CyberOps Associate 1.02 & CA v1.0 Modules 11 – 12: Network Infrastructure Security Group Exam Answers 2025 Full 100%
CyberOps Associate 1.02 & CA v1.0 Modules 11 – 12: Network Infrastructure Security Group Exam Answers Full 100% 2025
These are both versions of NetAcad Cisco CA 1.02 and CyberOps Associate (Version 1.0) – Modules 11 – 12: Network Infrastructure Security Group Exam Full 100% in 2025 verified by experts with explanations and hints.
| CyberOps - Associate 1.0 & 1.01 | |
| Final Exam Answers | |
| This Modules 11 - 12 | |
| Modules 11 - 12 Exam Answers | Online Test |
| Next Modules 13 - 17 | |
| Modules 13 - 17 Exam Answers | Online Test |
-
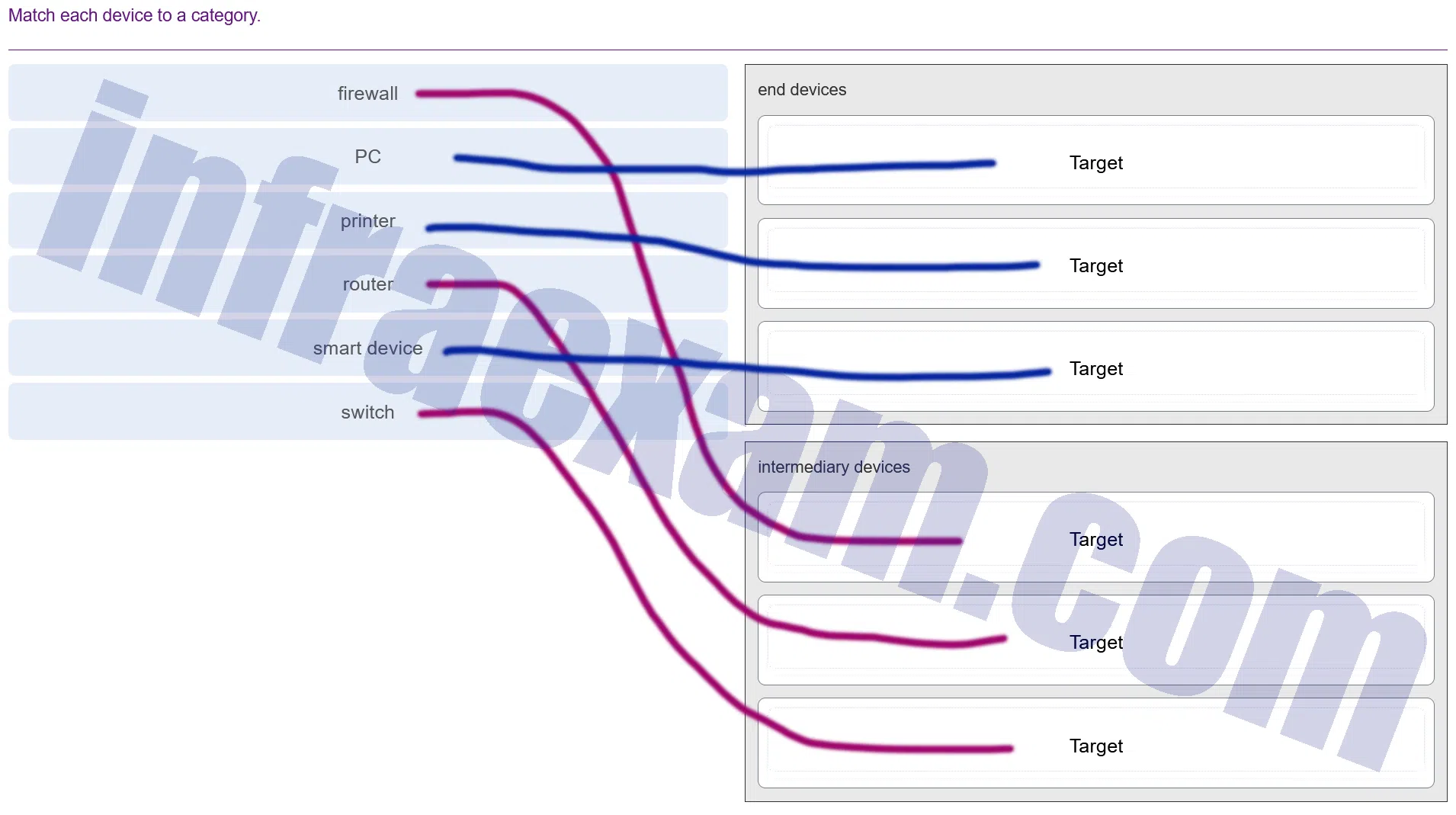
Match each device to a category.
