XK0-004 : CompTIA Linux+ : Part 04
XK0-004 : CompTIA Linux+ : Part 04
-
In order to comply with new security policies, an administrator needs to prevent the SSH server from using insecure algorithms.
Which of the following files should be edited to accomplish this?
- /etc/ssh/sshd_config
- /etc/ssh/ssh_config
- ~/.ssh/ssh_config
- /etc/ssh/known_hosts
-
Which of the following configuration files should be modified to disable Ctrl+Alt+Del in Linux?
- /etc/inittab
- ~/.bash_profile
- /etc/securetty
- /etc/security/limits.conf
-
Joe, a user, is unable to log in to the server and contracts the systems administrator to look into the issue. The administrator examines the /etc/passwd file and discovers the following entry:
joe:x:505:505::/home/joe:/bin/false
Which of the following commands should the administrator execute to resolve the problem?
- usermod –s /bin/bash joe
- passwd –u joe
- useradd –s /bin/bash joe
- chage –E -1 joe
-
A server is almost out of free memory and is becoming unresponsive. Which of the following sets of commands will BEST mitigate the issue?
- free, fack, partprobe
- lsof, lvcreate, mdadm
- df, du, rmmod
- fdisk, mkswap, swapon -a
-
A Linux administrator is using a public cloud provider to host servers for a company’s website. Using the provider’s tools, the administrator wrote a JSON file to define how to deploy the servers. Which of the following techniques did the administrator use?
- Infrastructure as code
- Build automation
- Platform as a service
- Automated configuration
-
A Linux system is running normally when the systems administrator receives an alert that one application spawned many processes. The application is consuming a lot of memory, and it will soon cause the machine to become unresponsive. Which of the following commands will stop each application process?
- kill `pidof application`
- killall application
- kill -9 `ps –aux | grep application`
- pkill -9 application
-
A systems administrator configured a new kernel module, but it stopped working after reboot. Which of the following will allow the systems administrator to check for module problems during server startup?
- lsmod
- modprobe
- modinfo
- dmesg
-
A junior Linux administrator is installing patches using YUM. The administrator issues the following command:
yum list installed
The output of the command is as follows:
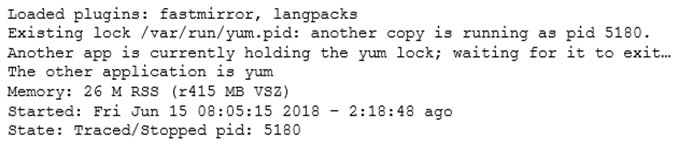
XK0-004 Part 04 Q08 025 Given this scenario and the output, which of the following should the administrator do to address this issue?
- renice –n 9 –p 5180
- killall yum
- ps –ef | grep yum
- top | grep yum
-
A systems administrator needs to retrieve specific fields from a CSV file. Which of the following tools would accomplish this task?
- awk
- sort
- echo
-
Two specific users need access to a directory owned by root where backups are located. Which of the following commands would BEST ensure the specified users can access the backup files?
- umask
- chcon
- chmod
- setfacl
-
Which of the following is the purpose of the monitoring server role?
- To aggregate web traffic to watch which websites employees are visiting
- To collect status and performance information about the servers in an environment
- To provide user authentication services to a network
- To provide real-time analysis of potential threats to the organization
-
A junior administrator is migrating a virtual machine from a Type 1 hypervisor to a Type 2 hypervisor. To ensure portability, which of the following formats should the administrator export from the Type 1 hypervisor to ensure compatibility?
- OWASP
- VDI
- VMDK
- OVA
-
A junior systems administrator is upgrading a package that was installed on a Red Hat-based system. The administrator is tasked with the following:
Update and install the new package.
Verify the new package version is installed.Which of the following should be done to BEST accomplish these task? (Choose two.)
- yum install <package name>
- yum upgrade
- rpm –e <package name>
- rpm –qa
- apt-get <package name>
- apt-get upgrade
-
Which of the following is the template for the grub.cfg file?
- /etc/default/grub
- /etc/grub2.cfg
- /etc/sysct1.conf
- /boot/efi
-
A Linux administrator implemented a new HTTP server using the default configuration. None of the users on the network can access the server. If there is no problem on the network or with the users’ workstations, which of the following steps will BEST analyze and resolve the issue?
- Run netstat to ensure the port is correctly bound, and configure the firewall to allow access on ports 80 and 443
- Run route to ensure the port is correctly bound, and configure the firewall to allow access on ports 80 and 443
- Run netcat to ensure the port is correctly bound, and configure a static route to the web to allow access on ports 80 and 443
- Run route to ensure the port is correctly bound, and configure SELinux to allow access on ports 80 and 443
-
A Linux storage administrator wants to create a logical volume group. Which of the following commands is required to start the process?
- pvcreate
- vgcreate
- lvcreate
- mkfs.xfs
-
A Linux administrator built a GitLab server. Later that day, a software engineer tried to access the server to upload the repository during the final step of installation. The software engineer could not access the website. Which of the following firewall rules would allow access to this site?
- iptables –A INPUT –p tcp –m multiport –dports 80,443 –m conntrack –cstate NEW, ESTABLISHED –j ACCEPT
- iptables –A INPUT –p tcp –m multiport –dports 80,443 –m conntrack –cstate ESTABLISHED –j ACCEPT
- iptables –A INPUT –p tcp –m multiport –dports 80,443 –m conntrack –cstate RELATED, ESTABLISHED –j ACCEPT
- iptables –A INPUT –p tcp –m multiport –dports 80,443 –m conntrack –cstate NEW, ESTABLISHED –j REJECT
-
While creating a file on a volume, the Linux administrator receives the following message: No space left on device. Running the df –m command, the administrator notes there is still 50% of usage left. Which of the following is the NEXT step the administrator should take to analyze the issue without losing data?
- Run the df –i command and notice the inode exhaustion
- Run the df –h command and notice the space exhaustion
- Run the df –B command and notice the block size
- Run the df –k command and notice the storage exhaustion
-
A user attempts to use the mount -a command but gets the following error:
mount: mount point /mnt/test does not exist
Which of the following commands best describes the action the Linux administrator should take NEXT?
- mount –a /mnt/test
- mkdir –p /mnt/test
- mdadm –p /mnt/test
- mkfs /mnt/test
- touch /mnt/test
-
Which of the following is modified to reconfigure the boot environment?
- grub-mkconfig
- grub.cfg
- update-grub
- grub2-mkconfig