98-365 : Windows Server Administration Fundamentals : Part 05
98-365 : Windows Server Administration Fundamentals : Part 05
-
Which of the following statements regarding the Secure Sockets Layer (SSL) security model are true? Each correct answer represents a complete solution. (Choose two.)
- The server always authenticates the client.
- The client can optionally authenticate the server.
- The server can optionally authenticate the client.
- The client always authenticates the server.
Explanation:
In the SSL model of security, the client always authenticates the server, and the server has the option to authenticate the client. In normal circumstances, Web servers do not authenticate the client during the handshake process. The verification of the client can be done externally from the SSL session to reserve precious processing resources for encrypted transactions.
The following image shows the steps SSL takes during the handshake process:
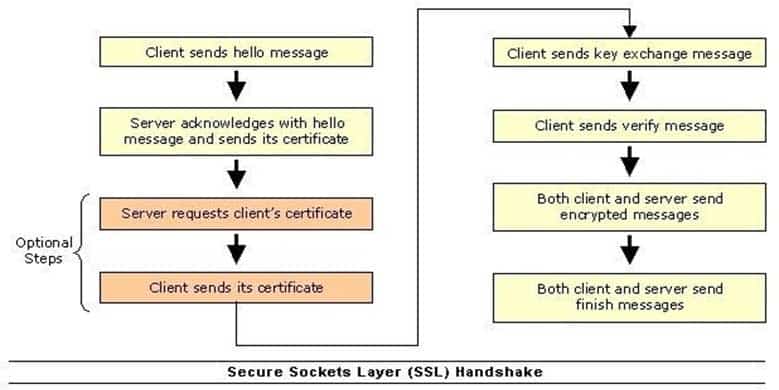
98-365 Part 05 Q01 014 -
You work as a Server Administrator for company Inc. The company has a virtual server hosted on a Windows Server 2016 server with the Hyper-V role installed.
You have upgraded an application on the virtual server. You experience that this upgrade causes problems. Now, you want to quickly revert back to the point before the changes are made.
Which of the following will you use to accomplish the task?
- Virtual Server Migration Toolkit
- Checkpoints
- Windows System Resource Manager
- Logical unit number
Explanation:
In order to accomplish the task, you should use checkpoints. Snapshots have been improved in Windows Server 2016 and are now called checkpoints.
Checkpoints are files that contain the configuration and data in a virtualized machine.
The Hyper-V Manager Console provides the facility to take a snapshot of a virtual machine running under Hyper-V. This snapshot can be used to quickly roll-back the instance of an operating system when the snapshot was taken. In state of any disaster such as malfunctioning virtual machine, these snapshots are very helpful to recover from such situations.Incorrect Answers:
A: The Virtual Server Migration Toolkit (VSMT), a command-line-based tool provided by Windows Server 2016, is used to migrate existing servers in the network environment to a virtualized partition of Windows Server 2016. VSMT has been specially designed for administrators to handle small number of servers that needs to be virtualized.
It however, cannot be used to manage these servers. It uses XML files to store configuration data during the migration process. The tool is compatible with both the Hyper-V and the Virtual Server 2005 R2.C: Windows System Resource Manager (WSRM) is a tool for resource management and enables the allocation of resources, including processor and memory resources, among multiple applications based on business priorities. With WSRM, a system administrator can set CPU and memory allocation policies on applications, manage CPU utilization, and apply policies to users or groups on a Terminal Services application server. WSRM also applies limits to process working set size and committed memory consumption.
D: The logical unit number or LUN is the identifier of a SCSI logical unit, and by extension of a Fibre Channel or iSCSI logical unit. A logical unit is a SCSI protocol entity, which performs classic storage operations such as read and write. Each SCSI target provides one or more logical units. A logical unit typically corresponds to a storage volume and is represented within a computer operating system as a device.
-
David and Vivian work as Network Administrators for company Inc. David installs a printer on his Windows 10 computer. The printer will be shared on the network and will be used only by the members of the Developers local group.
David wants to accomplish the following goals:
– Prevent all other members, except those of the Developers local group, from using the printer.
