98-365 : Windows Server Administration Fundamentals : Part 04
98-365 : Windows Server Administration Fundamentals : Part 04
-
Which Hyper-V network type shares the host’s physical network adapter?
- External
- Public
- Private
- Internal
Explanation:
For Hyper-V host networking, the most common option is to create an external access virtual switch. This allows VMs on the host to access other systems on a traditional VLAN or standard switched network. -
The University Chess Club has a single Windows Server 2016 server. The server has 12 GB of RAM and 1TB of disk space on a RAID 5 array. Using this server, you need to install two separate instances of Windows Server 2016: one to act as a web server and one to act as a database server.
Which Windows Server 2016 role or feature provides this capability?
- Windows Deployment Services
- Hyper-V
- Windows System Resource Manager
- Windows Internal Database
Explanation:
Hyper-V can create virtual machines on x86-64 systems.
Starting with Windows 8, Hyper-V supersedes Windows Virtual PC as the hardware virtualization component of the client editions of Windows NT. A server computer running Hyper-V can be configured to expose individual virtual machines to one or more networks. -
HOTSPOT
You create a user account named user1 and an Active Directory Domain Services group named RDGroup in Active Directory Domain Services. The lab environment is shown in the following image:
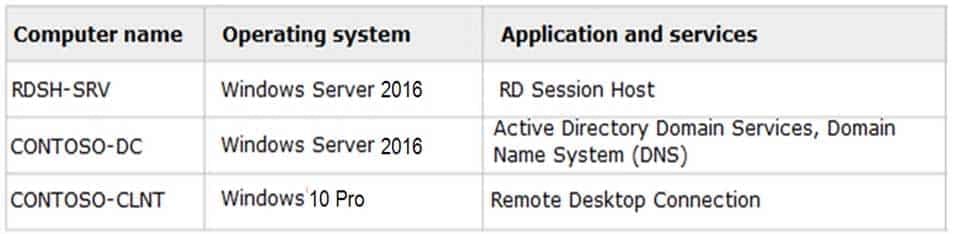
98-365 Part 04 Q03 007 
98-365 Part 04 Q03 008 Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.

98-365 Part 04 Q03 009 Question 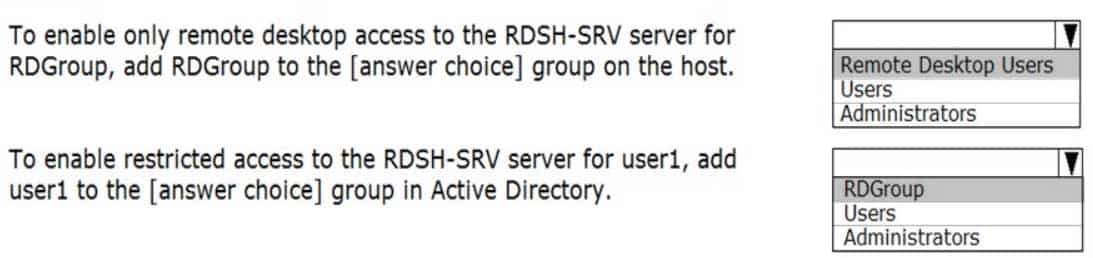
98-365 Part 04 Q03 009 Answer -
You are an IT intern for Tailspin Toys.
Your manager attends a conference out of town and wants you to perform routine maintenance directly on a Windows Server 2016 server console.
Because you have restricted access, you need your manager to enter credentials at a UAC prompt in your session.
What should you do?
- Have your manager use Server Manager to connect to the server.
- Have your manager use Remote Administration to connect to the server.
- Send a Remote Assistance request to your manager.
- Have your manager use Remote Desktop to connect to the server.
Explanation:
With Remote Assistance the manager can take control of your computer and enter the password.Note: Remote Assistance enables a trusted person (a friend, support person, or IT administrator) to remotely and activelyassistssomeone with a computer problem. The helper (also called an expert) can view the screen of the user requesting assistance and offer advice. With the permission of the user, the helper can take control of the user’s computer and perform tasks remotely.