Modules 11 – 12 Network Infrastructure Security Group Exam Answers 001 Explanation & Hint: Here’s how the devices typically categorize:
End devices usually include those that are at the end of the network communication process. In a typical network, these are the devices used by the end-user to interact with the network. Examples include:
- PC
- Printer
- Smart device (depending on context, this could be an end device or sometimes it can function as an intermediary device if it’s part of IoT infrastructure)
Intermediary devices are the devices that connect the end devices to the network and can also connect multiple networks together. They are responsible for managing and directing the data flow through the network. Examples include:
- Firewall
- Router
- Switch
-
A Cisco router is running IOS 15. What are the two routing table entry types that will be added when a network administrator brings an interface up and assigns an IP address to the interface? (Choose two.)
- directly connected interface
- local route interface
- route that is learned via EIGRP
- route that is learned via OSPF
- route that is manually entered by a network administrator
Answers Explanation & Hints: A local route interface routing table entry is found when a router runs IOS 15 or higher or if IPv6 routing is enabled. Whenever an interface is addressed and enabled (made active), a directly connected interface is automatically shown in the routing table.
-
What are two types of addresses found on network end devices? (Choose two.)
- IP
- MAC
- return
- TCP
- UDP
Answers Explanation & Hints: Intermediary devices use two types of addresses when sending messages to the final destination device, MAC and IP addresses. TCP and UDP are protocols used at Layer 4 to identify what port numbers are being used on the source and destination devices. A return address is used when mailing a letter, not in networking.
-
What information within a data packet does a router use to make forwarding decisions?
- the destination MAC address
- the destination IP address
- the destination host name
- the destination service requested
Answers Explanation & Hints: A Layer 3 device like a router uses a Layer 3 destination IP address to make a forwarding decision.
-
What type of route is created when a network administrator manually configures a route that has an active exit interface?
- static
- directly connected
- local
- dynamic
Answers Explanation & Hints: A static route is one that is manually configured by the network administrator.
-
In which memory location is the routing table of a router maintained?
- RAM
- NVRAM
- flash
- ROM
Answers Explanation & Hints: The routing table of a router is maintained in RAM, which is volatile memory. If a router loses power or is rebooted, the content of RAM is lost and the routing table must be rebuilt.
-
Which routing protocol is used to exchange routes between internet service providers?
- ISIS
- OSPF
- EIGRP
- BGP
- RIP
Answers Explanation & Hints: The routing table of a router is maintained in RAM, which is volatile memory. If a router loses power or is rebooted, the content of RAM is lost and the routing table must be rebuilt.
-
Which two protocols are link-state routing protocols? (Choose two.)
- OSPF
- ISIS
- BGP
- RIP
- EIGRP
Answers Explanation & Hints: ISIS and OSPF are link-state routing protocols. EIGRP and RIP are distance vector routing protocols. BGP is a path vector protocol.
-
What is a characteristic of a hub?
- regenerates signals received on one port out all other ports
- operates at Layer 2
- uses CSMA/CA to avoid collisions
- subdivides the network into collision domains
Answers Explanation & Hints: A hub is a Layer 1 device that regenerates signals out all ports other than the ingress port. All ports on a hub belong to the same collision domain. Hubs use CSMA/CD to detect collisions on the network.
-
What action does an Ethernet switch take when it receives a frame with an unknown Layer 2 source address?
- It records the source address in the address table of the switch.
- It drops the frame.
- It forwards the frame out all interfaces except the interface on which it was received.
- It forwards the frame to the default gateway.
Answers Explanation & Hints: When an Ethernet switch receives a frame with an unknown Layer 2 address, the switch records that address in the address table.
