CV1-003 : CompTIA Cloud+ : Part 05
CV1-003 : CompTIA Cloud+ : Part 05
-
An IaaS provider has numerous devices and services that are commissioned and decommissioned automatically on an ongoing basis. The cloud administrator needs to implement a solution that will help reduce administrative overhead.
Which of the following will accomplish this task?
- IPAM
- NAC
- NTP
- DNS
-
A systems administrator needs to configure an email client to ensure data integrity of the email messages.
Which of the following provides the BEST mechanism to achieve this goal?
- Cyclic redundancy check
- SHA-1 hashes
- SHA-256 hashes
- Digital signature
-
A systems administrator is troubleshooting network throughput issues following a deployment. The network is currently being overwhelmed by the amount of traffic between the database and the web servers in the environment.
Which of the following should the administrator do to resolve this issue?
- Set up affinity rules to keep web and database servers on the same hypervisor
- Enable jumbo frames on the gateway
- Move the web and database servers onto the same VXLAN
- Move the servers onto thick-provisioned storage
-
Which of the following strategies will mitigate the risk of a zero-day vulnerability MOST efficiently?
- Using only open-source technologies
- Keeping all resources up to date
- Creating a standby environment with a different cloud provider
- Having a detailed incident response plan
-
A systems administrator wants the VMs on the hypervisor to share CPU resources on the same core when feasible.
Which of the following will BEST achieve this goal?
- Configure CPU passthrough
- Oversubscribe CPU resources
- Switch from a Type 1 to a Type 2 hypervisor
- Increase instructions per cycle
- Enable simultaneous multithreading
-
An organization is hosting a DNS domain with private and public IP ranges.
Which of the following should be implemented to achieve ease of management?
- Network peering
- A CDN solution
- A SDN solution
- An IPAM solution
-
A systems administrator is creating a playbook to run tasks against a server on a set schedule.
Which of the following authentication techniques should the systems administrator use within the playbook?
A cloud administrator recently deployed an update to the network drivers of several servers. Following the update, one of the servers no longer responds to remote login requests. The cloud administrator investigates the issue and gathers the following information:
– The cloud management console shows the VM is running and the CPU and memory utilization is at or near 0%.
– The cloud management console does not show an IP address for that server.
– A DNS lookup shows the hostname resolves to an IP address.
– The server is a member of the same security group as the others.
– The cloud administrator is able to log in remotely to the other servers without issue.Which of the following is the MOST likely cause of the server being unavailable?
- The network driver updates did not apply successfully, and the interface is in a down state.
- The ACL policy for the server was updated as part of the server reboot, preventing login access.
- The server was assigned a new IP address, and DNS entry for the server name was not updated.
- The update caused an increase in the output to the logs, and the server is too busy to respond.
-
A systems administrator in a large enterprise needs to alter the configuration of one of the finance department’s database servers.
Which of the following should the administrator perform FIRST?
- Capacity planning
- Change management
- Backups
- Patching
-
A SaaS provider wants to maintain maximum availability for its service.
Which of the following should be implemented to attain the maximum SLA?
- A hot site
- An active-active site
- A warm site
- A cold site
-
An SQL injection vulnerability was reported on a web application, and the cloud platform team needs to mitigate the vulnerability while it is corrected by the development team.
Which of the following controls will BEST mitigate the risk of exploitation?
- DLP
- HIDS
- NAC
- WAF
-
A cloud architect wants to minimize the risk of having systems administrators in an IaaS compute instance perform application code changes. The development group should be the only group allowed to modify files in the directory.
Which of the following will accomplish the desired objective?
- Remove the file write permissions for the application service account.
- Restrict the file write permissions to the development group only.
- Add access to the fileshare for the systems administrator’s group.
- Deny access to all development user accounts
-
A technician is working with an American company that is using cloud services to provide video-based training for its customers. Recently, due to a surge in demand, customers in Europe are experiencing latency.
Which of the following services should the technician deploy to eliminate the latency issue?
- Auto-scaling
- Cloud bursting
- A content delivery network
- A new cloud provider
-
A web server has been deployed in a public IaaS provider and has been assigned the public IP address of 72.135.10.100. Users are now reporting that when they browse to the website, they receive a message indicating the service is unavailable. The cloud administrator logs into the server, runs a netstat command, and notices the following relevant output:
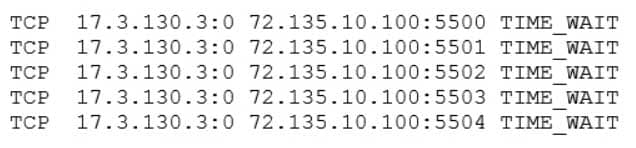
CV1-003 Part 05 Q13 017 Which of the following actions should the cloud administrator take to resolve the issue?
- Assign a new IP address of 192.168.100.10 to the web server
- Modify the firewall on 72.135.10.100 to allow only UDP
- Configure the WAF to filter requests from 17.3.130.3
- Update the gateway on the web server to use 72.135.10.1
-
The security team for a large corporation is investigating a data breach. The team members are all trying to do the same tasks but are interfering with each other’s work.
Which of the following did the team MOST likely forget to implement?
- Incident type categories
- A calling tree
- Change management
- Roles and responsibilities
-
A systems administrator is deploying a solution that requires a virtual network in a private cloud environment. The solution design requires the virtual network to transport multiple payload types.
Which of the following network virtualization options would BEST satisfy the requirement?
- VXLAN
- STT
- NVGRE
- GENEVE
-
A systems administrator is troubleshooting performance issues with a Windows VDI environment. Users have reported that VDI performance is very slow at the start of the work day, but the performance is fine during the rest of the day.
Which of the following is the MOST likely cause of the issue?
- Disk I/O limits
- Affinity rule
- CPU oversubscription
- RAM usage
-
Lateral-moving malware has infected the server infrastructure.
Which of the following network changes would MOST effectively prevent lateral movement in the future?
- Implement DNSSEC in all DNS servers
- Segment the physical network using a VLAN
- Implement microsegmentation on the network
- Implement 802.1X in the network infrastructure
-
An IaaS application has a two-hour RTO and a four-hour RPO. The application takes one hour to back up its data or restore from a local backup file. A systems administrator is tasked with configuring the backup policy.
Which of the following should the administrator configure to achieve the application requirements with the LEAST cost?
- Back up to long-term storage every night
- Back up to object storage every three hours
- Back up to long-term storage every four hours
- Back up to object storage every hour
-
A systems administrator needs to convert ten physical servers to virtual.
Which of the following would be the MOST efficient conversion method for the administrator to use?
- Rebuild the servers from scratch
- Use the vendor’s conversion tool
- Clone the hard drive
- Restore from backup
-
Which of the following cloud services is fully managed?
- IaaS
- GPU in the cloud
- IoT
- Serverless compute
- SaaS