98-365 : Windows Server Administration Fundamentals : Part 08
98-365 : Windows Server Administration Fundamentals : Part 08
-
What is used to store and distribute a public key?
- digital certificate
- digital signature
- digital lock
- digital envelope
Explanation:
When you use SSL to encrypt web traffic, you are using asymmetric encryption, which involves a private key and a public key. The public key is provided to anyone who wants to access the web server, and the private key is kept secret, usually by the web server that you are trying to protect. A common method to distribute a public key is to use a digital certificate. -
What protocol is used to transfer files to or from a server?
- FTP
- SNMP
- VPN
- SMTP
Explanation:
File Transfer Protocol (FTP) is used to transfer files to or from a server. Most FTP sites are used primarily to download files. In most of these situations, FTP uses anonymous authentication, in which username and password are not required. -
What technology is used to link two computers or sites over the Internet while providing a secure connection?
- FTP
- SMTP
- VPN
- telnet
Explanation:
Virtual private networks (VPNs) link two computers through a wide-area network such as the Internet. To keep the connection secure, the data sent between the two computers is encapsulated and encrypted. -
What does L2TP use to encrypt data?
- IPSec
- PPTP
- MPPE
- SSTP
-
Which form of authentication sends username and password in clear text?
- PAP
- CHAP
- MS-CHAP
- EAP
Explanation:
Password Authentication Protocol (PAP) uses plain text (unencrypted passwords). PAP is the least secure authentication and is not recommended. -
What popular application is used to access a Windows server remotely?
- remote assistance
- remote desktop
- TELNET
- SSH
Explanation:
With early networks, users utilized dumb terminals (systems consisting of a monitor and keyboard without a processor) to connect to a mainframe. Later, computers could use TELNET to connect to a server and execute commands at a command prompt. Remote Desktop Services, formerly known as Terminal Services, is one component of Microsoft Windows that allows users to access applications and data on remote computers over a network. -
What is Microsoft’s virtualization server called?
- RRAS
- VPN
- Telnet
- Hyper-V
Explanation:
Virtualization has become quite popular during the last few years.
By using virtual machine technology, you can run multiple operating systems concurrently on a single machine, which allows separation of services while keeping costs to a minimum.
It can also be used to create Windows test systems in a safe, self-contained environment. Microsoft Hyper-V is a hypervisor-based virtualization system for 64-bit computers starting with Windows Server 2016. -
What technology is used to consolidate multiple servers onto one large physical server?
- Virtual Machine Technology
- V-Farm Technology
- Instance Technology
- VHD
Explanation:
By using virtual machine technology, you can run multiple operating systems concurrently on a single machine, which allows separation of services while keeping costs minimal.
It can also be used to create Windows test systems in a safe, self-contained environment. -
What two ports does FTP use?
- 20 and 21
- 21 and 22
- 20 and 22
- 21 and 25
Explanation:
FTP uses TCP ports 20 and 21. Port 20 is used for control, while port 21 is used for data transfer. -
What port does Remote Desktop and Remote Assistance use?
- 1471
- 3389
- 4043
- 8080
Explanation:
To access a computer running Remote Desktop Services, you use Remote Desktop Connections to access a computer’s graphical user interface, including the desktop, start menu, and programs, just as if you were sitting in front of the computer. Two technologies that allow you to remotely access a computer’s desktop are Remote Desktop and Remote Assistance over TCP port 3389. -
A domain controller that is designated to perform a set of specialized domain controller tasks is commonly referred to as a/an:
- Windows Internet Name Service (WINS) server
- Operations Master
- Organizational Unit
- Primary domain controller
Explanation:
Operations Master Roles
The five operations master roles are assigned automatically when the first domain controller in a given domain is created. -
What is the minimum Windows Server version on which Hyper-V can be installed?
- 2016 64-bit
- 2012 64-bit
- 2008 32-bit
- 2008 64-bit
Explanation:
Hyper-V, formerly known as Windows Server Virtualization, is a native hypervisor that enables platform virtualization on x86-64 systems. A beta version of Hyper-V was shipped with certain x86-64 editions of Windows Server 2008, and a finalized version (automatically updated through Windows Update) was released on June 26, 2008.
-
What is the default port for HTTPS?
- 21
- 80
- 135
- 443
Explanation:
43, TCP, Hypertext Transfer Protocol over TLS/SSL (HTTPS) -
To enable enhanced keyboard and mouse functions for a Hyper-V virtual machine, you need to install:
- Hyper-V Integration Components.
- Keyboard and mouse drivers.
- Microsoft Updates.
- Hyper-V Server.
Explanation:
To get a virtual machine (VM) to work properly, it’s critical to install the Hyper-V integration components. These integration components install agents into a VM that enable a host to successfully back up a VM, recognize when it has gone down, copy and paste data into and out of a VM, and synchronize its clock to the host. These components are important to processing a VM’s workload: In effect, their installation reconfigures an operating system to make it “aware” that it has been virtualized, resulting in an “enlightened” OS. -
Which type of license is required to connect remotely to an application?
