98-365 : Windows Server Administration Fundamentals : Part 19
98-365 : Windows Server Administration Fundamentals : Part 19
-
The best method to data recovery is:
- backup
- DFS
- RAID
- spare drives
Explanation:
A backup, or the process of backing up, refers to making copies of data so that these copies can be used to restore the original after a data-loss event. They can be used to restore entire systems following a disaster or to restore small file sets that were accidentally deleted or corrupted. -
Which type of backup backs up only new and recently changed files since the last backup?
- full backup
- incremental backup
- differential backup
- copy backup
Explanation:
Full backups with incremental backups start with a full backup followed by several incremental backups. For example, once a week, you would perform a full backup on Friday night, which shuts off the archive attribute indicating that the files were backed up. Then any new files or changed files would have the archive attribute turned on. You would then perform an incremental backup Monday, Tuesday, Wednesday, and Thursday night, which only backs up new and changed files and shuts off the archive attribute. -
What file is used to translate host names to IP addresses?
- host file
- Imhosts file
- dns file
- wins file
Explanation:
Early TCP/IP networks used hosts (used with domain/hostnames associated with DNS) and lmhost (used with NetBIOS/computer names associated with WINS) files, which were text files that listed a name and its associated IP address. -
What is used to keep track of what a user does on a system?
- authentication
- auditing
- permissions
- user rights
Explanation:
Security can be divided into three areas:
– Authentication is used to prove the identity of a user.
– Authorization gives access to the user that was authenticated.
– To complete the security picture, you need to enable auditing so that you can have a record of the users who have logged in and what the user accessed or tried to access. -
How do you enable auditing on a Windows server?
- Windows Explorer
- Group Policies
- MS Configuration
- Registry editor
Explanation:
Auditing is not enabled by default. To enable auditing, you specify what types of system events to audit using Group Policy or the local security policy (Security Settings\Local Policies\Audit Policy). -
DRAG DROP
John works as a Virtualization Administrator for company Inc. The company has deployed Windows Server 2016 Server. He needs to change the size of the cache directly from the Application Virtualization node in Application Virtualization Client Management Console.
What are the correct and ordered steps for this process?
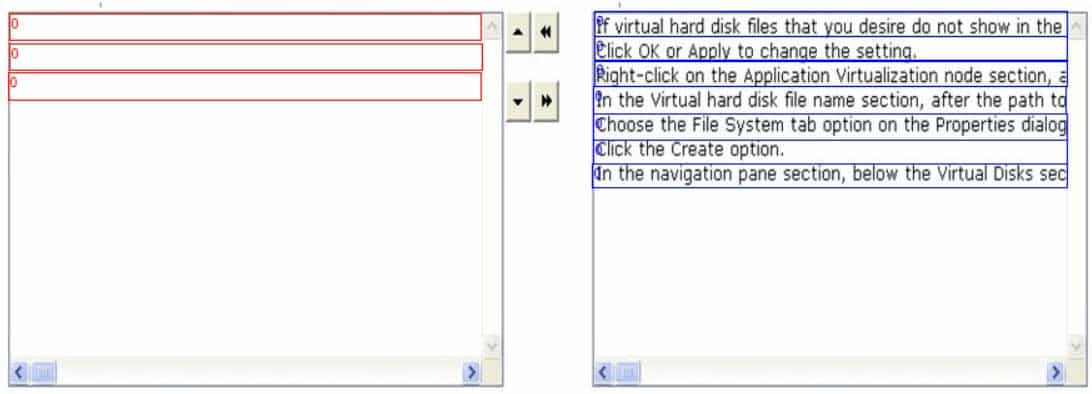
98-365 Part 19 Q06 043 Question 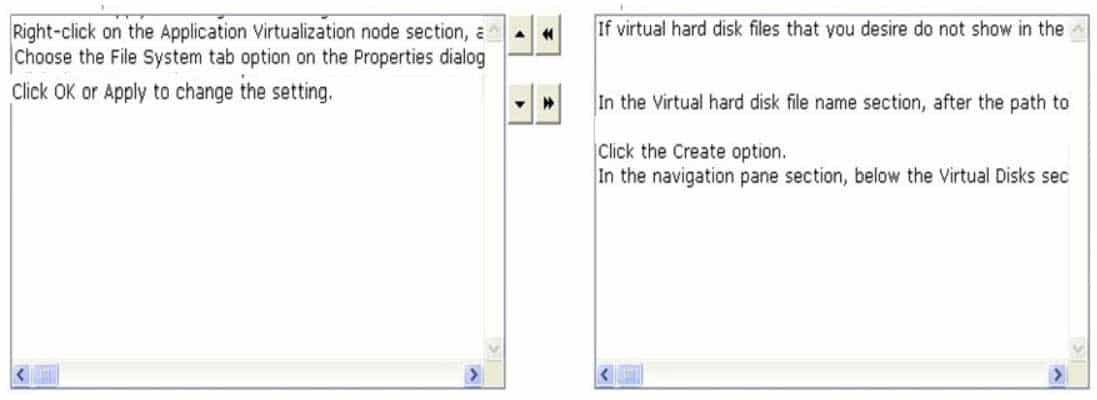
98-365 Part 19 Q06 043 Answer Explanation:
Right-click on the Application Virtualization node section, and then choose the Properties option from the pop-up menu section.