-
What is a characteristic of a routed port that is configured on a Cisco switch?
- It is assigned an IP address.
- It runs STP to prevent loops.
- It supports subinterfaces.
- It is associated with a single VLAN.
Answers Explanation & Hints: Routed ports on a Cisco switch behave similarly to those on a router. They are configured with an IP address and forward Layer 3 packets. Unlike Layer 2 switch interfaces, routed ports do not support STP, nor do they support subinterfaces as routers do.
-
What Wi-Fi management frame is regularly broadcast by APs to announce their presence?
- probe
- beacon
- association
- authentication
Answers Explanation & Hints: Beacon frames are broadcast periodically by the AP to advertise its wireless networks to potential clients. Probing, association, and authentication frames are only sent when a client is associating to the AP.
-
Which characteristic describes a wireless client operating in active mode?
- ability to dynamically change channels
- must know the SSID to connect to an AP
- must be configured for security before attaching to an AP
- broadcasts probes that request the SSID
Answers Explanation & Hints: A wireless client operating in active mode must know the name of the SSID. Probe requests are broadcast by a client across multiple channels and include the SSID name and supported standards. Active mode is used if an AP is configured to not broadcast beacon frames.
-
What is a characteristic of the WLAN passive discover mode?
- The AP periodically sends beacon frames containing the SSID.
- The beaconing feature on the AP is disabled.
- The client begins the discover process by sending a probe request.
- The client must know the name of the SSID to begin the discover process.
Answers Explanation & Hints: In passive mode, the wireless clients learn what networks and APs are available. The client learns this information from beacon frames, sent by the APs, that contain the WLAN SSID, supported standards, and security settings.
-
What is used on WLANs to avoid packet collisions?
- CSMA/CA
- STP
- VLANs
- SVIs
Answers Explanation & Hints: WLANs are half-duplex networks which means that only one client can transmit or receive at any given moment. WLANs use carrier sense multiple access with collision avoidance (CSMA/CA) to determine when to send data on the network to avoid packet collisions.
-
What is the first step in the CSMA/CA process when a wireless client is attempting to communicate on the wireless network?
- The client listens for traffic on the channel.
- The client sends an RTS message to the AP.
- The AP sends a CTS message to the client.
- The client sends a test frame onto the channel.
Answers Explanation & Hints: When a wireless client is attempting to communicate on the network, it will first listen to the channel to be sure it is idle. Next, the client sends an RTS message to the AP to request dedicated access to the network. The AP will then send a CTS message granting access to the client. The client will then transmit data.
-
What are the three parts of all Layer 2 frames? (Choose three.)
- header
- payload
- frame check sequence
- time-to-live
- sequence number
- source and destination IP address
Answers Explanation & Hints: Layer 2 frames have three components: the header, the payload, and a frame check sequence at the end.
-
Lightweight access points forward data between which two devices on the network? (Choose two.)
- wireless client
- wireless LAN controller
- wireless router
- default gateway
- autonomous access point
Answers Explanation & Hints: In a wireless deployment that is using lightweight access points (LWAPs), the LWAP forwards data between the wireless clients and the wireless LAN controller (WLC).
-
Which two devices would commonly be found at the access layer of the hierarchical enterprise LAN design model? (Choose two.)
- access point
- firewall
- Layer 2 switch
- Layer 3 device
- modular switch
Answers Explanation & Hints: While some designs do route at the access layer, the two devices that should always be placed at the access layer of the hierarchical design model are an access point and a Layer 2 switch. A modular switch is commonly used at the core layer. Routing by a Layer 3 device is commonly used in the distribution layer. The firewall is a device in the Internet edge network design.
-
Which statement describes one of the rules that govern interface behavior in the context of implementing a zone-based policy firewall configuration?
- An administrator can assign an interface to multiple security zones.
- An administrator can assign interfaces to zones, regardless of whether the zone has been configured.
- By default, traffic is allowed to flow among interfaces that are members of the same zone.
- By default, traffic is allowed to flow between a zone member interface and any interface that is not a zone member.
