XK0-004 : CompTIA Linux+ : Part 07
XK0-004 : CompTIA Linux+ : Part 07
-
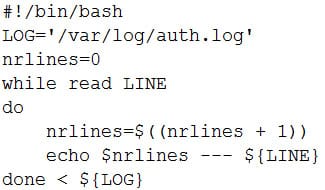
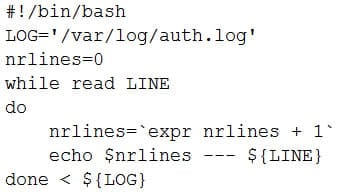
A user wants to list the lines of a log, adding a correlative number at the beginning of each line separated by a set of dashes from the actual message. Which of the following scripts will complete this task?
-
An analyst is trying to determine which public IP addresses are managed by Company A, but the script is not working correctly.
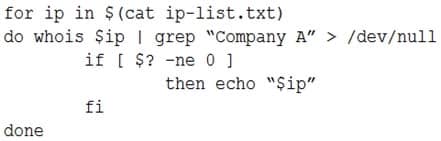
XK0-004 Part 07 Q02 042 Which of the following explains what is wrong with the script?
- $(cat ip-list.txt) should be changed to `cat ip-list.txt` in the for statement.
- The for should be changed to while in the loop.
- The > should be changed to 2> in the do statement.
- The -ne flag should be changed to -eq in the if statement.
-
All users are reporting that they cannot connect to the SFTP server. The administrator runs a scan:
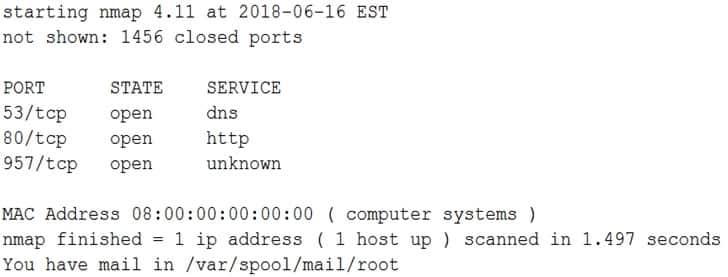
XK0-004 Part 07 Q03 043 Which of the following would allow the administrator to fix the problem?
- Allow SFTP connections on port 22 using /etc/sysconfig/iptables.
- Allow SFTP connections on port 20 and 21 using /etc/sysconfig/iptables.
- Allow SFTP connections on port 25 using /etc/sysconfig/iptables.
- Allow SFTP connections on port 1456 using /etc/sysconfig/iptables.
-
A Linux systems administrator installed a new web server, which failed while attempting to start. The administrator suspects that SELinux is causing an issue and wants to temporarily put the system into permissive mode. Which of the following would allow the administrator to accomplish this?
- echo SELINUX=PERMISSIVE >> /etc/sysconfig/selinux
- setenforce 0
- sestatus 0
- chcon httpd_sys_content_t /var/
-
A configuration management tool running every minute is enforcing the service HTTPd to be started. To perform maintenance, which of the following series of commands can be used to prevent the service from being started?
- systemctl stop httpd && systemctl mask httpd
- systemctl disable httpd && systemctl mask httpd
- systemctl stop httpd && systemctl hide httpd
- systemctl disable httpd && systemctl hide httpd
-
An administrator has written the following Bash script:
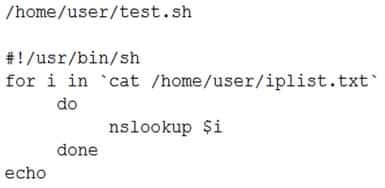
XK0-004 Part 07 Q06 044 All necessary files exist in the correct locations. However, when the administrator executes /home/user/test.sh the following error is received:
No such file or directory
Which of the following is the MOST likely cause of the error?
- The shebang points to the wrong path.
- The script is not executable.
- The formatting of the file is incorrect.
- Nslookup is not installed.
