XK0-004 : CompTIA Linux+ : Part 02
-
An administrator is analyzing a Linux server which was recently hacked.
Which of the following will the administrator use to find all unsuccessful login attempts?
- nsswitch
- faillock
- pam_tally2
- passwd
-
A junior administrator needs to unload an older video kernel module.
Which of the following commands would BEST accomplish this task?
- modprobe
- insmod
- rmmod
- chmod
-
An administrator is attempting to block SSH connections to 192.168.10.24 using the Linux firewall. After implementing a rule, a connection refused error is displayed when attempting to SSH to 192.168.10.24.
Which of the following rules was MOST likely implemented?
- iptables –A –p tcp –d 192.168.10.24 –-dport 22 –j REJECT
- iptables –A –p tcp –d 192.168.10.24 –-dport 22 –j DROP
- iptables –A –p tcp –d 192.168.10.24 –-dport 22 –j FORWARD
- iptables –A –p tcp –d 192.168.10.24 –-dport 22 –j REFUSE
-
A junior Linux administrator is setting up system-wide configuration settings. The goal is to ensure the PATH environment variable includes the following locations for all users who log into a Linux system:
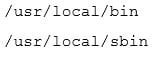
XK0-004 Part 02 Q05 012 The administrator issues the following commands at the terminal:

XK0-004 Part 02 Q05 013 Respectively, the output of these commands is as follows:
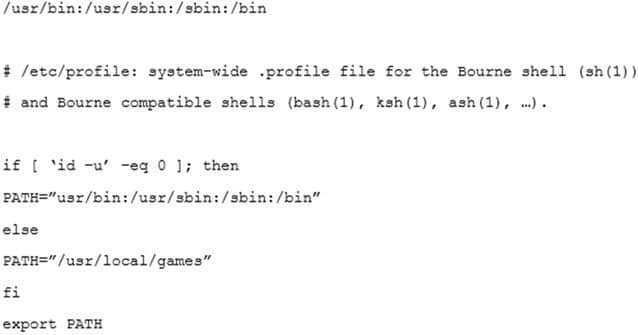
XK0-004 Part 02 Q05 014 Given this output, which of the following would be the BEST action for the administrator to perform to address this issue?
- Update the /etc/profile.d file using a text editor, navigate to the PATH element, add the missing locations, and run the bash_completion.sh script to update the changes.
- Update the /etc/profile file using a text editor, navigate to the PATH element, add the missing locations and run the . /etc/profile command to update the changes.
- Update the /etc/profile.d file using a text editor, navigate to the PATH element, add the missing locations, and reboot to update the changes.
- Update the /etc/profile file using a text editor navigate to the PATH element, add the missing locations, and restart the bash process to update the changes.
-
A Linux systems administrator needs to provision multiple web servers into separate regional datacenters. The systems architect has instructed the administrator to define the server infrastructure using a specific tool that consumes a text-based file.
Which of the following is the BEST reason to do this?
- To document the infrastructure so it can be included in the system security plan
- To ensure the administrator follows the planning phase of the systems development life cycle
- To define the infrastructure so it can be provisioned consistently with minimal manual tasks
- To validate user requirements have been met within each regional datacenter for compliance
-
A Linux administrator needs to set permissions on an application with the following parameters:
The owner of the application should be able to read, write, and execute the application.
Members of the group should be able to read and execute the application.
Everyone else should not have access to the application.Which of the following commands would BEST accomplish these tasks?
- chmod 710 <application name>
- chmod 730 <application name>
- chmod 750 <application name>
- chmod 760 <application name>
-
A junior Linux administrator is trying to verify connectivity to the remote host host1 and display round-trip statistics for ten ICMP requests.
Which of the following commands should the administrator execute?
- ping –c 10 host1
- traceroute –c 10 host1
- netstat host1
- pathping –c 10 host1
-
A junior Linux administrator is updating local name resolution to support IPv6. The administrator issues the command cat /etc/hosts and receives the following output:
127.0.0.1 localhostWhich of the following actions should the administrator perform to accomplish this task?
- Modify the /etc/hosts file, and add the ipv6 localhost entry to the file.
- Modify the /etc/hosts file, and add the ::1 localhost entry to the file.
- Modify the /etc/hosts file, and add the ipv4 localhost entry to the file.
- Modify the /etc/hosts file, and add the 0.0.0.0 localhost entry to the file.
-
A Linux systems administrator needs to copy the contents of a directory named “working” on the local working system to a folder /var/www/html on a server named “corporate-web”.
Which of the following commands will allow the administrator to copy all the contents to the web server?