Answers Explanation & Hints: An interface can belong to only one zone. Creating a zone is the first step in configuring a zone-based policy firewall. A zone cannot be assigned to an interface if the zone has not been created. Traffic can never flow between an interface that is assigned to a zone and an interface that has not been assigned to a zone.
-
What is the function of the distribution layer of the three-layer network design model?
- providing direct access to the network
- aggregating access layer connections
- providing secure access to the Internet
- providing high speed connection to the network edge
Answers Explanation & Hints: The function of the distribution layer is to provide connectivity to services and to aggregate the access layer connections
-
What two components of traditional web security appliances are examples of functions integrated into a Cisco Web Security Appliance? (Choose two.)
- firewall
- URL filtering
- web reporting
- VPN connection
- email virus and spam filtering
Answers Explanation & Hints: The Cisco Web Security Appliance is a secure web gateway which combines advanced malware protection, application visibility and control, acceptable use policy controls, reporting, and secure mobility functions. With traditional web security appliances, these functions are typically provided through multiple appliances. It is not a firewall appliance in that it only filters web traffic. It does not provide VPN connections, nor does it provide email virus and spam filtering; the Cisco Email Security Appliance provides these functions.
-
What are two disadvantages of using an IDS? (Choose two.)
- The IDS has no impact on traffic.
- The IDS does not stop malicious traffic.
- The IDS works offline using copies of network traffic.
- The IDS requires other devices to respond to attacks.
- The IDS analyzes actual forwarded packets.
Answers Explanation & Hints: The disadvantage of operating with mirrored traffic is that the IDS cannot stop malicious single-packet attacks from reaching the target before responding to the attack. Also, an IDS often requires assistance from other networking devices, such as routers and firewalls, to respond to an attack. An advantage of an IDS is that by working offline using mirrored traffic, it has no impact on traffic flow.
-
What is an advantage of HIPS that is not provided by IDS?
- HIPS provides quick analysis of events through detailed logging.
- HIPS deploys sensors at network entry points and protects critical network segments.
- HIPS monitors network processes and protects critical files.
- HIPS protects critical system resources and monitors operating system processes.
Answers Explanation & Hints: Network-based IDS (NIDS) sensors are typically deployed in offline mode. They do not protect individual hosts. Host-based IPS (HIPS) is software installed on a single host to monitor and analyze suspicious activity. It can monitor and protect operating system and critical system processes that are specific to that host. HIPS can be thought of as a combination of antivirus software, antimalware software, and a firewall.