-
An administrator is troubleshooting an application that has failed to start after the server was rebooted. Noticing the data volume is not mounted, the administrator attempts to mount it and receives this error:
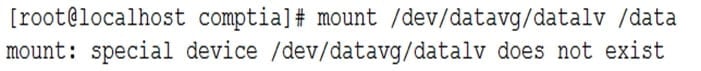
XK0-004 Part 07 Q07 045 Upon checking the logical volume status, the administrator receives this information:
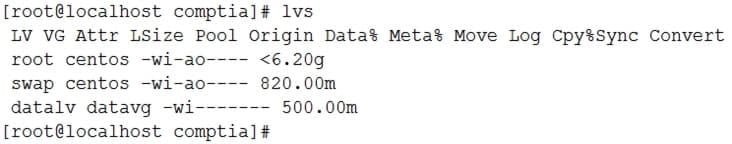
XK0-004 Part 07 Q07 046 Which of the following can be said about the data logical volume, and how can this problem be resolved?
- The logical volume is not active. The administrator should make it active with lvchange -ay /dev/datavg/datalv and then mount it.
- The logical volume file system has become corrupted. The administrator should repair it with xfs_repair /dev/datavg/datalv and then mount it.
- The logical volume is OK but the /dev special files are missing. The administrator should recreate them by running /dev/MAKEDEV.
- The file system is read-only. The administrator should remount it as read-write with the command mount -o remount.rw /data.
-