– Members of the Developers local group will only manage print jobs sent by them.
Only he and Vivian will manage the printer and all print jobs.David takes the following steps:
– Grant the Allow-Print permission to the Developers local group.
– Grant the Allow-Manage Documents and Allow-Manage Printers permissions to Vivian’s and his user accounts.Which of the above stated goals will David accomplish?
- Only the second goal will be accomplished.
- Only the third goal will be accomplished.
- Only the first and third goals will be accomplished.
- Only the second and third goals will be accomplished.
- All the three goals will be accomplished.
- Only the first goal will be accomplished.
- Only the first and second goals will be accomplished.
Explanation:
Granting the Allow-Print permission to the Developers local group will allow members of the group to print. By default, the Everyone group has print permission. This permission entry needs to be removed to meet the first goal.
When a printer is shared, all users by default can manage printing of their own documents. Therefore, the second goal is met.
David granted the Allow-Manage Documents and Allow-Manage Printers permissions to Vivian’s and his user accounts to manage the documents printed by other users. This meets the third goal. -
Which of the following statements best describe the features of a fixed-size VHD? Each correct answer represents a complete solution. (Choose two.)
- It offers better performance by eliminating the fragmentation associated with the growing file.
- It has a set amount of hard disk space and that amount does not change.
- It uses the space that is being used currently by the VHD.
- It provides a way to set up the VHD if hard drive space is limited on the server.
Explanation:
Fixed-size VHDs have a set amount of hard disk space and that amount does not change. Fixed size means that each VHD is set to a specific hard drive storage space and that space is taken by the system even if the VHD is less than what is set. As an example, if 16GB is designated to a fixed-size VHD, then all 16GB will be taken by VHD on the hard disk immediately – regardless of how much the system is actually using.
The fixed-size VHD option offers better performance by eliminating the fragmentation associated with the growing file.Incorrect Answers:
C, D: Dynamic VHDs only use the space that is being used currently by the VHD. So if a dynamic VHD is set to 20GB but the VHD is currently using only 10GB, then 10 GB is all that is currently being used by the dynamic VHD. This is the way that a user wants to set up his VHD if hard drive space is limited on the server. -
You have installed and configured the Application Server role on a server running Windows Server 2016.
For which of the following options can you add support on this server? Each correct answer represents a complete solution. (Choose four.)
- Web Server
- COM+ Network Access
- Windows Process Activation Service
- DFS Management
- File Server Resource Manager
- TCP Port Sharing
Explanation:
You can add support for the following options when you install the Application Server role on a computer running Windows Server 2016:– Web Server
– COM+ Network Access
– Windows Process Activation Service
– TCP Port Sharing
– Distributed TransactionsIncorrect Answers:
D, E: You cannot add support for the DFS Management and File Server Resource Manager options. -
You work as a Server Administrator for company Inc. The company has a Windows Server 2016 based network environment. There is a domain controller with Windows Server 2016 installed on it.
You want to install the Hyper-V role for production server consolidation and business continuity management.
Which of the following are the prerequisites for installing the Hyper-V role? Each correct answer represents a complete solution. (Choose three.)
- x32-based processor
- GUI accelerator
- Hardware-assisted virtualization
- Hardware-enforced Data Execution Prevention
- x64-based processor
Explanation:
The prerequisites for installing the Hyper-V role are as follows:
An x64-based processor: Hyper-V is available in x64-based versions of Windows Server 2016 – specifically, the x64-based versions of Windows Server 2016 Enterprise, Windows Server 2016 Datacenter, and Windows Server 2016 Standard.
Hardware-enforced Data Execution Prevention (DEP): This should be both available and enabled. Specifically, a user should enable the Intel XD bit (execute disable bit) or AMD NX bit (no execute bit).
Hardware-assisted virtualization: It is available in processors that include a virtualization option – particularly, Intel Virtualization Technology (Intel VT) or AMD Virtualization (AMD-V).Incorrect Answers:
A, B: These are not prerequisites for installing Hyper-V. -
You work as a Server Administrator for company Inc. The company has a Windows 2016-based Active Directory network.
