220-1002 : CompTIA A+ Certification Exam: Core 2 : Part 10
220-1002 : CompTIA A+ Certification Exam: Core 2 : Part 10
-
Joe, an end user, just changed his network password. A pop-up box appears a few minutes later, prompting him to enter his password. Joe enters his new network password and is able to continue working. A few minutes later, the same pop-up box appears again, asking him to enter his network password.
Which of the following Control Panel utilities can Joe use to help with this situation?
- Credential Manager
- Network and Sharing Center
- Security and Maintenance
- Troubleshooting
-
A technician is working on a virtual server migration project. The technician has already completed the SOW; however, the servers will not work without a critical network configuration that was missed in the original SOW. The technician needs to make the adjustments quickly.
Which of the following best practice processes should the technician perform NEXT?
- Obtain end-user acceptance for the proposed changes and submit a change plan for additional work.
- Submit the changes to the change board for approval.
- Notify the change team of the changes needed and perform the changes.
- Escalate to stakeholders and obtain override approval for out-of-scope changes.
- Document the changes and perform the work.
-
Ann, an end user, is utilizing a stylus on her tablet. The recognition point is off when she uses the stylus, but it registers in the correct spot when she uses her finger.
Which of the following would be the BEST resolution to Ann’s issue?
- Restart the tablet.
- Disable and then reenable Bluetooth.
- Calibrate the touchscreen sensor.
- Disconnect and then reconnect the stylus.
-
Which of the following should be enacted to reduce a company’s liability and exposure to a potential lawsuit?
- Acceptable use policy
- Incident documentation policy
- Password compliance policy
- Change control policy
-
Joe, a user, notifies Ann, a technician, of a message that is displaying on his screen. The message has taken over the entire screen, and no icons are displayed. Joe, further explains that the message still appears after several reboot attempts. Upon further inspection of the affected PC, Ann notices a request for cryptocurrency payment to obtain the unlock key.
Which of the following is MOST likely the cause?
- Ransomware
- Cryptomining
- Rootkit
- Keylogger
-
A user receives an email on a company smartphone. When trying to open the email, the user gets a message stating the email is encrypted, and the user cannot open it. The user forwards the email to a personal email account and receives the same message. The user calls the IT department to ask for help. To decrypt the message, the technician tells the user to contact the sender of the message to be able to exchange:
- keys
- passwords
- root CA
- tokens
-
A Linux user reports that an application will not open and gives the error. Only one instance of the application may run at one time. A root administrator logs on to the device and opens a terminal. Which of the following pairs of tools will be needed to ensure no other instances of the software are currently running?
- pad and chmod
- sudo and vi
- ls and chown
- ps and kill
- cp and rm
-
A technician responds to a report that a user’s desktop is operating much slower after upgrading the Windows OS to the latest version. The technician notices responsiveness is erratic, and the symptoms are similar to a failing hard drive. The technician runs a full hardware diagnostic, and all systems pass. The technician checks the properties for each device in Device Manager and the hard disk and the standard AHCI 1.0 serial ATA controller both indicate the following message: This device is working properly. Which of the following should the technician attempt that will MOST likely resolve the performance issue?
- Roll back the OS upgrade. Continue using the older version of Windows
- Reset the PC to its factory conditions. Perform the OS upgrade again
- Update the SATA controller driver from the manufacturer’s website
- Perform a full backup and replace the hard drive
-
Every time a user manually runs an antivirus scan, the workstation becomes unresponsive, and the user has to reboot. A technician is dispatched and sees an antivirus pop-up in the system tray, indicating the computer is severely damaged, and a “click here” button to resolve it. There is a timer in the pop-up, counting down the time until the computer is no longer usable.
Which of the following should the technician do NEXT?
- Research the pop-up to see if it is a legitimate malware solution.
- Click on the pop-up window to resolve the issue before the time runs out.
- Send an email to all staff members warning them of malware on their system.
- Disconnect the Ethernet cable from the workstation and disable WiFi.
-
Which of the following NTFS security settings overrides all other settings?
- Deny
- Modify
- Read
- Write
-
A technician is investigating the cause of a Windows 7 PC running very slow. While reviewing Task Manager, the technician finds one process is using more than 90% of the CPU. Outbound network traffic on port 25 is very high, while inbound network traffic is low. Which of the following tasks should be done FIRST?
- Disconnect the network cable.
- Update the antivirus software.
- Run an antivirus scan.
- Shut down the PC.
-
A user is staying at a hotel that only offers Fast Ethernet connectivity to the network. The user’s laptop is currently using the corporate network for access to network resources as well as the cloud. Which of the following should the help desk recommend performing prior to using the hotel network?
- Add a country code exception to the firewall
- Unmap all network drives
- Change the proxy settings
- Enable Remote Assistance
-
An executive has contacted you through the help-desk chat support about an issue with a mobile device.
Assist the executive to help resolve the issue.
INSTRUCTIONS
Select the MOST appropriate statement for each response.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

220-1002 Part 10 Q13 018 Let’s take a look at your phone settings.