A four-drive Linux NAS has been improperly configured. Each drive has a capacity of 6TB, for a total storage capacity of 24TB. To reconfigure this unit to be not pluggable for drive replacement and provide total storage of 11TB to 12TB, which of the following would be the correct RAID configuration?
- RAID 01
- RAID 03
- RAID 10
- RAID 50
-
A systems administrator suspects a process with a PID of 2864 is consuming resources at an alarming rate. The administrator uses the command renice -n -5 -p2864, but it does not solve the issue. Which of the following commands should the administrator execute to correct the issue?
- nice -n 5 -p 2864
- nice -n -5 -p 2864
- renice -n 10 -p 2864
- renice -n -10 -p 2864
- DRAG DROPYou have been asked to parse a log file of logins to determine various information about who is logging in and when.INSTRUCTIONSOpen and inspect the Login log file.Drag and drop the correct commands onto the output that was generated from that command.Tokens can be used only once and not all will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
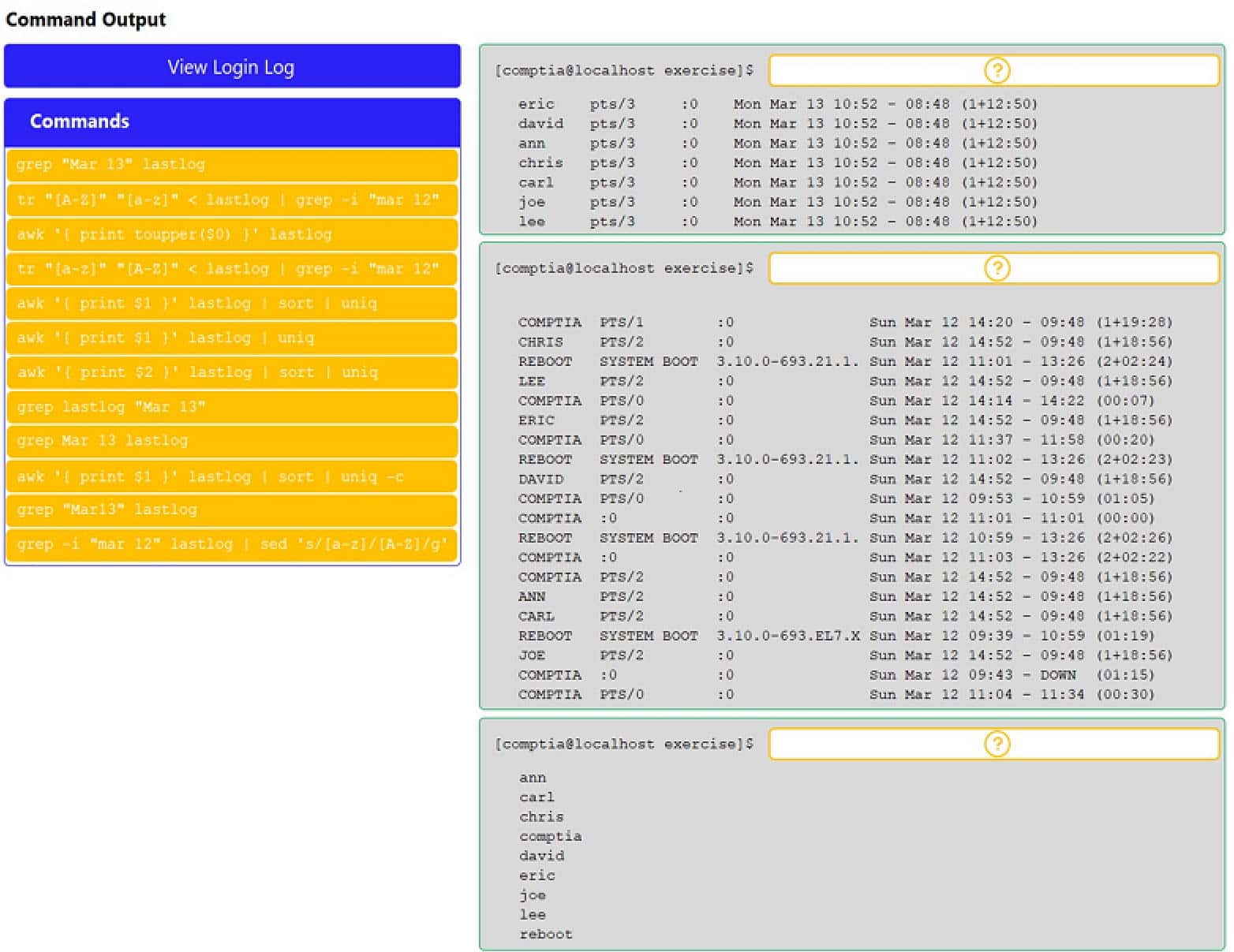
XK0-004 Part 07 Q10 047 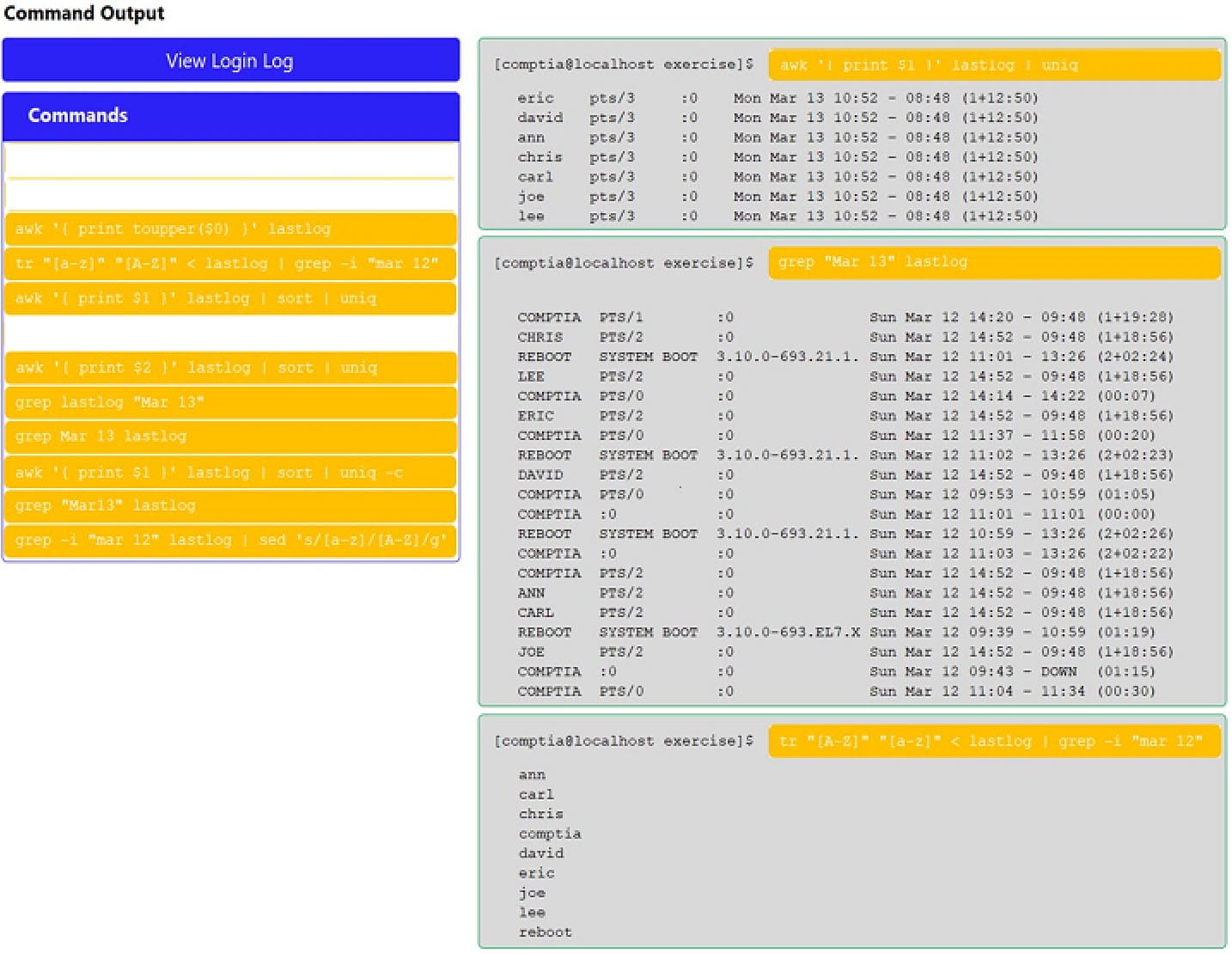
XK0-004 Part 07 Q10 048 -
A systems administrator wants to download a package from a remote server. Which of the following are the BEST commands to use for this task? (Choose two.)