You are assigning NTFS permissions to the E:\Projects folder for the Marketing group. You want to ensure that the members of the Marketing group can list the contents of the folder and read the data of files contained in the folder, but none of them can change or delete data from the folder.
Which of the following permissions will you apply?
- Write
- Full control
- Read
- Modify
Explanation:
You should apply Read permission to the E:\Projects folder for the Marketing group. After applying this NTFS permission, the members of the Marketing group can list the contents of the folder and read the data of files contained in the folder, but none of them can change or delete data from the folder.Incorrect Answers:
A: Write permission allows users to write in files or folders.
B: Full Control permission allows users to make changes in files or folders.
D: Modify permission allows users to make changes in files and folders. -
Which of the following statements best describe the features of a network printer? Each correct answer represents a complete solution. (Choose two.)
- Anyone in the network can use it to print only if the machine to which the printer is connected is switched on.
- It is shared by more than one computer.
- Print jobs can be sent only by the computer that is directly connected to the printer.
- It is connected directly to a computer.
Explanation:
A local printer is connected directly to a computer. On the local printer, print jobs can be sent only by the computer that is directly connected to the printer. A network printer, on the other hand, is one that is shared by more than one computer. If the printer is shared, the printer becomes a network printer to those machines connected on the network. However, users of other computers in the network will be able to print to that printer only if the machine to which printer is connected is switched on. -
You add Web Server support while installing the Application Server role on a computer running Windows Server 2016. Web Server support installs IIS (Internet Information Services) on the server.
Which of the following benefits are provided by IIS? Each correct answer represents a complete solution. (Choose three.)
- It is used to support ASP.NET applications accessed from a Web browser.
- It is used to support Web services built with ASP.NET or WCF (Windows Communication Foundation).
- It is used to disable Application Server to host external Websites with static or dynamic content.
- It is used to enable Application Server to host internal Websites with static or dynamic content.
Explanation:
The benefits of installing IIS in an application server are as follows:
– It is used to enable Application Server to host internal or external Websites or services with static or dynamic content.
– It is used to support ASP.NET applications accessed from a Web browser.
– It is used to support Web services built with ASP.NET or WCF (Windows Communication Foundation). -
Which of the following server roles simplifies the process of deploying applications that respond to requests sent over the network from remote applications?
- Windows Server Virtualization
- Network Policy and Access Services
- Active Directory Certificate Services
- Application Server
Explanation:
Application Server is an expanded server role of Windows Server 2016 that simplifies the process of deploying applications that respond to requests sent over the network from remote applications. Windows Server 2016 provides support for applications by enhancing application availability and accessibility through the Application Server role. The Application Server role provides environment for deploying and running line-of-business (LOB) applications that are built with the Microsoft .NET Framework.
The features provided by Application Server role are provided in the table below:
During the server role installation, administrators select services that support applications that are designed to use COM+, Message Queuing, Web services, and distributed transactions. Microsoft recommends installing the Application Server role when a custom business application is deployed on the network and the developer has indicated that specific role services are required.Incorrect Answers:
A: The Windows Server Virtualization server role is a server role of Windows Server 2008. It was renamed to Hyper-V in later versions of Windows. This server role offers services for creating and managing virtual machines and their resources. A virtual machine is a computer system that allows a user to run more than one operating system simultaneously.B: The Network Policy and Access Services server role is a server role of Windows Server 2016. This server role offers various methods to provide users with local and remote network connectivity, to connect network segments, and to permit network administrators to centrally manage network access and client health policies.
