XK0-004 : CompTIA Linux+ : Part 11
-
A systems administrator is implementing disk quotas on /home. During the process, the administrator receives the following error:
Cannot find filesystem to check or filesystem not mounted with user quota option.
Which of the following is the correct order of steps the administrator should follow to resolve this error?
- 1. Verify if /home has quotas enabled in /etc/fstab and, if not, enable it.
2. Remount /home.
3. Create the quota database files and generate the disk usage table.
4. Assign user quota policies. - 1. Create the quota database files and generate the disk usage table.
2. Verify if /home has quotas enabled in /etc/fstab and, if not, enable it.
3. Remount /home.
4. Assign user quota policies. - 1. Verify if /home has quotas enabled in /etc/fstab and, if not, enable it.
2. Create the quota database files and generate the disk usage table.
3. Remount /home.
4. Assign user quota policies. - 1. Assign user quota policies.
2. Verify if /home has quotas enabled in /etc/fstab and, if not, enable it.
3. Create the quota database files and generate the disk usage table.
4. Remount /home.
- 1. Verify if /home has quotas enabled in /etc/fstab and, if not, enable it.
-
A Linux user wants to give read-only permissions to a directory and its contents. Which of the following commands will allow the user to accomplish this task?
- chmod –R 400 /new_directory/
- chmod –R 600 /new_directory/
- chmod 400 /new_directory/
- chmod 600 /new_directory/
-
A Linux administrator needs to remove a USB drive from a system. The unmount command fails, stating the device is busy. Which of the following commands will show the reason for this error?
- lsusb | grep /mnt/usb
- mount | grep /mnt/usb
- ps aux | grep /mnt/usb
- lsof | grep /mnt/usb
-
A Linux systems administrator is troubleshooting an issue with the /home directory running out of space. The administrator needs to determine which /home directories are using the most space. Which of the following commands should be used?
- du
- lvs
- df
- fsck
-
An administrator needs a bootable USB for installing a new Linux machine. The administrator downloaded the image file and named it as Linux_OS.iso in the /tmp directory. Which of the following commands will accomplish that task?
- dd input=/tmp/Linux_OS.iso of=/dev/sda bs=512
- dd in=/tmp/Linux_OS.iso out=/dev/sdb bs=512
- dd if=/tmp/Linux_OS.iso of=/dev/sda bs=512
- dd if=/tmp/Linux_OS.iso out=/dev/sdb1 bs=512
-
A junior Linux administrator needs to create 16 empty files quickly that will contain sales information for each quarter for the past four years. Which of the following commands will meet this requirement?
- touch {2015,2016,2017,2018}.{q1,q2,q3,q4}
- touch [2015,2016,2017,2018].[q1,q2,q3,q4]
- touch ‘2015,2016,2017,2018‘.‘q1,q2,q3,q4‘
- touch {2015.2016.2017.2018}.{q1.q2.q3.q4}
-
An administrator needs to change the DNS domain search order of a single Linux host to localize it better. Which of the following files should the administrator edit?
- /etc/resolv.conf
- /etc/hosts
- /etc/nsswitch.conf
- /etc/dhcpd.conf
-
A user issues the following command:
ls –l /var/log | egrep –e ‘^d[rwx]{3}.*[rw-]{3}.*’
The list of files in the system is shown below:
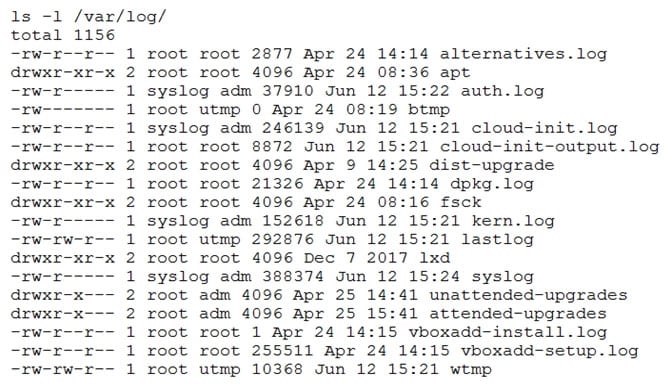
XK0-004 Part 11 Q08 059 Which of the following results matches the command issued?
- drwxr-x— 2 root adm 4096 Apr 25 14:41 unattended-upgrades
drwxr-x— 2 root adm 4096 Apr 25 15:41 attended-upgrades - drwxr-xr-x 2 root root 4096 Apr 24 08:36 apt
drwxr-xr-x 2 root root 4096 Apr 9 14:25 dist-upgrade
drwxr-x— 2 root adm 4096 Apr 25 14:41 unattended-upgrades - drwxr-xr-x 2 root root 4096 Apr 24 08:36 apt
drwxr-xr-x 2 root root 4096 Apr 9 14:25 dist-upgrade
drwxr-x— 2 root adm 4096 Apr 25 15:41 attended-upgrades - -rw-r–r– 1 root root 2877 Apr 24 14:14 alternatives.log
-rw-r–r– 1 syslog adm 246139 Jun 12 15:21 cloud-init.log
-rw-r–r– 1 root root 8872 Jun 12 15:21 cloud-init-output.log
- drwxr-x— 2 root adm 4096 Apr 25 14:41 unattended-upgrades
-
Which of the following BEST describes build automation?
- Automating the creation of software and related processes
- Automatically categorizing servers in the infrastructure
- Managing and provisioning servers via automatic templates
- Managing and provisioning servers via automatic templates
-
A Linux administrator needs to configure a new firewall without an existing ACL to allow incoming web traffic. The firewall must log the allowed network traffic. Which of the following command sequences would accomplish this task when they are executed in order?
