220-1002 : CompTIA A+ Certification Exam: Core 2 : Part 04
220-1002 : CompTIA A+ Certification Exam: Core 2 : Part 04
-
Ann, a user, has purchased a new Android phone and is attempting to access a public hotspot. When she opens a browser, she gets a message indicating the page cannot be displayed. She notices there is a “?” in the radio icon in the toolbar. She has verified Bluetooth is active, airplane mode is off, and tethering is turned on. She uses the cell phone to call a technician for assistance.
Which of the following is the MOST likely issue Ann is experiencing?
- There is unauthenticated wireless connectivity
- She has exceeded the data allowance
- The phone is only 3G capable
- It is an unrooted phone
- The SIM card was not activated
- A data plan was not purchased
-
A junior Linux systems administrator needs to update system software.
Which of the following shell commands would allow the administrator to gain the necessary permissions to update the software?
- sudo
- chmod
- grep
- pwd
-
A small business has an open wireless network so vendors can connect to the network without logging in. The business owners are concerned that a nearby company is connecting and using the wireless connection without permission.
If the small business requires that the network remain open, which of the following configuration settings should be changed to address these concerns?
- Default SSID
- MAC filtering
- Power levels
- Content filtering
- Firewall
-
A user’s computer is displaying a black screen. The technician restarts the computer, but the OS still does not load. The technician discovers the OS was patched the previous evening.
Which of the following should the technician attempt NEXT?
- Reboot into safe mode and roll back the updates
- Repair the Windows Registry
- Configure boot options in the BIOS
- Disable Windows services and applications
-
A user’s mobile device appears to be losing battery life rapidly and often feels warm to the touch, even when it is put away. The device is relatively new, so the user is concerned it is defective. A technician inspects the device and sees the following:
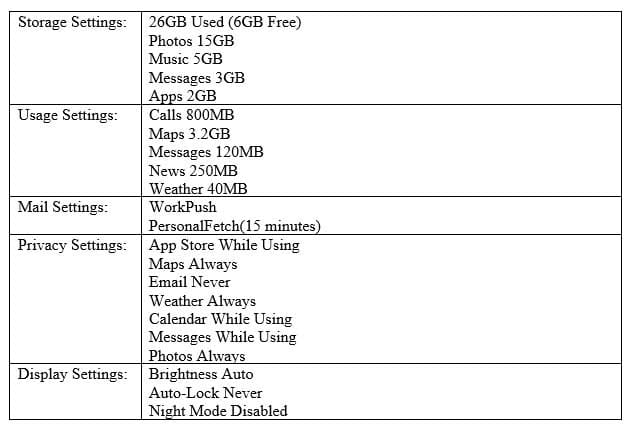
220-1002 Part 04 Q05 016 Which of the following should be changed to resolve this issue?
- Privacy – Maps
- Display – Brightness
- Storage – Photos
- Mail – Work
-
A Windows user is attempting to install a local printer and is unsuccessful based on permissions.
Which of the following user types BEST describes this user?
- Guest
- Power User
- Administrator
- Standard User
-
An end user is browsing the Internet when multiple browser pages open by themselves. The user notices the PC is running slowly, even while not browsing the Internet.
Which of the following actions should the user take?
- Update antivirus definitions
- Install anti-malware software
- Enable the pop-up blocker
- Reboot the PC
-
A desktop technician is attempting to upgrade several machines to Windows 10. After realizing there is only one disc for the installation, the technician decides to upgrade over the network.
Which of the following boot methods initiates such an upgrade?
- SSD
- Optical drive
- Flash drive
- PXE
-
A network administrator wants to plan a major OS upgrade of the router, which acts as a default gateway in an organization. The administrator has documented the purpose of the change, scoped the change, and completed a comprehensive risk analysis.
Which of the following is an important part of the change request process for which the administrator still must plan?
- Inform management regarding the anticipated amount of downtime
- Document a backout plan to roll back changes to the router
- Configure a redundant data path to eliminate downtime
- Make the downtime window larger than actually anticipated
-
A company brings in contractors several times a year to perform inventory, and the contractors use company-supplied laptops. The company’s security policy states that once the inventory is completed, the contractors should not be able to log in to the laptops until the next inventory.
Which of the following BEST enforces this policy?
- Delete the user accounts
- Disable the user accounts
- Restrict the user accounts
- Reset the user accounts
-
A wireless access point is going to be configured in a small office located in a crowded building.
Which of the following should the installation technician perform to increase the security of the wireless network? (Choose two.)
- Reduce the transmit power
- Reduce the channel availably
- Disable the DHCP server
- Enable QoS management
- Disable the SSID broadcast
- Implement WPA encryption
-
A technician is installing Windows 7 64-bit OS on a VM but keeps getting errors. The specifications for the machine are:
– Two 1GHz CPUs
– 2GB of memory
– 15GB hard drive
– 800 × 600 screen resolutionWhich of the following should the technician do to resolve the problem?
- Increase the number of CPUs
- Increase the amount of memory
- Increase the amount of hard drive space
- Increase the screen resolution
-
A technician is working on a user’s workstation and notices a lot of unknown processes running in the background. The user informs the technician that an application was recently downloaded from the Internet.
Which of the following types of infection does the user MOST likely have?
- Rootkit
- Keylogger
- Trojan
- Ransomware
-
Which of the following features has undergone the most significant changes from Windows 7 to Windows 10 and greatly simplified the operating system installation process?
- Driver detection
- Metro interface
- Account control
- PXE installation
-
Which of the following is considered government-regulated data?
- PHI
- End-user license agreement
- Digital Millennium Copyright Act
- DRM
-
A small business has an open WiFi network for employees but does not want customers to connect to the access point. A technician has been dispatched to address the business’s concerns.
Which of the following configuration settings should the technician change to satisfy the requirements of the business? (Choose two.)
- Default SSID
- MAC filtering
- NAT
- QoS
- Signal strength
- Encryption
-
A security team is auditing a company’s network logs and notices that a USB drive was previously inserted into several of the servers. Many login attempts were then successfully performed using common login information.
Which of the following actions should be taken to close the vulnerability? (Choose two.)
- Disable guest account
- Remove admin permissions
- Modify AutoRun settings
- Change default credentials
- Run OS security updates
- Install a software firewall
-
A technician is installing the latest OS on a user’s system. The user wants all of the settings and files to remain intact during the installation.
Which of the following upgrade methods should the technician use?
- network installation
- clean install
- in-place upgrade
- image deployment
-
A team needs to deploy a temporary server room at a site to provide support during construction.
Which of the following should they use at this site while setting up the server room?
- Air filters
- Privacy screens
- Vacuums
- ESD mats
-
A computer becomes infected with malware, which manages to steal all credentials stored on the PC. The malware then uses elevated credentials to infect all other PCs at the site. Management asks the IT staff to take action to prevent this from reoccurring.
Which of the following would BEST accomplish this goal?
- Use an antivirus product capable of performing heuristic analysis
- Use a host-based intrusion detection system on each computer
- Disallow the password caching of accounts in the administrators group
- Install a UTM in between PC endpoints to monitor for suspicious traffic
- Log all failed login attempts to the PCs and report them to a central server