These methods use VPN servers, dial- up servers, routers, and 802.11 protected WAP (wireless access point).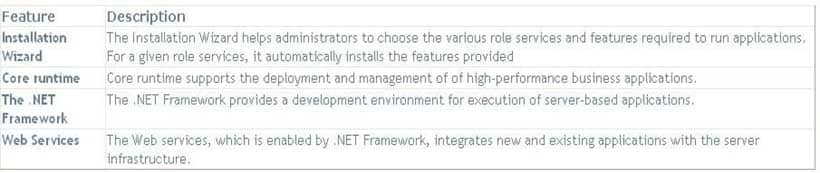
98-365 Part 05 Q10 015 C: The Active Directory Certificate Services server role is a server role of Windows Server 2016. This server role offers services to create and manage public key certificates that are used in software security systems. These software security systems use public key technologies to verify the identity of a person, device, or service, which can be used by secure mail, secure wireless networks, VPNs, lPSec, EFS, smart card logon, and others.
-
Which of the following server roles offers various methods to provide users with local and remote network connectivity, to connect network segments, and to permit network administrators to centrally manage network access and client health policies?
- Active Directory Certificate Services
- Network Policy and Access Services
- Web Services
- Terminal Services
Explanation:
The Network Policy and Access Services server role is a server role of Windows Server 2016. This server role offers various methods to provide users with local and remote network connectivity, to connect network segments, and to permit network administrators to centrally manage network access and client health policies. These methods use VPN servers, dial-up servers, routers, and 802.11 protected WAP (wireless access point).Incorrect Answers:
A: The Active Directory Certificate Services server role is a server role of Windows Server 2016. This server role offers services to create and manage public key certificates that are used in software security systems. These software security systems use public key technologies to verify the identity of a person, device, or service, which can be used by secure mail, secure wireless networks, VPNs, lPSec, EFS, smart card logon, and others.C: The Web Services server role enables sharing of information on the Internet, an intranet, or an extranet through a unified Web platform. The unified Web platform incorporates Internet Information Server (IIS) in order to provide Web pages, FTP services or newsgroups, ASP.NET, Windows Communication Foundation, and Windows SharePoint Services.
D: The Terminal Services server role is a legacy role that allows a user to connect to a terminal server in order to remotely run programs, use network resources, and access the Windows desktop on the server. Terminal Services is now called Remote Desktop Services.
-
Which of the following is NOT a purpose of using a container?
- To group tasks as a unit so that if a task fails all other tasks can be rolled back.
- To run all the tasks at a time until a condition becomes false.
- To queue up the tasks so that if a task fails, the next task in the queue gets operated.
- To run each task repeatedly.
Explanation:
Containers are objects that are used to provide services to a task. They cannot be used for queuing up the tasks.Incorrect Answers:
A, B, D: A container is an object used to provide a structure to a package or services to a task. A container can be used for the following purposes:
– To run each task repeatedly.
– To run all the tasks at a time until a condition becomes false.
– To group tasks as a unit so that if a task fails all other tasks can be rolled back. -
You work as a Server Administrator for company Inc. You want all transactions to the storefront on the Web server to be encrypted.
Which of the following security protocols will you use to encrypt Web traffic?
- L2TP
- PPTP
- SSL
- IPSec
Explanation:
In order to encrypt Web traffic, you should use the SSL protocol. The Secure Sockets Layer (SSL) is a commonly-used protocol for managing the security of a message transmission on the Internet. SSL has recently been succeeded by Transport Layer Security (TLS), which is based on SSL. SSL uses a program layer located between the Internet’s Hypertext Transfer Protocol (HTTP) and Transport Control Protocol (TCP) layers. URLs that require an SSL connection start with https: instead of http:.Incorrect Answers:
A: Layer 2 Tunneling Protocol (L2TP) is a more secure version of Point-to- Point Tunneling Protocol (PPTP). It provides tunneling, address assignment, and authentication. It allows the transfer of Point-to-Point Protocol (PPP) traffic between different networks. L2TP combines with IPSec to provide tunneling and security for Internet Protocol (IP), Internetwork Packet Exchange (IPX), and other protocol packets across IP networks.B: Point-to-Point Tunneling Protocol (PPTP) is a method for implementing virtual private networks. PPTP does not provide confidentiality or encryption. It relies on the protocol being tunneled to provide privacy. It is used to provide secure, low-cost remote access to corporate networks through public networks such as the Internet. Using PPTP, remote users can use PPP- enabled client computers to dial a local ISP and connect securely to the corporate network through the Internet. PPTP has been made obsolete by Layer 2 Tunneling Protocol (L2TP) and IPSec.
