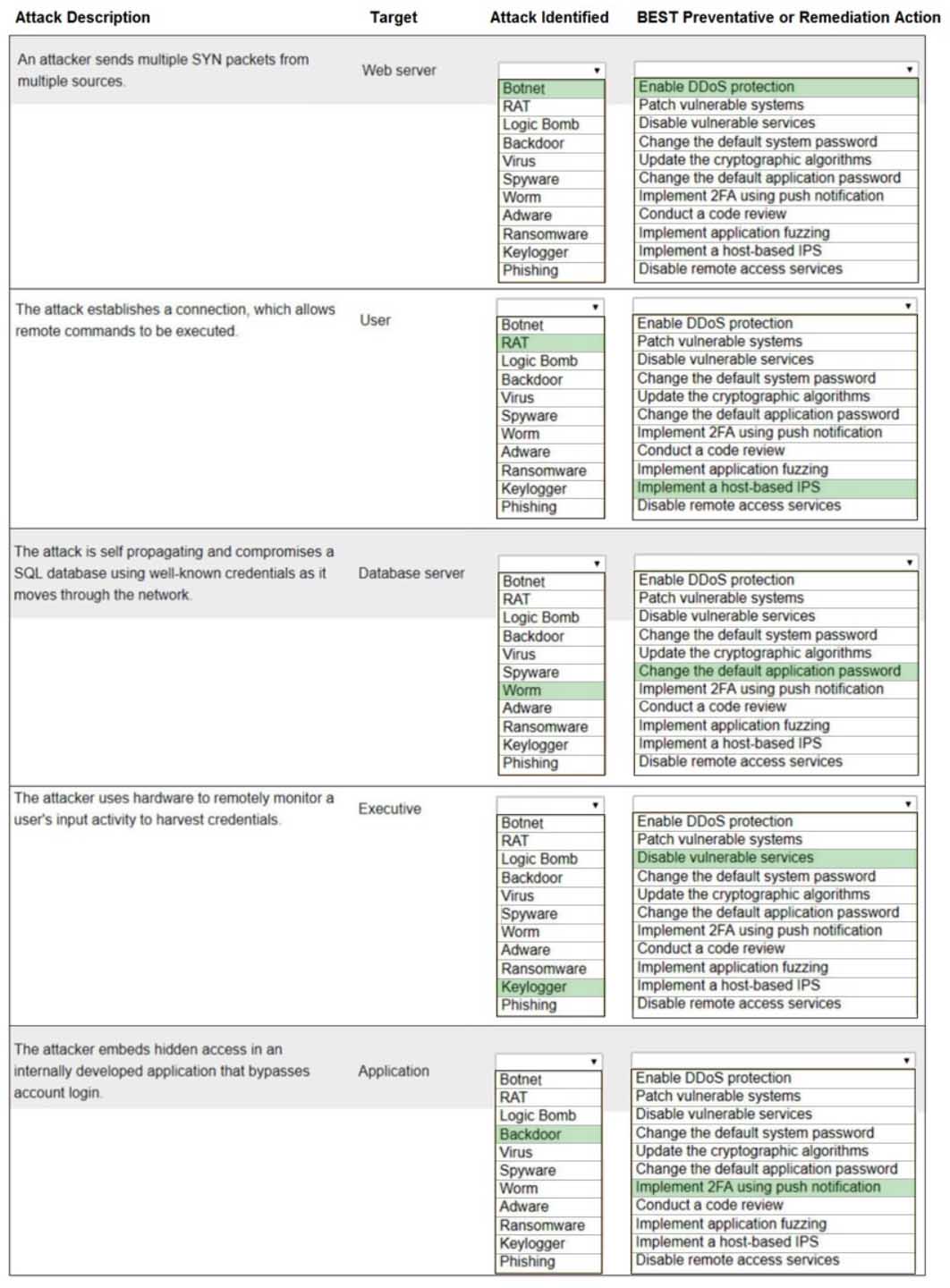
SY0-601 Part 01 Q03 006 Answer -
Which of the following will MOST likely adversely impact the operations of unpatched traditional programmable-logic controllers, running a back-end LAMP server and OT systems with human-management interfaces that are accessible over the Internet via a web interface? (Choose two.)
- Cross-site scripting
- Data exfiltration
- Poor system logging
- Weak encryption
- SQL injection
- Server-side request forgery
-
A company recently transitioned to a strictly BYOD culture due to the cost of replacing lost or damaged corporate-owned mobile devices. Which of the following technologies would be BEST to balance the BYOD culture while also protecting the company’s data?
- Containerization
- Geofencing
- Full-disk encryption
- Remote wipe
-
A Chief Security Office’s (CSO’s) key priorities are to improve preparation, response, and recovery practices to minimize system downtime and enhance organizational resilience to ransomware attacks. Which of the following would BEST meet the CSO’s objectives?
- Use email-filtering software and centralized account management, patch high-risk systems, and restrict administration privileges on fileshares.
- Purchase cyber insurance from a reputable provider to reduce expenses during an incident.
- Invest in end-user awareness training to change the long-term culture and behavior of staff and executives, reducing the organization’s susceptibility to phishing attacks.