-
Which firewall feature is used to ensure that packets coming into a network are legitimate responses to requests initiated from internal hosts?
- stateful packet inspection
- URL filtering
- application filtering
- packet filtering
Answers Explanation & Hints: Stateful packet inspection on a firewall checks that incoming packets are actually legitimate responses to requests originating from hosts inside the network. Packet filtering can be used to permit or deny access to resources based on IP or MAC address. Application filtering can permit or deny access based on port number. URL filtering is used to permit or deny access based on URL or on keywords.
-
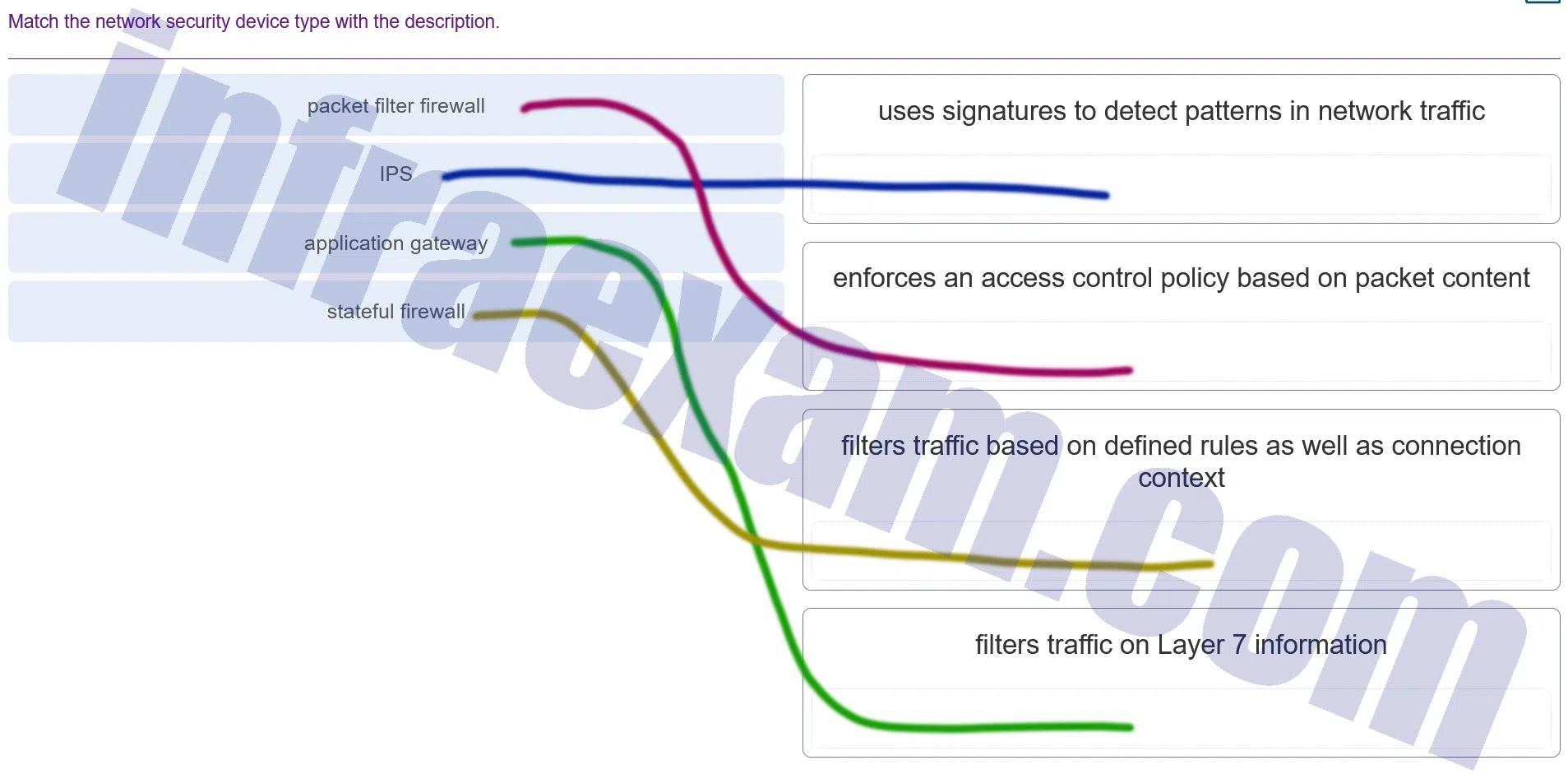
Match the network security device type with the description.
Modules 11 – 12 Network Infrastructure Security Group Exam Answers 002 Explanation & Hint: - Packet filter firewall: This device filters traffic based on defined rules such as IP addresses, ports, or protocols but does not maintain any state information about connections. It would match the description “filters traffic based on defined rules as well as connection context,” although the latter part of the description might more accurately describe a stateful firewall.
- IPS (Intrusion Prevention System): This device actively monitors network traffic to identify and respond to suspicious activity by using signatures to detect patterns. Therefore, it matches the description “uses signatures to detect patterns in network traffic.”
- Application gateway (also known as a proxy firewall or application-level gateway): This operates at the higher layers of the OSI model to filter traffic based on the payload of packets, which can include specific content, applications, or services. Hence, it matches “enforces an access control policy based on packet content.”
- Stateful firewall: This device keeps track of the state of active connections and makes decisions based on the context of the traffic (such as the state of the connection) as well as the defined rules. It corresponds to the description “filters traffic based on defined rules as well as connection context.”
- There is a description “filters traffic on Layer 7 information” which typically would match an application layer firewall or a web application firewall, which inspects traffic at the highest level in the OSI model, focusing on the actual content of the messages.
-
What is a host-based intrusion detection system (HIDS)?
- It is an agentless system that scans files on a host for potential malware.
- It identifies potential attacks and sends alerts but does not stop the traffic.
- It detects and stops potential direct attacks but does not scan for malware.
- It combines the functionalities of antimalware applications with firewall protection.