- scp –r working/* webuser@corporate-web:/var/www/html
- tar working/* webuser@corporate-web:/var/www/html
- cp –r working/* webuser@corporate-web:/var/www/html
- mv working webuser@corporate-web:/var/www/html
-
A systems administrator has received reports of intermittent network connectivity to a particular website. Which of the following is the BEST command to use to characterize the location and type of failure over the course of several minutes?
- mtr www.comptia.org
- tracert www.comptia.org
- ping www.comptia.org
- netstat www.comptia.org
-
A Linux administrator has configured a Linux system to be used as a router. The administrator confirms that two network adapters are properly installed and functioning correctly. In addition, the output of the iptables –L command appears to contain a complete firewall configuration.
Which of the following commands does the administrator need to issue for the router to be fully functional?
- echo “1” > /proc/sys/net/ipv4/ip_forward
- echo “0” > /proc/sys/net/ipv4/tcp_abort_on_overflow
- echo “0” > /proc/sys/net/ipv4/max_connections
- echo “1” > /proc/sys/net/ipv4/ip_default_ttl
-
A systems administration team has decided to treat their systems as immutable instances. They keep the desired state of each of their systems in version control and apply automation whenever they provision a new instance. If there is an issue with one of their servers, instead of troubleshooting the issue, they terminate the instance and rebuild it using automation.
Which of the following is this an example of?
- Inventory
- Orchestration
- Infrastructure as code
- Agentless deployment
-
A systems administrator wants to deploy several applications to the same server quickly. Each application should be abstracted from the host with its own dependencies and libraries and utilize a minimal footprint.
Which of the following would be BEST in this scenario?
- Virtual machines
- Type 2 hypervisor
- Chroot jails
- Containers
-
An operator finds a user is having issues with opening certain files.
Which of the following commands would allow the security administrator to list and check the SELinux context?
- ls –D
- ls –a
- ls –Z
- ls -1
-
A new corporate policy states that Bluetooth should be disabled on all company laptops. Which of the following commands would disable the use of Bluetooth?
- echo “blacklist bluetooth” > /etc/modprobe.d/blacklist-bluetooth
- echo “kill bluetooth” > /etc/modprobe.d/kill-bluetooth
- echo “modprobe bluetooth” > /etc/modprobe.d/modporbe-bluetooth
- echo “rmmod bluetooth” > /etc/modprobe.d/rmmod-bluetooth
-
A junior Linux administrator is installing a new application with CPU architecture requirements that have the following specifications:
x64 bit
3.0GHz speed
Minimum quad coreThe administrator wants to leverage existing equipment but is unsure whether the requirements of these systems are adequate. The administrator issues the following command cat /proc/cpuinfo. The output of the command is as follows:
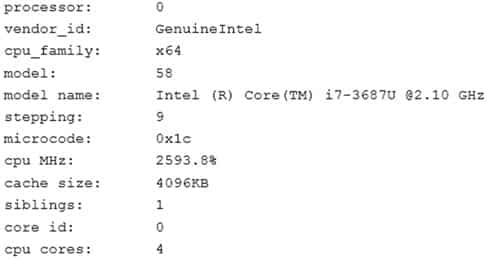
XK0-004 Part 02 Q16 015 Which of the following is the recommended course of action the administrator should take based on this output?
- Install the application, as the system meets the application requirements
- Procure new equipment that matches the recommended specifications
- Recompile the Linux kernel to support the installation.
- Reconfigure lib modules to support the new application.
-
A Linux systems administrator wants the ability to access systems remotely over SSH using RSA authentication. To which of the following files should the RSA token be added to allow this access?
- authorized_keys
- ~/.ssh/ssh_config
- id_rsa.pub
- known_hosts
-
A Linux server needs to be accessed, but the root password is not available.
Which of the following would BEST allow an administrator to regain access and set a new known password at the same time?
- Boot into single-user mode and reset the password via the passwd command.
- Boot into single-user mode and reset the password by editing the /etc/passwd file.
- Boot into single-user mode and reset the password by editing the /etc/shadow file.
- Boot into single-user mode and reset the password via the chage command.
-
A Linux administrator wants to fetch a Git repository from a remote Git server.
Which of the following is the BEST command to perform this task?
- git checkout
- git clone
- git merge
- git config
-
An administrator needs to create a shared directory in which all users are able to read, write, and execute its content but none of the regular users are able to delete any content.
Which of the following permissions should be applied to this shared directory?
- rwxrwxrwt
- rwxrwxrws
- rwxrwxrwx
- rwxrwxrw*
Subscribe
0 Comments
Newest