D: Internet Protocol Security (IPSec) is a standard-based protocol that provides the highest level of VPN security. IPSec can encrypt virtually everything above the networking layer. It is used for VPN connections that use the L2TP protocol. It secures both data and password. IPSec cannot be used with Point-to-Point Tunneling Protocol (PPTP).
-
Which of the following types of resource record is generally used with virtual servers that point to several servers offering network load balancing to distribute work?
- MX
- SRV
- SOA
- CNAME
Explanation:
CNAME (canonical name) is a resource record that creates an alias or an alternate DNS domain name for a specific hostname. This resource record is generally used with virtual servers that point to several servers that offer network load balancing in order to distribute work.Incorrect Answers:
A: MX (mail exchanger) is used to specify which mail exchanger to contact for a specified domain and in what order to use each mail host.
B: SRV (service) locates servers that are hosting a particular service, including LDAP servers or domain controllers.
C: SOA (Start of Authority) identifies the name server that is the authoritative source of information for a DNS domain or zone. -
You work as a Server Administrator for company Inc. The company has a Windows 2016-based Active Directory network. You are assigning effective permissions to the Tasks folder.
Which of the following factors will you use to determine effective permissions? Each correct answer represents a complete solution. (Choose three.)
- Local privileges
- Anonymous logon
- Global group membership
- Local permissions
- Enterprise domain controllers
Explanation:
In order to determine effective permissions, you should use the following factors:– Local permissions
– Local privileges
– Global group membership
– Local group membership
– Universal group membershipIncorrect Answers:
B, E: These factors are not used to determine effective permissions. -
Which of the following services provide network access over the Internet using a virtual private network so that a user can access his internal network resources, such as e-mails and data files?
- Remote access services
- Application services
- Monitoring services
- File services
Explanation:
Remote access is a service that maintains several inbound requests while connecting servers or networks. It provides terminal services to log on to a server remotely and access a desktop, the start menu, and a program easily from anywhere. Remote access also provides network access over the Internet using a virtual private network so that a user can access his internal network resources, such as e-mails and data files.Incorrect Answers:
B: Application services provide an integrated environment to deploy and run various applications.
D: File services define various settings for files stored in a computer system.
C: Monitoring services are used to troubleshoot various system related issues. -
You work as a System Administrator in SunInfo Inc. The company uses System Center Data Protection Manager 2012 R2 for data protection.
You want to protect data that is part of a Distributed File System (DFS) namespace hierarchy.
How will you select file shares for effective protection in this scenario?
- By their server-specific local paths.
- Through DNS namespace.
- Through DFS namespace paths.
- By selecting multiple targets.
Explanation:
You can protect data in a Distributed File System (DFS) namespace hierarchy using DPM. However, you cannot select file shares for protection through their DFS namespace paths. You can select shares for protection by their server-specific local paths.Incorrect Answers:
B: The Domain Name System (DNS) is a hierarchical naming system for computers, services, or any resource connected to the Internet or a private network.
C: DPM does not provide protection of shares through DFS namespace paths.
D: For effectively protecting data, if your namespace includes links or roots that have multiple targets with the same data, you should protect only one target. -
You work as a System Administrator for company Inc. The company has a Windows Server 2016 network environment. All client computers run Windows 10 Pro and all servers run Windows Server 2016.
You have configured a computer for virtualization using Hyper-V.
Which of the following files does the virtual machine use in Hyper-V? Each correct answer represents a complete solution. Choose all that apply.
- .vsv
- .vhd
- .vcv
- .vmcx
Explanation:
In Hyper-V, a virtual machine uses the following files:
Configuration (.VMCX): This is the binary machine configuration file that replaces the XML file. It can be found at <VM Location>\Virtual Machines.