Choose the File System tab option on the Properties dialog box section. In the Client Cache Configuration Settings section, select and click on one of the following radio buttons to select how to manage the cache space:
Utilize maximum cache size: Enter a numeric value from 100 to 1,048,576 in the Maximum size (MB) field to determine the utmost size of the cache. The value shown in Reserved Cache Size determines the total cache in use.
Utilize free disk space threshold: Enter a numeric value to determine the total of the free disk space, in MB, that the cache must leave available on the disk space. This permits the cache to develop until the amount of free disk space accomplishes this limit. The numeric value described in free disk space remaining determines how much disk space is unutilized.
Click OK or Apply to change the setting. -
What program allows you to view processor and memory utilization quickly?
- Task Manager
- Performance Monitor
- System Information
- Configuration Manager
Explanation:
Task Manager is one of the handiest programs you can use to take a quick glance at performance to see which programs are using the most system resources on your computer. You can see the status of running programs and programs that have stopped responding, and you can stop a program running in memory by using Task Manager. -
What is the default path for the print spool folder?
- C:\Windows\System32\Spool\Printers
- C:\Windows\System\Spool32\Printers
- C:\Users\<%USERNAME%>\Microsoft\Spool\Printers
- C:\Windows\System32\Spool\Printer
Explanation:
When the print device is available, the spooler retrieves the next print job and sends it to the print device.
By default, the spool folder is located at C:\Windows\System32\Spool\Printers.
If you have a server that handles a large number of print jobs or several large print jobs, make sure the drive where the spool folder is has sufficient disk space. -
Running a system in safe mode:
- protects the system from viruses.
- protects the system from data loss.
- loads a minimum number of drivers.
- prevents unauthorized access.
-
Your backup plan calls for a full backup every Sunday. Every other day of the week, you need to back up only the changes since the last full backup.
Which backup type should you use for Tuesday?
- Daily
- Normal
- Copy
- Differential
-
To protect a server in case of a blackout, you should use a/an:
- Uninterruptible Power Supply.
- Dedicated surge protector.
- Power Supply Unit.
- Redundant power supply.
- Hot-swappable power supply.
- Line conditioner.
-
Which tool would you use to retrieve detailed information about a significant occurrence in a computer system?
- Event Viewer
- System Information
- System Monitor
- Resource Monitor
-
Which task is executed during the Power-On Self Test (POST)?
- The amount of system RAM is detected.
- The Master Boot Record is created.
- The operating system is initialized.
- Disk file systems are detected.
-
You configure Volume Shadow Copy Service (VSS) to save previous versions of a shared folder. By default, the copies of shared folders are stored in:
- A Network Attached Storage (NAS) device.
- A Distributed File System (DFS) share.
- A failover cluster.
- A local volume.
Explanation:
Shadow Copy technology requires the file system to be NTFS to be able to create and store shadow copies. Shadow Copies can be created on local and external (removable or network) volumes by any Windows component that uses this technology, such as when creating a scheduled Windows Backup or automatic System Restore point. -
Which two components are required to configure a TCP/IP connection? (Choose two.)
- Subnet mask
- DHCP address
- Host address
- Domain name
Explanation:
An IP address and a subnet mask. The IP address is the host address. -
You need to make a share hidden. Which symbol should you append to the share name?
- _
- !
- @
- #
- $
Explanation:
The “$” appended to the end of the share name means that it is a hidden share. Windows will not list such shares among those it defines in typical queries by remote clients to obtain the list of shares. One needs to know the name of an administrative share in order to access it. Not every hidden share is administrative share; in other words, ordinary hidden shares may be created at user’s discretion. -
What is required to create a volume mount point?
- A dynamic disk
- RAID 1 implementation
- An NTFS file system volume or partition
- Extended volumes
Explanation:
A volume mount point can be placed in any empty folder of the host NTFS volume. -
The purpose of the Information Technology Infrastructure Library is to provide a:
- Set of standards for networking protocols.
- Set of best practices for managing IT services.
- Downloadable library of hardware drivers.
- Technical library of Windows infrastructure services.
Explanation:
The Information Technology Infrastructure Library (ITIL) is a set of practices for IT service management (ITSM) that focuses on aligning IT services with the needs of business. -
To change the boot device order of a computer, you should use:
- Device Manager.
- Disk Management.
- BIOS settings.
- Computer Policy.
Explanation:
Example: Change the Boot Order in BIOS
Turn on or restart your computer and watch for a message during the POST about a particular key, usually Del or F2, that you’ll need to press to …enter SETUP. Press this key as soon as you see the message. -
Which two locations can a Windows Server be backed up to? (Choose two.)
- Network router
- Local drive
- Local DFS root share
- Remote share folder