- iptables –A INPUT –p tcp –dport 80 –J LOG
iptables –A INPUT –p tcp –dport 443 –J LOG
iptables –I INPUT –p tcp –dport 80 –J ACCEPT
iptables –I INPUT –p tcp –dport 443 –J ACCEPT - iptables –I INPUT –m multiport –p tcp –dports 80,443 –J LOG
iptables –I INPUT –m multiport –p tcp –dports 80,443 –J ACCEPT - iptables –A INPUT –m multiport –p tcp –dports 80,443 –J LOG
iptables –A INPUT –m multiport –p tcp –dports 80,443 –J ACCEPT - iptables –A INPUT –p tcp –dport 80 –J ACCEPT
iptables –A INPUT –p tcp –dport 443 –J ACCEPT
iptables –A INPUT –p tcp –dport 80 –J LOG
iptables –A INPUT –p tcp –dport 443 –J LOG
- iptables –A INPUT –p tcp –dport 80 –J LOG
-
An organization wants to consolidate its entire user information in centralized storage using an X.500-based protocol. Which of the following protocols should be used for this implementation?
- RADIUS
- LDAP
- DNS
- DHCP
-
An administrator needs to kill the oldest Bash shell running in the system. Which of the following commands should be issued to accomplish this task?
- ps axjf | grep bash to obtain PID
kill -9 PID - ps –eo pid,etime,cmd | grep bash (to obtain PID)
kill -9 PID - ps –eo pid,etime| grep bash (to obtain PID)
killall -9 PID - killall -15 -o bash
- ps axjf | grep bash to obtain PID
-
Due to security policies, a restriction was implemented that forbids direct access to the database server. The junior administrator needs to connect using SSH tunneling. Which of the following commands allows the junior administrator to connect from a desktop?
- ssh –L dbserver.local:5432:localhost:95432 [email protected]
- ssh –L 5432:localhost dbserver.local:5432 postgres
- ssh –L 95432:localhost [email protected]
- ssh –L 9432:localhost:5432 [email protected]
-
Which of the following boot methods can a Linux administrator use to boot a Linux server remotely via a network interface card instead of a local disk?
- NTP
- PXE
- NFS
- Kickstart
-
A user requested a USB serial device to be added to a desktop computer. The device has built-in kernel driver support. The administrator tested the device installation and access, but the user cannot access the serial port. Each time the user attempts to access the device, an error log is created that shows the user does not have permission to use the serial port. Which of the following will add a user to the group that has serial port capabilities?
- usermod –a –G serialport $USER
- usermod –a –G modem $USER
- usermod –a –G dialout $USER
- usermod –a –G root $USER
-
A system ran out of storage space on a particular mount and will not allow anything to be written to disk. The df command shows there are 6GB free on the mount, and there is no inode exhaustion. This issue has happened before due to a known large log file that was not being rotated. The administrator remembers the file name but cannot remember the location of the log file or which process is writing to it. Which of the following would be the BEST solution to correct this issue while maintaining availability?
- Use the lsof command to find where the large log file is located and truncate it
- Use the locate command to find where the large log file is located and delete it
- Use the du command to find where the large log file is located and delete it
- Use the ps command to find which process is writing to the log file, and then kill and restart the process
-
A Linux administrator suspects unauthorized users are attempting to log in to the Linux server remotely. Which of the following should the administrator check FIRST?
- /var/log/messages
- /var/log/secure
- /var/log/dmesg
- /var/log/kern.log
-
A junior systems administrator is diagnosing an issue with latency. The administrator issues the command mtr www.comptia.org at a terminal and receives the following output:
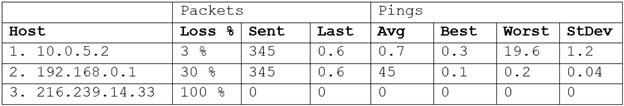
XK0-004 Part 11 Q18 060 Given this scenario and the output, which of the following should be reported to the network team for investigation? (Choose two.)
- Host 1 is set to filter ICMP reply packets.
- Host 1 is set to filter ICMP echo packets.
- Host 2 is experiencing high packet loss, indicating the link is overloaded.
- Host 2 is experiencing low bandwidth, indicating the ISP is blocking traffic.
- Host 3 is set to filter ICMP reply packets.
- Host 3 is set to filter ICMP echo packets.
-
A user receives an access_denied error when trying to modify a file, even though the file permissions are set to 777. Which of the following commands should be used to view additional file permissions?
- getsebool
- getenforce
- ls -z
- ps -z
-
A Linux administrator receives a call from the network operations team that one of the database applications is down on a Linux server. The Linux server is configured with RAID 1 for redundancy, and the array /dev/md0 consists of two devices called /dev/sda1 and /dev/sdb1. After looking at the status of the RAID 1 array in the /proc/mdstat file, the administrator discovers the RAID 1 array is degraded and the disk /dev/sdb1 on which the database application was installed appears to have failed.

XK0-004 Part 11 Q20 061 Which of the following steps should the administrator take to remove the device /dev/sdb1 from the RAID array md0? (Choose two.)
- mdadm /dev/md0 –remove /dev/sdb1
- mdadm /dev/sdb1 –fail /dev/md0
- mdadm /dev/md0 –fail /dev/sdb1
- mdadm /dev/sdb1 –remove /dev/md0
- racadm –remove /dev/sdb1
- racadm –fail /dev/sdb1
Subscribe
0 Comments
Newest