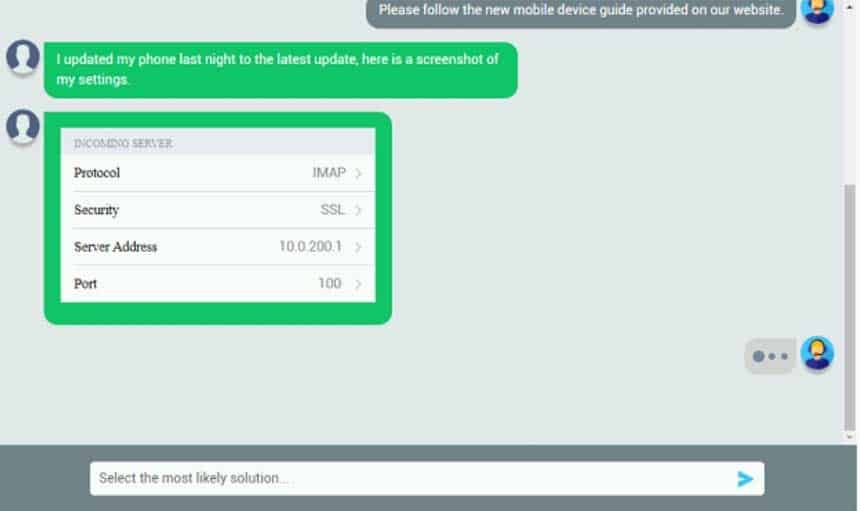
220-1002 Part 10 Q13 019 
220-1002 Part 10 Q13 020 Please change the port number on your mail settings to 993.
Which of the following should be done NEXT?
- Close the ticket out
- Educate the user on the solution that was performed
- Tell the user to take time to fix it themselves next time
- Send an email to Telecom to inform them of the issue and prevent reoccurrence
-
SIMULATION
A Windows 7 machine appears to have a failure. Every time it is rebooted, the message “BOOTMGR is missing” appears.
You have previously inserted a Windows 7 installation DVD into the DVD-ROM.
Please repair this failure without overwriting the customers’ local user profiles.
INSTRUCTIONS
Use the Windows recovery and repair utilities to remediate the issue.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

220-1002 Part 10 Q14 021 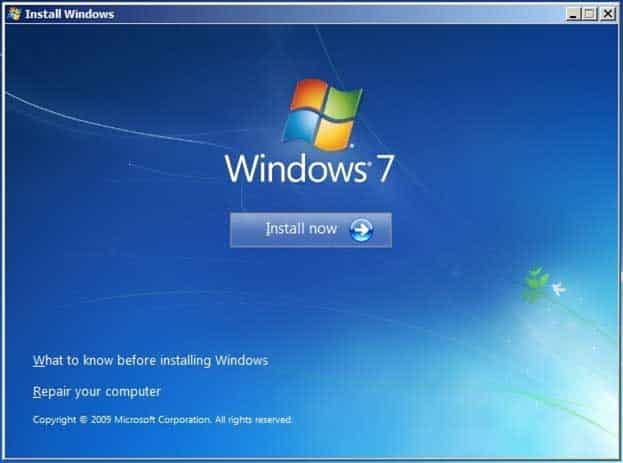
220-1002 Part 10 Q14 022 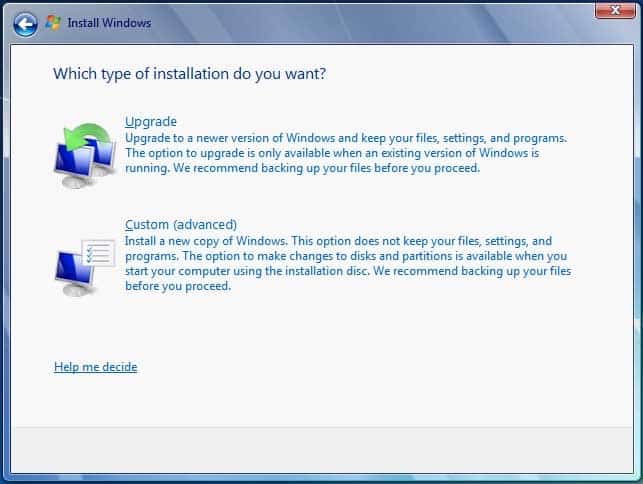
220-1002 Part 10 Q14 023 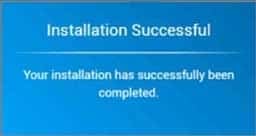
220-1002 Part 10 Q14 024 - Please see explanation.
Explanation:
Step 1: Choose Boot from Windows 7 DVD
Step 2: Click Install
Step 3: Choose Upgrade -
A user wants to see the workstations present on the LAN in a workgroup environment. Which of the following settings must be enabled to make this possible?
- Turn off public folder sharing
- Turn on network discovery
- Use 128-bit encryption
- Turn on file and folder sharing
-
The medical records department of a local hospital recently upgraded its computers. A technician needs to ensure the data stored on the hard drives is unrecoverable. Which of the following methods should the technician use to meet the requirement?
- Standard format
- Low-level format
- Overwrite
- Degauss
-
A large corporation wants to secure its wireless network so only employees can connect. Which of the following technologies should be used to control access by user account?
- RADIUS
- WPA2
- TKIP
- AES
-
A company needs to destroy several SSDs that contain sensitive information. Which of the following methods is BEST suited for the total destruction of the SSDs?
- Overwriting
- Formatting
- Incinerating
- Degaussing
-
Joe, a user, believes his computer is infected with malware. The device is having difficulty accessing some websites, and web services are not responding from any of the web browsers, although Joe can access these services from his smartphone without issue. The computer’s malware scanner has the latest definitions installed. Which of the following would BEST explain why the computer is functioning this way?
- Expired root certificate
- OS update failures
- Pop-up blocker
- Hijacked email
-
Which of the following is protected data that can be found in a medical record?
- PII
- PHI
- PCI
- SPI