- Implement application whitelisting and centralized event-log management, and perform regular testing and validation of full backups.
-
A network engineer has been asked to investigate why several wireless barcode scanners and wireless computers in a warehouse have intermittent connectivity to the shipping server. The barcode scanners and computers are all on forklift trucks and move around the warehouse during their regular use. Which of the following should the engineer do to determine the issue? (Choose two.)
- Perform a site survey
- Deploy an FTK Imager
- Create a heat map
- Scan for rogue access points
- Upgrade the security protocols
- Install a captive portal
-
A security administrator suspects an employee has been emailing proprietary information to a competitor. Company policy requires the administrator to capture an exact copy of the employee’s hard disk. Which of the following should the administrator use?
-
dd -
chmod
-
dnsenum
-
logger
-
-
Which of the following is MOST likely to outline the roles and responsibilities of data controllers and data processors?
- SSAE SOC 2
- PCI DSS
- GDPR
- ISO 31000
-
Phishing and spear-phishing attacks have been occurring more frequently against a company’s staff. Which of the following would MOST likely help mitigate this issue?
- DNSSEC and DMARC
- DNS query logging
- Exact mail exchanger records in the DNS
- The addition of DNS conditional forwarders
-
On which of the following is the live acquisition of data for forensic analysis MOST dependent? (Choose two.)
- Data accessibility
- Legal hold
- Cryptographic or hash algorithm
- Data retention legislation
- Value and volatility of data
- Right-to-audit clauses
-
Which of the following incident response steps involves actions to protect critical systems while maintaining business operations?
- Investigation
- Containment
- Recovery
- Lessons learned
-
A security auditor is reviewing vulnerability scan data provided by an internal security team. Which of the following BEST indicates that valid credentials were used?
- The scan results show open ports, protocols, and services exposed on the target host
- The scan enumerated software versions of installed programs
- The scan produced a list of vulnerabilities on the target host
- The scan identified expired SSL certificates
-
Which of the following BEST explains the difference between a data owner and a data custodian?
- The data owner is responsible for adhering to the rules for using the data, while the data custodian is responsible for determining the corporate governance regarding the data
- The data owner is responsible for determining how the data may be used, while the data custodian is responsible for implementing the protection to the data
- The data owner is responsible for controlling the data, while the data custodian is responsible for maintaining the chain of custody when handling the data
- The data owner grants the technical permissions for data access, while the data custodian maintains the database access controls to the data
-
A network engineer needs to build a solution that will allow guests at the company’s headquarters to access the Internet via WiFi. This solution should not allow access to the internal corporate network, but it should require guests to sign off on the acceptable use policy before accessing the Internet. Which of the following should the engineer employ to meet these requirements?
- Implement open PSK on the APs
- Deploy a WAF
- Configure WIPS on the APs
- Install a captive portal
-
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events:
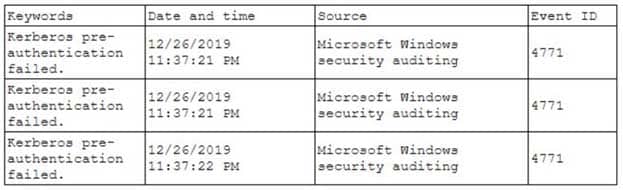
SY0-601 Part 01 Q16 007 To better understand what is going on, the analyst runs a command and receives the following output:
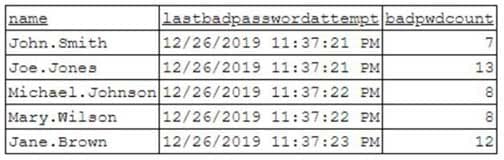
SY0-601 Part 01 Q16 008 Based on the analyst’s findings, which of the following attacks is being executed?
- Credential harvesting
- Keylogger
- Brute-force
- Spraying
-
Which of the following cloud models provides clients with servers, storage, and networks but nothing else?
- SaaS
- PaaS
- IaaS
- DaaS
-
A network administrator needs to build out a new datacenter, with a focus on resiliency and uptime. Which of the following would BEST meet this objective? (Choose two.)
- Dual power supply
- Off-site backups
- Automatic OS upgrades
- NIC teaming
- Scheduled penetration testing
- Network-attached storage
-
A researcher has been analyzing large data sets for the last ten months. The researcher works with colleagues from other institutions and typically connects via SSH to retrieve additional data. Historically, this setup has worked without issue, but the researcher recently started getting the following message:

SY0-601 Part 01 Q19 009 Which of the following network attacks is the researcher MOST likely experiencing?
- MAC cloning
- Evil twin
- Man-in-the-middle
- ARP poisoning
-
An organization is developing an authentication service for use at the entry and exit ports of country borders. The service will use data feeds obtained from passport systems, passenger manifests, and high-definition video feeds from CCTV systems that are located at the ports. The service will incorporate machine-learning techniques to eliminate biometric enrollment processes while still allowing authorities to identify passengers with increasing accuracy over time. The more frequently passengers travel, the more accurately the service will identify them. Which of the following biometrics will MOST likely be used, without the need for enrollment? (Choose two.)
- Voice
- Gait
- Vein
- Facial
- Retina
- Fingerprint