Virtual hard disk (.VHD or .VHDX): These are the files that contain everything of value, the disks. Here is the operating system, programs, settings, unique machine data, and the user data. These files can be stored anywhere, but I prefer to keep them at <VM Location>\Virtual Hard Disks.Incorrect Answers:
A: The .vsv file not used in Hyper-V 2016.
C: The .vcv file not used in Hyper-V 2016. -
You work as a Server Administrator for company Inc. The company has a Windows-based network environment with client computers running Windows 10 and a Windows Server 2016 server.
The company uses an order-processing application that accesses customer records stored in a database. The application accesses customer information through a set of WCF Web services.
Which of the following server roles will you configure on the server used in your organization?
- Windows Server Virtualization
- Network Policy and Access Services
- Application Server
- DHCP Server
Explanation:
You should configure the Windows Server 2016 computer as an application server. Application Server is an expanded server role of Windows Server 2016 that simplifies the process of deploying applications that respond to requests sent over the network from remote applications. Windows Server 2016 provides support for applications by enhancing application availability and accessibility through the Application Server role. The Application Server role provides environment for deploying and running line-of-business (LOB) applications that are built with the Microsoft .NET Framework version 3.0.
The features provided by Application Server role are provided in the table below:
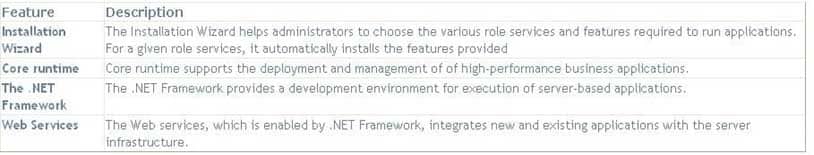
98-365 Part 05 Q19 016 During the server role installation, administrators select services that support applications that are designed to use COM+, Message Queuing, Web services, and distributed transactions. Microsoft recommends installing the Application Server role when a custom business application is deployed on the network and the developer has indicated that specific role services are required.
Incorrect Answers:
A: The Windows Server Virtualization role offers services for creating and managing virtual machines and their resources.B: Network Policy and Access Services (NPAS) is a server role in W indows Server 2008.
The role is a logical grouping of the following related network access technologies:– Network Policy Server (NPS)
– Routing and Remote Access
– Health Registration Authority (HRA)
– Host Credential Authorization Protocol (HCAP)These technologies are the role services of the NPAS server role. The NPAS server role allows administrators to deploy and operate a virtual private network (VPN), dial-up networking, 802.1x protected wired and wireless access, and Cisco Network Admission Control (NAC)-based devices.
D: The DHCP Server role allows you to centrally manage IP addresses and related information. This also allows you to configure client network settings at a server rather than configuring them on each client computer.
-
Which of the following is a web server application and set of feature extension modules created by Microsoft for use with Microsoft Windows?
- Secure Sockets Layer
- File Transfer Protocol
- Internet Information Services
- World Wide Web
Explanation:
Internet Information Services (IIS) is a web server application and set of feature extension modules created by Microsoft for use with Microsoft Windows. It is the world’s second most popular web server in terms of overall websites behind the industry leader Apache HTTP Server.Incorrect Answers:
A: The Secure Sockets Layer (SSL) is a commonly-used protocol for managing the security of a message transmission on the Internet. SSL has recently been succeeded by Transport Layer Security (TLS), which is based on SSL. SSL uses a program layer located between the Internet’s Hypertext Transfer Protocol (HTTP) and Transport Control Protocol (TCP) layers. URLs that require an SSL connection start with https: instead of http:.B: File Transfer Protocol (FTP) is a standard network protocol used to copy a file from one host to another over a TCP/IP-based network, such as the Internet. FTP is built on a client- server architecture and utilizes separate control and data connections between the client and server applications, which solves the problem of different end host configurations (i.e., Operating System, file names). FTP is used with user-based password authentication or with anonymous user access.
D: The World Wide Web is abbreviated as WWW and commonly known as the Web. It is a system of interlinked hypertext documents that can be accessed through the Internet. With WWW, anyone can view Web pages that contain text, images, videos, and other multimedia and navigate between them using hyperlinks.