Answers Explanation & Hints: A current HIDS is a comprehensive security application that combines the functionalities of antimalware applications with firewall protection. An HIDS not only detects malware but also prevents it from executing. Because the HIDS runs directly on the host, it is considered an agent-based system.
-
In the data gathering process, which type of device will listen for traffic, but only gather traffic statistics?
- NMS
- syslog server
- NetFlow collector
- SNMP agent
Answers Explanation & Hints: A NetFlow collector is the device that receives traffic statistics from networking devices. NetFlow only gathers traffic statistics, unlike syslog and SNMP which can collect various network events.
-
Which AAA component can be established using token cards?
- accounting
- authorization
- auditing
- authentication
Answers Explanation & Hints: The authentication component of AAA is established using username and password combinations, challenge and response questions, and token cards. The authorization component of AAA determines which resources the user can access and which operations the user is allowed to perform. The accounting and auditing component of AAA keeps track of how network resources are used.
-
Which statement describes a difference between RADIUS and TACACS+?
- RADIUS uses TCP whereas TACACS+ uses UDP.
- RADIUS is supported by the Cisco Secure ACS software whereas TACACS+ is not.
- RADIUS encrypts only the password whereas TACACS+ encrypts all communication.
- RADIUS separates authentication and authorization whereas TACACS+ combines them as one process.
Answers Explanation & Hints: TACACS+ uses TCP, encrypts the entire packet (not just the password), and separates authentication and authorization into two distinct processes. Both protocols are supported by the Cisco Secure ACS software.
-
Which statement describes a VPN?
- VPNs use dedicated physical connections to transfer data between remote users.
- VPNs use logical connections to create public networks through the Internet.
- VPNs use open source virtualization software to create the tunnel through the Internet.
- VPNs use virtual connections to create a private network through a public network.
Answers Explanation & Hints: A VPN is a private network that is created over a public network. Instead of using dedicated physical connections, a VPN uses virtual connections routed through a public network between two network devices.
-
Which two statements are true about NTP servers in an enterprise network? (Choose two.)
- There can only be one NTP server on an enterprise network.
- All NTP servers synchronize directly to a stratum 1 time source.
- NTP servers at stratum 1 are directly connected to an authoritative time source.
- NTP servers ensure an accurate time stamp on logging and debugging information.
- NTP servers control the mean time between failures (MTBF) for key network devices.
Answers Explanation & Hints: Network Time Protocol (NTP) is used to synchronize the time across all devices on the network to make sure accurate timestamping on devices for managing, securing and troubleshooting. NTP networks use a hierarchical system of time sources. Each level in this hierarchical system is called a stratum. The stratum 1 devices are directly connected to the authoritative time sources.
-
What is a function of SNMP?
- provides statistical analysis on packets flowing through a Cisco router or multilayer switch
- provides a message format for communication between network device managers and agents
- captures packets entering and exiting the network interface card
- synchronizes the time across all devices on the network
Answers Explanation & Hints: SNMP is an application layer protocol that allows administrators to manage devices on the network by providing a messaging format for communication between network device managers and agents.