-
Your relative is the owner of Humongous Insurance, and you provide part time IT support for the company’s Windows desktops and servers. All of its computers are on a private network behind a firewall.
Because you are going away to college, you need a secure method to manage the servers and desktops.
Which two Windows Server 2016 features should you use? (Choose two.)
- VPN Server
- Hyper-V
- Remote Desktop
- Active Directory Federation Services
- FTP Server
Explanation:
You can set VPN Server or Remote Desktop to securely access the network remotely. -
This question requires that you evaluate the underlined text to determine if it is correct.
The minimum permission needed to delete other users’ documents from a print queue is “Print”.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- Manage Documents
- Manage Printers
- Deny
- No change is needed
Explanation:
Manage documents. If you have this permission, you can manage all jobs for a printer that are waiting in the print queue, including documents or files that are being printed by other users.Incorrect Answers:
D: With print permissions you can only delete your own documents. -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

98-365 Part 04 Q07 010 Question 
98-365 Part 04 Q07 010 Question Explanation:
IIS Manager is a graphical interface for configuring your application pools or your Web, FTP, SMTP, or NNTP sites. With IIS Manager, you can configure IIS security, performance, and reliability features. You can add or delete sites; start, stop, and pause sites; back up and restore server configurations; and create virtual directories for better content management, to name only a few of the administrative capabilities. -
You use group policy to manage users and computers in your Active Directory Domain Services (AD DS) domain. All domain controllers run Windows Server 2016.
You need to see what effect the applied group policies are having on an individual computer.
What should you use?
- Local Users and Groups
- Resultant Set of Policy
- Local Security Policy
- Effective Permissions
Explanation:
If you would like to find out what group policy settings are applied to a user, you can use Resultant Set of Policy. You’ll find this tool in the Group Policy Management Console. This tool evaluates all the group policies that apply to the user and lists the resultant settings that are applied from the group policies. -
You need to grant a set of users permissions to a specific folder.
Where should you place the user accounts?
- Domain root
- Security group
- Shared folder
- Organizational Unit
Explanation:
You can use security groups to group users who need the same permissions to a folder. Permissions applied to the security group are applied to all members of the group. -
HOTSPOT
You are troubleshooting a permissions issue with the Reports share. The permissions are shown in the following image:

98-365 Part 04 Q10 011 The groups connect to the share.
What are the effective permissions applied to the groups when they access files in the Reports share?
Use the drop-down menus to select the answer choice that answers the question. Each correct selection is worth one point.

98-365 Part 04 Q10 012 Question 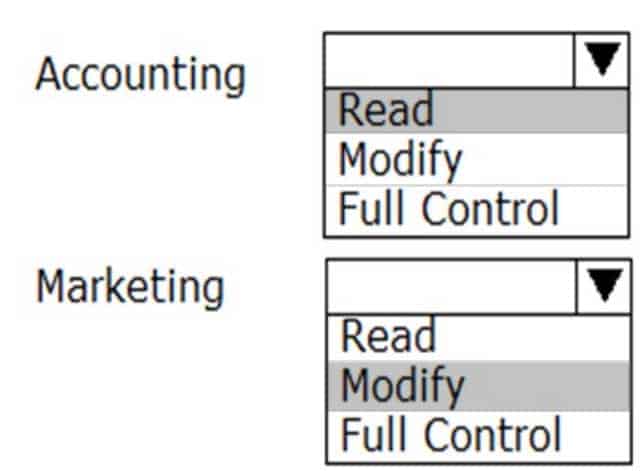
98-365 Part 04 Q10 012 Answer Explanation:
Accounting: Read
Read plus Modify equals Read as it is the most restrictive.