- Windows Server External Connector License
- Remote Desktop Services Client Access License
- System Center Operations Manager Client Management License
- Remote Server Application License
Explanation:
Remote Desktop Services Client Access License is used to access applications on a Windows server. -
Which technology is designed to host calendars, contacts, and e-mail on the server?
- Microsoft Host Integration Server
- Microsoft Expression Studio
- Microsoft SQL Server
- Microsoft Exchange Server
-
Which is used to verify that a secure Web site is legitimate?
- Active Directory
- Enterprise trust
- Private key
- Digital certificate
-
One advantage of application virtualization is:
- Fewer operating system updates.
- Improved collaboration.
- Reduced network traffic.
- Reduced client administrative overhead.
-
HOTSPOT
You are configuring a web server for your school newspaper. The computer is running Windows Server 2016 and Internet Information Services (IIS).
You need to disable the ability for anonymous users to connect to the web server.
Which feature in IIS manager should you use?
To answer, select the appropriate feature in the IIS manager window in the answer area.
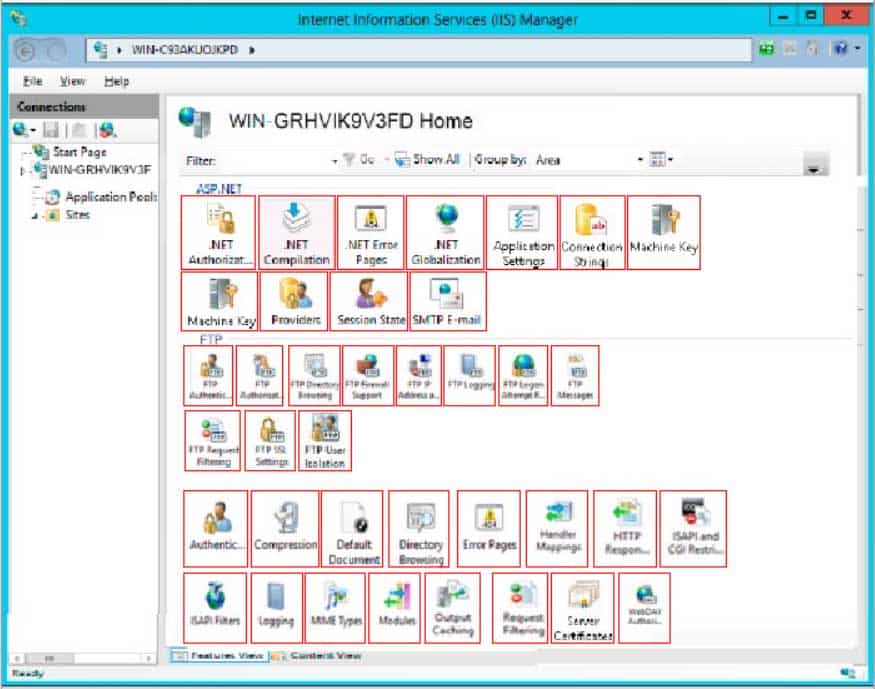
98-365 Part 08 Q19 017 Question 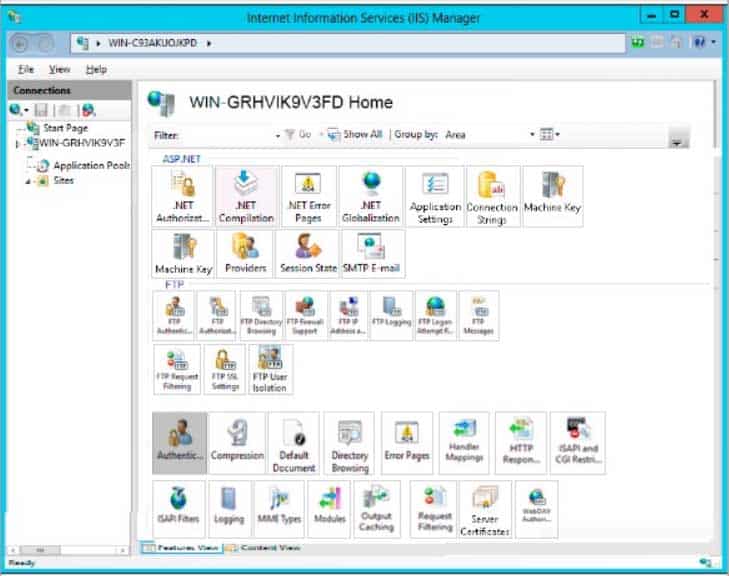
98-365 Part 08 Q19 017 Answer -
This question requires that you evaluate the underlined text to determine if it is correct.
Your network includes a server running a Server Core installation of Windows Server 2016 Datacenter Edition. You need to use graphic management utilities to manage the server from a network client computer running Windows 10.
You should install Remote Server Administration Tools on the Windows 10 client.
Review the underlined text. If it makes the statement correct, select “No change is needed”. If the statement is incorrect, select the answer choice that makes the statement correct.
- DirectAccess client
- Remote Desktop client
- Remote Assistance
- No change is needed.