-
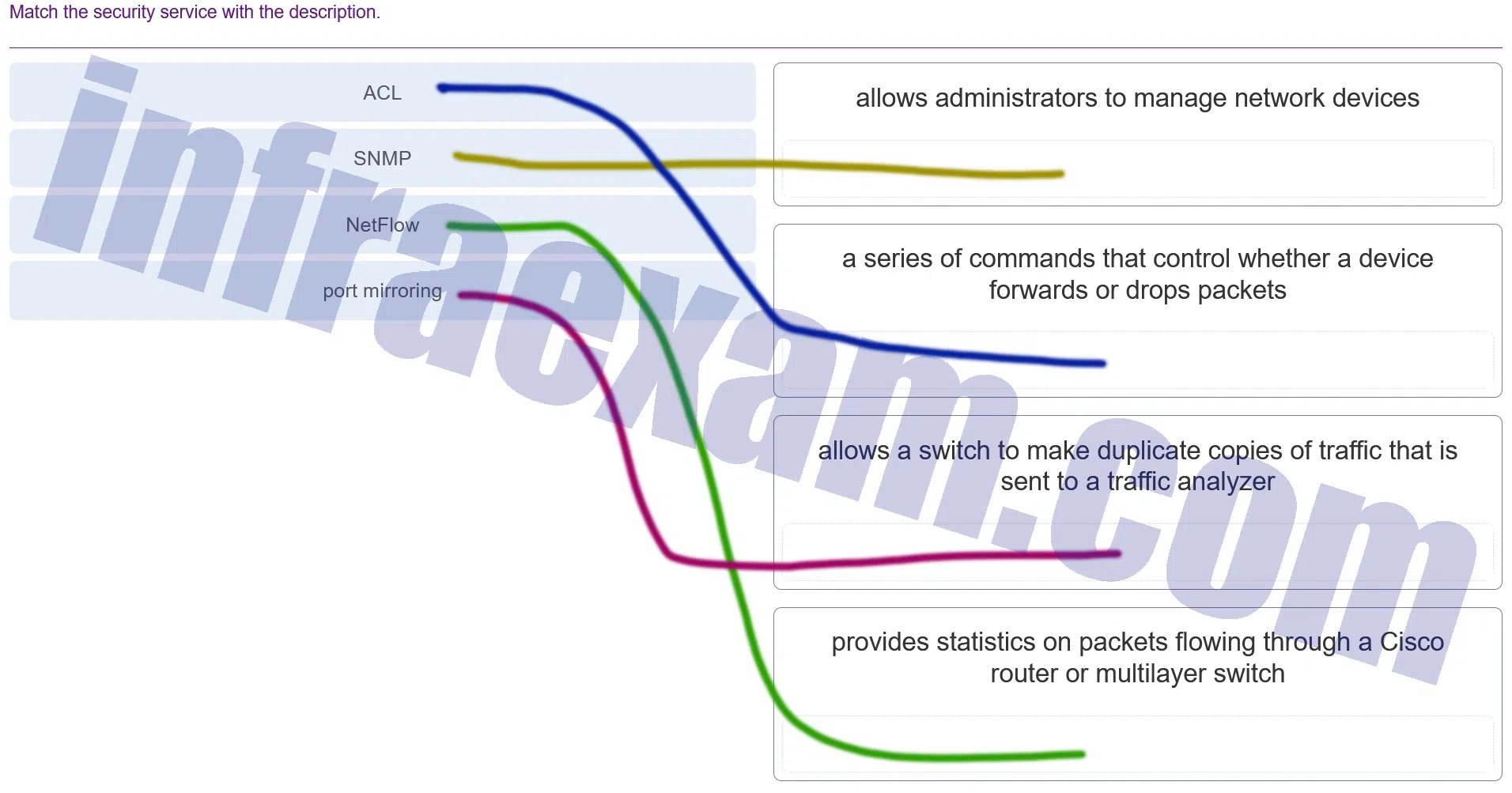
Match the security service with the description.
Modules 11 – 12 Network Infrastructure Security Group Exam Answers 003 Explanation & Hint: - ACL (Access Control List): This is a series of commands that control whether a device forwards or drops packets. ACLs define which users or system processes are granted access to objects, as well as what operations are allowed on given objects.
- SNMP (Simple Network Management Protocol): This allows administrators to manage network devices. SNMP is used in network management systems to monitor network-attached devices for conditions that warrant administrative attention.
- NetFlow: This provides statistics on packets flowing through a Cisco router or multilayer switch. NetFlow is a feature that was introduced on Cisco routers that provides the ability to collect IP network traffic as it enters or exits an interface.
- Port Mirroring: This allows a switch to make duplicate copies of traffic that is sent to a traffic analyzer. Port mirroring is a method used on a network switch to send a copy of network packets seen on one switch port to a network monitoring connection on another switch port.
-
Which technique is necessary to ensure a private transfer of data using a VPN?
- authorization
- encryption
- scalability
- virtualization
Answers Explanation & Hints: Confidential and secure transfers of data with VPNs require data encryption.
| CyberOps - Associate 1.0 & 1.01 | |
| Final Exam Answers | |
| This Modules 11 - 12 | |
| Modules 11 - 12 Exam Answers | Online Test |
| Next Modules 13 - 17 | |
| Modules 13 - 17 Exam Answers | Online Test |