Marketing: Modify
Modify plus Change equals Modify as they are equal.Note: Share permissions and NTFS permissions are independent in the sense that neither changes the other. The final access permissions on a shared folder are determined by taking into consideration both the share permission and the NTFS permission entries. The more restrictive permissions are then applied.
-
You manage the servers for the School of Business at your university. The school has a Hyper-V server that runs three virtual machines (VMs). Each VM runs Windows Server 2016.
You need to apply the latest Windows server updates to each of the VMs. You need to be able to revert the servers back to their original state before applying the updates.
Which Microsoft Virtualization feature should you use?
- Live Migration
- Checkpoints
- VHD Virtual Hard Disks
- Failover Cluster
Explanation:
Checkpoints (formerly called snapshots) provide a fast and easy way to revert the virtual machine to a previous state. -
This question requires that you evaluate the underlined text to determine if it is correct.
“Microsoft App-V” can make applications available to end user computers without having to install the applications on those computers.
Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
- Microsoft Hyper-V
- DirectAccess
- Windows Deployment Services
- No change is needed.
Explanation:
Microsoft Application Virtualization (MS App-V) platform allows applications to be deployed (“streamed”) in real-time to any client from a virtual application server. It removes the need for traditional local installation of the applications. -
This question requires that you evaluate the underlined text to determine if it is correct.
The default security permission assigned to Everyone when a new share is created is “change”.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- Read
- Full control
- None
- No change is needed.
Explanation:
Read is the default permission. -
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
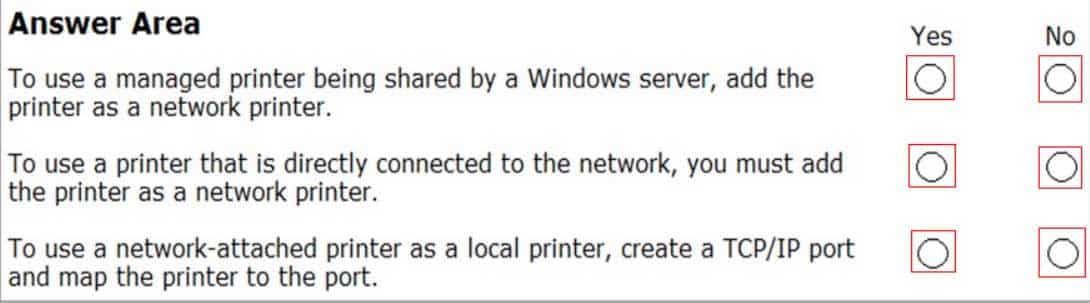
98-365 Part 04 Q14 013 Question 
98-365 Part 04 Q14 013 Answer -
You are an IT technician for a company that has an environment consisting entirely of computers running Windows Server 2016 or Windows 10. Your network is configured as an Active Directory Domain Services (AD DS) domain.
You need to establish a secure method that allows employees to work remotely but still have access to the internal network resources.
What are two possible ways to achieve this goal? (Choose two.)
- Offline Files
- DirectAccess
- Network Access Protection (NAP)
- Virtual Private Network (VPN)
- Distributed File System (DFS) Namespace
- Remote Desktop
Explanation:
B: DirectAccess, also known as Unified Remote Access, is a VPN-like technology that provides intranet connectivity to client computers when they are connected to the Internet.
D: The remote users can get secure remote access through VPN. -
Which of the following statements best describe the functions of RD Connection Broker in network infrastructure? Each correct answer represents a complete solution. (Choose two.)
- It is used to permit a user to reconnect to his existing session in a load-balanced RD Session Host server farm.
- It is used to integrate with Hyper-V to provide virtual machines by using RemoteApp and Desktop Connection.
- It is used to redirect users to a shared virtual machine pool where a virtual machine is dynamically assigned.
- It is used to enable a user to evenly distribute the session load among RD Session Host servers in a load-balanced RD Session Host server farm.
Explanation:
The various functions of RD Connection Broker are as follows:– It is used to permit a user to reconnect to his existing session in a load-balanced RD Session Host server farm.