- curl
- wget
- make
- tar
- zip
- nc
-
An administrator is logged into a server remotely and wants to determine if the system is a VM. Which of the following commands would assist with this?
- dmesg
- ps
- top
- vmstat
-
Ann, a Linux administrator, wants to edit a configuration management file. When she opens the file to edit, her text editor reports that the file has been opened in read-only mode. She then tries to edit the file as root by elevating via sudo and is still unable to save any changes. The error message in her text editor says that the read-only option is set on the file. Ann checks the permissions on the file and sees the following:
-rw-rw-r– 1 root wheel 30 Jun 13 15:38 infrastructure.yml
Which of the following commands is the BEST option to allow her to successfully modify the file?
- chmod 600 infrastructure.yml
- chown root: infrastructure.yml
- chattr -i infrastructure.yml
- chmod o+w infrastructure.yml
-
Joe, a member of the accounting group on a Linux system, is unable to write a file called “taxes” in the accounting shared directory. The ownership and permissions on the directory and file are as follows:
accounting drwxrw-r– user = ann, group = accounting
taxes -rw-r–r– , user = ann, group = accountingWhich of the following commands would allow Joe to write to the file? (Choose two.)
- chmod g+x accounting
- chmod 777 taxes
- chgrp taxes accounting
- chgrp accounting taxes
- chmod 774 accounting
- chmod u+x accounting
-
An administrator needs to generate a list of services that are listening on TCP and/or UDP ports. Which of the following tools should the administrator use?
- ethtool
- route
- netstat
- portmap
-
Ann, a user, has created a new directory and noticed that permissions on the new directory are as follows:
drwx——. 1 ann ann 0 Jun 11 08:20 work
Which of the following should the administrator do to restore default permissions for newly created directories?
- Change umask value in /etc/profile.
- Run chmod command to update permissions.
- Modify directory ownership to ann:ann with chown.
- Execute chattr command to restore default access.
-
A Linux engineer is troubleshooting a newly added SCSI device for a Linux server that needed more disk space without rebooting. The engineer discovers that the new device is not visible by the Linux kernel in fdisk -l output. Which of the following commands should be used to rescan the entire SCSI bus?
- echo “- – -” > /sys/class/scsi_host/host0/scan
- echo ‘ ‘ > /sys/class/scsi_host/host0/scan
- echo “- – -” > /sys/scsi/scsi_host/host0/scan
- echo “scan” > /sys/class/scsi_host/host0/scan
-
A systems administrator is troubleshooting an intermittent network connection at the IP address 192.168.1.23. The administrator wishes to monitor the connection at five-minute intervals for one hour. Which of the following commands will accomplish this task?
- ping -i 5 192.168.1.23
- ping -c 12 192.168.1.23
- ping -c 12 -i 300 192.168.1.23
- ping -c 60 -i 100 192.168.1.23
-
A systems administrator wants to mount an ISO to access its content. Using /mnt as a mount point, which of the following is the correct syntax?
- mount -o iso9660 /dev/sr0 /mnt
- mount -o loop -t iso /mnt
- mount -o loop /tmp/image.iso /mnt
- mount -o loop /dev/kvm /mnt
-
An administrator is uncomfortable allowing users to log in as root. Which of the following ensures that root logins are disallowed?
- usermod -L root
- usermod -G root
- usermod -B root
- usermod -U root