– It is used to enable a user to evenly distribute the session load among RD Session Host servers in a load-balanced RD Session Host server farm.
– It is used to provide users access to virtual desktops that are hosted on RD Virtualization Host servers and to RemoteApp programs that are hosted on RD Session Host servers using RemoteApp and Desktop Connection.Incorrect Answers:
B, C: Both of these are the functions of RD Virtualization Host. -
Which of the following are the levels of printer permissions provided by Windows Server 2016? Each correct answer represents a complete solution. (Choose three.)
- Manage documents
- Reload the printer
- Manage this printer
Explanation:
There are three levels of printer permissions provided by Windows Server 2016: Print: It permits users to send documents to the printer.
Manage this printer: It permits users to modify printer settings and configurations. Manage documents: It gives the ability to cancel, pause, resume, or restart a print lob.Incorrect Answers:
C: There is no such level of printer permission in Windows Server 2016 as reload the printer. -
Which of the following servers is used to store and forward e-mail messages using several protocols, including SMTP, POP3, and IMAP?
- File server
- Monitoring server
- Database server
- Mail server
Explanation:
A mail server is a program used to store and forward e-mail messages using several protocols, including SMTP, POP3, and IMAP. A mail server is also recognized by the names, such as a mail transfer agent or MTA, a mail transport agent, a mail router, and an Internet mailer. It works with other programs to build a messaging system.Incorrect Answers:
A: A file server on a network is a computer configured to provide a central network location for users to store files and share them with other users on the network.B: A monitoring server is used to monitor the network and servers for intruders or other security breaches.
C: A database server is a computer program that provides database services to other computer programs or computers, as defined by the client-server model. The term may also refer to a computer dedicated to running such a program. Database management systems frequently provide database server functionality, and some DBMSs (e.g., MySQL) rely exclusively on the client-server model for database access.
-
Adam works as a Software Tester for SecureEnet Inc. He is required to test the software on different operating systems. Adam installs Windows 10 on his laptop, which enables him to create, mount, and boot from VHD files.
Which of the following statements are true about Virtual Hard Disk (VHD)? Each correct answer represents a complete solution. (Choose three.)
- VHD can be used to install a wide variety of operating systems.
- VHD allows multiple operating systems to reside on a single host machine
- VHDs are implemented as files that reside on the native host file system.
- VHD is a file formatted to be structurally different to a physical Hard Disk Drive.
Explanation:
A Virtual Hard Disk (VHD) is a file formatted to be structurally identical to a physical Hard Disk Drive. It is typically used in various virtualization packages, and can be used to install a wide variety of operating systems.
A Virtual Hard Disk allows multiple operating systems to reside on a single host machine. This method enables developers to test software on different operating systems.
VHDs are implemented as files that reside on the native host file system.
Native VHD Boot refers to the ability of a physical computer to mount and boot from an operating system contained within a VHD. Windows 10 supports this ability using VHDX files, both with and without a host operating system to be present. -
Web developers request FTP access to the Web server so that they can upload and download updated contents.
Which of the following ports does FTP use for communication? Each correct answer represents a complete solution. (Choose two.)
- 20
- 80
- 23
- 21
Explanation:
File Transfer Protocol (FTP) is a standard network protocol used to copy a file from one host to another over a TCP/IP-based network, such as the Internet. FTP is built on a client-server architecture and utilizes separate control and data connections between the client and server applications, which solves the problem of different end host configurations (i.e., Operating System, file names).
FTP is used with user-based password authentication or with anonymous user access. FTP uses ports 20 and 21 for communication.Incorrect Answers:
B: Port 80 is used for HTTP which is used to request and transmit files, especially Web pages and Webpage components, on the World Wide Web.
C: Port 23 is used for Telnet which is used on the Internet to provide a bidirectional interactive text-oriented communications using a virtual terminal connection.